Intelligent Sensors Security
Abstract
:1. Introduction
2. Intelligent Sensors and Their Basic Security Issues
- airplane health monitoring systems,
- safety-critical assets distribution systems,
- motion sensors of digital tachographs,
- SCADA-related products,
- specialized firewalls used in control and automation systems, co-operating with sensor networks.
3. Common Criteria Methodology—Primer
- IT security development process, identified with the security target (ST) work-out, specifying the TOE security functions;
- TOE development process with the use of the assumed technology (elaboration of the TOE evaluation evidences, expressing the implementation of these functions on the EAL declared for the TOE);
- IT security evaluation and certification process (not discussed here), providing independent analyses, verifications if the claimed EAL is met.
- Work-out of the “ST introduction”, containing different identifiers, informal TOE overview and TOE description;
- Conformance claims with the Common Criteria version, protection profiles and packages, including EAL;
- Security problem definition (SPD); SPD specified threats, OSPs (organizational security policies) and assumptions for the TOE and its environment;
- Solution of this problem by specifying security objectives (SO)—for the TOE and its environment;
- Extended components definition, when needed (i.e., when the developer should define his/her own component due to its lack in the standard);
- Work-out of the security functional requirements (SFRs) specification on the security objectives basis, and the set of security assurance requirements (SARs) which are derived mainly from the declared EAL;
- Creating the TOE summary specification, including the TOE security functions derived from the SFRs; they are implemented in the TOE on the claimed EAL during the TOE development process.
- TOE architecture, its functional specification, design, security policy, implementation—expressed by the ADV (Development) assurance class components (please note that according to [1] each assurance class name begins with the letter “A”, two other letters concern the issues described by the class),
- configuration management, product delivery, development process security, used tools—represented by the ALC (Life-cycle support) class components,
- tests specification, test depth and coverage – influenced by the ATE (Tests) class components,
- product manuals and procedures, worked out according to the AGD (Guidance documents) class components,
- vulnerability assessment according to the AVA (Vulnerability assessment) assurance class.
4. Intelligent Sensors Model for IT Security Development Process
- microcontroller, equipped with a specialized operating system, communication and application software, different devices, such as memories, including non-volatile memories, interfaces, timers, counters, sometimes other coprocessors (e.g., crypto-processors, network processors and other specialized processors), interfaces to external memories, and other devices (I2C, SPI),
- low-power transducers (varied sensing/controlling devices),
- communication facilities, including low-power wireless facilities or traditional/industrial network interfaces (wired, optical facilities),
- power source (battery, solar, external sources).
5. Common Criteria IT Security Development Process—Intelligent Sensor Specific Issues
- models of data structures and processes of IT security development stages, including: security problem definition, security objectives elaboration, security requirements, and security functions workout;
- models of the specification means used for these IT security development stages, including CC components and the introduced semiformal enhanced generics.
- sharing common understanding of the structure of information among people or software, i.e., mainly the structure of the components, generics and evidences;
- reusing the domain knowledge, i.e., using the same specification means in different projects and deriving their new variants from the previously defined ones;
- making explicit assumptions for a domain; it concerns predefined parameters and predefined mapping relations between specification items;
- separating the domain knowledge, expressed by the specification means as a whole, from the operational knowledge allowing to use these means to compose the ST of the given IT products or systems;
- providing the domain knowledge analyses concerning: variants, semantics, risk, relationships of the developed specification means, etc.
6. Evaluation Issues
- extensive validation on near-real projects like the above mentioned motion sensor; validation on intelligent sensors detecting methane is in progress and will be summarized in a separate paper;
- partial validation focused on the selected issues; it will be shown on the example below.
