4.1. Evaluation by RCF Optimization
In this section, we analyze the enhancement in robustness allowed by our proposal, according to the RCF. Comparisons with torus automorphism in [
11] and Rombaut’s SA [
14] are also given. Different strategies where implemented in the Java language (Java 8 Update 91) and executed in an HP Envy 4-1152la computer with an Intel Core i5-3317U 64-bit processor, 8 GB RAM, 128GB SSD and Windows 8.1 PRO as the operating system.
For evaluation purposes, we select a number of different scenarios that represent various possible situations reported in the application field of Wireless Visual Sensor Networks (WVSN) [
29,
30]. We must note that, even if we restrict the number of scenarios to some particular cases due to the problem’s complexity, the number of scenarios simulated in this paper exceeds most of the related works found in the literature. Eight application scenarios were selected, differing in mask sizes (
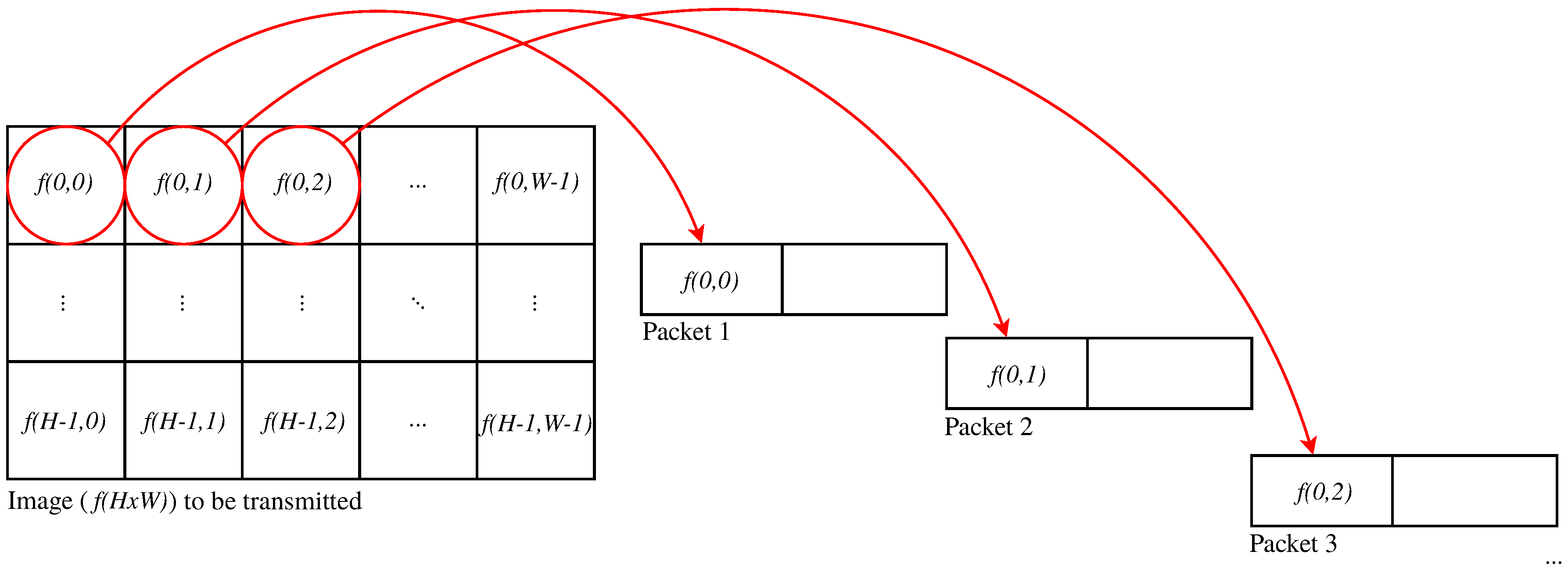
f matrix) and the number of elements per packet
P. For simplicity, we consider a fixed Packet Loss Rate (PLR) of 0.2, based on previous applications, which show that this represents a usual situation in real-world WVSN, such as the work in [
8] (note that this simplifies
calculation in Equations (A6)–(A8) to one if
i corresponds to the 20% of the required amount of packets and zero in any other case). In any case, we must argue that, from experimentation, we observe no significant changes in resulting RCF when varying (even greatly) PLR, for the selected evaluation scenarios.
