An Efficient Advantage Distillation Scheme for Bidirectional Secret-Key Agreement
Abstract
:1. Introduction
- The proposed AD scheme provides an advantage of Alice and Bob over Eve when the channel between Alice and Bob is not less noisy than Eve’s eavesdropper channel.
- The unidirectional SKA—whose transmission rate is 0.5—can be realized by using the original TWWC as the AD scheme. However, a bidirectional SKA whose transmission rate is 1 can be realized by using the proposed AD scheme.
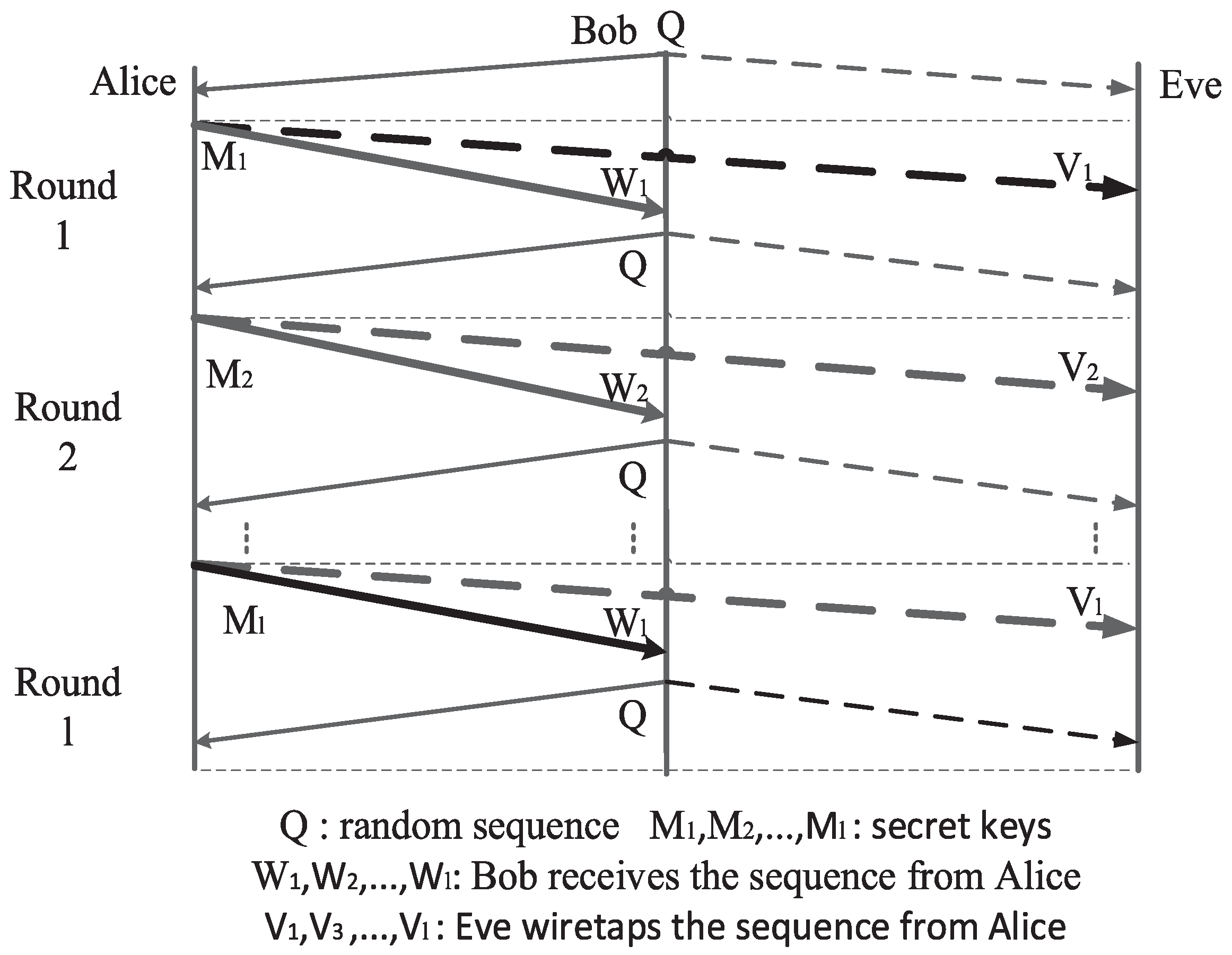
2. Original Two-Way Wiretap Channel
2.1. Transmission Scheme
2.2. Transmission Rate
