Secure and Lightweight Cloud-Assisted Video Reporting Protocol over 5G-Enabled Vehicular Networks
Abstract
:1. Introduction
- The Eiza-Ni-Shi protocol is built on expensive pairing operations. Thus, the overall efficiency of the Eiza-Ni-Shi protocol can be decreased despite the merits of 5G cellular networks.
- The Eiza-Ni-Shi protocol is designed by using an attribute-based encryption. When attribute-based encryption is used to achieve access control, the video sender should know the public key of the receiver. This preliminary makes the Eiza-Ni-Shi protocol to be only applicable in limited services.
- We define an application model for a secure and lightweight cloud-assisted video reporting protocol over 5G-Enabled vehicular networks. The model highlights the security objectives that the protocol should satisfy within the 5G-Enabled vehicular networks architecture.
- We develop a secure and lightweight cloud-assisted video reporting protocol for 5G-enabled vehicular networks. Without using the conventional public key certificates, the proposed protocol supports entities’ authorization through anonymous credential. Since the reported videos are broadcasted by the fixed entities, the designated vehicles can recover the reported videos without making any time-consuming communication. Also, by using lightweight security primitives, the proposed protocol minimizes the computation overhead and meets the performance requirement for the real-time ITS-based services in 5G-Enabled vehicular networks.
- We evaluate the performance of the proposed protocol in terms of security objectives, computation cost and communication overhead.
2. Related Work
2.1. VANETs and 5G-Enabled Cloud-Assisted VANETs
2.2. Security and Video Reporting in 5G Enabled Vehicular Network
3. Preliminary
3.1. Attribute-Based Encryption Scheme
3.1.1. ABE.Setup
- On input of a random as the attribute master secret key, output the corresponding public key .
- For each , choose an attribute secret to generate the attribute public key .
- Set and .
- Returns .
3.1.2. ABE.ENC
- On input of , then output the key .
- Compute .
- For , compute , respectively.
- Output the ciphertext .
3.1.3. ABE.KGN
- Based on access tree , allocate index to every node other than root.
- A polynomial over is set in top-down manner for each node where each polynomial is of degree and is considered as the threshold value of the node.
- −
- Set for the root node.
- −
- Set for every node with a leaf, where represents the node’s index value.
- Suppose contains n leaves, for every leaf node (), a secret share for the decryption key is generated as where i represents the attribute linked to and a random number for i taken in ABE.Setup.
- Output .
3.1.4. ABE.DEC
- For every leaf node linked to an attribute i, NodeKey(, D, ) is computed as follows. Note that we represent NodeKey(, D, ) into in the next paragraph for convenience.
- In case the associated attribute i to is not comprised in , then NodeKey(, D, ) = ⊥.
- else,
- To proceed with a non-leaf node u, the algorithm calls NodeKey(, D, z) for all children z which are attached to the node u.
- Suppose that is an arbitrary set of children nodes satisfying NodeKey(, D, z) ⊥. In case no such set is existent, NodeKey(, D, u) output ⊥. We use N to denote NodeKey(, D, u) in the next paragraph for paper formatting.
- Else, let represent the Lagrange coefficient with ,
- Compute the decryption key K = NodeKey(, D, ) = .
- Output the decrypted message .
3.2. Certificateless Signature Scheme
- CertS.Setup() computes a master key along with a public system parameters as follows:
- −
- Let G be an additive group with a prime order q and be a generator based on an elliptic curve.
- −
- Choose as master secret key and generates the master public key .
- −
- Let and be two cryptographic hash functions.
- −
- Output the public parameters .
- −
- Output
- CertS.Secret() returns a secret value for every identity as follows:
- −
- Choose as a secret value, then compute .
- −
- Return
- CertS.PartialK(s, , ) computes a partial private/public key for the given as follows:
- −
- Select a random and generate .
- −
- Compute (mod q).
- −
- Output as the corresponding partial private key.
- CertS.SKey(, ) sets and representing the private key and public key for , respectively.
- CertS.Sign(m, ) computes the signature for a given message m as follows:
- −
- Select a random such that gcd(, q) = 1, where and .
- −
- Generates (mod q).
- −
- Output the signature .
- CertS.Verify(m, , , ) provides the signature verification for the message m for the identity as follows:
- −
- Generate and .
- −
- Check whether .
