SOUNET: Self-Organized Underwater Wireless Sensor Network
Abstract
:1. Introduction
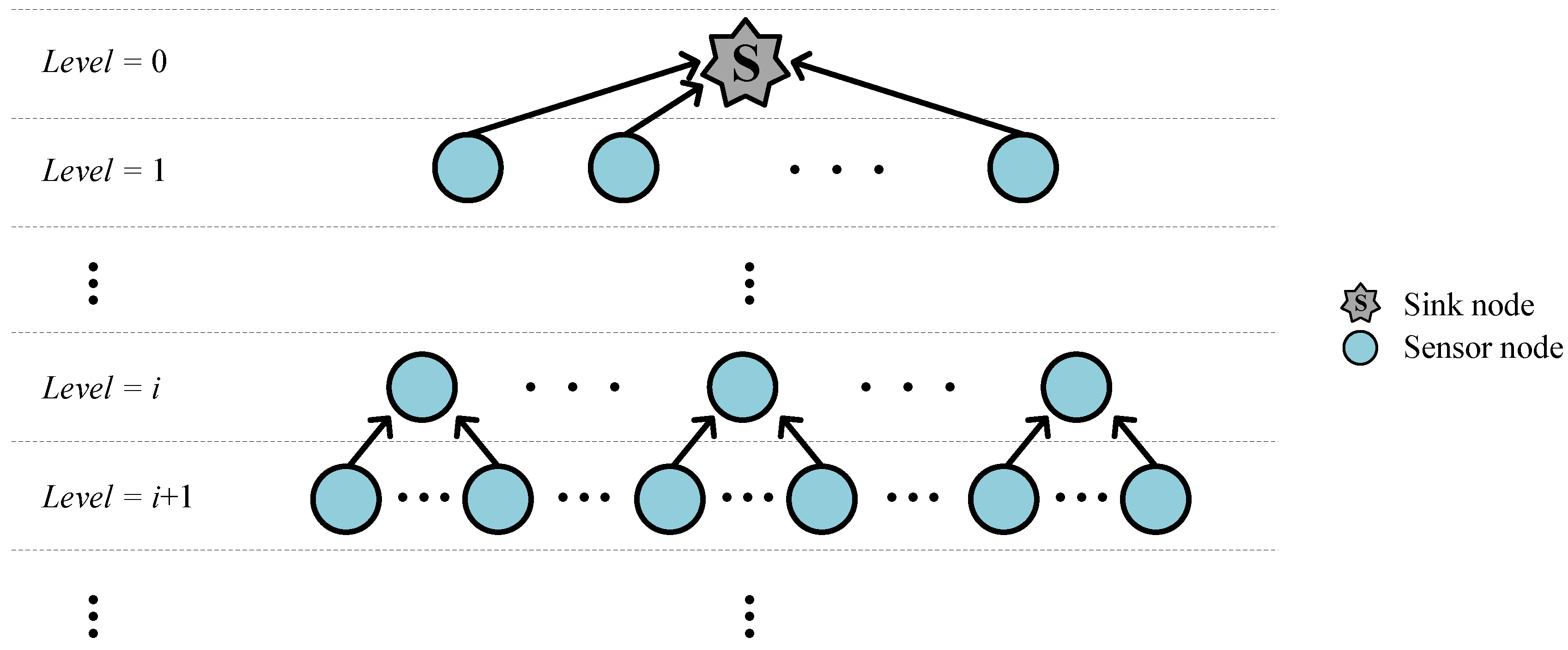
2. System Description
3. Problem Statement
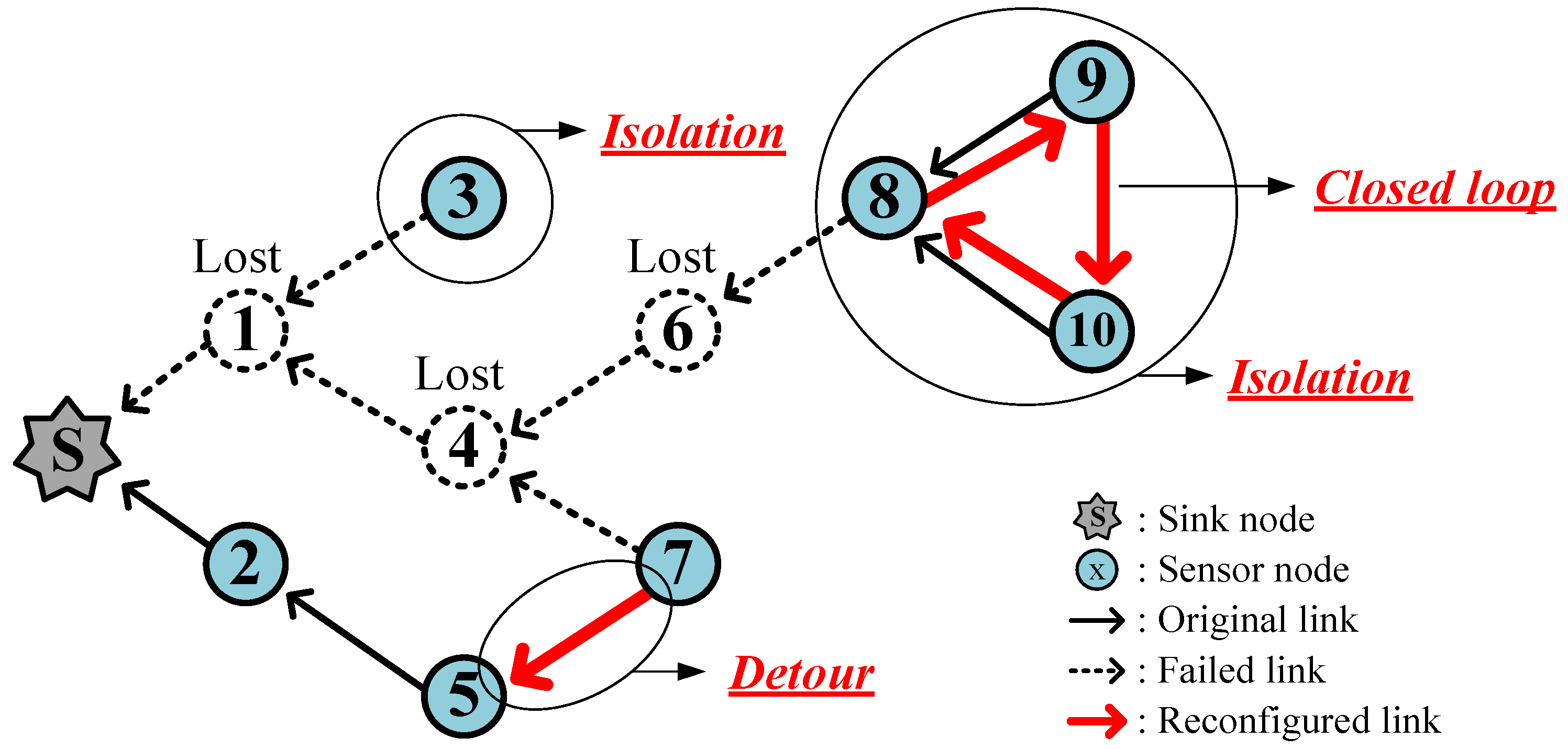
3.1. Detour and Isolation
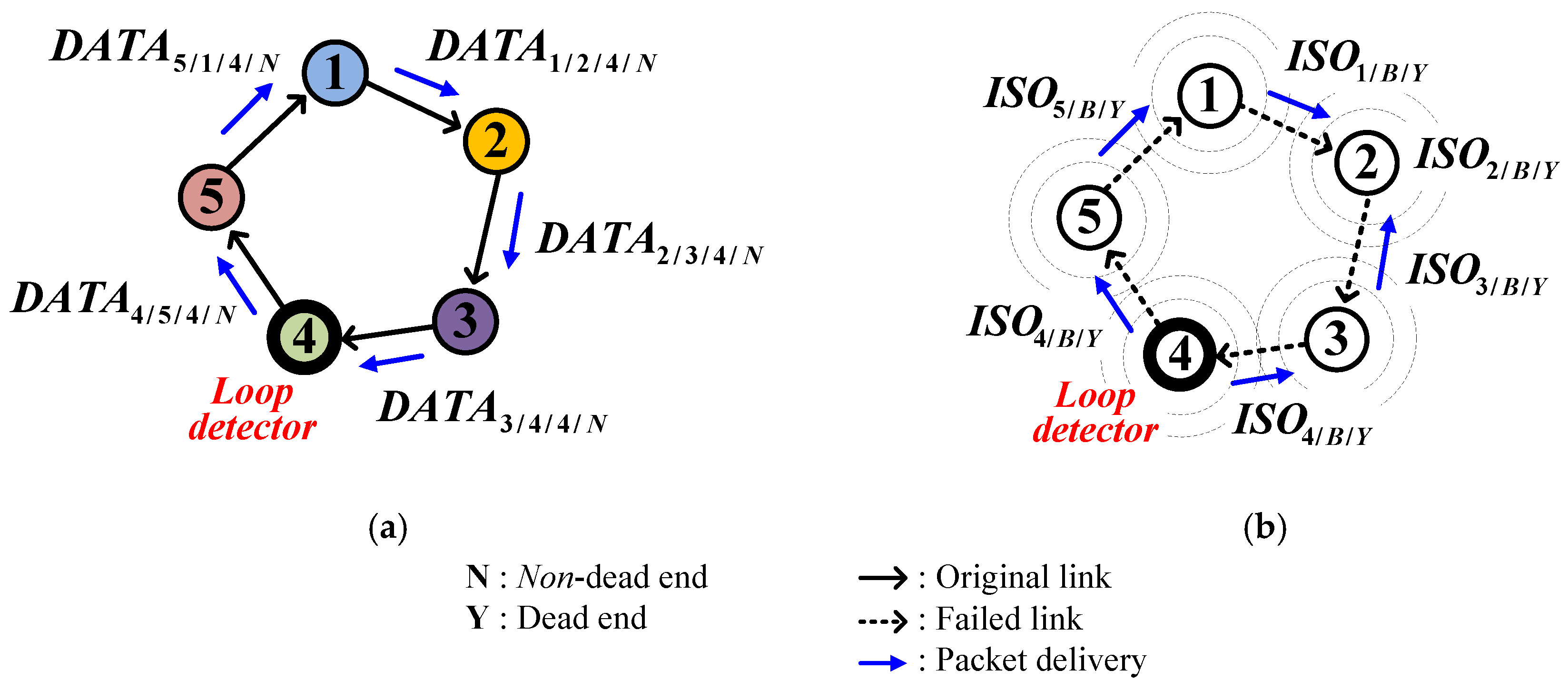
3.2. Closed Loops
