A Dependable Localization Algorithm for Survivable Belt-Type Sensor Networks
Abstract
:1. Introduction
- (1)
- We design a node deployment mechanism that could effectively save energy.
- (2)
- A hop-distance calculation method that can eliminate blurring is proposed.
- (3)
- We improve the accuracy of the proposed algorithm.
2. Topological Modeling
2.1. Model Requirements
- (1)
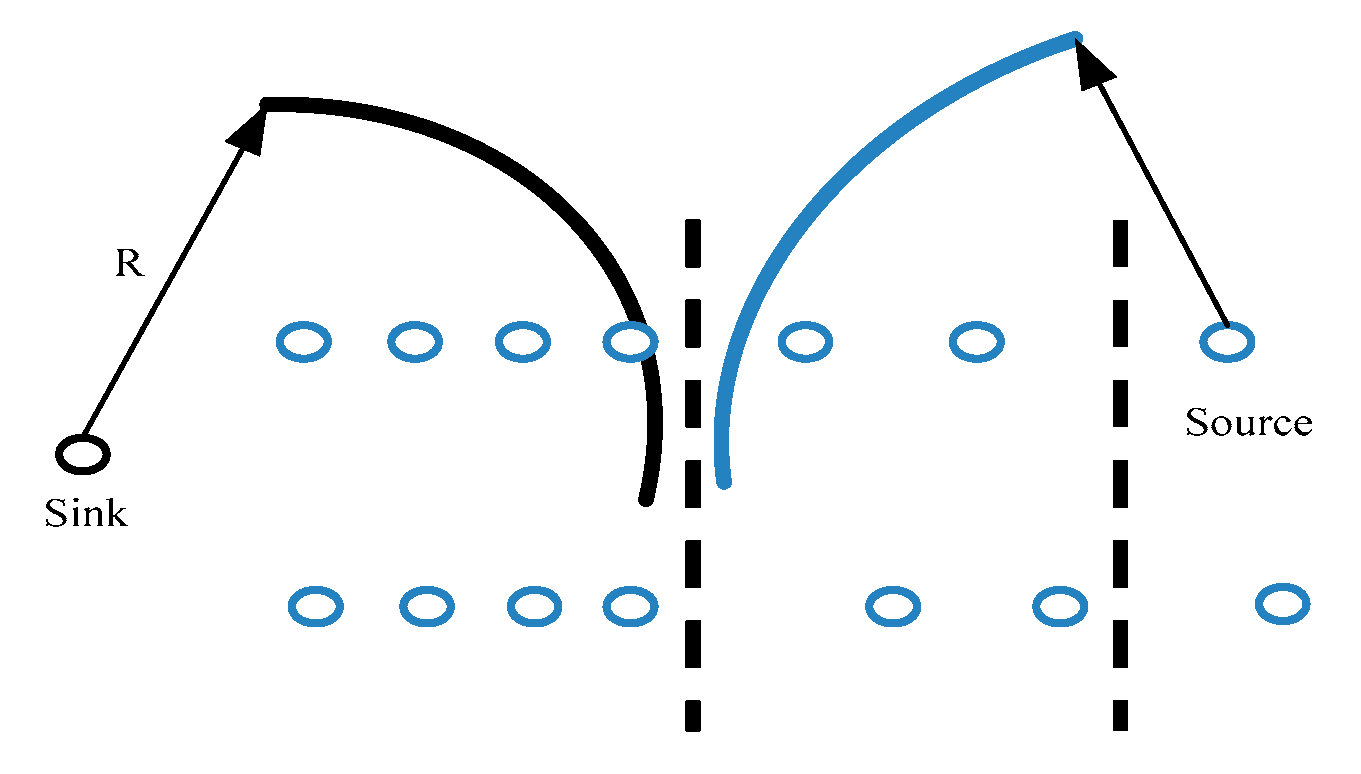
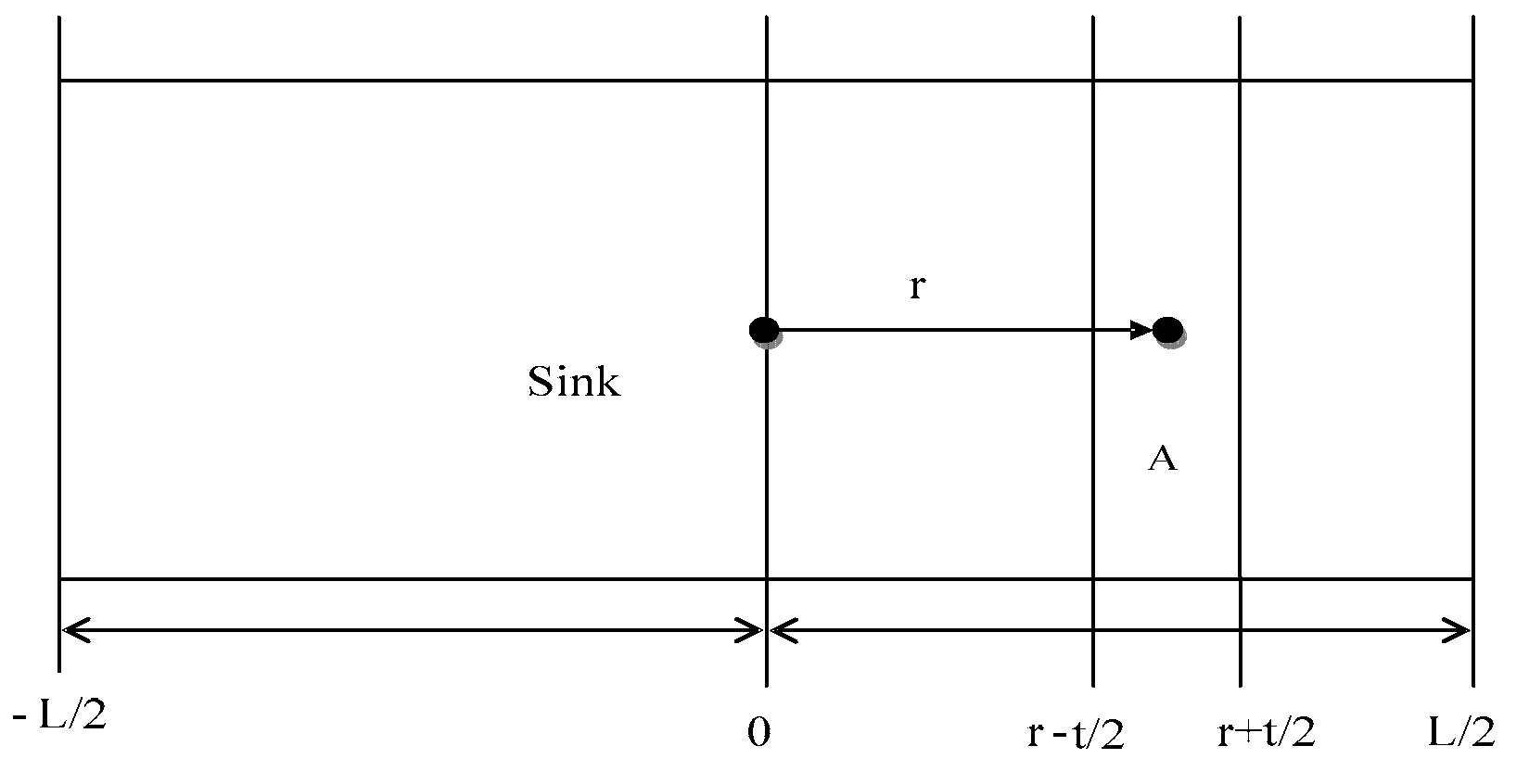
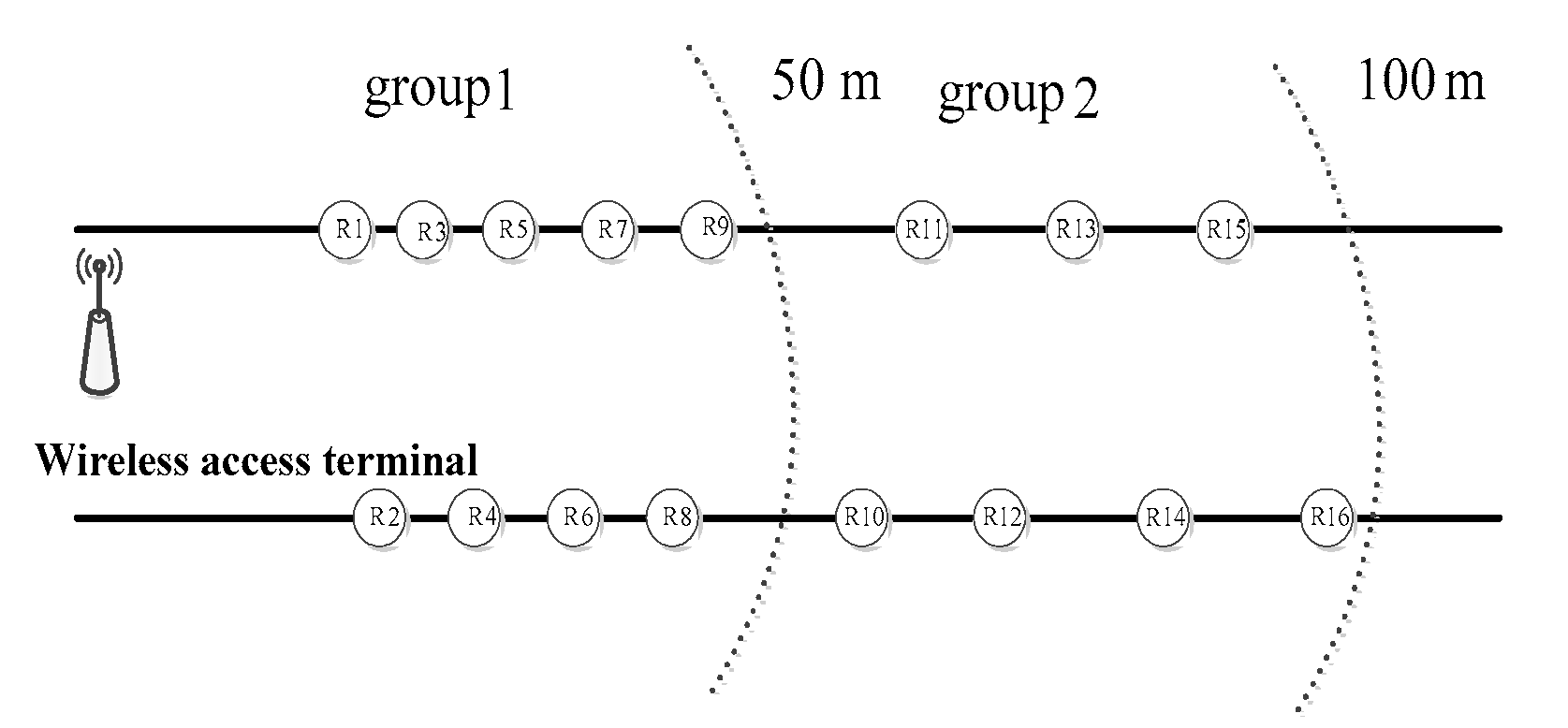
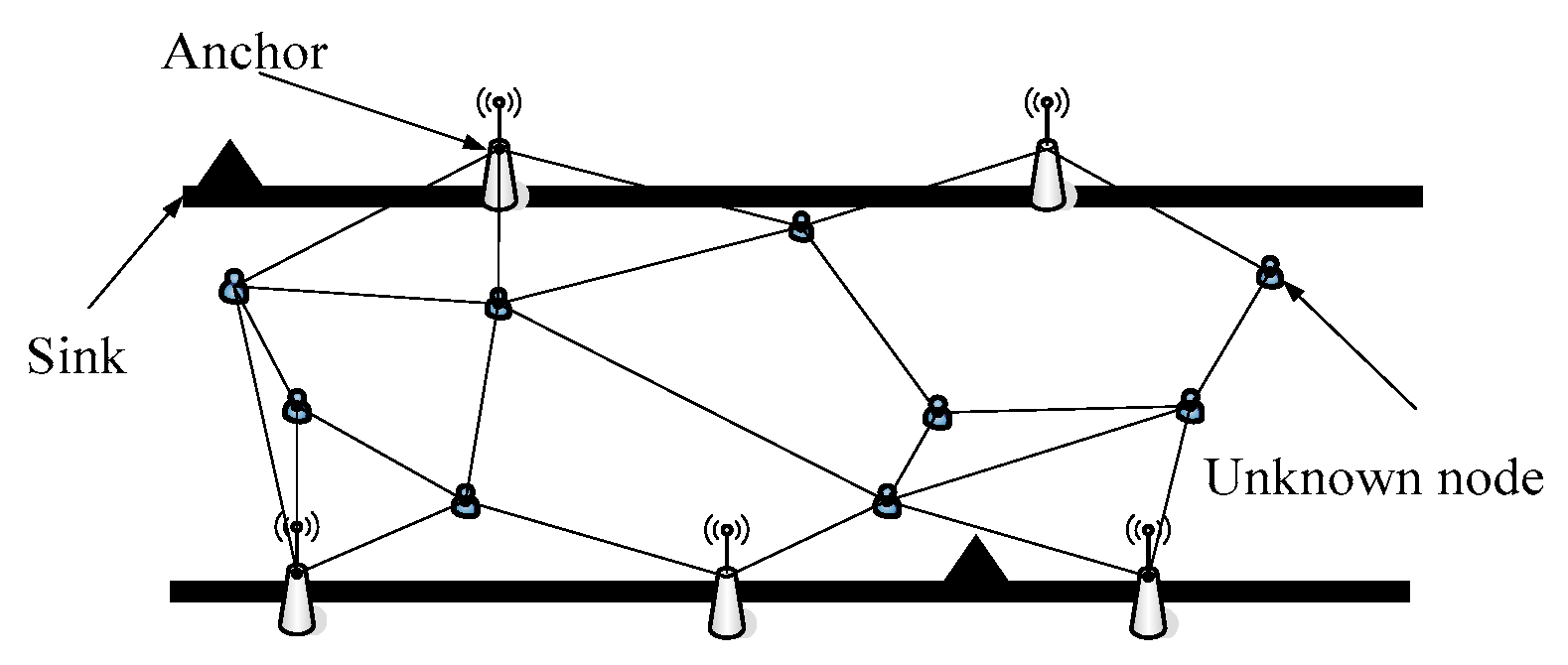
- The sensor nodes are distributed in a wide rectangular area (length is L and width is M, L >> M). The central gateway node is located in the middle of the strip area, and the sink node