Novel Hybrid Scheduling Technique for Sensor Nodes with Mixed Criticality Tasks
Abstract
:1. Introduction
2. Related Work
3. System Model, Notations and Assumptions
- Ti: the period, if τi is periodic, or the minimum inter-arrival time of its jobs, if τi is a sporadic task;
- Ci: the computational cost of τi, defined as the worst-case execution time (WCET) among all jobs issued by τi;
- Di: the relative deadline of τi, defined as the maximum allowable response time of any job generated by this task;
- Ui: the worst-case processor utilization factor of τi, defined as the ratio Ci/Ti; the system (total) utilization factor is denoted as U = ∑iUi; and
- In addition to these parameters we included another parameter to describe the criticality level:
- Li: the criticality level.
4. H2RTS: The Hybrid Hard Real-Time Scheduling Algorithm
- Providing the system predictability and timeliness even under worst-case operating conditions;
- Maximizing the efficiency of highly predictable scheduling techniques, regarding mainly the processor utilization factor;
- Reducing the schedulability analysis effort (time and complexity); and
- Keeping the system overhead introduced by the online task scheduling and execution mechanisms at a low value.
4.1. FENP Scheduling Algorithm
4.2. MEDF Scheduling Algorithm
- (a)
- it has not been already executed within its period (the last executed instance is kj); and
- (b)
- its absolute deadline is the closest to t among all the other MEDF tasks which are also ready. After selecting the task to be scheduled next (εj), its start time will either be the current moment (t), or the start of its next period (kjTj), if the current period has not elapsed yet.
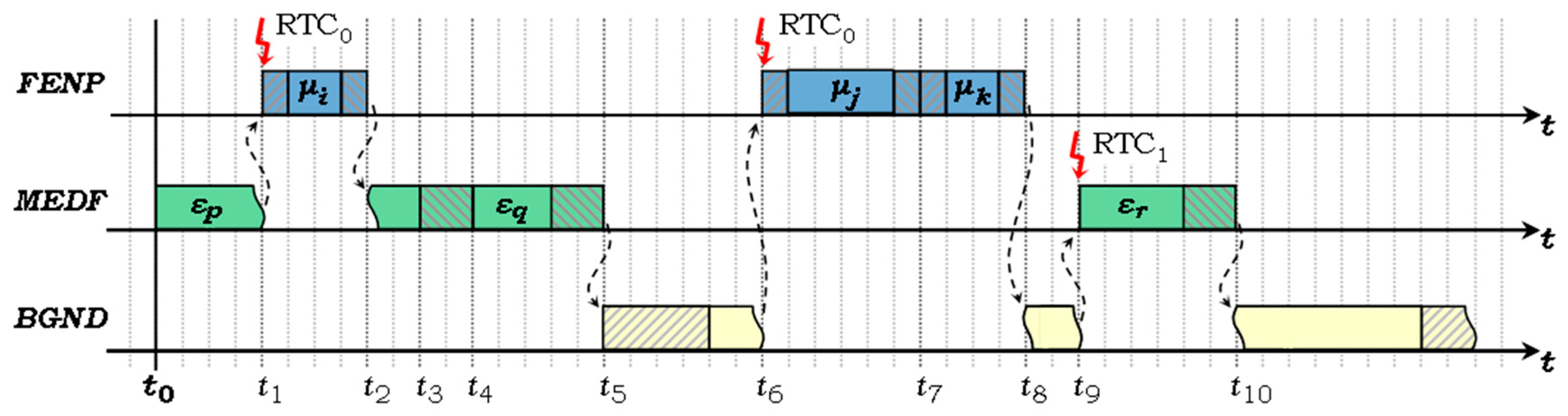
4.3. H2RTS Hybrid Scheduling Method
- (a)
- The first subset, SFENP ≡ {μ1, μ2, ..., μm}, contains the tasks with perfect synchronous operating requirements, which are scheduled with the FENP algorithm, and executed in the highest priority, non-preemptive context, a context which can be considered the highest criticality level of the system (marked as “extreme” in the task model).
- (b)
- The second subset, SMEDF ≡ {ε1, ε2, ..., εn}, also consists of tasks with hard timing specifications, but which do not require perfect periodic operation. They are dynamically scheduled with the MEDF algorithm and are executed in a semi-preemptive context, i.e., any active εj task can be preempted only by tasks in the FENP context, which represents a higher criticality level. This context is also a high criticality context (marked as “high” in the task model), but having a smaller priority compared to the FENP context.
- (c)
- Additionally, we consider a third execution context (“background context—BGND”), of the lowest priority and criticality level (marked as “low” in the task model), which accommodates tasks with soft or without any timing specifications. These are scheduled using traditional multitasking/multi-threading techniques with or without priorities, such as round-robin or multilevel queue algorithms. Further details regarding this context are out of the scope of this paper and, hence, our discussion resumes to the task system in Equation (1).
4.4. Runtime Overhead Analysis
- (a)
- FENP execution context is supported by the online scheduler and the task dispatcher. Runtime scheduling of the FENP tasks is carried out, based on periodic scheduling cycles (or frames), by a scheduling task, which fills a Dispatch Table with the task IDs and start times of each scheduling cycle. The runtime scheduler is also a FENP task, part of the SFENP subset (μj in Figure 1, for example), and thus it takes itself too into consideration when applying the scheduling algorithm.
- (b)
- MEDF execution context is supported by the online scheduling module, which is called upon the completion of each MEDF job. It serves also as a dispatcher, as it prepares the execution of the next job, either by launching it immediately, if the job is ready, or by programming the RTC1 timer interrupt, as in the case of εr in Figure 1. The execution time of the MEDF scheduling module is added to the computational cost of each task εj (j = 1…n) during offline system schedulability analysis and is also considered when scheduling each MEDF task at runtime.