3.3. Network Joining Delay
4. Construction and Operation of SOUNET
4.1. Phase 1: Network Initialization
4.2. Phase 2: Network Maintenance
4.2.1. Data Transfer
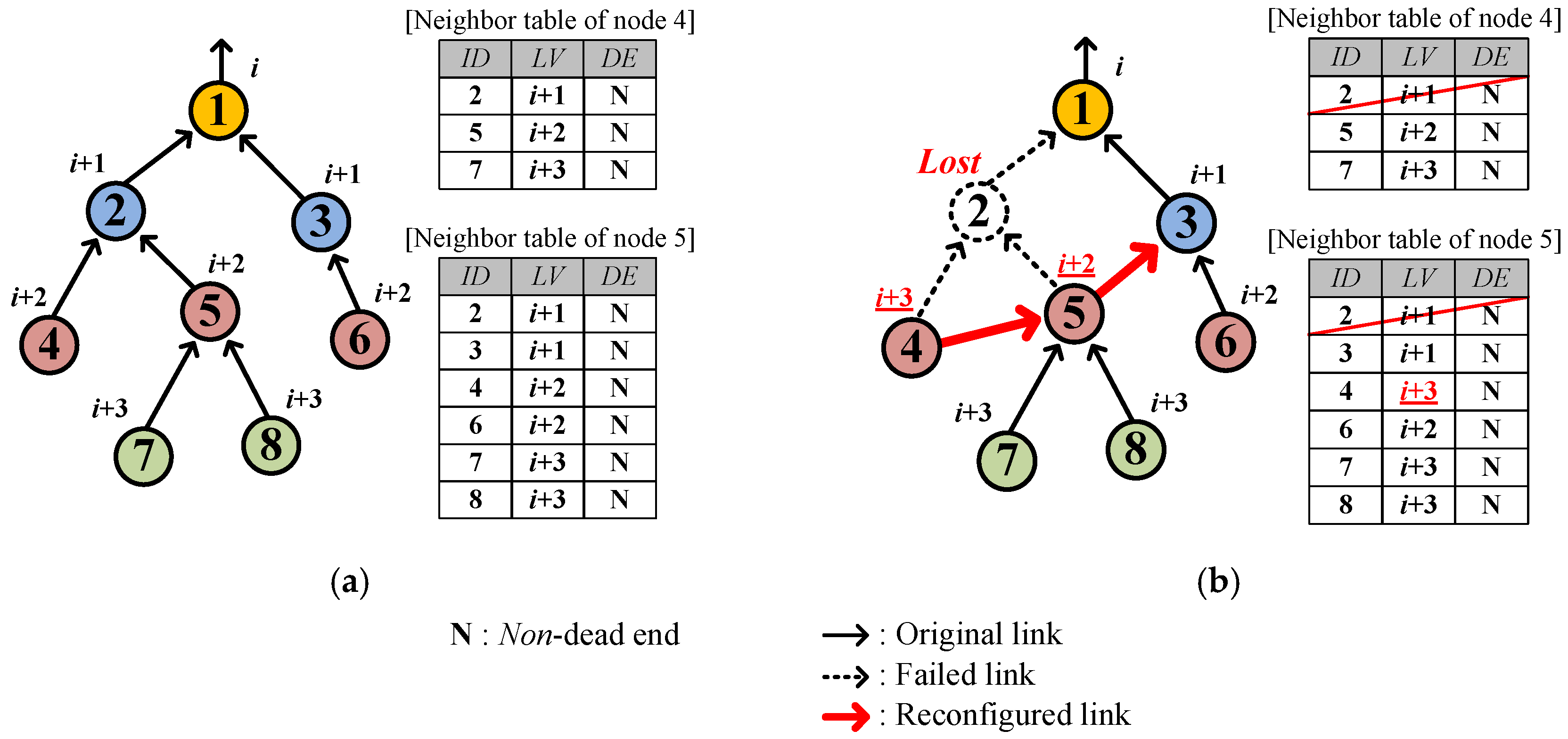
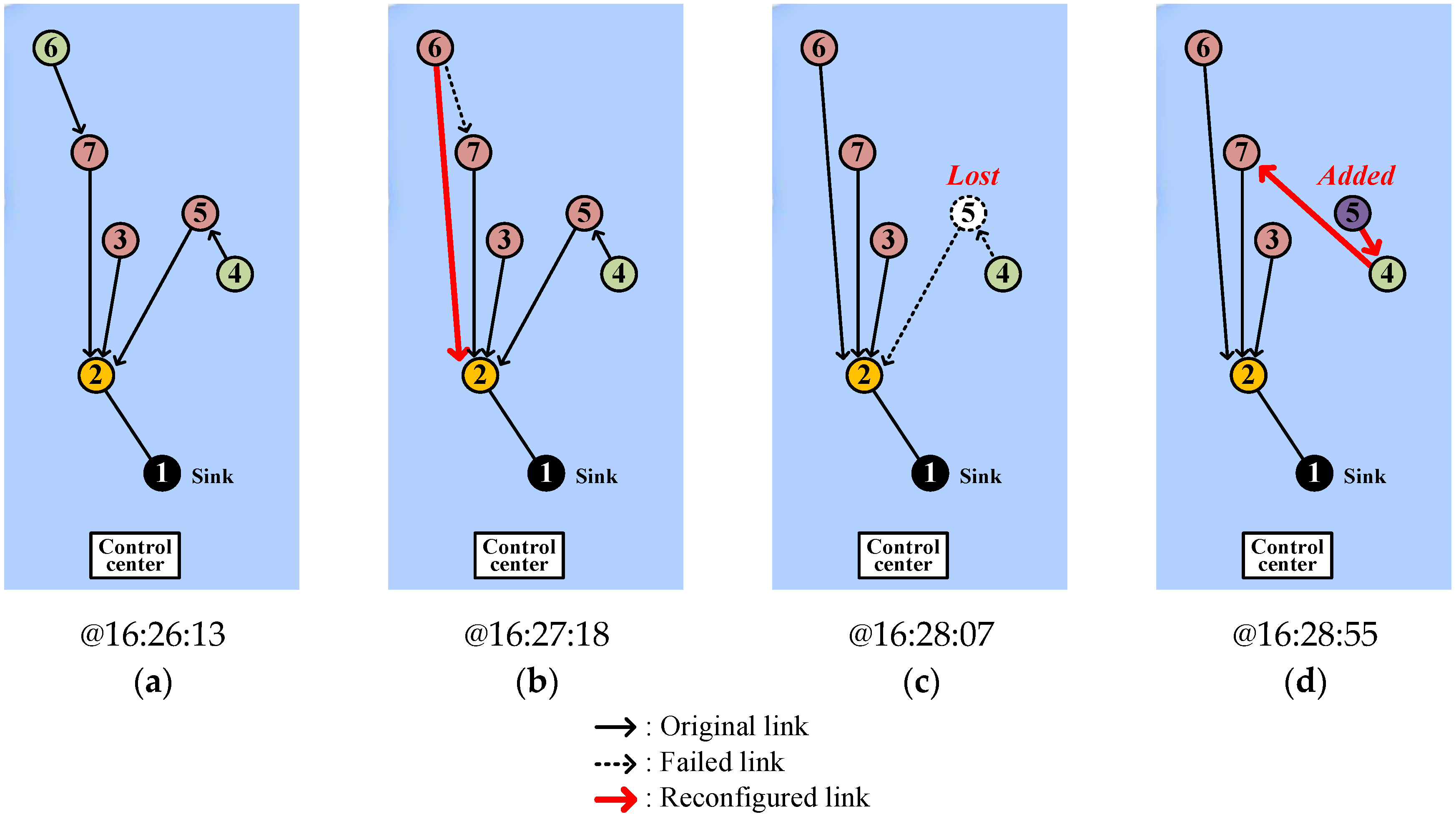
4.2.2. Link Hole Recovery
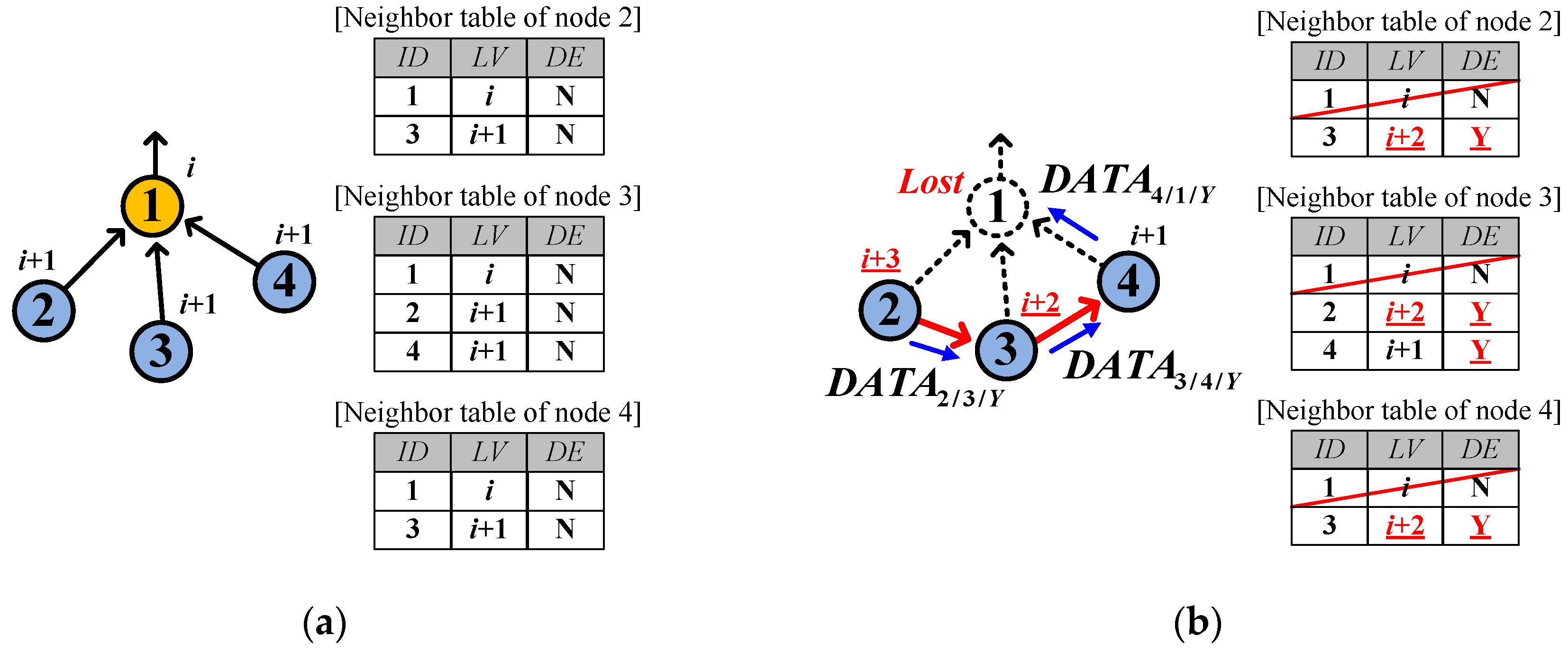