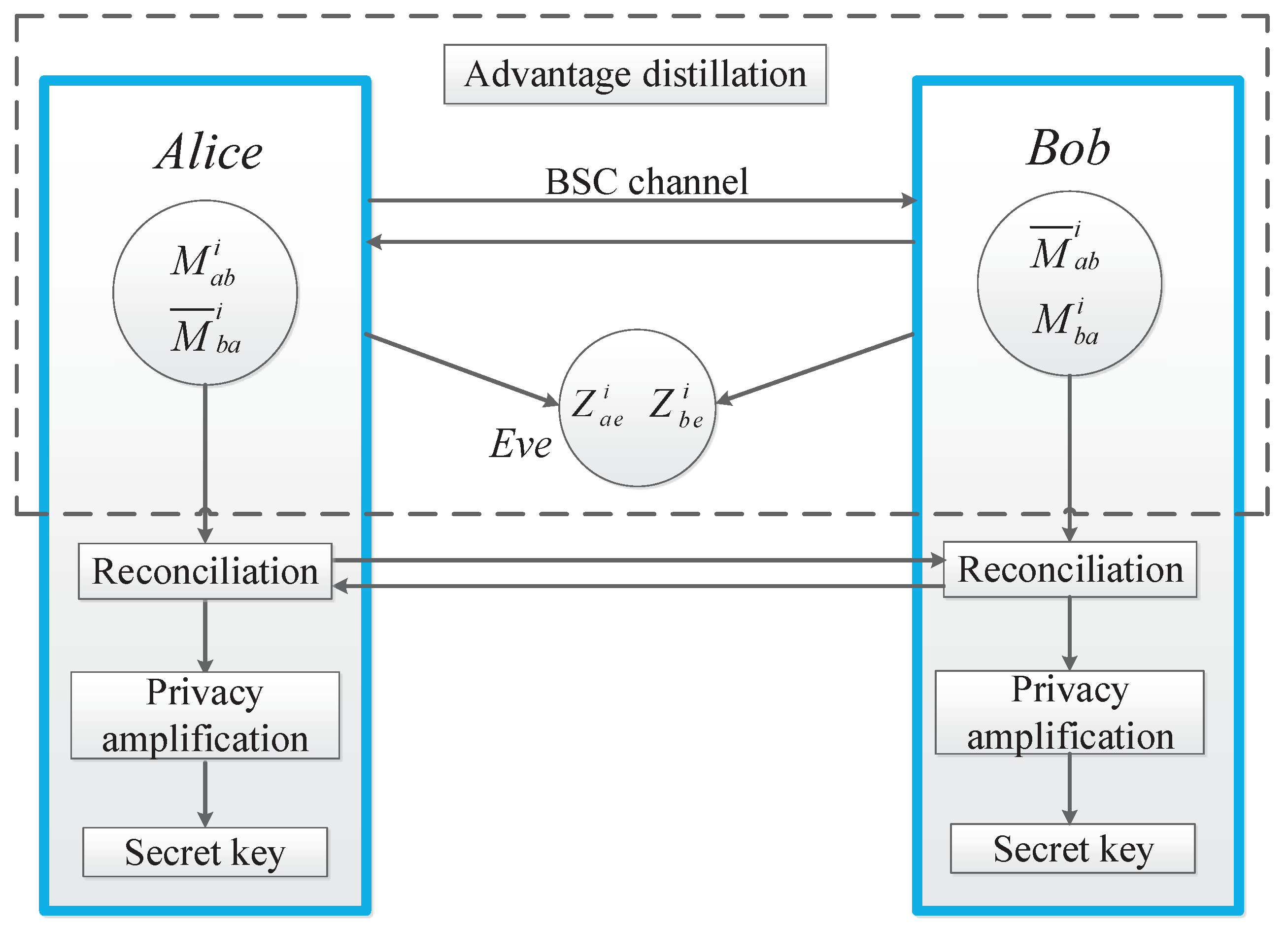
3. Bidirectional Secret-Key Agreement
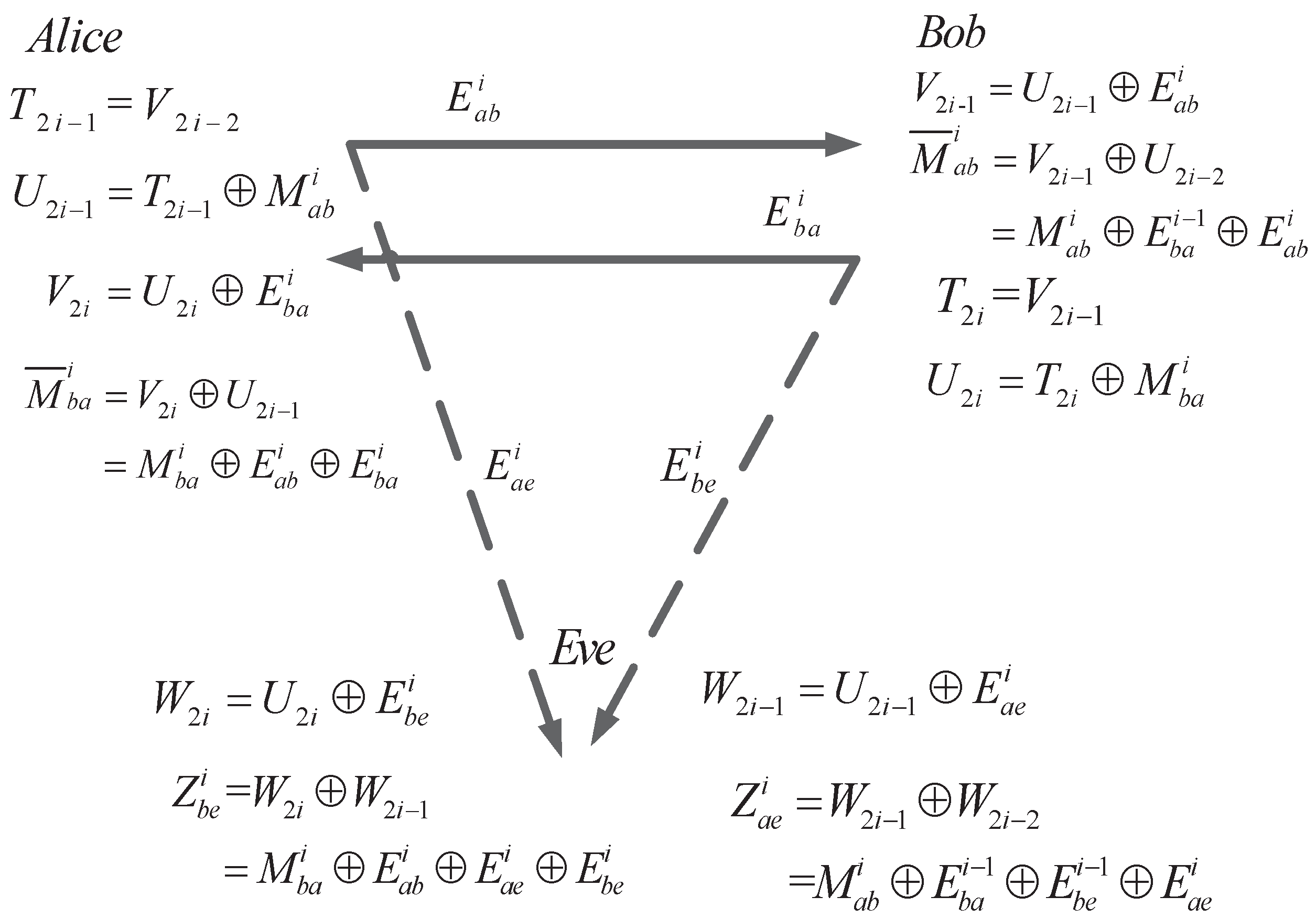
3.1. Proposed Advantage Distillation scheme
3.1.1. Preprocessing
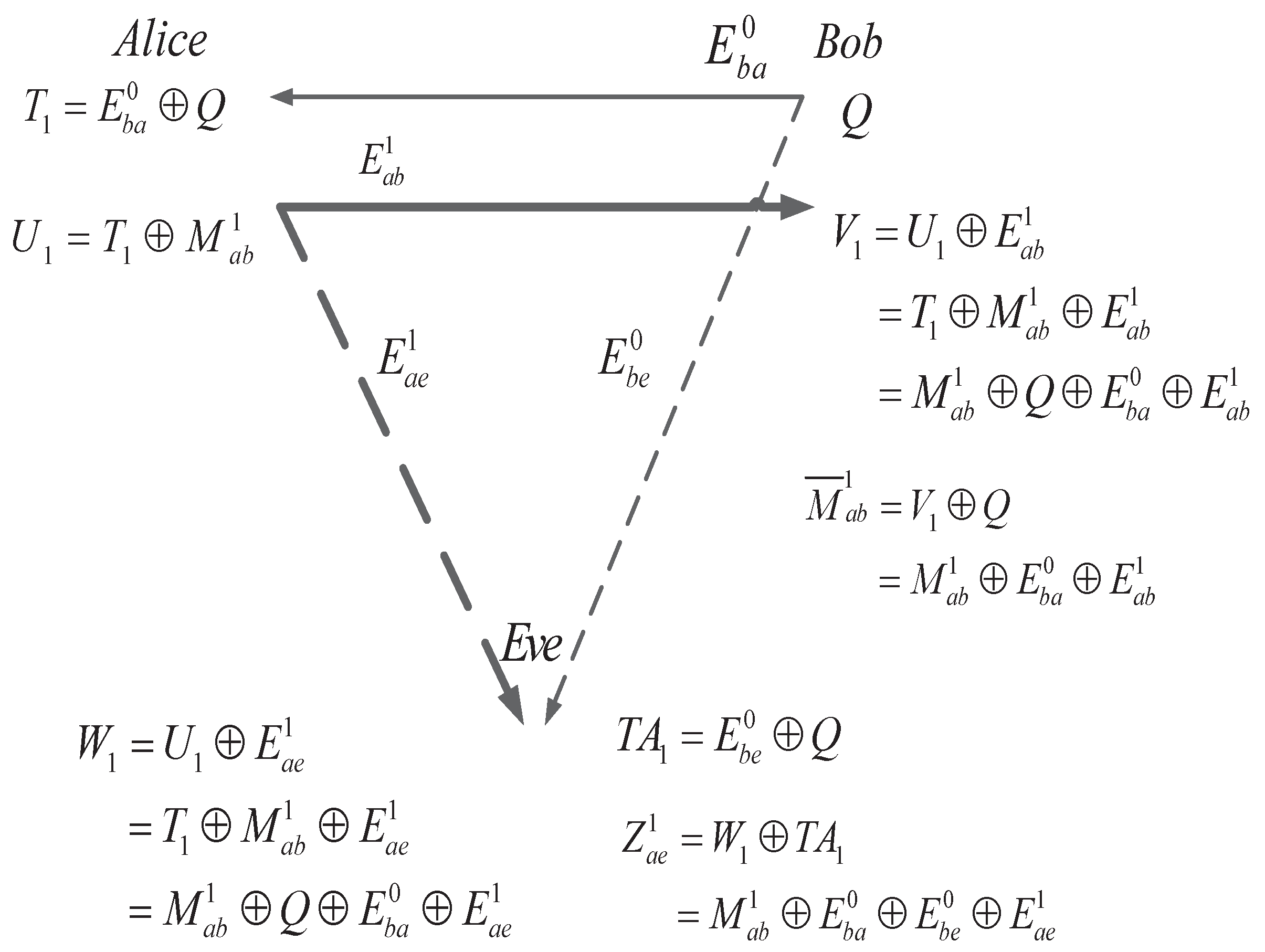
3.1.2. SKA from Alice to Bob
- (A1. 1)
- Alice uses the received sequence to calculatewhere . Alice sends over the main channel and Eve wiretaps through the eavesdropper’s channel.
- (A1. 2)
- Bob and Eve receive the noisy version of as and , respectively, as
- (A1. 3)
- Bob knows Q, so he can XOR Q to aswhere is the received raw key. Eve only knows the noisy version of Q, which is . Therefore, she can only XOR to aswhere in the eavesdropped raw key.
