Antijamming Schemes for the Generalized MIMO Y Channel
Abstract
:1. Introduction and Related Work
- Two antijamming schemes are proposed for the SSA-based MIMO Y channel with a single-antenna jammer. In the first scheme, the jamming signal and interferences are projected onto the null space of each signal pair, while the second scheme removes interference originating from the jammer at the relay by subtracting the disturbance estimate from the incoming signal.
- The results of Monte Carlo simulations are provided and compared with those received for the SSA-based MIMO Y channel for the iterative beamforming optimization algorithm presented in [24] for two scenarios when the jammer is present or not. These results can be treated as an upper bound for the proposed jammer scenarios.
2. System Model
2.1. Antijamming Schemes in the MA Phase
2.1.1. Antijamming Signal Space Alignment (AJ-SSA)
2.1.2. Jammer’s Interference Cancellation (J-IC)
2.2. Computational Complexity of the Proposed Algorithms
- —transposing an matrix has time complexity ;
- —matrix multiplication resulting in a matrix with complexity ;
- —inverting an matrix has complexity ;
- —multiplying with has complexity ;
- multiplying the result with has complexity of ;
- subtracting with of size is straightforward and has complexity ;
2.3. Antijamming Signal Space Alignment in the BC Phase
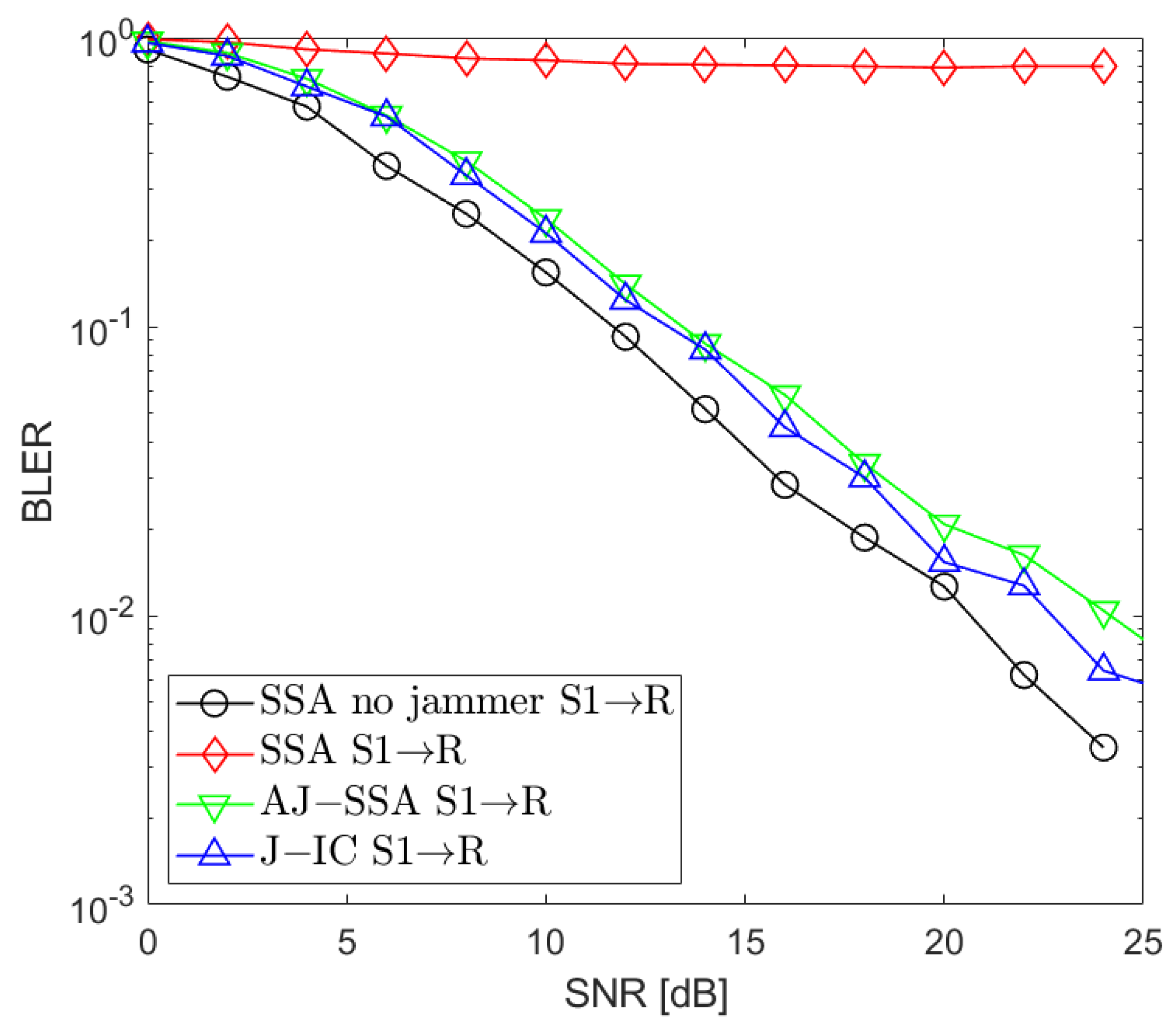
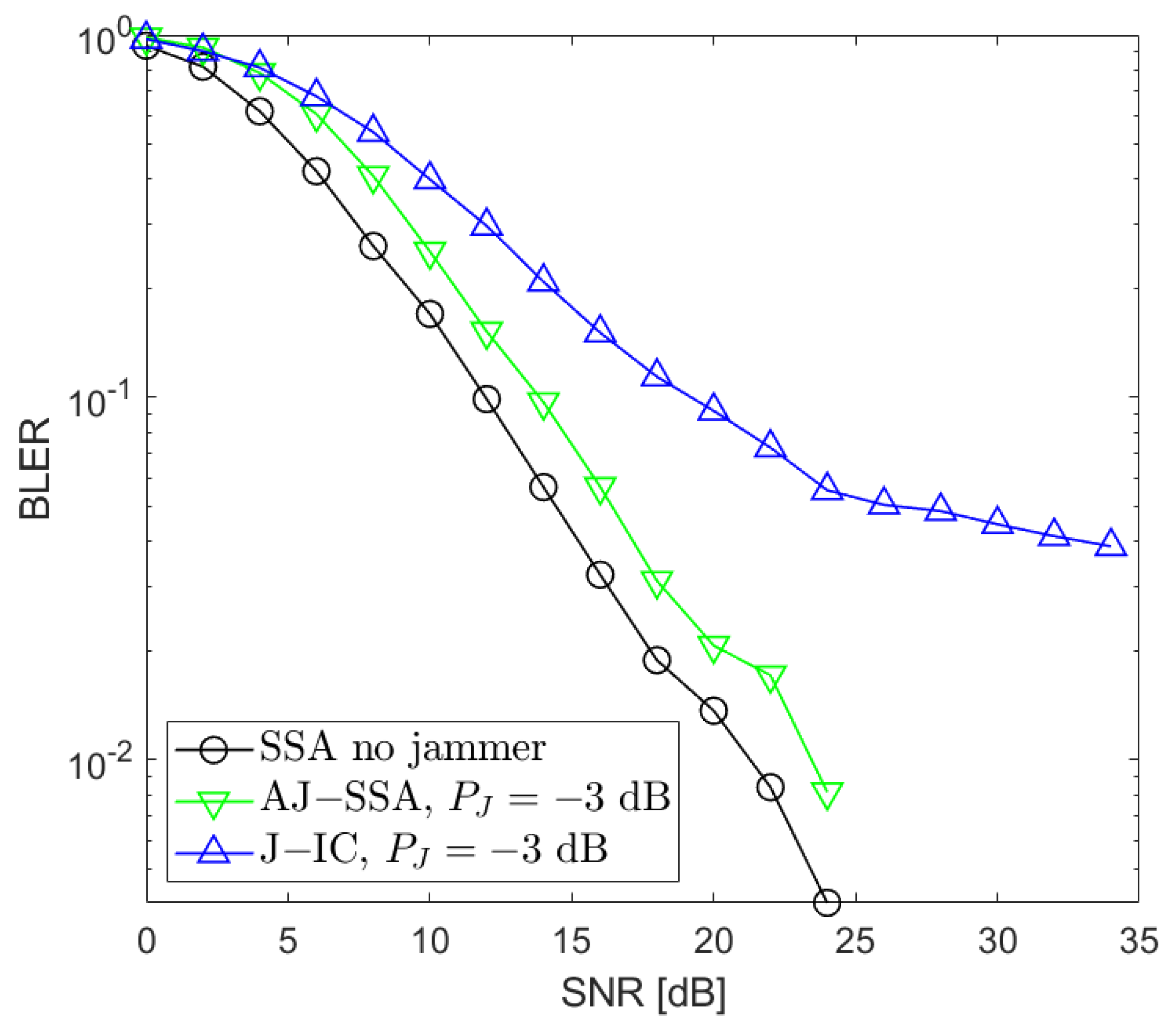
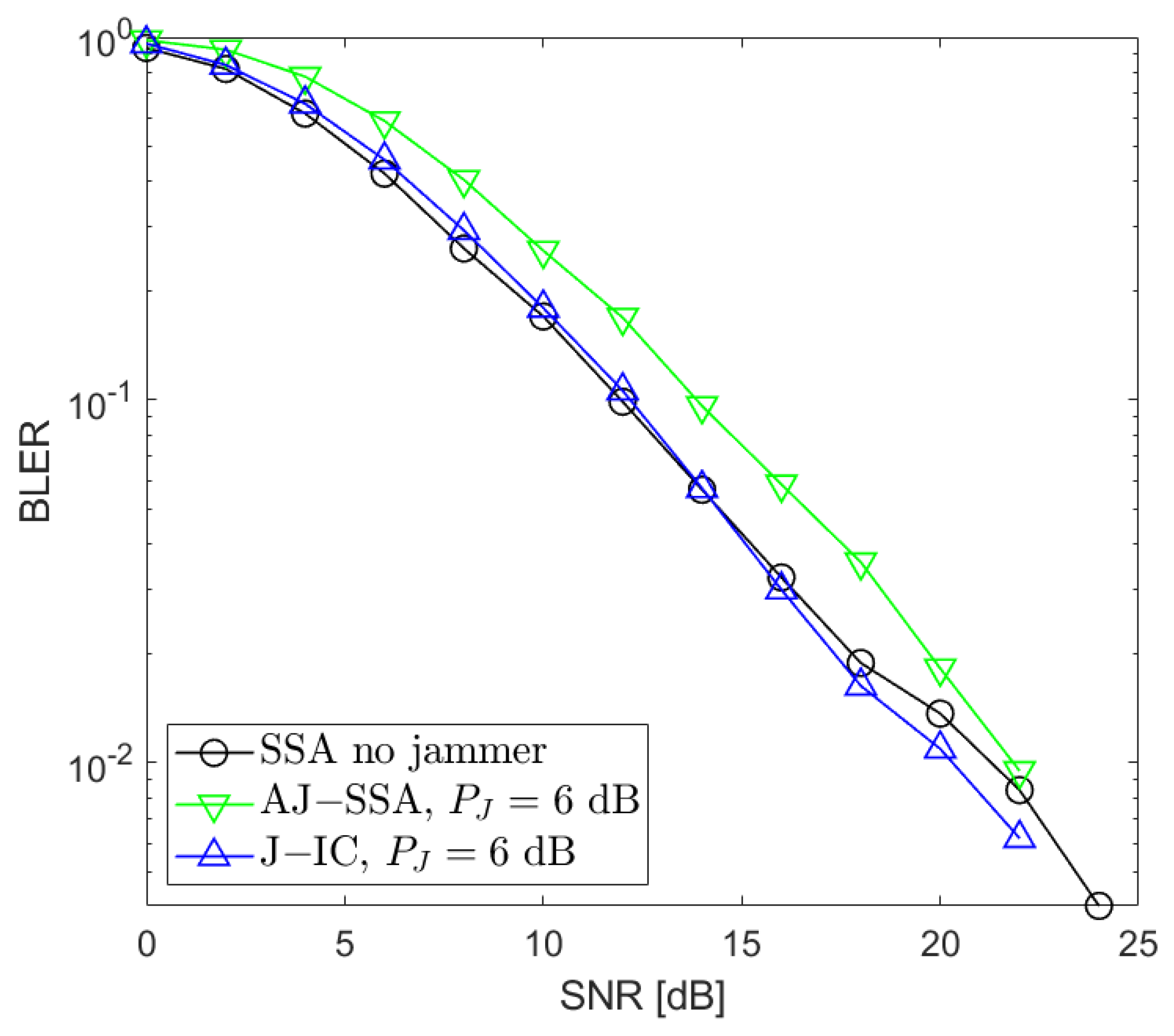
3. Simulation Results
3.1. Simulation Procedure and Parameters
3.2. Simulation Results
4. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| ANC | Analog Network Coding |
| ARQ | Automatic Repeat reQuest |
| AWGN | Additive White Gaussian Noise |
| BC | Broadcast |
| BER | Bit Error Rate |
| BLER | Block Error Rate |
| CSI | Channel State Information |
| DOF | Degrees Of Freedom |
| EPA | Extended Pedestrian A Model |
| GSA | Generalized Signal Alignment |
