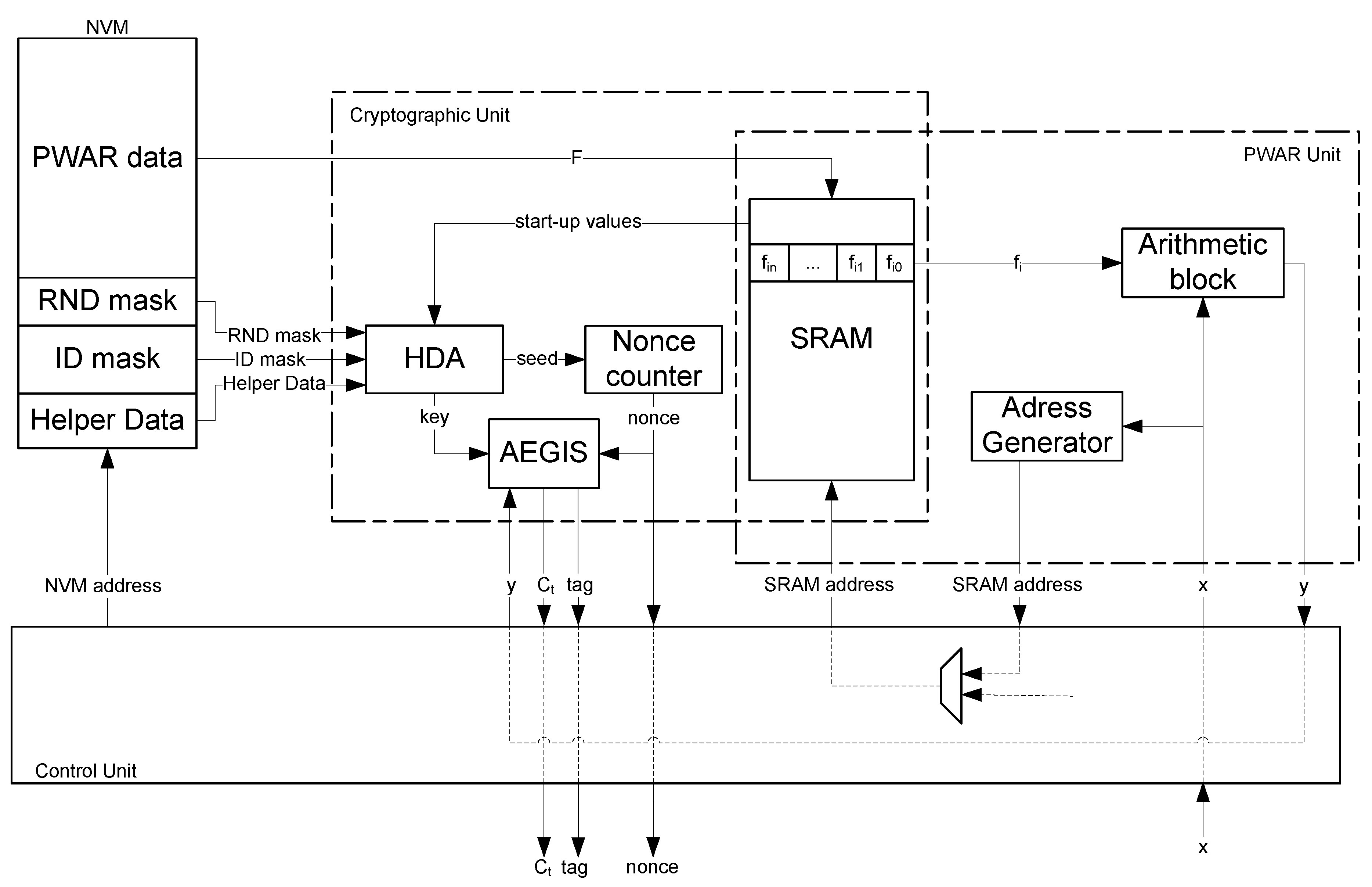
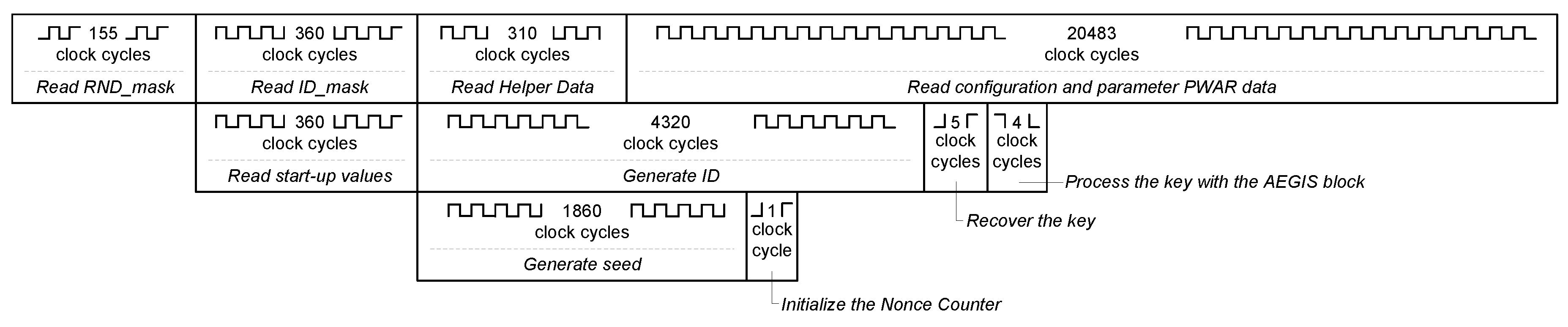
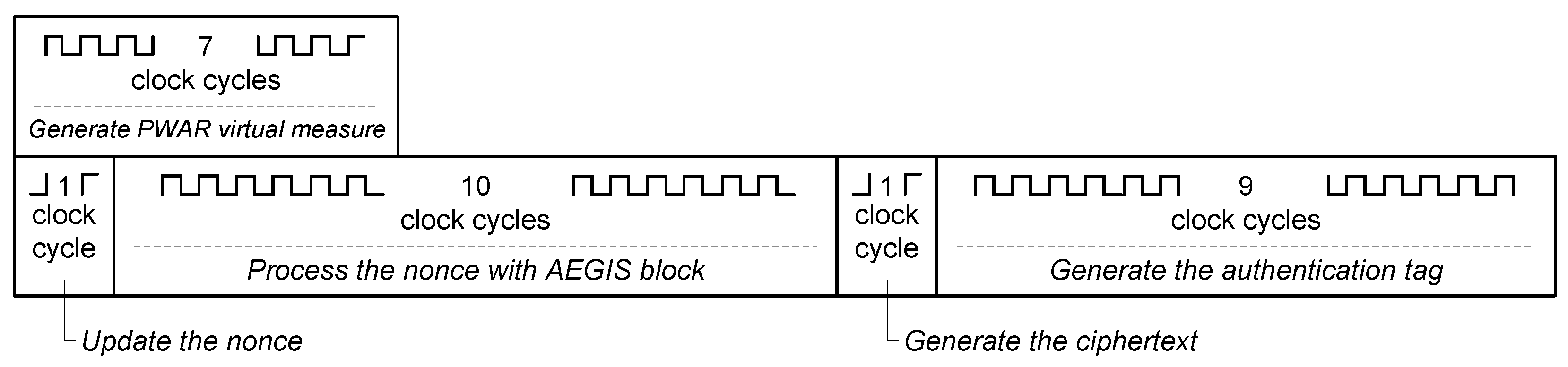
The proposed sensor provides the encrypted value of a variable that is virtually measured. In addition, it provides an authentication code that ensures the integrity, confidentiality, and authenticity of the sensor data.
The algorithm AEGIS is selected to encrypt and authenticate the virtual measurement providing confidentiality and authenticity to the virtual sensor. AEGIS offers a high security since it is not possible to recover the state and the key faster than exhaustive key search provided that a non-reused nonce is used and assuming that forgery attacks are not successful. The output provided by the proposed trusted virtual sensor are the used nonce, the resulting ciphertext, and the authentication tag.
Hence, two main components are differentiated in the proposed trusted virtual sensor. One part is associated with the generation of the virtual measurement and the other one provides the security of the measurement. They are both detailed in the following.