is located at the left side. The communication between the sensor node and the gateway node adopts the multi-hop mode, and the communication radius of the node is R. The distances between most sensor nodes and base stations are greater than the R of the nodes themselves. The nodes in the group can communicate directly with the sink nodes, and the communication distances between the intergroup nodes are one-hop. At this point, the sink node and the source node communication radius should be greater than the length of the group (shown in Figure 2).
- (2)
- Each sensor node has a unique ID, and they can carry out information perception and collection independently. They can also send their own information through the wireless channel to the gateway node. In a unit area, let the rate of data generation is and let the initial energy of the sensor node is .
2.2. Regional Energy Consumption
2.3. Node Deployment Method
2.4. Node Activation Mechanism
- (1)
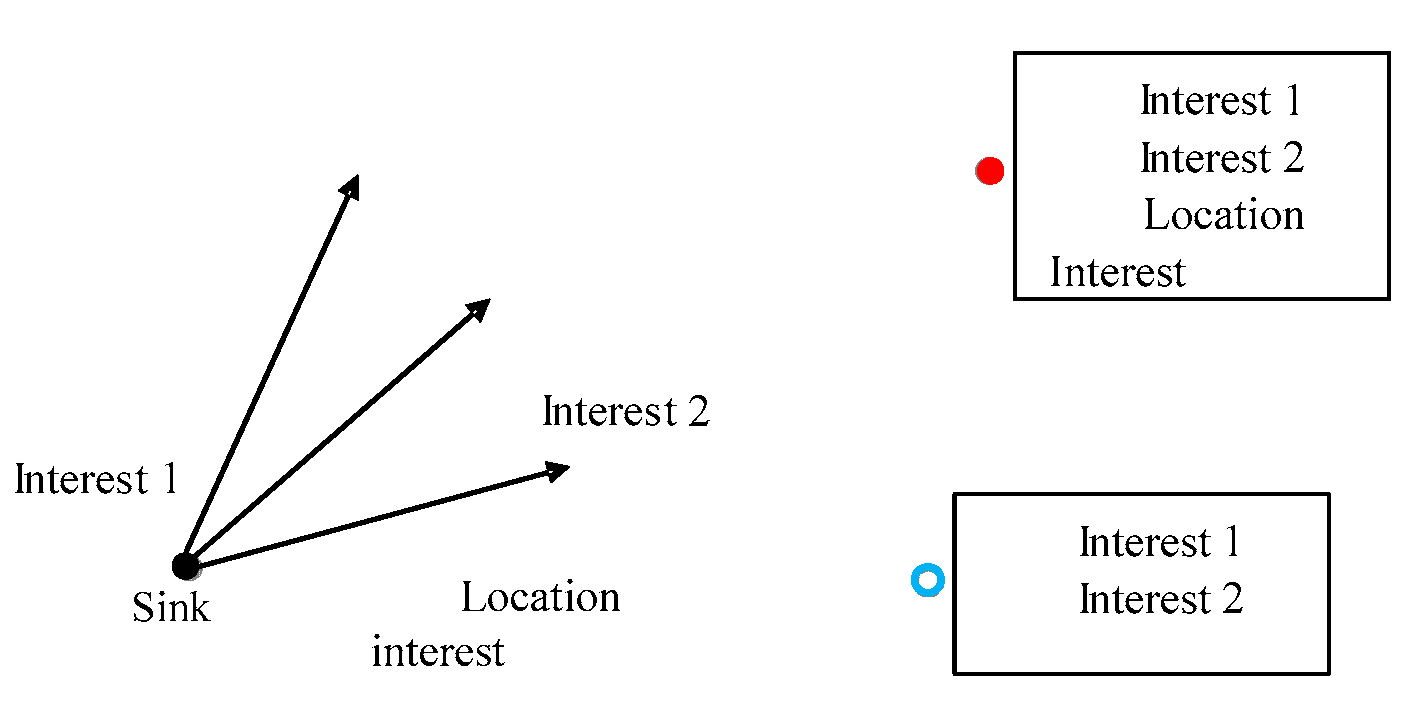
- When the target node enters the monitoring area, the sensor node starts searching and receiving the broadcast flood message “Request-MSG” issued by the target. According to the chronological order, sink node records the minimum hop number information “Hop-count” and its own identification information “Node-ID”. Subsequently, all information about anchor nodes in the neighbor area of the target node is stored and the initial positioning tree is constructed.