| IA | Interference Alignment |
| MA | Multiple Access |
| MIMO | Multiple-Input–Multiple-Output |
| MinIL | Minimizing Interference Leakage |
| NC | Network Coding |
| OIA | Opportunistic IA |
| PNC | Physical-Layer Network Coding |
| RS | Relay Station |
| SINR | Signal-to-Interference-and-Noise Ratio |
| SNR | Signal-to-Noise Ratio |
| SSA | Signal Space Alignment |
| SVD | Singular Value Decomposition |
| VRB | Virtual Resource Block |
References
- Jafar, S.; Shamai, S. Degrees of freedom region for the MIMO X channel. IEEE Trans. Inf. Theory 2008, 54, 151–170. [Google Scholar] [CrossRef]
- Ahlswede, R.; Cai, N.; Li, S.-Y.R.; Yeung, R.W. Network information flow. IEEE Trans. Inf. Theory 2000, 46, 1204–1216. [Google Scholar] [CrossRef]
- Zhang, S.; Liew, S.C.; Lam, P. Physical Layer Network Coding. In Proceedings of the Twelfth Annual International Conference on Mobile Computing and Networking ACM MobiCom’06, Los Angeles, CA, USA, 23–29 September 2006. [Google Scholar]
- Katti, S.; Gollakota, S.; Katabi, D. Embracing wirelss interference: Analog network coding. In Computer Science and Artificial Intelligence Laboratory Technical Report; Association for Computing Machinery: New York, NY, USA, 2007. [Google Scholar]
- Chen, M.; Yener, A. Multiuser two-way relaying for interference limited systems. In Proceedings of the IEEE International Conference on Communication, Beijing, China, 19–23 May 2008. [Google Scholar]
- Lee, N.; Lim, J.B. A novel signaling for communication on MIMO Y channel: Signal space alignment for network coding. In Proceedings of the 2009 IEEE International Symposium on Information Theory, Seoul, Republic of Korea, 28 June–3 July 2009; pp. 2892–2896. [Google Scholar]
- Lee, N.; Lim, J.B.; Chun, J. Degrees of freedom of the MIMO Y channel: Signal space alignment for network coding. IEEE Trans. Inf. Theory 2010, 56, 3332–3342. [Google Scholar] [CrossRef]
