Multi-User Detection for Sporadic IDMA Transmission Based on Compressed Sensing
Abstract
:1. Introduction
2. Sporadic IDMA Transmission System Model and Chip-by-Chip Multi-User Detection
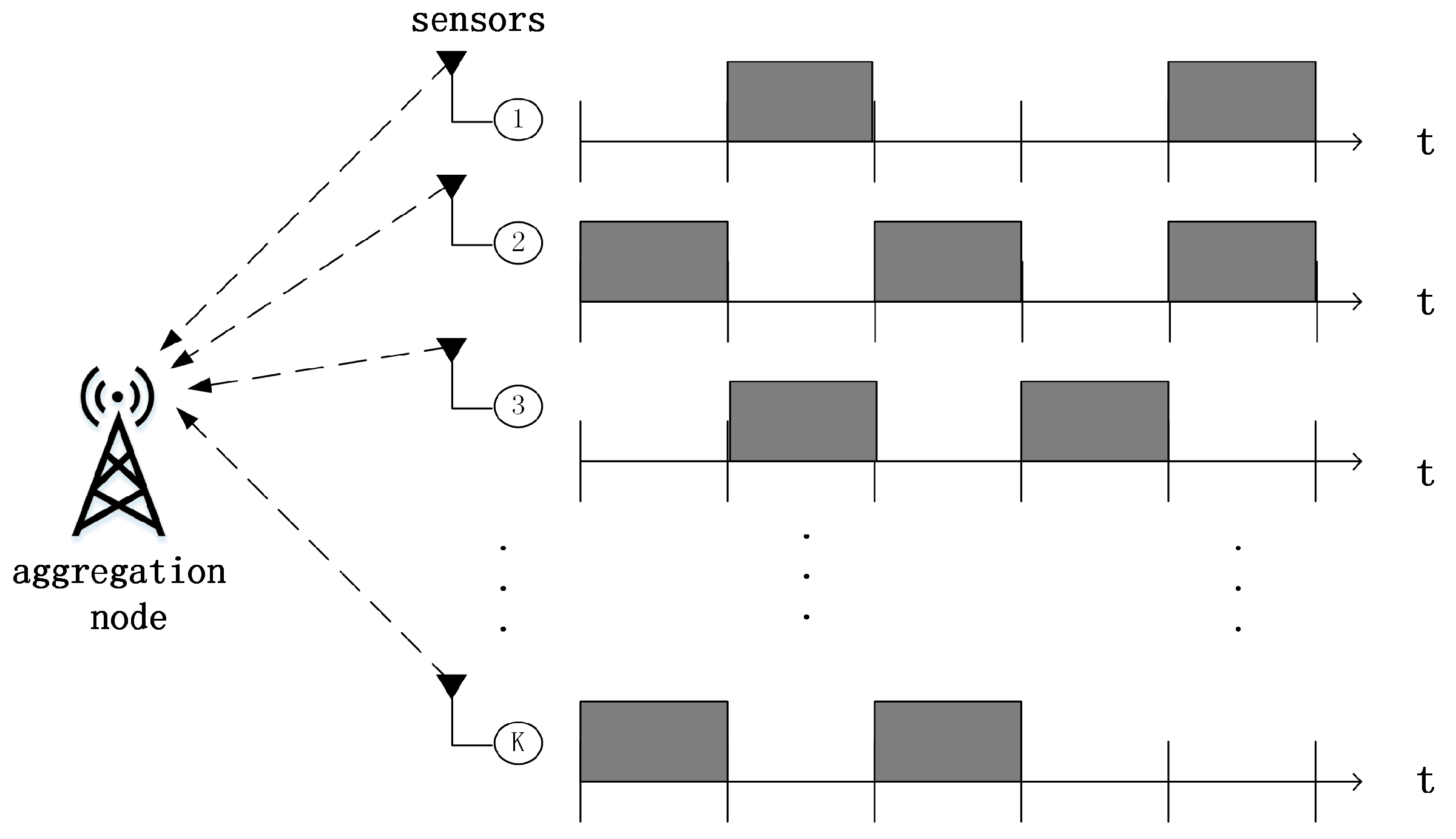
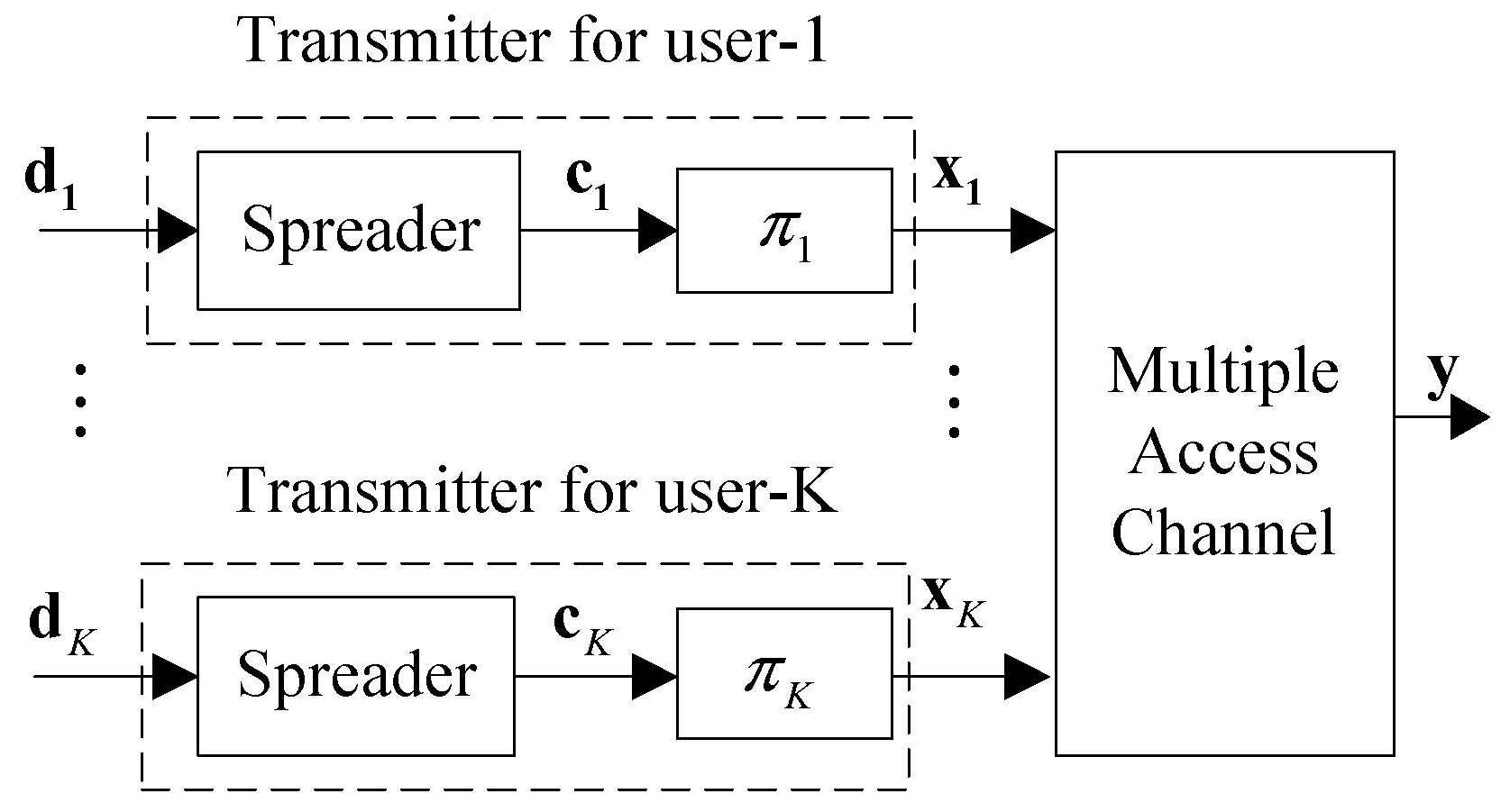
2.1. Sporadic IDMA Transmission System Model