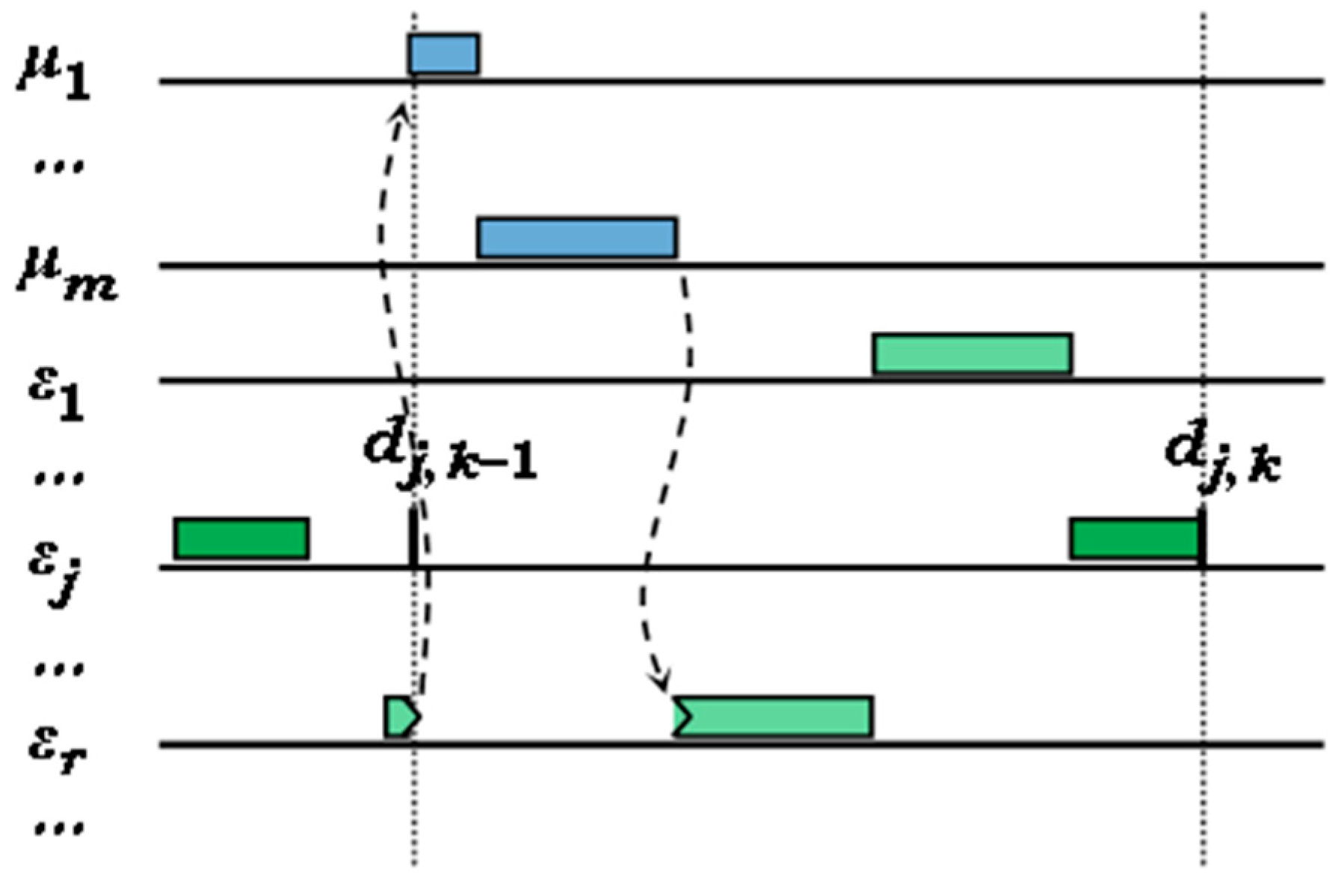
5. Integrated Schedulability Analysis of H2RTS
5.1. Preliminaries
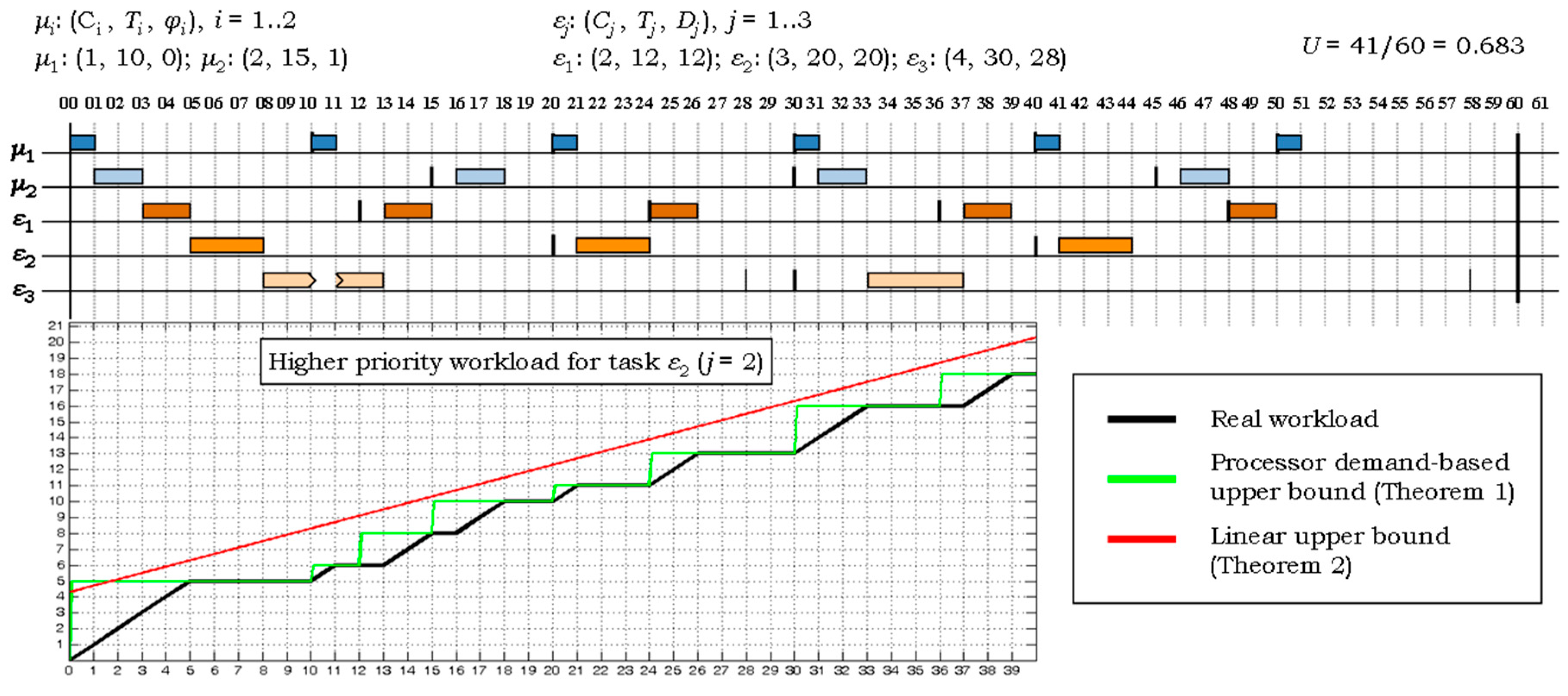
5.2. Schedulability Analysis of the H2RTS Algorithm
- (a)
- SFENP is feasible, and
- (b)
- (a)
- SFENP is feasible, and
- (b)
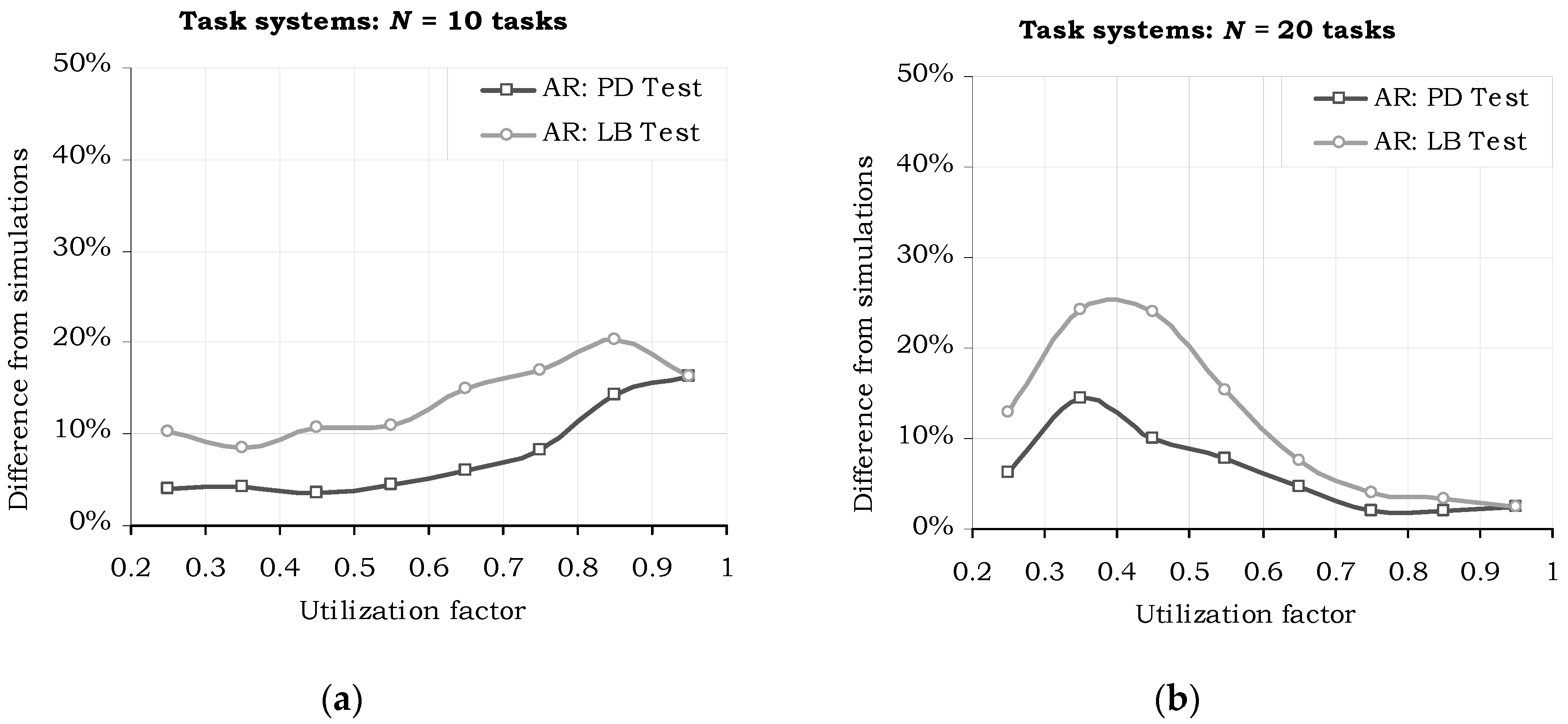
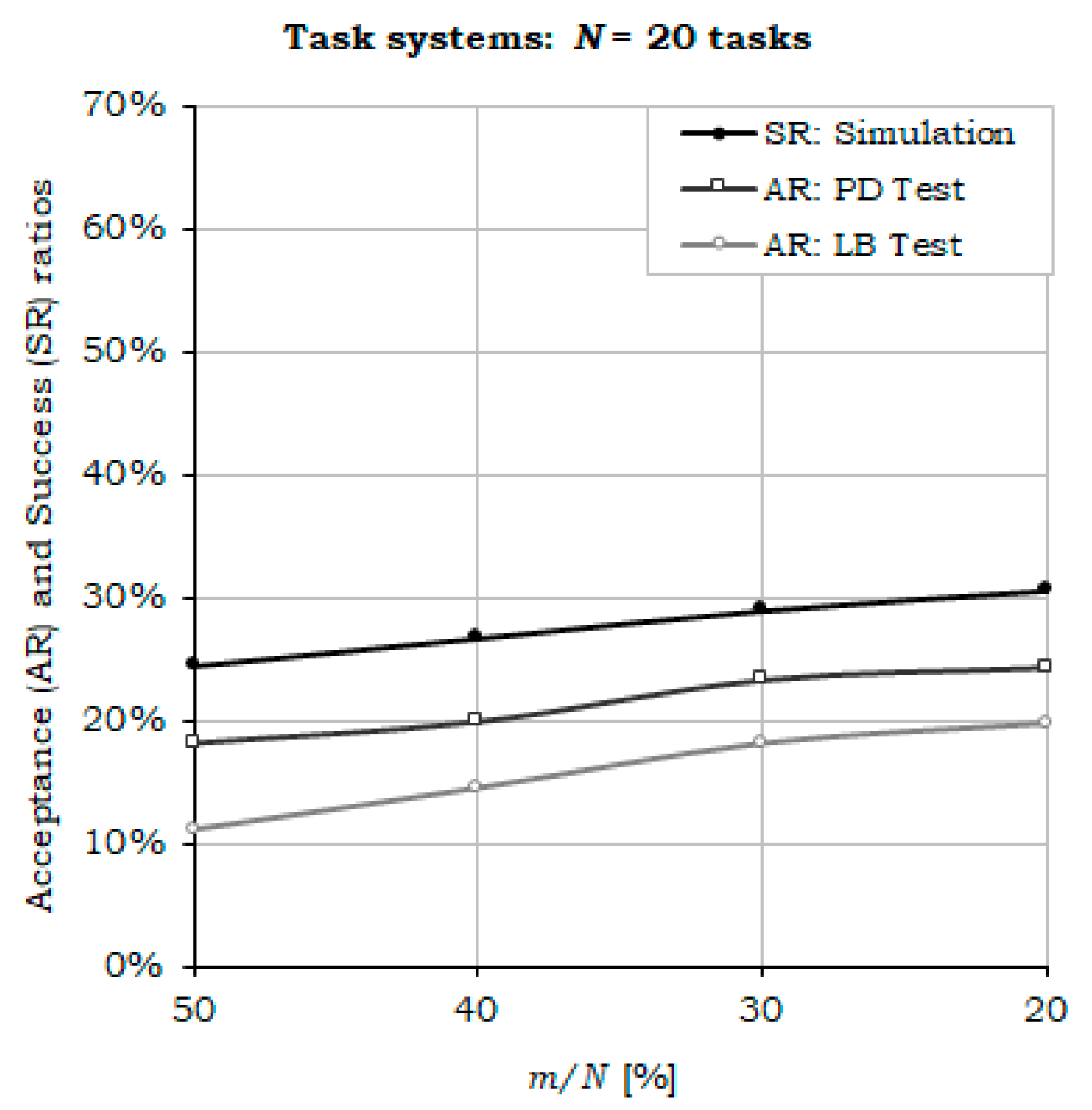
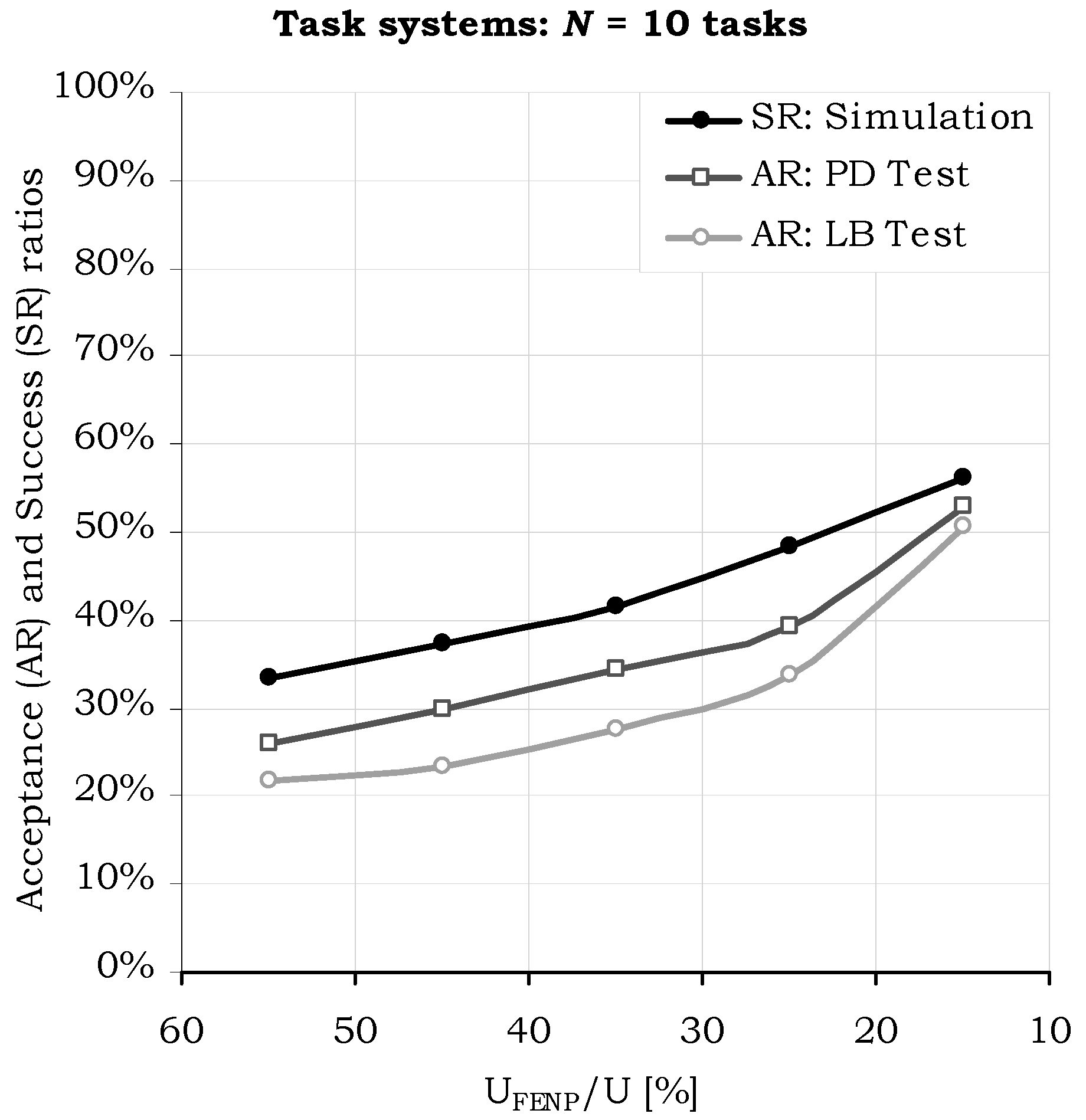
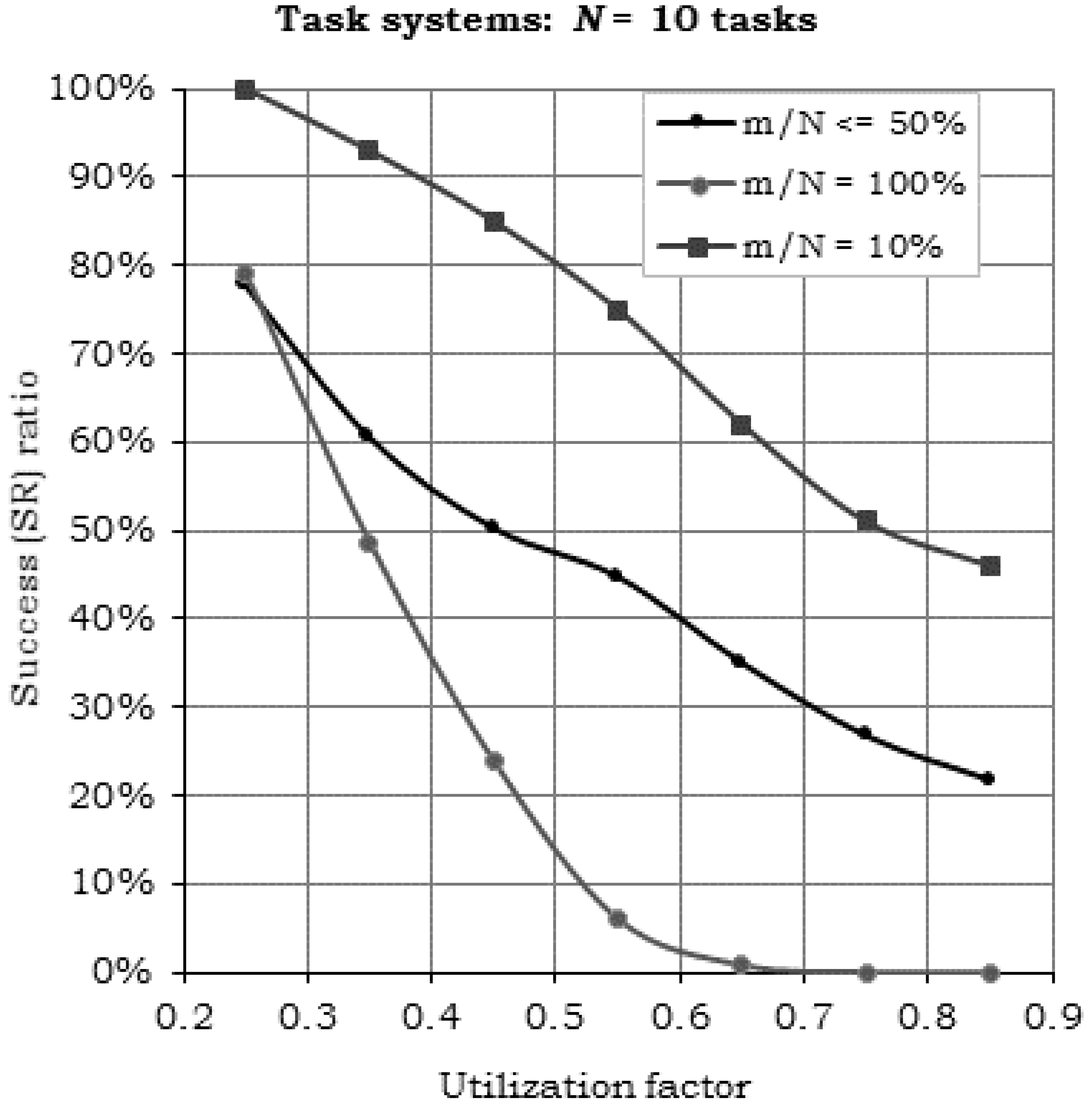
