1. Introduction
Massive multiple-input multiple-output (MIMO) is currently being investigated as one of the key enabling technologies for the 5th generation wireless standard [
1]. Specifically, in massive MIMO systems, very large antenna arrays are used for aggressive spatial multiplexing and focusing radiated energy towards desired spatial directions [
2,
3]. Thereby, massive MIMO can potentially provide unprecedented gains in spectral and energy efficiencies compared to conventional MIMO.
Confidentiality of transmitted information is one of the key challenges for system designers of next generation wireless communication networks [
4]. To protect confidential communication against intruders and eavesdropper attacks, the concept of physical layer security [
5,
6,
7,
8,
9] has recently attracted significant interest to complement current cryptographic approaches on higher layers. These techniques realize secure communication directly at the physical layer by exploiting the noisiness and imperfection of the wireless communication channel for degrading the quality of signal reception at eavesdroppers, and thereby prevent them from eavesdropping upon the confidential information from the intercepted signals [
4].
Another concept that promises significant gains in performance for wireless communication networks are so-called
cognitive radio networks. These cognitive networks allow secondary systems to access the licensed spectrum of the primary systems by exploiting the underlay spectrum sharing techniques, and thereby, mitigating the spectrum under-utilization of current wireless systems and significantly improving the spectral efficiency [
10]. In cognitive radio systems, where the primary spectrum is an open medium to be accessed and utilized by the secondary systems, achieving end-to-end security is a crucial challenge to the system designs and configurations. Information theoretic secrecy provisioning for cognitive radio networks has been investigated, e.g., in [
11,
12].
In the event that the eavesdroppers intercept confidential signals passively, they do not transmit in order to conceal their existence. Therefore, the acquisition of the channel state information (CSI) of the eavesdropping channels at the massive MIMO base-stations (BSs) will be difficult. Although the null-space beamforming techniques can be effectively used in conventional MIMO BS for provisioning of physical layer security, constructing such sophisticated precoders at the massive MIMO BSs will be prohibitively complicated. Alternatively, artificial noise (AN) sequences can be exploited for massive MIMO BSs. In this context, massive MIMO techniques can be used in cognitive radio systems for provisioning physical layer security by exploiting the large antenna arrays at the BSs to simultaneously transmit confidential signals towards the legitimate user nodes and AN sequences towards eavesdroppers for perturbing the intercepted signals.
Notwithstanding that the massive MIMO techniques have received significant interest recently, little research exists on securing massive MIMO systems by exploiting physical layer security strategies. Next, some of the important contributions to the development of physical layer provisioning in massive MIMO systems are summarized. In [
13], a secure transmission scheme for single-hop massive MIMO systems is investigated by deriving the secrecy rates and secrecy outage probabilities for perfect and imperfect CSI. Furthermore, in [
14], the effects of linear precoding of data and AN in secure massive MIMO downlink are studied. Specifically, in [
14], linear precoders that are based on matrix polynomials are proposed for both data and AN precoding, and consequently, the corresponding polynomial coefficients are optimized to minimize the sum mean-squared error and the AN leakage to the user nodes. In [
15], optimal power allocation with security constraints in multi-user massive MIMO systems with distributed antennas is investigated. Moreover, in [
16], the physical layer security and energy efficiency aspects are investigated for massive MIMO-enabled heterogeneous cloud radio access networks.
Although there is a symbiotic relationship between massive MIMO and cognitive radio networks to achieve a groundbreaking spectral and energy efficiencies for future wireless systems, facilitating secrecy at the physical layer of cognitive massive MIMO systems has not yet received any attention in the existing studies in the literature. To fill this gap, in this paper, a secure downlink transmission strategy is investigated for cognitive massive MIMO systems with underlay spectrum sharing in the presence of a passive multi-antenna eavesdropper. To this end, a secondary massive MIMO system is allowed to access the licensed spectrum of a primary massive system subject to an interference temperature constraint, which is the maximum tolerable co-channel interference (CCI) power at the primary system. Consequently, the secondary transmit power is constrained such that the CCI inflicted at the primary system due to secondary concurrent transmission is maintained below this interference temperature. The motive of the eavesdropper is to intercept the confidential transmissions of the primary or secondary systems. By assuming that the eavesdropper’s CSI is unavailable, AN sequences are generated at the primary base-station (PBS) for provisioning physical layer security by exploiting the additional degrees-of-freedom offered by its massive antenna array. The construction of null-space-based AN shaping precoders at the PBS is prohibitively complicated due to its massive antenna array, and hence, random AN shaping matrices are advocated. Furthermore, zero-forcing (ZF) based precoders are used at the PBS and the secondary base-station (SBS).
