Secure Transmission of Cooperative Zero-Forcing Jamming for Two-User SWIPT Sensor Networks
Abstract
:1. Introduction
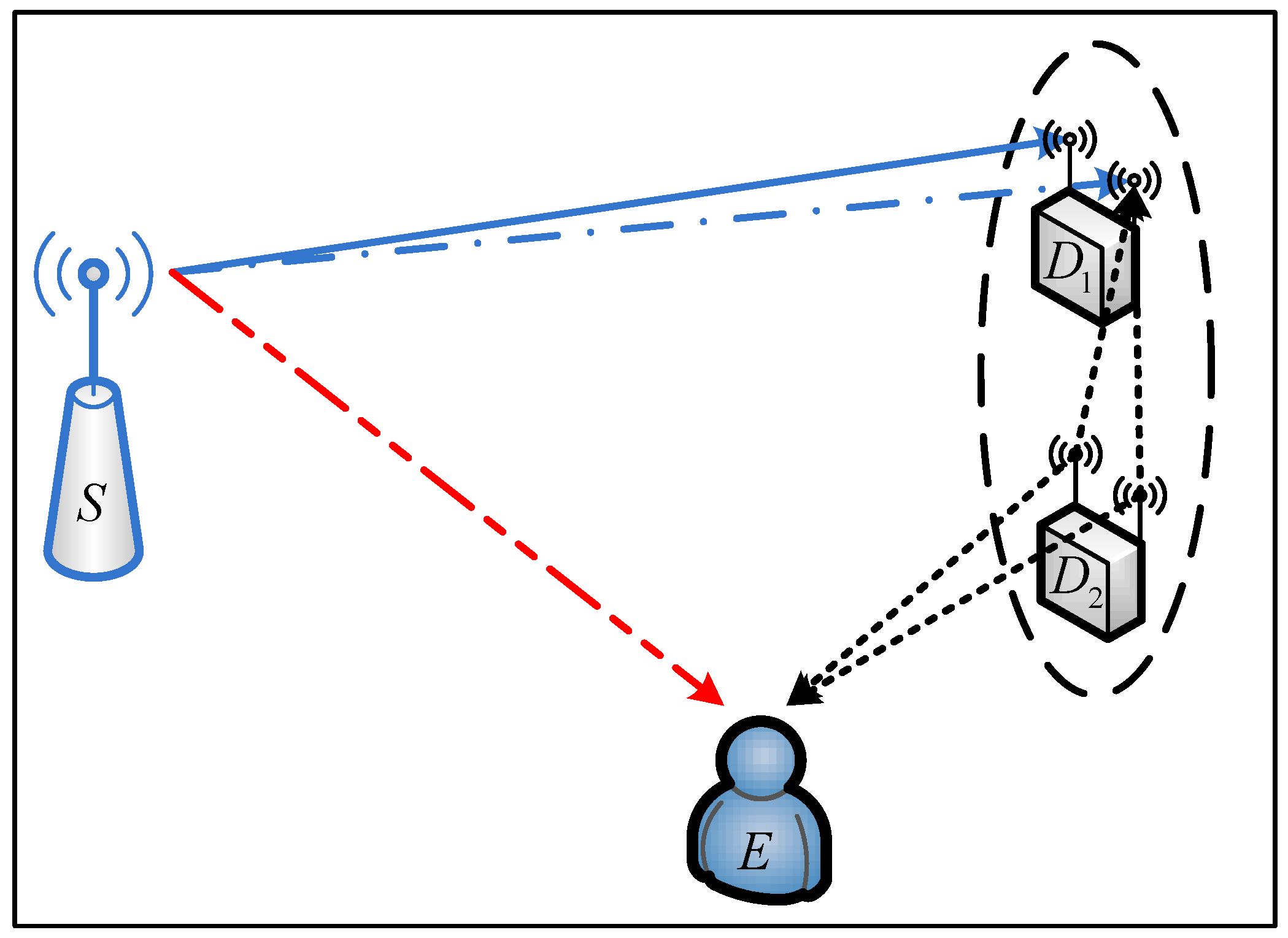
2. System Model
2.1. System Description
2.2. Secure Transmission
3. Secrecy Performance Analysis
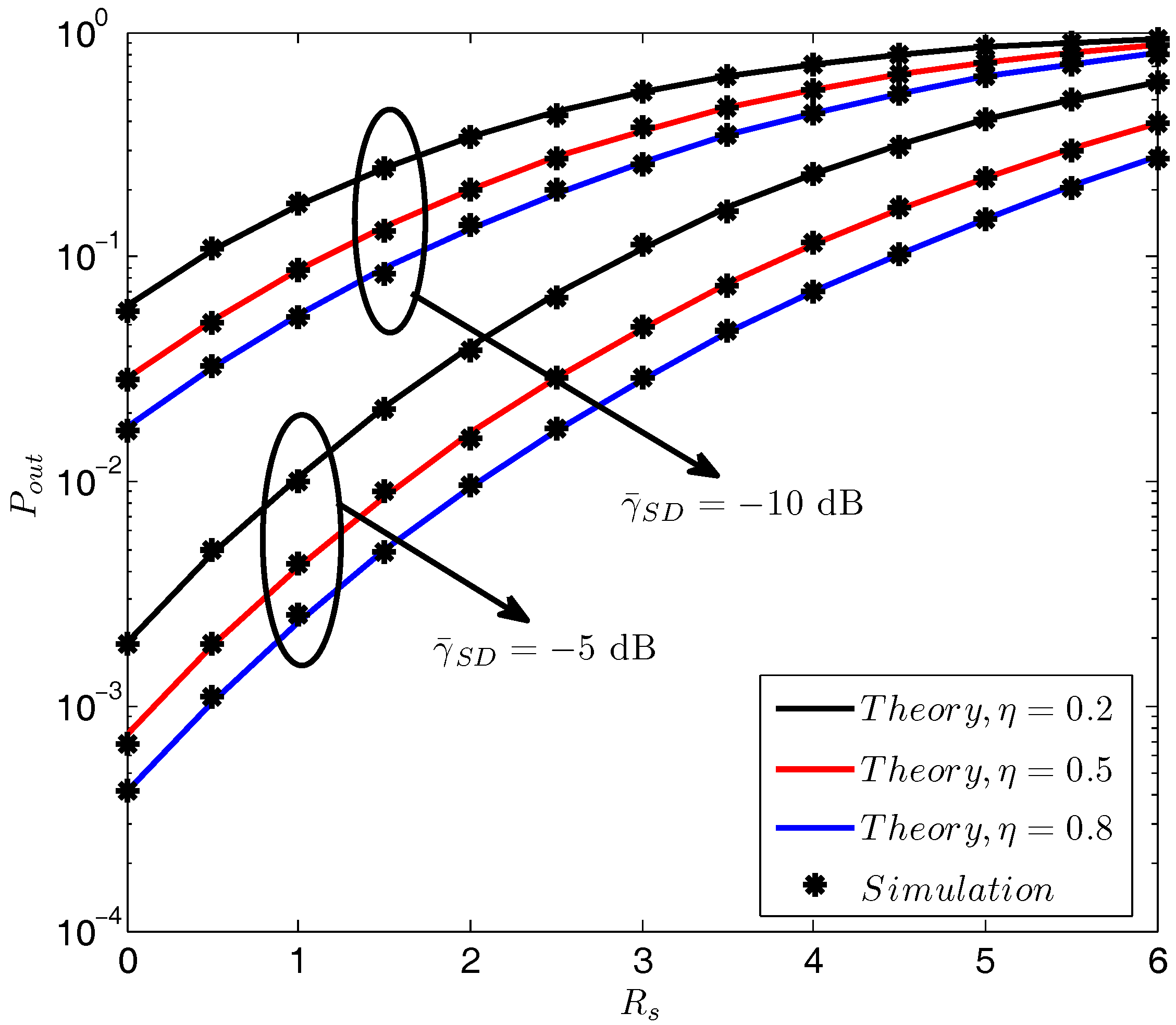
3.1. Secrecy Outage Probability
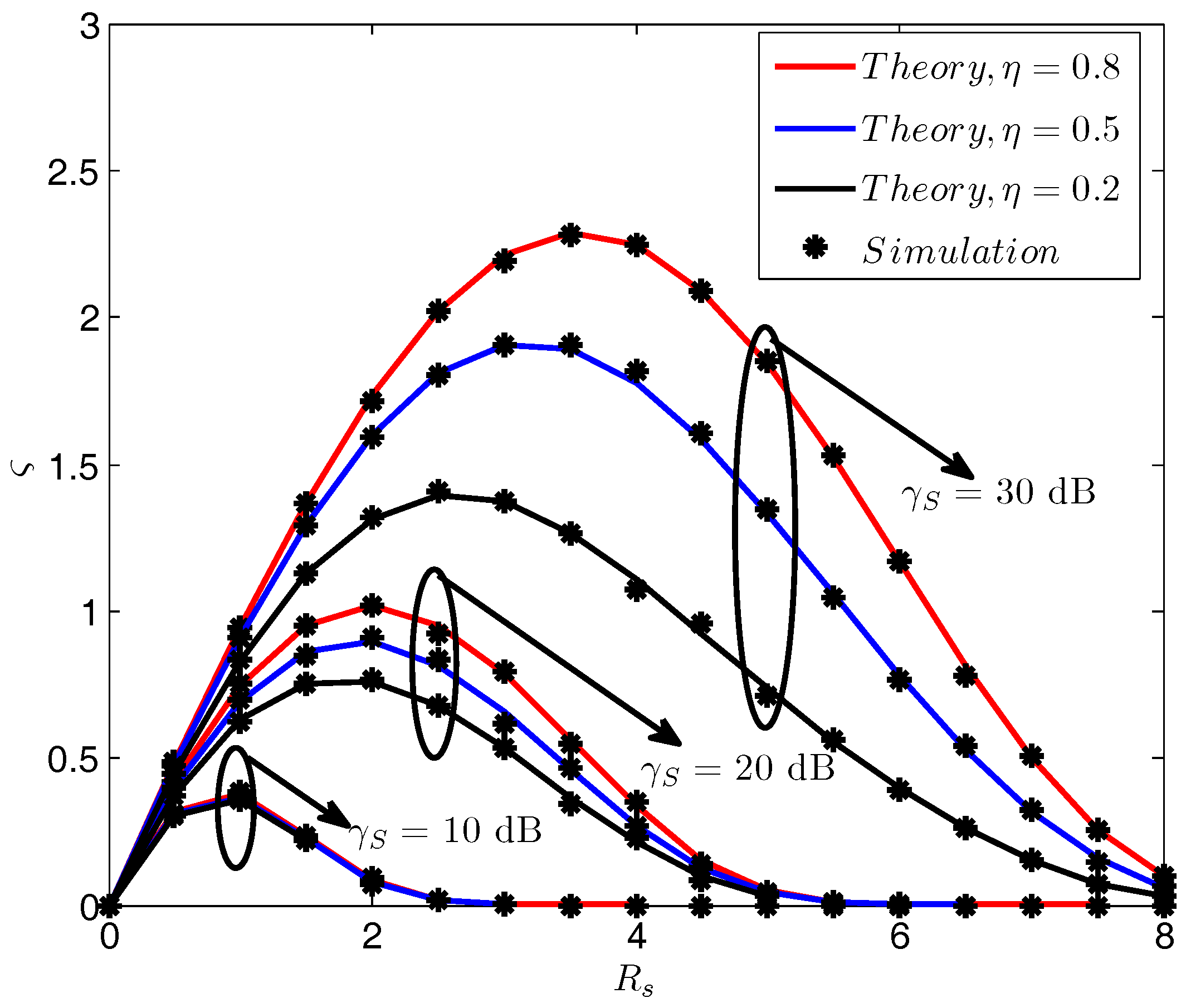
3.2. Secrecy Throughput
4. Simulation Results and Discussion
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Zheng, J.; Cai, Y.; Shen, X.; Zheng, Z.; Yang, W. Green energy optimization in energy harvesting wireless sensor networks. IEEE Commun. Mag. 2015, 53, 150–157. [Google Scholar] [CrossRef]
- Hu, J.; Yang, W.; Yang, N.; Zhou, X.; Cai, Y. On-off-based secure transmission design with outdated channel state information. IEEE Trans. Veh. Technol. 2016, 65, 6075–6088. [Google Scholar] [CrossRef]
- Mukherjee, A.; Fakoorian, S.A.A.; Huang, J.; Swindlehurst, A.L. Principles of physical layer security in multiuser wireless networks: A survey. IEEE Commun. Surv. Tutor. 2014, 16, 1550–1573. [Google Scholar] [CrossRef]
- Yang, N.; Wang, L.; Geraci, G.; Elkashlan, M.; Yuan, J.; Renzo, M.D. Safeguarding 5G wireless communication networks using physical layer security. IEEE Commun. Mag. 2015, 53, 20–27. [Google Scholar] [CrossRef]
- Tang, X.; Cai, Y.; Huang, Y.; Duong, T.Q.; Yang, W.; Yang, W. Secrecy outage analysis of buffer-aided cooperative MIMO relaying systems. IEEE Trans. Veh. Technol. 2017. [Google Scholar] [CrossRef]
- Chen, G.; Gong, Y.; Xiao, P.; Chambers, J.A. Physical layer network security in the full-duplex relay system. IEEE Trans. Inf. Forensics Secur. 2015, 10, 574–583. [Google Scholar] [CrossRef]