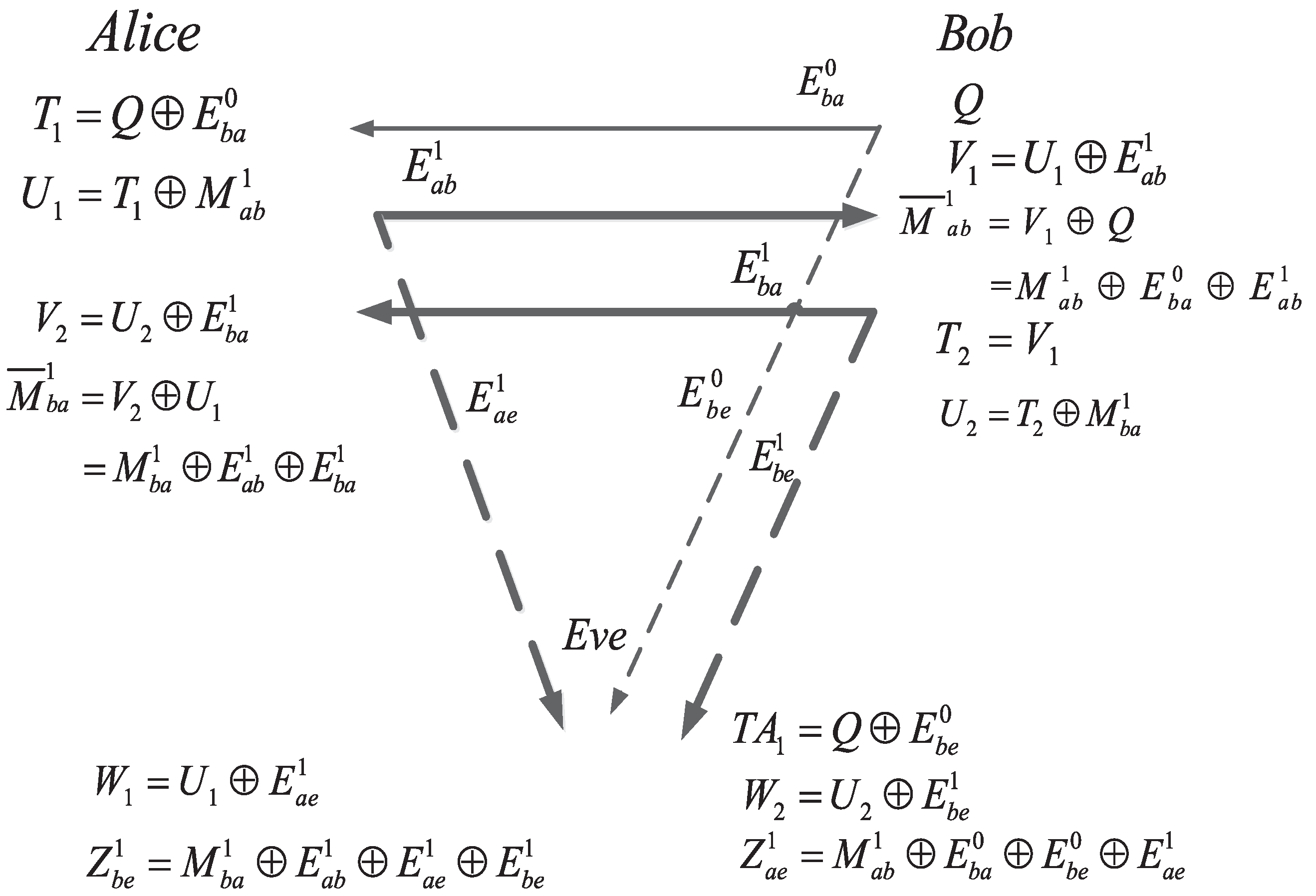
3.1.3. SKA from Bob to Alice
- (B1. 1)
- Before Bob sends the raw key to Alice, he has to makeThen, we can calculateand send to Alice through the main channel when Eve wiretaps it via the eavesdropper’s channel.
- (B1. 2)
- In this step, when Bob transmits the sequence to Alice, the noise of the two channels are and , respectively. Both Alice and Eve receive a noisy version of as and :
- (B1. 3)
- Alice has the knowledge of and Eve has the knowledge of , therefore Alice can obtain the intended raw key byand Eve can obtain the intended sequence by