Note that, as the optimization problem considers mask size and elements per packet as input parameters, not making any specifications about the blocks content, one combination of parameters (and the resulting output) can be applied to many application cases. For example, a mask size of blocks with a number of elements (blocks) per packet may, represent, in the same way, the following application cases:
The input image has a pixel resolution, codified in 8 bpp and divided in blocks of pixels (by pixels) to be packetized into packets of six bytes of payload (so, six elements per packet),
the input image has a pixel resolution, codified in 4 bpp (so it is compressed) and divided in blocks of pixels (by pixels) to be packetized into packets of three bytes of payload (so, six elements per packet),
The image is pixels resolution, codified in 1 bpp, divided in blocks of and packetized into packets of 48 bytes of payload (so, six elements per packet).
The considered scenarios for the evaluation of the packetization mask generation are summarized in
Table 1. As usual, each case considers a squared number of blocks, defining masks of
elements.
As said, selected parameters are based on related works with application in WVSN. Parameters scenarios were selected considering:
Maximum block size according to the JPEG standard ()
Image sizes according to real-world WVSN resolutions , , and .
Payload packets according to various reported applications, particularly: 27 bytes (as Cyclops camera firmware [
31]) and 100 bytes as works in [
32,
33] related to IEEE 802.15.4 XBee modules [
34].
For evaluation purposes, the following parameters were selected for each considered method:
For the proposed Genetic Algorithm (GA):
- -
Number of executions (number of times the algorithm was executed with the same parameters, but different random seeds): 20
- -
- -
- -
- -
- -
For Rombaut Simulated Annealing (RA):
- -
Number of executions: 20
- -