6. Performance Evaluation and Experimental Results
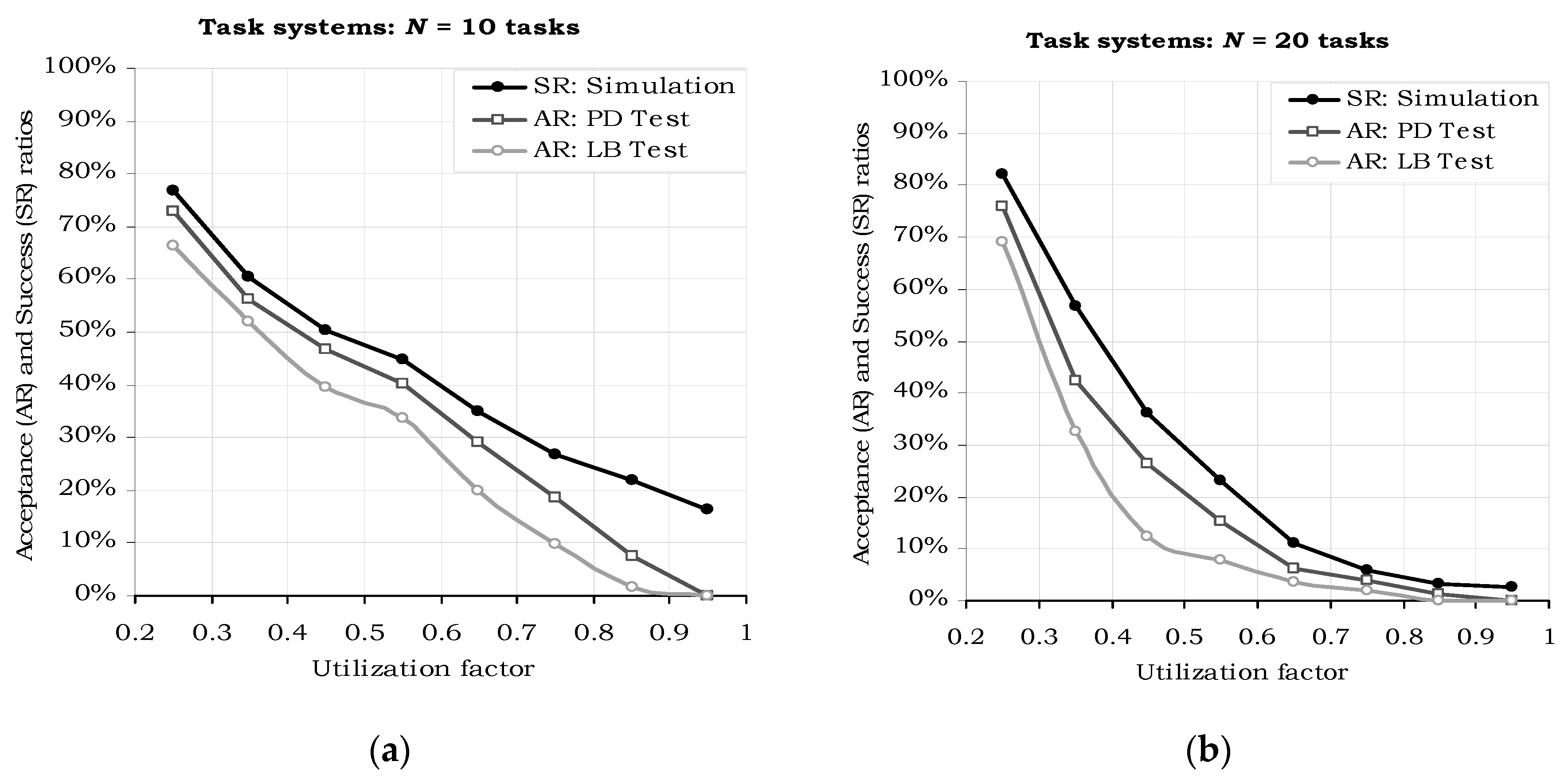
6.1. Performance Analysis
- The task period, Ti, is usually defined by the user; therefore, treating periods as random numbers does not reflect the real situations. Moreover, tasks can have harmonic relations between their periods which cannot be reflected by random numbers.
- The computation time, Ci, depends on the platform where the application runs and it cannot be estimated without a prior knowledge of the tasks. Moreover, to consider a uniform distribution of the Ci on the [0, Ti] interval is equivalent to consider the processor utilization factor Ui uniform on the [0, 1] interval.
- The processor utilization factor of a task, Ui, is proposed to be taken into consideration, because of the numerous algorithms that actually depend on it. In addition, a randomly generated uniform distribution of Ui is closer to the real situations.
- Compared to the case, where m/N = 10%, H2RTS method (m/N ≤ 50%) provides up to 50% jitter-less task execution, but reduced the success ratio by a factor of 24.25%.
- Compared with the limit case, when S = SFENP (m/N = 100%), H2RTS offers an increase of success ratio with 21.79%, but a decrease in the number of tasks with jitter-less execution up to 50%.