- Hu, J.; Cai, Y.; Yang, N.; Yang, W. A new secure transmission scheme with outdated antenna selection. IEEE Trans. Inf. Forensics Secur. 2015, 10, 2435–2446. [Google Scholar] [CrossRef]
- Zou, Y.; Wang, X.; Shen, W. Optimal relay selection for physical-layer security in cooperative wireless networks. IEEE J. Sel. Areas Commun. 2013, 31, 2099–2111. [Google Scholar] [CrossRef]
- Yang, M.Q.; Zhang, B.N.; Huang, Y.Z.; Yang, N.; Guo, D.X.; Gao, B. Secure multiuser communications in wireless sensor networks with TAS and cooperative jamming. Sensors 2016, 16, 1908. [Google Scholar] [CrossRef] [PubMed]
- Wang, C.; Wang, H.M.; Xia, X.G.; Liu, C. Uncoordinated jammer selection for securing SIMOME wiretap channels: A stochastic geometry approach. IEEE Trans. Wirel. Commun. 2015, 14, 2596–2612. [Google Scholar] [CrossRef]
- Zhang, R.; Song, L.; Han, Z.; Jiao, B. Physical layer security for two-way untrusted relaying with friendly jammers. IEEE Trans. Veh. Technol. 2012, 61, 3693–3704. [Google Scholar] [CrossRef]
- Yun, S.; Park, J.; Im, S.; Ha, J. On the secrecy rate of artificial noise assisted MIMOME channels with full-duplex receiver. In Proceedings of the IEEE Wireless Communications and Networking Conference, San Francisco, CA, USA, 19–22 March 2017; pp. 1–6. [Google Scholar]
- Liu, H.; Kim, K.J.; Kwak, K.S.; Poor, H.V. Power splitting-based SWIPT with decode-and-forward full-duplex relaying. IEEE Trans. Wirel. Commun. 2016, 15, 7561–7577. [Google Scholar] [CrossRef]
- Zhou, X. Training-based SWIPT: Optimal power splitting at the receiver. IEEE Trans. Veh. Technol. 2015, 64, 4377–4382. [Google Scholar] [CrossRef]