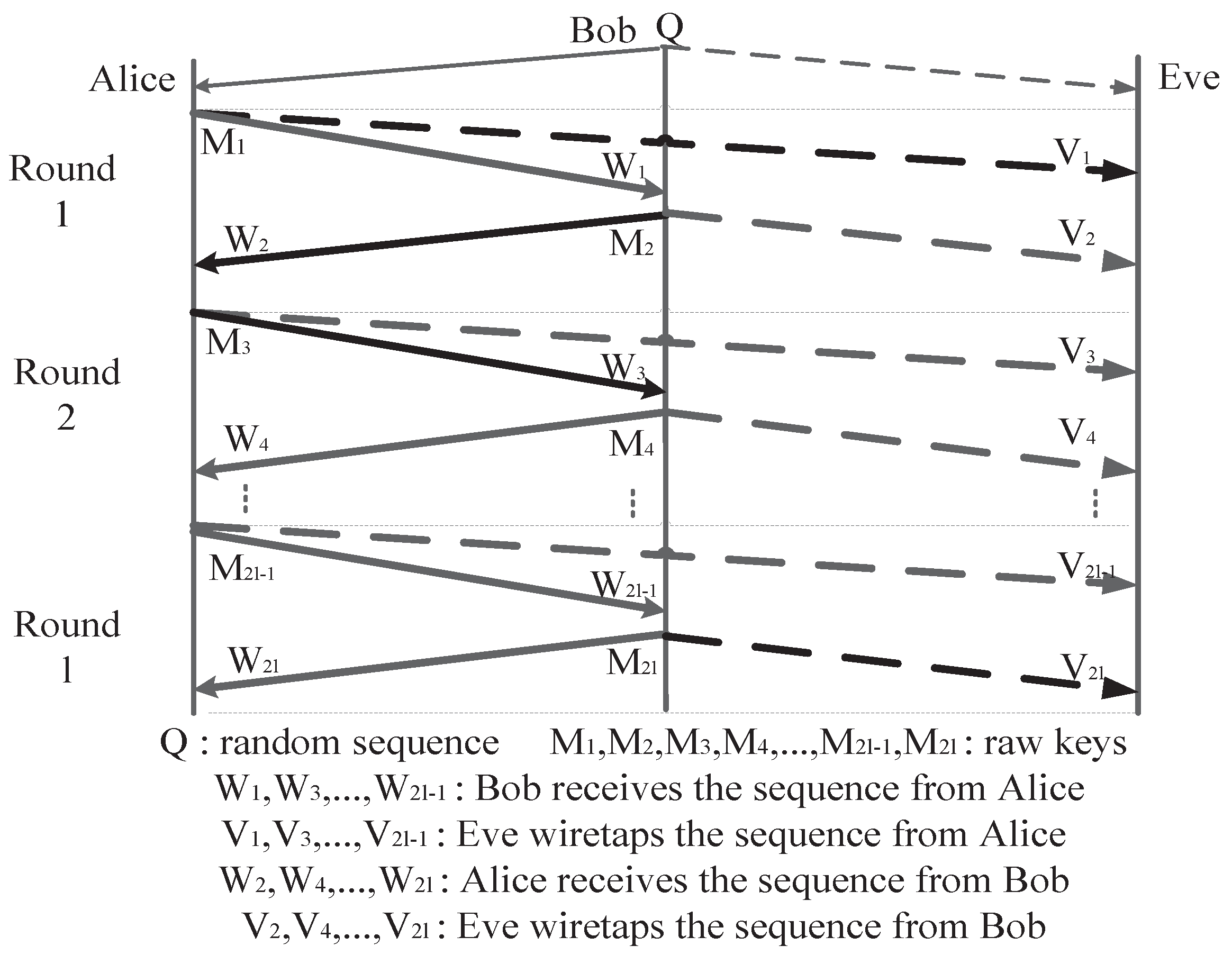
4. Multiple Rounds of Secret-Key Agreement
4.1. SKA from Alice to Bob
- (A2. 1)
- LetThen, Alice sends the raw key to Bob by
- (A2. 2)
- Bob and Eve can receive the noisy version of as
- (A2. 3)
- Bob and Eve have the knowledge of and . Therefore, they can obtain the noisy version of by XOR and to and , respectively. The result is calculated asand
4.2. SKA from Bob to Alice
- (B2. 1)
- In the i-th round, Bob has to makeThen, he sends the raw key in the noisy form, which isover the main channel. Meanwhile, Eve may wiretap it by the eavesdropper’s channel.