The uplink channels of the primary and secondary systems are estimated at the corresponding BSs by using pilots transmitted by the primary user nodes (PUs) and secondary user nodes (SUs), respectively. The number of orthogonal pilot sequences is limited and depends on the coherence interval of the wireless channels [
2]. Hence, the same pilot sequence is shared among both PUs and SUs for minimum mean square error (MMSE) channel estimation. Nevertheless, a normalized pseudo-inverse of a complex Gaussian random matrix is used for AN shaping at the PBS, and thereby, the burden of estimating the eavesdropper’s channels is avoided.
The performance of the aforementioned system set-up is investigated by deriving the achievable secrecy rates in closed-form for both imperfect and perfect channel state information (CSI) cases. The impacts of the numbers of PBS and SBS antennas are investigated in the context of provisioning physical layer secure transmission for cognitive massive MIMO systems. Furthermore, the detrimental effects of intra-cell secondary interference, channel estimation errors, intra-cell pilot contamination, and AN leakage into the desired signals at the PUs and SUs are investigated for the imperfect and perfect CSI cases. Thereby, the achievable secrecy rate degradation due to intra-cell pilot contamination and inaccurate channel estimation is quantified.
Notation: , , , and denote the conjugate, transpose, Hermitian-transpose, and the element of a matrix , respectively. is the expectation and the operator ⊗ denotes the Kronecker product.
3. Secrecy Rate Analysis
An achievable secrecy rate of the
k-th PU is given by the difference between channel capacities of the PBS to PU channel and the PBS to eavesdropper channel. Thus, the achievable secrecy rate at the
k-th PU is:
where
.
A lower bound for the achievable rate at the