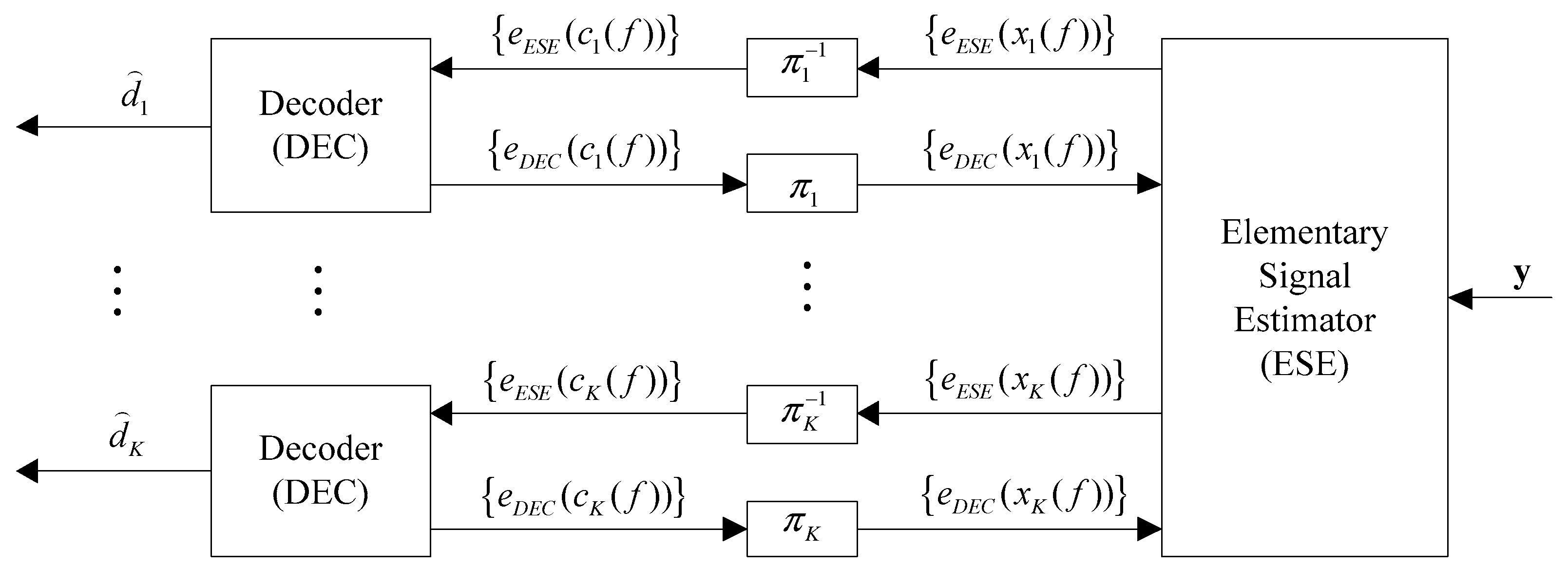
2.2. Chip-by-Chip Iterative Multi-Users Detection
2.2.1. The Basic ESE Function
2.2.2. The DEC Function
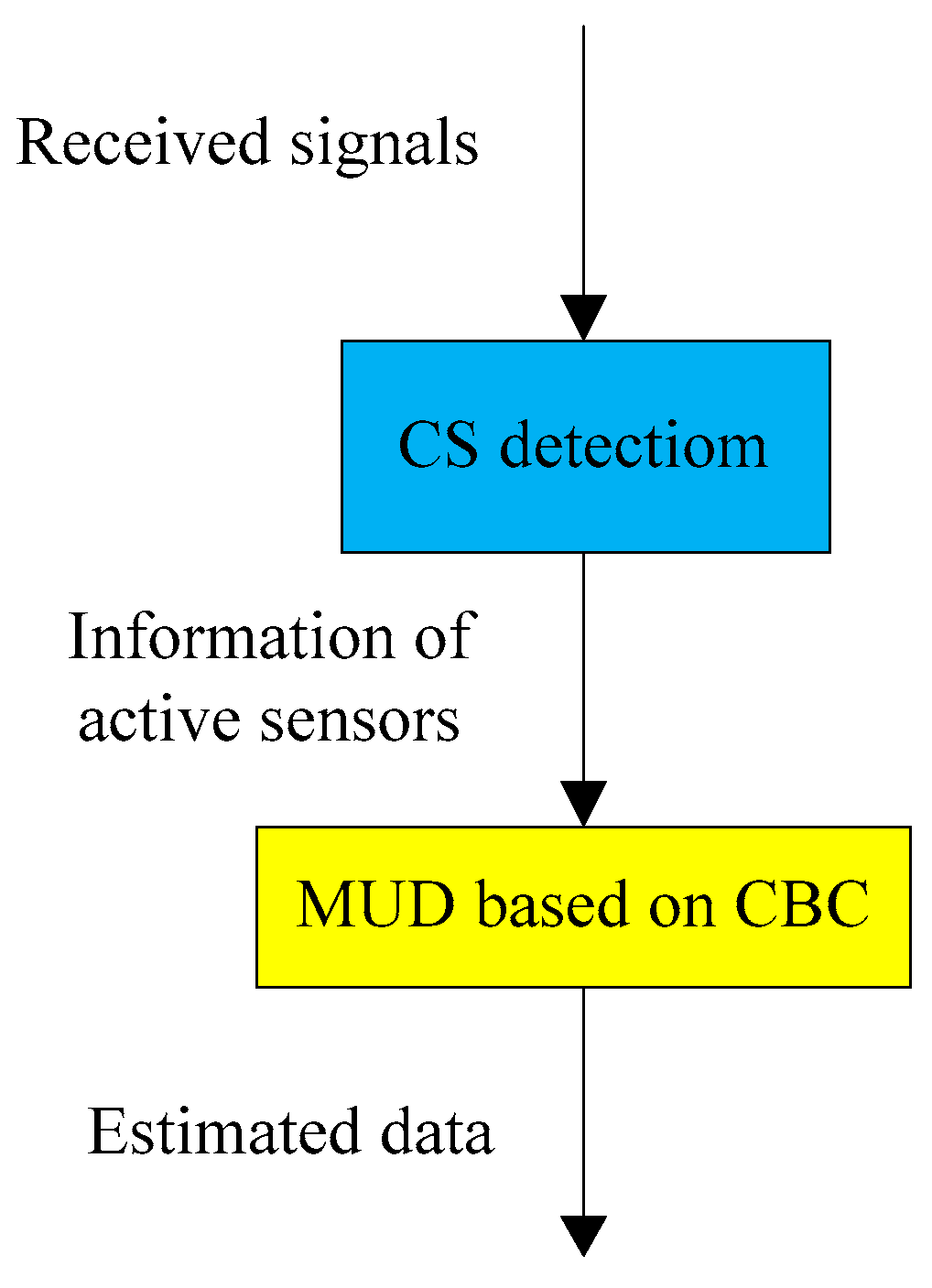
3. Activity and Data Detection Based on Compressed Sensing
3.1. CS Detection
3.1.1. Compressed Sensing
3.1.2. Application to Multi-User Detection
3.1.3. GOMP
| Algorithm 1: Group orthogonal matching pursuit. |
| Input: y, A, Output: 1: initialize |
| 2: repeat |
| 3: |
| 4: |
| 5: |
| 6: |
| 7: 8: until 9: |
- (1)
- (Step 4 in Algorithm 1) Group support selection: To be specific, the GOMP chooses the group , which has the highest correlation to the previous residual as the active support.
- (2)
- (Step 5 in Algorithm 1) Update the group-indices set G: The set of the newly-selected group index obtained in the previous step is added to the set
- (3)
- (Steps 6 and 7 in Algorithm 1) LS estimation is executed by using the sub-matrix of all columns in to determine the values of nonzero elements in and renew the current residual.