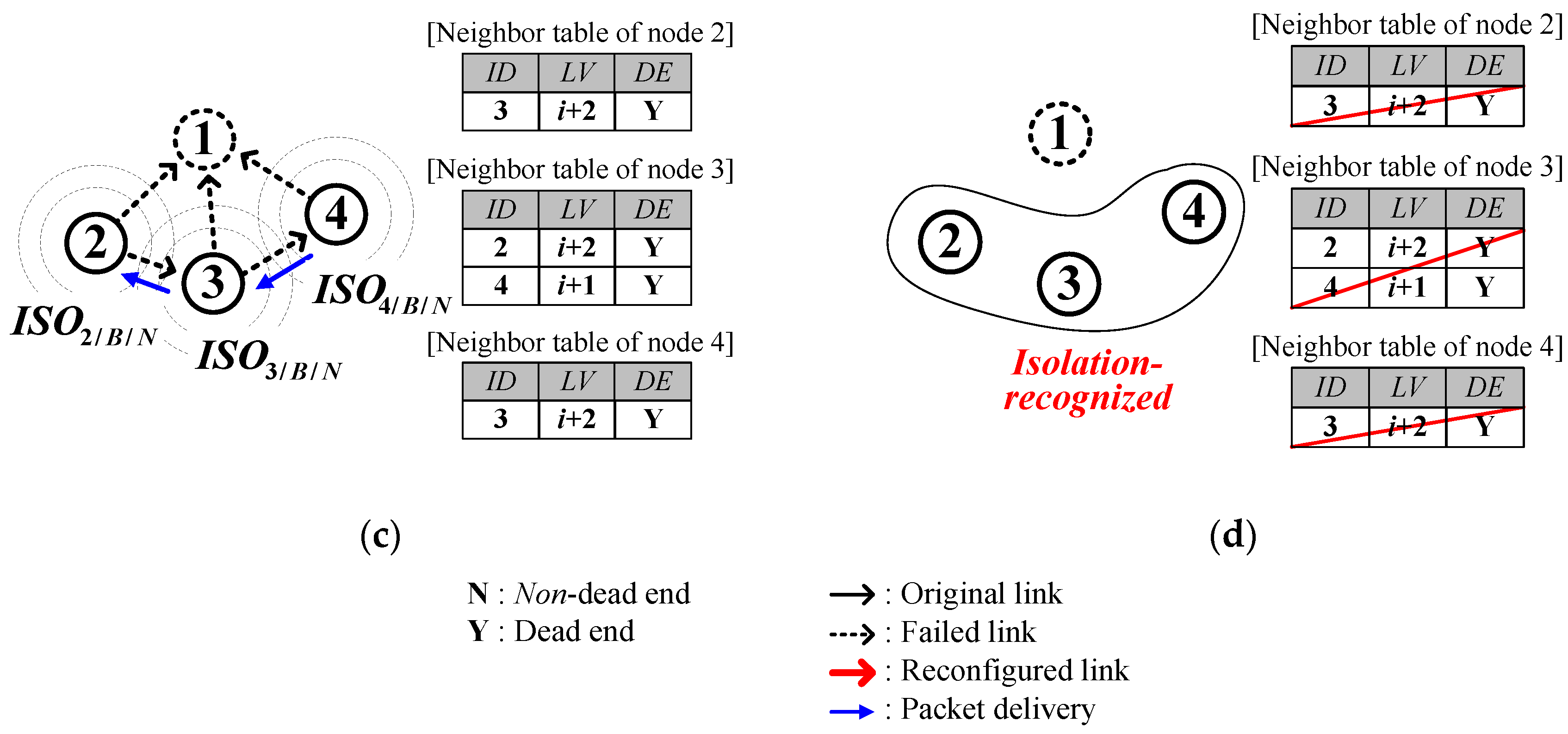
4.2.3. Isolation Recognition
- Receiving ISO from the parent.
- Receiving DATA back from the parent who becomes a dead end.
- reaches .
- Receiving a DATA of which source ID is its own.
- Receiving a DATA of which value reaches the threshold, .
