Secure Utilization of Beacons and UAVs in Emergency Response Systems for Building Fire Hazard
Abstract
:1. Introduction
2. Related Works and Backgrounds
2.1. Emergency Alert and Response System
2.2. UAV-Based Warning System
2.3. Incorporating Sensor-Based Monitoring Systems into Existing Buildings
3. UAV-Assisted Emergency Monitoring and Response System
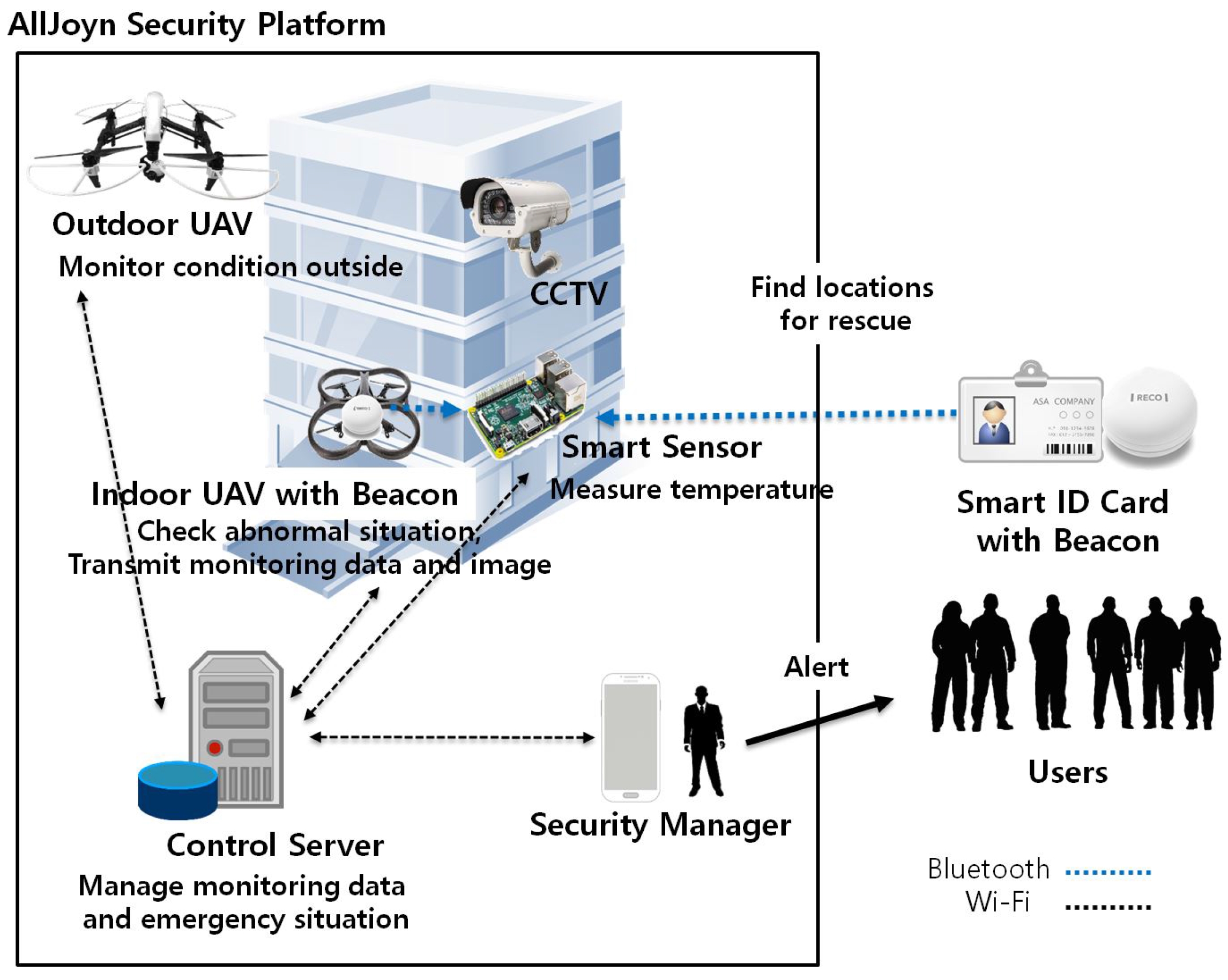
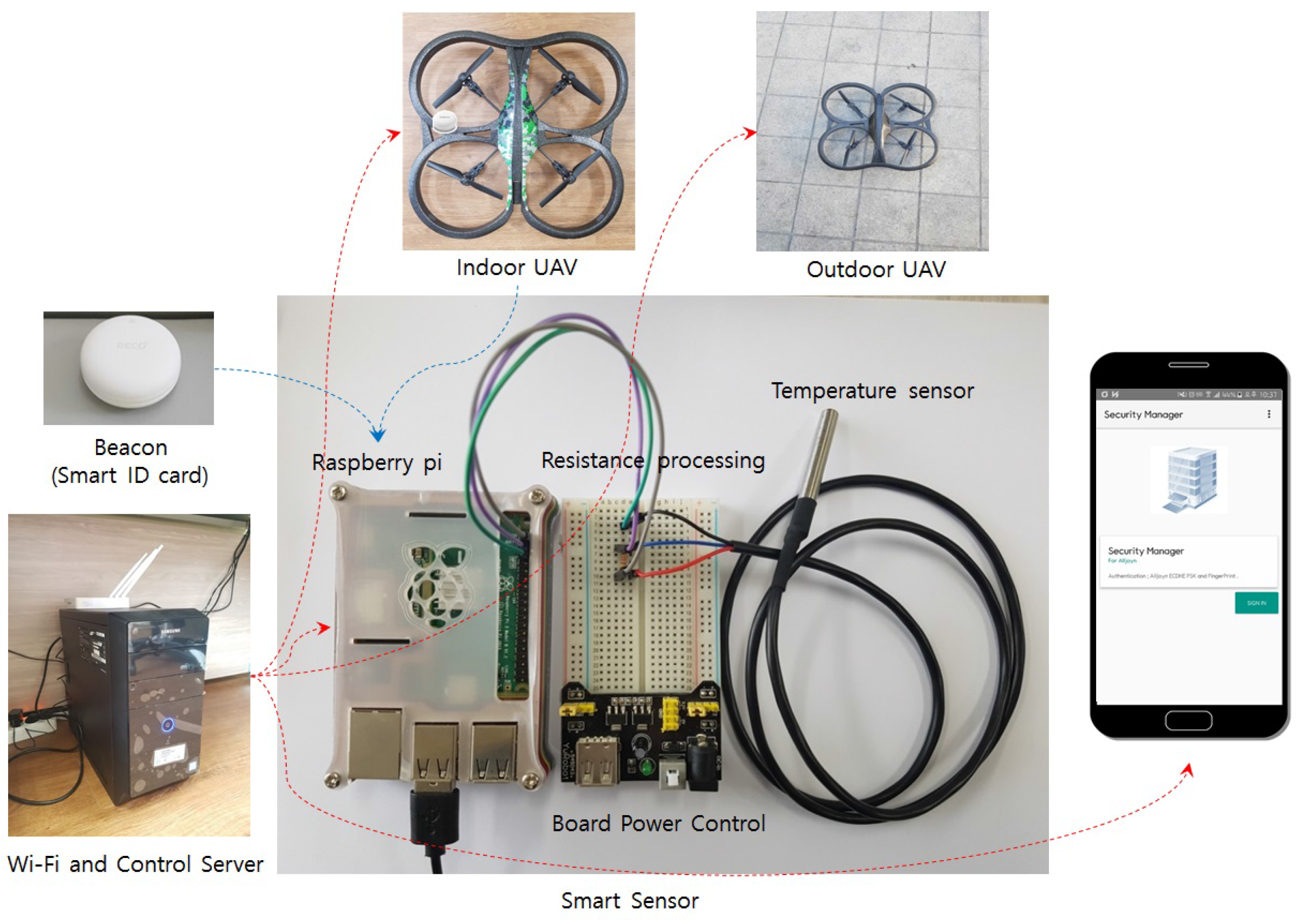
3.1. Overview of UAV-EMOR System
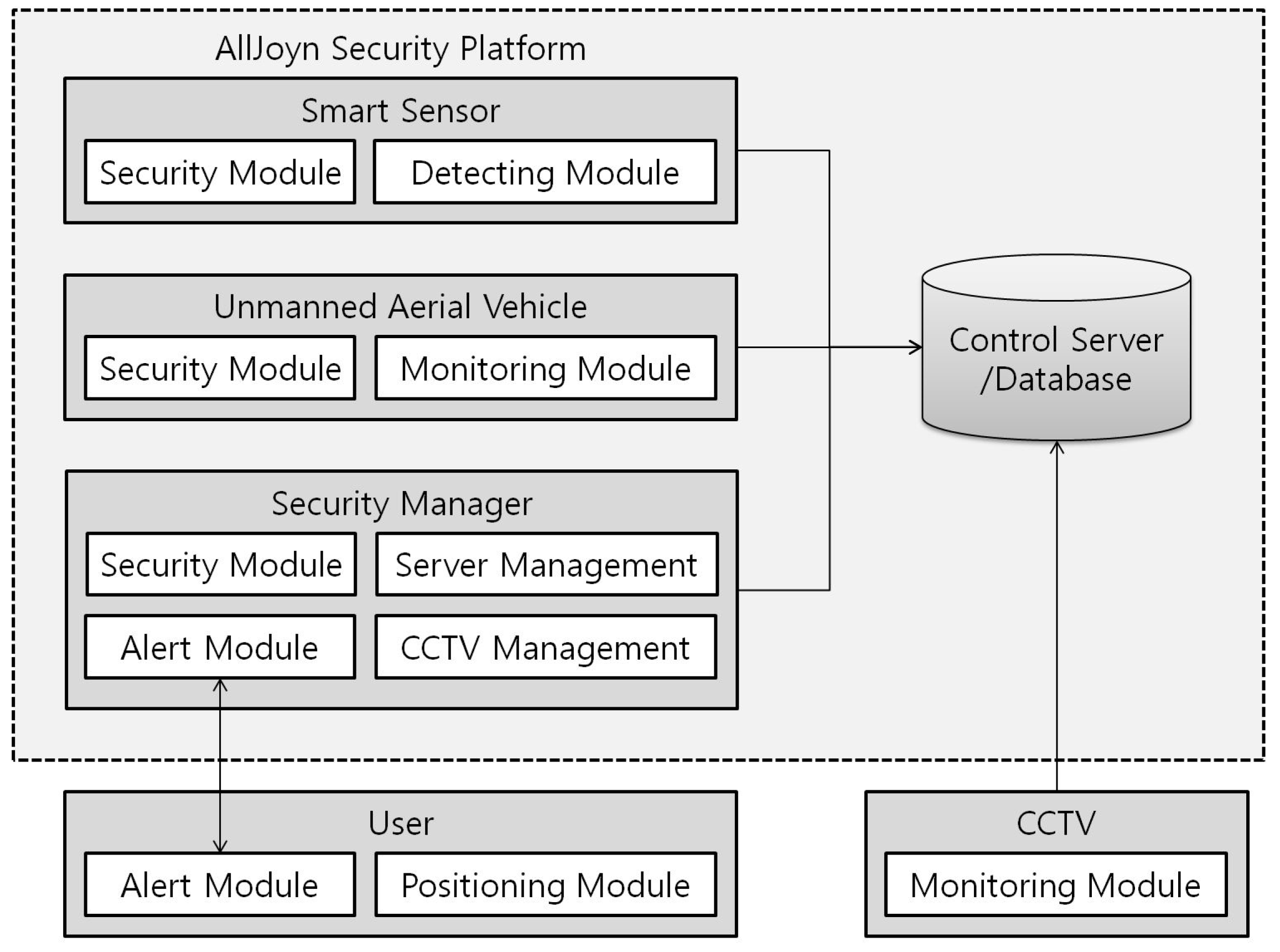
3.2. AllJoyn Security Platform for UAV-EMOR System
- ALLJOYN_SRP_KEYX: Secure Remote Password (SRP) key exchange.
- ALLJOYN_SRP_LOGON: Secure Remote Password (SRP) log on with username and password.
- ALLJOYN_ECDHE_NULL: Elliptic Curve Diffie–Hellman (ephemeral) key exchange with no authentication.
- ALLJOYN_ECDHE_PSK: Elliptic Curve Diffie–Hellman (ephemeral) key exchange authenticated with a pre-shared key (PSK).
- ALLJOYN_ECDHE_ECDSA: Elliptic Curve Diffie–Hellman (ephemeral) key exchange authenticated with an X.509 ECDSA certificate.