4. Overview of Proposed Protocol
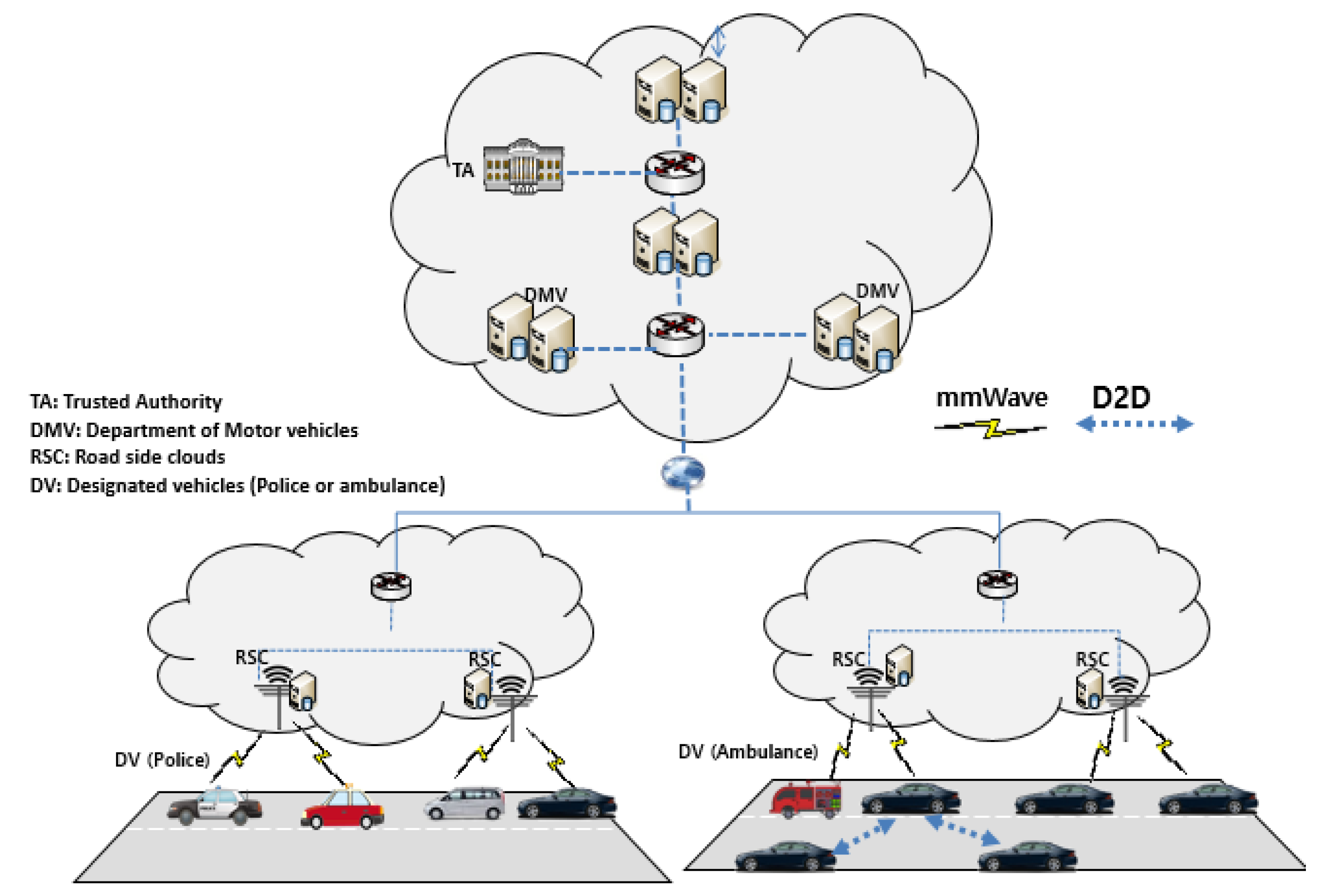
4.1. System Architecture
- Heterogeneous Networks: This network is originated from the ultimate desire to achieve high data rate and network capacity for the 5G-enabled network. Thus, two solutions may help to attain the aforementioned capacities by making the size of cells smaller and embracing the mmWave spectrum. Making the size of the cell much smaller would increase the spectral efficiency [48]. On the other side, the mmWave communications will offer high data rates because it operates in the range of 30–300 GHz and 1–10 mm for the spectrum and wavelength respectively. As mentioned in [38], the mmWave technology still suffers from considerable propagation loss that generates tremendous line of sight (LOS) connections.
- D2D Communications: D2D communication enables devices to communicate with each other within the licensed cellular bandwidth without involving the BS. In the 5G-Enabled vehicular networks, the vehicles can communicate through D2D communication or by direct link under the mmWare technology.
- Trusted Authority (TA): It is in charge of the registration of all entities (DMV, DV, RSC and vehicles) inside our system and issues cryptographic materials during the system initialization.
- Department of Motor Vehicles (DMV): All the vehicles are assumed to register with the DMV periodically. Beside the conventional techniques for vehicle’s identification including the Electronic License Plate (ELP) or the Electronic Chassis Number (ECN), each vehicle is registered with a 5G identifier (5GID) with the same functionalities as the subscriber identification module (SIM) chip.
- Road Side cloud (RSC): RSCs are servers located along the roads and accessible by the vehicles. RSCs stores the videos files (VFs) sent by the vehicles. In that case, the designated vehicles (DV) such as police or ambulance can download the files through the RSCs using mmWare communications. Due to the advancements of technology, we assume that RSCs are connected to an electricity power generator with enough computational capability.
- Designated Vehicles: The designated vehicles can be public or private vehicles registered by the government through the DMV that offers public services.
- Vehicles: Vehicles are equipped with OBUs which allow them to communicate with RSCs in order to send the recorded video files.
4.2. Security Objectives
- Authentication and Authorization: Any vehicle has to be authenticated before it can send (report) a video recorded by its camera.
- Identity privacy preservation: The real identity of every vehicle should be protected from being known by other vehicles, RSC, DVs and DMV.
- Fine-grained access control: ABE should guarantee a fine-grained access control by which a designated vehicle should strictly be capable to recover a video fitting to its possessed access structure.
- Non-repudiation: A given vehicle should not deny its participation in video reporting.
- Traceability: TA should be capable of disclosing the real identity of all the entities in the system.