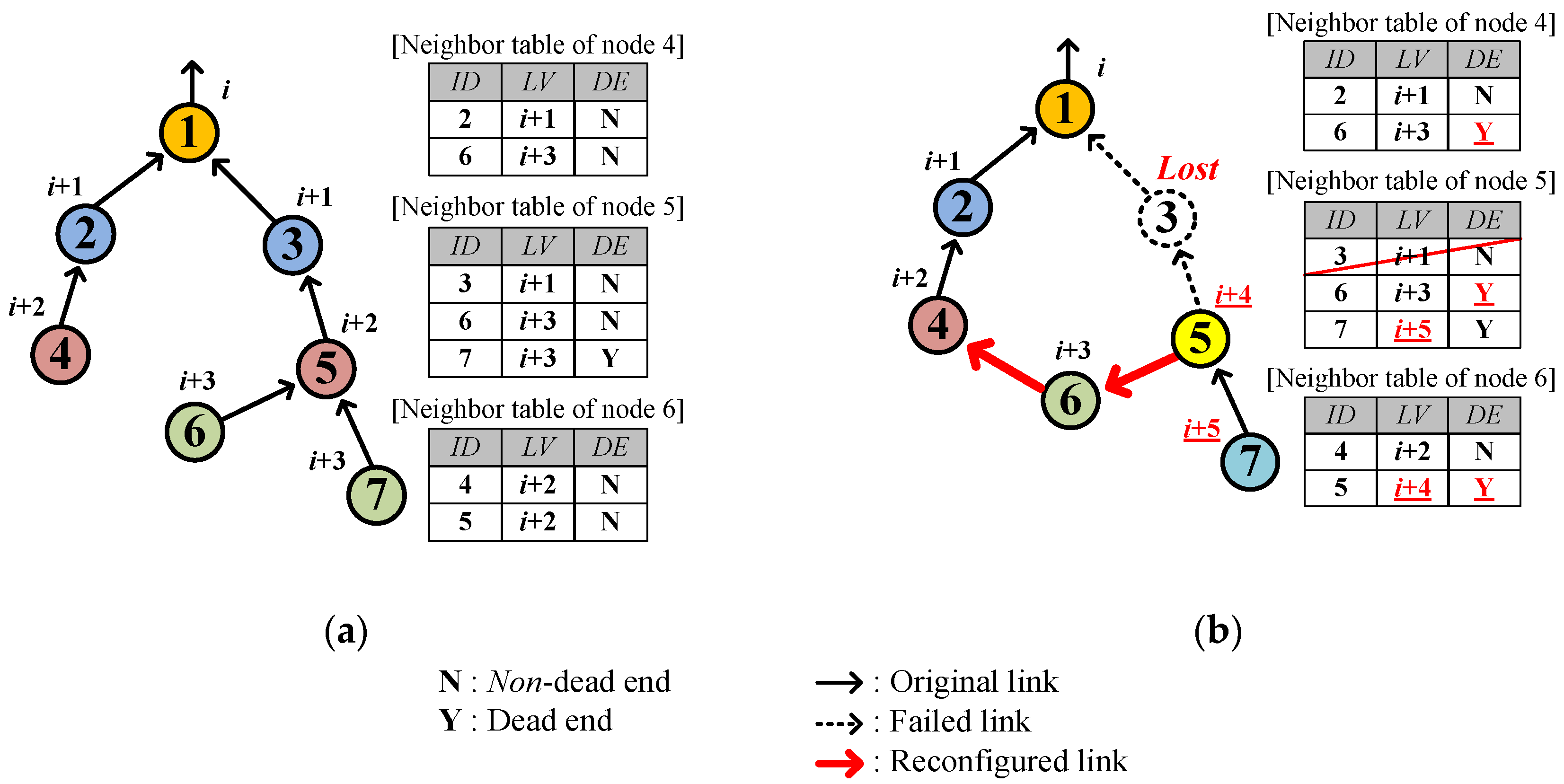
4.2.4. Temporary Closed Loop and Its Cure
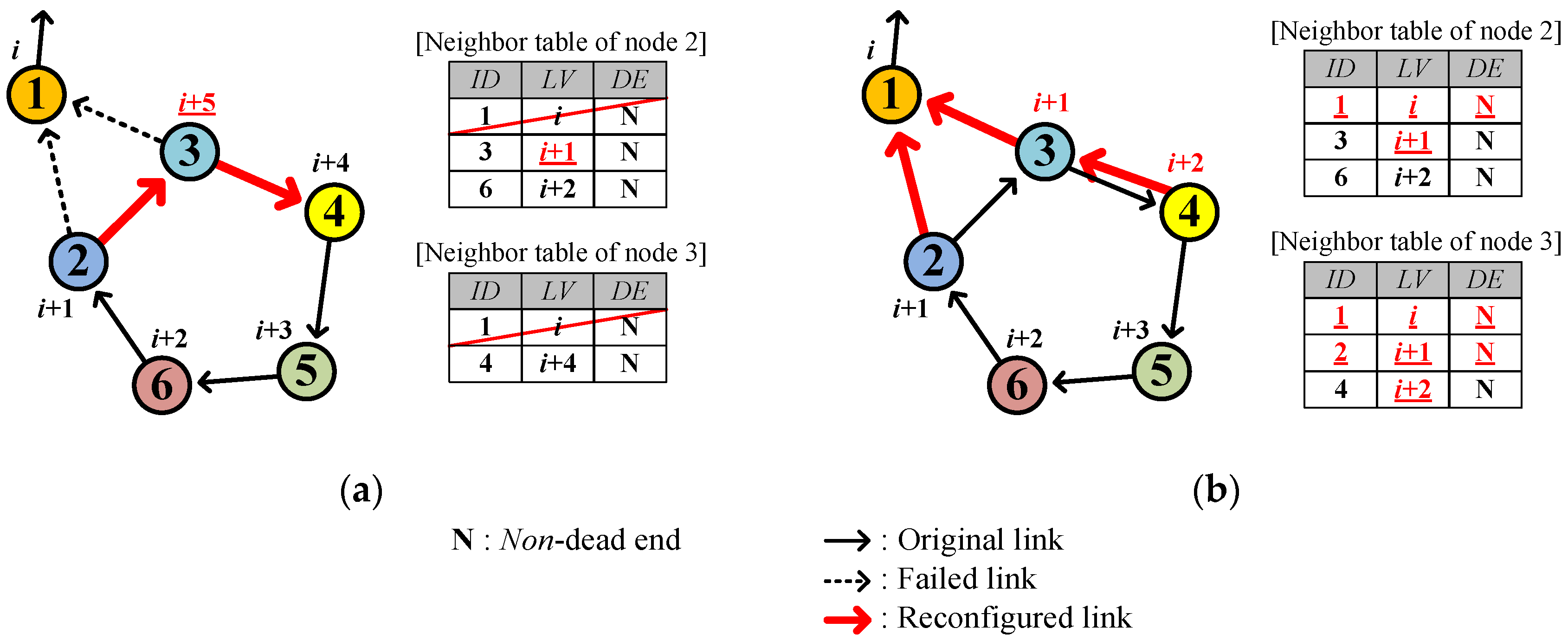
4.2.5. Fast Network Joining
5. Simulation Results
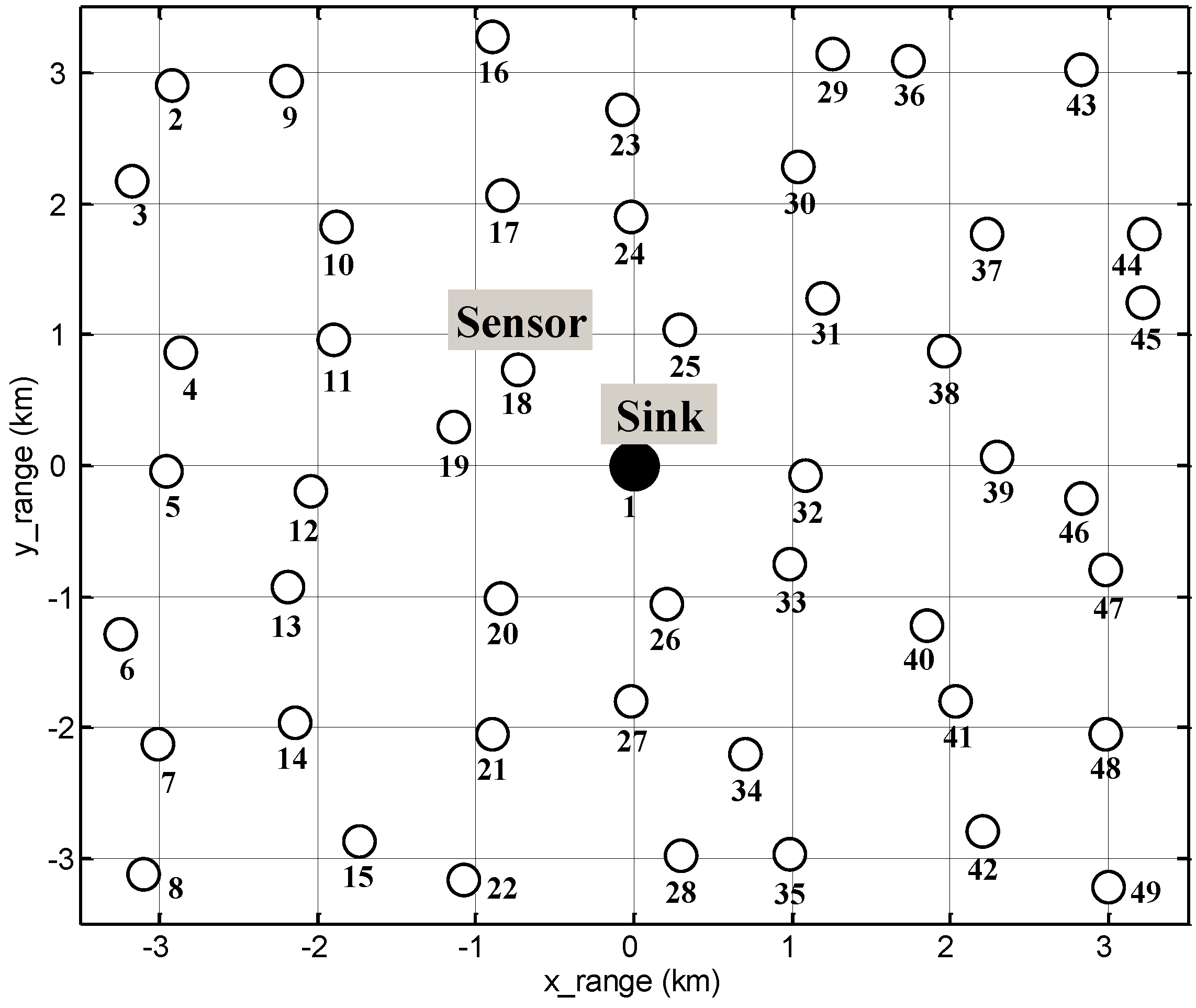
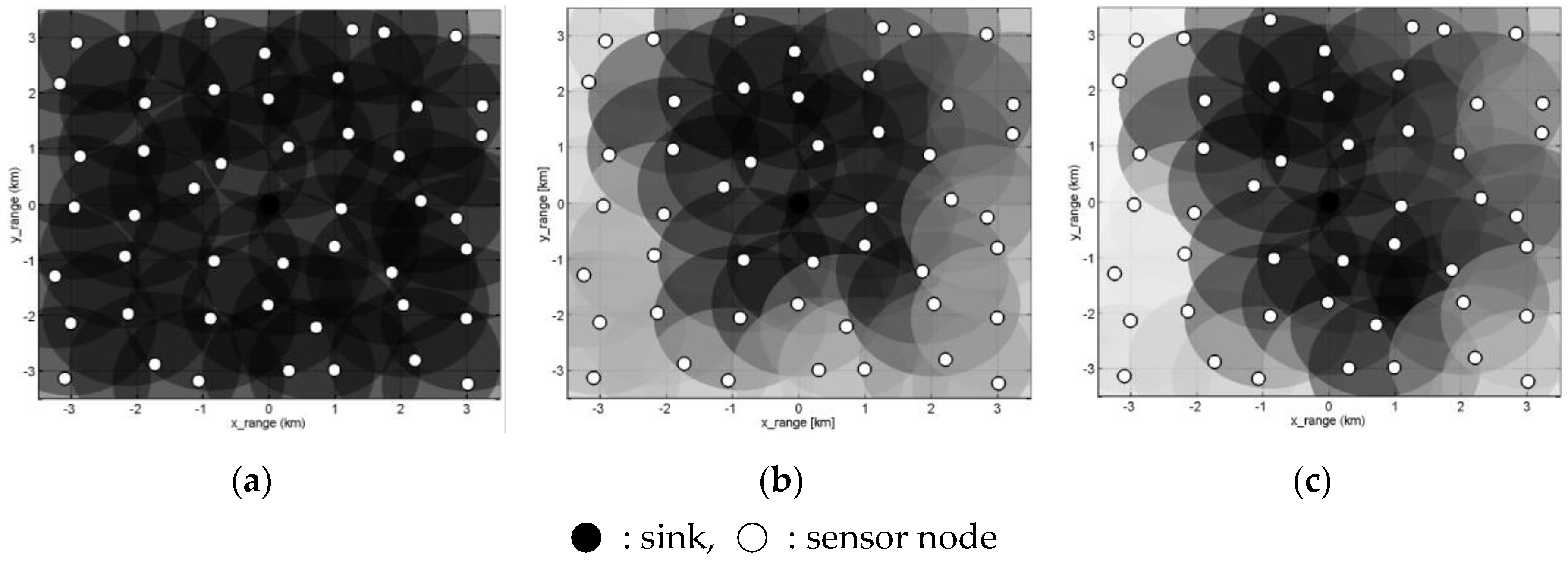
5.1. Simulation Model
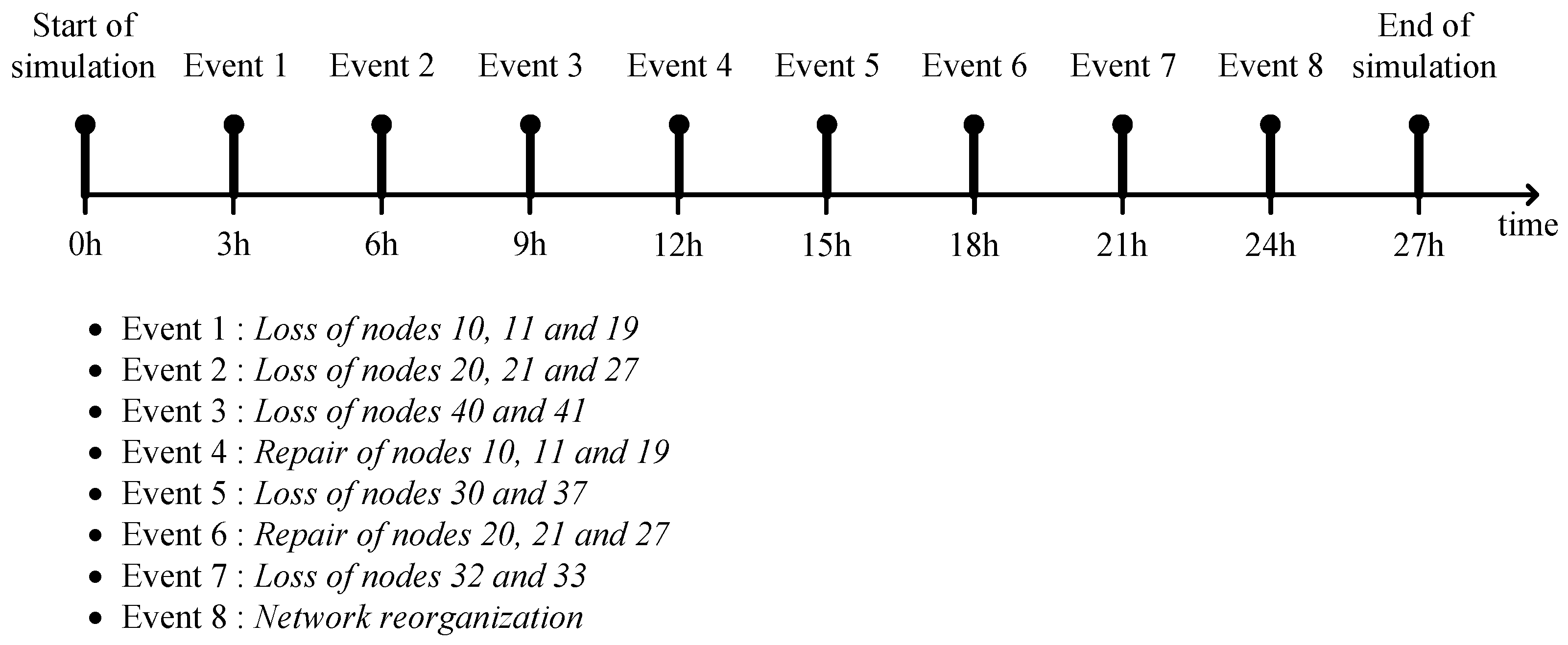
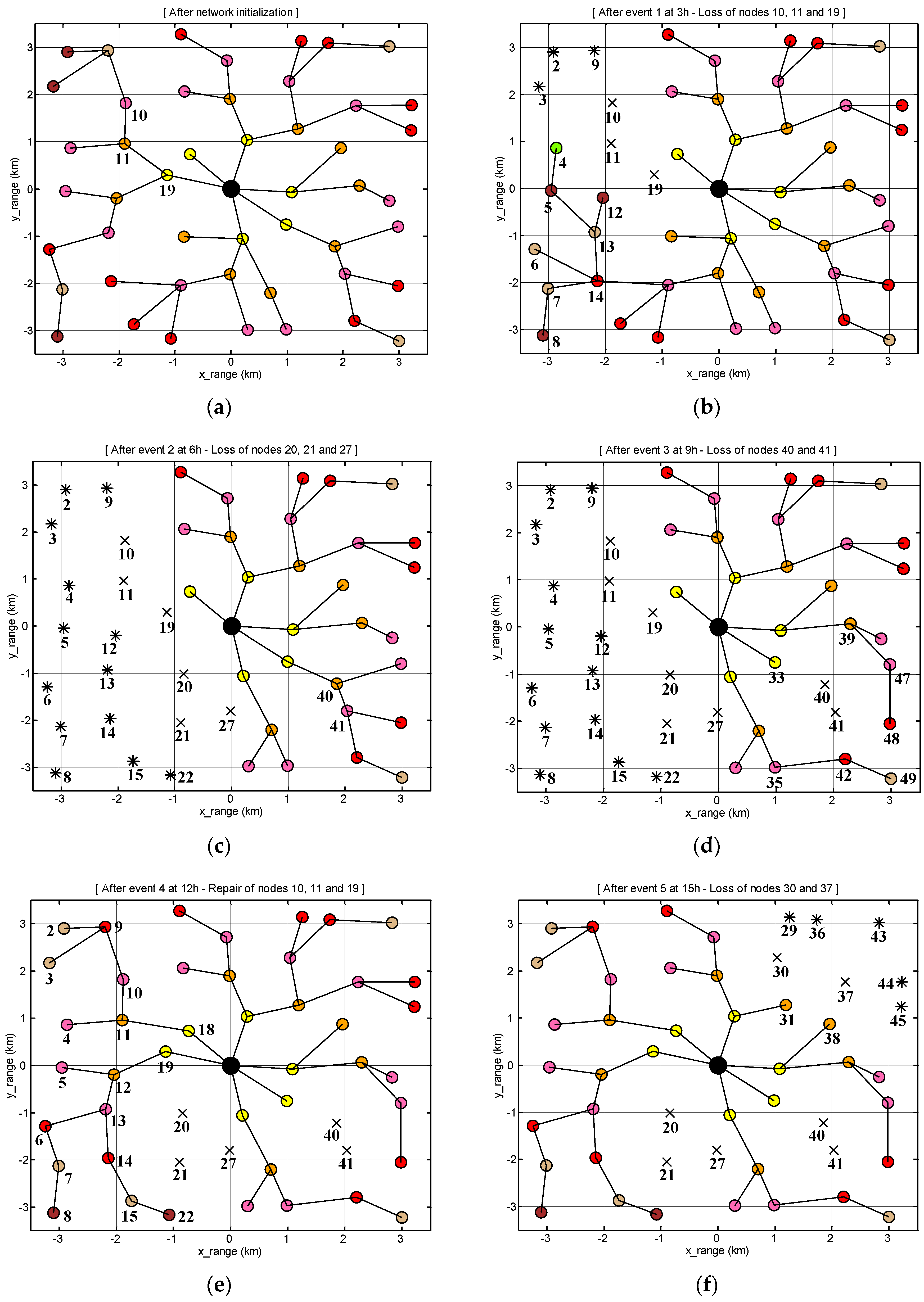