3.2. CBC-AD
3.3. CS-CBC
4. Simulation Results and Discussions
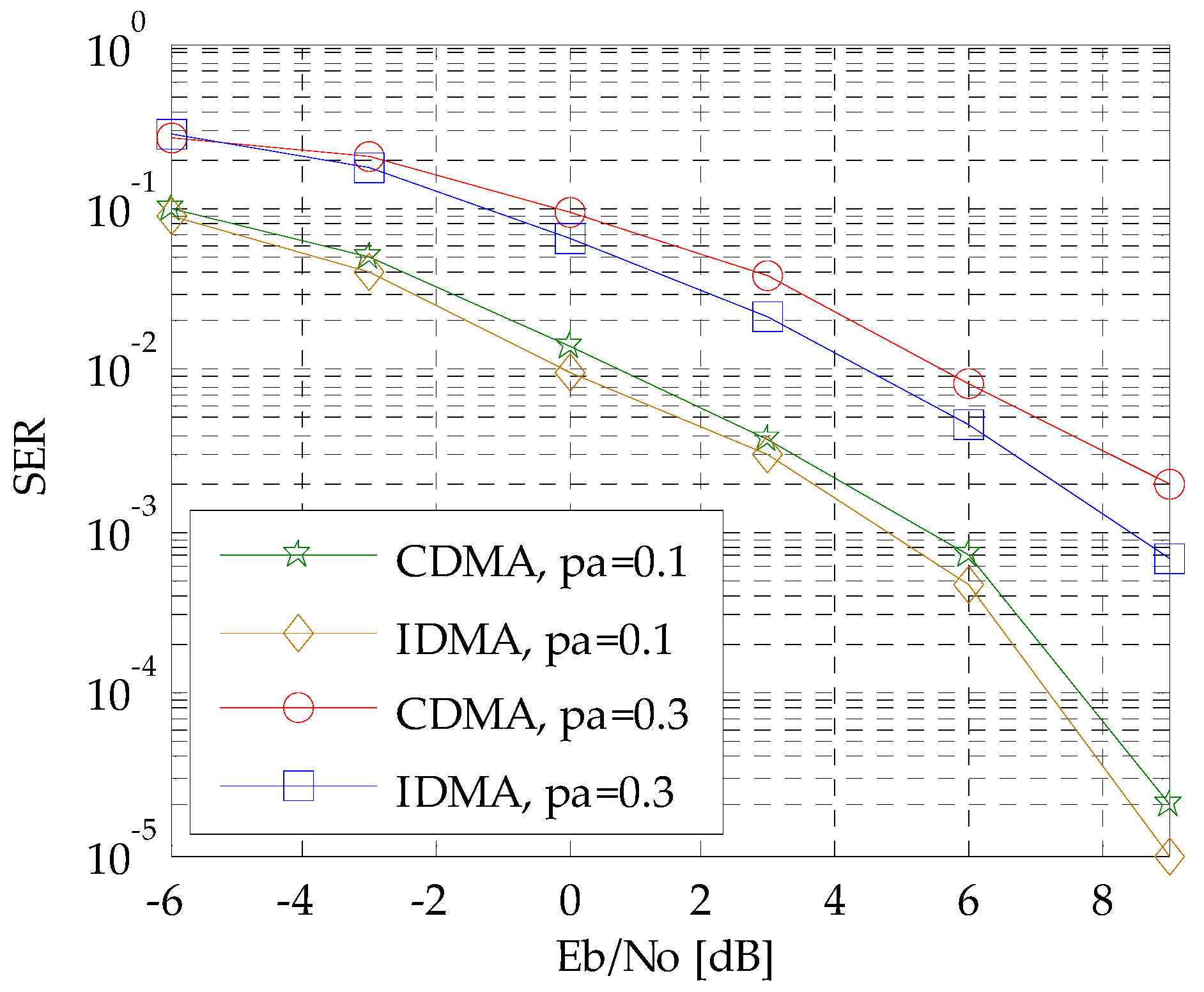
4.1. The SER Performance Comparison between IDMA and CDMA System
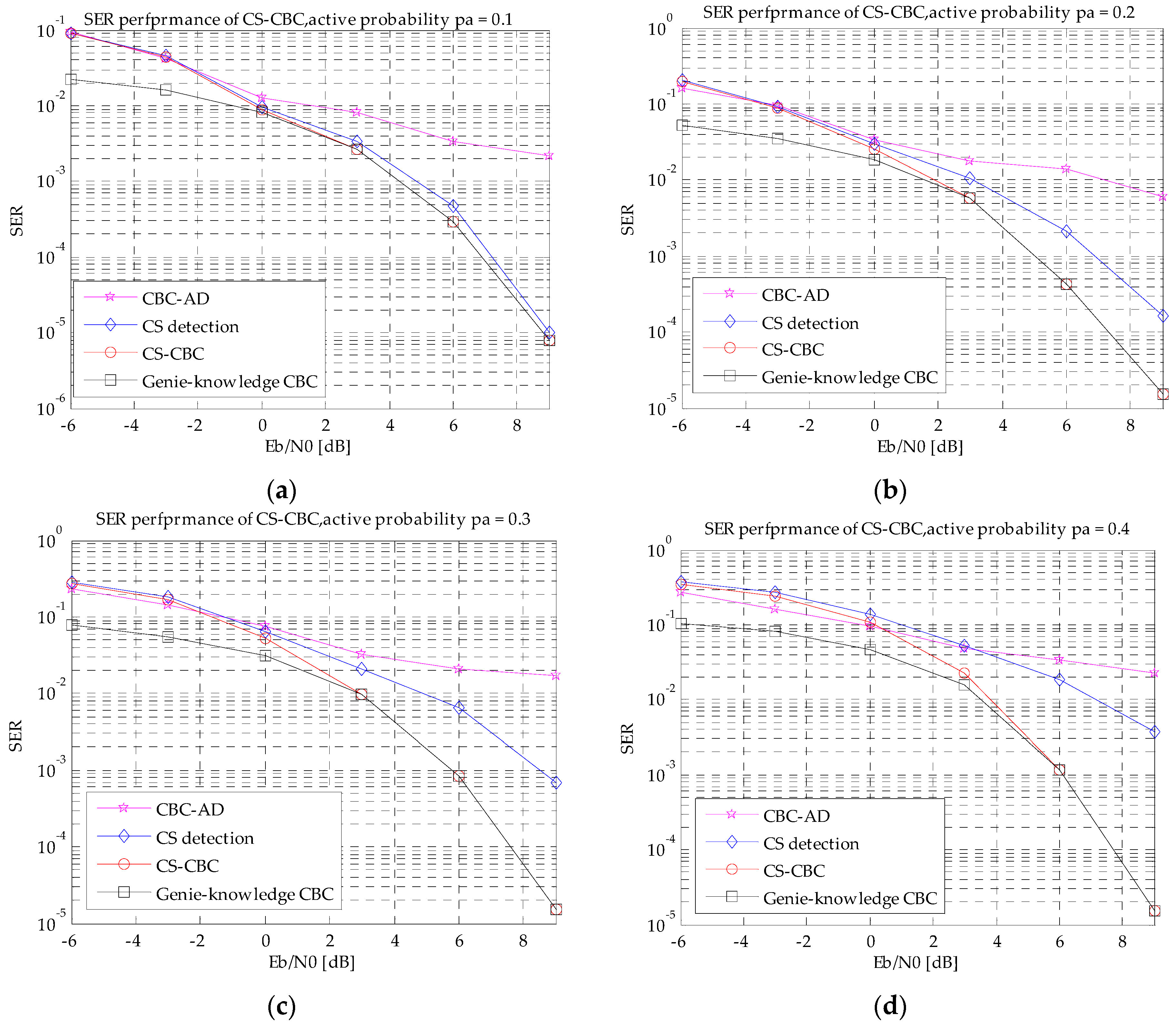
4.2. SER Performance with Different Eb/N0
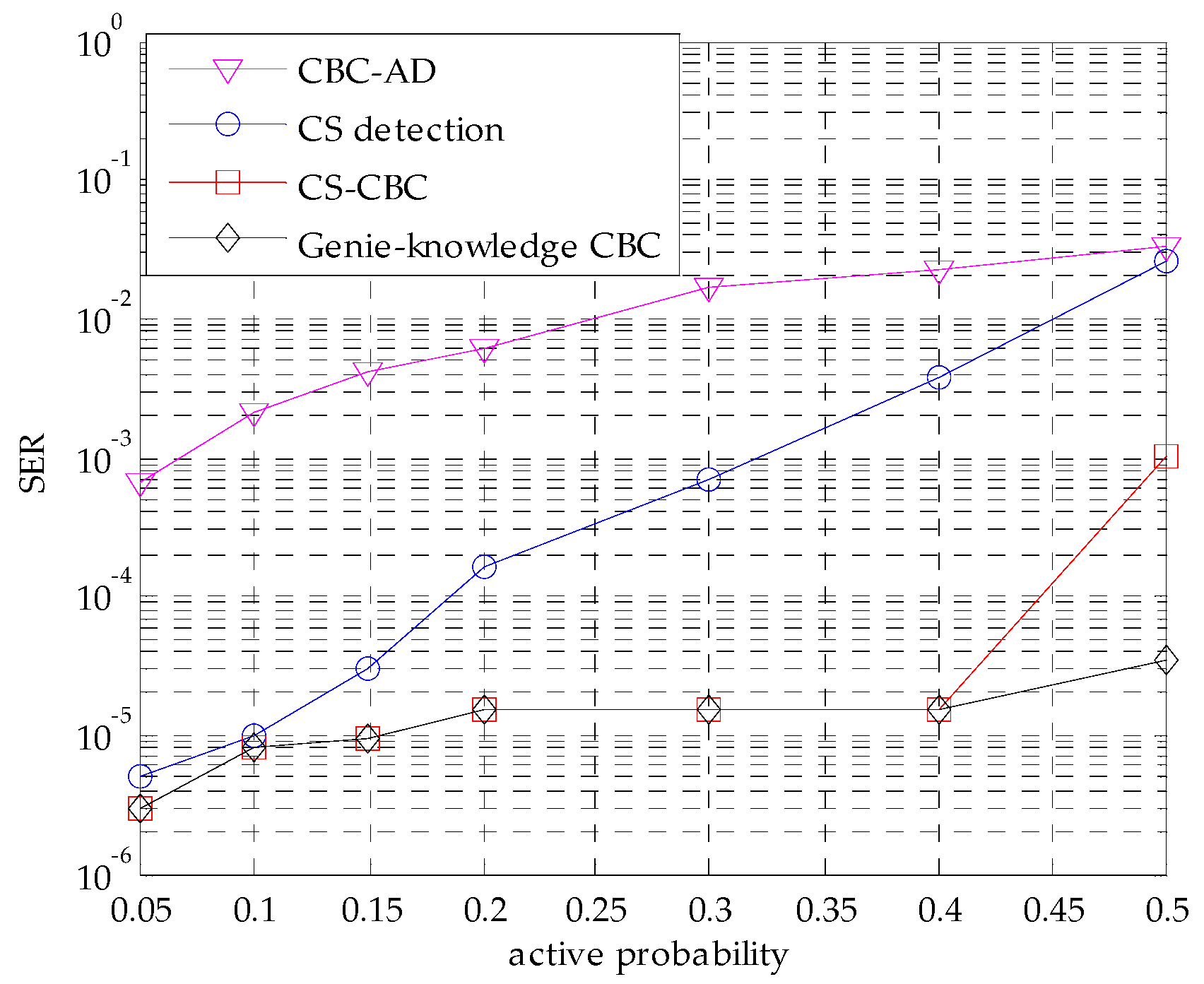
4.3. SER Performance with Different Active Probability pa
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Islam, S.M.R.; Kwak, D.; Kabir, M.H.; Hossain, M. The Internet of things for health care: A comprehensive survey. IEEE Access 2015, 3, 678–708. [Google Scholar] [CrossRef]
- Fang, S.; Xu, L.D.; Zhu, Y.; Ahati, J. An integrated system for regional environmental monitoring and management based on internet of things. IEEE Trans. Ind. Inf. 2014, 10, 1596–1605. [Google Scholar] [CrossRef]
- Chen, Y.; Schaich, F.; Wild, T. Multiple Access and Waveforms for 5G: IDMA and Universal Filtered Multi-Carrier. In Proceedings of the 2014 IEEE 79th Vehicular Technology Conference, Seoul, Korea, 18–21 May 2014. [Google Scholar]
- Ping, L.; Liu, L.; Wu, K.; Leung, W.K. Interleave division multiple-access. IEEE Trans. Wirel. Commun. 2006, 5, 938–947. [Google Scholar] [CrossRef]
- Kusume, K.; Bauch, G.; Utschick, W. Idma vs. cdma: Analysis and comparison of two multiple access schemes. IEEE Trans. Wirel. Commun. 2012, 11, 78–87. [Google Scholar] [CrossRef]