- Lee, K.; Lee, N.; Lee, I. Feasibility conditions of signal space alignment for network coding on k-user MIMO Y channels. In Proceedings of the IEEE International Conference on Communications, Kyoto, Japan, 5–9 June 2011. [Google Scholar]
- Wang, N.; Ding, Z.; Dai, X.; Vasilakos, A.V. On Generalized MIMO Y Channels: Precoding Design, Mapping, and Diversity Gain. IEEE Trans. Veh. Technol. 2011, 60, 3525–3532. [Google Scholar] [CrossRef]
- Teav, K.K.; Zhou, Z.; Vucetic, B. Throughput Optimization for MIMO Y Channels with Physical Network Coding and Adaptive Modulation. In Proceedings of the IEEE 75th Vehicular Technology Conference (VTC Spring), Yokohama, Japan, 6–9 May 2012; pp. 1–5. [Google Scholar]
- Teav, K.K.; Zhou, Z.; Vucetic, B. Performance Optimization of MIMO Y Channels: Interference Alignment and Signal Detection. IEEE Commun. Lett. 2014, 18, 66–69. [Google Scholar] [CrossRef]
- Li, Q.; Li, H.; Wu, G.; Li, S. Retrospective Network Coding Alignment Over K-User MIMO Y Channel. IEEE Commun. Lett. 2016, 20, 502–505. [Google Scholar] [CrossRef]
- Li, Q.; Li, H.; Wu, G.; Li, S. Degrees of freedom of MIMO Y channel with three semi-blind users. In Proceedings of the 2016 25th Wireless and Optical Communication Conference (WOCC), Chengdu, China, 21–23 May 2016; pp. 1–5. [Google Scholar]
- Zhou, R.; Li, Z.; Wu, C.; Williamson, C. Signal Alignment: Enabling Physical Layer Network Coding for MIMO Networking. IEEE Trans. Wirel. Commun. 2013, 12, 3012–3023. [Google Scholar] [CrossRef]
- Liu, K.; Xiang, Z.; Tao, M.; Wang, X. An efficient beamforming scheme for generalized MIMO two-way X relay channels. In Proceedings of the 2013 IEEE International Conference on Communications (ICC), Budapest, Hungary, 9–13 June 2013; pp. 5306–5310. [Google Scholar]
- Liu, K.; Tao, M.; Xiang, Z.; Long, X. Generalized signal alignment for MIMO two-way X relay channels. In Proceedings of the 2014 IEEE International Conference on Communications (ICC), Sydney, NSW, Australia, 10–14 June 2014; pp. 4436–4441. [Google Scholar]
