A Survey on Robust Interference Management in Wireless Networks
Abstract
:1. Introduction
2. Channel Model
3. Metrics
4. Channel State Information
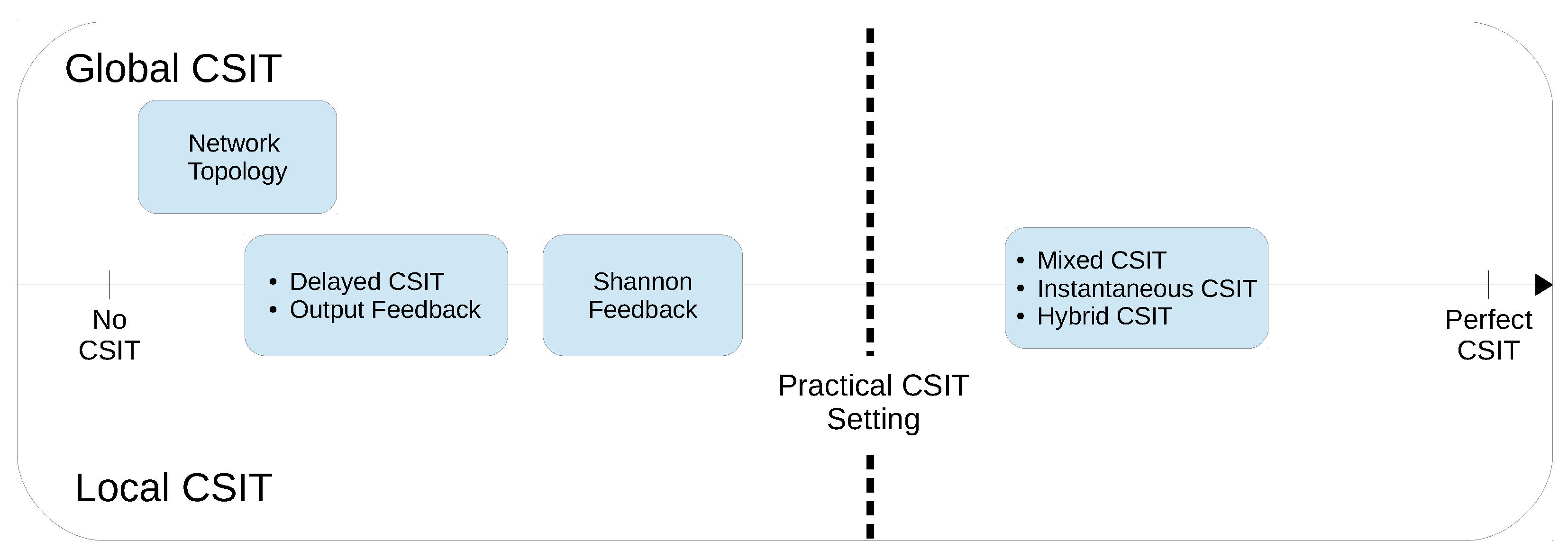
4.1. Perfect CSIT
- (a)
- ,
- (b)
- ,
4.2. Imperfect CSIT
4.2.1. Imperfect Instantaneous CSIT
4.2.2. Delayed CSIT
4.2.3. Mixed CSIT
4.3. Alternating CSIT
4.4. Feedback
4.5. Network Topology
5. Robust Schemes
5.1. MISO Broadcast Channel
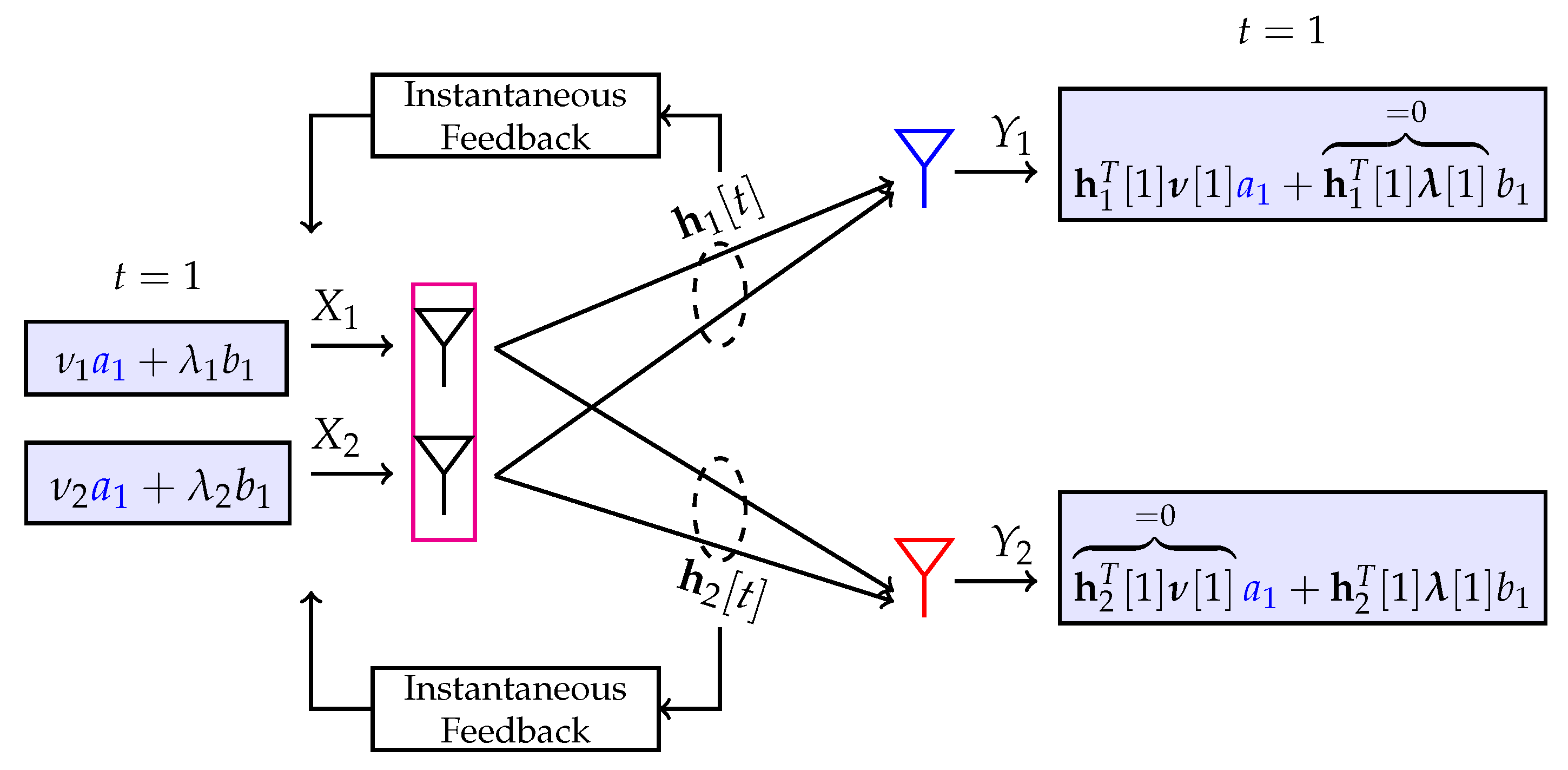
5.1.1. Perfect CSIT
5.1.2. Delayed CSIT
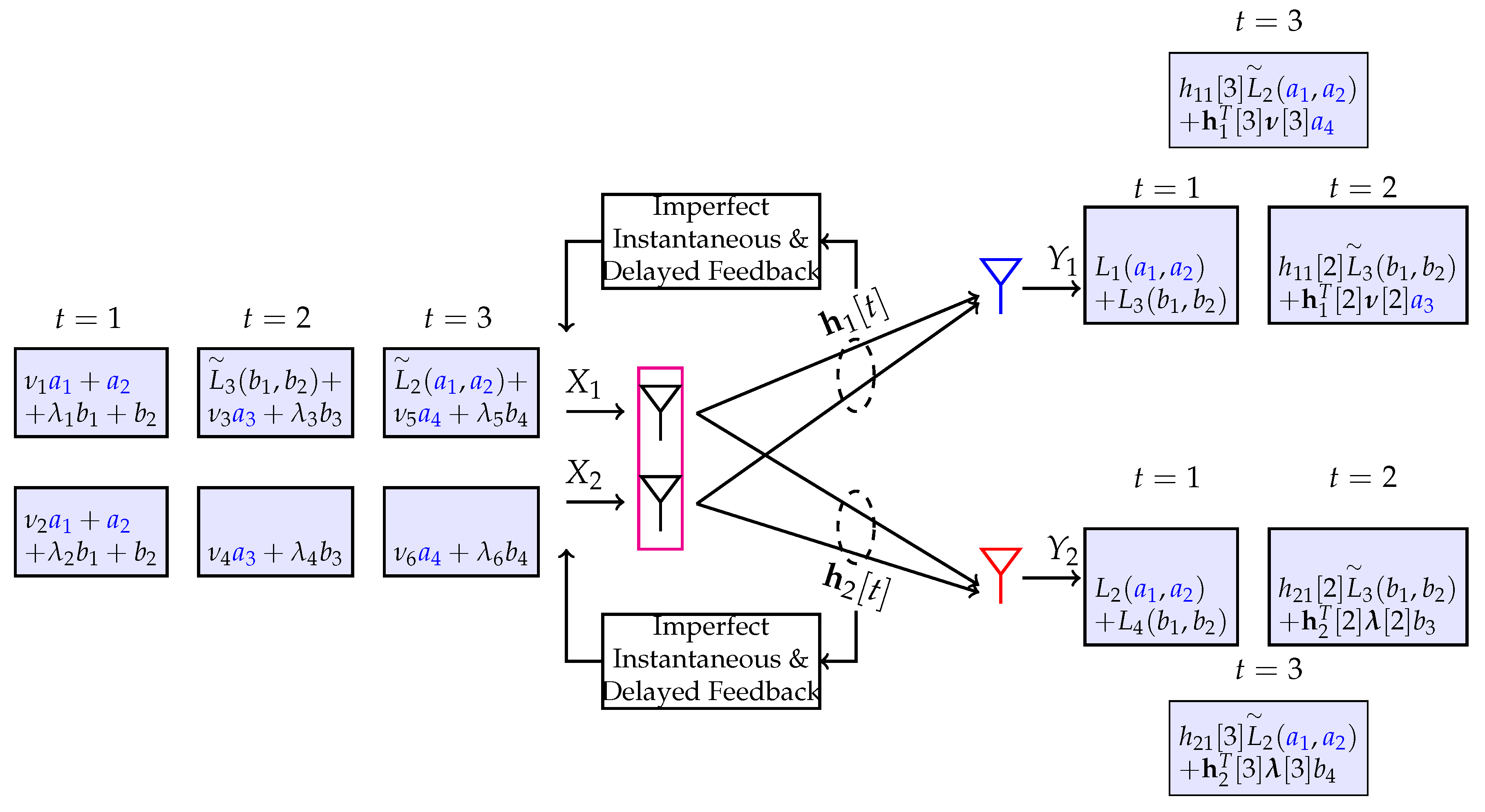
- In the first phase consisting of two channel uses ( and in Figure 3a) the transmitter broadcasts symbols and in and and in . Thus, the received signal at Rx-1 and Rx-2 are (noise-corrupted) linear combinations of and the respective channels at , i.e.,as well as linear combinations of at given by:Thus, channel use is used to serve Rx-1, while channel use is utilized to serve Rx-2. Specifically, this means that received signals and are overheard signals at Rx-2 and Rx-1, respectively. These two overheard signals do not provide the respective receivers with useful information on their desired symbols. However, the i.i.d. assumption in the channel matrixfor arbitrary t implies that is of full rank almost surely. This suggests that the overheard signal of Rx-2 is an independent observation in Rx-1’s desired symbols and than the signal . The same relationship applies to and . In DoF sense at which SNR is asymptotically large, it suffices to restrict the focus on overheard equations and (that are free from noise) instead of overheard signals and . Since every receiver seeks to decode two symbols, either or , each receiver needs two independent observations as a function of its desired symbols. Specifically, for these two receivers this means: If Rx-1 is aware of and Rx-2 of , decoding of and at the respective receivers becomes feasible within bounded noise distortion. Recall that and are yet unknown to receivers 1 and 2 from channel uses and . Consequently, in phase two, the goal is to convey to Rx-1 and to Rx-2. In phase two, delayed CSIT comes into play when locally constructing overheard equations at the transmitter.
- In phase two, the overheard equations and are conveyed to their desired receivers in the single channel use . At time instant , the transmitter is aware of both and since it has access to delayed CSIT. Therefore, the transmitter can generate overheard equations and at time instant . By sending the common symbolfrom a single antenna element allows each receiver to use its side information and obtain the overheard equation of the complementary receiver. E.g., when sending , Rx-1 uses the knowledge of the overheard equation as side information and CSIR to cancel its contribution from . By doing so, Rx-1 retrieves from . Thus, Rx-1 now possesses two (noisy) linear independent equations in enabling Rx-1 to decode its desired symbols within bounded noise [41].
5.1.3. Mixed CSIT
- After decoding of and , the receivers can remove the contribution of the decoded signals and retrieve their desired symbols, i.e., at Rx-1 and at Rx-2.
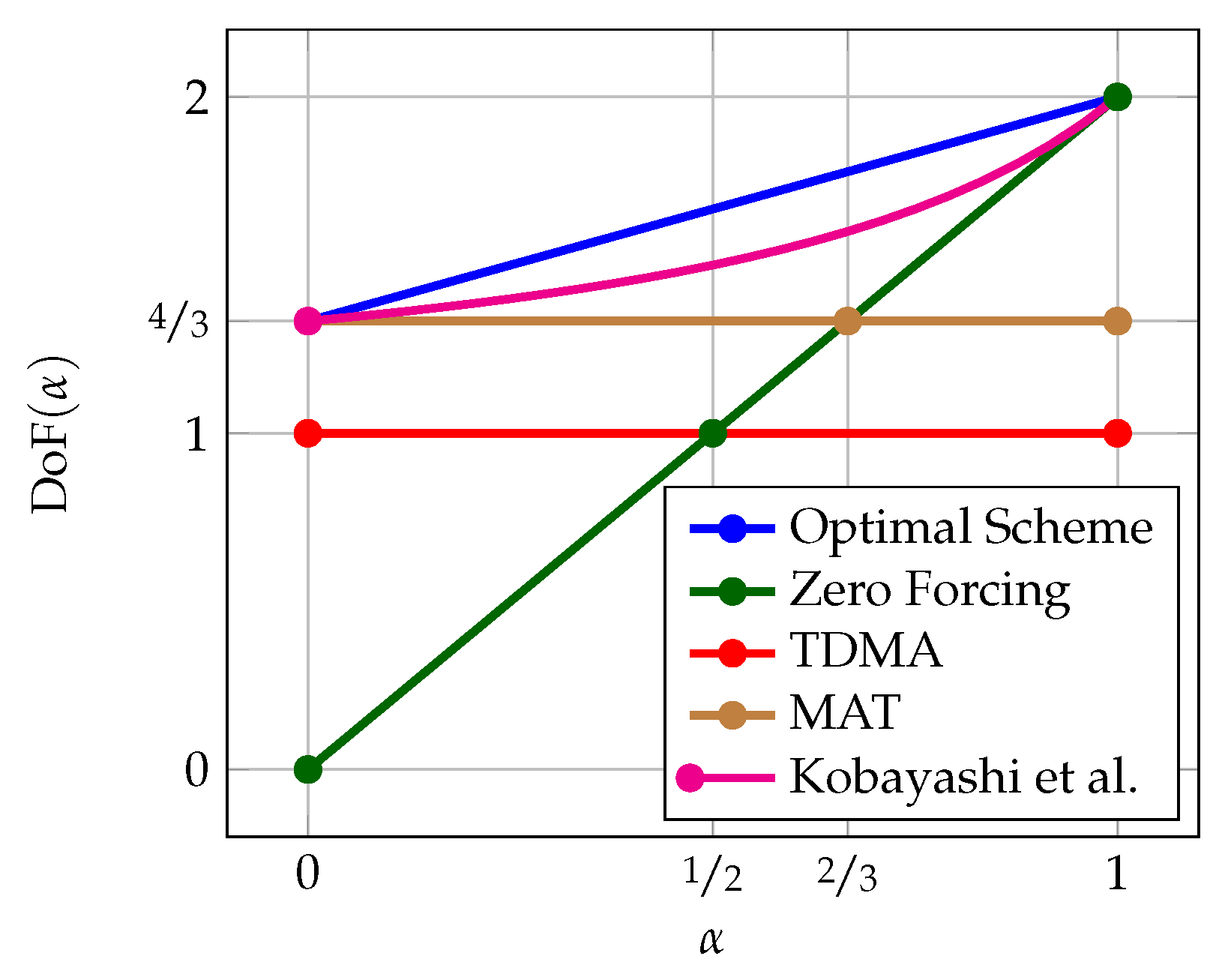
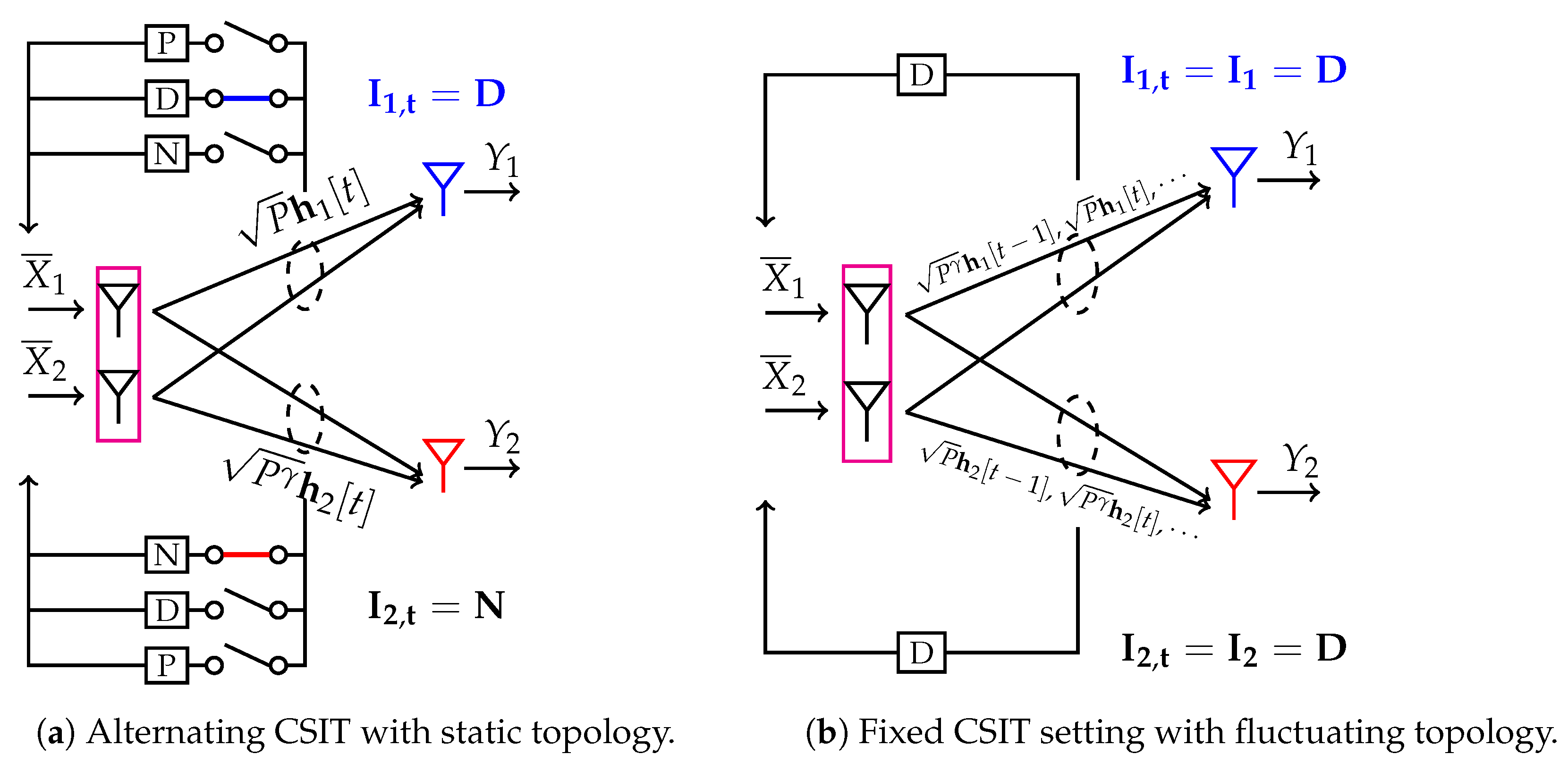
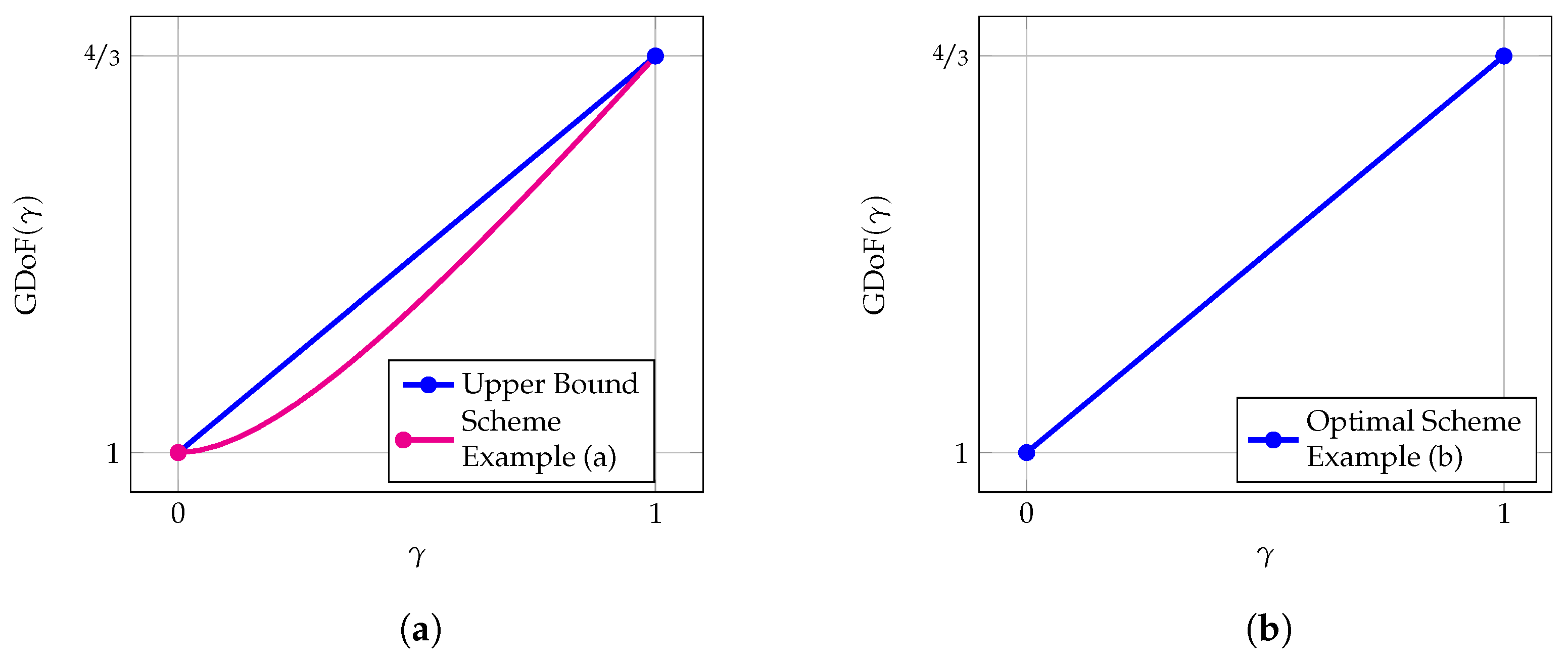
5.1.4. Alternating CSIT with Fluctuating Topology
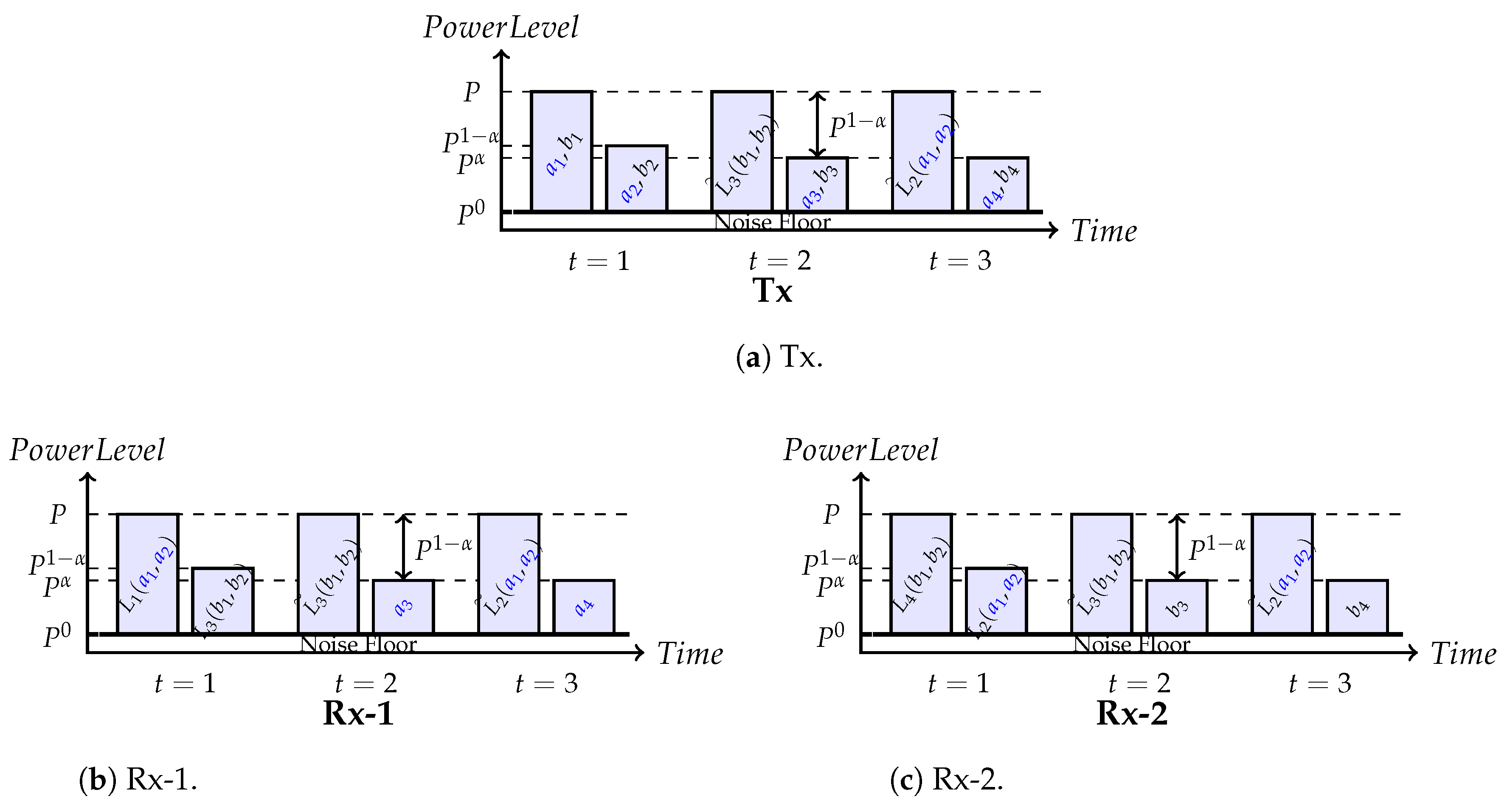