- (B2. 2)
- Alice can receive , consisting of the noisy vector and , and Eve can receive , which consists of the noisy vector and ,
- (B2. 3)
- Alice and Eve have the knowledge of and , respectively. Therefore, they can obtain the noisy version of by XOR and to (36) and (37). The and can be received byand
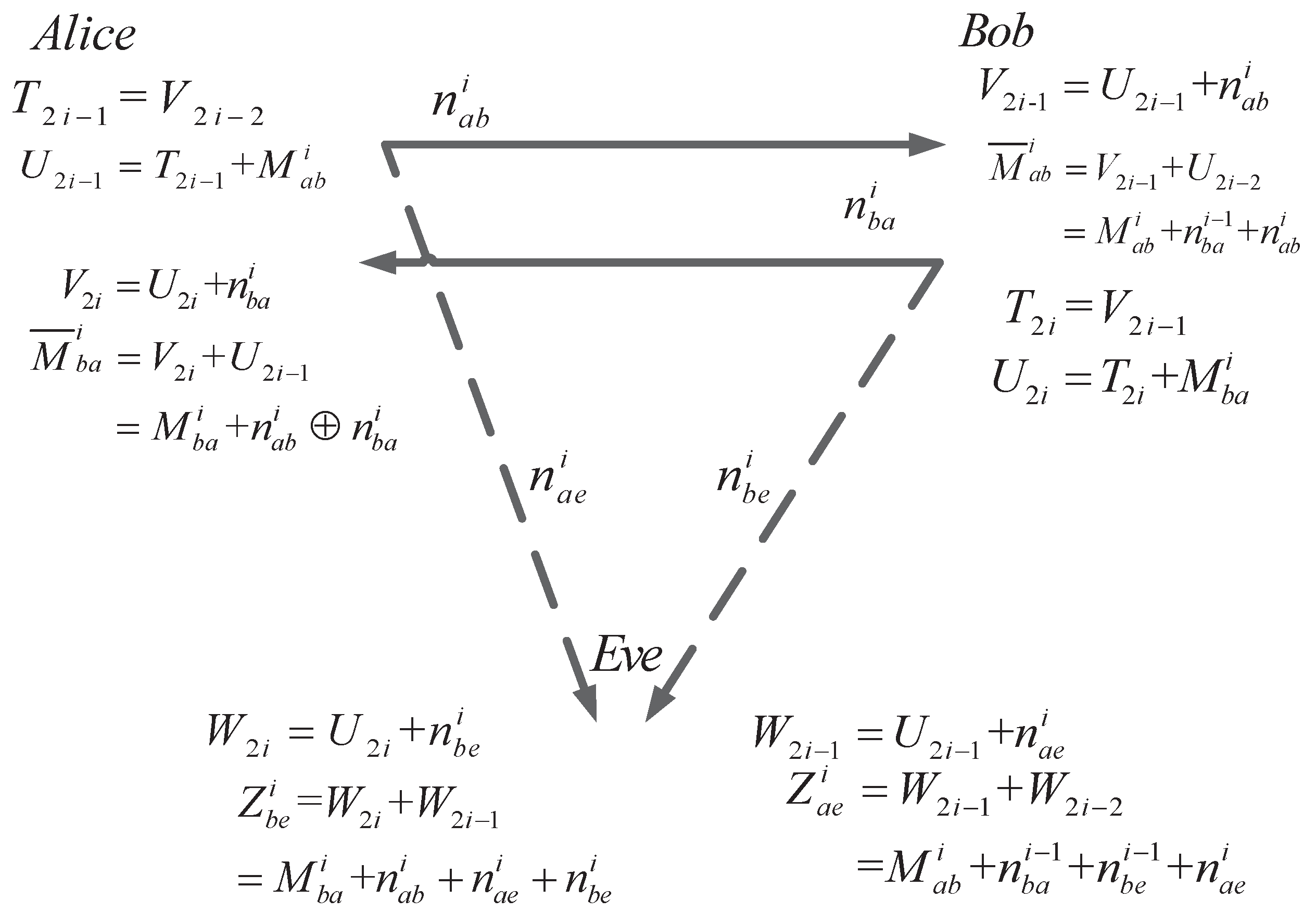
5. Bidirectional Secret-Key Agreement over AWGN Channel
5.1. SKA from Alice to Bob
- (A3. 1)
- LetThen, Alice sends the raw key to Bob bywhere (, , ⋯, )
- (A3. 2)
- Bob and Eve can receive the noisy version of aswhere the variance of AWGN over the main channel and the eavesdropper’s channel are and , respectively.
- (A3. 3)
- Bob and Eve can obtain the noisy version of by minusing and to and , respectively. The result will beandwhere the variance of AWGN or is .
5.2. SKA from Bob to Alice
- (B3. 1)
- In the ith round, Bob has to makeThen, he sends the raw key in the noisy form, which isover the main channel.
