User-Centric Key Entropy: Study of Biometric Key Derivation Subject to Spoofing Attacks
Abstract
:1. Introduction
2. Literature Review
3. System Implementation Details
3.1. Fingerprint Feature Extraction
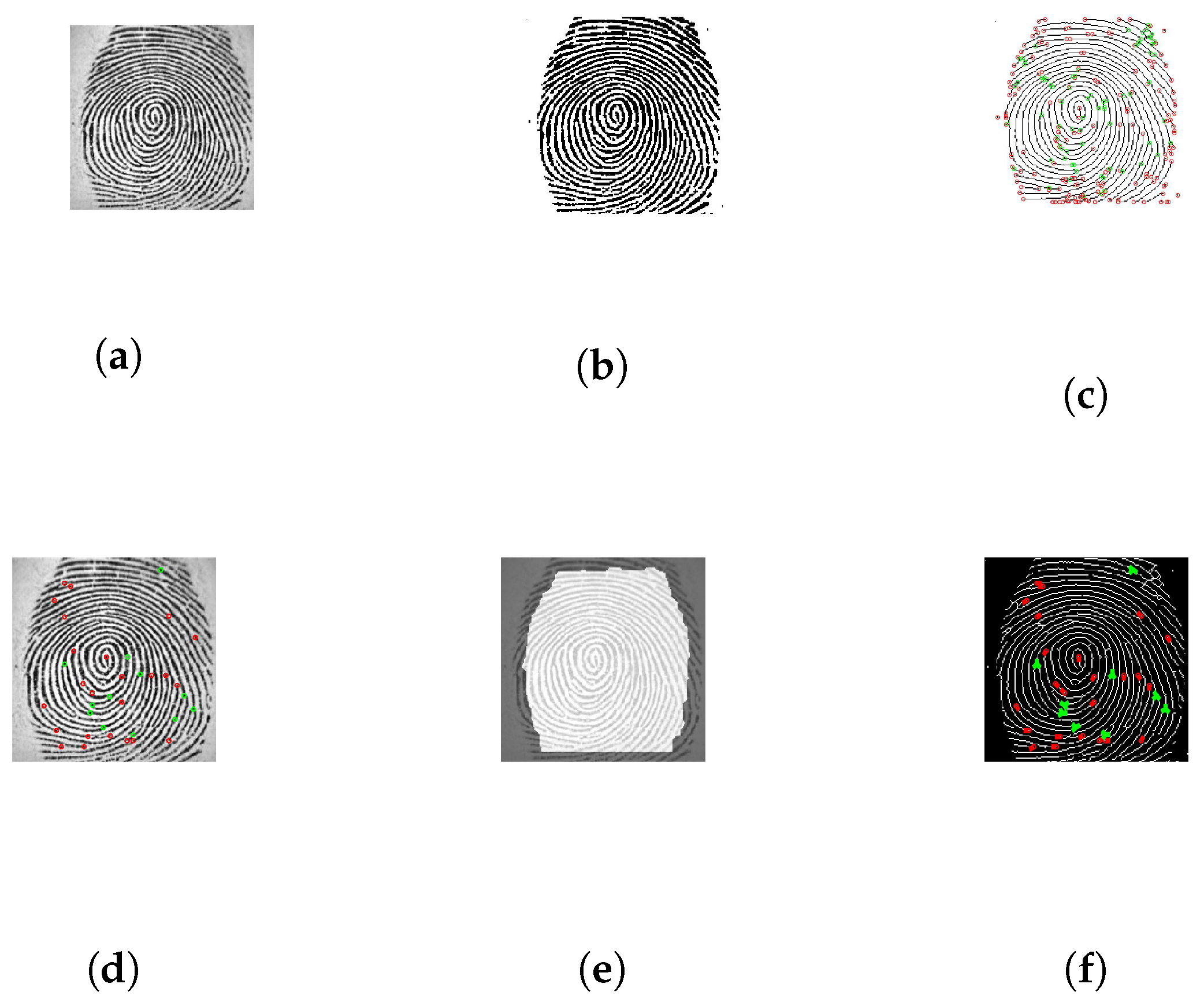
- Image pre-processing, depicted in Figure 1a. Image enhancement is very important because the quality of the extraction process is dependant on the enhancement algorithm. Image enhancement is done by applying Gabor Filter to the image. Another important step in the preprocessing stage is limiting the search of the fingerprint extraction by only detecting and storing the position and orientation of bifurcations and terminations.
- Image binarization, depicted in Figure 1b. The purpose of this process is to differentiate between ridges marked with black and furrows marked with white.
- Image thinning and minutiae extraction, depicted in Figure 1c. The image is thinned so ridges are only one pixel wide, and all the redundant pixel information is eliminated. For minutiae extraction, the local neighbourhood of each pixel ridge is scanned using a 3 × 3 window. A pixel is either a termination (central pixel is 1 and 1 value neighbour), bifurcation (central pixel is 1 and 3 value neighbour), and usual pixel (central pixel is 1 and 2 value neighbour). The Terminations are marked with red and bifurcations with green.
- Minutiae processing, depicted in Figure 1d. This step eliminates minutiae that are too close together. If the distance between a termination and a bifurcation is smaller then a minimum accepted value d, then that minutiae is removed.
- ROI, depicted in Figure 1e. A Region of Interest is defined and based on that region the extra minutiae are omitted.
- Orientation, depicted in Figure 1f. When the minutiae extraction is complete, the orientation of each element, bifurcation, termination and their respective angles.
- Binary template. The extracted points are each binarised resulting in a binary biometric template.
3.2. Iris Feature Extraction
- Segmentation. Is the most important step and the success of this step determines the quality of the feature extraction. Image segmentation translates into isolating the iris image from the input image. Circular Hough transform is used to detect the boundaries of iris and pupil. Depending on the database quality specular reflections should be removed. The process is depicted in Figure 2a.
- Normalisation. This process creates fixed iris dimensions to allow comparisons, because no two iris images are alike due to different environmental factors when capturing the image, like: distance from the sensor, amount of light. Figure 2b,c depict normalised iris and noise corresponding to normalised image.
- Feature encoding. Feature encoding is done using 1D Log-Gabor wavelets, creating a iris bitwise template and a corresponding noise mask.