- Krikidis, I.; Timotheou, S.; Nikolaou, S.; Zheng, G.; Ng, D.W.K.; Schober, R. Simultaneous wireless information and power transfer in modern communication systems. IEEE Commun. Mag. 2014, 52, 104–110. [Google Scholar] [CrossRef] [Green Version]
- Liu, M.; Liu, Y. Power allocation for secure SWIPT systems with wireless-powered cooperative jamming. IEEE Commun. Lett. 2017, 21, 1353–1356. [Google Scholar] [CrossRef]
- Zhang, Q.; Huang, X.; Li, Q.; Qin, J. Cooperative jamming aided robust secure transmission for wireless information and power transfer in MISO channels. IEEE Trans. Commun. 2015, 63, 906–915. [Google Scholar] [CrossRef]
- Tang, X.; Yang, W.; Cai, Y.; Yang, W.; Cao, K.; Yuan, P. Secrecy analysis of full-duplex power-splitting SWIPT networks with artificial noise. In Proceedings of the International Workshop on Computer Science and Engineering, Beijing, China, 25–27 June 2017; pp. 950–955. [Google Scholar]
- Yang, W.; Mou, W.; Xu, X.; Yang, W.; Cai, Y. Energy efficiency analysis and enhancement for secure transmission in SWIPT systems exploiting full duplex techniques. IET Commun. 2016, 10, 1712–1720. [Google Scholar] [CrossRef]
- Zhang, J.; Pan, G.; Wang, H.M. On physical-layer security in underlay cognitive radio networks with full-duplex wireless-powered secondary system. IEEE Access 2016, 4, 3887–3893. [Google Scholar] [CrossRef]
- Zhou, X.; Maham, B.; Hjorungnes, A. Pilot contamination for active eavesdropping. IEEE Trans. Wirel. Commun. 2012, 11, 903–907. [Google Scholar] [CrossRef]