- (2)
- Based on the network topology of the target node and neighbor anchor nodes in the sensing area, the two sets of nodes which need to wake up or keep the sleeping (low power state) are estimated and sorted. Once they are determined, the message “Wakeup-MSG” is immediately sent to the target, wake up and activate anchor nodes with h hop from the target node, launch them into working state and holding. After all above actions are completed, the message “Prune-MSG” is sent to the target, and the anchor nodes are cleared once again when the locating tree is created.
- (3)
- According to the business type, we constantly and dynamically reconstruct the locating tree. As the target node moves and the sensing area continually changes, the anchor nodes that need to participate in the location continue to wake up or to remain dormant.
3. Hop-Distance Estimation Correction
- (1)
- Using the protocol of distance vector exchange in sensor networks, the hop count h and distanced information between unknown nodes and anchor nodes are collected. In the network, packets containing location information are forwarded until all nodes are aware of the location of each anchor node. With data fusion technology, data in all packages is associated.
- (2)
- According to the location information of other anchor nodes received by the known node, the hop-distance conversion model is established. Using the distance formula, we can estimate the actual distance about per hop, and then broadcast it over the entire network.
- (3)
- We can obtain the estimated distance between the unknown target node and each anchor node. By applying the mathematical method (triangular method and maximum likelihood estimation method), we can further estimate the position coordinates of the target node and correct the calibration.
3.1. Mechanism of Data Broadcasting
3.2. Correcting the Accumulated Values
3.3. Locating the Node and Fix the Result
4. Simulation and Analysis
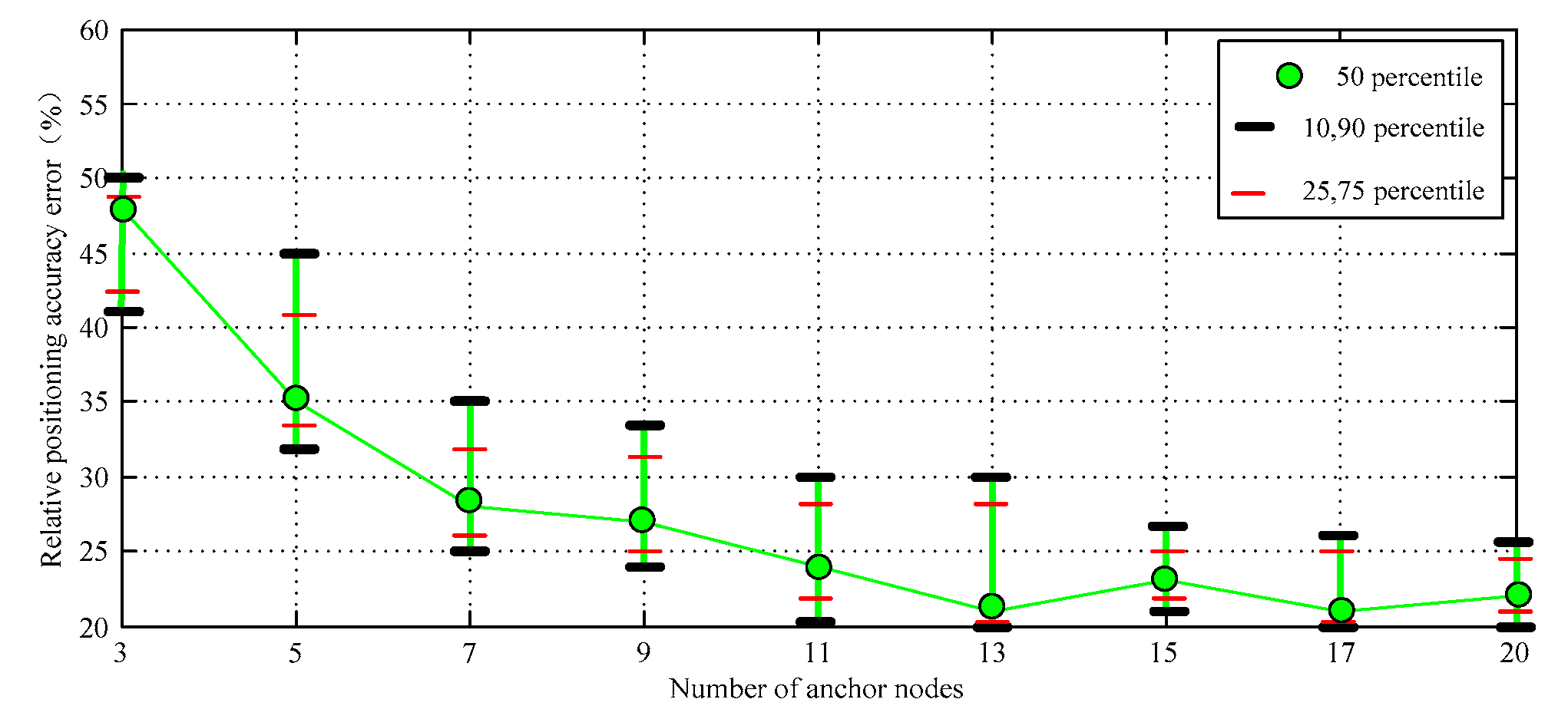
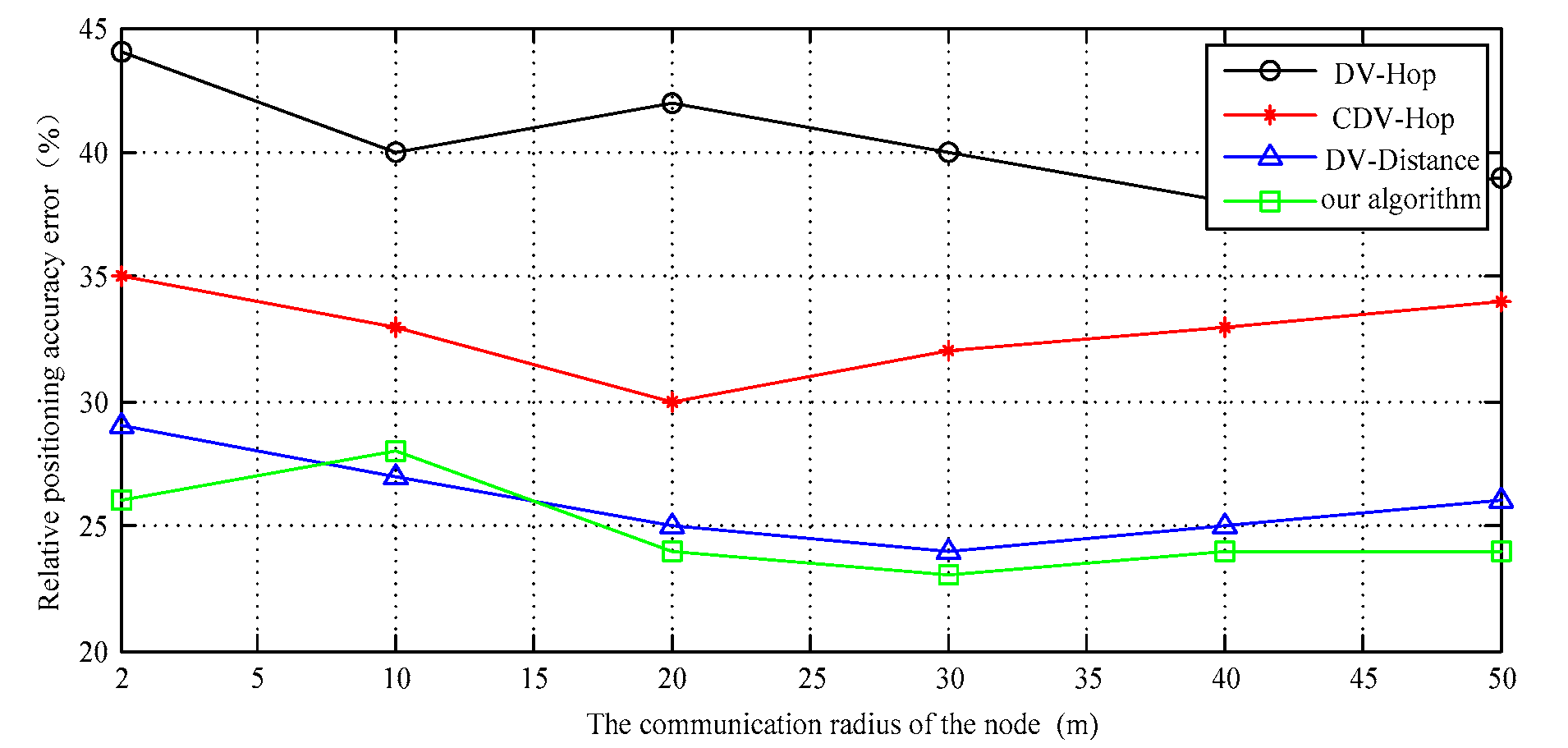
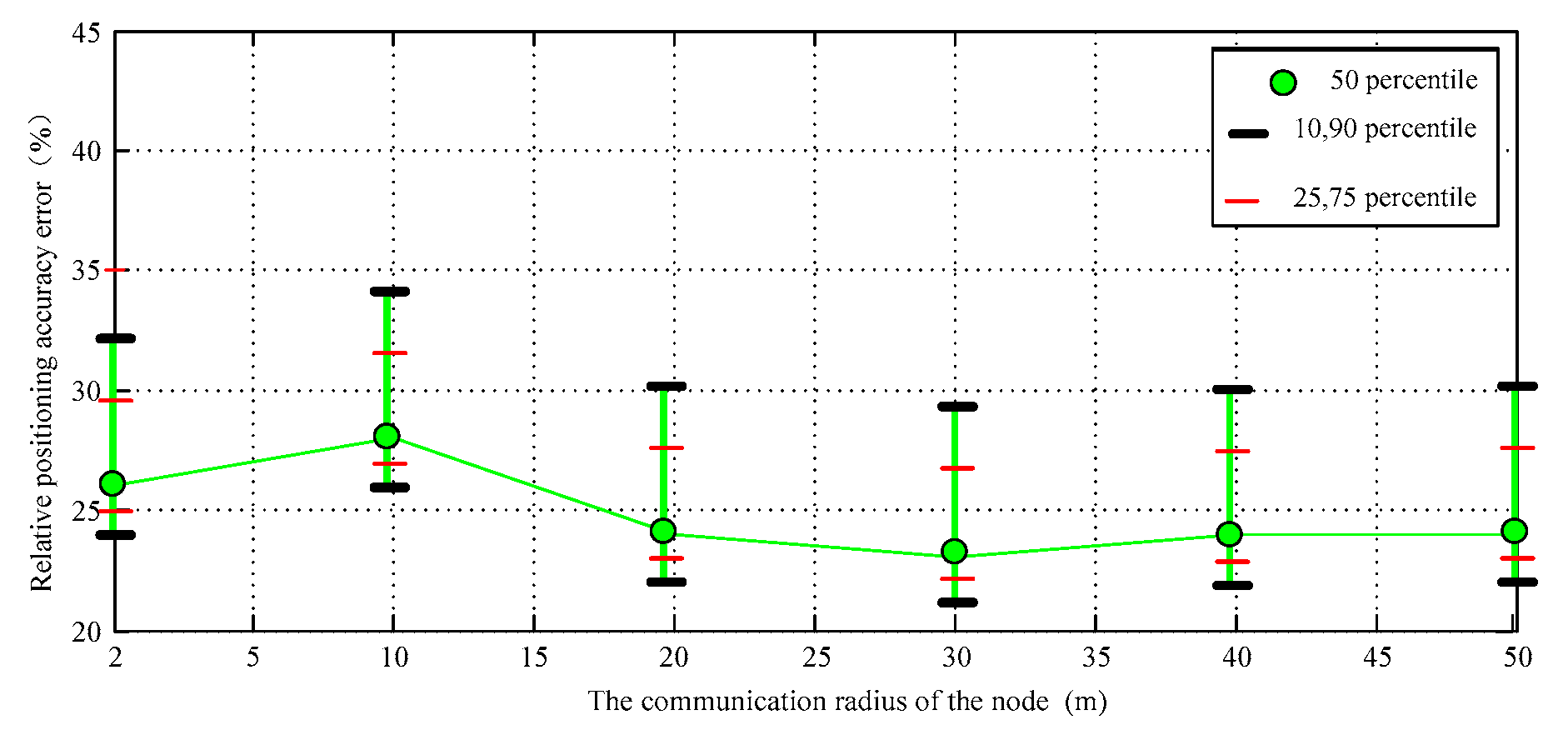
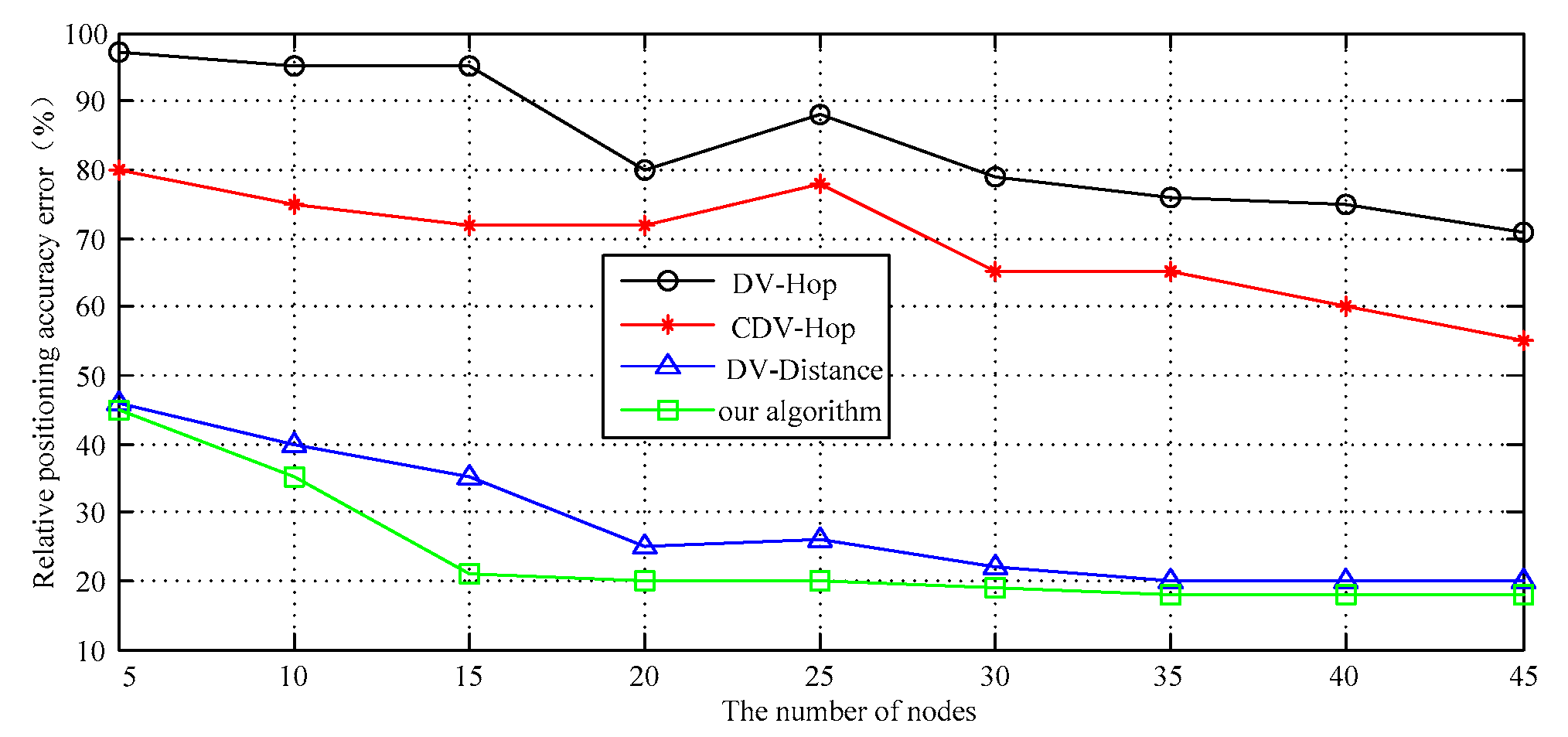
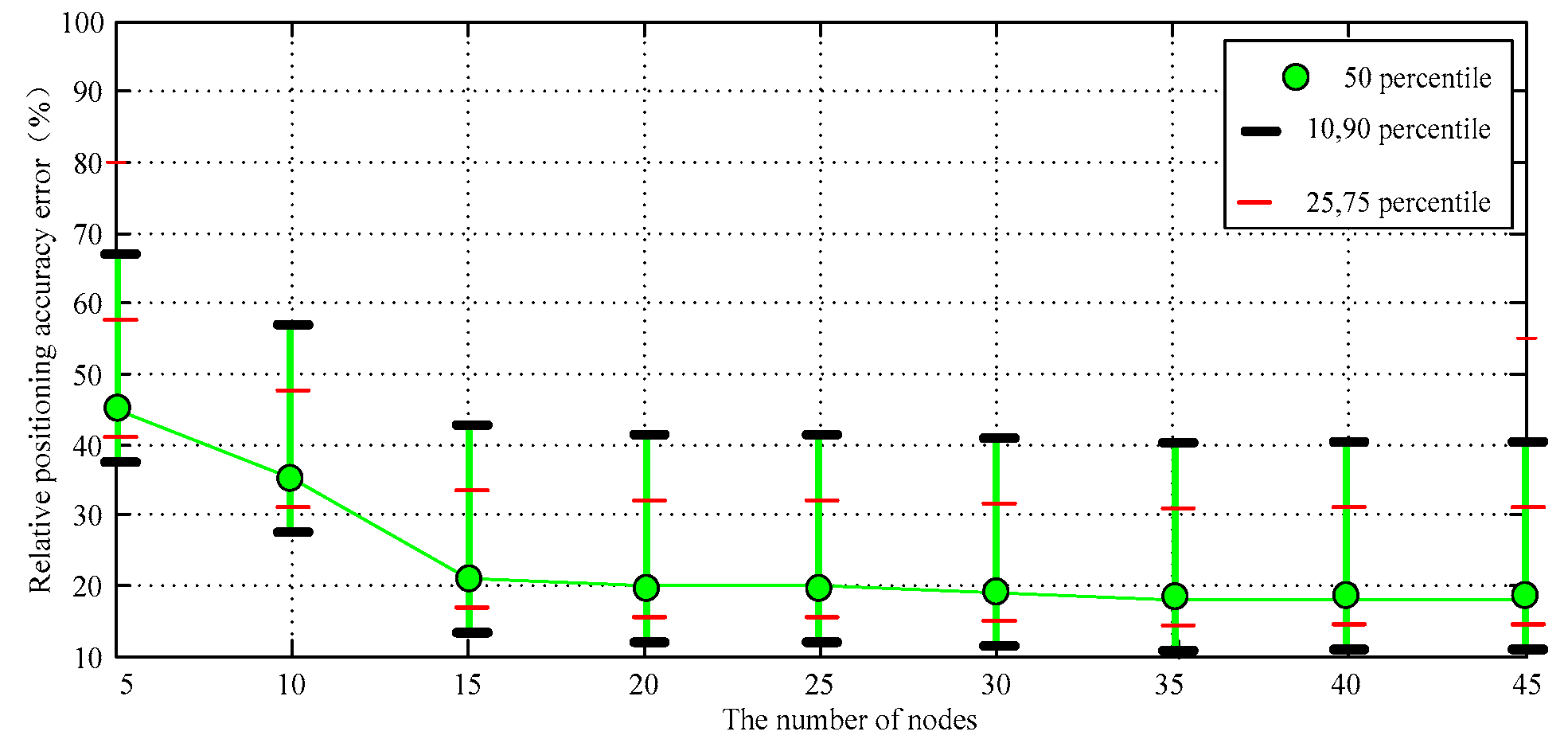