Equilibrium criteria for SA: 500 iterations
- -
Equilibrium criteria for the Metropolis algorithm: 150 iterations
- -
- -
SA acceptance probability
(according to [
35,
36])
For Torus Automorphisms (TA):
- -
Best parameters
k and
n (Equation (
1)) obtained by exhaustive search for each different scenario (according with methodology in [
11]). Identified parameters are presented in
Table 2.
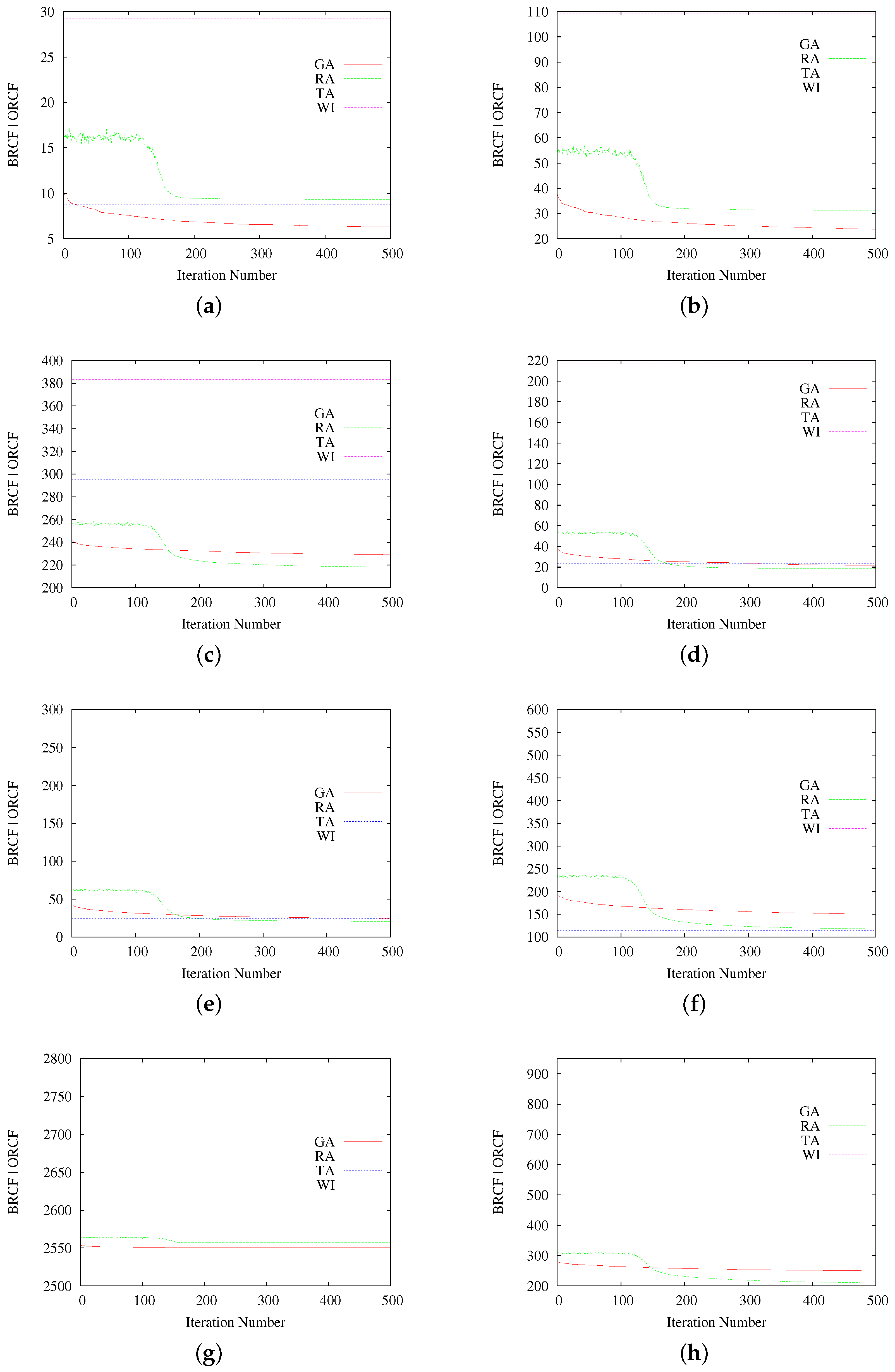
Obtained results are in terms of the average Best-obtained RCF (BRCF) from all of the iterations, for the case of GA and RA, and of the Obtained RCF (ORCF) for the case of deterministic cases Without Interleaving (WI; i.e., sequential communication line-by-line) and TA with its best parameters. Each BRCF value is obtained by averaging the best result of each of the 20 executions for the corresponding iteration number (so it represents the average best results of the genetic algorithm at a certain number of iterations, for a given number of executions).
Results for each scenario are shown in
Figure 4.
Obtained BRCF values for GA and RA at the considered 500 iterations, for each evaluation scenario, are shown in
Table 3. ORCF for the TA and WI cases are also given. Finally, the table also shows the Average RCF (ARCF) for GA and RA, which represents the average of all of the results at the 500th iteration, for each evaluation scenario.
As a general rule, the results summarized in
Table 3 (and each of the graphics in
Figure 4) show better RCF results of interleaving-based methods in comparison with the non-interleaving case (WI). In terms of the best obtained RCF values, Scenarios 1, 2 and 7 show that the proposed GA presents equivalent or superior results to RA and TA, while only in Scenarios 1 and 2, the average RCF obtained by GA outperforms the other methods. In Scenarios 3, 4, 5 and 8, the best results were reported by RA. Finally, in Scenarios 6 and 7, the obtained results are slightly in favor of TA.