3.3. Extraction oF Biometric Key
Listing 1: Partial listing for RSA key generation.
public void generateKey(String features, int size, String fileName,
String path) {
try {
byte[] featuresBytes = features.getBytes();
SecureRandom random = SecureRandom.getInstance("SHA1PRNG");
random.setSeed(featuresBytes);
KeyPairGenerator keyGen = KeyPairGenerator.getInstance("RSA");
keyGen.initialize(size, random);
KeyPair generatedKeyPair = keyGen.genKeyPair();
saveEncodedKeyPair(generatedKeyPair, fileName, size, path);
} catch (Exception e) {
e.printStackTrace();
return;
}
}
4. Experiments and Results
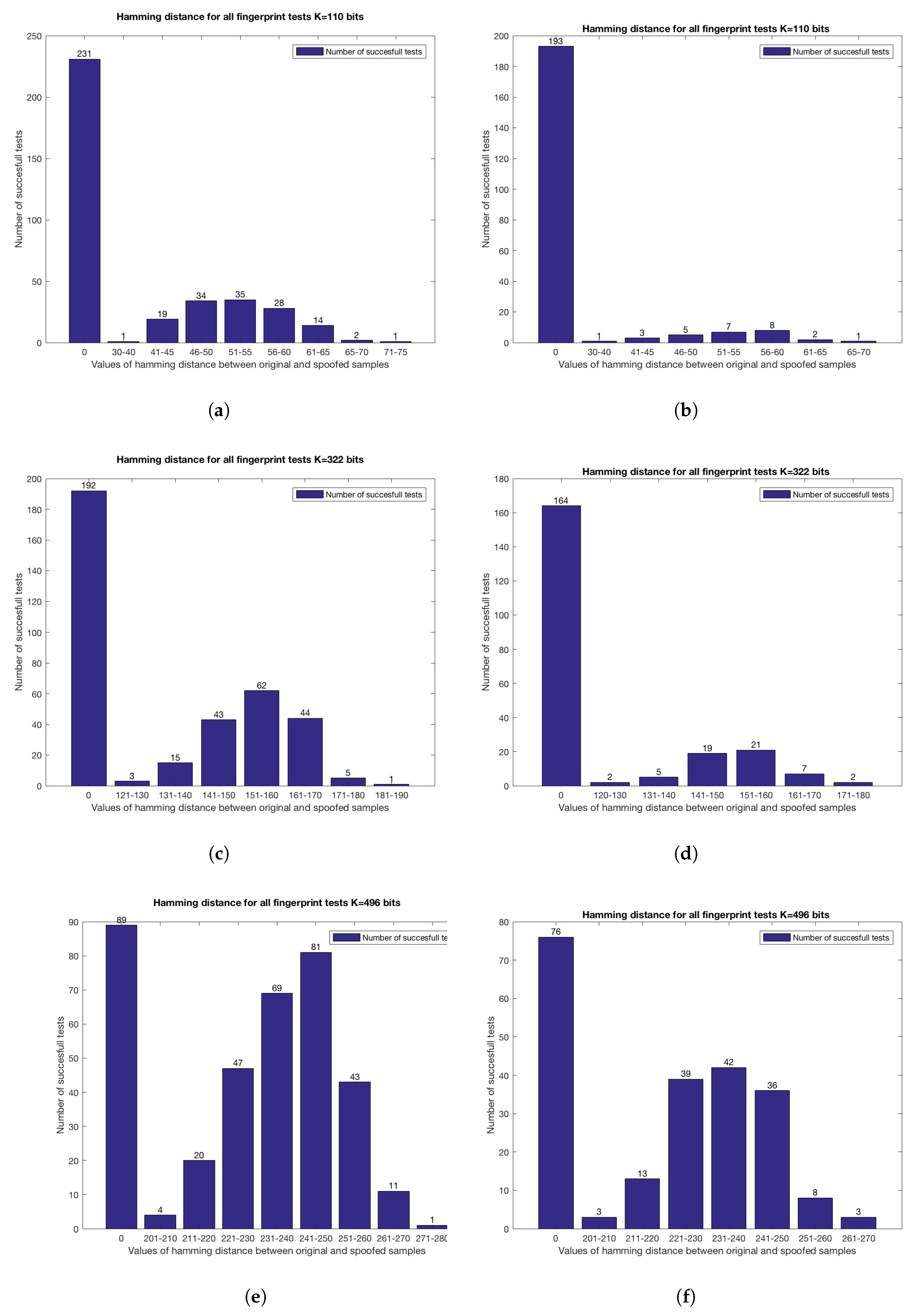
4.1. Fingerprints
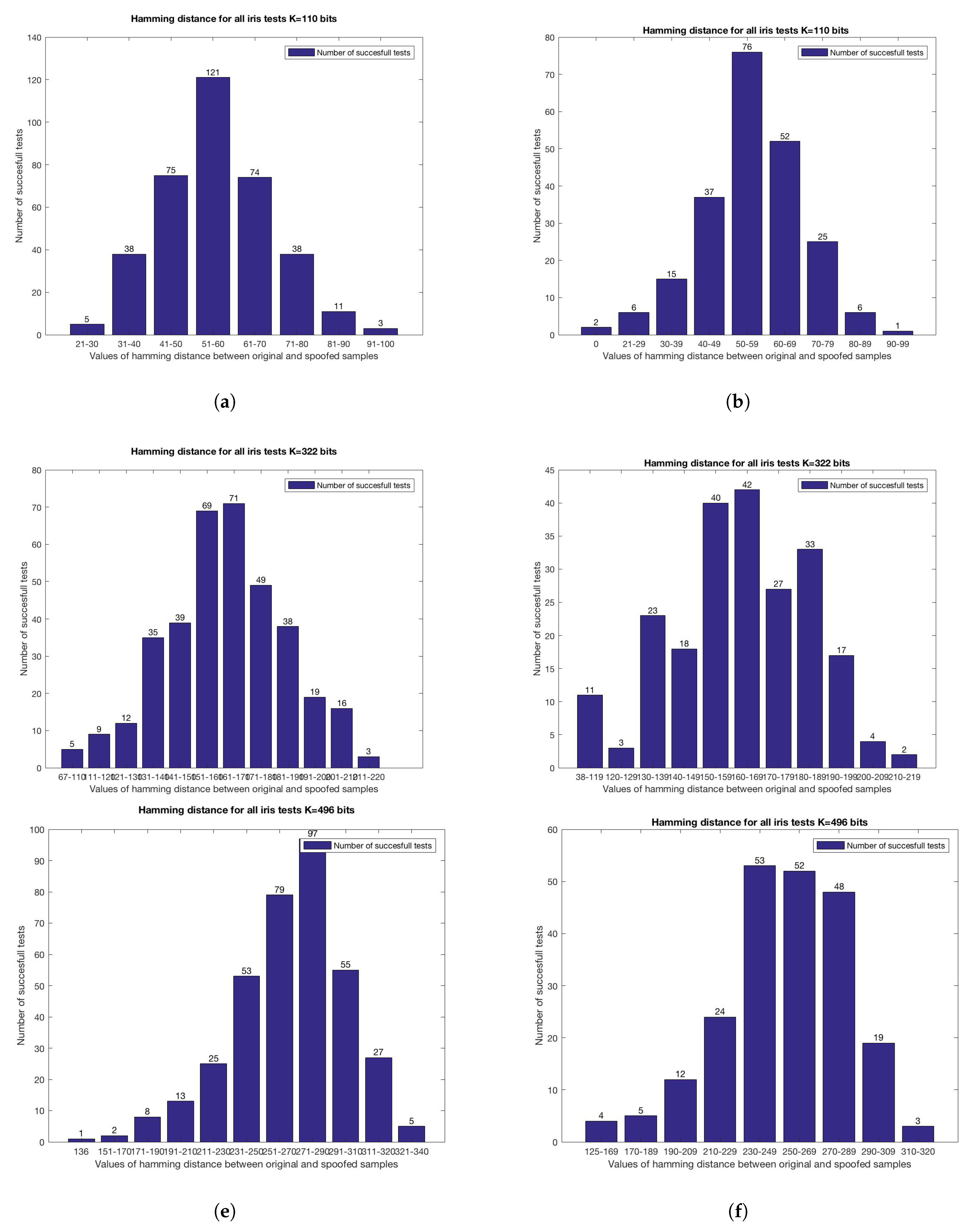
4.2. Iris
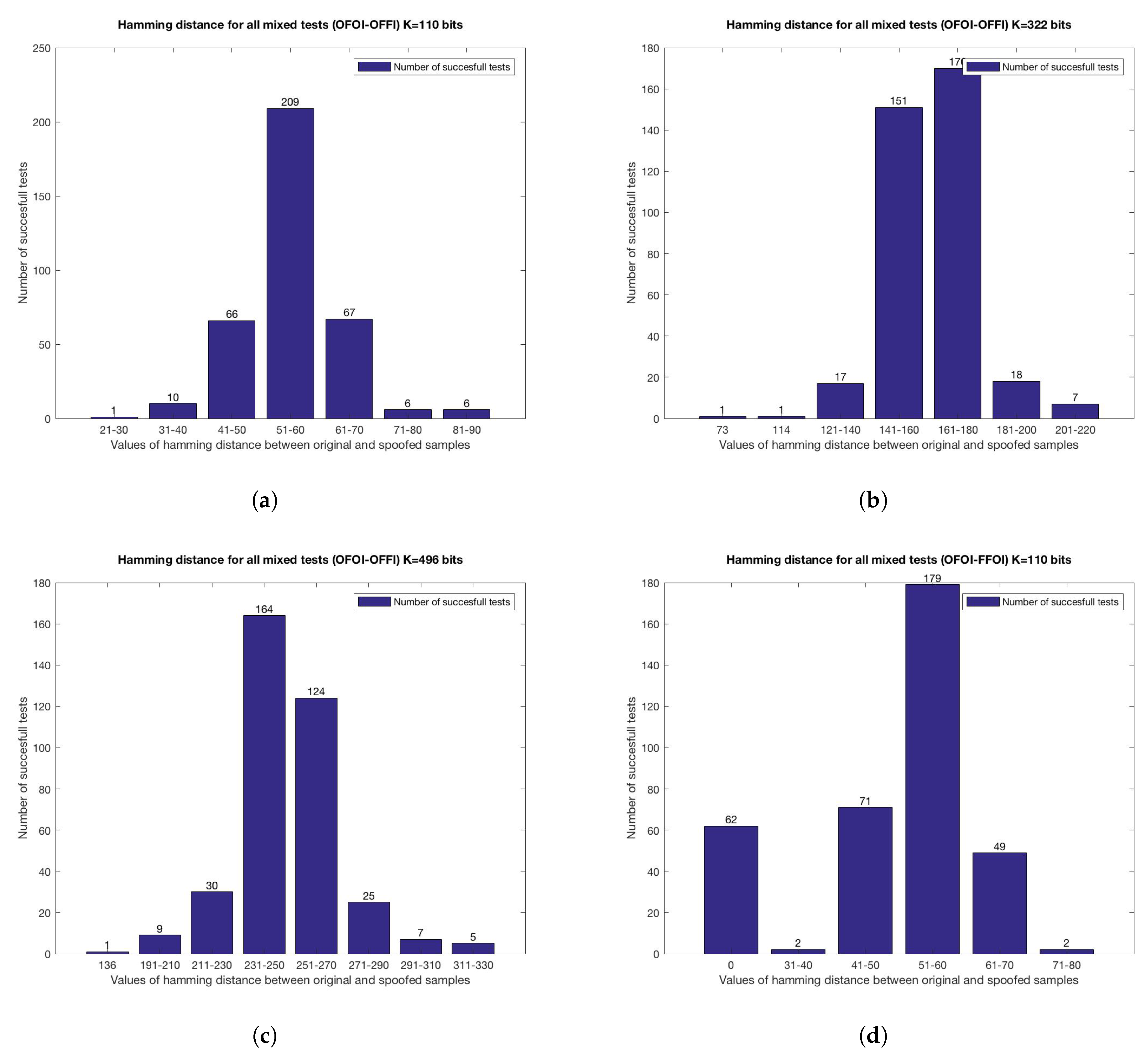
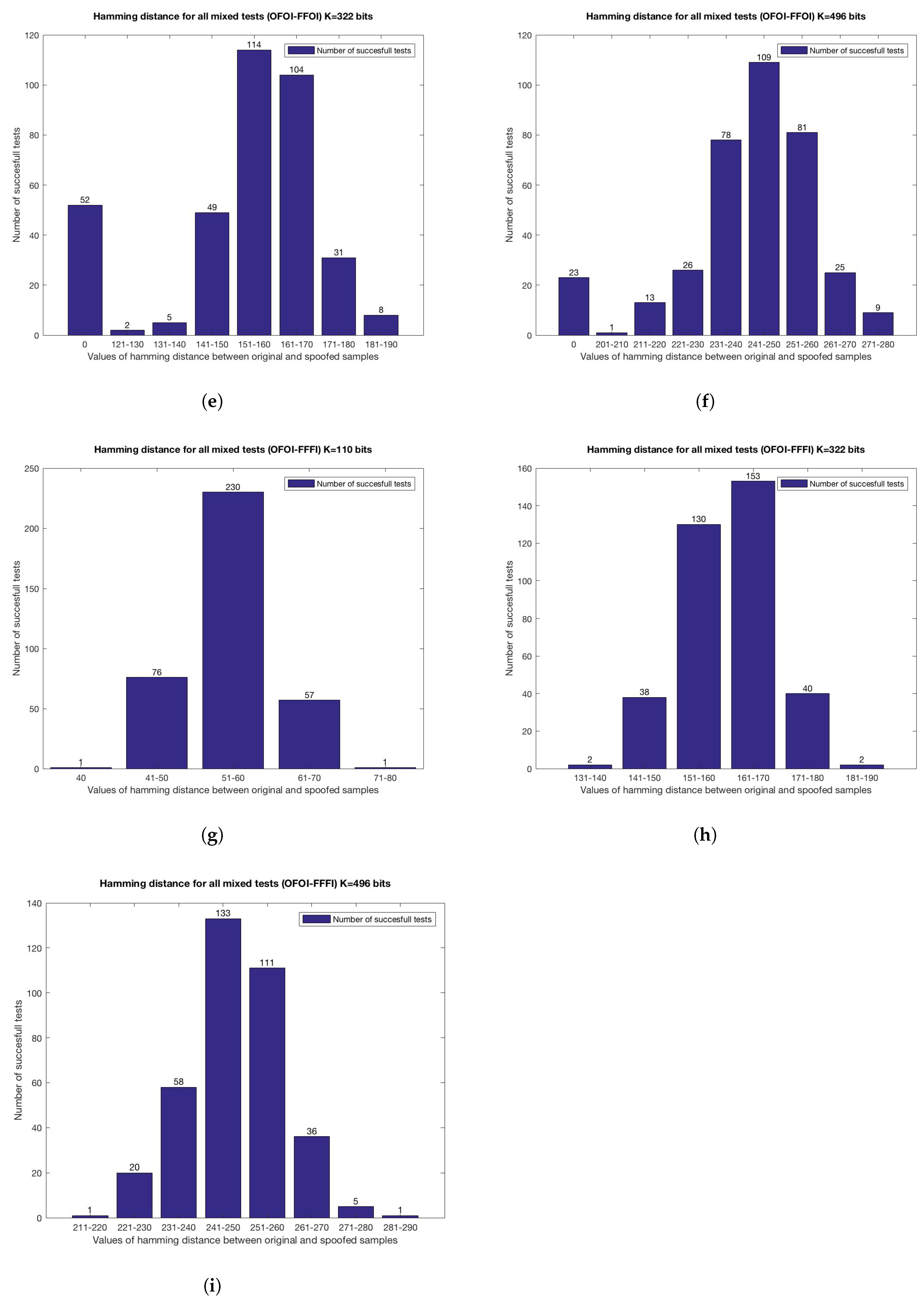
4.3. Multi-Biometrics