- With the use of private symbol , we account for the fixed -topology (TP). Concretely, due to its scaling with , this symbol is received at power level at its intended receiver Rx-1, whereas it is received at noise level at its unintended receiver Rx-2. Being received at noise level at Rx-2, makes it a negligible interference term in (G)DoF sense.
- Depending on whether the CSIT state or is present, we can improve the achievable rate of the user with no CSIT feedback by utilizing the general idea of the MAT scheme. That is, we can create interference at the unintended receiver as side information which can be canceled in retrospect through the use of delayed CSIT while providing the intended receiver with additional information on its desired symbols. For instance, in state , we send among others and , which creates interference at Rx-1, but represents desired information for Rx-2. Constructing, the observation of Rx-1 in terms and locally at the transmitter and broadcasting this information, will help Rx-1 canceling interference and provide Rx-2 with extra information for decoding and .
- In state , it is advisable not to send any additional private information. This is simply because private information represents interference to one of the two receivers which cannot be reconstructed (and thus canceled) due to the lack of CSIT.
5.1.5. Conclusion: MISO Broadcast Channel
5.2. Distributed Interference Networks
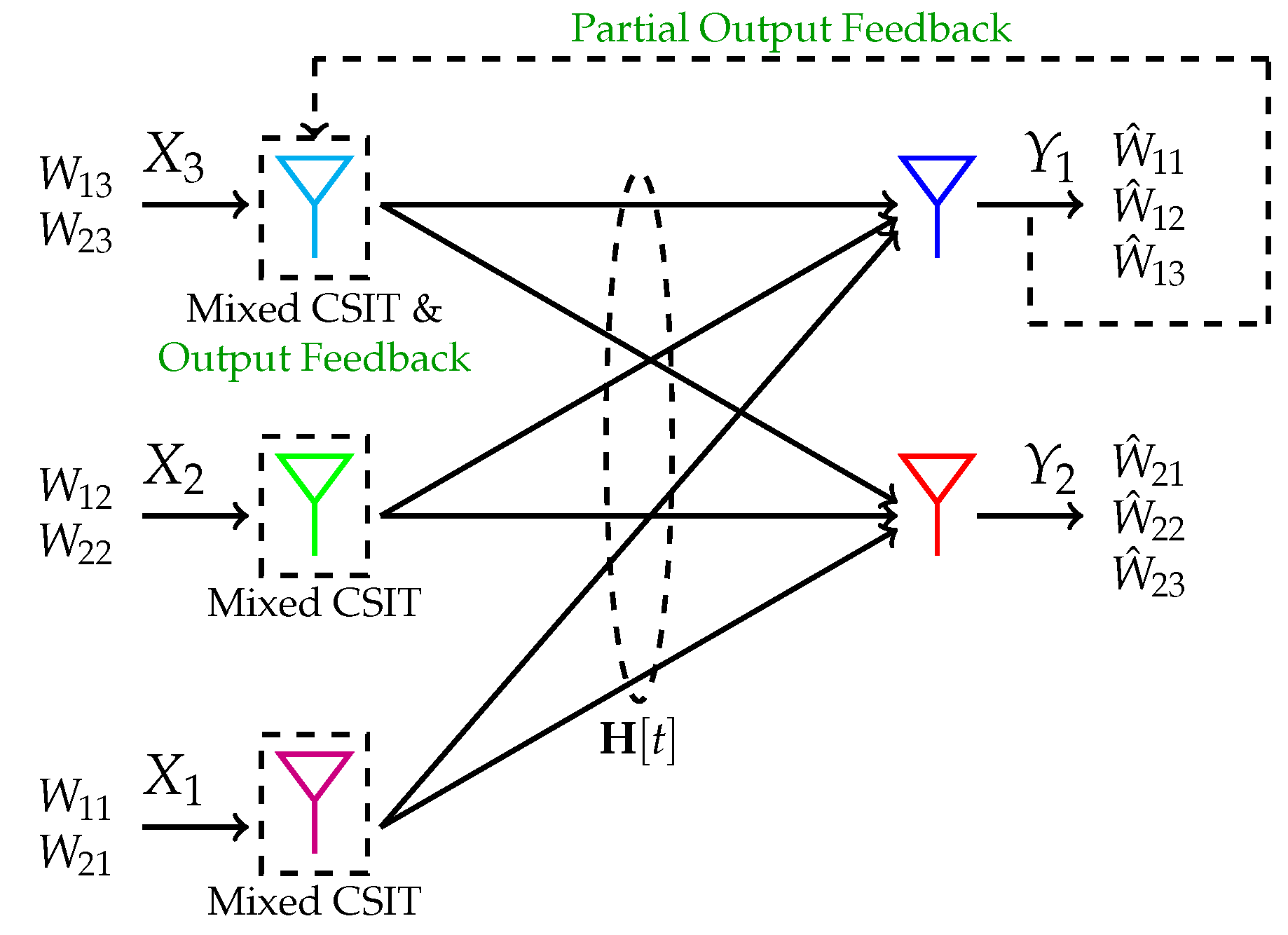
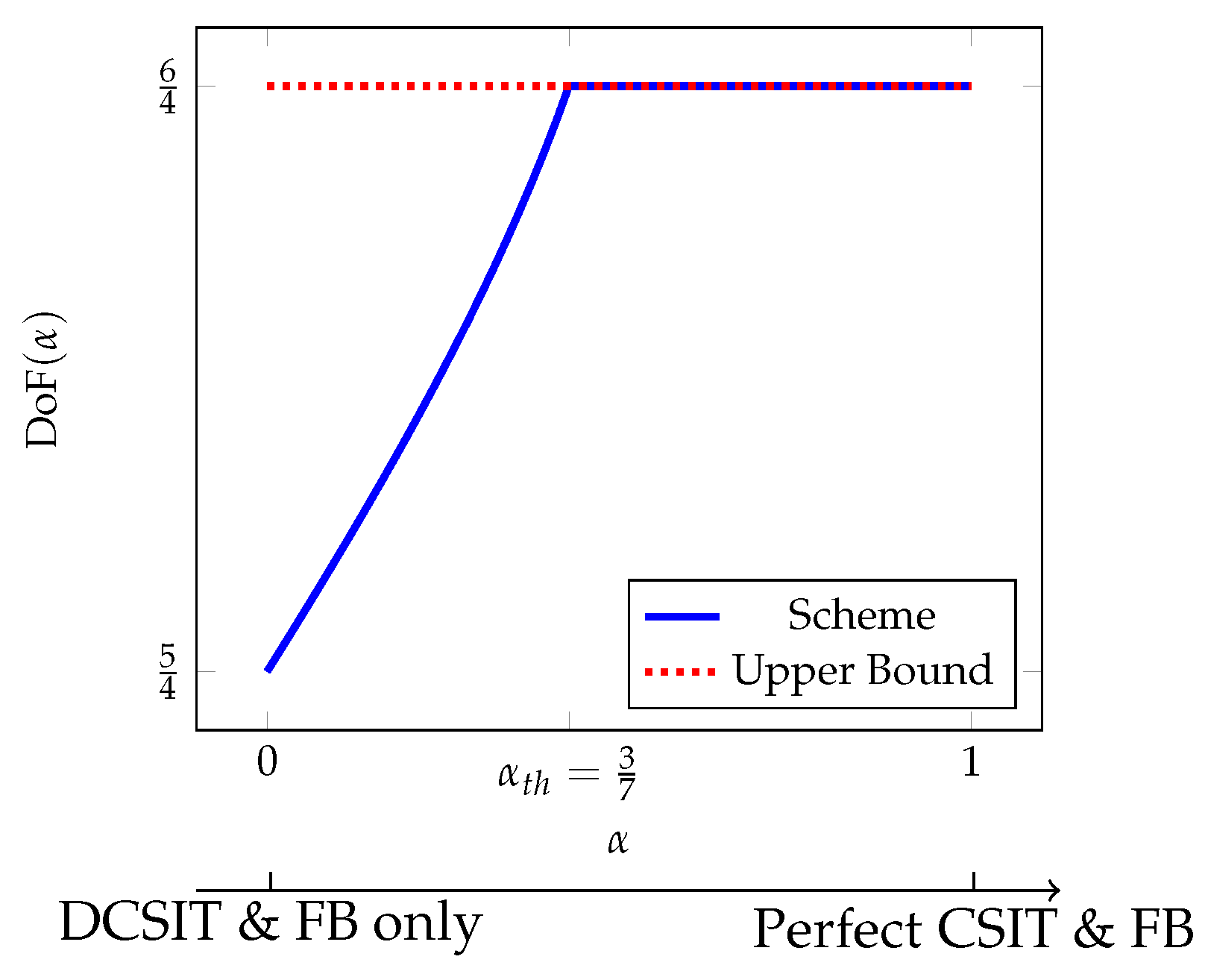
5.2.1. X-Channel with Mixed CSIT and Feedback
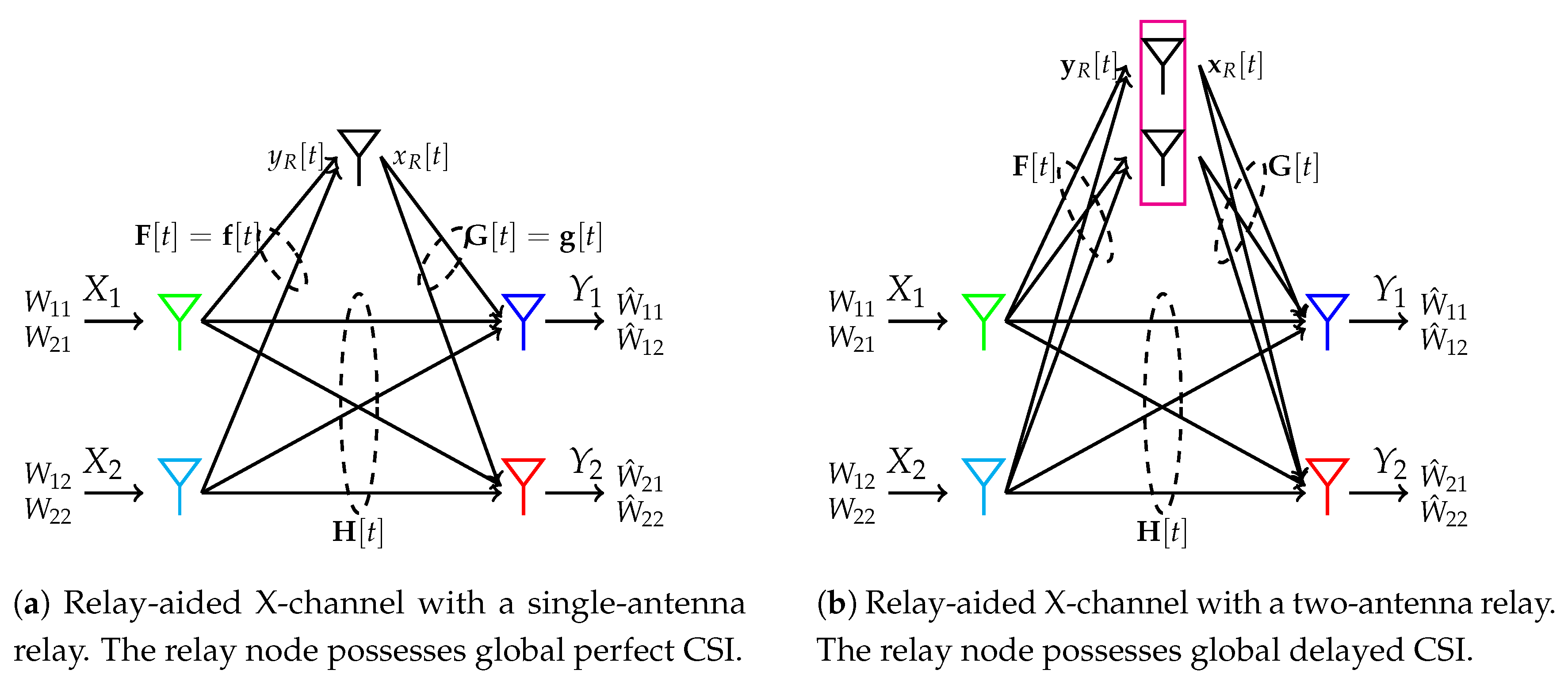
5.2.2. Relay-Aided Interference Alignment for X-Channel without CSIT
6. Conclusions and Open Problems
Acknowledgments
Author Contributions
Conflicts of Interest
Abbreviations
| AWGN | Additive white Gaussian noise |
| BC | Broadcast channel |
| CSI | Channel state information |
| CSIR | Channel state information receiver |
| CSIT | Channel state information transmitter |
| DoF | Degrees of freedom |
| FDD | Frequency division duplex |
| GDoF | Generalized degrees of freedom |
| IA | Interference alignment |
| IC | Interference channel |
| MAC | Multiple-access channel |
| MAT | Maddah-Ali-Tse |
| MISO | Multiple-input single-output |
| MSE | Mean square error |
| SDoF | Secure degrees of freedom |
| SIMO | Single-input multiple-output |
| SNR | Signal-to-noise ratio |
| TDMA | Time division multiple access |
| TP | Topology |
| ZF | Zero-forcing |
References
- Shannon, C.E. A Mathematical Theory of Communication. Bell Labs Tech. J. 1948, 27, 379–423. [Google Scholar] [CrossRef]
- Paulraj, A.; Charafeddine, M.; Pereira, S.; Sezgin, A. Interference—The Final Frontier? IEEE Communication Theory Workshop (CTW): Sedona, AZ, USA, 2007. [Google Scholar]
- Etkin, R.H.; Tse, D.N.C.; Wang, H. Gaussian Interference Channel Capacity to Within One Bit. IEEE Trans. Inf. Theory 2008, 54, 5534–5562. [Google Scholar] [CrossRef]
- Cadambe, V.R.; Jafar, S.A. Interference Alignment and Degrees of Freedom of the K-User Interference Channel. IEEE Trans. Inf. Theory 2008, 54, 3425–3441. [Google Scholar] [CrossRef]
- Maddah-Ali, M.A.; Motahari, A.S.; Khandani, A.K. Communication Over MIMO X Channels: Interference Alignment, Decomposition, and Performance Analysis. IEEE Trans. Inf. Theory 2008, 54, 3457–3470. [Google Scholar] [CrossRef]
- Nazer, B.; Gastpar, M.; Jafar, S.A.; Vishwanath, S. Ergodic Interference Alignment. IEEE Trans. Inf. Theory 2012, 58, 6355–6371. [Google Scholar] [CrossRef]
- Jafar, S.A. Interference Alignment: A New Look at Signal Dimensions in a Communication Network. Found. Trends Commun. Inf. Theory 2011, 7, 1–136. [Google Scholar] [CrossRef]
