Secrecy Performance Analysis of Cognitive Sensor Radio Networks with an EH-Based Eavesdropper
Abstract
:1. Introduction
- (1)
- Considering the interference temperature issues of PU, the closed-form expressions of the secrecy outage probability (SOP) and the average secrecy rate (ASR) are derived, which are validated by Monte Carlo simulations;
- (2)
- Two different scenarios are studied: Case 1, the transmit power of the ST is only affected by the interference power constraint of the PU, and Case 2, the transmit power of the ST is limited by the maximal transmit power of ST itself and the interference power constraint for PU simultaneously;
- (3)
- The effects of various parameters, (such as power splitting factor, link power gain ratio, target secrecy rate), on the physical layer secrecy performance of the CSRNs are investigated, which can give an intuitive insight into the secrecy performance of the considered system.
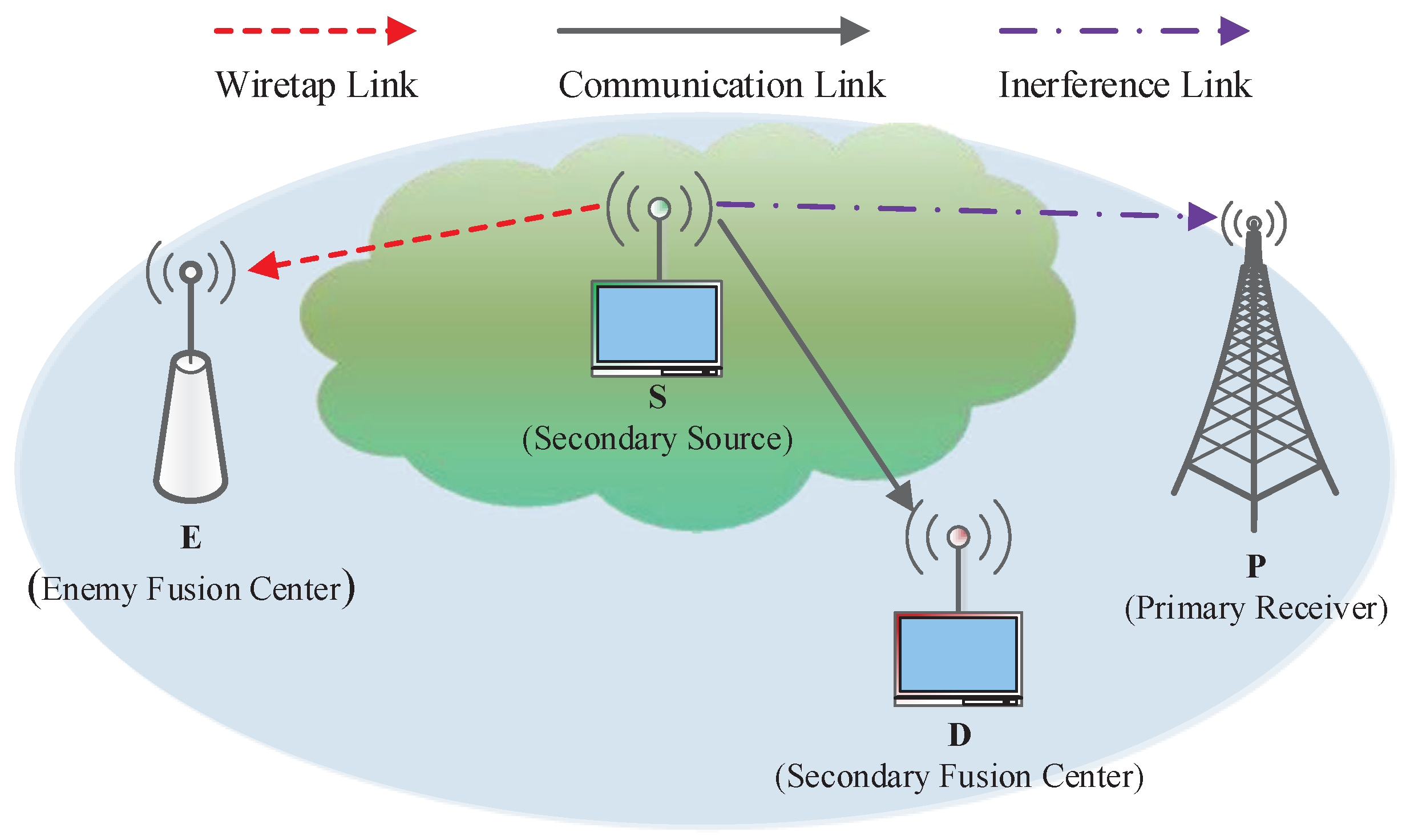
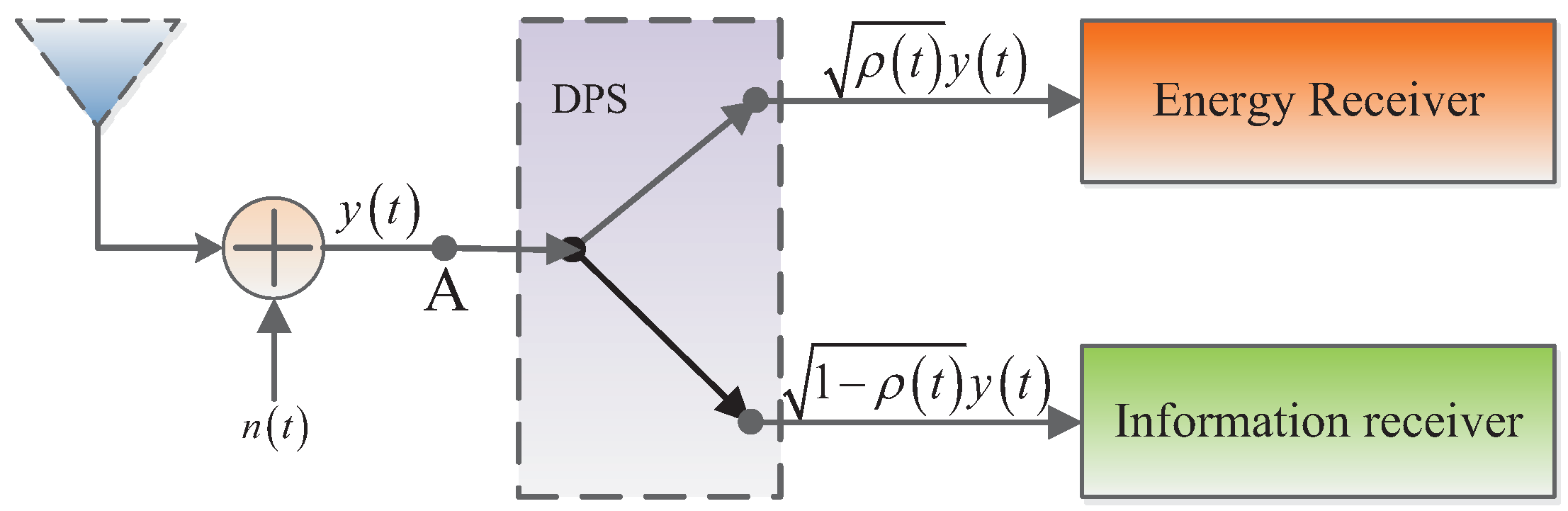
2. System Model
3. Secrecy Performance Analysis
3.1. Case 1: Interference Power Constraint for the Secondary Transmitter
3.1.1. Secrecy Outage Probability
3.1.2. Average Secrecy Rate
3.2. Case 2: Maximum Source Power Constraint and Interference Power Constraint for the Secondary Transmitter
4. Discussions
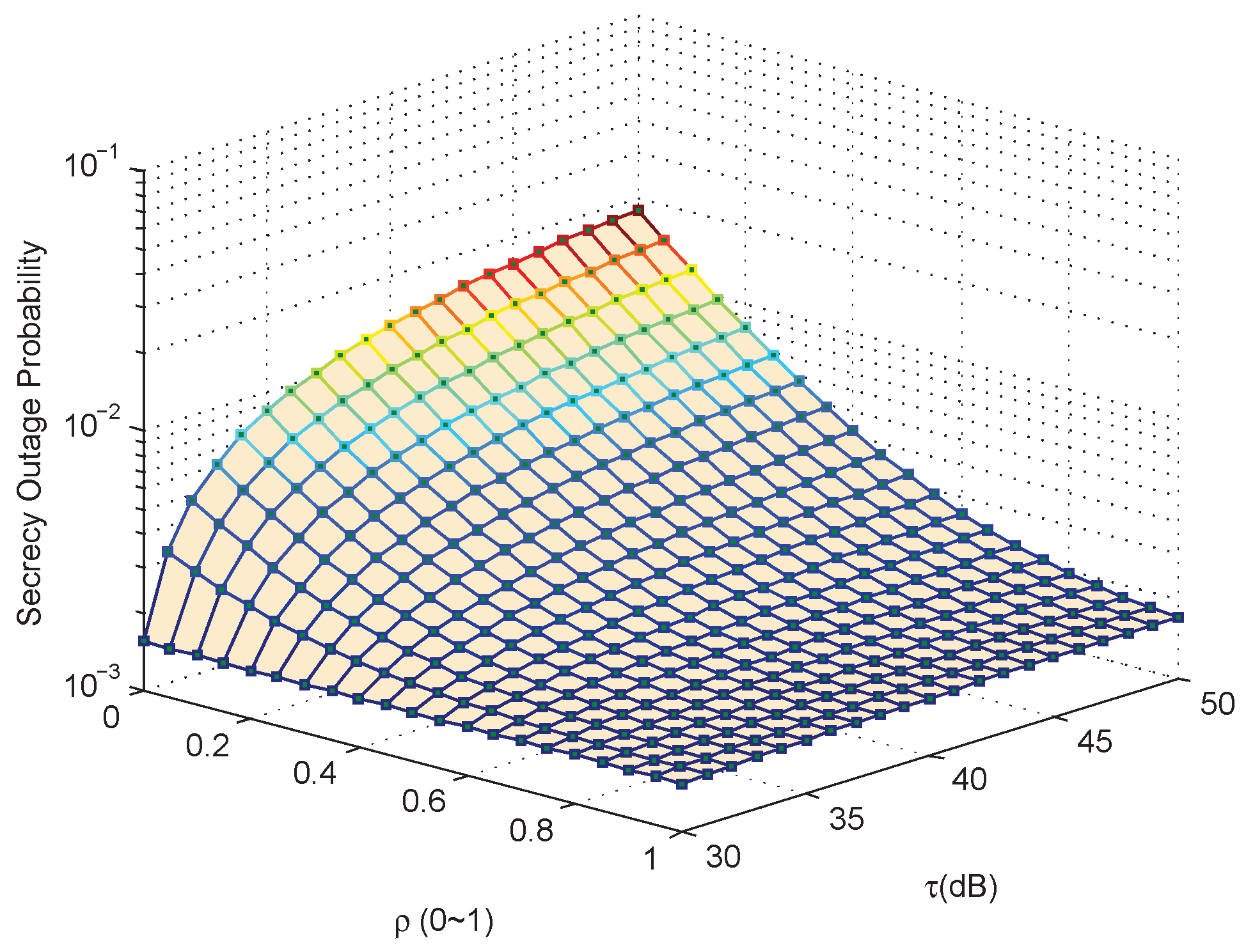
5. Simulation Results and Analysis
5.1. Simulation Results for Case 1
5.2. Simulation Results for Case 2
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Zhao, Y.; Hong, Z.; Wang, G.; Huang, J. High-Order Hidden Bivariate Markov Model: A Novel Approach on Spectrum Prediction. In Proceedings of the 25th International Conference on Computer Communications and Networks (2016 ICCCN), Waikoloa, HI, USA, 1–4 August 2016; pp. 1–7. [Google Scholar]
- Zhao, Y.; Pradhan, J.; Wang, G.; Huang, J. Experimental approach: Two-stage spectrum sensing using GNU radio and USRP to detect primary user’s signal. In Proceedings of the 31st Annual ACM Symposium on Applied Computing (SAC 2016), Pisa, Italy, 4–8 April 2016; pp. 2165–2170. [Google Scholar]