- Liu, K.; Tao, M.; Yang, D. Generalized signal alignment for arbitrary MIMO two-way relay channels. In Proceedings of the 2014 IEEE Global Communications Conference, Austin, TX, USA, 8–12 December 2014; pp. 1661–1666. [Google Scholar]
- Liu, K.; Tao, M. Generalized Signal Alignment: On the Achievable DoF for Multi-User MIMO Two-Way Relay Channels. IEEE Trans. Inf. Theory 2015, 61, 3365–3386. [Google Scholar]
- Long, W.; Gao, H.; Lv, T. Asymmetric signal space alignment for multi-pair two-way relaying network. In Proceedings of the 2014 IEEE International Conference on Communications Workshops (ICC), Sydney, NSW, Australia, 10–14 June 2014; pp. 308–313. [Google Scholar]
- Ali, S.S.; Castanheira, D.; Silva, A.; Gameiro, A. Joint signal alignment and physical network coding for heterogeneous networks. In Proceedings of the 2016 23rd International Conference on Telecommunications (ICT), Thessaloniki, Greece, 16–18 May 2016; pp. 1–5. [Google Scholar]
- Chan, T.-T.; Lok, T.-M. Signal-Aligned Network Coding in Interference Channels with Limited Receiver Cooperation. In Proceedings of the 2018 IEEE/CIC International Conference on Communications in China (ICCC), Beijing, China, 16–18 August 2018; pp. 573–577. [Google Scholar]
- Chan, T.-T.; Lok, T.-M. Reverse Signal-Aligned Network Coding in Interference Channels with Limited Transmitter Cooperation. In Proceedings of the 2018 IEEE International Conference on Signal Processing, Communications and Computing (ICSPCC), Qingdao, China, 14–16 September 2018; pp. 1–6. [Google Scholar]
- Zhou, Z.; Vucetic, B. Beamforming optimization for generalized MIMO Y channels with both multiplexing and diversity. In Proceedings of the 2012 IEEE 75th Vehicular Technology Conference (VTC Spring), Yokohama, Japan, 6–9 May 2012; pp. 1–5. [Google Scholar]