- OFOI-OFFI Original samples against original fingerprint and fake iris sample.
- OFOI-FFOI Original samples against fake fingerprint and original iris sample.
- OFOI-FFFI Original samples against fake samples for both biometrics.
5. Security Analysis
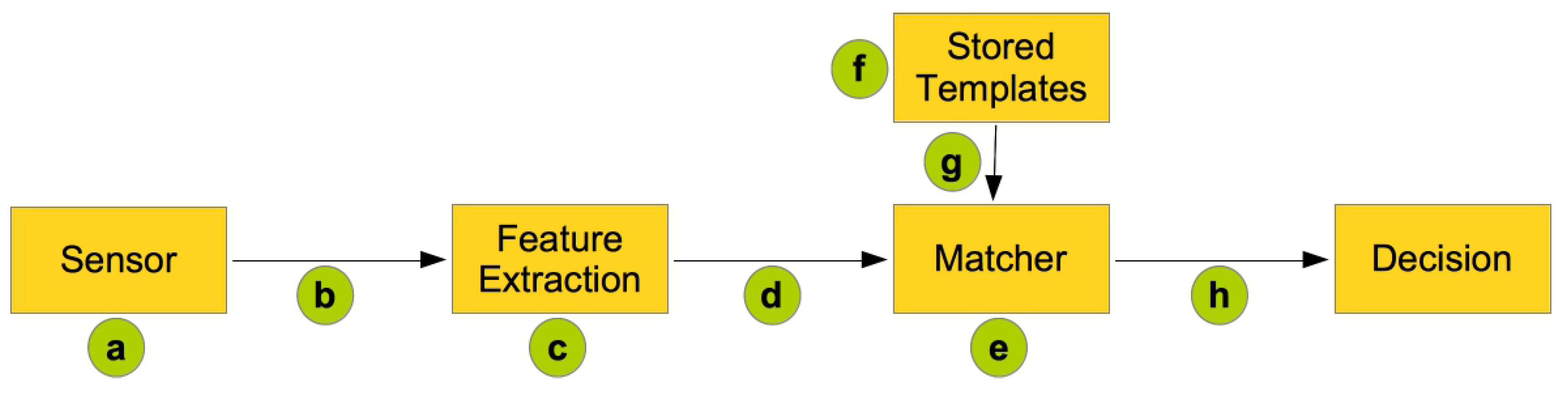
5.1. Overall Biometric System Security
- (a) Biometric spoofing—the biometric characteristic is spoofed and presented to the sensor.