2.1. Virtual Sensing Based on PWAR approach
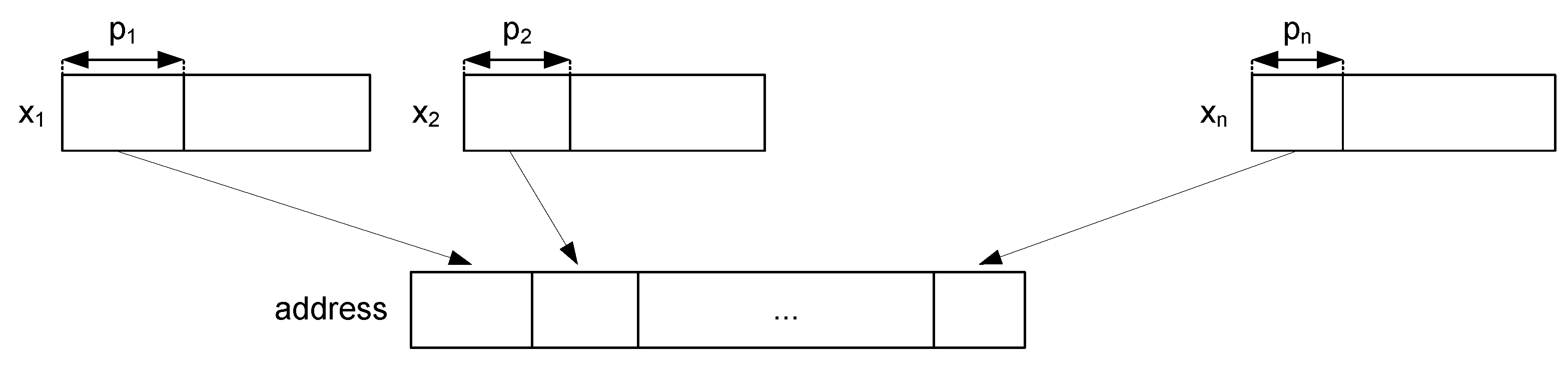
A black-box model establishes the relation between input variables and the empirical or simulated output. The virtual sensor is obtained using a black-box identification algorithm by assuming that the virtually measured output, y, is set as a PWAR function of the input variables, .
A generic PWA function with multiple inputs and one output
is represented as
where
, and
are
P non-overlapping regions (
), called polytopes, which form a polyhedral partition of the domain,
D, so that
.
In the case of regular PWAR functions, the domain is partitioned into hyper-rectangular polytopes by dividing each
k dimension of the domain into
intervals with the same amplitude, thus resulting
polytopes. Hence, a PWAR function is defined by its partition,
, and the coefficients and the offset of each affine function,
with
.
Figure 1 shows a bi-dimensional example of a regular PWAR function with its domain partitioned into
rectangles, that is
.
The partition and affine functions of a PWAR function can be adjusted conveniently to approximate the relation between input variables and sensing variable to estimate. An algorithm has been developed to find the parameters that minimize the mean square error (MSE) between the PWAR function output (variable to sense, y) and the empirical or simulated output data, . The algorithm takes into account the constraints imposed by digital implementations, which are the following.
Maximum number of input variables: n.
Maximum number of hyper-rectangles: .
Maximum number of intervals per input: , being the number of intervals per input, so that, .
The algorithm determines the hyper-rectangular partition of the input domain, , and the value of the affine functions, .
First, the partition is established, and then an off-line optimization algorithm extracts the F parameters using a set of simulated or empirical values of the output and its corresponding input data. All input data should belong to the domain D. At least, a given percentage, C, of the hyper-rectangles in a partition should be covered by the data in order to proceed with optimization. Otherwise, such high resolution is not required and the partition is not considered. The result of the approximation algorithm for a given partition, L, is not only the value of the F parameters but also the MSE between the simulated or empirical output data and the output of the PWAR function (the MSE taking into account training and testing data). Then, the MSE of all possible partitions are compared, and the partition with the lowest MSE (with the MSE that allows the best trade-off taking into account training and testing data) is selected.