- Zhao, Y.; Anjum, M.N.; Song, M.; Xu, X.; Wang, G.; Huang, J. Optimal Resource Allocation for Delay Constrained Users in Self-coexistence WRAN. In Proceedings of the IEEE Globecom Workshops, San Diego, CA, USA, 6–10 December 2015; pp. 1–6. [Google Scholar]
- Akan, O.B.; Karli, O.B.; Ergul, O. Cognitive radio sensor networks. IEEE Netw. 2009, 23, 34–40. [Google Scholar] [CrossRef]
- Goh, H.G.; Kwong, K.H.; Shen, C.; Michie, C.; Andonovic, I. CogSeNet: A Concept of Cognitive Wireless Sensor Network. In Proceedings of the 7th IEEE Consumer Communications and Networking Conference, Las Vegas, NV, USA, 9–12 January 2010; pp. 1–2. [Google Scholar]
- Ren, J.; Zhang, Y.; Zhang, N.; Zhang, D.; Shen, X. Dynamic Channel Access to Improve Energy Efficiency in Cognitive Radio Sensor Networks. IEEE Trans. Wirel. Commun. 2016, 15, 3143–3156. [Google Scholar] [CrossRef]
- Zheng, M.; Liang, W.; Yu, H.; Sharif, H. Utility-based opportunistic spectrum access for cognitive radio sensor networks: Joint spectrum sensing and random access control. IET Commun. 2016, 10, 1044–1052. [Google Scholar] [CrossRef]
- Nobar, S.K.; Mehr, K.A.; Niya, J.M.; Tazehkand, B.M. Cognitive Radio Sensor Network With Green Power Beacon. IEEE Sens. J. 2016, 17, 1549–1561. [Google Scholar] [CrossRef]
- Zhang, D.; Chen, Z.; Ren, J.; Zhang, N.; Awad, M.K.; Zhou, H.; Shen, X. Energy-Harvesting-Aided Spectrum Sensing and Data Transmission in Heterogeneous Cognitive Radio Sensor Network. IEEE Trans. Veh. Technol. 2017, 66, 831–843. [Google Scholar] [CrossRef]
- Varshney, L.R. Transporting information and energy simultaneously. Proceeding of the IEEE International Symposium on Information Theory (ISIT), Toronto, ON, Canada, 6–11 July 2008; pp. 1612–1616. [Google Scholar]
- Grover, P.; Sahai, A. Shannon meets Tesla: Wireless information and power transfer. Proceeding of the IEEE International Symposium on Information Theory (ISIT), Austin, TX, USA, 13–18 June 2010; pp. 2363–2367. [Google Scholar]