4.1. Relative Error of Positioning Accuracy
4.2. The Time Required to Locate Nodes
5. Conclusions
Acknowledgment
Author Contributions
Conflicts of Interest
References
- Assaf, A.E.; Zaidi, S.; Affes, S.; Kandil, N. Robust ANNs-Based WSN Localization in the Presence of Anisotropic Signal Attenuation. IEEE Wirel. Commun. Lett. 2016, 5, 504–507. [Google Scholar] [CrossRef]
- Wu, Y.I.; Wang, H.; Zheng, X. WSN Localization Using RSS in Three-Dimensional Space—A Geometric Method With Closed-Form Solution. IEEE Sens. J. 2016, 16, 4397–4404. [Google Scholar] [CrossRef]
- Jiang, J.A.; Zheng, X.Y.; Chen, Y.F.; Wang, C.H.; Chen, P.T.; Chuang, C.L.; Chen, C.P. A distributed RSSI-based localization using a dynamic circle expanding mechanism. IEEE Sens. J. 2013, 13, 3754–3766. [Google Scholar] [CrossRef]
- Song, F.; Zhou, Y.T.; Kong, K.; Zheng, Q.; You, I. Smart collaborative connection management for identifier-based network. IEEE Access 2017, 5, 7936–7949. [Google Scholar] [CrossRef]
- Singh, A.; Verma, S. Graph Laplacian Regularization with Procrustes Analysis for Sensor Node Localization. IEEE Sens. J. 2017, 17, 5367–5376. [Google Scholar] [CrossRef]
- Song, F.; Huang, D.; Zhou, H.; Zhang, H.; You, I. An Optimization-based Scheme for Efficient Virtual Machine Placement. Int. J. Parallel Program. 2014, 42, 853–872. [Google Scholar] [CrossRef]
- Sahu, P.K.; Wu, E.H.K.; Sahoo, J. DuRT: Dual RSSI trend based localization for wireless sensor networks. IEEE Sens. J. 2013, 13, 3115–3123. [Google Scholar] [CrossRef]
- Cheng, T.; Li, P.; Zhu, S.; Torrieri, D. M-cluster and X-ray: Two methods for multi-jammer localization in wireless sensor networks. Int. Comput. Aided Eng. 2014, 21, 19–34. [Google Scholar]
- Wang, Q.; Wei, X.; Fan, J.; Wang, T.; Sun, Q. A step further of PDR-based jammer localization through dynamic power adaption. In Proceedings of the 11th International Conference on Wireless Communications, Networking and Mobile Computing (WiCOM 2015), Shanghai, China, 21–23 September 2015; pp. 651–654. [Google Scholar]
- Stephan, S.; Armin, D.; Christian, M. Positioning in Wireless Communications Systems; Wiley: Chichester, UK, 2014; pp. 1–20. [Google Scholar]