- Cadambe, V.R.; Jafar, S.A. Interference Alignment and the Degrees of Freedom of Wireless X Networks. IEEE Trans. Inf. Theory 2009, 55, 3893–3908. [Google Scholar] [CrossRef]
- Tandon, R.; Jafar, S.A.; Shamai, S.; Poor, H.V. On the Synergistic Benefits of Alternating CSIT for the MISO Broadcast Channel. IEEE Trans. Inf. Theory 2013, 59, 4106–4128. [Google Scholar] [CrossRef]
- Awan, Z.H.; Zaidi, A.; Sezgin, A. Achievable secure degrees of freedom of MISO broadcast channel with alternating CSIT. In Proceedings of the 2014 IEEE International Symposium on Information Theory, Honolulu, HI, USA, 29 June–4 July 2014; pp. 31–35. [Google Scholar]
- Maddah-Ali, M.A.; Tse, D. Completely Stale Transmitter Channel State Information is Still Very Useful. IEEE Trans. Inf. Theory 2012, 58, 4418–4431. [Google Scholar] [CrossRef]
- Abdoli, M.J.; Ghasemi, A.; Khandani, A.K. On the degrees of freedom of three-user MIMO broadcast channel with delayed CSIT. In Proceedings of the 2011 IEEE International Symposium on Information Theory, Petersburg, Russia, 31 July–5 August 2011; pp. 209–213. [Google Scholar]
- Chen, J.; Elia, P. Can imperfect delayed CSIT be as useful as perfect delayed CSIT? DoF analysis and constructions for the BC. In Proceedings of the Annual Allerton Conference on Communication, Control, and Computing (Allerton), Monticello, IL, USA, 1–5 Octomber 2012; pp. 1254–1261. [Google Scholar]
- Kao, D.T.H.; Avestimehr, A.S. Linear Degrees of Freedom of the MIMO X-Channel With Delayed CSIT. IEEE Trans. Inf. Theory 2017, 63, 297–319. [Google Scholar] [CrossRef]
- Jafar, S.A. Blind Interference Alignment. IEEE J. Sel. Top. Signal Process. 2012, 6, 216–227. [Google Scholar] [CrossRef]
- Jafar, S.A. Topological Interference Management Through Index Coding. IEEE Trans. Inf. Theory 2014, 60, 529–568. [Google Scholar] [CrossRef]
- Gherekhloo, S.; Chaaban, A.; Sezgin, A. Resolving entanglements in topological interference management with alternating connectivity. In Proceedings of the 2014 IEEE International Symposium on Information Theory, Honolulu, HI, USA, 29 June–4 July 2014; pp. 1772–1776. [Google Scholar]
- Chaaban, A.; Sezgin, A. Multi-Hop Relaying: An End-to-End Delay Analysis. IEEE Trans. Wirel. Commun. 2016, 15, 2552–2561. [Google Scholar] [CrossRef]
- Tian, Y.; Yener, A. Guiding Blind Transmitters: Degrees of Freedom Optimal Interference Alignment Using Relays. IEEE Trans. Inf. Theory 2013, 59, 4819–4832. [Google Scholar] [CrossRef]
- Frank, D.; Ochs, K.; Sezgin, A. A systematic approach for interference alignment in CSIT-less relay-aided X-networks. In Proceedings of the 2014 IEEE Wireless Communications and Networking Conference (WCNC), Istanbul, Turkey, 6–9 April 2014; pp. 1126–1131. [Google Scholar]
- Tian, Y.; Yener, A. Guiding blind transmitters: Relay-aided interference alignment for the X channel. In Proceedings of the 2012 IEEE International Symposium on Information Theory, Cambridge, MA, USA, 1–6 July 2012; pp. 1513–1517. [Google Scholar]
- Gherekhloo, S.; Chaaban, A.; Di, C.; Sezgin, A. (Sub-)Optimality of Treating Interference as Noise in the Cellular Uplink With Weak Interference. IEEE Trans. Inf. Theory 2016, 62, 322–356. [Google Scholar] [CrossRef]
- Han, T.; Kobayashi, K. A new achievable rate region for the interference channel. IEEE Trans. Inf. Theory 1981, 27, 49–60. [Google Scholar] [CrossRef]