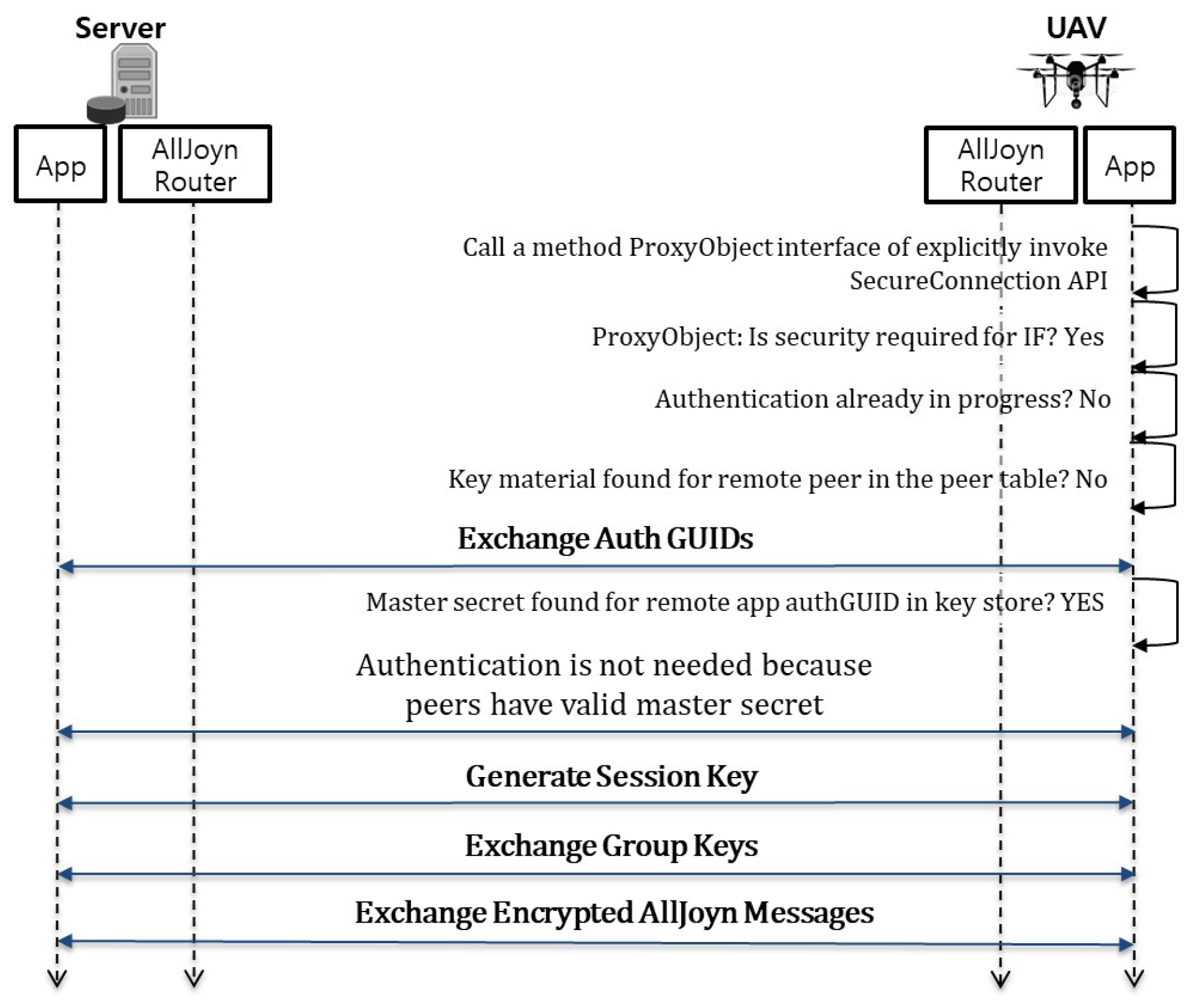
- Exchange Auth GUIDs (Authentication Group User Identifications): In this step, two peers such as the control server and the UAV exchange Auth GUIDs. The Auth GUID is used to see if the pre-shared key is present for that Auth GUID in the key store. If no pre-shared key is found, the two peers have not authenticated each other. Therefore, the two peers should execute the next app-to-app authentication step.
- App-to-app authentication: In this step, two peers perform the authentication mechanism supported by the AllJoyn platform. At the end of this step, the two peers have authenticated each other and share a common pre-shared key.
- Generate a session key: In this step, two peers generate a session key for encrypting communication messages between them. The session key is generated independently by both peers based on the pre-shared key. A group key is also generated when the first session key is generated.
- Exchange group keys: In this step, two peers exchange their own group keys with each other via an encrypted AllJoyn message. The group key is used to encrypt the session multicast and broadcast signals. At the end of this step, the two peers share group keys to decrypt secure broadcast signals received from each other.
3.3. System Protocols
- Active: When a smart sensor is functioning correctly or if it detects that a fire has ended, it indicates this by sending an “Active” message to the server.
- Unsafe: If a smart sensor detects an abnormal temperature or the smoke detection system detects smoke , it is indicated with the message “Unsafe”. The manager receives the abnormal temperature data or the smoke data and confirms whether there is an abnormality or not.
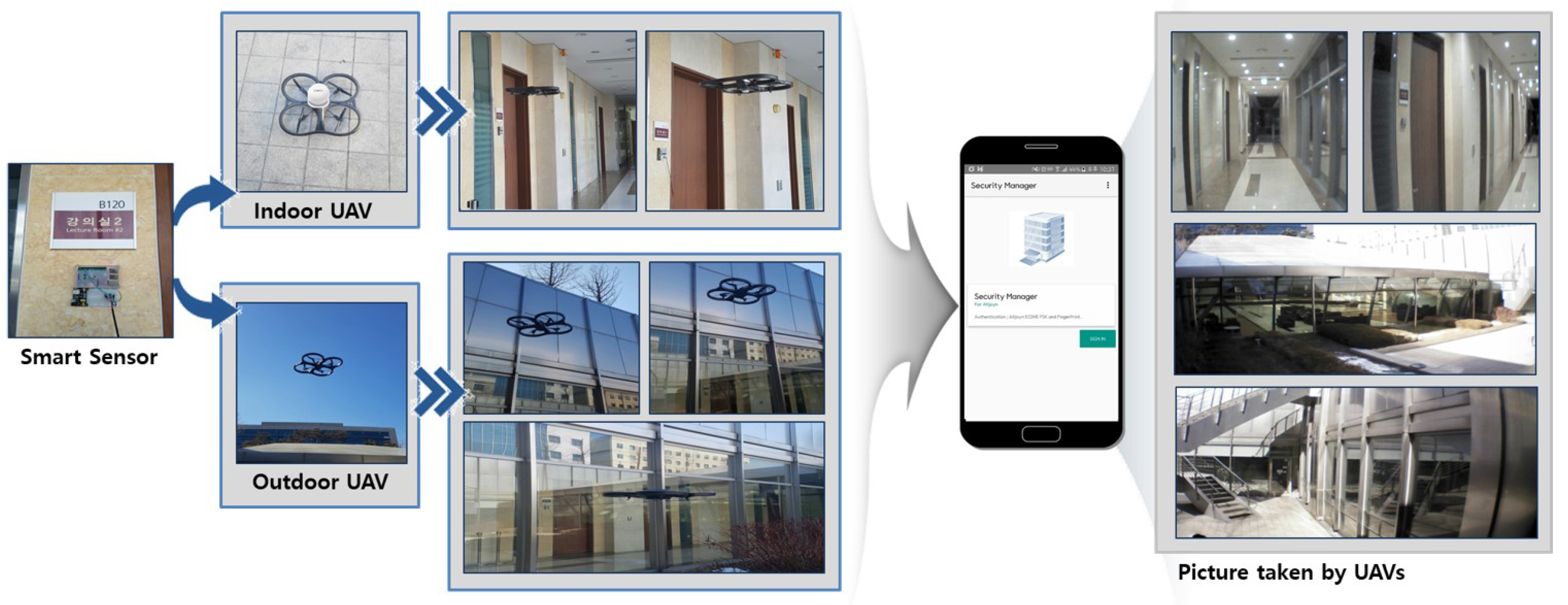
- Fire: If a manager confirms that there is a fire, the smart sensor enters the “Fire” state. When the control server receives the “Fire” message, it guides UAVs to observe the location of the smart sensor where the fire has been detected and the sprinkler is activated Furthermore, the control server sends an emergency message to everyone who is connected to the system. Via beacons, the smart sensors collect user positions and send them to the control server and manager.