- Ping, L.; Guo, Q.; Tong, J. The OFDM-IDMA approach to wireless communication systems. IEEE Wirel. Commun. Mag. 2007, 14, 18–24. [Google Scholar] [CrossRef]
- Peng, T.; Xiao, Y.; He, X.; Li, S. Improved detection of uplink OFDM-IDMA signals with carrier frequency offsets. IEEE Commun. Lett. 2012, 16, 646–649. [Google Scholar] [CrossRef]
- Verdu, S. Multiuser Detection; Cambridge University Press: Cambridge, UK, 1998; pp. 3–18. [Google Scholar]
- Donoho, D.L. Compressed sensing. IEEE Trans. Inf. Theory 2006, 52, 1289–1306. [Google Scholar] [CrossRef]
- Candes, E.J.; Romberg, J.; Tao, T. Robust uncertainty principles: Exact signal reconstruction from highly incomplete frequency information. IEEE Trans. Inf. Theory 2004, 52, 489–509. [Google Scholar] [CrossRef]
- Xu, W.; Lin, J.; Niu, K.; He, Z. A joint recovery algorithm for distributed compressed sensing. Trans. Emerg. Telecommun. Technol. 2012, 23, 550–559. [Google Scholar] [CrossRef]
- Baraniuk, R.; Steeghs, P. Compressive Radar Imaging. In Proceedings of the 2007 IEEE Radar Conference, Boston, MA, USA, 17–20 April 2007. [Google Scholar]
- Shim, B.; Song, B. Multiuser detection via compressive sensing. IEEE Commun. Lett. 2012, 16, 972–974. [Google Scholar] [CrossRef]