6.1. Validation example
6.1.1. Informal IT product description included in the “ST introduction”
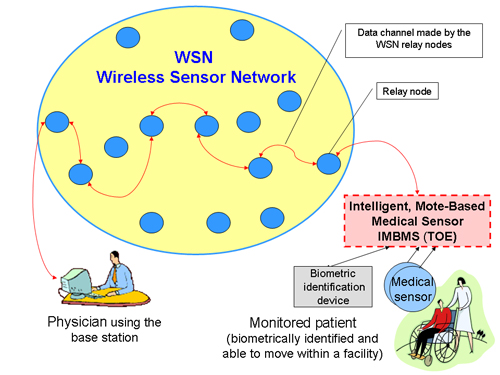
“The IMBMS system (Figure 2) is designed for distance, long-term monitoring of patients with chronic diseases. Each patient, biometrically identified, is provided with the mote with medical sensors watching her/his vital signs. Patients can move in the range of medical or home facilities. Motes are communicating with the distinguished base station through relay nodes of the wireless sensor network (WSN). Using the base station, the physician (a legitimate, authenticated user) is able to send a data query related to the given patient to the mote, which activates the appropriate medical sensors. The data channel is formed by a set of relay nodes. Many motes and base stations may exist within the system.”
“The TOE (target of evaluation) is a Crossbow MICA2 based mote (Figure 3). The TOE consists of the Atmega128L microcontroller with the TinyOS operating system, Chipcon’s CC1000 RF transceiver with antenna, “Flash Data Logger” (4-Mbit serial flash memory for storing data, measurements, user-defined information, and used for over-the-air reprogramming provided by TinyOS), power source (2 AA-type batteries), 3 LEDs displaying status, and the expansion connector. The TOE also includes the application and communication software running under TinyOS. The TOE boundary is marked with dashed lines. The medical sensors, measuring physical values related to vital signs, and the biometric identification device, like a fingerprint reader, all connected to the expansion connector, are not the parts of the TOE”.
6.1.2. Protected assets
- DTO.SensorData. Data measured, stored, processed, or transmitted by the intelligent sensor and data related to the network services.
- Refinement: Medical data of the monitored patient.
- DTO.SensorService. Services provided by a sensor: measuring, sampling, processing, transferring data, and displaying its status.
- DTO.BioData. Biometric or physiological data used for the identification of a person.
- DTO.NodePowerRes. Energy supplying a sensor node.
- DTO.NodeProcesRes. Node processing ability.
- DTO.NodeTransmRes. Node data transmission ability.
- DAP.DesignData. Sensitive project data and documentation.
- Refinement: Logical, physical design data of the TOE hardware, software specifications, code and other related documentation, development aids, test data, user data related documentation, material for software development and manufacturing process.
- DIT.BaseStation. A distinguished node of a wireless sensor network (WSN) used to control the network or as a gateway intermediating between WSN and other network.
6.1.3. Identification of active entities—legal users and intruders
- SAU.IntellSensorUser(1). Authorized entity (user, process) who/which directly or indirectly uses the intelligent sensor.
- Refinement: The monitored patient.
- SAU.IntellSensorUser(2). Authorized entity (user, process) who/which directly or indirectly uses the intelligent sensor.
- Refinement: The medical personnel (a physician remotely monitoring patients, a nurse visiting patients) and household members.
- SAU.SensorNetAdmin. Authorized administrator of the sensor network and applications.
- SAU.Developer. Personnel involved in the design phase (hardware/software designer, programmer, test engineer).
- SAU.ManufPers. Personnel involved in the manufacturing processes (components manufacturing, assembly, security data insertion, storage, distribution, repair).
- SAU.ServicePers. Personnel involved in sensor or sensors system maintenance (storage, installation, inspection, calibration, repair).
- SNA.HighPotIntruder. Attacker having high level skills, enough resources and deep motivation to perform a deliberate attack.
- SNA.IndustIntrud. Industry spy or intruder trying to get or counterfeit the design data.
6.1.4. Identification of threats and security objectives which counter them
- TDA.NodeCompromise. Attacker [Sparam <= SNA.HighPotIntrud] can: eavesdrop the traffic, inject packets or replay older messages because wireless communication generally is not secure. After the node compromising, all information it holds [Dparam <= DTO.SensorData, DTO.BioData, DIT.BaseStation] is known to the attacker and/or node operation or communication is broken [Dparam <= DTO.SensorService].
- TDA.SensDataMdfy. Intruder [Sparam <= SNA.HighPotIntruder] modifies sensor data (falsifies them) [Dparam <= DTO.SensorData, DTO.BioData].
- OACC.Access. The sensor must control access of connected entities.
- OIDA.Authentication. The sensor must authenticate connected entities.
- OADT.Audit. The sensor must audit attempts to undermine its security and should trace them to the associated entities.
- OINT.Processing The sensor must ensure that the processing of input to derive output data [Dparam <= DTO.SensorData] is accurate.