- Inactive: This status indicates that a smart sensor is no longer functioning correctly due to error, loss of power, etc. In such a situation, the smart sensor notifies the control server of its “Inactive” state.
| Algorithm 1: Management Algorithm of Control Server |
|
State : Tt : Temperature value in time T Tm : Normal threshold of temperature IPhoto : Photo taken by an indoor drone OPhoto : Photo taken by an outdoor drone CCTVimage : image taken by CCTV Monitoring Group : Indoor Drone, Outdoor Drone, CCTV, Smart Sensor 1 Connect to Smart Sensor 2 if Smart Sensor == InActive then 3 Transmit “InActive” message to Security Manager 4 end 5 while Smart Sensor == Active do 6 Receive Tt from Smart Sensor 7 if The temperature change == True then 8 Save Tt to DB 9 Transmit Warning Message to Security Manager 10 if Tt < Tm then 11 Receive “Safe” message from Security Manager 12 Run Normal Operation of Day-to-Day Monitoring 13 end 14 if Tt Tm then 15 State = UnSafe 16 Broadcast “UnSafe” message to Security Manager and Monitoring Group 17 while State == Unsafe of Fire do 18 Run “Abnormal Response” operation 19 Run the fire detection system (or smoke detection system) 20 Update IPhoto in DB 21 Update OPhoto in DB 22 Update CCTVimage in DB 23 Receive Tt from Smart sensors 24 Receive State and location from Security Manager 25 if State == Fire then 26 Broadcast “Fire” message to Users and Monitoring Group 27 Run “Emergency Response” operation 28 Run the sprinkler system 29 end 30 end 31 end 32 end 33 end |
3.3.1. Day to Day Monitoring
3.3.2. Abnormal Situation Response
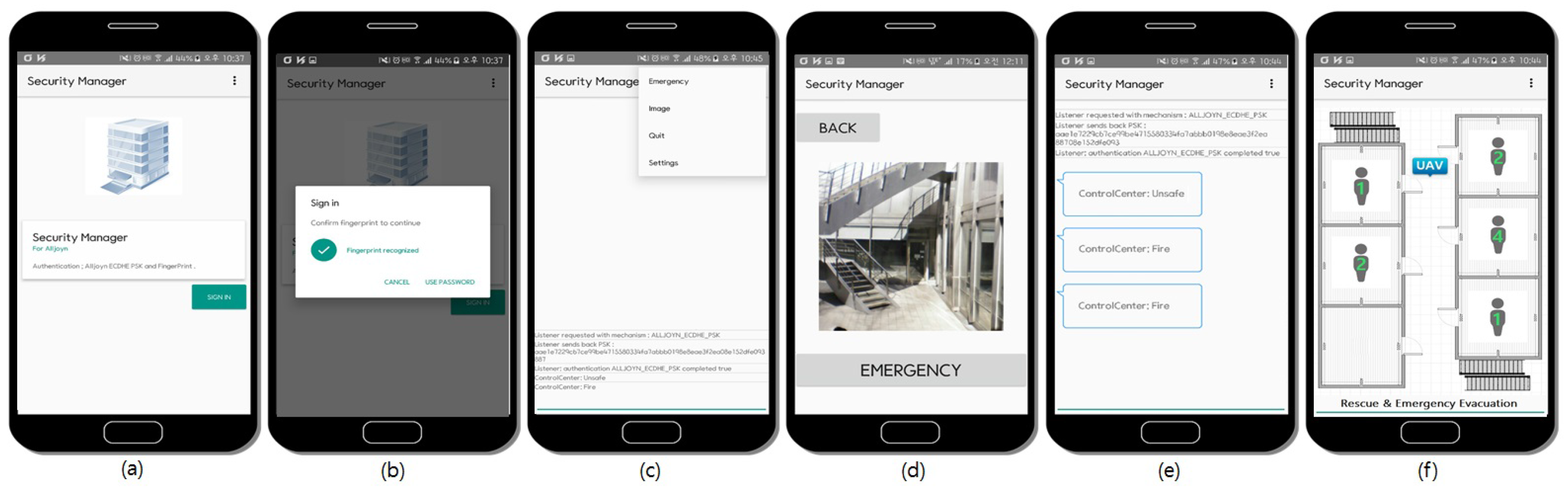
3.3.3. Emergency Response
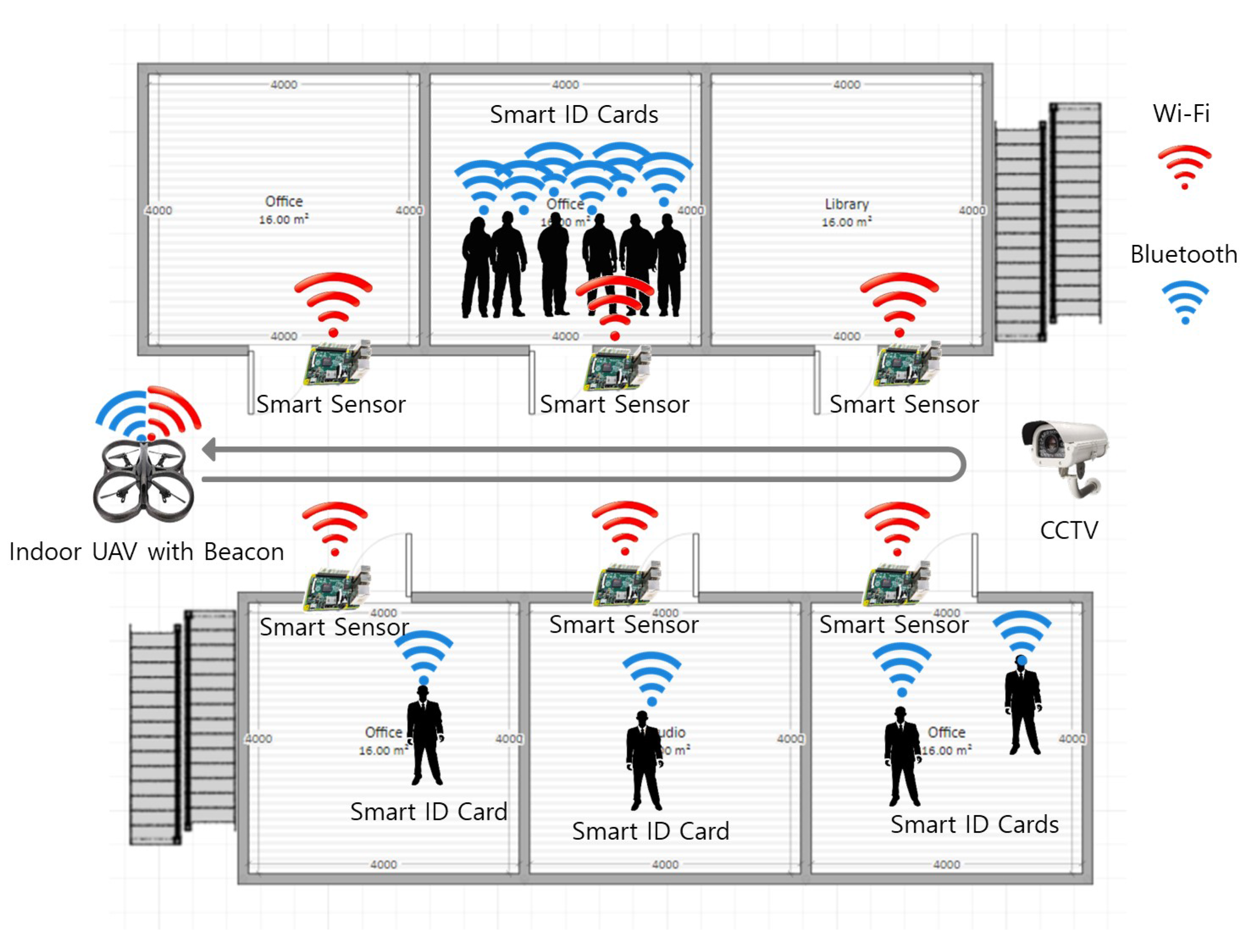
4. Prototype of UAV-EMOR and Use Scenarios
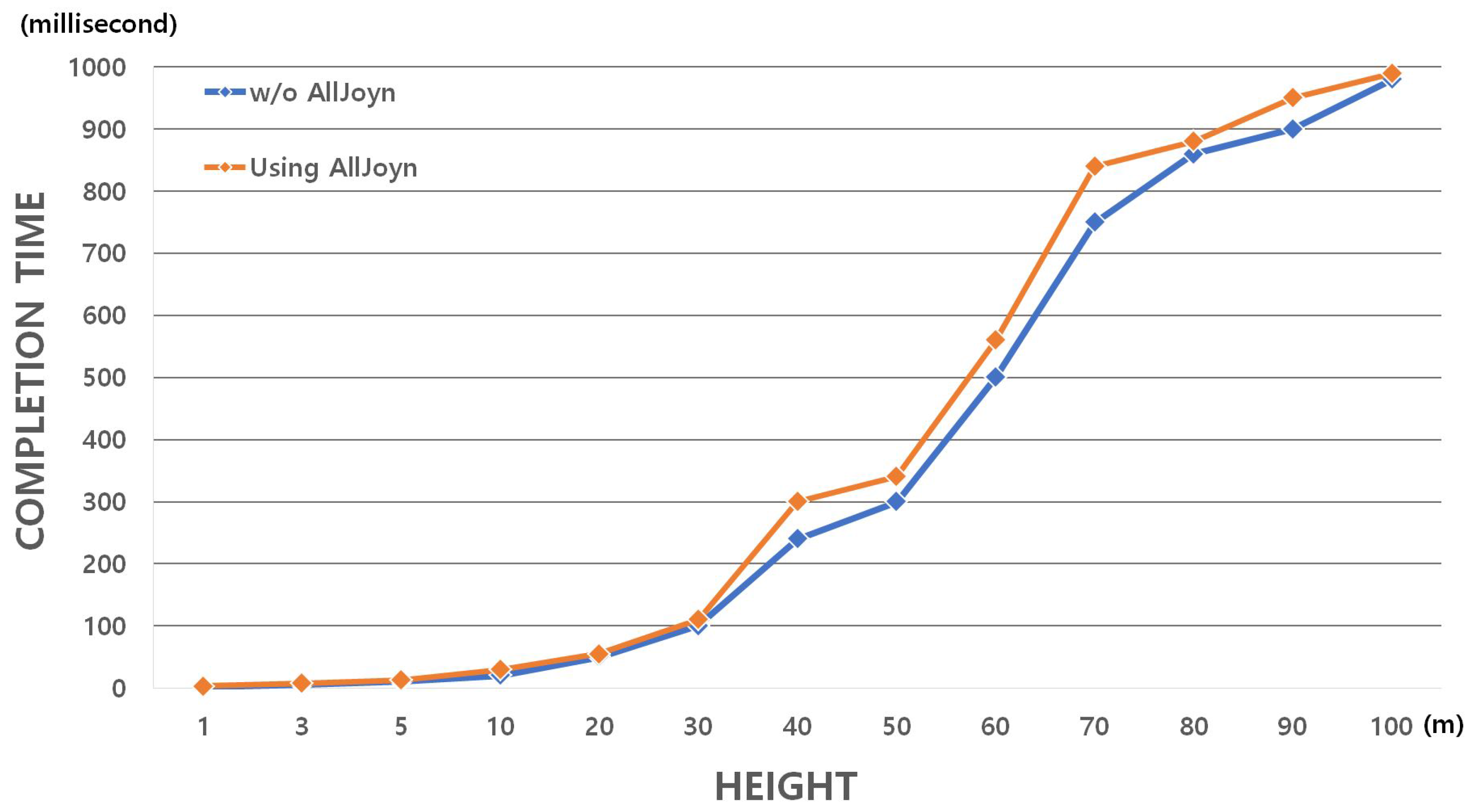
5. Performance Evaluation
6. Discussion
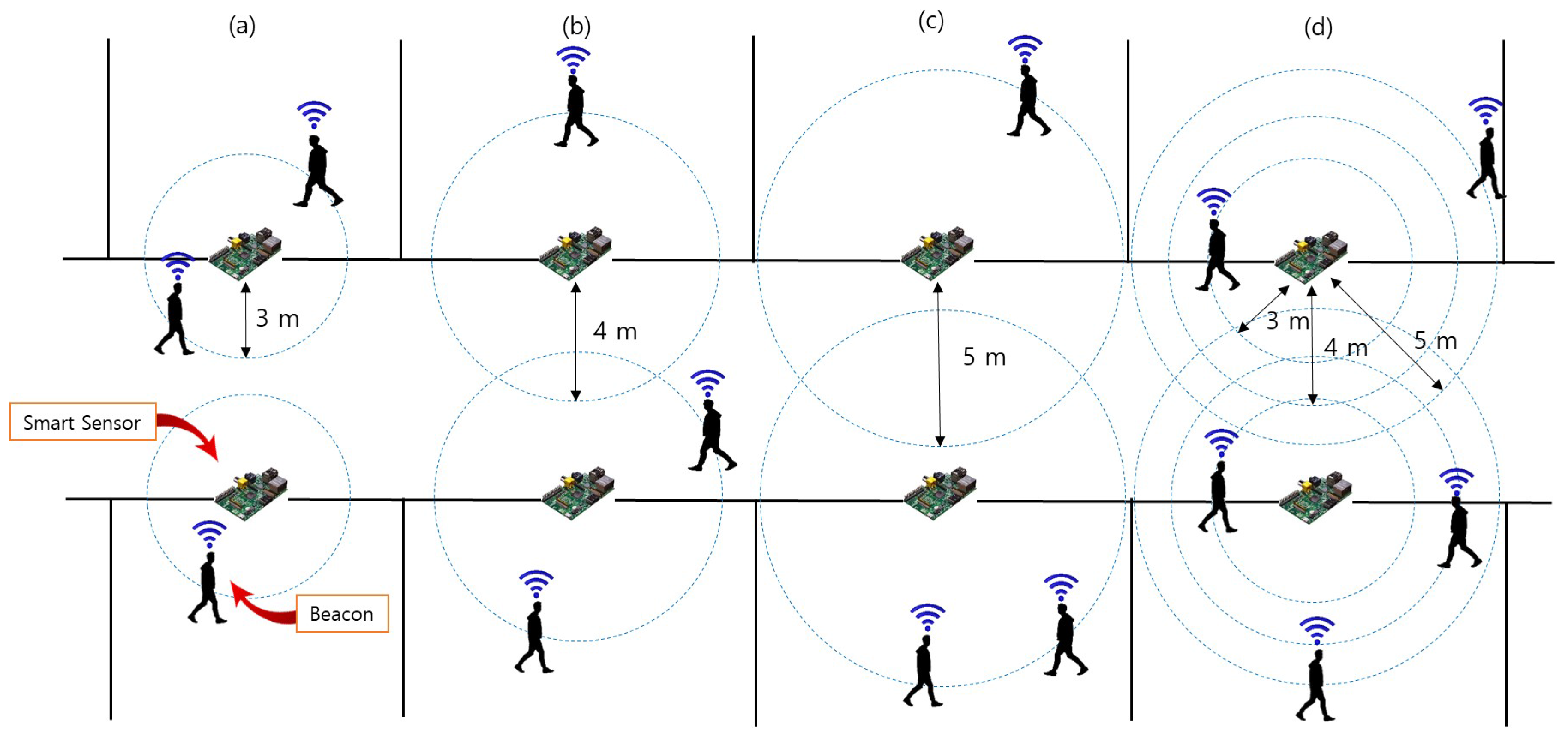
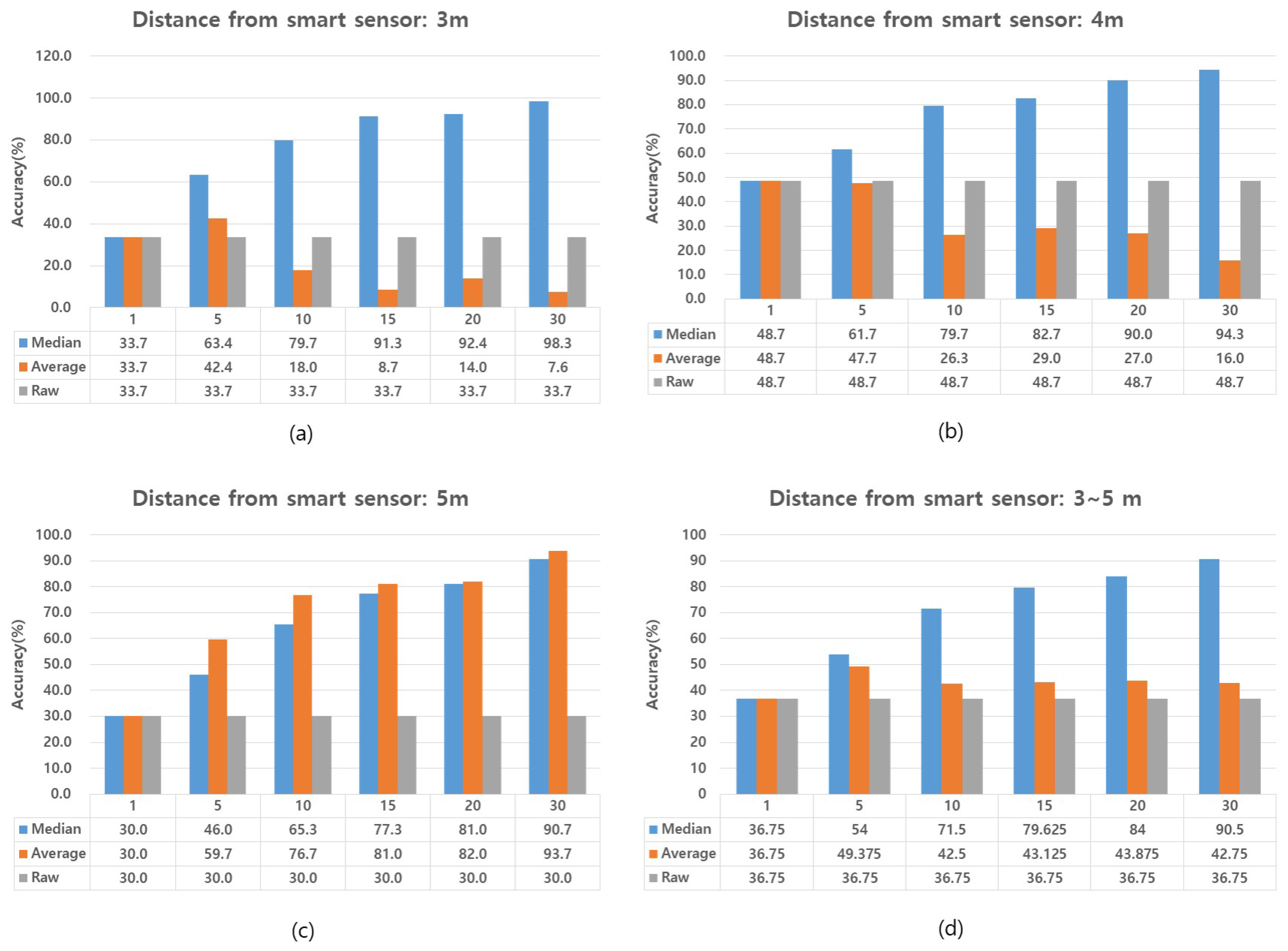