Regarding the performance of the proposed metaheuristic with respect to the deterministic method TA, most of the considered scenarios show the advantage of our GA, but this advantage seems to decrease as the complexity of the problem increases. Indeed, Scenarios 1 to 4 (also 8) present better performance of GA, but, when the amount of possible combinations increases (because of the mask size), TA seems to perform better. The same observation can be done for RA. In this sense, there is still an open question about the number of iterations necessary for botGA and SA, in order to reach solutions as best as possible, or a more suitable stopping criterion. What is clear (and is not said in other works) is that TA, even if effective, is far from ensuring optimal values as observed in Scenarios 3 and 8.
In the matter of the metaheuristic approaches’ comparison, even if the number of generated solutions and iterations was the same for both GA and RA, the RCF values reached for those methods differ. Indeed, only in Scenarios 1, 2 and 7, GA results overtake RA, while in Scenarios 3 to 6 and 8, RA shows the best RCF results. Regarding their behavior, GA does not present abrupt changes over the iterations, while RA presents a temporary big acceleration on the improvement of the calculated RCF around Iteration 150.
From these results, even if GA achieved good RCF values in various cases, better or equal to other methods, in most of the scenarios, the better results were achieved by RA or TA. Even though, it is difficult to evaluate this disadvantage because there are no recipes to assess a difference of one RCF point. Indeed, results are in terms of an absolute value coming from penalty functions, but it results in being hard to estimate which difference is significant. We expect to find a valuable answer by using the generated packetization masks for communicating images through unreliable channels, as commented in the following subsection. Anyway, the first results are encouraging, and future works could enhance these indicators by applying other kinds of operators or (event) computing approaches, such as parallel or distributed computing.
About the execution times, the eventual enhancing of the resulting patterns allowed by using metaheuristics contrasts with their required time of execution. Indeed, the calculation of TA (and other deterministic methods) is performed in a few milliseconds [
11]. Actually, TA complexity is low enough to be implemented in very resource-constrained hardware [
8]. Simulation times for RA and GA are summarized in
Figure 5. Of course, execution times depend on the hardware adopted and the implementation itself. For the executions of the selected scenarios, our implementations of RA and GA spend almost the same time. For example, for a
mask (mask size = 1024), the obtained average execution times are around 250 and 268 minutes for GA and RA, respectively. This is much too complex for being applied in real time or resource-constrained devices, even if enhancements can be allowed by using other kinds of platforms (like parallel or distributed computing), but the real goal of applying metaheuristics for this kind of problem is to provide optimal parameters for off-line analysis and design. In particular, this kind of solution can be valuable for, e.g., providing comparison references to evaluate how “optimal”a packetization mask, obtained by deterministic/fast methods, is, the off-line design of the optimal packetization mask for sensor hardware or interleaver chip designs, etc.
4.2. Image Quality Assessment Results
Results reported in
Section 4.1 allow one to observe the behavior of our GA compared with the considered related works RA and TA, in terms of their reached RCF values. From all of the executions, from each of the considered method, we select the best obtained patterns (masks) in order to evaluate the improvement in the quality of images transmitted through unreliable media using simulation framework Sim-LIT 2.0 [
37]. Sim-LIT allows analyzing the effects of packet loss in communicated images, providing results in terms of the well-known quality assessment metric PSNR (Peak Signal-to-Noise Ratio). As said above, the considered scenarios are based on WVSN, so we select images in typically adopted resolutions and color depths. For testing purposes, we select:
eight different loss rates: 10%, 20%, 30%, 40%, 50%, 60%, 70%, and 80%,
200 different, randomly generated, loss distributions, for each different PLR, and
eight different uncompressed (raw) 8 bpp grayscale images.
For testing, and in order to consider different kinds of images, we select classical testing images Baboon, Barbara, Cameraman, F-16, Goldhill, Lena, Peppers and Sailboat, which are depicted in
Figure 6.
For estimating the intensities of missing pixels, we adopt the average value of an eight-connected pixel neighborhood, as the error concealment technique.
Finally, the considered parameters defining the simulation scenarios are summarized in
Table 4.