- (b) Relaying stored signals—a recorded signal is relayed to the system, overwriting the captured biometric data.
- (c) Attacking feature extraction—the feature extraction process itself is under attack, the intruder changes the extracted features with the desired set.
- (d) Tampering with biometric features—the extracted features are intercepted before going to the matcher module and replaced with the desired set.
- (e) Attacking the matcher—the matcher itself is under attack, meaning the intruder obtains the desired match scores.
- (f) Attacking the stored templates—penetrating the biometric database might allow an attacker to reconstruct the original biometric based on the template, or even worse replace a certain template with another one.
- (g) Communication interception—the communication between the database and the matcher might be intercepted by an intruder.
- (h) Attacking the final decision—an attacker will obtain the desired decision.
5.2. Smartphone Application Security
5.3. Liveness Detection
5.4. Which Biometrics to Use
5.5. Which Fusion Method to Use
5.6. No Access to Private Key
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Potter, C.H.; Hancke, G.P.; Silva, B.J. Machine-to-Machine: Possible applications in industrial networks. In Proceedings of the 2013 IEEE International Conference on Industrial Technology (ICIT), Cape Town, South Africa, 25–28 February 2013; pp. 1321–1326.
- Opperman, C.A.; Hancke, G.P. Using NFC-enabled phones for remote data acquisition and digital control. In Proceedings of the AFRICON 2011, Livingstone, Zambia, 13–15 September 2011; pp. 1–6.
- Hancke, G.P.; Markantonakis, K.; Mayes, K.E. Security Challenges for User-Oriented RFID Applications within the “Internet of Things”. J. Internet Technol. 2010, 11, 307–313. [Google Scholar]
- Markantonakis, K.; Tunstall, M.; Hancke, G.; Askoxylakis, I.; Mayes, K. Attacking smart card systems: Theory and practice. Inf. Secur. Tech. Rep. 2009, 14, 46–56. [Google Scholar] [CrossRef]
- Francis, L.; Hancke, G.; Mayes, K.; Markantonakis, K. Potential misuse of NFC enabled mobile phones with embedded security elements as contactless attack platforms. In Proceedings of the 2009 International Conference for Internet Technology and Secured Transactions (ICITST), London, UK, 9–12 November 2009; pp. 1–8.
- AlMahafzah, H.; AlRwashdeh, M.Z. A Survey of Multibiometric Systems. arXiv 2012. [Google Scholar]
- Ross, A.; Shah, J.; Jain, A.K. From template to image: Reconstructing fingerprints from minutiae points. IEEE Trans. Pattern Anal. Mach. Intell. 2007, 29, 544–560. [Google Scholar] [CrossRef] [PubMed]
- Jain, A.K.; Nandakumar, K.; Nagar, A. Biometric template security. EURASIP J. Adv. Signal Process. 2008, 2008, 113. [Google Scholar] [CrossRef]
- Ratha, N.; Chikkerur, S.; Connell, J.; Bolle, R. Generating Cancelable Fingerprint Templates. IEEE Trans. Pattern Anal. Mach. Intell. 2007, 29, 561–572. [Google Scholar] [CrossRef] [PubMed]
- Rathgeb, C.; Uhl, A. A survey on biometric cryptosystems and cancelable biometrics. EURASIP J. Inf. Secur. 2011, 2011, 1–25. [Google Scholar] [CrossRef]
- Patel, V.M.; Ratha, N.K.; Chellappa, R. Cancelable Biometrics: A review. IEEE Signal Process. Mag. 2015, 32, 54–65. [Google Scholar] [CrossRef]
- Prins, J.; Cybercrime, B.U. DigiNotar Certificate Authority breach “Operation Black Tulip”. Available online: http://www.cs.ru.nl/klaus/SiO2011/Assignments/rapport.pdf (accessed on 10 February 2017).
- Farwell, J.P.; Rohozinski, R. Stuxnet and the future of cyber war. Survival 2011, 53, 23–40. [Google Scholar] [CrossRef]
- Goodin, D. Certificate Stolen from Malaysian Gov Used to Sign Malware. Available online: https://www.theregister.co.uk/2011/11/14/stolen_certificate_discovered/ (accessed on 13 February 2017).
- Krebs, B. Signed Malware = Expensive “Oops” for HP — Krebs on Security. 2014. Available online: https://krebsonsecurity.com/2014/10/signed-malware-is-expensive-oops-for-hp/ (accessed on 13 February 2017).
- Kushnir, K.; Mirmulstein, M.L.; Ramalho, R. Micro, Small, and Medium Enterprises Around the World: How Many Are There, and What Affects the Count? Technical Report; World Bank/IFC: Washington, DC, USA, 2010. [Google Scholar]
- EU. Stork—What Is It? Available online: https://www.eid-stork.eu/index.php?option=com_content&task=view&id=37&Itemid=61 (accessed on 13 February 2017).
- Dinca, L.; Hancke, G. A Framework for User-Centric Key Sharing in Personal Sensor Networks. In Proceedings of the INDIN 2016 IEEE International Conference on Industrial Informatics, Poitiers, France, 18–21 July 2016.
- Rodrigues, R.N.; Kamat, N.; Govindaraju, V. Evaluation of biometric spoofing in a multimodal system. In Proceedings of the 2010 Fourth IEEE International Conference on Biometrics: Theory Applications and Systems (BTAS), Washington, DC, USA, 27–29 September 2010; pp. 1–5.
- Akhtar, Z.; Alfarid, N. Robustness of Serial and Parallel Biometric Fusion against Spoof Attacks. In Computer Networks and Intelligent Computing; Venugopal, K.R., Patnaik, L.M., Eds.; Springer: Berlin/Heidelberg, Germany, 2011; pp. 217–225. [Google Scholar]
- Akhtar, Z.; Kale, S. Security Analysis of Multimodal Biometric Systems against Spoof Attacks. In Advances in Computing and Communications; Abraham, A., Mauri, J.L., Buford, J.F., Suzuki, J., Thampi, S.M., Eds.; Number 191 in Communications in Computer and Information Science; Springer: Berlin/Heidelberg, Germany, 2011; pp. 604–611. [Google Scholar]
- Nandakumar, K.; Jain, A. Multibiometric Template Security Using Fuzzy Vault. In Proceedings of the 2nd IEEE International Conference on Biometrics: Theory, Applications and Systems (BTAS), Washington, DC, USA, 29 September–1 October 2008; pp. 1–6.