The algorithm steps are detailed in the pseudo-code of Algorithm 1. Its inputs are a set, B, of output data, , with , corresponding to the input data ; the value of p that fixes the maximum number of hyper-rectangles; the value q that fixes the maximum number of intervals per input; and the minimum percentage, C, of hyper-rectangles that should be covered by input data. Data set B is divided into two subsets, one used as training file and the other as test (validation) file.
The partitions with high resolution, that is, which verify that
, are firstly explored with the function
TryPartition (line 1.17) because they have higher capability of providing a lower approximation error (and they can be implemented in the proposed IC sensor as well as partitions with lower resolution). The function
TryPartition(
A,
B,
C) evaluates if the partition,
A, meets or not the condition to be included in the partition list,
. The condition is that the data set,
B, should belong to no less than the
C in percentage of the hyper-rectangles of the partition,
A. Otherwise, such high resolution model has too many undefined affine functions. Finally, the partition list is explored (with the function
Optimization) to determine the partition that provides the lowest approximation error. The function
Optimization(i,B) (line 1.34) applies Levenberg-Marquardt algorithm to find the parameters
F that achieve the minimum MSE (and, hence, the Root Mean Square Error, RMSE) for each partition candidate,
i, considering the data set
B [
26]. Since the partition candidate (hyper-rectangle) is fixed, this optimization finds the best linear (affine) regression for the data. The
F parameters of hyper-rectangles not covered by data are fixed as the arithmetic mean of the
F in the neighbourhood. Once the algorithm finishes, if all the coefficients,
, associated with the input
, are zero, that input can be removed, thus resulting
with
.
The proposed sensor can be configured to provide several PWAR functions depending on the application. Therefore, it can be used to sense different variables. The configuration data are the number of input variables, and the number of intervals in which each dimension is divided that is, the hyper-rectangular partition is configurable. The sensor is also configurable in the affine functions of each hyper-rectangle by changing the value of the parameters associated with each hyper-rectangle. The input variables can be a same variable measured at several sampling times as well as the output measured at previous instants, for example, .
| Algorithm 1 Pseudo-code of PWAR virtual sensor algorithm. |
| Require: |
| |
| |
| while do |
| |
| 5: if then |
| |
| end if |
| while do |
| … |
| 10: while do |
| |
| if then |
| |
| end if |
| 15: while do |
| |
| part=TryPartition(A, B, C); |
| if part==SUCCESS then |
| ; |
| 20: end if |
| |
| end while |
| |
| |
| 25: end while |
| … |
| |
| |
| end while |
| 30: |
| |
| end while |
| for do |
| [RMSE, F]=Optimization(i, B); |
| 35: if then |
| |
| |
| end if |
| end for |
| 40: return L, F |
2.2. Trusted Sensing Based on AEGIS and PUF
The virtual measurement,
y, is encrypted and authenticated by using the AEGIS algorithm, which is a dedicated authentication encryption algorithm. AEGIS is based on the AES encryption round function, providing the advantage of a computational cost about half that of AES [
23]. If the nonce is not reused (which should be the case for a true nonce), AEGIS provides a high security since state and key can only be recovered by exhaustive search.
AEGIS algorithm takes the cryptographic key,
, a number used only once,
, and a plaintex, in this case the virtual measurement,
y, and provides a ciphertext,
, and an authentication tag,
.
An interesting feature of the proposed sensor is that the secret key, is not stored in the IC but it is recovered whenever needed. From a security point of view, a secret that is not stored is much more difficult to discover. Among the wide number of PUFs proposed in the literature, SRAM-based PUFs [
27] are selected in this work since the proposed IC sensor requires SRAMs for its virtual sensing functionality.
Since an SRAM cell is composed of two cross-coupled inverters, as shown in
Figure 2, the start-up value is imposed by the inverter which begins to conduct. The conditions that make one inverter be the winner can be intrinsic or external. Intrinsic conditions are related to mismatching between the inverters, while external conditions are aging, ambient temperature, power supply voltage value (
) or ramp-up time (i.e., the time to reach
after power-on) [
27,
28,
29]. As discussed in [
27], there are SRAM cells whose intrinsic conditions dominate over the external conditions. Hence, although the external conditions change, their start-up values are mostly the same. This type of cells will be named herein as ID cells. There are also SRAM cells whose external conditions dominate over the intrinsic conditions so that they are able to extract the noise of the external conditions as a source of entropy. They will be named herein as RND cells.