- (B3. 2)
- Alice can receive , consisting of the noisy vector and , and Eve can receive , which consists of the noisy vector and ,
- (B3. 3)
- Alice and Eve can obtain the noisy version of by minusing and to (48) and (49). and can be received byand
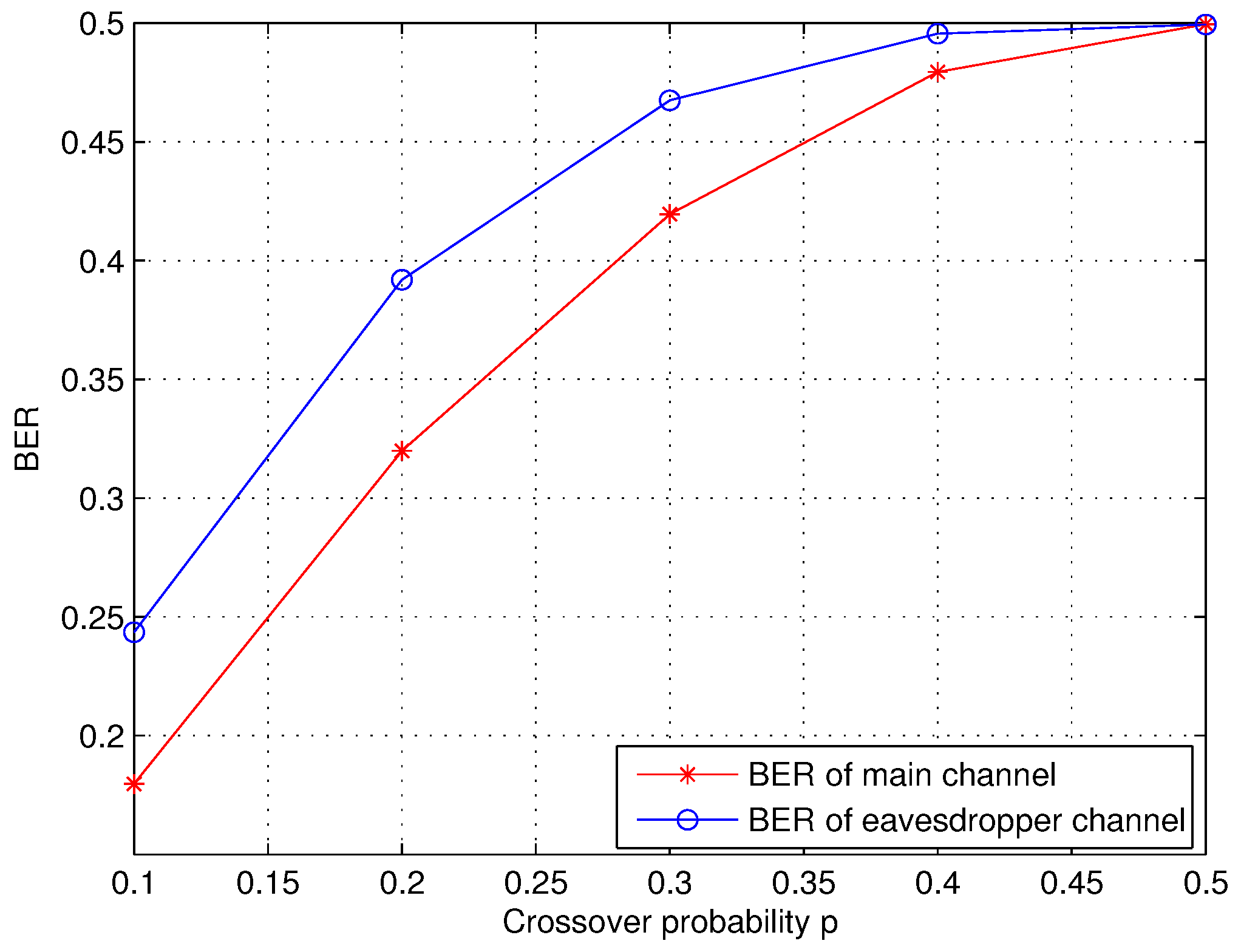
6. Performance Analysis
7. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Vernam, G.S. Cipher printing telegraph systems for secret wire and radio telegraphic communications. Trans. Am. Inst. Electr. Eng. 1926, 45, 295–301. [Google Scholar] [CrossRef]
- Shannon, C.E. Communication theory of secrecy systems. Bell Syst. Tech. J. 1949, 28, 656–715. [Google Scholar] [CrossRef]
- Tomasin, S. Secret key agreement by LLR thresholding and syndrome feedback over awgn channel. IEEE Commun. Lett. 2014, 18, 26–29. [Google Scholar] [CrossRef]
- Cao, Y.; Jiang, X.Q.; Wang, H.M.; Bai, E.; Li, J. Advantage distillation over MIMO wiretap channels based on generalized extended orthogonal space-time block codes. In Proceedings of the 2016 International Conference on Computer, Information and Telecommunication Systems (CITS), Kunming, China, 6–8 July 2016; pp. 1–5. [Google Scholar]
- Maurer, U. Secret key agreement by public discussion from common information. IEEE Trans. Inf. Theory 1993, 39, 733–742. [Google Scholar] [CrossRef]
- Csiszar, I.; Narayan, P. Common randomness and secret key generation with a helper. IEEE Trans. Inf. Theory 2000, 46, 344–366. [Google Scholar] [CrossRef]
- Csiszar, I.; Narayan, P. Secrecy capacities for multiterminal channel Models. IEEE Trans. Inf. Theory 2008, 54, 2437–2452. [Google Scholar] [CrossRef]
- Watanabe, S.; Oohama, Y. Secret key agreement from vector Gaussian sources by rate limited public communication. Proc. IEEE Int. Symp. Inf. Theory 2010, 93, 2597–2601. [Google Scholar]
- Nitinawarat, S.; Narayan, P. Secret key generation for correlated Gaussian sources. IEEE Trans. Inf. Theory 2012, 58, 3373–3391. [Google Scholar] [CrossRef]
- Ahlswede, R.; Csiszar, I. Common randomness in information theory and cryptography-Part I: Secret sharing. IEEE Trans. Inf. Theory 1993, 39, 1121–1132. [Google Scholar] [CrossRef]