- Bashar, M.; Lejosne, Y.; Slock, D.; Yuan, W.Y. MIMO broadcast channels with Gaussian CSIT and application to location based CSIT. In Proceedings of the Information Theory and Applications Workshop (ITA), San Diego, CA, USA, 9–14 February 2014; pp. 1–7. [Google Scholar]
- Goldsmith, A.; Jafar, S.A.; Jindal, N.; Vishwanath, S. Capacity limits of MIMO channels. IEEE J. Sel. Areas Commun. 2003, 21, 684–702. [Google Scholar] [CrossRef]
- Médard, M. The effect upon channel capacity in wireless communications of perfect and imperfect knowledge of the channel. IEEE Trans. Inf. Theory 2000, 46, 933–946. [Google Scholar]
- Gou, T.; Jafar, S.A. Optimal Use of Current and Outdated Channel State Information: Degrees of Freedom of the MISO BC with Mixed CSIT. IEEE Commun. Lett. 2012, 16, 1084–1087. [Google Scholar] [CrossRef]
- Yang, S.; Kobayashi, M.; Gesbert, D.; Yi, X. Degrees of Freedom of Time Correlated MISO Broadcast Channel With Delayed CSIT. IEEE Trans. Inf. Theory 2013, 59, 315–328. [Google Scholar] [CrossRef]
- Kobayashi, M.; Yang, S.; Gesbert, D.; Yi, X. On the degrees of freedom of time correlated MISO broadcast channel with delayed CSIT. In Proceedings of the IEEE International Symposium on Information Theory, Cambridge, MA, USA, 1–6 July 2012; pp. 2501–2505. [Google Scholar]
- Caire, G.; Jindal, N.; Kobayashi, M.; Ravindran, N. Multiuser MIMO Achievable Rates With Downlink Training and Channel State Feedback. IEEE Trans. Inf. Theory 2010, 56, 2845–2866. [Google Scholar] [CrossRef]
- Zhang, J.; Slock, D.; Elia, P. Achieving the DoF limits of the SISO X channel with imperfect-quality CSIT. In Proceedings of the IEEE International Symposium on Information Theory (ISIT), Hong Kong, China, 14–19 June 2015; pp. 626–630. [Google Scholar]
- Kakar, J.; Awan, Z.H.; Sezgin, A. Achieving the optimal DoF with feedback and mixed CSIT for the 3x2 X-channel. In Proceedings of the International Symposium on Wireless Communication Systems (ISWCS), Poznan, Poland, 20–23 September 2016; pp. 131–135. [Google Scholar]
- Mohanty, K.; Varanasi, M.K. On the DoF Region of the K-user MISO Broadcast Channel with Hybrid CSIT. arXiv, 2013; arXiv:1312.1309. [Google Scholar]
- Amuru, S.; Tandon, R.; Shamai, S. On the degrees-of-freedom of the 3-user MISO broadcast channel with hybrid CSIT. In Proceedings of the IEEE International Symposium on Information Theory, Honolulu, HI, USA, 29 June–4 July 2014; pp. 2137–2141. [Google Scholar]
- Tandon, R.; Mohajer, S.; Poor, H.V.; Shamai, S. On X-channels with feedback and delayed CSI. In Proceedings of the IEEE International Symposium on Information Theory, Cambridge, MA, USA, 1–6 July 2012; pp. 1877–1881. [Google Scholar]
- Abdoli, J.; Ghasemi, A.; Khandani, A.K. Interference and X Networks With Noisy Cooperation and Feedback. IEEE Trans. Inf. Theory 2015, 61, 4367–4389. [Google Scholar] [CrossRef]
- Weingarten, H.; Steinberg, Y.; Shamai, S.S. The Capacity Region of the Gaussian Multiple-Input Multiple-Output Broadcast Channel. IEEE Trans. Inf. Theory 2006, 52, 3936–3964. [Google Scholar] [CrossRef]
- Jafar, S.A.; Fakhereddin, M.J. Degrees of Freedom for the MIMO Interference Channel. IEEE Trans. Inf. Theory 2007, 53, 2637–2642. [Google Scholar] [CrossRef]
- Telatar, I.E. Capacity of Multi-antenna Gaussian Channels. Eur. Trans. Telecommun. 1999, 10, 585–595. [Google Scholar] [CrossRef]
- Cover, T.M.; Thomas, J.A. Elements of Information Theory; Wiley: Hoboken, NJ, USA, 2006. [Google Scholar]