SRAM ID cells are used in the proposed IC sensor to recover the cryptographic key. The reliability of these stable cells is measured by the maximum fractional Hamming distance,
, between pairs of responses,
R, generated by the same
n cells at
m different times:
Ideally, is zero but some bit flipping of the start-up values is unavoidable.
The SRAM cells are classified by using Algorithm 2 to obtain an ID_mask and a RND_mask. The SRAM is powered-up and down several times under different operating conditions.
HDA is used to obfuscate and to recover the key [
25]. It is based on an error correcting repetition code whose correction capability should to be able to correct the maximum bit flipping probability of
in (
3). Algorithm 3 describes how Helper Data,
H, are generated from a secret key and the start-up values of the SRAM.
| Algorithm 2 Pseudo-code of Masks Extraction algorithm. |
| Require: Number, J, of conditions to evaluate. Number of measurements, K, per condition |
| for i=1 to J do |
| for j=1 to K do |
| power down and up the SRAM |
| if j=1 then |
| save the start-up values |
| else |
| compare the start-up values with the stored ones |
| end if |
| for all the cells of SRAM do |
| if cell value does not change then |
| add cell to |
| else |
| add cell to |
| end if |
| end for |
| end for |
| end for |
| for all the cells of SRAM do |
| if cell belongs to all then |
| add cell to ID_mask |
| else if cell belongs to all then |
| add cell to RND_mask |
| end if |
| end for |
| return ID_mask, RND_mask |
| Algorithm 3 Pseudo-code of Helper Data Generation algorithm. |
| Require: , start-up values of SRAM |
| Each bit of the key is repeated r times ⟹. |
| concatenation of the SRAM ID cells start-up values at Helper Data generation step. |
| . |
| return H |
The secret key is recovered as described in Algorithm 4. A response, , slightly different to R, since even ID cells may provide some bit flipping, is obtained by concatenating the new start-up values of the SRAM ID cells used to generate the Helper Data. The key is recovered by using an ECC with codeword length r, employed to correct up to errors.
| Algorithm 4 Pseudo-code of Key Recovering algorithm. |
| Require: H, start-up values of SRAM |
| = concatenation of the SRAM ID cells start-up values at key recovering step. |
| |
| . |
| return |
Helper Data do not reveal anything about the cryptographic key because the start-up values of SRAM ID cells obfuscate it. Similarly, Helper Data do not reveal anything about the intrinsic nature of the IC sensor because the cryptographic key obfuscates it. A way to measure the non-sensitiveness of Helper Data is to evaluate the average fractional Hamming distance,
, between all the possible pairs of Helper Data of
p different sensors that use the same key, as follows:
This way, instead of storing the key, only Helper Data are stored and the integrity of the sensor is ensured. If the sensor is copied, its SRAM ID cells will have other intrinsic features and they will not be able to recover the key.
The start-up values of the SRAM cells are also exploited to generate the nonce required by AEGIS. The nonce is initialized by the start-up values of SRAM RND cells and then updated by a counter. A way to measure the change of the nonce seed is to evaluate the minimum fractional Hamming distance,
, between pairs of responses,
R, generated by the same
n RND cells at
m different times:
A value of strictly greater than zero ensures that the nonce seed is time variant, as required.