- TDA.Tamper. Intruder [Sparam <= SNA.HighPotIntrud, SAU.IntellSensorUser(1)] physically/logically compromises a sensor node to get assets [Dparam <= DTO.SensorData, DTO.BioData] or disrupt the node operation [Dparam <= DTO.SensorService].
- OINT.TamperResistance. The TOE guarantees its own physical/logical integrity. The means of detecting physical tampering must be provided (e.g., seals, tampering detection, special reinforced cases, intrinsically safe solutions).
- OAVB.Reliability. The sensor must provide reliable service. Applying fault tolerance methods and techniques.
- OSMN.RegularInpections. The sensor must be periodically inspected and calibrated (if necessary).
- OEPH.PatientSecurity. The monitored patient is within the access-restricted area and the medical personnel or household members take care of her/him.
- TDA.LimitResour. Exploiting vulnerability related to the node limited resources [Dparam <= DTO.NodePowerRes, DTO.NodeProcesRes, DTO.NodeTransmRes], an intruder [Sparam <= SNA.HighPotIntruder] causes misbehaviour, disconnection or faults within the system.
- OAVB.ResUnderControl. Control resource [Dparam <= DTO.NodePowerRes, DTO.NodeProcesRes, DTO.NodeTransmRes].
- OEPH.PatientSecurity. The monitored patient is within the access-restricted area and the medical personnel or household members take care of her/him.
- TIT.UncontrolledArea. Due to uncontrolled pervasiveness of a wireless sensors network, the node works in an uncontrolled network area accessible to potential intruders [Sparam <= SNA.HighPotIntruder].
- OEIT.SecPerimVsTrRangeCtrl. The physically controlled security perimeter, where nodes are placed, should be defined with respect to the range of wireless transmission.
- TIT.SecDataAdmin. Insufficient administration of the network and security related data [Dparam] of the sensor network by [Sparam <= SAU.SensorNetAdmin].
- OSMN.SecDatManag. Periodic changes to security data [Dparam] managed by [Sparam <= SAU.SensorNetAdmin].
- OSMN.NetAdmin. Network administration and security policy procedures implementation.
- TPH.Design. Users or intruders [Sparam <= SAU.Developer, SAU.ManufPers, SAU.ServicePers, SNA.IndustIntrud] could try to gain illicit knowledge of the design [Dparam <= DAP.DesignData] either from the manufacturer's materials (through theft, bribery, illegal access to IT resources) or from reverse engineering.
- TPH.Test. The use of non-invalidated test modes by [Sparam <= SAU.Developer, SAU.ManufPers, SAU.ServicePers] or not detected backdoors could compromise the sensor security.
- OSMN.SiteProcess. Site processes encompassing the development-, manufacturing- and maintenance activities in the life cycle are properly defined, implemented and managed.
6.1.5. Organizational security policies (OSPs) and security objectives which enforce them
- PAVB.SensorSysMain. The data [Dparam <= DTO.SensorData] transmitted by the sensor must be available to the supervising- or data sampling unit [Dparam <= DIT.BaseStation] so as to allow the unit to determine fully and accurately the sampled data.
- OAVB.SensorSysMain. The data [Dparam <= DTO.SensorData], sampled by the sensor-based acquisition/monitoring system [Dparam <= DIT.BaseStation] checked by control authorities, must be available and reflect fully and accurately the system objectives.
- PSMN.HIPAA. Ensure the compliance with the Health Insurance Portability and Accountability Act.
- OEPH.HIPAA. The medical system should comply with the HIPAA Act.
6.1.6. Assumptions and TOE environment security objectives which uphold them
- APR.Development. Sensor developers [Sparam <= SAU.Developer] must ensure that the assignment of responsibilities during the development is done in a manner which maintains IT security.
- APR.Manufacturing. Sensor manufacturers [Sparam <= SAU.ManufPers] must ensure that the assignment of responsibilities during manufacturing is done in a manner which maintains IT security, and that during the manufacturing process the sensor is protected against physical attacks which might compromise IT security. All testing facilities for the manufacturing phase (test points, commands) should be removed or disabled before delivery.
- APR.Delivery. Sensor manufacturers, fitters, workshops [Sparam <= SAU.ManufPers, SAU.ServicePers] must ensure that handling of the sensor is done in a manner which maintains IT security.