- Gamal, A.E.; Kim, Y.H. Network Information Theory; Cambridge University Press: New York, NY, USA, 2012. [Google Scholar]
- Vaze, C.S.; Varanasi, M.K. The Degrees of Freedom Region of the Two-User and Certain Three-User MIMO Broadcast Channel with Delayed CSI. arXiv, 2011; arXiv:1101.0306. [Google Scholar]
- Vaze, C.S.; Varanasi, M.K. The degrees of freedom region of the two-user MIMO broadcast channel with delayed CSIT. In Proceedings of the IEEE International Symposium on Information Theory, Petersburg, Russia, 31 July–5 August 2011; pp. 199–203. [Google Scholar]
- Ghasemi, A.; Motahari, A.S.; Khandani, A.K. Interference Alignment for the MIMO Interference Channel with Delayed Local CSIT. arXiv, 2011; arXiv:1102.5673. [Google Scholar]
- Vaze, C.S.; Varanasi, M.K. The Degrees of Freedom Region and Interference Alignment for the MIMO Interference Channel with Delayed CSIT. IEEE Trans. Inf. Theory 2012, 58, 4396–4417. [Google Scholar] [CrossRef]
- Tandon, R.; Mohajer, S.; Poor, H.V.; Shamai, S. Degrees of Freedom Region of the MIMO Interference Channel With Output Feedback and Delayed CSIT. IEEE Trans. Inf. Theory 2013, 59, 1444–1457. [Google Scholar] [CrossRef]
- Maleki, H.; Jafar, S.A.; Shamai, S. Retrospective Interference Alignment Over Interference Networks. IEEE J. Sel. Top. Signal Process. 2012, 6, 228–240. [Google Scholar] [CrossRef]
- Mohanty, K.; Varanasi, M.K. Degrees of Freedom of the MIMO Z-Interference Channel with Delayed CSIT. IEEE Commun. Lett. 2015, 19, 2282–2285. [Google Scholar] [CrossRef]
- Ghasemi, A.; Motahari, A.S.; Khandani, A.K. On the degrees of freedom of X channel with delayed CSIT. In Proceedings of the 2011 IEEE International Symposium on Information Theory, Petersburg, Russia, 31 July–5 August 2011; pp. 767–770. [Google Scholar]
- Abdoli, M.J.; Ghasemi, A.; Khandani, A.K. On the Degrees of Freedom of K-User SISO Interference and X Channels with Delayed CSIT. IEEE Trans. Inf. Theory 2013, 59, 6542–6561. [Google Scholar] [CrossRef]
- Zaidi, A.; Awan, Z.H.; Shamai (Shitz), S.; Vandendorpe, L. Secure Degrees of Freedom of MIMO X-Channels With Output Feedback and Delayed CSIT. IEEE Trans. Inf. Forensics Secur. 2013, 8, 1760–1774. [Google Scholar] [CrossRef]
- Yeung, R.W. Information Theory and Network Coding, 1st ed.; Springer Publishing: New York City, NY, USA, 2008. [Google Scholar]
- Bandemer, B.; Sezgin, A.; Paulraj, A. On the noisy interference regime of the MISO Gaussian interference channel. In Proceedings of the Asilomar Conference on Signals, Systems and Computers, Pacific Grove, CA, USA, 26–29 October 2008; pp. 1098–1102. [Google Scholar]
- Charafeddine, M.A.; Sezgin, A.; Han, Z.; Paulraj, A. Achievable and Crystallized Rate Regions of the Interference Channel with Interference as Noise. IEEE Trans. Wirel. Commun. 2012, 11, 1100–1111. [Google Scholar] [CrossRef]
- Geng, C.; Jafar, S.A. On the Optimality of Treating Interference as Noise: Compound Interference Networks. IEEE Trans. Inf. Theory 2016, 62, 4630–4653. [Google Scholar] [CrossRef]
- Chaaban, A.; Sezgin, A. On the Capacity of the 2-user Gaussian MAC Interfering with a P2P Link. In Proceedings of the 11th European Wireless Conference 2011—Sustainable Wireless Technologies (European Wireless), Vienna, Austria, 27–29 April 2011; pp. 1–6. [Google Scholar]
- Chaaban, A.; Sezgin, A. Sub-optimality of treating interference as noise in the cellular uplink. In Proceedings of the 2012 International ITG Workshop on Smart Antennas, Berlin, Germany, 15–17 March 2012; pp. 238–242. [Google Scholar]