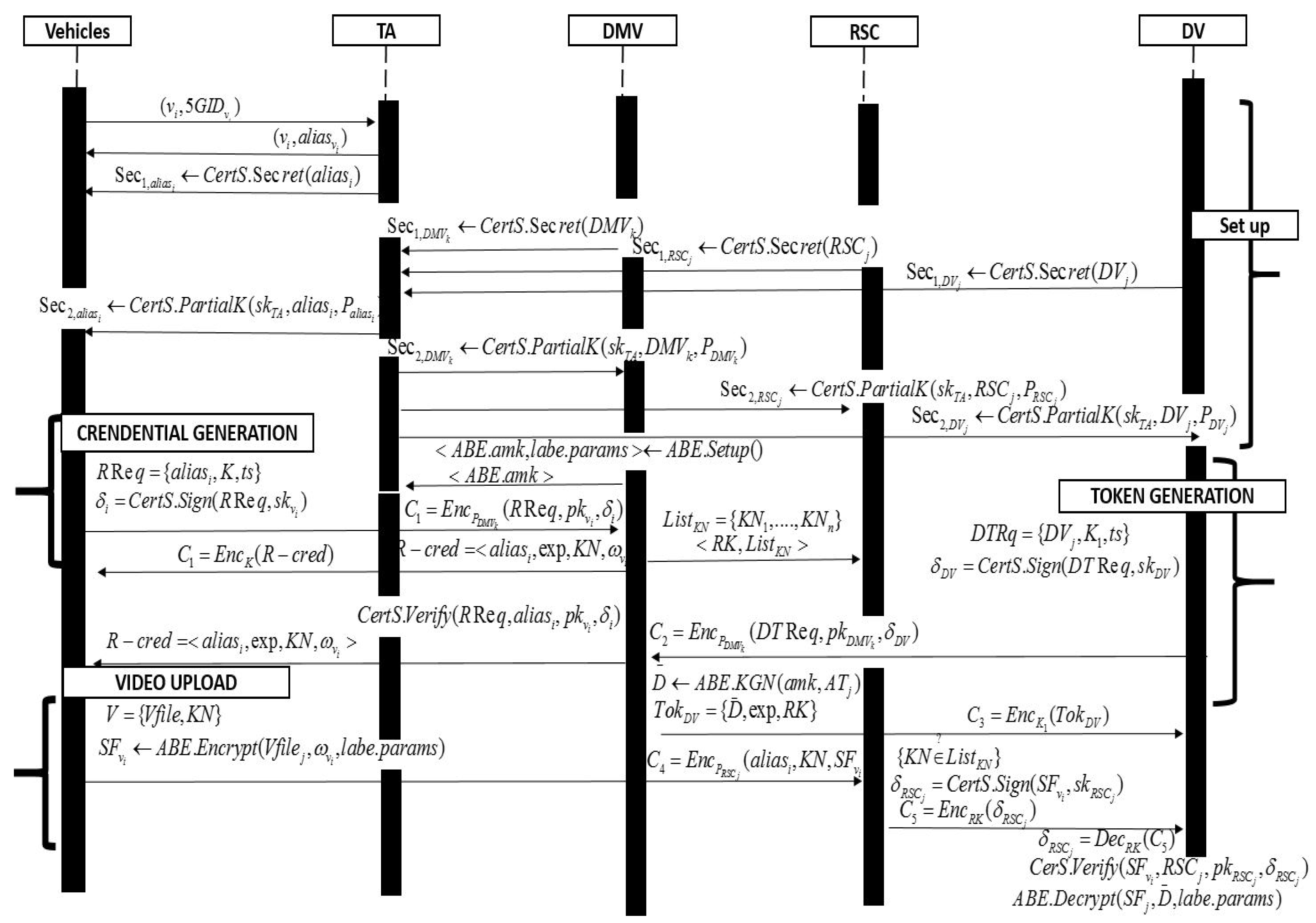
4.3. Overall Operation
- System setup: TA sets up its master secret key and its corresponding public key. Each vehicle provides its real identity and TA generates the corresponding pseudo identity from which a partial private key is computed. DMVs and RSCs also provide their real identities and TA computes their partial private keys. Each vehicle registers with the TA through the DMV, the designated vehicles such as the police or ambulance also register with the TA through the DMV.
- Periodic credential generation: Periodically, a vehicle request for credential in order report the recorded videos. DMV generates the periodic credential to vehicles along with the set of attributes corresponding to the type of request. We assume that based on some criteria such as accident record or reckless driving, DMV can decide to give different set of attributes to participating vehicles.
- On-duty token generation: The designated vehicles also received on-duty tokens. These tokens will be used by the designated to retrieve reported videos from the RSCs.
- Accident Reporting: Periodically, a vehicle registers for road reporting services. During the registration, the vehicle specifies the types of services to be reported such as accident or abnormal scene (we assume that the camera of a vehicle is not limited to report road’s accidents only). An incentive technique based on point accumulation could be considered in order to motivate the vehicle users to participate in video reporting. Whenever an accident or abnormal scene occurs the camera records the scene and upload the files to the RSC using mmWare technology or D2D communication. The designated vehicles would later on acquire the report from the RSCs as long as they possess enough access structure to recover the secret.
5. Details of Proposed Protocol
5.1. System Setup
- TA selects an elliptic curve group of order q with as a generator.
- In order to get the master secret and public key , TA executes CertS.Setup() and sets CLS.Setup(), then output .
- In order to keep a record of each vehicle , TA set a pseudonym to every based on its real identity .
- Each , and registers to TA, then computes CertS private keys as follows:
- , and computes CertS.Secret(), CertS.Secret() and CertS.Secret(), and makes a request for partial private key to the TA, respectively.
- TA provides CertS.PartialK(, , ); CertS.PartialK(, , ) and CertS.PartiaK(, , ) to each entity securely.
- , and set CertS.SKey(, ); CertS.SKey(, ) and CertS.SKey(, ), respectively.
- Likewise, every computes CertS.Secret(), TA provides CertS.PartialK(, , ), then sets CertS.SKey(, ).
- selects a given universe of attributes , computes ABE parameters as ABE.Setup(), then avails to the whole system. Note that will later send to TA in non busy hours.
5.2. Periodic Credential Generation
- composes a credential request message where is the time stamp and K is a secret key to be used later.
- sends to the , where is the signature for the set as = CertS.Sign(, ).
- Upon receiving the message , first decrypts using its private key, then verifies the signature as CertS.Verify(, , , ).