- Wang, H.M.; Zheng, T.; Mu, P. Secure MISO wiretap channels with multi-antenna passive eavesdropper via artificial fast fading. In Proceedings of the IEEE International Conference on Communications, Sydney, NSW, Australia, 10–14 June 2014; pp. 5396–5401. [Google Scholar]
- Hu, J.; Yang, N.; Zhou, X.; Yang, W.; Cai, Y. A versatile secure transmission strategy in the presence of outdated CSI. IEEE Trans. Veh. Technol. 2016, 65, 10084–10090. [Google Scholar] [CrossRef]
- Bi, Y.; Chen, H. Accumulate and jam: Towards secure communication via a wireless-powered full-duplex jammer. IEEE J. Sel. Top. Signal Process. 2016, 10, 1538–1550. [Google Scholar] [CrossRef]
- Afana, A.; Asghari, V.; Ghrayeb, A.; Affes, S. On the performance of cooperative relaying spectrum-sharing systems with collaborative distributed beamforming. IEEE Trans. Commun. 2014, 62, 857–871. [Google Scholar] [CrossRef]
- Afana, A.; Asghari, V.; Ghrayeb, A.; Affes, S. Cooperative relaying in spectrum-sharing systems with beamforming and interference constraints. In Proceedings of the 2012 IEEE 13th International Workshop on Signal Processing Advances in Wireless Communications (SPAWC), Cesme, Turkey, 17–20 June 2012; pp. 429–433. [Google Scholar]
- Zhang, T.; Cai, Y.; Huang, Y.; Duong, T.Q.; Yang, W. Secure full-duplex spectrum-sharing wiretap networks with different antenna reception schemes. IEEE Trans. Commun. 2017, 65, 335–346. [Google Scholar] [CrossRef]
- Zhang, T.; Huang, Y.; Cai, Y.; Zhong, C.; Yang, W.; Karagiannidis, G. Secure multi-antenna cognitive wiretap networks. IEEE Trans. Veh. Technol. 2017, 66, 4059–4072. [Google Scholar] [CrossRef]
- Zeng, Y.; Zhang, R. Full-duplex wireless-powered relay with self-energy recycling. IEEE Wirel. Commun. Lett. 2015, 4, 201–204. [Google Scholar] [CrossRef]