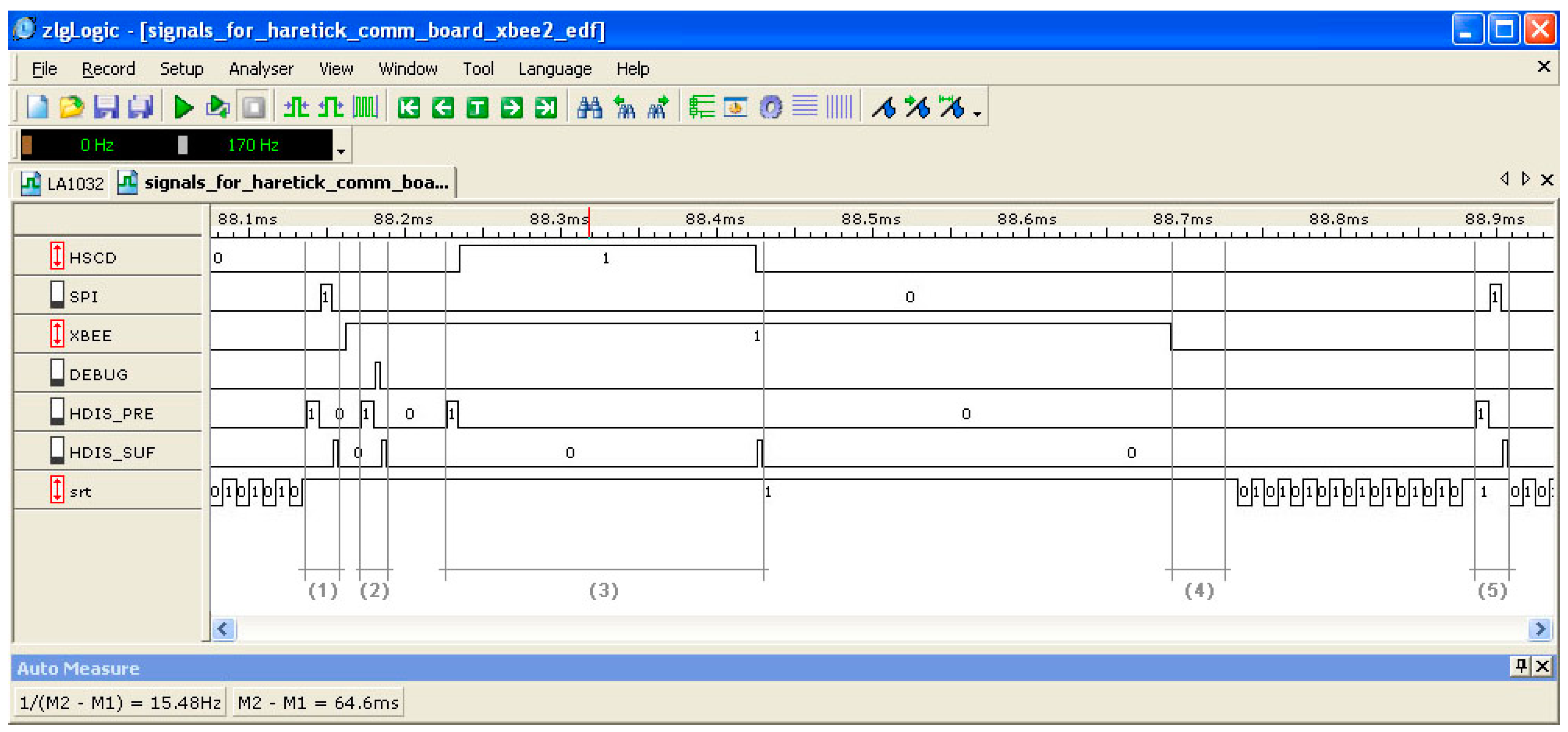
6.2. Experimental Validation
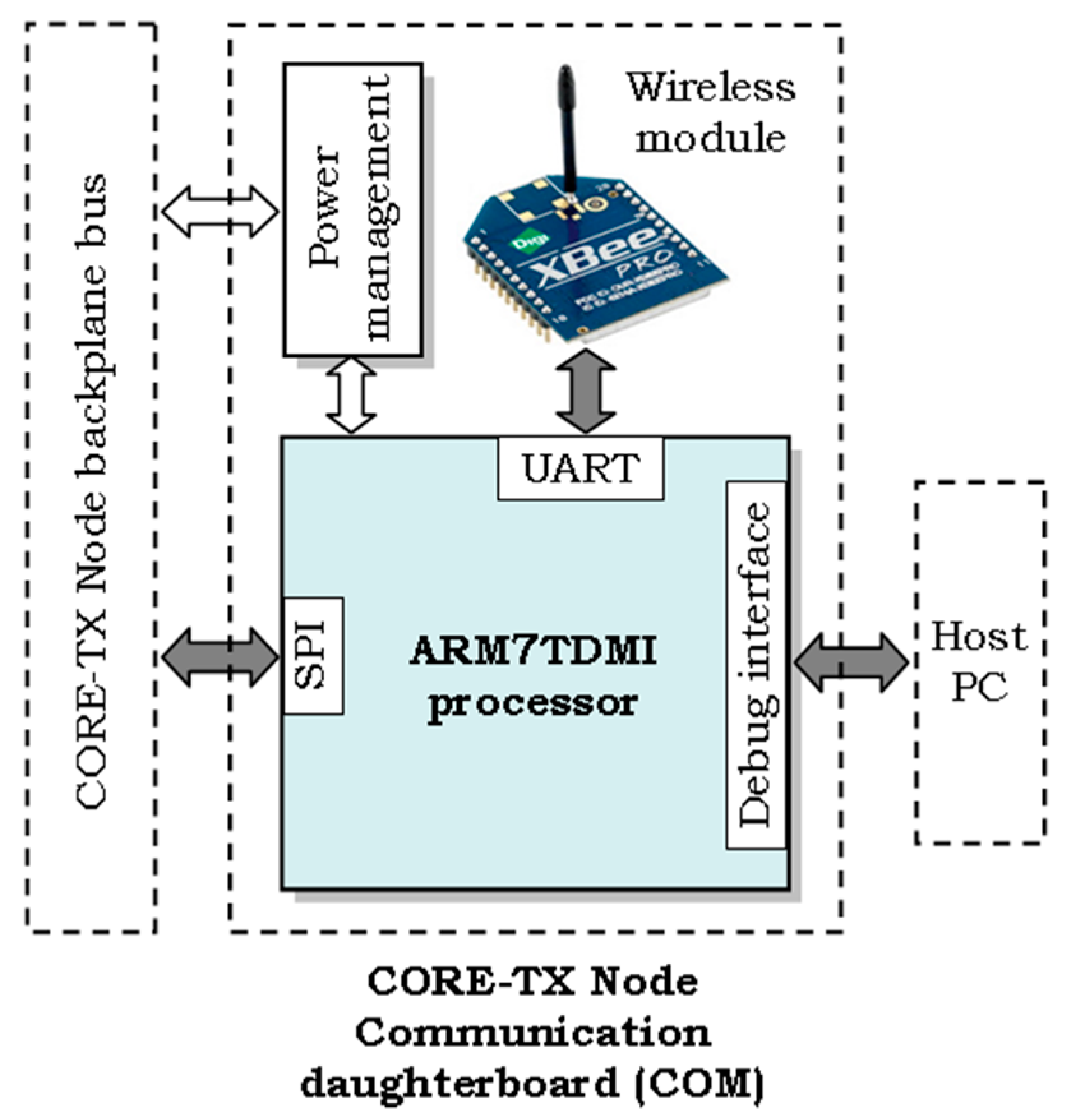
- Communication with the other CORE-TX node boards, including the motherboard, which generates and processes the wireless data at node level. The SPI synchronous interface is used by this task and, therefore, it must be scheduled with hard real-time constraints to obtain a minimum execution jitter.
- Control of and communication with the onboard wireless module (an XBee module in our case), to provide the necessary data exchanges with the other nodes of the wireless network. This task uses the UART interface, which also needs to be operated in a hard real-time manner. Nevertheless, due to its asynchronous behavior and relatively low bit rates, it does not require a perfectly synchronous operation as in the case of the SPI task.