- Zhou, Z.; Vucetic, B. An iterative beamforming optimization algorithm for generalized MIMO Y channels. In Proceedings of the 2012 IEEE International Conference on Communications (ICC), Ottawa, ON, Canada, 10–15 June 2012; IEEE: New York, NY, USA, 2012; pp. 4595–4599. [Google Scholar]
- Xu, W.; Ma, K.; Trappe, W.; Zhang, Y. Jamming sensor networks: Attack and defense strategies. IEEE Netw. 2006, 20, 41–47. [Google Scholar]
- Zhang, Y.; Dill, J. An anti-jamming algorithm using wavelet packet modulated spread spectrum. MILCOM 1999. In Proceedings of the IEEE Military Communications. Conference Proceedings, Atlantic City, NJ, USA, 31 October–3 November 1999; Volume 2, pp. 846–850. [Google Scholar]
- Popper, C.; Strasser, M.; Capkun, S. Anti-jamming broadcast communication using uncoordinated spread spectrum techniques. IEEE J. Sel. Areas Commun. 2010, 28, 703–715. [Google Scholar] [CrossRef]
- Wang, B.; Wu, Y.; Liu, K.J.R.; Clancy, T.C. An anti-jamming stochastic game for cognitive radio networks. IEEE J. Sel. Areas Commun. 2011, 29, 877–889. [Google Scholar] [CrossRef]
- He, X.; Dai, H.; Ning, P. Dynamic Adaptive Anti-Jamming via Controlled Mobility. IEEE Trans. Wirel. Commun. 2014, 13, 4374–4388. [Google Scholar] [CrossRef]
- Fang, S.; Liu, Y.; Ning, P. Wireless Communications under Broadband Reactive Jamming Attacks. IEEE Trans. Dependable Secur. Comput. 2016, 13, 394–408. [Google Scholar] [CrossRef]
- Akhlaghpas, H.; Björnson, E.; Razavizadeh, S.M. Jamming Suppression in Massive MIMO Systems. IEEE Trans. Circuits Syst. II Express Briefs 2020, 67, 182–186. [Google Scholar]
- Pirayesh, H.; Zeng, H. Jamming Attacks and Anti-Jamming Strategies in Wireless Networks: A Comprehensive Survey. IEEE Commun. Surv. Tutor. 2022, 24, 767–809. [Google Scholar] [CrossRef]
- Guo, J.; Zhao, N.; Yu, F.R.; Li, M.; Leung, V.C.M. A novel anti-jamming scheme for interference alignment (IA)-based wireless networks. In Proceedings of the 2015 IEEE/CIC International Conference on Communications in China (ICCC), Shenzhen, China, 2–4 November 2015; pp. 1–5. [Google Scholar]