Simulation results are presented separately by packetization mask and image. Without loss of generality and due to the enormous quantity of obtained data, we describe only results analysis Scenario A and examples of reconstructed images for Scenario B. We must argue that the rest of the scenarios and executed simulations behave in a similar way. With this, we attempt to provide results to validate the suitability of the selected metric.
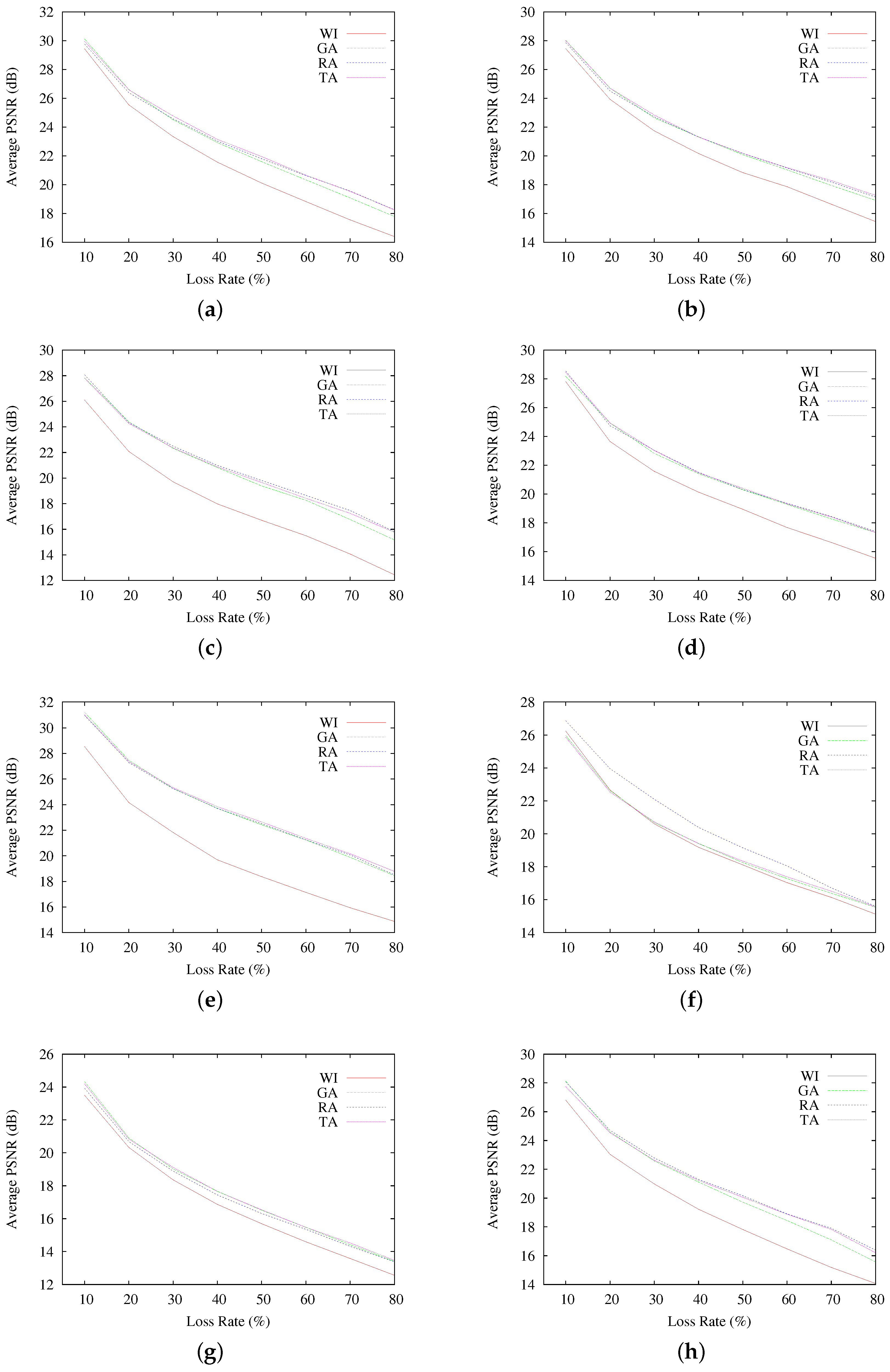
Figure 7 presents the average PSNR of reconstructed images, as a function of the loss rate. Each graphed average result corresponds to the 200 resulting images at each different