- Generate R- where is the expiration date, the set of attributes and the keyword for the credential. Note that is not specific for each credential but is the same based on the access structure.
- sends - to . Then, can recover R- by decrypting the under the shared secret key K.
- sends periodically a list of all the keywords enclosed in the credentials to .
5.3. On-Duty Token Generation
- composes an on-duty token request where is the time stamp and is a secret key to be used later.
- sends to the , where is the signature for the set as = CertS.Sign(, ).
- Upon receiving the message , first decrypts using its private key, then verifies the signature as CertS.Verify(, , , ).
- set ABE.KGN(, ) where is the access structure corresponding to the designated vehicle’s type (police or ambulance).
- composes a token message where is the expiring date, a shared secret which is given to DVs that are supposed to work within a defined geographic zone. Note that in real word, one police vehicle can be assign to attend to all the requests from a defined geographic area (three or five consecutive streets). send it to encrypted under the shared symmetric key as .
5.4. Abnormal Video Recording
- After recording a video file, composes a message ; uses the access policy retrieved in the credential R- and encrypts the file under the given attribute set as ABE.Encrypt(, , ).
- sends to .
- decrypts and check if {}.
- If not is discarded. Note that value are similar for all the vehicles which have a similar set of attribute such as . As mentioned before, can choose to give a type of attributes to a vehicle based on different criteria such accident record and reckless driving record. The choice of those criteria is beyond the scope of this paper.
- Otherwise, forwards the file securely to neighboring .
- generates = CertS.Sign(, ) and broadcast within its coverage area.
- decrypts using the area shared key of . Note that only assigned to work within coverage can decrypt the .
- runs CertS.Verify(, , , ).
- runs ABE.Decrypt(, , ) to get the original file of .
6. Performance Evaluation
6.1. Security
- Authentication: The authentication for every requesting a service file is provided by the certificateless signature scheme on messagewith . No malicious user can falsify a valid signature based on the hardness of DL problem. Otherwise the verifier could check the validity of the message by running CLS.Verify(m, , , ) to check if . Thus, the authentication is guaranteed for the proposed protocol.
- Authorization: Every vehicle has to get a periodic credential before it can participate in video reporting. sends to the to request a credential. After a valid verification, sends where as ’s credential which allows the to participate in video reporting.
- Identity privacy preservation: It is hard for an attacker to get a real identity of a vehicle within our proposed protocol. In the registration stage of the vehicle provided by TA, every vehicle is provided with a pseudo-identity . Though the malicious user would get the credential request message , the single plain identity of which is available is its pseudo-identity . In the rest of the protocol, the remaining available information concerning is its pseudo-identity . We confirm that our protocol achieves identity privacy preservation.