6.1. Position Accuracy
6.2. Privacy Considerations
7. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Osello, A.; Acquaviva, A.; Aghemo, C.; Blaso, L.; Dalmasso, D.; Erba, D.; Fracastoro, G.; Dondre, D.; Jahn, M.; Macii, E.; et al. Energy saving in existing buildings by an intelligent use of interoperable ICTs. Energy Effic. 2013, 6, 707–723. [Google Scholar] [CrossRef]
- Aedo, I.; Yu, S.; Diaz, P.; Acuna, P.; Onorati, T. Personalized alert notifications and evacuation routes in indoor environments. Sensors 2012, 12, 7804–7827. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Liu, J.W.S.; Lin, F.T.; Chu, E.T.H.; Zhong, J.L. Intelligent Indoor Emergency Evacuation Systems. In Proceedings of the Future Technologies Conference (FTC), San Francisco, CA, USA, 6–7 December 2016; pp. 600–609. [Google Scholar]
- Wu, Z.Y.; Lv, W.; Yu, K. A Framework of Intelligent Evacuation Guidance System for Large Building. In Proceedings of the 5th International Conference on Civil, Architectural and Hydraulic Engineering (ICCAHE 2016), Zhuhai, China, 30–31 July 2016; pp. 695–701. [Google Scholar]
- Zeng, Y.; Sreenan, C.J.; Sitanayah, L.; Xiong, N.; Park, J.H.; Zheng, G. An emergency-adaptive routing scheme for wireless sensor networks for building fire hazard monitoring. Sensors 2011, 11, 2899–2919. [Google Scholar] [CrossRef] [PubMed]
- Lin, C.Y.; Chu, E.T.H.; Ku, L.W.; Liu, J.W. Active disaster response system for a smart building. Sensors 2014, 14, 17451–17470. [Google Scholar] [CrossRef] [PubMed]
- Choi, K.; Lee, I. A UAV based close-range rapid aerial monitoring system for emergency responses. Int. Arch. Photogramm. Remote Sens. Spat. Inf. Sci. 2011, 38, 247–252. [Google Scholar] [CrossRef]
- Erdelj, M.; Natalizio, E. UAV-assisted disaster management: Applications and open issues. In Proceedings of the 2016 International Conference on Computing, Networking and Communications (ICNC), Kauai, Hawaii, USA, 15–18 February 2016; pp. 1–5. [Google Scholar]