PLR. As seen, in terms of average PSNR, interleaving-based communication using GA, RA and TA indeed achieves better qualities of the reconstructed images than the sequential communication case (WI). However, the obtained quality results do not allow one to observe discernible differences among the selected interleaving schemes, resulting in average PSNR fairly similar for all GA, RA and TA, even if they obtain quite different RCF results. A similar observation can be made by looking at the results in
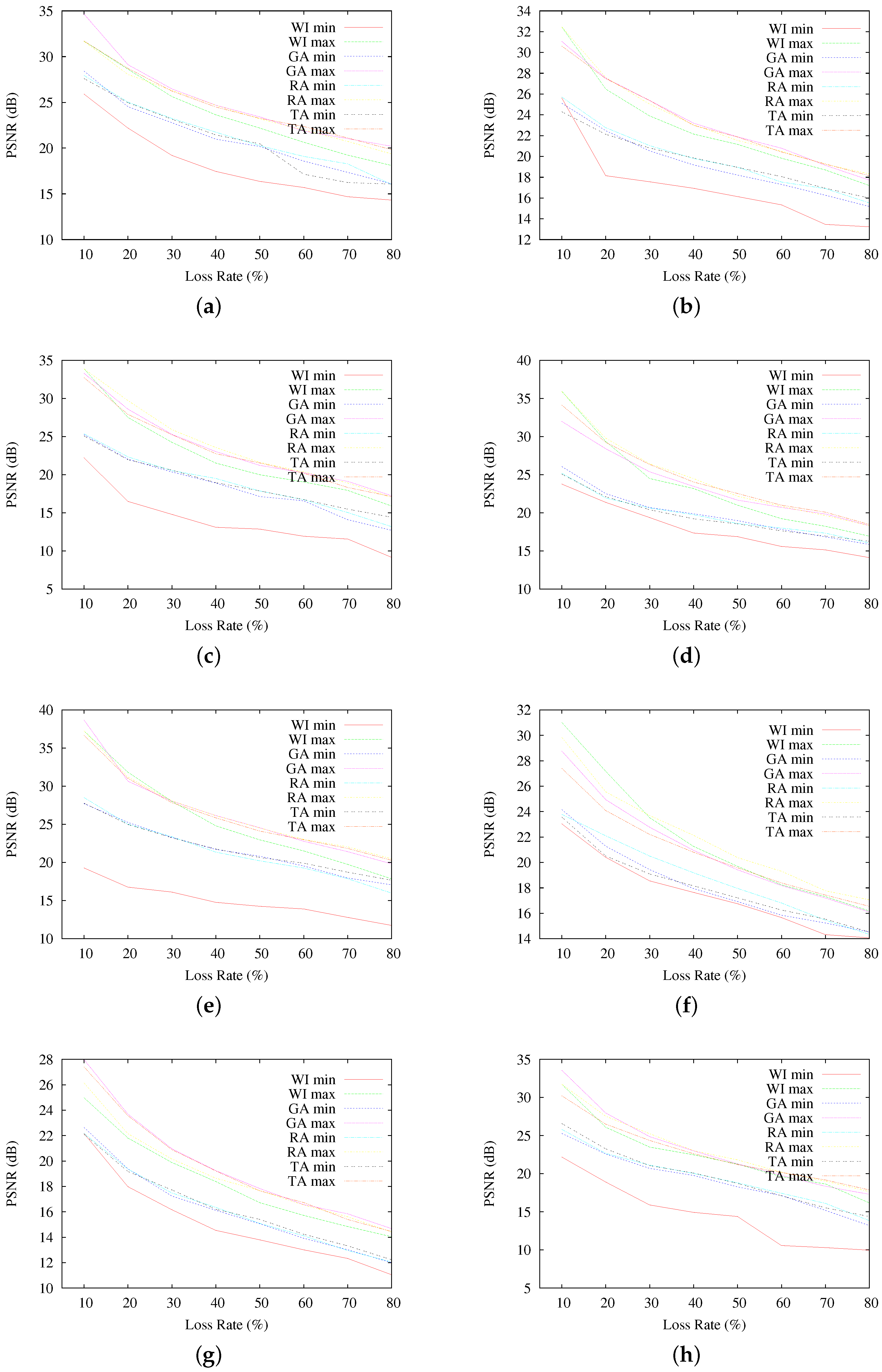
Figure 8, where the highest and lowest resulting PSNR for all of the reconstructed images are presented.