- Kelkboom, E.J.C.; Zhou, X.; Breebaart, J.; Veldhuis, R.N.S.; Busch, C. Multi-algorithm Fusion with Template Protection. In Proceedings of the 3rd IEEE International Conference on Biometrics: Theory, Applications and Systems ( BTAS’09), Washington, DC, USA, 28–30 September 2009; pp. 222–229.
- Hao, F.; Anderson, R.; Daugman, J. Combining Crypto with Biometrics Effectively. IEEE Trans. Comput. 2006, 55, 1081–1088. [Google Scholar]
- Ballard, L.; Kamara, S.; Monrose, F.; Reiter, M.K. Towards Practical Biometric Key Generation with Randomized Biometric Templates. In Proceedings of the 15th ACM Conference on Computer and Communications Security (CCS ’08), Alexandria, VA, USA, 27–31 October 2008; pp. 235–244.
- Jagadeesan, A.; Thillaikkarasi, T.; Duraiswamy, K. Cryptographic key generation from multiple biometric modalities: Fusing minutiae with iris feature. Int. J. Comput. Appl. 2010, 2, 16–26. [Google Scholar] [CrossRef]
- Jagadeesan, A.; Duraiswamy, K. Secured Cryptographic Key Generation From Multimodal Biometrics: Feature Level Fusion of Fingerprint and Iris. arXiv 2010. [Google Scholar]
- Kanade, S.; Petrovska-Delacrétaz, D.; Dorizzi, B. Obtaining cryptographic keys using feature level fusion of iris and face biometrics for secure user authentication. In Proceedings of the 2010 IEEE Computer Society Conference on Computer Vision and Pattern Recognition—Workshops, San Francisco, CA, USA, 3–18 June 2010; pp. 138–145.
- Abuguba, S.; Milosavljevic, M.M.; Macek, N. An Efficient Approach to Generating Cryptographic Keys from Face and Iris Biometrics Fused at the Feature Level. Int. J. Comput. Sci. Netw. Secur. 2015, 15, 6. [Google Scholar]
- Sharma, R.K. Generation of Biometric Key for use in DES. arXiv 2012. [Google Scholar]
- Kumar, A.; Kumar, A. A palmprint-based cryptosystem using double encryption. In Proceedings of the SPIE Defense and Security Symposium, Orlando, Florida, 16–21 March 2008; Volume 6944, pp. 69440D:1–69440D:9.
- Arunachalam, M.; Subramanian, K. AES Based Multimodal Biometric Authentication using Cryptographic Level Fusion with Fingerprint and Finger Knuckle Print. Int. Arab J. Inf. Technol. 2015, 12, 431–440. [Google Scholar]
- Marimuthu, M.; Kannammal, A. Dual Fingerprints Fusion for Cryptographic Key Generation. Int. J. Comput. Appl. 2015, 122, 20–25. [Google Scholar] [CrossRef]
- Nguyen, T.H.L.; Nguyen, T.T.H. An approach to protect Private Key using fingerprint Biometric Encryption Key in BioPKI based security system. In Proceedings of the 10th International Conference on Control, Automation, Robotics and Vision (ICARCV), Hanoi, Vietnam, 17–18 December 2008; pp. 1595–1599.
- Boukhari, A.; Chitroub, S.; Bouraoui, I. Biometric Signature of Private Key by Reliable Iris Recognition Based on Flexible-ICA Algorithm. Int. J. Commun. Netw. Syst. Sci. 2011, 4, 778. [Google Scholar] [CrossRef]
- Dao, V.H.; Tran, Q.D.; Nguyen, T.H.L. A Multibiometric Encryption Key Algorithm Using Fuzzy Vault to Protect Private Key in BioPKI Based Security System. In Proceedings of the 2010 IEEE RIVF International Conference on Computing and Communication Technologies, Research, Innovation, and Vision for the Future (RIVF), Hanoi, Vietnam, 1–4 November 2010; pp. 1–6.
- Janbandhu, P.K.; Siyal, M.Y. Novel biometric digital signatures for internet based applications. Inf. Manag. Comput. Secur. 2001, 9, 205–212. [Google Scholar] [CrossRef]
- Janbandhu, P.K.; Siyal, M.Y. Modified Private Key Generation for Biometric Signatures. Available online: https://www.researchgate.net/publication/201599731 (accessed on 10 February 2017).
- Gong, Y.; Deng, K.; Shi, P. PKI Key Generation Based on Iris Features. In Proceedings of the 2008 International Conference on Computer Science and Software Engineering, Wuhan, China, 12–14 December 2008; Volume 6, pp. 166–169.
- Lakshmi, A.J.; Kiran, P.S. PKI Key Generation Based On Multimodal Biometrics. IJCC 2012, 1, 9–16. [Google Scholar]
- Lakshmi, A.J.; Babu, R. PKI Key Generation Using Multimodal Biometrics Fusion of Fingerprint and Iris. Int. J. Eng. Sci. Adv. Technol. 2012, 2, 285–290. [Google Scholar]
- Kussener, F. FingerPrint Application—File Exchange—MATLAB Central. 2007. Available online: https://www.mathworks.com/matlabcentral/fileexchange/16728-fingerprint-application (accessed on 13 February 2017).
- Wildes, R.P. Iris recognition: An emerging biometric technology. Proc. IEEE 1997, 85, 1348–1363. [Google Scholar] [CrossRef]
- Masek, L. Recognition of Human Iris Patterns for Biometric Identification. Master’s Thesis, The University of Western Australia, Perth, Australia, 2003. [Google Scholar]
- Dodis, Y.; Reyzin, L.; Smith, A. Fuzzy Extractors: How to Generate Strong Keys from Biometrics and Other Noisy Data. In Advances in Cryptology—EUROCRYPT 2004; Cachin, C., Camenisch, J.L., Eds.; Springer: Berlin/Heidelberg, Germany, 2004; pp. 523–540. [Google Scholar]
- Kang, H.; Hori, Y.; Katashita, T.; Hagiwara, M. The Implementation of Fuzzy Extractor is Not Hard to Do: An Approach Using PUF Data. In Proceedings of the 30th Symposium on Cryptography and Information Security, Kyoto, Japan, 22–25 January 2013.