- APR.ApprovedWorkshops. Installation, calibration and repair of the sensor and its monitoring unit must be carried out by trusted and approved fitters or workshops by the authorized [Sparam <= SAU.ServicePers].
- OSMN.SiteProcess. Site processes encompassing the development-, manufacturing- and maintenance activities in the life cycle are properly defined, implemented and managed.
- APR.TrustAdmin. One or more authorized administrators [Sparm <= SAU.SensorNetAdmin] are assigned who are competent to manage the TOE and the security of the information it contains, and who can be trusted not to deliberately abuse their privileges so as to undermine security.
- OSMN.SecManAdmin. The TOE will provide facilities to enable an authorized administrator [Sparam <= SAU.SensorNetAdmin] to effectively manage the TOE and its security functions, and will ensure that only authorized administrators are able to access such functionality.
- APR.IntendedUse. The TOE will be used to perform a task or function for which it was designed by [Sparam <= SAU.IntellSensorUser(2)].
- OSMN.UserAwarn. User awareness, proper operation regulations and procedures.
6.2. Summary of the example
- OACC.Access, OIDA.Authentication, OADT.Audit, OINT.Processing, OINT.TamperResistance, OAVB.Reliability, OAVB.ResUnderControl.
- OSMN.RegularInpections, OEPH.PatientSecurity, OEIT.SecPerimVsTrRangeCtrl, OSMN.SecDatManag, OSMN.NetAdmin, OSMN.SiteProcess, OAVB.SensorSysMain, OEPH.HIPAA, OSMN.SecManAdmin, OSMN.UserAwarn.
- DTO.BioData, DTO.SensorService, OEPH.PatientSecurity, PSMN.HIPAA, OEPH. HIPAA.
7. Conclusions
- Common Criteria related security design patterns, called here enhanced generics, to define elementary security problems (i.e., threats, security organizational policies, assumptions) and elementary solutions of these problems (i.e., security objectives), with respect to the intelligent sensors needs and the life-cycle model,
- knowledge how to apply these patterns to elaborate the Common Criteria complaint security model, called security target.
- sensor operating within a wireless network,
- sensor supervised by a monitoring unit and connected through a copper cable.
References and Notes
- Common Criteria for IT Security Evaluation; v3.1; Common Criteria member organizations, 2009; part 1–3.
- Schumacher, M.; Fernandez-Buglioni, E.; Hybertson, D.; Buschmann, F.; Sommerlad, P. Security Patterns: Integrating Security and Systems Engineering; John Wiley and Sons: Chichester, UK, 2006. [Google Scholar]
- Hill, J.L. System Architecture for Wireless Sensor Networks, Ph.D. Thesis;. University of California, Berkeley, CA, USA, 2003. Available online: http://www.jlhlabs.com/jhill_cs/jhill_thesis.pdf (accessed on 1 November 2009).
- Hebden, P. Self-Organization of Wireless Sensor Networks for Data-Centric Routing Using Bloom Filters, Ph.D. Thesis,. The University of Melbourne, Melbourne, Australia, 2009. Available online: http://www.cs.mu.oz.au/~phebden/pubs/thesis.pdf (accessed on 1 November 2009).
- Moya, J.M.; Vallejo, J.C.; Fraga, D.; Araujo, A.; Villanueva, D.; de Goyeneche, J.M. Using Reputation Systems and Non-Deterministic Routing to Secure Wireless Sensor Networks. Sensors 2009, 9, 3958–3980. [Google Scholar]
- Ertaul, L.; Ganta, M. Security in Wireless Sensor networks—A Study. Proceedings of the 2009 International Conference on Wireless Networks, Las Vegas, NV, USA, July 13–16, 2009; 1, pp. 33–39.
- Abdullah, M.J.; Hua, G.W.; Alsharabi, N. A Novel Re-Keying Function Protocol (NRFP) for Wireless Sensor Network Security. Sensors 2008, 8, 7866–7881. [Google Scholar]
- Ertaul, L.; Mullapudi, S. The Security Problems of Vehicular Ad Hoc Networks (VANETs) and Proposed Solutions in Securing Their Operations. Proceedings of the 2009 International Conference on Wireless Networks, Las Vegas, NV, USA, July 13–16, 2009; 1, pp. 33–39.