- Bockelmann, C.; Schepker, H.F.; Dekorsy, A. Compressive sensing based multi-user detection for machine-to-machine communication. Trans. Emerg. Telecommun. Technol. 2013, 24, 389–400. [Google Scholar] [CrossRef]
- Monsees, F.; Woltering, M.; Bockelmann, C.; Dekorsy, A. Compressive Sensing Multi-User Detection for Multicarrier Systems in Sporadic Machine Type Communication. In Proceedings of the 2015 IEEE 81st Vehicular Technology Conference, Glasgow, UK, 11–14 May 2015. [Google Scholar]
- Schepker, H.F.; Bockelmann, C.; Dekorsy, A. Coping with CDMA Asynchronicity in Compressive Sensing Multi-User Detection. In Proceedings of the 2013 IEEE 77th Vehicular Technology Conference, Dresden, Germany, 2–5 June 2013. [Google Scholar]
- Schepker, H.F.; Bockelmann, C.; Dekorsy, A. Exploiting Sparsity in Channel and Data Estimation for Sporadic Multi-User Communication. In Proceedings of the Tenth International Symposium on Wireless Communication Systems, Ilmenau, Germany, 27–30 August 2013. [Google Scholar]
- Donoho, D.L.; Tanner, J. Precise undersampling theorems. Proc. IEEE 2013, 98, 913–924. [Google Scholar] [CrossRef]
- Candes, E.J.; Tao, T. Decoding by linear programming. IEEE Trans. Inf. Theory 2005, 51, 4203–4215. [Google Scholar] [CrossRef]
- Eldar, Y.C.; Kuppinger, P.; Lcskei, H. Block-sparse signals: Uncertainty relations and efficient recovery. IEEE Trans. Signal Process. 2010, 58, 3042–3054. [Google Scholar] [CrossRef]