- Gradshteyn, I.S.; Ryzhik, I.M. Table of Integrals, Series, and Products, 7th ed.; Elsevier/Academic Press: Amsterdam, The Netherlands, 2007. [Google Scholar]
- Xu, X.; Yang, W.; Cai, Y.; Jin, S. On the secure spectral-energy efficiency tradeoff in random cognitive radio networks. IEEE J. Sel. Areas Commun. 2016, 34, 2706–2722. [Google Scholar] [CrossRef]
- Yan, S.; Yang, N.; Geraci, G.; Malaney, R.; Yuan, J. Optimization of code rates in SISOME wiretap channels. IEEE Trans. Wirel. Commun. 2015, 14, 6377–6388. [Google Scholar] [CrossRef]
- Wang, L.; Cai, Y.; Zou, Y.; Yang, W.; Hanzo, L. Joint relay and jammer selection improves the physical layer security in the face of CSI feedback delays. IEEE Trans. Veh. Technol. 2016, 65, 6259–6274. [Google Scholar] [CrossRef]


| Sensor | Antenna | Working Mode |
|---|---|---|
| Information receiving | ||
| Energy harvesting | ||
| Zero-forcing jamming | ||
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tang, X.; Cai, Y.; Yang, W.; Yang, W.; Chen, D.; Hu, J. Secure Transmission of Cooperative Zero-Forcing Jamming for Two-User SWIPT Sensor Networks. Sensors 2018, 18, 331. https://doi.org/10.3390/s18020331
Tang X, Cai Y, Yang W, Yang W, Chen D, Hu J. Secure Transmission of Cooperative Zero-Forcing Jamming for Two-User SWIPT Sensor Networks. Sensors. 2018; 18(2):331. https://doi.org/10.3390/s18020331
Chicago/Turabian StyleTang, Xuanxuan, Yueming Cai, Wendong Yang, Weiwei Yang, Dechuan Chen, and Junquan Hu. 2018. "Secure Transmission of Cooperative Zero-Forcing Jamming for Two-User SWIPT Sensor Networks" Sensors 18, no. 2: 331. https://doi.org/10.3390/s18020331