- Zhang, R.; Ho, C.K. MIMO broadcasting for simultaneous wireless information and power transfer. IEEE Trans. Wirel. Commun. 2013, 12, 1989–2001. [Google Scholar] [CrossRef]
- Xing, C.; Wang, N.; Ni, J. MIMO beam-forming designs with partial CSI under energy harvesting constraints. IEEE Signal Process. Lett. 2013, 20, 363–366. [Google Scholar] [CrossRef]
- Xiang, Z.; Tao, M. Robust beamforming for wireless information and power transmission. IEEE Wirel. Commun. Lett. 2012, 1, 372–375. [Google Scholar] [CrossRef]
- Zhou, X.; Zhang, R.; Ho, C.K. Wireless information and power transfer: Architecture design and rate-energy tradeoff. IEEE Trans. Commun. 2013, 61, 4754–4765. [Google Scholar] [CrossRef]
- Shi, Q.; Liu, L.; Xu, W.; Zhang, R. Joint transmit beam-forming and receive power splitting for MISO SWIPT systems. IEEE Trans. Wirel. Commun. 2014, 13, 3269–3280. [Google Scholar] [CrossRef]
- Huang, J.; Li, Q.; Zhang, Q.; Zhang, G.; Qin, J. Relay beamforming for amplify-and-forward multi-antenna relay networks with energy harvesting constraint. IEEE Signal Process. Lett. 2014, 21, 454–458. [Google Scholar] [CrossRef]
- Chalise, B.K.; Ma, W.K.; Zhang, Y.D.; Himal, A.S. Optimum performance boundaries of OSTBC-based AF-MIMO relay system with energy harvesting receiver. IEEE Trans. Signal Process. 2013, 61, 4199–4231. [Google Scholar] [CrossRef]
- Shen, C.; Li, W.; Chang, T. Wireless information and energy transfer in multi-antenna interference channel. IEEE Trans. Signal Process. 2014, 62, 6249–6264. [Google Scholar] [CrossRef]
- Park, J.; Clerckx, B. Joint wireless information and energy transfer in a two-user MIMO interference channel. IEEE Trans. Wirel. Commun. 2013, 12, 4210–4221. [Google Scholar] [CrossRef]
- Soosahabi, R.; Naraghi-Pour, M. Scalable PHY-layer security for distributed detection in wireless sensor networks. IEEE Trans. Inf. Forensics Secur. 2012, 7, 1118–1126. [Google Scholar] [CrossRef]