- Zhao, N.; Guo, J.; Yu, F.R.; Li, M.; Leung, V.C.M. Antijamming schemes for interference-alignment-based wireless networks. IEEE Trans. Veh. Technol. 2017, 66, 1271–1283. [Google Scholar] [CrossRef]
- Guo, J.; Cao, Y.; Yang, Z.; Zhao, N.; Yu, F.R.; Chen, Y.; Leung, V.C.M. Beneficial jamming design for interference alignment networks. In Proceedings of the 2017 9th International Conference on Wireless Communications and Signal Processing (WCSP), Nanjing, China, 11–13 October 2017; pp. 1–6. [Google Scholar]
- Kumar, N.; Pradhan, P.M. Development of a minimum interference leakage based interference aligned network in presence of jammers. In Proceedings of the 2018 IEEE International Conference on Advanced Networks and Telecommunications Systems (ANTS), Indore, India, 16–19 December 2018; pp. 1–5. [Google Scholar]
- Zhou, Z.; Vucetic, B. An orthogonal projection optimization algorithm for multi-user MIMO channels. In Proceedings of the 2010 IEEE 71st Vehicular Technology Conference, Taipei, Taiwan, 16–19 May 2010; IEEE: New York, NY, USA, 2010; pp. 1–5. [Google Scholar]
- Tong, L.; Zhao, Q. Joint order detection and blind channel estimation by least squares smoothing. IEEE Trans. Signal Process. 1999, 47, 2345–2355. [Google Scholar] [CrossRef]
- Scaglione, A.; Giannakis, G.B.; Barbarossa, S. Redundant filterbank precoders and equalizers. II. Blind channel estimation, synchronization, and direct equalization. IEEE Trans. Signal Process. 1999, 47, 2007–2022. [Google Scholar] [CrossRef]
- Darsena, D.; Gelli, G.; Iudice, I.; Verde, F. Detection and blind channel estimation for UAV-aided wireless sensor networks in smart cities under mobile jamming attack. IEEE Internet Things J. 2022, 9, 11932–11950. [Google Scholar] [CrossRef]
- Lu, C.; Chen, P. Robust channel estimation scheme for multi-UAV mmWave MIMO communication with jittering. Electronics 2023, 12, 2102. [Google Scholar] [CrossRef]