- Davoodi, A.G.; Jafar, S.A. Aligned Image Sets Under Channel Uncertainty: Settling Conjectures on the Collapse of Degrees of Freedom Under Finite Precision CSIT. IEEE Trans. Inf. Theory 2016, 62, 5603–5618. [Google Scholar] [CrossRef]
- Mohanty, K.; Varanasi, M.K. Degrees of Freedom Region of the MIMO Z-Interference Channel with Mixed CSIT. IEEE Commun. Lett. 2016, 20, 2422–2425. [Google Scholar] [CrossRef]
- Yi, X.; Yang, S.; Gesbert, D.; Kobayashi, M. The Degrees of Freedom Region of Temporally Correlated MIMO Networks With Delayed CSIT. IEEE Trans. Inf. Theory 2014, 60, 494–514. [Google Scholar] [CrossRef]
- Hao, C.; Rassouli, B.; Clerckx, B. Achievable DoF Regions of MIMO Networks with Imperfect CSIT. arXiv, 2016; arXiv:1603.07513. [Google Scholar]
- Chen, J.; Elia, P.; Jafar, S.A. On the vector broadcast channel with alternating CSIT: A topological perspective. In Proceedings of the IEEE International Symposium on Information Theory, Honolulu, HI, USA, 29 June–4 July 2014; pp. 2579–2583. [Google Scholar]
- Chen, J.; Elia, P.; Jafar, S.A. On the Two-User MISO Broadcast Channel With Alternating CSIT: A Topological Perspective. IEEE Trans. Inf. Theory 2015, 61, 4345–4366. [Google Scholar] [CrossRef]
- Leon-Garcia, A. Probability and Random Processes For EE’s, 3rd ed.; Prentice-Hall, Inc.: Upper Saddle River, NJ, USA, 2007. [Google Scholar]
- Cover, T.; Gamal, A.E. Capacity theorems for the relay channel. IEEE Trans. Inf. Theory 1979, 25, 572–584. [Google Scholar] [CrossRef]
- Willems, F.M. Informationtheoretical Results for the Discrete Memoryless Multiple Access Channel. Ph.D. Thesis, Katholieke Universiteit Leuven, Leuven, Belgium, 1982. [Google Scholar]
- Tse, D.; Viswanath, P. Fundamentals of Wireless Communication; Cambridge University Press: New York, NY, USA, 2005. [Google Scholar]
- Awan, Z.H.; Zaidi, A.; Sezgin, A. On SDoF of Multi-Receiver Wiretap Channel With Alternating CSIT. IEEE Trans. Inf. Forensics Secur. 2016, 11, 1780–1795. [Google Scholar] [CrossRef]
- Liu, T.; Viswanath, P. An Extremal Inequality Motivated by Multiterminal Information-Theoretic Problems. IEEE Trans. Inf. Theory 2007, 53, 1839–1851. [Google Scholar] [CrossRef]
- Lashgari, S.; Avestimehr, A.S.; Suh, C. A rank ratio inequality and the linear degrees of freedom of X-channel with delayed CSIT. In Proceedings of the 2013 51st Annual Allerton Conference on Communication, Control, and Computing (Allerton), Monticello, IL, USA, 2–4 Octomber 2013; pp. 218–225. [Google Scholar]
- Jafar, S.A.; Shamai, S. Degrees of Freedom Region of the MIMO X Channel. IEEE Trans. Inf. Theory 2008, 54, 151–170. [Google Scholar] [CrossRef]
- Cadambe, V.R.; Jafar, S.A.; Wang, C. Interference Alignment With Asymmetric Complex Signaling—Settling the Host-Madsen-Nosratinia Conjecture. IEEE Trans. Inf. Theory 2010, 56, 4552–4565. [Google Scholar] [CrossRef]
- Motahari, A.S.; Gharan, S.O.; Khandani, A.K. On the Degrees of Freedom of the 3-user Gaussian interference channel: The symmetric case. In Proceedings of the 2009 IEEE International Symposium on Information Theory, Seoul, South Korea, 28 June–3 July 2009; pp. 1914–1918. [Google Scholar]
- Maddah-Ali, M.A. On the degrees of freedom of the compound MISO broadcast channels with finite states. In Proceedings of the 2010 IEEE International Symposium on Information Theory, Austin, TX, USA, 13–18 June 2010; pp. 2273–2277. [Google Scholar]