- Bloch, M.; Barros, J. Physical-Layer Security; Cambridge University Press: New York, NY, USA, 2004. [Google Scholar]
- Lee, J.-H.; Sohn, I.; Kim, Y.-H. Transmit Power Allocation for Physical Layer Security in Cooperative Multi-Hop Full-Duplex Relay Networks. Sensors 2016, 16, 1726–1739. [Google Scholar] [CrossRef] [PubMed]
- Deng, Y.; Wang, L.; Elkashlan, M.; Nallanathan, A.; Mallik, R.K. Physical layer security in three-tier wireless sensor networks: A stochastic geometry approach. IEEE Trans. Inf. Forensics Secur. 2016, 11, 1128–1138. [Google Scholar] [CrossRef]
- Hong, Y.W.P.; Lan, P.C.; Kuo, C.C.J. Enhancing physical-layer secrecy in multi-antenna wireless systems: An overview of signal processing approaches. IEEE Signal Process. Mag. 2013, 30, 29–40. [Google Scholar] [CrossRef]
- Yang, J.; Kim, I.M.; Kim, D.I. Optimal cooperative jamming for multiuser broadcast channel with multiple eavesdroppers. IEEE Trans. Wirel. Commun. 2013, 12, 2840–2852. [Google Scholar] [CrossRef]
- Liu, L.; Zhang, R.; Chua, K.C. Secrecy wireless information and power transfer with MISO beam-forming. IEEE Trans. Signal Process. 2014, 62, 1850–1863. [Google Scholar] [CrossRef]
- Hung, S.-C.; Xiao, Y.; Chen, K.-C. Transmission Strategy With Cooperative Sensors in Cognitive Radio Networks. IEEE Trans. Veh. Technol. 2016, 65, 3416–3429. [Google Scholar] [CrossRef]
- Ding, G.; Wang, J.; Wu, Q.; Song, F.; Chen, Y. Spectrum Sensing in Opportunity–Heterogeneous Cognitive Sensor Networks: How to Cooperate? IEEE Sens. J. 2013, 13, 4247–4255. [Google Scholar] [CrossRef]
- Zheng, M.; Chen, L.; Liang, W.; Yu, H.; Wu, J. Energy-efficiency Maximization for Cooperative Spectrum Sensing in Cognitive Sensor Networks. IEEE Trans. Green Commun. Netw. 2016. [Google Scholar] [CrossRef]
- Chiti, F.; Fantacci, R.; Tani, A. Performance Evaluation of An Adaptive Channel Allocation Technique for Cognitive Wireless Sensor Networks. IEEE Trans. Veh. Technol. 2016. [Google Scholar] [CrossRef]