- Matsumoto, T.; Matsumoto, H.; Yamada, K.; Hoshino, S. Impact of Artificial “gummy” Fingers on Fingerprint Systems. Available online: http://proceedings.spiedigitallibrary.org/proceeding.aspx?articleid=878135# (accessed on 13 February 2017).
- Espinoza, M.; Champod, C.; Margot, P. Vulnerabilities of fingerprint reader to fake fingerprints attacks. Forensic Sci. Int. 2011, 204, 41–49. [Google Scholar] [CrossRef] [PubMed]
- Galbally, J.; Cappelli, R.; Lumini, A.; Gonzalez-de Rivera, G.; Maltoni, D.; Fierrez, J.; Ortega-Garcia, J.; Maio, D. An evaluation of direct attacks using fake fingers generated from ISO templates. Pattern Recogn. Lett. 2010, 31, 725–732. [Google Scholar] [CrossRef]
- Galbally, J.; Cappelli, R.; Lumini, A.; Maltoni, D.; Fierrez, J. Fake fingertip generation from a minutiae template. In Proceedings of the 19th International Conference on Pattern Recognition (ICPR 2008), Tampa, FL, USA, 8–11 December 2008; pp. 1–4.
- Cappelli, R.; Maio, D.; Lumini, A.; Maltoni, D. Fingerprint Image Reconstruction from Standard Templates. IEEE Trans. Pattern Anal. Mach. Intell. 2007, 29, 1489–1503. [Google Scholar] [CrossRef] [PubMed]
- Ruiz-Albacete, V.; Tome-Gonzalez, P.; Alonso-Fernandez, F.; Galbally, J.; Fierrez, J.; Ortega-Garcia, J. Direct Attacks Using Fake Images in Iris Verification. In Biometrics and Identity Management; Schouten, B., Juul, N.C., Drygajlo, A., Tistarelli, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2008; pp. 181–190. [Google Scholar]
- Galbally, J.; Alonso-Fernandez, F.; Fierrez, J.; Ortega-Garcia, J. A high performance fingerprint liveness detection method based on quality related features. Future Gener. Comput. Syst. 2012, 28, 311–321. [Google Scholar] [CrossRef]
- Fierrez, J.; Ortega-Garcia, J.; Torre Toledano, D.; Gonzalez-Rodriguez, J. Biosec baseline corpus: A multimodal biometric database. Pattern Recogn. 2007, 40, 1389–1392. [Google Scholar] [CrossRef]
- Ratha, N.; Connell, J.; Bolle, R. Enhancing security and privacy in biometrics-based authentication systems. IBM Syst. J. 2001, 40, 614–634. [Google Scholar] [CrossRef]
- Felt, A.P.; Chin, E.; Hanna, S.; Song, D.; Wagner, D. Android Permissions Demystified. In Proceedings of the 18th ACM Conference on Computer and Communications Security (CCS ’11), Chicago, IL, USA, 17–21 October 2011; pp. 627–638.
- Labs, Z. 10% of Mobile Apps Leak Passwords, 40% Communicate with Third Parties | Cloud Security Solutions | Zscaler. 2012. Available online: https://www.zscaler.com/press/10-mobile-apps-leak-passwords-40-communicate-third-parties (accessed on 13 February 2017).
- Zhou, Y.; Jiang, X. Dissecting Android Malware: Characterization and Evolution. In Proceedings of the 2012 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 20–23 May 2012; pp. 95–109.
- Al-Ajlan, A. Survey on fingerprint liveness detection. In Proceedings of the 2013 International Workshop on Biometrics and Forensics (IWBF), Lisbon, Portugal, 4–5 April 2013; pp. 1–5.
- DeCann, B.; Tan, B.; Schuckers, S. A Novel Region Based Liveness Detection Approach for Fingerprint Scanners; Advances in Biometrics; Springer: Berlin/Heidelberg, Germany, 2009; pp. 627–636. [Google Scholar]
- Abhyankar, A.; Schuckers, S. Integrating a wavelet based perspiration liveness check with fingerprint recognition. Pattern Recogn. 2009, 42, 452–464. [Google Scholar] [CrossRef]
- Tan, B.; Schuckers, S. Liveness Detection for Fingerprint Scanners Based on the Statistics of Wavelet Signal Processing. In Proceedings of the 2006 Conference on Computer Vision and Pattern Recognition Workshop (CVPRW’06), New York, NY, USA, 17–22 June 2006.
- Zhang, Y.; Tian, J.; Chen, X.; Yang, X.; Shi, P. Fake Finger Detection Based on Thin-Plate Spline Distortion Model; Advances in Biometrics; Springer: Berlin/Heidelberg, Germany, 2007; pp. 742–749. [Google Scholar]
- Jia, J.; Cai, L.; Zhang, K.; Chen, D. A New Approach to Fake Finger Detection Based on Skin Elasticity Analysis; Advances in Biometrics; Springer: Berlin/Heidelberg, Germany, 2007; pp. 309–318. [Google Scholar]
- Tan, B.; Schuckers, S. New approach for liveness detection in fingerprint scanners based on valley noise analysis. J. Electron. Imaging 2008, 17. [Google Scholar] [CrossRef]
- Nikam, S.B.; Agarwal, S. Ridgelet-based fake fingerprint detection. Neurocomputing 2009, 72, 2491–2506. [Google Scholar] [CrossRef]
- Nikam, S.B.; Agarwal, S. Curvelet-based fingerprint anti-spoofing. Signal Image Video Process. 2010, 4, 75–87. [Google Scholar] [CrossRef]
- Abhyankar, A.; Schuckers, S. Fingerprint Liveness Detection Using Local Ridge Frequencies and Multiresolution Texture Analysis Techniques. In Proceedings of the 2006 International Conference on Image Processing, Atlanta, GA, USA, 8–11 October 2006; pp. 321–324.