- Exchange and process debug and execution trace information with a host PC, to provide additional experimental data, besides the direct measurements performed with the oscilloscope and the logic analyzer. To prevent loss of debug and trace information during the exchanges with the host PC, this task is executed with synchronous, hard real-time specifications, similarly to the SPI task.
- Various, local data processing and control operations are included in a common processing task, which does not require real-time execution.
7. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Baruah, S.; Bonifaci, V.; D’Angelo, G.; Li, H.; Marchetti-Spaccamela, A.; Megow, N.; Stougie, L. Scheduling real-time mixed-criticality jobs. IEEE Trans. Comput. 2012, 61, 1140–1152. [Google Scholar] [CrossRef]
- Micea, M.V.; Cretu, V.I.; Groza, V. Maximum predictability in signal interactions with HARETICK kernel. Instrum. Meas. IEEE Trans. 2006, 55, 1317–1330. [Google Scholar] [CrossRef]
- Stankovic, J.A.; Spuri, M.; Ramamritham, K.; Buttazzo, G.C. Deadline Scheduling for Real-Time Systems: EDF and Related Algorithms; Springer Science & Business Media: New York, NY, USA, 2012; Volume 460, ISBN 1461555353. [Google Scholar]
- Farooq, M.O.; Kunz, T. Operating Systems for Wireless Sensor Networks: A Survey. Sensors 2011, 11, 5900–5930. [Google Scholar] [CrossRef] [PubMed]
- Liu, X.; Hou, K.; de Vaulx, C.; Shi, H.; Gholami, K. MIROS: A Hybrid Real-Time Energy-Efficient Operating System for the Resource-Constrained Wireless Sensor Nodes. Sensors 2014, 14, 17621–17654. [Google Scholar] [CrossRef] [PubMed]
- Levis, P.; Madden, S.; Polastre, J.; Szewczyk, R.; Whitehouse, K.; Woo, A.; Gay, D.; Hill, J.; Welsh, M.; Brewer, E. TinyOS: An operating system for sensor networks. In Ambient Intelligence; Springer: New York, NY, USA, 2005; pp. 115–148. [Google Scholar]
- Dunkels, A.; Gronvall, B.; Voigt, T. Contiki-a lightweight and flexible operating system for tiny networked sensors. In Proceedings of the 29th Annual IEEE International Conference on Local Computer Networks, Tampa, FL, USA, 16–18 November 2004; pp. 455–462. [Google Scholar]
- Cao, Q.; Abdelzaher, T.; Stankovic, J.; He, T. The liteos operating system: Towards unix-like abstractions for wireless sensor networks. In Proceedings of the International Conference On Information Processing in Sensor Networks, St. Louis, MO, USA, 22–24 April 2008; pp. 233–244. [Google Scholar]
- Bhatti, S.; Carlson, J.; Dai, H.; Deng, J.; Rose, J.; Sheth, A.; Shucker, B.; Gruenwald, C.; Torgerson, A.; Han, R. MANTIS OS: An embedded multithreaded operating system for wireless micro sensor platforms. Mob. Netw. Appl. 2005, 10, 563–579. [Google Scholar] [CrossRef]
- Eswaran, A.; Rowe, A.; Rajkumar, R. Nano-rk: An energy-aware resource-centric rtos for sensor networks. In Proceedings of the 26th IEEE International Real-Time Systems Symposium (RTSS 2005), Miami, FL, USA, 5–8 December 2005. [Google Scholar]
- Baruah, S.K.; Bonifaci, V.; D’Angelo, G.; Marchetti-Spaccamela, A.; Van Der Ster, S.; Stougie, L. Mixed-criticality scheduling of sporadic task systems. Eur. Symp. Algorithms 2011, 555–566. [Google Scholar] [CrossRef]
- Li, H.; Baruah, S. An algorithm for scheduling certifiable mixed-criticality sporadic task systems. In Proceedings of the 31st IEEE Real-Time Systems Symposium (RTSS), San Diego, CA, USA, 30 November–3 December 2010; pp. 183–192. [Google Scholar]
- Baruah, S.K. Optimal utilization bounds for the fixed-priority scheduling of periodic task systems on identical multiprocessors. IEEE Trans. Comput. 2004, 53, 781–784. [Google Scholar] [CrossRef]
- Socci, D.; Poplavko, P.; Bensalem, S.; Bozga, M. Mixed critical earliest deadline first. In Proceedings of the 25th Euromicro Conference on Real-Time Systems, Paris, France, 9–12 July 2013; pp. 93–102. [Google Scholar]
- Ren, J.; Phan, L.T.X. Mixed-criticality scheduling on multiprocessors using task grouping. In Proceedings of the 27th Euromicro Conference on Real-Time Systems, Lund, Sweden, 8–10 July 2015; pp. 25–34. [Google Scholar]
- Gratia, R.; Robert, T.; Pautet, L. Scheduling of mixed-criticality systems with RUN. In Proceedings of the IEEE 20th Conference on Emerging Technologies & Factory Automation (ETFA), Luxembourg, 8–11 September 2015; pp. 1–8. [Google Scholar]
- Dobrin, R.; Fohler, G.; Puschner, P. Translating Off-line Schedules into Task Attributes for Fixed Priority Scheduling. In Proceedings of the 22nd IEEE Real-Time Systems Symposium, London, UK, 3–6 December 2001. [Google Scholar]
- Tianzhou, C.; Wei, H.; Bin, X.; Like, Y. A Real-Time Scheduling Algorithm for Embedded Systems with Various Resource Requirements. In Proceedings of the International Workshop on Networking, Architecture and Storages, Shenyang, China, 1–3 August 2006. [Google Scholar]
- Seongje, C.; Suk-Kyoon, L.; Sang, A.; Kwei-Jay, L. Efficient real-time scheduling algorithms for multiprocessor systems. IEICE Trans. Commun. 2002, 85, 2859–2867. [Google Scholar]
- Micea, M.V.; Stangaciu, C.S.; Stangaciu, V.; Cretu, V.I. Improving the efficiency of highly predictable wireless sensor platforms with hybrid scheduling. In Proceedings of the IEEE International Symposium on Robotic and Sensors Environments (ROSE), Magdeburg, Germany, 16–18 November 2012; pp. 73–78. [Google Scholar]
- Vestal, S. Preemptive scheduling of multi-criticality systems with varying degrees of execution time assurance. In Proceedings of the 28th IEEE International Real-Time Systems Symposium (RTSS 2007), Tucson, AZ, USA, 3–6 December 2007; pp. 239–243. [Google Scholar]
- De Niz, D.; Lakshmanan, K.; Rajkumar, R. On the scheduling of mixed-criticality real-time task sets. In Proceedings of the 30th IEEE Real-Time Systems Symposium(RTSS 2009), Washington, DC, USA, 1–4 December 2009; pp. 291–300. [Google Scholar]