- Fine-grained access control: In the proposed protocol, the video file sent to is encrypted under a set of attributes as ABE.Encrypt(, , ). The file is sent encrypted under the public key of . only checks if ; this will save the from availing bogus files to . can not recover the file. Even for , unless a possesses the required secret shares , it cannot reconstruct the root node R to be able to get the secret . Throughout the decryption stage based on the root or child node, except has the obligatory secret shares, the decryption procedure returns ⊥. Consequently, even the entities (vehicles)that share a certain number of attributes can not conspire (collude) together to recuperate the secret that will achieves the decryption of the video file.
- Non-repudiation: A vehicle can not deny of participating in video reporting because the receiving keeps ’s pseudo identity and its anonymous keyword contained in the credential .
- Traceability: Even though it is hard for an attacker to know the real identity of a vehicle, TA has the capability of revealing the vehicle’s real identity in case of disputes. TA makes a search to find which real identity corresponds to any given or reported . We conclude that the proposed protocol satisfies the traceability property.
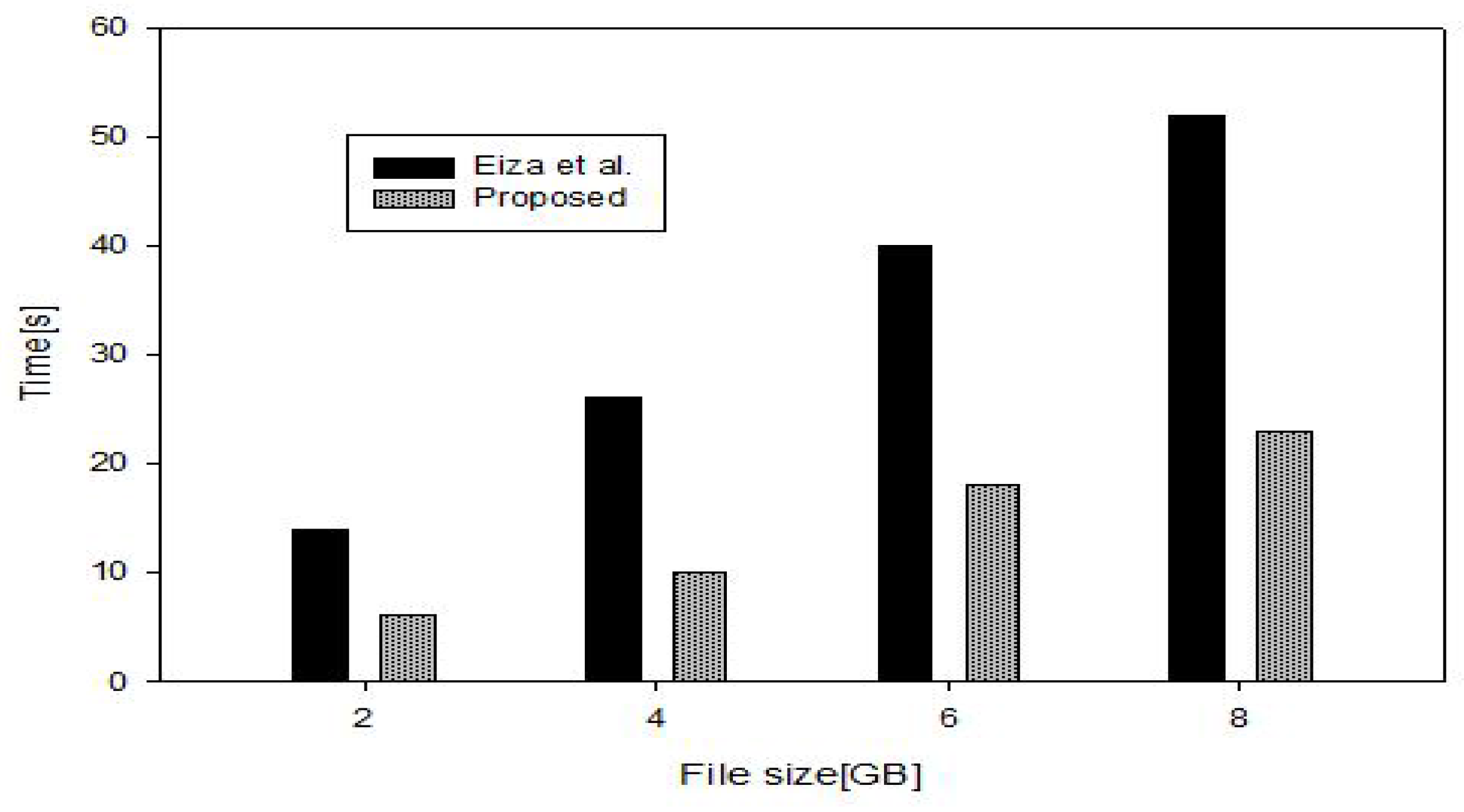
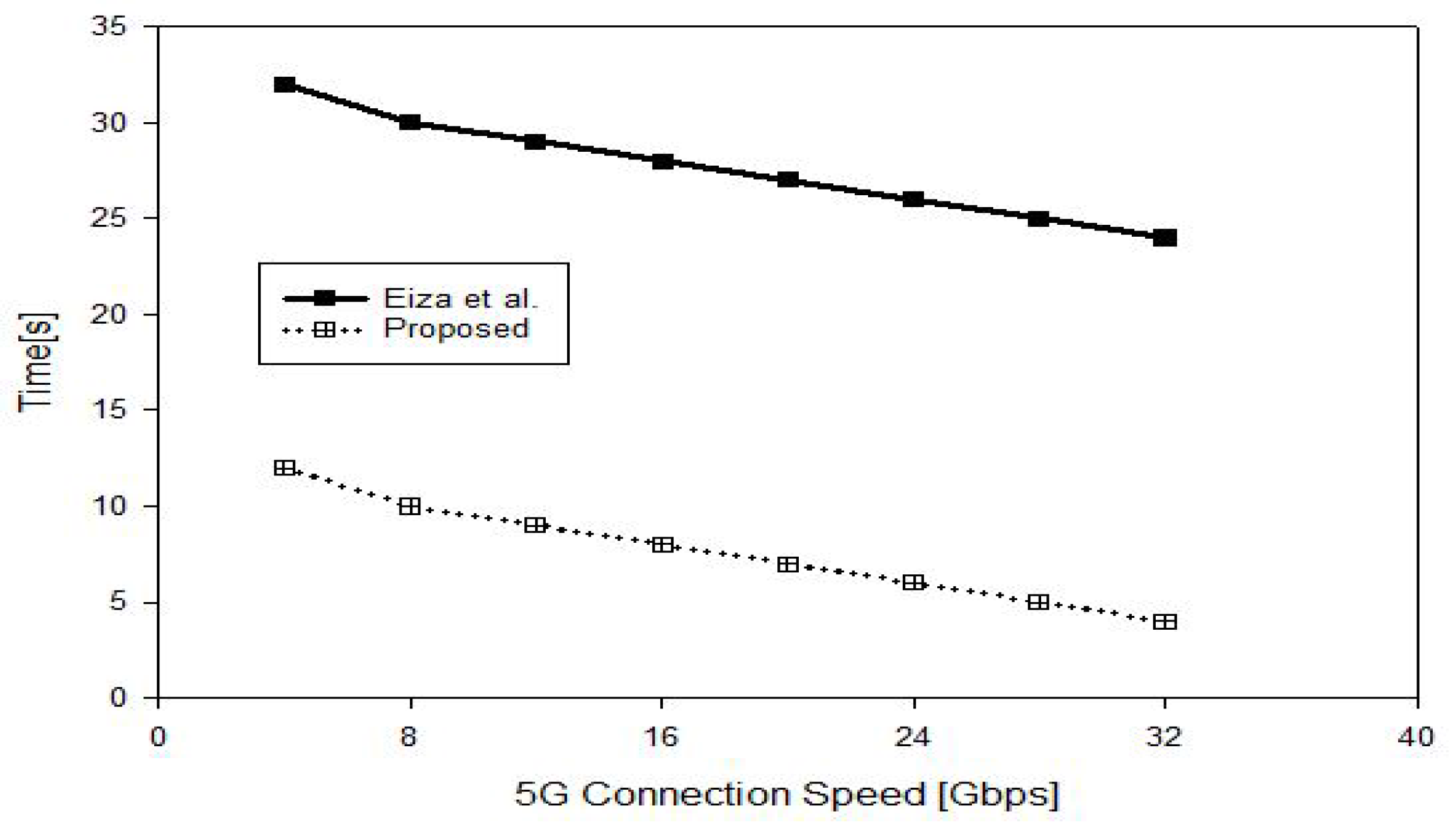
6.2. Cost Comparison
6.2.1. Computation Cost
6.2.2. Overall Cost Including Communication Cost
7. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Shen, X. Device-to-device communication in 5G cellular networks. IEEE Netw. 2015, 29, 2–3. [Google Scholar] [CrossRef]
- Yu, R.; Ding, J.; Huang, X.; Zhou, M.T.; Gjessing, S.; Zhang, Y. Optimal resource sharing in 5g-enabled vehicular networks: A matrix game approach. IEEE Trans. Veh. Technol. 2016, 65, 7844–7856. [Google Scholar] [CrossRef]
- Andrews, J.G.; Buzzi, S.; Choi, W.; Hanly, S.V.; Lozano, A.; Soong, A.C.; Zhang, J.C. What will 5G be? IEEE J. Sel. Areas Commun. 2014, 32, 1065–1082. [Google Scholar] [CrossRef]
- Li, Q.C.; Niu, H.; Papathanassiou, A.T.; Wu, G. 5G network capacity: Key elements and technologies. IEEE Veh. Technol. Mag. 2014, 9, 71–78. [Google Scholar] [CrossRef]
- Bhushan, N.; Li, J.; Malladi, D.; Gilmore, R.; Brenner, D.; Damnjanovic, A.; Sukhavasi, R.; Patel, C.; Geirhofer, S. Network densification: The dominant theme for wireless evolution into 5G. IEEE Commun. Mag. 2014, 52, 82–89. [Google Scholar] [CrossRef]
- Bloom, C.; Tan, J.; Ramjohn, J.; Bauer, L. Self-driving cars and data collection: Privacy perceptions of networked autonomous vehicles. In Proceedings of the Thirteenth Symposium on Usable Privacy and Security (SOUPS), Santa Clara, CA, USA, 12–14 July 2017; USENIX Association: Berkeley, CA, USA, 2017; pp. 357–375. [Google Scholar]
- Bellalta, B.; Belyaev, E.; Jonsson, M.; Vinel, A. Performance evaluation of IEEE 802.11p-enabled vehicular video surveillance system. IEEE Commun. Lett. 2014, 18, 708–711. [Google Scholar] [CrossRef]
- Vinel, A. 3GPP LTE versus IEEE 802.11 p/WAVE: Which technology is able to support cooperative vehicular safety applications? IEEE Wirel. Commun. Lett. 2012, 1, 125–128. [Google Scholar] [CrossRef]
- Mir, Z.H.; Filali, F. LTE and IEEE 802.11 p for vehicular networking: A performance evaluation. EURASIP J. Wirel. Commun. Netw. 2014, 2014, 89. [Google Scholar]
- Chen, S.; Zhao, J. The requirements, challenges, and technologies for 5G of terrestrial mobile telecommunication. IEEE Commun. Mag. 2014, 52, 36–43. [Google Scholar] [CrossRef]
- Belyaev, E.; Vinel, A.; Surak, A.; Gabbouj, M.; Jonsson, M.; Egiazarian, K. Robust vehicle-to-infrastructure video transmission for road surveillance applications. IEEE Trans. Veh. Technol. 2015, 64, 2991–3003. [Google Scholar] [CrossRef]
- Eiza, M.H.; Ni, Q.; Owens, T.; Min, G. Investigation of routing reliability of vehicular ad hoc networks. EURASIP J. Wirel. Commun. Netw. 2013, 2013, 179. [Google Scholar] [CrossRef] [Green Version]