- Marcialis, G.L.; Roli, F.; Tidu, A. Analysis of Fingerprint Pores for Vitality Detection. In Proceedings of the 2010 20th International Conference on Pattern Recognition, Istanbul, Turkey, 23–26 August 2010; pp. 1289–1292.
- Espinoza, M.; Champod, C. Using the Number of Pores on Fingerprint Images to Detect Spoofing Attacks. In Proceedings of the 2011 International Conference on Hand-Based Biometrics, Hong Kong, China, 17–18 November 2011; pp. 1–5.
- Memon, S.; Manivannan, N.; Balachandran, W. Active pore detection for liveness in fingerprint identification system. In Proceedings of the 2011 19th Telecommunications Forum (FOR) Proceedings of Papers, Belgrade, Serbia, 22–24 November 2011; pp. 619–622.
- Tan, B.; Schuckers, S. Spoofing protection for fingerprint scanner by fusing ridge signal and valley noise. Pattern Recogn. 2010, 43, 2845–2857. [Google Scholar] [CrossRef]
- Jia, J.; Cai, L. Fake Finger Detection Based on Time-Series Fingerprint Image Analysis; Advanced Intelligent Computing Theories and Applications. With Aspects of Theoretical and Methodological Issues; Springer: Berlin/Heidelberg, Germany, 2007; pp. 1140–1150. [Google Scholar]
- Marasco, E.; Sansone, C. An anti-spoofing technique using multiple textural features in fingerprint scanners. In Proceedings of the 2010 IEEE Workshop on Biometric Measurements and Systems for Security and Medical Applications, Taranto, Italy, 9 September 2010; pp. 8–14.
- Bodade, R.; Talbar, S. Dynamic iris localisation: A novel approach suitable for fake iris detection. In Proceedings of the 2009 International Conference on Ultra Modern Telecommunications Workshops, St. Petersburg, Russia, 12–14 October 2009; pp. 1–5.
- Pacut, A.; Czajka, A. Aliveness Detection for IRIS Biometrics. In Proceedings of the 40th Annual 2006 International Carnahan Conference on Security Technology, Istanbul, Turkey, 11–15 June 2006; pp. 122–129.
- Connell, J.; Ratha, N.; Gentile, J.; Bolle, R. Fake iris detection using structured light. In Proceedings of the 2013 IEEE International Conference on Acoustics, Speech and Signal Processing, Vancouver, BC, Canada, 26–31 May 2013; pp. 8692–8696.
- Ballard, L.; Kamara, S.; Reiter, M.K. The Practical Subtleties of Biometric Key Generation. In Proceedings of the USENIX Security Symposium, SAN JOSE, CA, USA, 28–1 August 2008; pp. 61–74.
- Sanderson, C.; Paliwal, K. Information Fusion and Person Verification Using Speech & Face Information; Technical Report; IDIAP Research Institute: Martigny, Switzerland, 2002. [Google Scholar]
- Ross, A.; Nandakumar, K.; Jain, A. Introduction to Multibiometrics. In Handbook of Biometrics; Jain, A., Flynn, P., Ross, A., Eds.; Springer: Berlin/Heidelberg, Germany, 2008; pp. 271–292. [Google Scholar]
- Mai, G.; Lim, M.H.; Yuen, P.C. Fusing binary templates for multi-biometric cryptosystems. In Proceedings of the 2015 IEEE 7th International Conference on Biometrics Theory, Applications and Systems (BTAS), Arlington, VA, USA, 8–11 September 2015; pp. 1–8.
- Nagar, A.; Nandakumar, K.; Jain, A.K. Multibiometric Cryptosystems Based on Feature-Level Fusion. IEEE Trans. Inf. Forensics Secur. 2012, 7, 255–268. [Google Scholar] [CrossRef]
- Sutcu, Y.; Li, Q.; Memon, N. Secure Biometric Templates from Fingerprint-Face Features. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition (CVPR ’07), Minneapolis, MN, USA, 17–22 June 2007; pp. 1–6.
- Merkle, J.; Kevenaar, T.; Korte, U. Multi-modal and multi-instance fusion for biometric cryptosystems. In Proceedings of the International Conference of the Biometrics Special Interest Group (BIOSIG) (2012 BIOSIG), Darmstadt, Germany, 6–7 September 2012; pp. 1–6.
- Boneh, D.; Durfee, G.; Frankel, Y. An Attack on RSA Given a Small Fraction of the Private Key Bits; In Advances in Cryptology—ASIACRYPT’98; Springer: Berlin/Heidelberg, Germany, 1998; pp. 25–34. [Google Scholar]
- Blömer, J.; May, A. New Partial Key Exposure Attacks on RSA; Advances in Cryptology—CRYPTO 2003; Springer: Berlin/Heidelberg, Germany, 2003; pp. 27–43. [Google Scholar]

| Type | Name | Description |
|---|---|---|
| Cancelable biometrics | Biometric salting | Adds a salt (randoms bits) to the key. If the biometric template is compromised it can be renewed and the user doesn’t loose the biometric characteristic. |
| Non-invertible transforms | The biometric data is transformed using a non-invertible function before being stored in the database. A template can be renewed by using a different transformation. | |
| Biometric Cryptosystems | Key-binding schemes | The biometric template is binded by an encryption key and stored in the database. |
| Key-generation schemes | The key is derived from the biometric template. |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license ( http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Dinca, L.M.; Hancke, G. User-Centric Key Entropy: Study of Biometric Key Derivation Subject to Spoofing Attacks. Entropy 2017, 19, 70. https://doi.org/10.3390/e19020070
Dinca LM, Hancke G. User-Centric Key Entropy: Study of Biometric Key Derivation Subject to Spoofing Attacks. Entropy. 2017; 19(2):70. https://doi.org/10.3390/e19020070
Chicago/Turabian StyleDinca, Lavinia Mihaela, and Gerhard Hancke. 2017. "User-Centric Key Entropy: Study of Biometric Key Derivation Subject to Spoofing Attacks" Entropy 19, no. 2: 70. https://doi.org/10.3390/e19020070