- Szczodrak, M.; Kim, J. 4G and MANET, Wireless Network of Future Battlefield. Proceedings of the 2007 International Conference on Security and Management, Las Vegas, NV, USA, June 25–28, 2007; pp. 282–288.
- Malasri, K.; Wang, L. Design and Implementation of a Secure Wireless Mote-Based Medical Sensor Network. Sensors 2009, 9, 6273–6297. [Google Scholar]
- Eagles, K.; Markantonakis, K.; Mayes, K. A Comparative Analysis of Common Threats, Vulnerabilities, Attacks and Countermeasures Within Smart Card and Wireless Sensor Network Node Technologies. In Information Security Theory and Practices; Sauveron, D., Markantonakis, K., Bilas, A., Quisquater, J.J., Eds.; Springer: Berlin/Heidelberg, Germany, 2007; Volume 4462, pp. 161–174. [Google Scholar]
- Dräger Polytron 7000. Available online: http://www.draeger.com (accessed on 1 November 2009).
- Sampigethaya, K.; Li, M.; Poovendran, R.; Robinson, R.; Bushnell, L.; Lintelman, S. Secure Wireless Collection and Distribution of Commercial Airplane Health Data. Proceedings of the 26th Digital Avionics Systems Conference, Dallas, TX, USA, October 21–25, 2007; Available online: http://www.ee.washington.edu/research/nsl/papers/DASC-07.pdf (accessed on 1 November 2009).
- Robinson, R.; Li, M.; Lintelman, S.; Sampigethaya, K.; Poovendran, R.; von Oheimb, D.; Bußer, J.W.; Cuellar, J. Electronic Distribution of Airplane Software and the Impact of Information Security on Airplane Safety. Proceedings of the 26th International Conference on Computer Safety, Reliability, and Security, Nuremberg, Germany, September 18–21, 2007; Saglietti, F., Oster, R., Eds.; Springer: Berlin/Heidelberg, Germany, 2009. LNCS 4680/2009,. pp. 28–39. [Google Scholar]
- Sampigethaya, K.; Poovendran, R.; Bushnell, L. Secure Operation, Control, and Maintenance of Future E-Enabled Airplanes. Proc. IEEE 2008, 96, 1992–2007. [Google Scholar]
- Lintelman, S.; Sampigethaya, K.; Li, M.; Poovendran, R.; Robinson, R. High Assurance Aerospace CPS & Implications for the Automotive Industry. Available online: http://www.ee.washington.edu/research/nsl/papers/HCSS-08.pdf (accessed on 5 November 2009).
- Commission Regulation (EC) No.1360/2002 on Recording Equipment in Road Transport. Annex 1B Requirements for Construction, Testing, Installation and Inspection. Off. J. Eur. Commun 2002, L207, 204–252.
- ISO/IEC 16844-3 Road Vehicles—Tachograph Systems, Part 3: Motion Sensor Interface; ISO: Geneva, Switzerland, 2004.
- Furgel, I.; Lemke, K. A Review of the Digital Tachograph System. In Embedded Security in Cars; Springer: Berlin/Heidelberg, Germany, 2006; pp. 69–94. [Google Scholar]
- Security Target IS2000 Smartach SRES, P206412; Actia: Toulouse, France, 2005.
- Bialas, A. Security-Related Design Patterns for Intelligent Sensors Requiring Measurable Assurance. Electr. Rev (Przegląd Elektrotechniczny) 2009, 85, 92–99. [Google Scholar]
- Bialas, A. Ontological Approach to the Motion Sensor Security Development. Electr. Rev (Przegląd Elektrotechniczny) 2009, 85, 36–44. [Google Scholar]
- Veryha, Y. SCADA Systems for Virtual Utilities. Electr. Today 2005, 17, 24–30. [Google Scholar]
- Common Criteria Portal Home Page. http://www.commoncriteriaportal.org/ (accessed on 5 December 2009).
- Hill, J.; Szewczyk, R.; Woo, A.; Hollar, S.; Culler, D.; Pister, K. System Architecture Directions for Networked Sensors. ACM SIGPLAN Notices. 2000, 35, pp. 93–104. Available online: http://webs.cs.berkeley.edu/tos/papers/tos.pdf (accessed on 15 November 2009).