k-th PU can be derived from (
29) as (see
Appendix A.2 for the derivation):
The eavesdropper’s rate, on the other hand, cannot be lower bounded, since in that case the obtained secrecy rate is no longer a lower bound. Thus, the ergodic rate of the
k-th PU signal leaked into the eavesdropper is computed as
, where
is a closed-form expression for the SINR of the
k-th PU signal intercepted at the eavesdropper, which is derived from (
24) as (by assuming eavesdropper is able to mitigate inter-pair interference [
13]):
Similarly, the achievable secrecy rate of the
m-th SU is:
where
is an achievable rate of the
m-th SU and its lower bound is derived by following steps similar to those used for deriving (
36) as:
Furthermore,
is the information leakage rate to the eavesdropper for decoding the
m-th SU’s confidential information, and can be computed as:
, where
is the SINR expression of the
m-th SU signal intercepted at the eavesdropper, which is derived from (
24) as:
6. Numerical Results
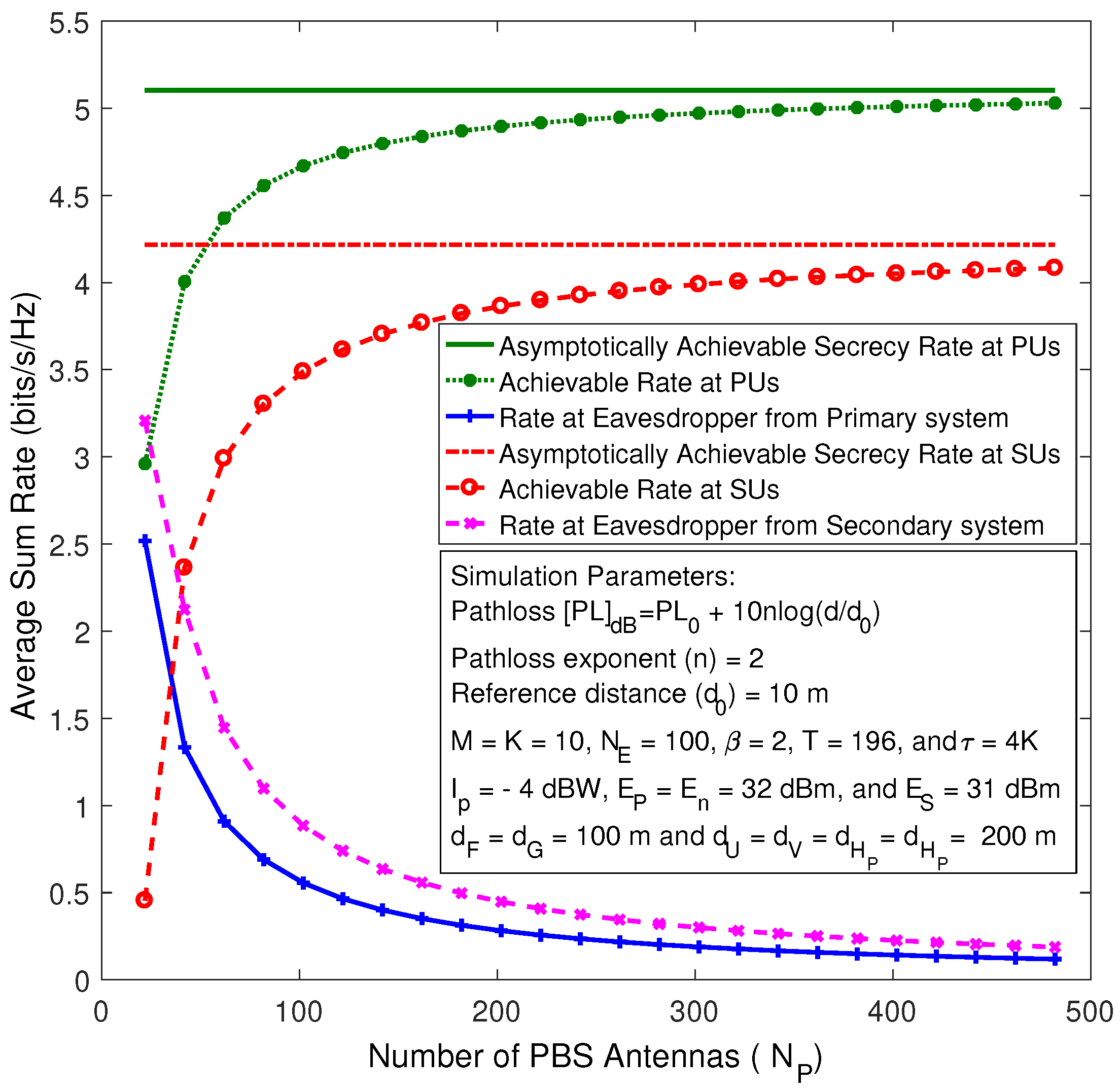
In
Figure 2, the achievable secrecy sum rates at the PUs and SUs are plotted. Furthermore, the information leakage rates to the eavesdropper from the primary and secondary transmissions are plotted against
while keeping
fixed. The exact (simulation) curves are generated by using (
29), (
33), (
37), and (
40) through Monte-Carlo simulations. Moreover, the asymptotic secrecy rate is plotted by using (
41) and (
42).
Figure 2 reveals that the corresponding information leakage rates to the eavesdropper asymptotically vanish when
and
. Hence, the secrecy rate asymptotically approaches the achievable rate at the user nodes. Therefore, the intra-cell pilot contamination effects in cognitive massive MIMO systems do not hinder the use of random pseudo-inverse based AN shaping matrices.