- Chen, D.; Liu, Z.; Wang, L.; Dou, M.; Chen, J.; Li, H. Natural disaster monitoring with wireless sensor networks: A case study of data intensive applications upon low-cost scalable systems. Mob. Netw. Appl. 2013, 18, 651–663. [Google Scholar] [CrossRef]
- Frigerio, S.; Schenato, L.; Bossi, G.; Cavalli, M.; Mantovani, M.; Marcato, G.; Pasuto, A. A web-based platform for automatic and continuous landslide monitoring: The rotolon (Eastern Italian Alps) case study. Comput. Geosci. 2014, 63, 96–105. [Google Scholar] [CrossRef]
- Ueyama, J.; Freitas, H.; Faiçal, B.S.; Geraldo Filho, P.R.; Fini, P.; Pessin, G.; Gomes, P.H.; Villas, L.A. Exploiting the use of unmanned aerial vehicles to provide resilience in wireless sensor networks. IEEE Commun. Mag. 2014, 52, 81–87. [Google Scholar] [CrossRef]
- Marinho, M.A.; De Freitas, E.P.; da Costa, J.P.C.L.; De Almeida, A.L.F.; De Sousa, R.T. Using cooperative MIMO techniques and UAV relay networks to support connectivity in sparse Wireless Sensor Networks. In Proceedings of the 2013 International Conference on Computing, Management and Telecommunications (ComManTel), Ho Chi Minh City, Vietnam, 21–24 January 2013; pp. 49–54. [Google Scholar]
- Morgenthaler, S.; Braun, T.; Zhao, Z.; Staub, T.; Anwander, M. UAVNet: A mobile wireless mesh network using unmanned aerial vehicles. In Proceedings of the 2012 IEEE Globecom Workshops (GC Wkshps), Anaheim, CA, USA, 3–7 December 2012; pp. 1603–1608. [Google Scholar]
- Tuna, G.; Mumcu, T.V.; Gulez, K. Design strategies of unmanned aerial vehicle-aided communication for disaster recovery. In Proceeding of the 9th International Conference on High Capacity Optical Networks and Enabling Technologies (HONET), Istanbul, Turkey, 12–14 December 2012; pp. 115–119. [Google Scholar]