- Sun, Y. Distributed fast channel allocation in cognitive wireless sensor networks. IET Signal Process. 2016, 10, 471–477. [Google Scholar] [CrossRef]
- Wang, D.; Ren, P.; Du, Q.; Sun, L.; Wang, Y. Optimal Power Allocation for Cognitive Radio Sensor Networks under Primary Secrecy Outage Constraint. In Proceedings of the IEEE International Conference on Communication Systems (ICCS), Shenzhen, China, 14–16 December 2016; pp. 1–5. [Google Scholar]
- Pan, G.; Tang, C.; Li, T.; Chen, Y. Secrecy Performance Analysis for SIMO Simultaneous Wireless Information and Power Transfer Systems. IEEE Trans. Wirel. Commun. 2015, 63, 3423–3433. [Google Scholar] [CrossRef]
- Elkashlan, M.; Wang, L.; Duong, T.Q.; Karagiannidis, G.K.; Nallanathan, A. On the security of cognitive radio networks. IEEE Trans. Veh. Technol. 2015, 64, 3790–3795. [Google Scholar] [CrossRef]
- Duong, T.Q.; da Costa, D.B.; Elkashlan, M.; Bao, V.N.Q. Cognitive Amplify-and-Forward Relay Networks Over Nakagami-m Fading. IEEE Trans. Veh. Technol. 2012, 61, 2368–2374. [Google Scholar] [CrossRef]
- Grinstead, C.M.; Snell, J.L. Introduction to Probability, 2nd ed.; American Mathmatical Society: Providence, RI, USA, 1991. [Google Scholar]
- Gradshteyn, I.S.; Ryzhir, I.M. Tables of Integrals, Series and Products, 7th ed.; Academic Press: NewYork, NY, USA, 2007. [Google Scholar]




© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sun, A.; Liang, T.; Li, B. Secrecy Performance Analysis of Cognitive Sensor Radio Networks with an EH-Based Eavesdropper. Sensors 2017, 17, 1026. https://doi.org/10.3390/s17051026
Sun A, Liang T, Li B. Secrecy Performance Analysis of Cognitive Sensor Radio Networks with an EH-Based Eavesdropper. Sensors. 2017; 17(5):1026. https://doi.org/10.3390/s17051026
Chicago/Turabian StyleSun, Aiwei, Tao Liang, and Bolun Li. 2017. "Secrecy Performance Analysis of Cognitive Sensor Radio Networks with an EH-Based Eavesdropper" Sensors 17, no. 5: 1026. https://doi.org/10.3390/s17051026