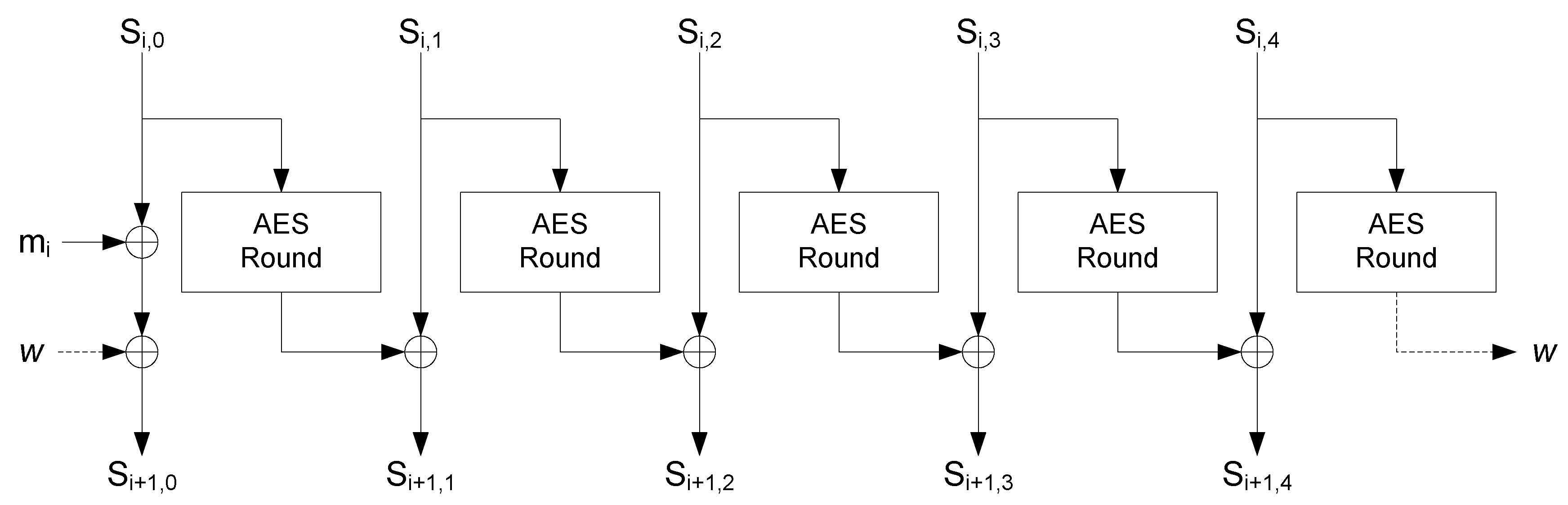
AEGIS is based on the AES round function [
23]. There are three variations. AEGIS-128 processes a 16-byte message block with five AES round functions in parallel. It consumes the least resources, but it is the slowest for large messages. AEGIS-128L processes a 32-byte message block with eight AES round functions in parallel. In terms of resource consumption, it is the biggest version, but it is also the fastest. Finally, AEGIS-256 processes a 32-byte message block with six AES round functions. Then, it offers an intermediate performance in terms of resource consumption and time response. Since the virtual measurement is smaller or equal to 128-bits, only one 16-byte state has to be processed. Hence, AEGIS-128 is more adequate in this application, since it is as fast as AEGIS-128L, using less resources.
AEGIS-128 uses a 128-bit key and a 128-bit nonce. The algorithm is based on the function described in Algorithm 5 where the function is the AES encryption round function being A the state. The main operations in the AES round are SubBytes operation, ShiftRows and AES-MixColumns.
| Algorithm 5 State Update function. |
| 1: function StateUpdate() |
| 2: AESRound |
| 3: AESRound |
| 4: AESRound |
| 5: AESRound |
| 6: AESRound |
| 7: return |
| 8: end function |
The pseudo-code of the AEGIS-128 applied to the virtual measurement is described in Algorithm 6. The main steps of the algorithm are to initialize the state (line 6.1), process the nonce (line 6.6), process the measurement and generate the ciphertext (line 6.14), and generate the authentication tag (line 6.20). constant1 and constant2 are two 128-bit constants fixed by the algorithm.
| Algorithm 6 Pseudo-code of AEGIS algorithm. |
| Require: key, nonce, y |
| 1: key ⊕ nonce |
| 2: constant1 |
| 3: constant2 |
| 4: key ⊕ constant1 |
| 5: key ⊕ constant2 |
| 6: for do |
| 7: if i is odd then |
| 8: key ⊕ nonce |
| 9: else |
| 10: key |
| 11: end if |
| 12: |
| 13: end for |
| 14: |
| 15: |
| 16: |
| 17: for do |
| 18: |
| 19: end for |
| 20: |
| 21: return , tag |