- Waharte, S.; Trigoni, N. Supporting search and rescue operations with UAVs. In Proceeding of the 2010 International Conference on Emerging Security Technologies (EST), Canterbury, UK, 6–7 September 2010; pp. 142–147. [Google Scholar]
- Tomic, T.; Schmid, K.; Lutz, P.; Domel, A.; Kassecker, M.; Mair, E.; Grixa, I.L.; Ruess, F.; Suppa, M.; Burschka, D. Toward a fully autonomous UAV: Research platform for indoor and outdoor urban search and rescue. IEEE Robot. Autom. Mag. 2012, 19, 46–56. [Google Scholar] [CrossRef]
- Erdos, D.; Erdos, A.; Watkins, S.E. An experimental UAV system for search and rescue challenge. IEEE Aerosp. Electron. Syst. Mag. 2013, 28, 32–37. [Google Scholar] [CrossRef]
- Allseen Alliance, AllJoyn Security 2.0 Feature High-Level Design. 2016. Available online: https://allseenalliance.org/ (accessed on 6 December 2016).
- Papadakis, P. Terrain traversability analysis methods for unmanned ground vehicles: A survey. Eng. Appl. Artif. Intell. 2013, 26, 1373–1385. [Google Scholar] [CrossRef]
- Yang, Z.; Zhang, P.; Chen, L. RFID-enabled indoor positioning method for a real-time manufacturing execution system using OS-ELM. Neurocomputing 2016, 174, 121–133. [Google Scholar] [CrossRef]
- Gualda, D.; Ureña, J.; García, J.C.; Lindo, A. Locally-referenced ultrasonic–LPS for localization and navigation. Sensors 2014, 14, 21750–21769. [Google Scholar] [CrossRef] [PubMed]
- Ozdenizci, B.; Coskun, V.; Ok, K. NFC internal: An indoor navigation system. Sensors 2015, 15, 7571–7595. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Cheng, R.S.; Hong, W.J.; Wang, J.S.; Lin, K.W. Seamless guidance system combining GPS, BLE beacon, and NFC technologies. Mob. Inf. Syst. 2016, 2016, 5032365. [Google Scholar] [CrossRef]
- Reco Beacon Homepage. Available online: http://reco2.me/ (accessed on 27 January 2017).
- iBeacon for Developers. Available online: http://developer.apple.com/ibeacon/ (accessed on 27 January 2017).