- Crossbow Technology. MPR-MIB Users Manual. Revision A,. June 2007. Available online: http://www.xbow.com/Support/Support_pdf_files/MPR-MIB_Series_Users_Manual.pdf (accessed on 15 November, 2009).
- Atmel© ATMega128. Available online: http://www.atmel.com/dyn/resources/prod_documents/doc2467.pdf11 (accessed on 16 November 2009).
- ZigBee Alliance Home Page. http://www.zigbee.org/ (accessed on 16 November 2009).
- ZigBee Chips. Available online: http://www.ember.com/products_zigbee_chips.html (accessed on 17 November 2009).
- Lymberopoulos, D.; Savvides, A. A Wireless Sensor Node Architecture for Exploring Distributed Sensor Network Applications. Draft—Work in Progress. Available online: http://www.eng.yale.edu/enalab/publications/xyz_paper.pdf (accessed on 21 January 2010).
- Echelon Corporation. Series 5000 Chip Data Book. 2009. Available online: http://www.echelon.com (accessed on 18 November 2009).
- Bialas, A. Semiformal Common Criteria Compliant IT Security Development Framework. Stud. Inf 2008, 29. No. 2B(77);. Available online: http://www.znsi.aei.polsl.pl/ (accessed on 15 September 2009). [Google Scholar]
- Bialas, A. Semiformal Framework for ICT Security Development. Proceedings of the 8th International Common Criteria Conference, Rome, Italy, September 25–27, 2007; Available online: http://www.8iccc.com/index.php (accessed September 2009).
- Bialas, A. Semiformal Approach to the IT Security Development. Proceedings of the International Conferences on Dependability of Computer Systems (DepCoS-RELCOMEX 2007), Szklarska Poreba, Poland, June 14–16, 2007; Zamojski, W., Mazurkiewicz, J., Sugier, J., Walkowiak, T., Eds.; IEEE Computer Society: Washington, DC, USA, 2007; pp. 3–11. [Google Scholar]
- Noy, N.F.; McGuiness, D.L. Ontology Development 101: A Guide to Creating Your First Ontology, Knowledge Systems Laboratory. March 2001. Available online: http://www-ksl.stanford.edu/people/dlm/papers/ontology-tutorial-noy-mcguinness-abstract.html (accessed on 18 November 2009).
- Bialas, A. Validation of the Specification Means Ontology on the Simple Firewall Case. Proceedings of the 2009 International Conference on Security and Management, Las Vegas, NV, USA, July 13–16, 2009; 1, pp. 278–284.
- Bialas, A. Ontology-Based Security Problem Definition and Solution for the Common Criteria Compliant Development Process. Proceedings of International Conference on Dependability of Computer Systems (DepCoS-RELCOMEX 2009), Szklarska Poreba, Poland, June 26–28, 2009; Zamojski, W., Mazurkiewicz, J., Sugier, J., Walkowiak, T., Eds.; IEEE Computer Society: Washington, DC, USA, 2009; pp. 3–10. [Google Scholar]
- Protégé Ontology Editor and Knowledge Acquisition System; Stanford University: Palo Alto, CA, USA; Available online: http://protege.stanford.edu/ (Accessed on 18 November 2009).
- Site Certification. Supporting Document Guidance, Version 1.0 Revision 1 (CCDB-2007-11-001),; October 2007. Available online; http://www.commoncriteriaportal.org/ (accessed on 20 November 2009).
- Office for Civil Rights, United State Department of Health and Human Services. Health Insurance Portability and Accountability Act of 1996 (HIPAA). Available online: http://hhs.gov/ocr/privacy/hipaa/administrative/index.html (accessed December 2009).



©2010 by the authors; licensee Molecular Diversity Preservation International, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/3.0/)
Share and Cite
Bialas, A. Intelligent Sensors Security. Sensors 2010, 10, 822-859. https://doi.org/10.3390/s100100822
Bialas A. Intelligent Sensors Security. Sensors. 2010; 10(1):822-859. https://doi.org/10.3390/s100100822
Chicago/Turabian StyleBialas, Andrzej. 2010. "Intelligent Sensors Security" Sensors 10, no. 1: 822-859. https://doi.org/10.3390/s100100822