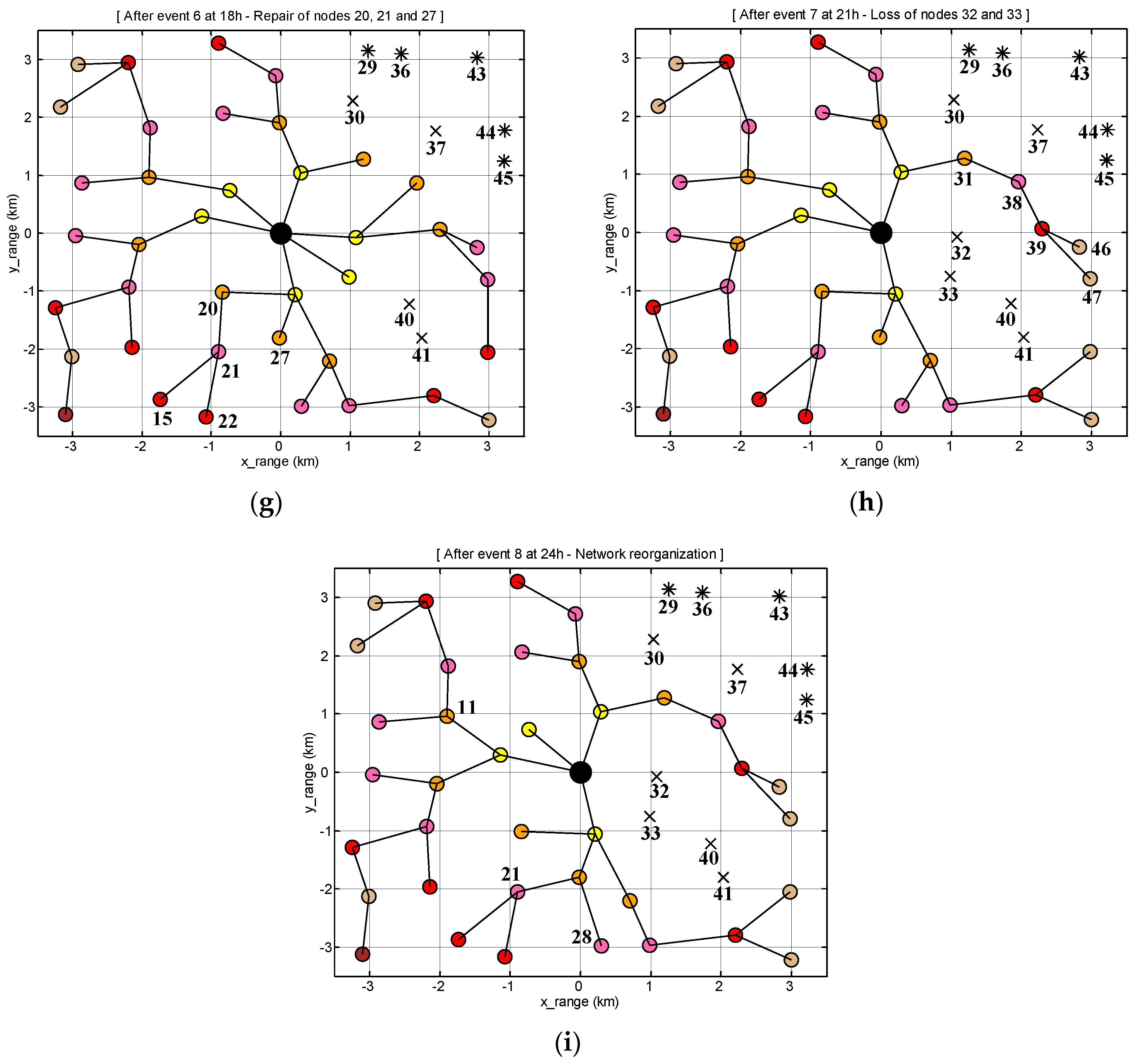
5.2. Simulation Scenario
5.3. Analysis of Results
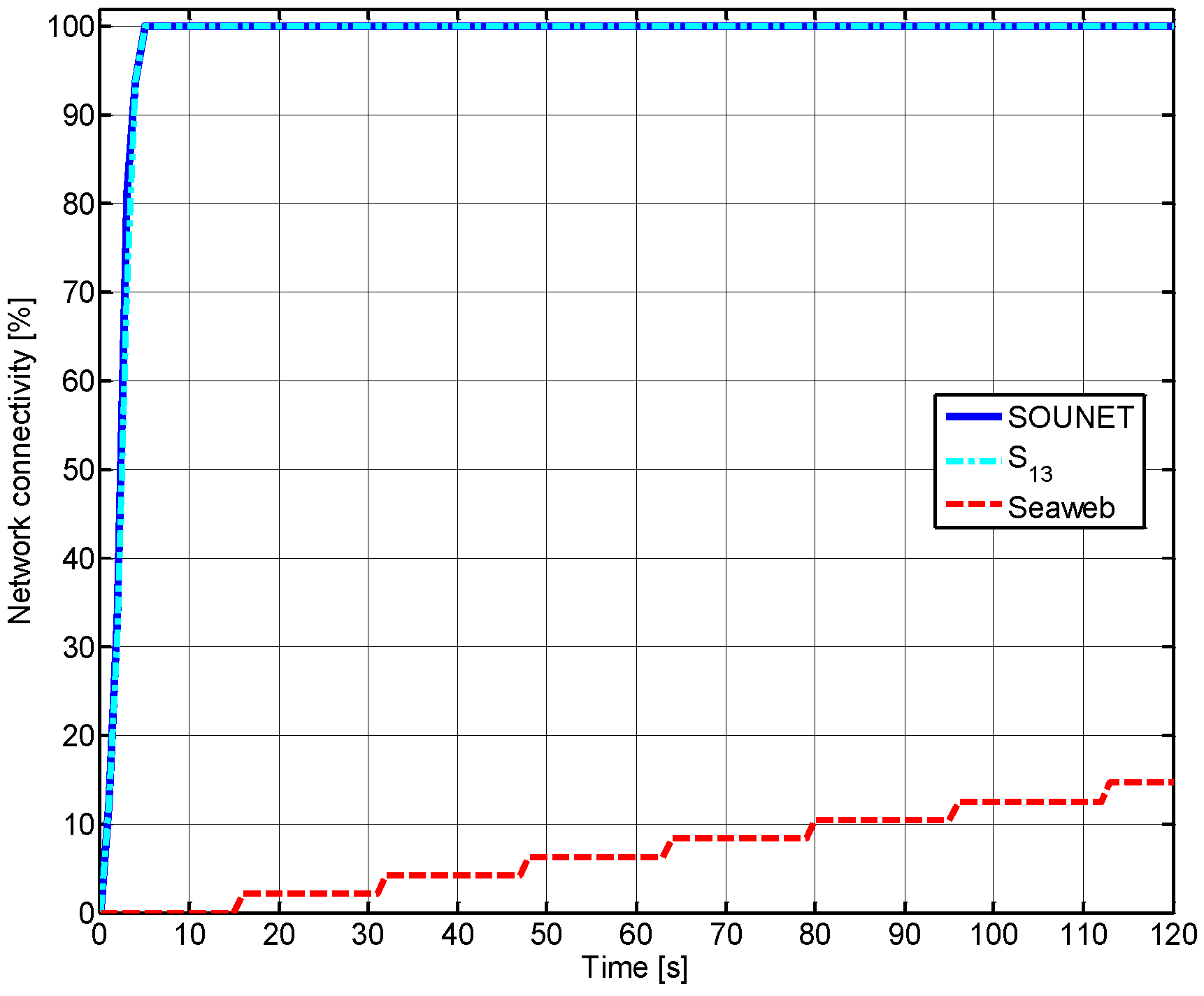
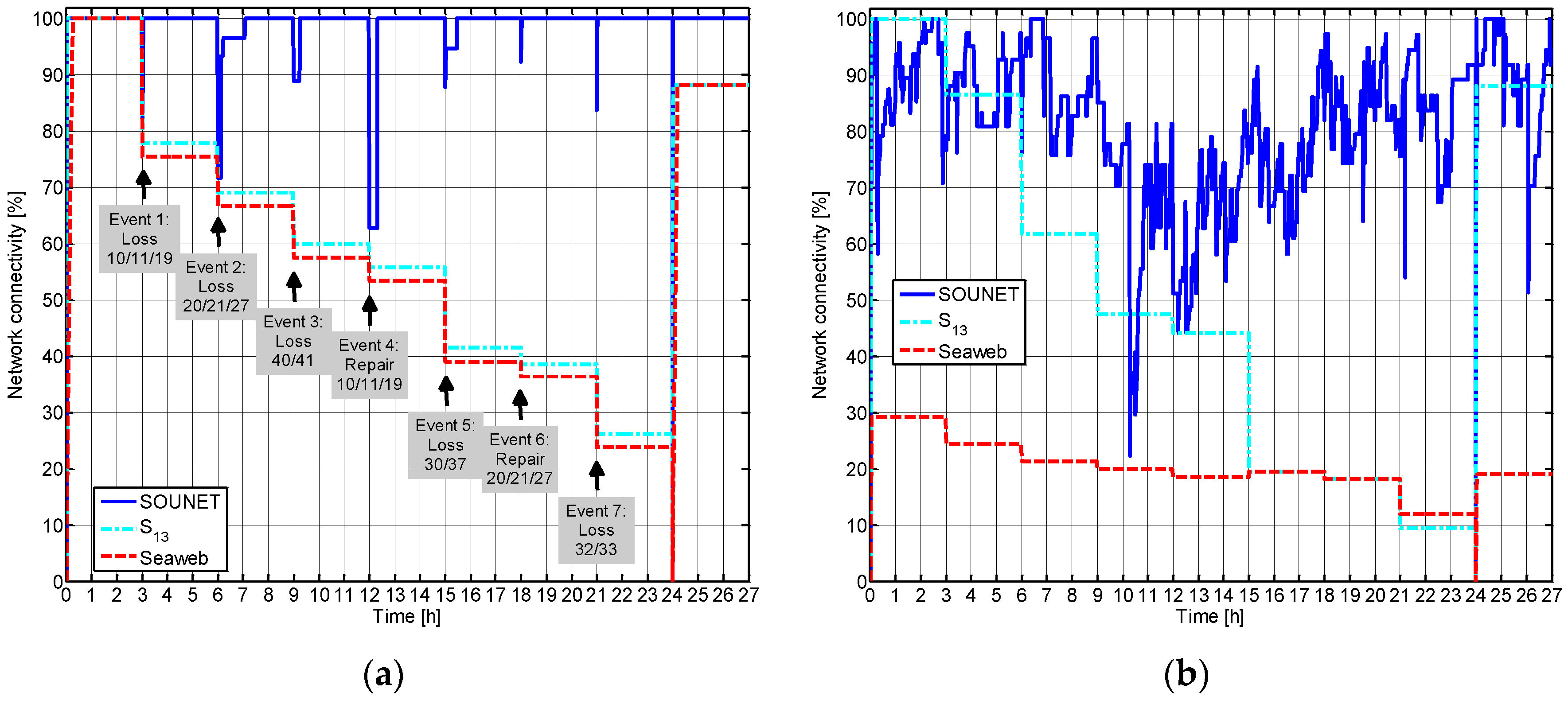
5.3.1. Network Connectivity
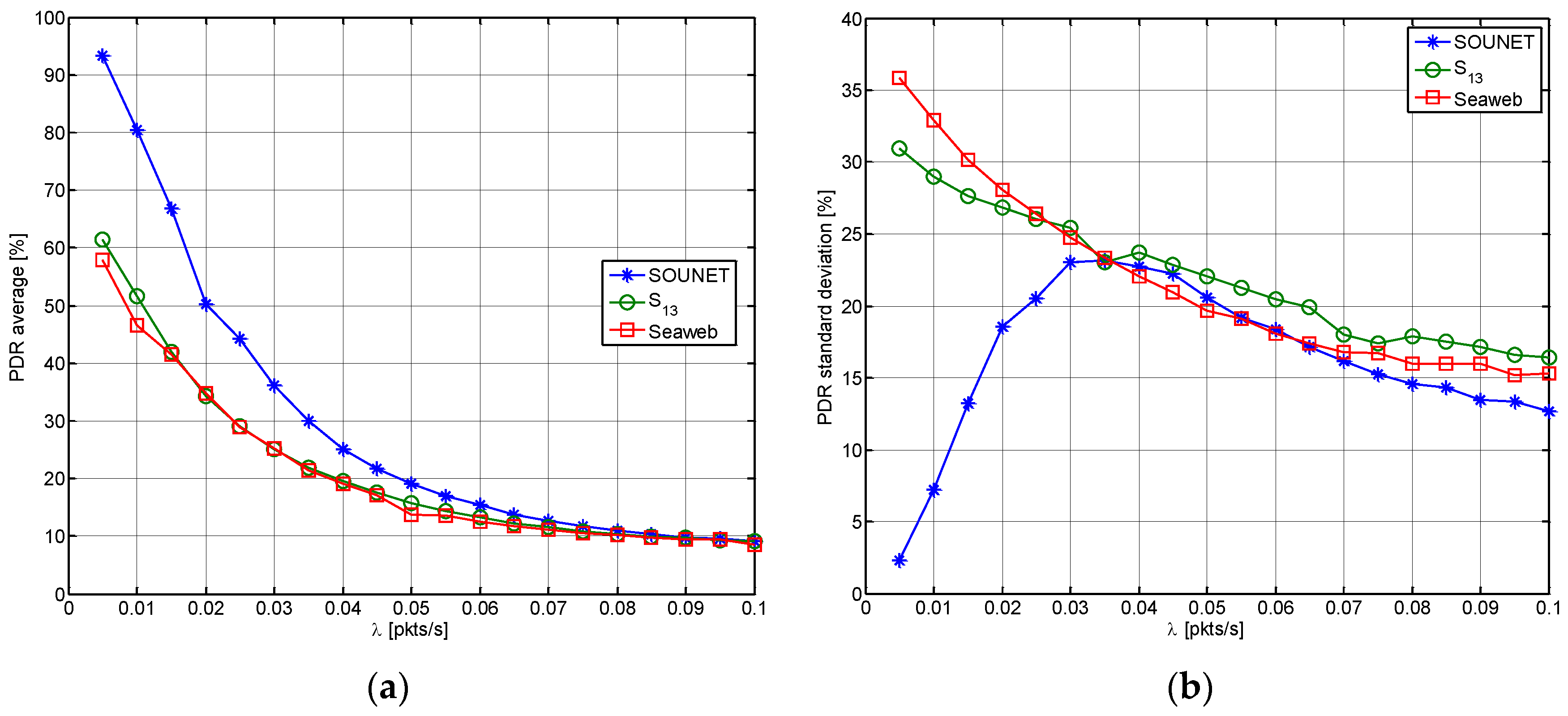
5.3.2. Packet Delivery Ratio
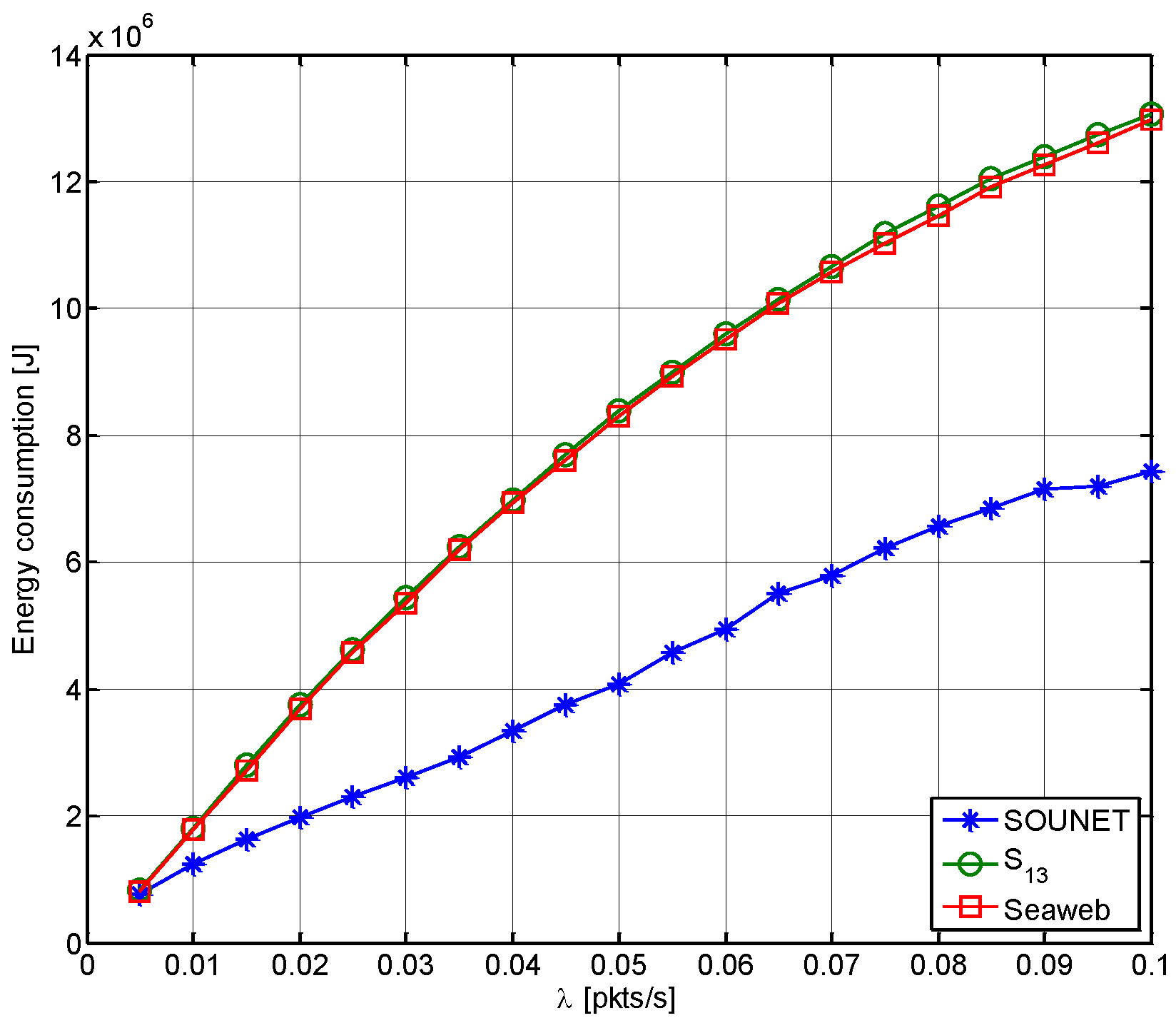
5.3.3. Energy Consumption
5.3.4. Signaling Overhead
6. Experimental Results
7. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Sozer, E.M.; Stojanovic, M.; Proakis, J.G. Underwater Acoustic Networks. IEEE J. Ocean. Eng. 2000, 25, 72–83. [Google Scholar] [CrossRef]
- Akyildiz, I.F.; Pompili, D.; Melodia, T. Underwater acoustic sensor networks: Research challenges. Ad Hoc Netw. 2005, 3, 257–279. [Google Scholar] [CrossRef]
- Heidemann, J.; Ye, W.; Wills, J.; Syed, A.; Li, Y. Research Challenges and Applications for Underwater Sensor Networking. In Proceedings of the 2006 IEEE Wireless Communications and Networking Conference (WCNC 2006), Las Vegas, NV, USA, 3–6 April 2006; pp. 228–235.