- Muranov, K.; Smida, B.; Devroye, N. On blind channel estimation in full-duplex relay systems. IEEE Trans. Wirel. Commun. 2021, 20, 4685–4701. [Google Scholar] [CrossRef]
- Lin, T.-C.; Phoong, S.-M. Blind channel estimation in OFDM-based amplify-and-forward two-way relay networks. In Proceedings of the IEEE International Conference on Acoustics, Speech, and Signal Processing (ICASSP), Shanghai, China, 20–25 March 2016; pp. 3816–38120. [Google Scholar]
- Chiong, C.W.R.; Xiang, Y. Blind estimation of MIMO relay channels. In Proceedings of the IEEE Workshop on Statistical Signal Processing (SSP), Gold Coast, QLD, Australia, 29 June–2 July 2014; pp. 400–403. [Google Scholar]
- Luo, W.; Jin, H.; Li, H.; Liu, K.; Yang, E. A Novel complex-valued blind source separation and its applications in integrated reception. Electronics 2023, 12, 3954. [Google Scholar] [CrossRef]





| Parameter | Value |
|---|---|
| Radio channel | EPA 5 Hz |
| Channel estimation | Ideal |
| Channel coding | LDPC NR, rate 1/3 |
| Modulation | QPSK |
| Multiplexing | OFDM |
| Subcarrier spacing | 60 kHz |
| Slot length | 0.25 ms |
| OFDM symbol length | 16.67 μs |
| CP length | 1.2 μs |
| Subframes in a frame | 10 |
| Slots in a subframe | 4 |
| Slot length | 0.25 ms |
| OFDM symbols in a slot | 14 |
| Subcarriers in a PRB | 12 |
| PRB width | 0.72 MHz |
| Number of PRBs | 6 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lenarska, K.; Wesołowski, K. Antijamming Schemes for the Generalized MIMO Y Channel. Sensors 2024, 24, 3237. https://doi.org/10.3390/s24103237
Lenarska K, Wesołowski K. Antijamming Schemes for the Generalized MIMO Y Channel. Sensors. 2024; 24(10):3237. https://doi.org/10.3390/s24103237
Chicago/Turabian StyleLenarska, Karolina, and Krzysztof Wesołowski. 2024. "Antijamming Schemes for the Generalized MIMO Y Channel" Sensors 24, no. 10: 3237. https://doi.org/10.3390/s24103237