- Naito, M.; Watanabe, S.; Matsumoto, R.; Uyematsu, T. Secret key agreement by soft-decision of signals in Gaussian Maurer’s model. IEICE Trans. Fundam. 2009, 92, 525–534. [Google Scholar] [CrossRef]
- Bloch, M.; Barros, J.; Rodriguez, M.R.D.; McLaughlin, S.W. Wireless information-theoretic security. IEEE Trans. Inf. Theory 2008, 54, 2515–2534. [Google Scholar] [CrossRef]
- Kobara, K.; Morozov, K.; Imai, H. On the possibility of key agreement using variable directional antenna. In Proceedings of the 1st Joint Workshop on Information Security, Seoul, Korea, 20–21 September 2006; pp. 1432–1436. [Google Scholar]
- Aono, T.; Higuchi, K.; Ohira, T.; Komiyama, B.; Sasaoka, H. Wireless secret key generation exploiting reactance-domain scalar response of multipath fading channels. IEEE Trans. Antennas Propag. 2005, 53, 3776–3784. [Google Scholar] [CrossRef]
- Ye, C.; Mathur, S.; Reznik, A.; Shah, Y.; Trappe, W.; Mandayam, N.B. Information-theoretically secret key generation for fading wireless channels. IEEE Trans. Inf. Forensics Secur. 2010, 5, 240–254. [Google Scholar]
- Isaka, M.; Kawata, S. Signal sets for secret key agreement with public discussion based on Gaussian and fading channels. IEEE Trans. Inf. Forensics Secur. 2011, 6, 523–531. [Google Scholar] [CrossRef]
- Wyner, A.D. The wire-tap channel. Bell Syst. Tech. J. 1975, 54, 1355–1387. [Google Scholar] [CrossRef]
- Wen, H.; Gong, G.; Ho, P.H. Build-in wiretap channel I with feedback and LDPC codes. J. Commun. Netw. 2009, 11, 538–643. [Google Scholar] [CrossRef]
- Bloch, M.; Barros, J. Physical-Layer Security: From Information Theory to Security Engineering; Cambridge University Press: Cambridge, UK, 2011. [Google Scholar]
- Pacher, C.; Grabenweger, P.; Martinez-Mateo, J.; Martin, V. An information reconciliation protocol for secret-key agreement with small leakage. In Proceedings of the 2015 IEEE International Symposium on Information Theory (ISIT), Hong Kong, China, 14–19 June 2015; pp. 730–734. [Google Scholar]
| Symbols | Meaning |
|---|---|
| raw keys | |
| Q | random sequence |
| noise vector from Bob to Alice over BSC channel | |
| noise vector from Bob to Eve over BSC channel | |
| noise vector from Alice to Bob over BSC channel | |