- Motahari, A.S.; Oveis-Gharan, S.; Maddah-Ali, M.A.; Khandani, A.K. Real Interference Alignment: Exploiting the Potential of Single Antenna Systems. IEEE Trans. Inf. Theory 2014, 60, 4799–4810. [Google Scholar] [CrossRef]
- Sankar, L.; Kramer, G.; Mandayam, N.B. Offset Encoding for Multiple-Access Relay Channels. IEEE Trans. Inf. Theory 2007, 53, 3814–3821. [Google Scholar] [CrossRef]
- Tandon, R.; Poor, H.V. On the capacity region of multiple-access relay channels. In Proceedings of the 2011 45th Annual Conference on Information Sciences and Systems, Baltimore, MD, USA, 23–25 March 2011; pp. 1–5. [Google Scholar]
- Tian, Y.; Yener, A. The Gaussian Interference Relay Channel: Improved Achievable Rates and Sum Rate Upperbounds Using a Potent Relay. IEEE Trans. Inf. Theory 2011, 57, 2865–2879. [Google Scholar] [CrossRef]
- Sahin, O.; Simeone, O.; Erkip, E. Interference Channel With an Out-of-Band Relay. IEEE Trans. Inf. Theory 2011, 57, 2746–2764. [Google Scholar] [CrossRef]
- Chaaban, A.; Sezgin, A. On the Generalized Degrees of Freedom of the Gaussian Interference Relay Channel. IEEE Trans. Inf. Theory 2012, 58, 4432–4461. [Google Scholar] [CrossRef]
- Gherekhloo, S.; Chaaban, A.; Sezgin, A. Cooperation for Interference Management: A GDoF Perspective. IEEE Trans. Inf. Theory 2016, 62, 6986–7029. [Google Scholar] [CrossRef]
- Cadambe, V.R.; Jafar, S.A. Degrees of Freedom of Wireless Networks With Relays, Feedback, Cooperation, and Full Duplex Operation. IEEE Trans. Inf. Theory 2009, 55, 2334–2344. [Google Scholar] [CrossRef]
- Nourani, B.; Motahari, S.A.; Khandani, A.K. Relay-aided interference alignment for the quasi-static X channel. In Proceedings of the 2009 IEEE International Symposium on Information Theory, Seoul, Korea, 28 June–3 July 2009; pp. 1764–1768. [Google Scholar]
- Nourani, B.; Motahari, S.A.; Khandani, A.K. Relay-aided Interference Alignment for the quasi-static interference channel. In Proceedings of the 2010 IEEE International Symposium on Information Theory, Austin, TX, USA, 13–18 June 2010; pp. 405–409. [Google Scholar]
- Jin, D.S.; No, J.S.; Shin, D.J. Interference alignment aided by relays for the quasi-static X channel. In Proceedings of the 2011 IEEE International Symposium on Information Theory, Petersburg, Russia, 31 July–5 August 2011; pp. 2637–2641. [Google Scholar]
- Ning, H.; Ling, C.; Leung, K.K. Relay-aided interference alignment: Feasibility conditions and algorithm. In Proceedings of the 2010 IEEE International Symposium on Information Theory, Austin, TX, USA, 13–18 June 2010; pp. 390–394. [Google Scholar]
- Loeliger, H.A. Averaging bounds for lattices and linear codes. IEEE Trans. Inf. Theory 1997, 43, 1767–1773. [Google Scholar] [CrossRef]
- Zamir, R.; Shamai, S.; Erez, U. Nested linear/lattice codes for structured multiterminal binning. IEEE Trans. Inf. Theory 2002, 48, 1250–1276. [Google Scholar] [CrossRef]
- Erez, U.; Zamir, R. Achieving 1/2 log (1+SNR) on the AWGN channel with lattice encoding and decoding. IEEE Trans. Inf. Theory 2004, 50, 2293–2314. [Google Scholar] [CrossRef]
- Sridharan, S.; Jafarian, A.; Vishwanath, S.; Jafar, S.A.; Shamai, S. A layered lattice coding scheme for a class of three user Gaussian interference channels. In Proceedings of the Annual Allerton Conference on Communication, Control, and Computing, Urbana-Champaign, IL, USA, 23–26 September 2008; pp. 531–538. [Google Scholar]