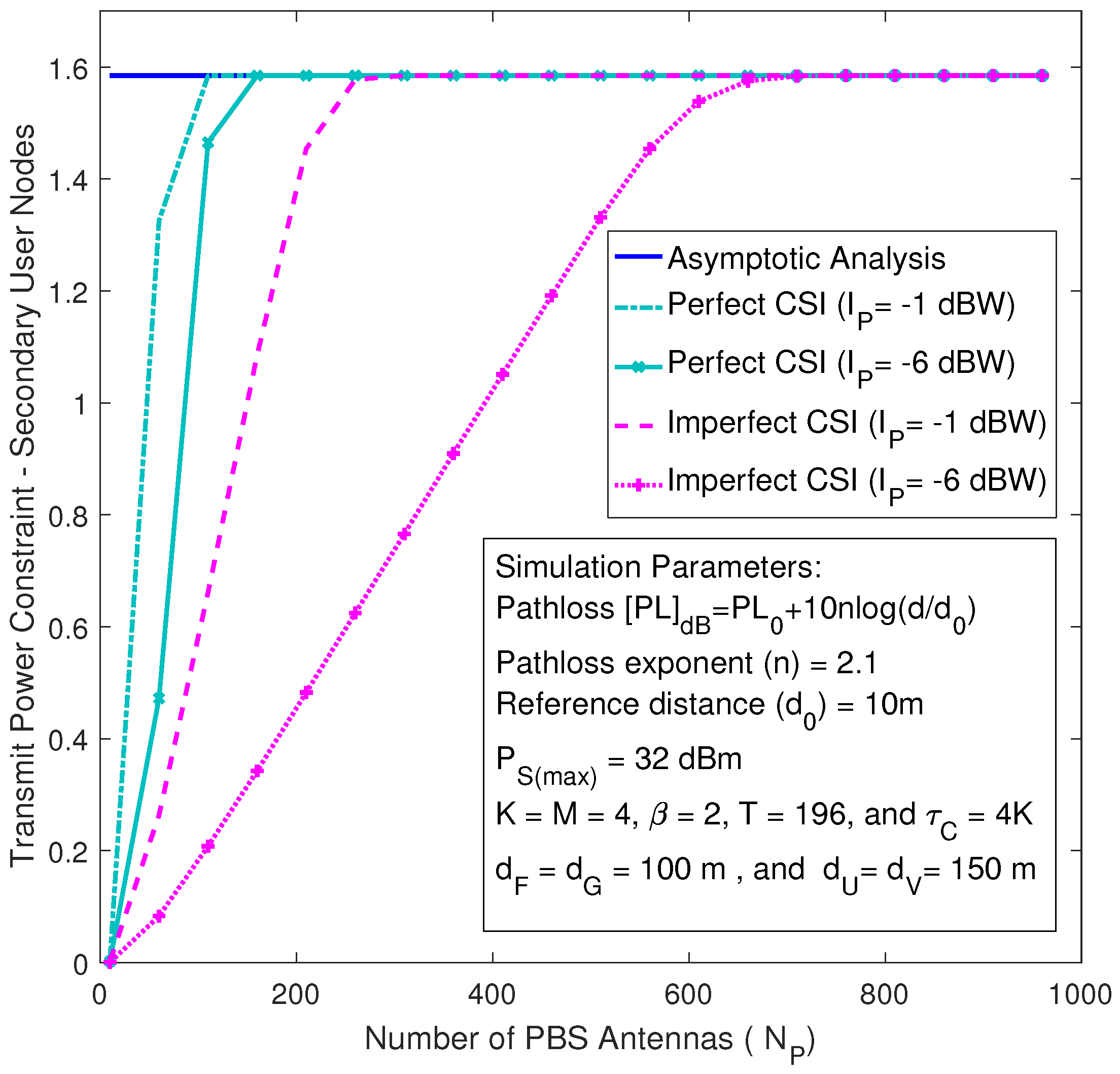
To investigate the impact of the primary interference temperatures on the secondary system transmissions for the imperfect and perfect CSI cases, the transmit power constraint of the SUs is plotted, in
Figure 3, against the number of PBS antennas for two different primary interference temperatures. The asymptotic transmit power constraints are plotted by using the asymptotic analysis in (
14) and (
47), while the exact curves are plotted by using Monte-Carlo simulations.
Figure 3 clearly reveals that the transmit power of the secondary system approaches its allowable peak value when the number of PBS antennas grows large. However, the rate of asymptotic convergence depends on the CSI assumption and the primary interference temperature. Specifically, the curves corresponding to imperfect CSI exhibit the lowest rate of asymptotic convergence compared to the perfect CSI case. Moreover, the asymptotic rate of convergence decreases whenever the primary interference temperature decreases.