Reconstructed images from Scenario B in
Table 5 show the effect of data loss, when applying a packet loss rate of 50%, per each of the adopted images used in the simulations. These results correspond to the highest reached PSNR from the 200 loss distributions (at a 50% PLR) after applying the best GA packetization mask and WI communication. As seen, even if the resulting RCF for the WI and GA cases are distant, the obtained image qualities are similar, as when high PLR occurs, a good packetization in terms of RCF does not ensure good reconstruction of missing information. This is rather a combination of factors, including error concealment and the losses’ nature.
Table 6 shows the Baboon image reconstructed after applying different loss rates (10%, 30%, 50% and 70%), for the WI case and the interleaving-based schemes based on GA, RA and TA according to their best resulting packetization masks (from the 200 distributions), corresponding to Scenario B. As the previous case, even if the resulting RCF are different, PSNR results are fairly similar.
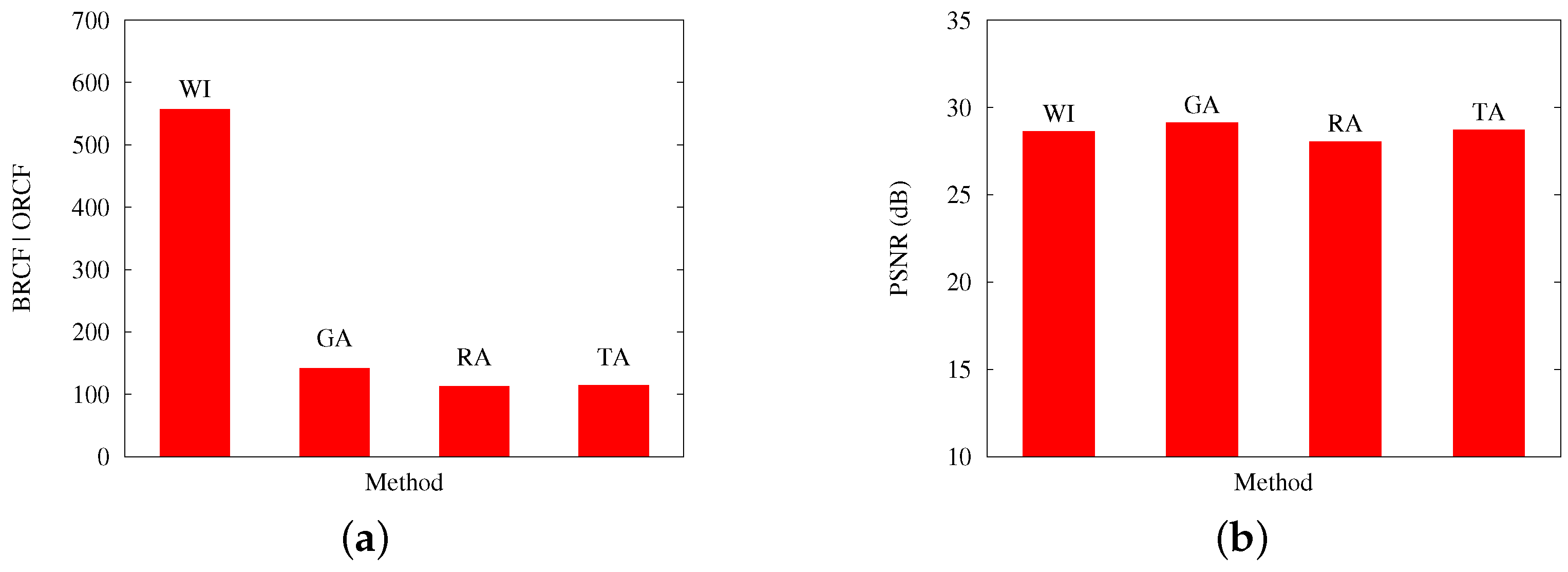
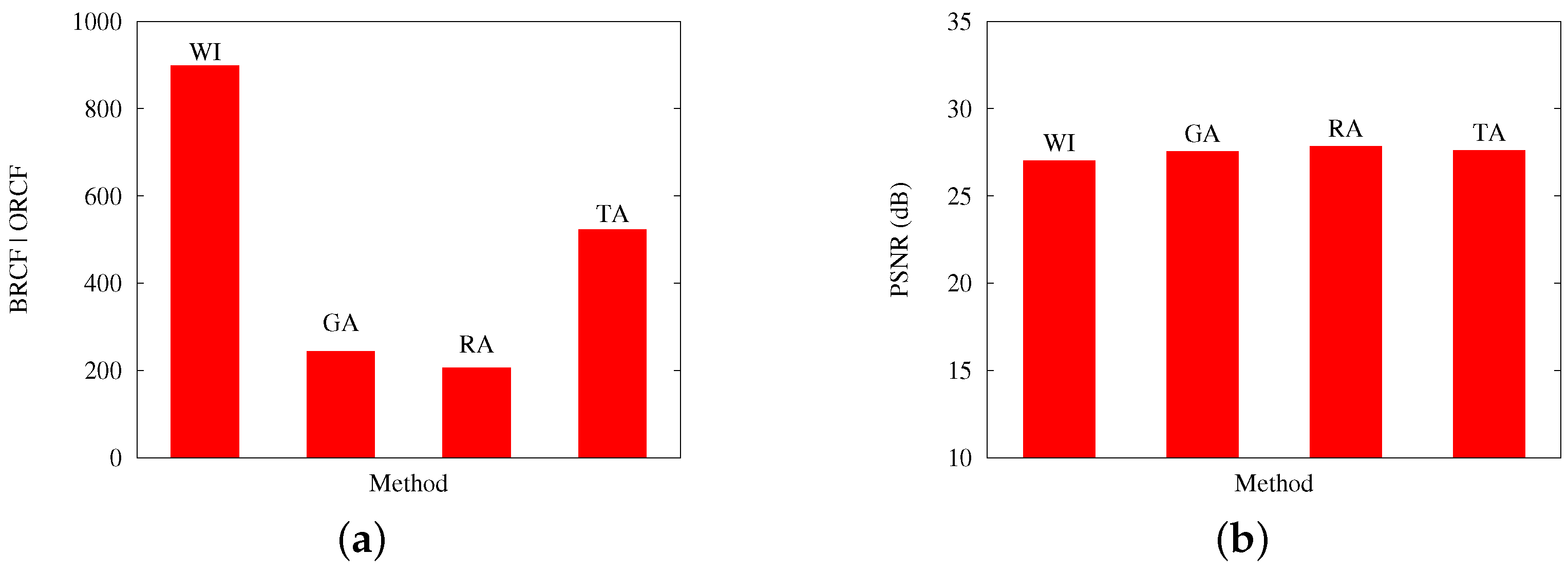
The previous comments are reinforced by
Figure 9 and
Figure 10, which contrast, for Scenarios A and B, respectively: (a) the best obtained RCF per algorithm; and (b) the best PSNR results. Both cases present results with an applied loss rate of 20%