- Eiza, M.H.; Owens, T.; Ni, Q.; Shi, Q. Situation-aware QoS routing algorithm for vehicular ad hoc networks. IEEE Trans. Veh. Technol. 2015, 64, 5520–5535. [Google Scholar] [CrossRef]
- Wang, C.X.; Haider, F.; Gao, X.; You, X.H.; Yang, Y.; Yuan, D.; Aggoune, H.; Haas, H.; Fletcher, S.; Hepsaydir, E. Cellular architecture and key technologies for 5G wireless communication networks. IEEE Commun. Mag. 2014, 52, 122–130. [Google Scholar] [CrossRef]
- Gai, K.; Qiu, M.; Tao, L.; Zhu, Y. Intrusion detection techniques for mobile cloud computing in heterogeneous 5G. Secur. Commun. Netw. 2016, 9, 3049–3058. [Google Scholar] [CrossRef]
- Chen, S.; Qin, F.; Hu, B.; Li, X.; Chen, Z. User-centric ultra-dense networks for 5G: Challenges, methodologies, and directions. IEEE Wirel. Commun. 2016, 23, 78–85. [Google Scholar] [CrossRef]
- Chatterjee, S.; Kar, A.K.; Gupta, M. Critical Success Factors to Establish 5G Network in Smart Cities: Inputs for Security and Privacy. J. Glob. Inf. Manag. 2017, 25, 15–37. [Google Scholar] [CrossRef]
- Eiza, M.H.; Ni, Q.; Shi, Q. Secure and Privacy-Aware Cloud-Assisted Video Reporting Service in 5G-Enabled Vehicular Networks. IEEE Trans. Veh. Technol. 2016, 65, 7868–7881. [Google Scholar] [CrossRef]
- Yoo, S.G. 5G-VRSec: Secure Video Reporting Service in 5G Enabled Vehicular Networks. Wirel. Commun. Mob. Comput. 2017, 2017, 7256307. [Google Scholar] [CrossRef]
- Malhi, A.K.; Batra, S. An efficient certificateless aggregate signature scheme for vehicular ad-hoc networks. Discrete Math. Theor. Comput. Sci. 2015, 17, 317–338. [Google Scholar]
- Horng, S.J.; Tzeng, S.F.; Huang, P.H.; Wang, X.; Li, T.; Khan, M.K. An efficient certificateless aggregate signature with conditional privacy-preserving for vehicular sensor networks. Inf. Sci. 2015, 317, 48–66. [Google Scholar] [CrossRef]
- Cho, W.; Park, Y.; Sur, C.; Rhee, K.H. An Improved Privacy-Preserving Navigation Protocol in VANETs. JoWUA 2013, 4, 80–92. [Google Scholar]
- Altayeb, M.; Mahgoub, I. A survey of vehicular ad hoc networks routing protocols. Int. J. Innov. Appl. Stud. 2013, 3, 829–846. [Google Scholar]
- Yin, J.; ElBatt, T.; Yeung, G.; Ryu, B.; Habermas, S.; Krishnan, H.; Talty, T. Performance evaluation of safety applications over DSRC vehicular ad hoc networks. In Proceedings of the 1st ACM International Workshop on Vehicular Ad Hoc Networks, Philadelphia, PA, USA, 1 October 2004; ACM: New York, NY, USA, 2004; pp. 1–9. [Google Scholar]
- Hussain, R.; Son, J.; Eun, H.; Kim, S.; Oh, H. Rethinking vehicular communications: Merging VANET with cloud computing. In Proceedings of the 2012 IEEE 4th International Conference on Cloud Computing Technology and Science (CloudCom), Taipei, Taiwan, 3–6 December 2012; pp. 606–609. [Google Scholar]
- Olariu, S.; Khalil, I.; Abuelela, M. Taking VANET to the clouds. Int. J. Pervasive Comput. Commun. 2011, 7, 7–21. [Google Scholar] [CrossRef]
- Hussain, R.; Abbas, F.; Son, J.; Oh, H. TIaaS: Secure cloud-assisted traffic information dissemination in vehicular ad hoc networks. In Proceedings of the 2013 13th IEEE/ACM International Symposium on Cluster, Cloud and Grid Computing (CCGrid), Delft, The Netherlands, 13–16 May 2013; pp. 178–179. [Google Scholar]
- He, W.; Yan, G.; Xu, L.D. Developing vehicular data cloud services in the IoT environment. IEEE Trans. Ind. Inform. 2014, 10, 1587–1595. [Google Scholar] [CrossRef]
- Lee, E.; Lee, E.K.; Gerla, M.; Oh, S.Y. Vehicular cloud networking: architecture and design principles. IEEE Commun. Mag. 2014, 52, 148–155. [Google Scholar] [CrossRef]