- Liu, J.W.S.; Chen, L.J.; Su, J.; Li, C.C.; Chu, E.T.H. BeDIPS: A building environment data based indoor positioning system. In Proceeding of the International Conference on Internet of Things (iThings 2015), Sydney, Australia, 11–13 December 2015. [Google Scholar]
- Murphy, R.R.; Stover, S. Rescue robots for mudslides: A descriptive study of the 2005 La Conchita mudslide response. J. Field Robot. 2008, 25, 3–16. [Google Scholar] [CrossRef]
- Sardouk, A.; Mansouri, M.; Merghem-Boulahia, L.; Gaiti, D.; Rahim-Amoud, R. Multi-agent system based wireless sensor network for crisis management. In Proceedings of the Global Telecommunications Conference (GLOBECOM 2010), Miami, FL, USA, 6–10 December 2010; Volume 2010, pp. 1–6. [Google Scholar]
- Dalmasso, I.; Galletti, I.; Giuliano, R.; Mazzenga, F. WiMAX networks for emergency management based on UAVs. In Proceedings of the 2012 IEEE First AESS European Conference on Satellite Telecommunications (ESTEL), Rome, Italy, 2–5 October 2012; pp. 1–6. [Google Scholar]
- Ye, J.; Hassan, T.M.; Carter, C.D.; Zarli, A. ICT for Energy Efficiency: The Case for Smart Buildings; Department of Civil and Building Engineering, Loughborough University: Loughborough, UK, 2008. [Google Scholar]
- Weng, T.; Agarwal, Y. From buildings to smart buildings—Sensing and actuation to improve energy efficiency. IEEE Des. Test Comput. 2012, 29, 36–44. [Google Scholar] [CrossRef]
- Certicom Research, Standards for Efficient Cryptography, SEC 1: Elliptic Curve Cryptography, Version 2.0, 21 May 2009. Available online: http://www.secg.org/sec1-v2.pdf (accessed on 5 April 2017).
- RFC 4422, Simple Authentication and Security Layer (SASL), June 2006. Available online: https://tools.ietf.org/html/rfc4422 (accessed on 28 March 2017).
- National Institute of Standards and Technology (NIST). Federal Information Processing Standards Publication 197; Announcing the Advanced Encrypition Standard (AES). Available online: http://nvlpubs.nist.gov/nistpubs/FIPS/NIST.FIPS.197.pdf (accessed on 1 August 2017).
- Constantine, A.B. Antenna Theory: Analysis and Design; John Wiley and Sons: New York, NY, USA, 1997. [Google Scholar]
- Apple Core Location. Available online: https://developer.apple.com/documentation/corelocation (accessed on 28 December 2016).
- Choi, J.I.; Yong, H.S. Real-time intragroup familiarity analysis model using beacon based on proximity. In Proceedings of the IEEE Annual Ubiquitous Computing, Electronics and Mobile Communication Conference (UEMCON), New York, NY, USA, 20–22 October 2016; pp. 1–5. [Google Scholar]
- Spreitzer, M.; Theimer, M. Providing Location Information in a Ubiquitous Computing Environment. In Proceedings of the 14th ACM Symposium on Operating System Principles, Asheville, NC, USA, 5–8 December 1994; Volume 27, pp. 270–283. [Google Scholar]
- Gruteser, M.; Schelle, G.; Jain, A.; Han, R.; Grunwald, D. Privacy-Aware Location Sensor Networks. In Proceedings of the 9th USENIX Workshop on Hot Topics in Operating Systems(HotOS IX), Lihue, HI, USA, 18–21 May 2003; Volume 3, pp. 163–168. [Google Scholar]
- Al-Muhtadi, J.; Campbell, R.; Kapadia, A.; Mickunas, M.D.; Yi, S. Routing through the mist: Privacy preserving communication in ubiquitous computing environments. In Proceedings of the 22nd International Conference on Distributed Computing Systems, Vienna, Austria, 2–5 July 2002; pp. 74–83. [Google Scholar]
- Deng, J.; Han, R.; Mishra, S. Countermeasures against traffic analysis attacks in wireless sensor networks. In Proceedings of the First International Conference on Security and Privacy for Emerging Areas in Communications Networks, SecureComm 2005, Athens, Greece, 5–9 September 2005; pp. 113–126. [Google Scholar]
- Jian, Y.; Chen, S.; Zhang, Z.; Zhang, L. Protecting receiver-location privacy in wireless sensor networks. In Proceedings of the INFOCOM 2007, 26th IEEE International Conference on Computer Communications, Barcelona, Spain, 6–12 May 2007; pp. 1955–1963. [Google Scholar]
- Beresford, A.R.; Stajano, F. Location privacy in pervasive computing. IEEE Pervasive Comput. 2003, 2, 46–55. [Google Scholar] [CrossRef]


| Source | Types of Functionalities | Service Area | User Interface | |||||
|---|---|---|---|---|---|---|---|---|
| Sensor | UAV | Monitoring | Alarm | Rescue | Security | |||
| UAV-EMOR (Our System) | O | O | O | O | O | O | Building, Outside | Smartphone App |
| [2] | O | O | O | Building | Smartphone App | |||
| [3] | O | O | O | O | Building | |||
| [4] | O | O | O | O | Building | |||
| [5] | O | O | Building | |||||
| [6] | O | O | O | O | Building | Smartphone App | ||
| [7] | O | O | O | Nature | ||||
| [9] | O | O | O | Nature | ||||
| [10] | O | O | O | Nature | Web | |||
| [11] | O | O | O | River | ||||
| Text | Image | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| Message Size (Byte) | 32 | 128 | 512 | 2048 | 10,240 | 473 | 824 | 2453 | 8530 | 10,703 |
| Encryption (ms) | 0.6 | 1.1 | 5 | 40 | 180 | 15 | 36.5 | 106 | 220.5 | 306 |
| Decryption (ms) | 0.6 | 0.9 | 5 | 40 | 180 | 15 | 36.5 | 106 | 220.5 | 306 |
| Text | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| Message Size (Byte) | 16 | 32 | 64 | 128 | 256 | 512 | 1024 | 2048 | 4096 | 10,240 |
| Encryption (ms) | 0.31 | 0.5 | 0.7 | 0.86 | 1.79 | 4.1 | 13.4 | 36 | 71 | 164 |
| Decryption (ms) | 0.31 | 0.49 | 0.69 | 0.86 | 1.77 | 4 | 13.3 | 36 | 70 | 164 |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Seo, S.-H.; Choi, J.-I.; Song, J. Secure Utilization of Beacons and UAVs in Emergency Response Systems for Building Fire Hazard. Sensors 2017, 17, 2200. https://doi.org/10.3390/s17102200
Seo S-H, Choi J-I, Song J. Secure Utilization of Beacons and UAVs in Emergency Response Systems for Building Fire Hazard. Sensors. 2017; 17(10):2200. https://doi.org/10.3390/s17102200
Chicago/Turabian StyleSeo, Seung-Hyun, Jung-In Choi, and Jinseok Song. 2017. "Secure Utilization of Beacons and UAVs in Emergency Response Systems for Building Fire Hazard" Sensors 17, no. 10: 2200. https://doi.org/10.3390/s17102200