- Dressler, F. A study of self-organization mechanisms in ad hoc and sensor networks. Comput. Commun. 2008, 31, 3018–3029. [Google Scholar] [CrossRef]
- Prehofer, C.; Bettstetter, C. Self-Organization in Communication Networks: Principles and Design Paradigms. IEEE Commun. Mag. 2005, 43, 78–85. [Google Scholar] [CrossRef]
- Lloret, J.; Garcia, M.; Bri, D.; Diaz, J.R. A Cluster-Based Architecture to Structure the Topology of Parallel Wireless Sensor Networks. Sensors 2009, 9, 10513–10544. [Google Scholar] [CrossRef] [PubMed]
- Salva-Garau, F.; Stojanovic, M. Multi-Cluster Protocol for Ad Hoc Mobile Underwater Acoustic Networks. In Proceedings of the MTS/IEEE OCEANS 2003, San Diego, CA, USA, 22–26 September 2003; pp. 91–98.
- Domingo, M.C.; Prior, R. A Distributed Clustering Scheme for Underwater Wireless Sensor Networks. In Proceedings of the 2007 IEEE 18th International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC 2007), Athens, Greece, 3–7 September 2007; pp. 1–5.
- Huang, C.; Wang, Y.; Lin, C.; Chen, Y.; Chen, H.; Shen, H.; Chen, Y.; Chen, I.; Hu, K.; Yang, D. A self-healing clustering algorithm for underwater sensor networks. Cluster Comput. 2011, 14, 91–99. [Google Scholar] [CrossRef]
- Wang, F.; Wang, L.; Han, Y.; Liu, B.; Wang, J.; Su, X. A Study on the Clustering Technology of Underwater Isomorphic Sensor Networks Based on Energy Balance. Sensors 2014, 14, 12523–12532. [Google Scholar] [CrossRef] [PubMed]
- Souiki, S.; Hadjila, M.; Feham, M. Energy Efficient Routing for Mobile Underwater Wireless Sensor Networks. In Proceedings of the 2015 IEEE 12th International Symposium on Programming and Systems (ISPS 2015), Algiers, Algeria, 28–30 April 2015; pp. 1–6.
- Angskun, T.; Fagg, G.; Bosilca, G.; Pješivac-Grbović, J.; Dongarra, J. Self-healing network for scalable fault-tolerant runtime environments. Future Gener. Comput. Syst. 2010, 26, 479–485. [Google Scholar] [CrossRef]
- Yang, X.; Ong, K.G.; Dreschel, W.R.; Zeng, K.; Mungle, C.S.; Grimes, C.A. Design of a Wireless Sensor Network for Long-term, In-Situ Monitoring of an Aqueous Environment. Sensors 2002, 2, 455–472. [Google Scholar] [CrossRef]
- Rice, J.; Creber, B.; Fletcher, C.; Baxley, P.; Rogers, K.; McDonald, K.; Rees, D.; Wolf, M.; Merriam, S.; Mehio, R. Evolution of Seaweb Underwater Acoustic Networking. In Proceedings of the MTS/IEEE OCEANS 2000, Providence, RI, USA, 11–14 September 2000; pp. 2007–2017.
- Rice, J. Seaweb Acoustic Communication and Navigation Networks. In Proceedings of the 1st International Conference on Underwater Acoustic Measurements: Technologies and Results 2005 (UAM 2005), Heraklion, Greece, 28 June–1 July 2005.
- Rice, J.; Green, D. Underwater Acoustic Communications and Networks for the US Navy’s Seaweb Program. In Proceedings of the 2nd International Conference on Sensor Technologies and Applications 2008 (SENSORCOMM 2008), Cap Esterel, France, 25–31 August 2008; pp. 715–722.
- Ong, C.W. A Discovery Process for Initializing Ad Hoc Underwater Acoustic Networks. Master’s Thesis, Naval Postgraduate School, Monterey, CA, USA, December 2008. [Google Scholar]
- Ayaz, M.; Abdullah, A.; Faye, I.; Batira, Y. An efficient Dynamic Addressing based routing protocol for Underwater Wireless Sensor Network. Comput. Commun. 2012, 35, 475–486. [Google Scholar] [CrossRef]
- Li, N.; Martínez, J.-F.; Meneses Chaus, J.M.; Eckert, M. A Survey on Underwater Acoustic Sensor Network Routing Protocols. Sensors 2016, 16, 414. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Tariq, M.; Abd Latiff, M.S.; Ayaz, M.; Coulibaly, Y.; Wahid, A. Pressure Sensor Based Reliable (PSBR) Routing Protocol for Underwater Acoustic Sensor Networks. Ad Hoc. Sens. Wirel. Networks 2016, 32, 175–196. [Google Scholar]
- Petroccia, R. A Distributed ID Assignment and Topology Discovery Protocol for Underwater Acoustic Networks. In Proceedings of 3rd IEEE Underwater Communications and Networking Conference (UComms 2016), Lerici, Italy, 30 August–1 September 2016.
- Nanda, A.; Rath, A.K.; Rout, S.K. Node Sensing & Dynamic Discovering Routes for Wireless Sensor Networks. Int. J. Comput. Sci. Inf. Secur. 2010, 7, 122–131. [Google Scholar]
- Noh, Y.; Lee, U.; Wang, P.; Choi, B.S.C.; Gerla, M. VAPR: Void-Aware Pressure Routing for Underwater Sensor Networks. IEEE Trans. Mobile Comput. 2013, 12, 895–908. [Google Scholar] [CrossRef]
- Noh, Y.; Lee, U.; Lee, S.; Wang, P.; Wang, P.; Vieira, L.F.M.; Cui, J.; Gerla, M.; Kim, K. HydroCast: Pressure Routing for Underwater Sensor Networks. IEEE Trans. Veh. Technol. 2016, 65, 333–347. [Google Scholar] [CrossRef]
- Abramson, N. THE ALOHA SYSTEM—Another alternative for computer communications. In Proceedings of the Fall Joint Computer Conference (AFIPS 1970), Houston, TX, USA, 17–19 November 1970; pp. 281–285.
- Xiao, Y.; Zhang, Y.; Gibson, J.H.; Xie, G.G.; Chen, H. Performance analysis of ALOHA and p-persistent ALOHA for multi-hop underwater acoustic sensor networks. Cluster Comput. 2011, 14, 65–80. [Google Scholar] [CrossRef]
- Lee, J.-W.; Cho, H.-S. Cascading Multi-Hop Reservation and Transmission in Underwater Acoustic Sensor Networks. Sensors 2014, 14, 18390–18409. [Google Scholar] [CrossRef] [PubMed]
- Khan, J.U.; Cho, H.-S. A Distributed Data-Gathering Protocol Using AUV in Underwater Sensor Networks. Sensors 2015, 15, 19331–19350. [Google Scholar] [CrossRef] [PubMed]
- Lee, J.-W.; Cho, H.-S. A Hybrid Sender- and Receiver-Initiated Protocol Scheme in Underwater Acoustic Sensor Networks. Sensors 2015, 15, 28052–28069. [Google Scholar] [CrossRef] [PubMed]
- Khan, J.U.; Cho, H.-S. Data-Gathering Scheme Using AUVs in Large-Scale Underwater Sensor Networks: A Multihop Approach. Sensors 2016, 16, 1626. [Google Scholar] [CrossRef] [PubMed]
- Cho, J.; Shitiri, E.; Cho, H.-S. Network Allocation Vector (NAV) Optimization for Underwater Handshaking-Based Protocols. Sensors 2017, 17, 32. [Google Scholar] [CrossRef] [PubMed]
- Zhu, Y.; Zhou, Z.; Peng, Z.; Cui, J. “Busy Terminal Problem” and Implications in Underwater Acoustic Networks. In Proceedings of the 7th ACM International Conference on Underwater Networks and Systems 2012 (WUWNet 2012), Los Angeles, CA, USA, 5–6 November 2012.
- Forum Energy Technologies. Available online: http://www.f-e-t.com/images/uploads/Teledyne_Benthos_ATM-885_LF_(9–14kHz)_Subsea_Modem.pdf (accessed on 30 August 2016).
- Skiena, S.S. The Algorithm Design Manual; Springer: Berlin, Germany, 2008; pp. 103–144. [Google Scholar]
- Ahn, G.; Miluzzo, E.; Campbell, A.T.; Hong, S.G.; Cuomo, F. Funneling-MAC: A Localized, Sink-Oriented MAC for Boosting Fidelity in Sensor Networks. In Proceedings of the 4th ACM International Conference on Embedded Networked Sensor Systems (SenSys 2006), Boulder, CO, USA, 1–3 November 2006; pp. 293–306.

| Parameter | Value |
|---|---|
| Grid spacing | 1 km |
| Data rate | 2400 bps |
| Propagation speed | 1500 m/s |
| Transmission/Sensing range | 1300 m |
| HELLO/ACK/ISO packet length | 120 bits |
| DATA packet length | 1200 bits |
| Tx mode power | 20 W |
| Rx mode power | 756 mW |
| 3 | |
| 10 | |
| 10 | |
| λ | 0.001 packets/s |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license ( http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kim, H.-w.; Cho, H.-S. SOUNET: Self-Organized Underwater Wireless Sensor Network. Sensors 2017, 17, 283. https://doi.org/10.3390/s17020283
Kim H-w, Cho H-S. SOUNET: Self-Organized Underwater Wireless Sensor Network. Sensors. 2017; 17(2):283. https://doi.org/10.3390/s17020283
Chicago/Turabian StyleKim, Hee-won, and Ho-Shin Cho. 2017. "SOUNET: Self-Organized Underwater Wireless Sensor Network" Sensors 17, no. 2: 283. https://doi.org/10.3390/s17020283