- Nkenyereye, L.; Rhee, K.H. Secure Traffic Data Transmission Protocol for Vehicular Cloud. In Advances in Computer Science and Ubiquitous Computing; Springer: Berlin, Germany, 2015; pp. 497–503. [Google Scholar]
- Nkenyereye, L.; Tama, B.A.; Park, Y.; Rhee, K.H. A Fine-Grained Privacy Preserving Protocol over Attribute Based Access Control for VANETs. JoWUA 2015, 6, 98–112. [Google Scholar]
- Nkenyereye, L.; Rhee, K.H. Secure Taxi Service Scheme in Vehicular Cloud Environment. Int. Inf. Inst. (Tokyo) Inf. 2015, 18, 3495. [Google Scholar]
- Zhang, N.; Cheng, N.; Gamage, A.T.; Zhang, K.; Mark, J.W.; Shen, X. Cloud assisted HetNets toward 5G wireless networks. IEEE Commun. Mag. 2015, 53, 59–65. [Google Scholar] [CrossRef]
- Trivisonno, R.; Guerzoni, R.; Vaishnavi, I.; Soldani, D. SDN-based 5G mobile networks: Architecture, functions, procedures and backward compatibility. Trans. Emerg. Telecommun. Technol. 2015, 26, 82–92. [Google Scholar] [CrossRef]
- Mantas, G.; Komninos, N.; Rodriuez, J.; Logota, E.; Marques, H. Security for 5G communications. In Fundamentals of 5G Mobile Networks; John Wiley & Sons, Ltd.: Hoboken, NJ, USA, 2015. [Google Scholar]
- Yang, N.; Wang, L.; Geraci, G.; Elkashlan, M.; Yuan, J.; Di Renzo, M. Safeguarding 5G wireless communication networks using physical layer security. IEEE Commun. Mag. 2015, 53, 20–27. [Google Scholar] [CrossRef]
- Alam, M.; Yang, D.; Rodriguez, J.; Abd-alhameed, R. Secure device-to-device communication in LTE-A. IEEE Commun. Mag. 2014, 52, 66–73. [Google Scholar] [CrossRef]
- Lin, X.; Sun, X.; Ho, P.H.; Shen, X. GSIS: A secure and privacy-preserving protocol for vehicular communications. IEEE Trans. Veh. Technol. 2007, 56, 3442–3456. [Google Scholar]
- Raya, M.; Papadimitratos, P.; Aad, I.; Jungels, D.; Hubaux, J.P. Eviction of misbehaving and faulty nodes in vehicular networks. IEEE J. Sel. Areas Commun. 2007, 25, 1557–1568. [Google Scholar] [CrossRef]
- Dikaiakos, M.D.; Florides, A.; Nadeem, T.; Iftode, L. Location-aware services over vehicular ad-hoc networks using car-to-car communication. IEEE J. Sel. Areas Commun. 2007, 25, 1590–1602. [Google Scholar] [CrossRef]
- Sampigethaya, K.; Li, M.; Huang, L.; Poovendran, R. AMOEBA: Robust location privacy scheme for VANET. IEEE J. Sel. Areas Commun. 2007, 25, 1569–1589. [Google Scholar] [CrossRef]
- Chim, T.W.; Yiu, S.; Hui, L.C.; Li, V.O. VSPN: VANET-based secure and privacy-preserving navigation. IEEE Trans. Comput. 2014, 63, 510–524. [Google Scholar] [CrossRef]
- Coronado, E.; Cherkaoui, S. Provisioning of on-demand services in vehicular networks. In Proceedings of the Global Telecommunications Conference (GLOBECOM), Honolulu, HI, USA, 30 November–4 December 2009; pp. 1–6. [Google Scholar]
- Li, C.T.; Hwang, M.S.; Chu, Y.P. A secure and efficient communication scheme with authenticated key establishment and privacy preserving for vehicular ad hoc networks. Comput. Commun. 2008, 31, 2803–2814. [Google Scholar] [CrossRef]
- Zhu, H.; Lu, R.; Shen, X.; Lin, X. Security in service-oriented vehicular networks. IEEE Wirel. Commun. 2009, 16, 16–22. [Google Scholar]
- Yao, X.; Chen, Z.; Tian, Y. A lightweight attribute-based encryption scheme for the Internet of Things. Future Gener. Comput. Syst. 2015, 49, 104–112. [Google Scholar] [CrossRef]
- He, D.; Chen, J.; Zhang, R. An efficient and provably-secure certificateless signature scheme without bilinear pairings. Int. J. Commun. Syst. 2012, 25, 1432–1442. [Google Scholar] [CrossRef]
- Chin, W.H.; Fan, Z.; Haines, R. Emerging technologies and research challenges for 5G wireless networks. IEEE Wirel. Commun. 2014, 21, 106–112. [Google Scholar] [CrossRef]