- CamLy, N.; Orestis, G.; Yusuke, D. Maximum likelihood based multihop localization in wireless sensor networks. In Proceedings of the IEEE International Conference on Communications (ICC), London, UK, 8–12 June 2015; pp. 6663–6668. [Google Scholar]
- Cota-Ruiz, J.; Rivas-Perea, P.; Sifuentes, E. A Recursive Shortest Path Routing Algorithm with Application for Wireless Sensor Network Localization. IEEE Sens. J. 2016, 16, 4631–4637. [Google Scholar] [CrossRef]
- He, S.; Chan, S.H.G. Wi-Fi fingerprint-based indoor positioning: Recent advances and comparisons. IEEE Commun. Surv. Tutor. 2016, 18, 466–490. [Google Scholar] [CrossRef]
- Song, F.; Li, R.; Zhou, H. Feasibility and Issues for Establishing Network-based Carpooling Scheme. Pervasive Mob. Comput. 2015, 24, 4–15. [Google Scholar] [CrossRef]
- Song, F.; Zhang, Y.; An, Z.; Zhou, H.; You, I. The Correlation Study for Parameters in Four Tuples. Int. J. Ad Hoc Ubiquitous Comput. 2015, 19, 38–49. [Google Scholar] [CrossRef]
- Abu-Mahfouz, A.; Hancke, G. ALWadHA Localisation Algorithm: Yet More Energy Efficient. IEEE Access 2017, 5, 6661–6667. [Google Scholar] [CrossRef]
- Garcia, M.; Martinez, C.; Tomas, J.; Lloret, J. Wireless Sensors Self-Location in an Indoor WLAN Environment. In Proceedings of the International Conference on Sensor Technologies and Applications, SensorComm2007, Valencia, Spain, 14–20 October 2007; pp. 146–151. [Google Scholar]
- Garcia, M.; Tomas, J.; Boronat, F.; Lloret, J. The Development of Two Systems for Indoor Wireless Sensors Self-location. Ad Hoc Sens. Wirel. Netw. 2009, 8, 235–258. [Google Scholar]
- Domingoperez, F.; Lazarogalilea, J.L.; Bravo, I.; Gardel, A.; Rodriguez, D. Optimization of the Coverage and Accuracy of an Indoor Positioning System with a Variable Number of Sensors. Sensors 2016, 16, 934. [Google Scholar] [CrossRef]
- Zhang, Q.; Wan, J.; Wang, D. Sparse recovery formulation for secure distance-based localization in the presence of cheating anchors. J. Wirel. Netw. 2017, 5, 1–12. [Google Scholar] [CrossRef]
- Li, J.; Liu, Y.; Qian, Z.H.; Lu, C.G. Improved DV-Hop localization algorithm based on two communication ranges for wireless sensor network. J. Jilin Univ. (Eng. Technol. Ed.) 2014, 2, 502–507. [Google Scholar]