| noise vector from Bob to Alice over BSC channel | |
| noise vector from Alice to Eve over BSC channel | |
| noise vector from Bob to Eve over BSC channel | |
| noisy version of Q obtained by Alice | |
| noisy version of Q obtained by Eve | |
| raw keys covered by | |
| noisy version of obtained by Bob or Alice | |
| equals to | |
| noisy version of obtained by Eve | |
| noisy version of raw keys obtained by Bob or Alice | |
| noisy version of raw keys obtained by Eve | |
| number of raw keys M | |
| number of random sequence Q | |
| cross over probability between Alice and Bob | |
| cross over probability between legitimate users and Eve | |
| noise vector from Alice to Bob over AWGN channel | |
| noise vector from Bob to Alice over AWGN channel | |
| noise vector from Alice to Eve over AWGN channel | |
| noise vector from Bob to Eve over AWGN channel | |
| capacity of the main channel | |
| capacity of the eavesdropper’s channel | |
| secret-key capacity |
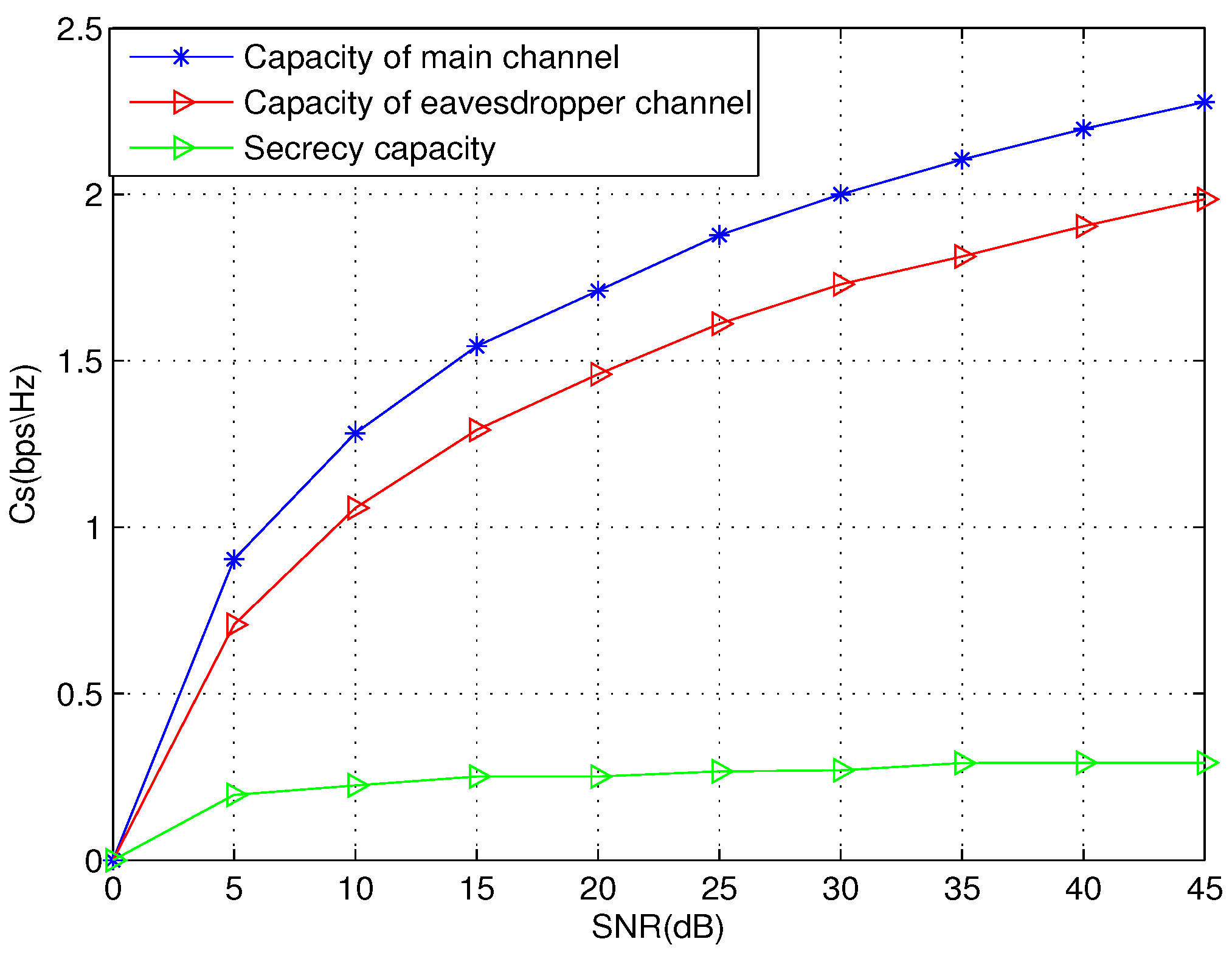
| 0.1 | 0.2 | 0.3 | 0.4 | 0.5 | |
|---|---|---|---|---|---|
| Main channel | 0.093 | 0.165 | 0.216 | 0.247 | 0.258 |
| Eavesdropper’s channel | 0.244 | 0.392 | 0.468 | 0.496 | 0.499 |
| 0.01 | 0.02 | 0.03 | 0.04 | 0.05 | |
|---|---|---|---|---|---|
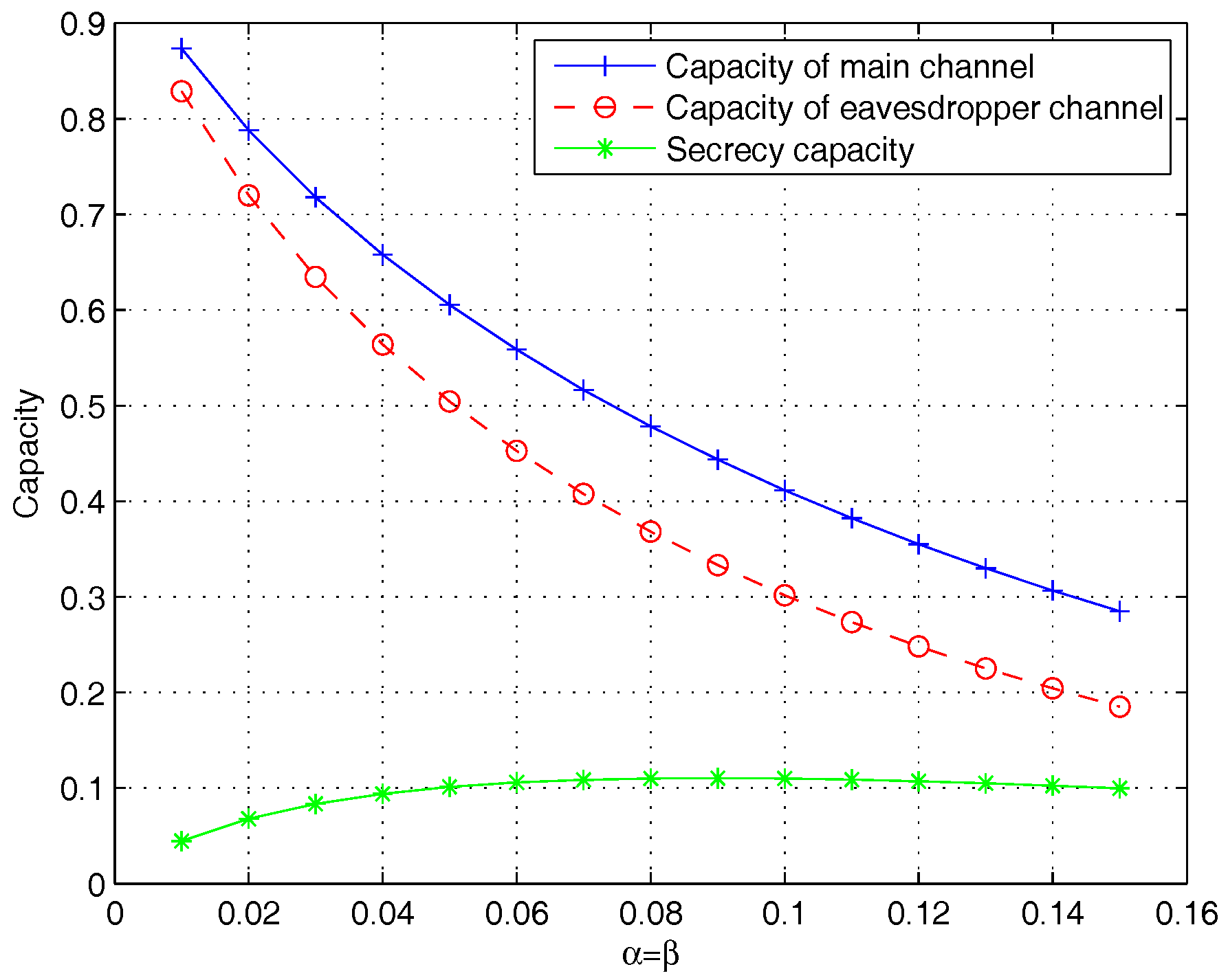
| 0.87 | 0.79 | 0.72 | 0.66 | 0.61 | |
| 0.83 | 0.72 | 0.63 | 0.56 | 0.50 | |
| 0.04 | 0.07 | 0.09 | 0.10 | 0.11 |
| Scheme | Transmission Rate | Number of XOR Operations |
|---|---|---|
| Unidirectional TWWC scheme | 0.5 | |
| Bidirectional TWWC scheme | 1 |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Feng, Y.; Jiang, X.-Q.; Hou, J.; Wang, H.-M.; Yang, Y. An Efficient Advantage Distillation Scheme for Bidirectional Secret-Key Agreement. Entropy 2017, 19, 505. https://doi.org/10.3390/e19090505
Feng Y, Jiang X-Q, Hou J, Wang H-M, Yang Y. An Efficient Advantage Distillation Scheme for Bidirectional Secret-Key Agreement. Entropy. 2017; 19(9):505. https://doi.org/10.3390/e19090505
Chicago/Turabian StyleFeng, Yan, Xue-Qin Jiang, Jia Hou, Hui-Ming Wang, and Yi Yang. 2017. "An Efficient Advantage Distillation Scheme for Bidirectional Secret-Key Agreement" Entropy 19, no. 9: 505. https://doi.org/10.3390/e19090505