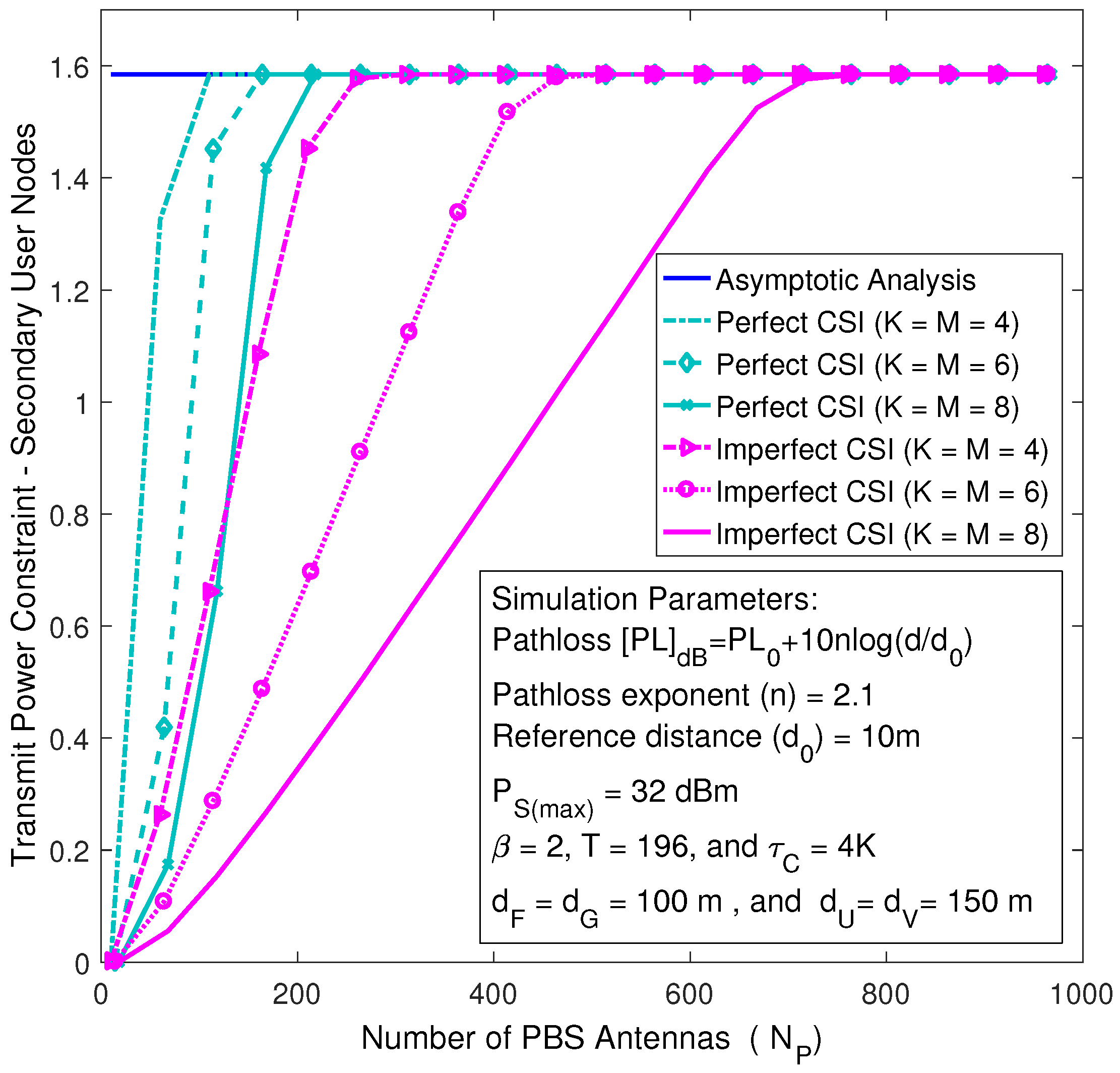
In
Figure 4, the transmit power constraint at the secondary system is plotted versus the number of PBS antennas by varying the number of user nodes for the cases of imperfect and perfect CSI.
Figure 4 shows that the secondary system transmit power asymptotically approaches its peak level as the number of PBS antennas grows without bound, irrespective of the number of user nodes. Nevertheless, the rate of asymptotic convergence decreases when the numbers of user nodes increase. Therefore, the secondary system can asymptotically be operated at its peak transmit power, regardless of the number of user nodes and primary interference temperature, whenever the PBS is equipped with a very large antenna array.