- Wu, J.; Chen, H.; Lou, W.; Wang, Z.; Wang, Z. Label-based DV-Hop localization against wormhole attacks in wireless sensor networks. In Proceedings of the 5th International Conference on Networking, Architecture and Storage (NAS), Macau, China, 15–17 July 2010; pp. 79–88. [Google Scholar]
- Kumar, S.; Lobiyal, D. An advanced DV-hop localization algorithm for wireless sensor networks. Wirel. Pers. Commun. 2012, 71, 1365–1385. [Google Scholar] [CrossRef]
- Huang, Z.; Liu, S.; Mao, X.; Chen, K.; Li, J. Insight of the protection for data security under selective opening attacks. Inf. Sci. 2017, 412–413, 223–241. [Google Scholar] [CrossRef]
- Li, J.; Zhang, Y.; Chen, X.; Xiang, Y. Secure attribute-based data sharing for resource-limited users in cloud computing. Comput. Secur. 2018, 72, 1–12. [Google Scholar] [CrossRef]
- Woo, H.; Lee, S.; Lee, C. Range-free localization with isotropic distance scaling in wireless sensor networks. In Proceedings of the International Conference on Information Networking, Bangkok, Thailand, 28–30 January 2013; pp. 632–636. [Google Scholar]
- Liao, L.; Chen, W.; Zhang, C.; Zhang, L.; Xuan, D.; Jia, W. Two Birds with One Stone: Wireless Access Point Deployment for Both Coverage and Localization. IEEE Trans. Veh. Technol. 2011, 60, 2239–2252. [Google Scholar] [CrossRef]
- Shahzad, F.; Sheltami, T.R.; Shakshuki, E.M. Multi-objective optimization for a reliable localization scheme in wireless sensor networks. J. Commun. Net. 2016, 18, 796–805. [Google Scholar]
- Heinzelman, W.; Chandrakasan, A.; Balakrishnan, H. An application specific protocol architecture for wireless microsensor networks. IEEE Trans. Wirel. Commun. 2002, 1, 660–670. [Google Scholar] [CrossRef]
- Zhao, Y.H.; Qian, Z.H.; Shang, X.H.; Chen, C. PSO localization algorithm for WSN nodes based on modifying average hop distances. J. Commun. 2013, 34, 107–116. [Google Scholar]
- Abouzar, P.; Michelson, D.G.; Hamdi, M. RSSI-Based Distributed Self-Localization for Wireless Sensor Networks Used in Precision Agriculture. IEEE Trans. Wirel. Commun. 2016, 15, 6638–6650. [Google Scholar] [CrossRef]