- Ekberg, P.; Yi, W. Bounding and shaping the demand of generalized mixed-criticality sporadic task systems. Real Time Syst. 2014, 50, 48–86. [Google Scholar] [CrossRef]
- Liu, C.L.; Layland, J.W. Scheduling algorithms for multiprogramming in a hard-real-time environment. JACM 1973, 20, 46–61. [Google Scholar] [CrossRef]
- Micea, M.V.; Certejan, C.; Stangaciu, V.; Goarga, R.; Cretu, V.; Petriu, E. Inter-Task Communication and Synchronization in the Hard Real-Time Compact Kernel HARETICK. In Proceedings of the 2008 International Workshop on Robotic and Sensors Environments, Ottawa, ON, Canada, 17–18 October 2008; pp. 19–24. [Google Scholar]
- Goswami, D.; Lukasiewycz, M.; Schneider, R.; Chakraborty, S. Time-triggered implementations of mixed-criticality automotive software. DATE 2012, 2012, 1227–1232. [Google Scholar]
- Micea, M.V.; Cretu, V.I. Highly predictable execution support for critical applications with HARETICK kernel. AEU Int. J. Electron. Commun. 2005, 59, 278–287. [Google Scholar] [CrossRef]
- Micea, M.V.; Carstoiu, G.N.; Ungurean, L.; Chiciudean, D.; Cretu, V.-I.; Groza, V. PARSECS: A predictable data communication system for smart sensors and hard real-time applications. IEEE Trans. Instrum. Meas. 2010, 59, 2968–2981. [Google Scholar] [CrossRef]
- Micea, M.V.; Stangaciu, V.; Stangaciu, C.; Filote, C. Sensor-Level Real-Time Support for XBee-Based Wireless Communication. In Advances in Intelligent and Soft Computing; Gaol, F.L., Nguyen, Q.V., Eds.; Springer: Berlin/Heidelberg, Germany, 2012; Volume 145, pp. 147–154. ISBN 978-3-642-28307-9. [Google Scholar]
- Balbastre, P.; Ripoll, I.; Crespo, A. Period sensitivity analysis and D–P domain feasibility region in dynamic priority systems. J. Syst. Softw. 2009, 82, 1098–1111. [Google Scholar] [CrossRef]
- Burns, A.; Wellings, A.J.; Zhang, F. Combining EDF and FP scheduling: Analysis and implementation in Ada 2005. In Reliable Software Technologies—Ada-Europe 2009; Springer: Berlin, Germany, 2009; pp. 119–133. ISBN 3642019234. [Google Scholar]
- Buttazzo, G.; Gai, P. Efficient EDF Implementation for Small Embedded Systems. In Proceedings of the OSPERT 2006—Workshop on Operating Systems Platforms for Embedded Real-Time applications, Dresden, Germany, 6 July 2006. [Google Scholar]
- Kargahi, M.; Movaghar, A. Non-preemptive earliest-deadline-first scheduling policy: A performance study. In Proceedings of the 13th IEEE International Symposium on Modeling, Analysis, and Simulation of Computer and Telecommunication Systems, Atlanta, GA, USA, 27–29 September 2005; pp. 201–208. [Google Scholar]
- Georges, L.; Mühlethaler, P.; Rivierre, N. A Few Results on Non-Preemptive Real Time Scheduling. Available online: https://hal.archives-ouvertes.fr/file/index/docid/72726/filename/RR-3926.pdf (accessed on 20 February 2017).
- Bini, E.; Buttazzo, G.C. Measuring the performance of schedulability tests. Real Time Syst. 2005, 30, 129–154. [Google Scholar] [CrossRef]
- Bini, E.; Buttazzo, G.C. Schedulability analysis of periodic fixed priority systems. IEEE Trans. Comput. 2004, 53, 1462–1473. [Google Scholar] [CrossRef]
- Bini, E.; Nguyen, T.H.C.; Richard, P.; Baruah, S.K. A Response-Time Bound in Fixed-Priority Scheduling with Arbitrary Deadlines. IEEE Trans. Comp. 2009, 58, 279–286. [Google Scholar] [CrossRef]
- Cioarga, R.-D.; Micea, M.V.; Ciubotaru, B.; Chiuciudean, D.; Stanescu, D. CORE-TX: Collective Robotic Environment-the Timisoara Experiment. In Proceedings of the IEEE International Symposium on Applied Computational Intelligence and Informatics, Timisoara, Romania, 12–14 May 2006; pp. 495–506. [Google Scholar]

| Parameter | Value/Range |
|---|---|
| Total utilization factor | U = 0.2/0.95 |
| Size of task sets (FENP + MEDF tasks) | N = m + n = {5, 10, 20} |
| FENP tasks ratio | m/N = {20%, 30%, 40%, 50%} |
| Processor utilization factor of FENP tasks versus total utilization factor | UFENP/U = 10%/60% |
| Interval for generating the task periods | Ti = 10/510 |
| Algorithm for generating the task periods | Random, with uniform distribution |
| Greatest common divisor of FENP task periods | GCD = 30 |
| Algorithm for generating the task execution times | Random, with uniform distribution |
| Additional conditions for generating the task execution times | (23) |
| Parameter | Value/Range |
|---|---|
| ARM7TDMI CPU clock | 58.9824 MHz |
| HARETICK Real-Time Clock (RTC) | 14.7456 MHz |
| XBee UART transfer rate | 57,600 bps |
| FENP execution environment: | |
| Worst case execution time (WCET) of the FENP Dispatch Prefix (HDIS_Pre) | 112 RTC cycles (7.59 μs) |
| WCET of the FENP Dispatch Suffix (HDIS_Suf) | 68 RTC cycles (4.61 μs) |
| WCET of the FENP Scheduler (HSCD) | 4052 RTC cycles (274.79 μs) |
| SPI communication task WCET (FENP task) | 310 RTC cycles (21 μs) |
| DEBUG task WCET (FENP task) | 605 RTC cycles (41 μs) |
| XBee task minimum frequency (MEDF task) | 360 Hz (considering a UART FIFO buffer of 16 frames and 10 bits per frame) |
| XBee task WCET | 4568 RTC cycles (309.79 μs) |
| Common low priority processing task, including LED toggle (SRT/BGND task) | No timing specifications |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Micea, M.-V.; Stangaciu, C.-S.; Stangaciu, V.; Curiac, D.-I. Novel Hybrid Scheduling Technique for Sensor Nodes with Mixed Criticality Tasks. Sensors 2017, 17, 1504. https://doi.org/10.3390/s17071504
Micea M-V, Stangaciu C-S, Stangaciu V, Curiac D-I. Novel Hybrid Scheduling Technique for Sensor Nodes with Mixed Criticality Tasks. Sensors. 2017; 17(7):1504. https://doi.org/10.3390/s17071504
Chicago/Turabian StyleMicea, Mihai-Victor, Cristina-Sorina Stangaciu, Valentin Stangaciu, and Daniel-Ioan Curiac. 2017. "Novel Hybrid Scheduling Technique for Sensor Nodes with Mixed Criticality Tasks" Sensors 17, no. 7: 1504. https://doi.org/10.3390/s17071504