- Birem, M.; Berry, F. Dreamcam: A modular fpga-based smart camera architecture. J. Syst. Archit. 2014, 60, 519–527. [Google Scholar] [CrossRef]
- Lu, R.; Lin, X.; Zhu, H.; Ho, P.H.; Shen, X. A novel anonymous mutual authentication protocol with provable link-layer location privacy. IEEE Trans. Veh. Technol. 2009, 58, 1454–1466. [Google Scholar]
- Miyaji, A.; Nakabayashi, M.; Takano, S. New explicit conditions of elliptic curve traces for FR-reduction. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 2001, 84, 1234–1243. [Google Scholar]
- Wei, D. Crypto++ Library 5.6.5, a Free C++ Class Library of Cryptographic schemes. 2017. Available online: http://www.cryptopp.com (accessed on 12 May 2017).
- Demestichas, P.; Georgakopoulos, A.; Karvounas, D.; Tsagkaris, K.; Stavroulaki, V.; Lu, J.; Xiong, C.; Yao, J. 5G on the horizon: Key challenges for the radio-access network. IEEE Veh. Technol. Mag. 2013, 8, 47–53. [Google Scholar] [CrossRef]
- Bethencourt, J.; Sahai, A.; Waters, B. Advanced Crypto Software Collection—Ciphertext-Policy Attribute-Based Encryption. Available online: http://acsc.cs.utexas.edu/cpabe/ (accessed on 20 June 2017).
- MIRACL Crypto SDK; CertiVox UK, R.U. Multiprecision Integer and Rational Arithmetic Cryptographic Library. 2016. Available online: https://www.certivox.com/miracl (accessed on 15 June 2017).
- Baek, J.; Safavi-Naini, R.; Susilo, W. Public key encryption with keyword search revisited. In Proceedings of the International Conference on Computational Science and Its Applications, Perugia, Italy, 30 June–3 July 2008; pp. 1249–1259. [Google Scholar]
- BBCNews. 5G Researchers Manage Record Connection Speed. 2015. Available online: http://www.bbc.co.uk/news/technology-31622297 (accessed on 10 May 2017).

| Term | Notation |
|---|---|
| Unique 5G identity for each OBU’s vehicle | |
| Trusted Authority | |
| Department of Motor vehicle’s server | |
| Roadside cloud’s server | |
| Identity of designated vehicle’s OBU | |
| R- | ’s credential issued by |
| Key word within a vehicle’s credential | |
| List of generated periodically | |
| A duty token for generated by | |
| ’s pseudo identity | |
| time stamp | |
| certificateless signature of entity i | |
| Elliptic curve group with the same order q | |
| A generator of | |
| private, public key pair of an entity X | |
| Master secret for each attribute i | |
| Attribute master key | |
| Public key for each attribute | |
| ’s pseudonym | |
| U | Universe of attribute |
| Access tree | |
| Attribute set | |
| Access Structure corresponding to entity j | |
| D | Set of secret share in |
| Symmetric encryption under key k |
| Notation | Operations | Time (ms) |
|---|---|---|
| Bilinear pairing | 4.5 | |
| Point scalar multiplication | 0.6 | |
| Asymmetric encryption | 1.17 | |
| Asymmetric decryption | 0.61 | |
| Symmetric encryption | 0.51 | |
| Symmetric decryption | 0.55 | |
| hash function | 0.0001 |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Nkenyereye, L.; Kwon, J.; Choi, Y.-H. Secure and Lightweight Cloud-Assisted Video Reporting Protocol over 5G-Enabled Vehicular Networks. Sensors 2017, 17, 2191. https://doi.org/10.3390/s17102191
Nkenyereye L, Kwon J, Choi Y-H. Secure and Lightweight Cloud-Assisted Video Reporting Protocol over 5G-Enabled Vehicular Networks. Sensors. 2017; 17(10):2191. https://doi.org/10.3390/s17102191
Chicago/Turabian StyleNkenyereye, Lewis, Joonho Kwon, and Yoon-Ho Choi. 2017. "Secure and Lightweight Cloud-Assisted Video Reporting Protocol over 5G-Enabled Vehicular Networks" Sensors 17, no. 10: 2191. https://doi.org/10.3390/s17102191