- Baraniuk, R.; Davenport, M.; Devore, R.; Wakin, M. A simple proof of the restricted isometry property for random matrices. Constr. Approx. 2008, 28, 253–263. [Google Scholar] [CrossRef]
- Pati, Y.C.; Rezaiifar, R.; Krishnaprasad, P.S. Orthogonal matching pursuit: Recursive function approximation with applications to wavelet decomposition. Signals Syst. Comput. 1993, 1, 40–44. [Google Scholar]
- Majumdar, A.; Ward, R.K. Fast group sparse classification. Can. J. Electr. Comput. Eng. 2009, 34, 136–144. [Google Scholar] [CrossRef]
- Bockelmann, C. Iterative Soft Interference Cancellation for Sparse BPSK Signals. IEEE Commun. Lett. 2015, 19, 855–858. [Google Scholar] [CrossRef]
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, B.; Du, R.; Kang, W.; Liu, G. Multi-User Detection for Sporadic IDMA Transmission Based on Compressed Sensing. Entropy 2017, 19, 334. https://doi.org/10.3390/e19070334
Li B, Du R, Kang W, Liu G. Multi-User Detection for Sporadic IDMA Transmission Based on Compressed Sensing. Entropy. 2017; 19(7):334. https://doi.org/10.3390/e19070334
Chicago/Turabian StyleLi, Bo, Rui Du, Wenjing Kang, and Gongliang Liu. 2017. "Multi-User Detection for Sporadic IDMA Transmission Based on Compressed Sensing" Entropy 19, no. 7: 334. https://doi.org/10.3390/e19070334