- Shannon, C.E. Two-way Communication Channels. In Proceedings of the Fourth Berkeley Symposium on Mathematical Statistics and Probability; University of California Press: Berkeley, CA, USA, 1961; pp. 611–644. [Google Scholar]
- Wyner, A.D. The wire-tap channel. Bell Syst. Tech. J. 1975, 54, 1355–1387. [Google Scholar] [CrossRef]
- Davoodi, A.G.; Jafar, S.A. GDoF of the K user Symmetric MISO BC: Bridging the Gap between Finite Precision and Perfect CSIT. arXiv, 2016; arXiv:1602.02203. [Google Scholar]
- Chaaban, A.; Sezgin, A. Multi-way Communications: An Information Theoretic Perspective. Found. Trends Commun. Inf. Theory 2015, 12, 185–371. [Google Scholar] [CrossRef]
- Xiang, Z.; Mo, J.; Tao, M. Degrees of freedom of MIMO two-way X relay channel. In Proceedings of the 2012 IEEE Global Communications Conference, Anaheim, CA, USA, 3–7 December 2012; pp. 2420–2425. [Google Scholar]
- Cheng, Z.; Devroye, N. The Degrees of Freedom of the K-pair-user Full-Duplex Two-way Interference Channel with and without a MIMO Relay. arXiv, 2013; arXiv:1311.6880. [Google Scholar]
- Chaaban, A.; Sezgin, A. The capacity region of the linear shift deterministic Y-channel. In Proceedings of the 2011 IEEE International Symposium on Information Theory Proceedings (ISIT), Petersburg, Russia, 31 July–5 August 2011; pp. 2457–2461. [Google Scholar]
- Chaaban, A.; Ochs, K.; Sezgin, A. The degrees of freedom of the MIMO Y-channel. In Proceedings of the 2013 IEEE International Symposium on Information Theory, Istanbul, Turkey, 7–12 July 2013; pp. 1581–1585. [Google Scholar]
- Chaaban, A.; Sezgin, A.; Avestimehr, A.S. Approximate Sum-Capacity of the Y-Channel. IEEE Trans. Inf. Theory 2013, 59, 5723–5740. [Google Scholar] [CrossRef]
- Li, Q.; Li, H.; Wu, G.; Yi, X.; Zhou, B.; Lin, W.; Li, S. Achievable Degrees of Freedom of MIMO Y Channel With Delayed CSIT. IEEE Commun. Lett. 2014, 18, 1583–1586. [Google Scholar] [CrossRef]
- Li, Q.; Wu, G.; Li, H.; Li, S. Degrees of freedom of MIMO Y channel with three semi-blind users. In Proceedings of the Wireless and Optical Communication Conference, Chengdu, China, 21–23 May 2016; pp. 1–5. [Google Scholar]
- Tandon, R.; Piantanida, P.; Shamai, S. On multi-user MISO wiretap channels with delayed CSIT. In Proceedings of the 2014 IEEE International Symposium on Information Theory, Honolulu, HI, USA, 29 June–4 July 2014; pp. 211–215. [Google Scholar]
- Yang, S.; Kobayashi, M.; Piantanida, P.; Shamai, S. Secrecy Degrees of Freedom of MIMO Broadcast Channels with Delayed CSIT. IEEE Trans. Inf. Theory 2013, 59, 5244–5256. [Google Scholar] [CrossRef]
- Lashgari, S.; Avestimehr, A.S. Blind wiretap channel with delayed CSIT. In Proceedings of the 2014 IEEE International Symposium on Information Theory, Honolulu, HI, USA, 29 June–4 July 2014; pp. 36–40. [Google Scholar]
- Jorswieck, E.; Tomasin, S.; Sezgin, A. Broadcasting Into the Uncertainty: Authentication and Confidentiality by Physical-Layer Processing. Proc. IEEE 2015, 103, 1702–1724. [Google Scholar] [CrossRef]

© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kakar, J.; Sezgin, A. A Survey on Robust Interference Management in Wireless Networks. Entropy 2017, 19, 362. https://doi.org/10.3390/e19070362
Kakar J, Sezgin A. A Survey on Robust Interference Management in Wireless Networks. Entropy. 2017; 19(7):362. https://doi.org/10.3390/e19070362
Chicago/Turabian StyleKakar, Jaber, and Aydin Sezgin. 2017. "A Survey on Robust Interference Management in Wireless Networks" Entropy 19, no. 7: 362. https://doi.org/10.3390/e19070362