- Wang, Q.; Zhuang, Y.; Gu, J.J. Target Positioning Algorithm Based on WSN in Perimeter Intrusion Detection. Comput. Eng. 2013, 39, 39–44. [Google Scholar]
- Agashe, A.A.; Patil, R.S. An Optimum DV Hop Localization Algorithm for Variety of Topologies in Wireless Sensor Networks. Int. J. Comput. Sci. Eng. 2012, 4, 957–961. [Google Scholar]
- Ayllón, D.; Sánchez-Hevia, H.; Gil-Pita, R. Indoor blind localization of smartphones by means of sensor data fusion. In Proceedings of the Sensors Applications Symposium, Catania, Italy, 20–22 April 2016. [Google Scholar]
- Nicoiescu, D.; Nath, B. DV based positioning in ad hoc networks. J. Telecommun. Syst. 2003, 22, 267–280. [Google Scholar] [CrossRef]
- Gui, L.; Val, T.; Wei, A. Improving Localization Accuracy Using Selective 3-Anchor DV-Hop Algorithm. In Proceedings of the Vehicular Technology Conference, Budapest, Hungary, 15–18 May 2011; pp. 1–5. [Google Scholar]


| Algorithm Type | The Number of Anchor Nodes | |||
|---|---|---|---|---|
| 3 | 7 | 10 | 15 | |
| DV-Hop | 200 ms | 210 ms | 270 ms | 310 ms |
| C DV-Hop | 400 ms | 420 ms | 550 ms | 590 ms |
| DV-Distance | 1350 ms | 1500 ms | 1820 ms | 1970 ms |
| Our algorithm | 1200 ms | 1200 ms | 1500 ms | 1550 ms |
| Algorithm Type | The Number of Sensor Nodes | |||
|---|---|---|---|---|
| 10 | 20 | 30 | 50 | |
| DV-Hop | 1200 ms | 1200 ms | 1500 ms | 1500 ms |
| C DV-Hop | 900 ms | 1000 ms | 1600 ms | 1750 ms |
| DV-Distance | 1400 ms | 1500 ms | 1700 ms | 17,500 ms |
| Our algorithm | 1700 ms | 1750 ms | 1900 ms | 1950 ms |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhu, M.; Song, F.; Xu, L.; Seo, J.T.; You, I. A Dependable Localization Algorithm for Survivable Belt-Type Sensor Networks. Sensors 2017, 17, 2767. https://doi.org/10.3390/s17122767
Zhu M, Song F, Xu L, Seo JT, You I. A Dependable Localization Algorithm for Survivable Belt-Type Sensor Networks. Sensors. 2017; 17(12):2767. https://doi.org/10.3390/s17122767
Chicago/Turabian StyleZhu, Mingqiang, Fei Song, Lei Xu, Jung Taek Seo, and Ilsun You. 2017. "A Dependable Localization Algorithm for Survivable Belt-Type Sensor Networks" Sensors 17, no. 12: 2767. https://doi.org/10.3390/s17122767