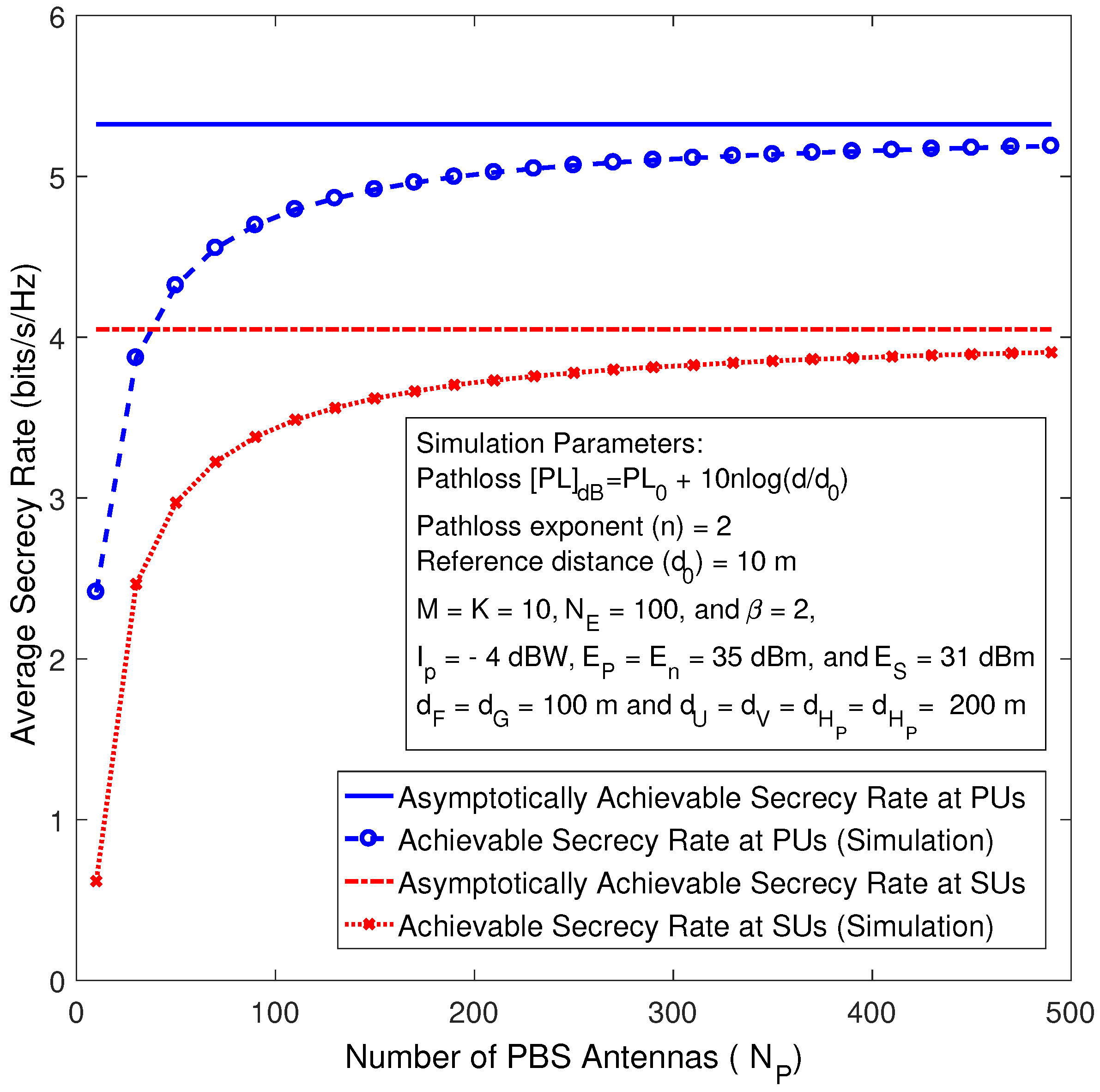
Figure 5 depicts the achievable secrecy rate of the primary and secondary systems against the number of PBS antennas for the perfect CSI case. The asymptotic secrecy rate curves are plotted by using (
52) and (
53), whereas the exact sum rate curves are plotted by using Monte-Carlo simulations. As shown in
Figure 5, for a fixed number of antennas at the eavesdropper (
), the achievable secrecy rates at the primary and secondary systems go up gradually with the growing of
and
until they approach their corresponding asymptotic curves, which basically means the capability of the eavesdropper decreases and eventually vanishes whenever the number of antennas grows large.