1. Introduction
Deregulation of the electric industry throughout the world, grid interconnections and ever continuous increasing demand for electricity have resulted in heavy stress on power systems. System operators are facing many challenges related to power system security. Various factors such as expansion of the generation and transmission systems cannot be match the growth in load. Meanwhile, the creation of electricity markets has led to the trading of significant amounts of electrical energy over long transmission distances, and also the number of unplanned power exchanges has increased due to the competition among utilities and contracts concluded directly between producers and consumers, which have weakened the level of security of power systems. As the power system becomes more complex and more heavily loaded and unexpected outages occur, the systems can be operated in unstable or insecure situations like transmission congestion and voltage violations. Therefore, the power system security has become an important and critical issue and obtained much attention in the deregulated power industry [
1,
2,
3,
4]. In order to eliminate or alleviate congestion and voltage violations and to improve system security, rather than constructing new lines, the existing power lines need to be utilized more efficiently. The reason is that building new transmission lines is rather time consuming and sometimes impossible, due to political and environmental problems in many countries. Hence, the first alternative provides an economically and technically attractive solution to power system security problem by use of some efficient controls [
5], such as generation rescheduling, load shedding and controllable FACTS, etc. Although generation rescheduling [
6] and load shedding [
7] to eliminate/alleviate emergency transmission line overloads and bus voltage violations is an important problem in power system operation, these two ways may not be acceptable by both power providers and customers due to their significant effect on the existing power transaction contracts, so the use of controllable FACTS to enhance power system static security by eliminating/alleviating congestion and voltage violations is one of the main interests among current issues.
FACTS devices, which were first defined by Hingorani in 1988 [
8], have a significant potential ability to make power systems operate in a more flexible, secure and economical way. They can benefit the emerging power system in terms of improving the system stability, reducing the flow in heavily loaded lines, maintaining bus voltages at their desired level and thus enhance power system security under contingency conditions. However, the benefits of these devices are mainly dependent on their location in the system [
9]. The proper location of FACTS devices is a key to maximize power system security. Therefore, the system operators are facing the problem of where and which types of FACTS devices should be installed for achieving the required goals. This is a difficult problem due to the large size of the search space for a practical system.
In practice, due to transfer capacity of the transmission lines, some lines located on particular paths may become overloaded if the unplanned power exchanges were not controlled. This is the main bottleneck of the power system. The existence of bottlenecks in power networks directly affects market transactions and impedes system security [
10]. The security of the power system can be enhanced if appropriate types of FACTS devices are chosen and suitably installed on transmission lines and buses to redistribute real power flows and regulate bus voltages by modifying line reactance and injecting reactive power.
From the view point of optimization, the optimal installation of FACTS devices is a highly multimodal, constrained and complex optimization problem [
11]. Generally, the approaches for optimal allocation of FACTS devices can be classified into three categories: classical optimization approaches, sensitivity-based approaches and heuristic optimization approaches.
In classical optimization approaches, a Newton Raphson (NR) algorithm has been developed to find out the best operating point of a SVC for the enhancement of system security by minimizing the security index iteratively [
12]. A mixed integer nonlinear programming (MINLP) based on line flow- based equations (LFB) is utilized to find the optimal location and setting of the TCSC under single line contingency conditions [
13]. In [
14], by applying a mixed integer optimization technique, the demand response (DR) and the TCSC and SVC controllers are optimally coordinated with the conventional generators to manage the network congestion in a restructured market environment. In [
15], mixed integer linear programming (MILP) is used to the optimal allocation of thyristor controlled phase shifter transformers (TCPSTs) for maximizing power system loadability. Mixed integer linear and nonlinear programming-based optimal power flow (OPF) methods have been utilized for finding the optimal installation of FACTS to enhance system loadability [
16,
17]. Although classical optimization approaches have excellent convergence characteristics, they are not flexible and especially, handling constraints in them is hard work.
In sensitivity-based approaches, for enhancing the security of the system, a sensitivity-based approach has been proposed to decide the optimal location of TCSCs and unified power flow controllers (UPFCs) [
18]. In [
19], a real power flow performance index (PI) sensitivity-based approach and the concept of a line outage distribution factor have been proposed to decide the optimal location of TCSCs and static synchronous series compensators (SSSCs) to enhance the security of the power systems. Line loading security Performance Index (PI) sensitivity factors have been suggested for optimal placement of UPFCs for enhancing the security of the power system [
20]. The approach based on the sensitivity of the reduction of total system VAR power loss and real power performance index has been suggested for determining the optimal TCSC location for congestion management [
21]. In order to evaluate the suitability of a given line for installing a TCSC, two new indices called Thermal Capacity Index (TCI) and Contingency Capacity Index (CCI) [
22] have been used to obtain secured optimal power flow under normal and network contingencies. In [
23], an approach based on an index called the single contingency sensitivity index is proposed to find the optimal installations of TCSCs to enhance static security by eliminating line overloads under a single contingency. In [
24], a transmission network is analyzed based on line parameters variation to improve Total Transmission Capacity (TTC) of the interconnected system. Real power flow PI sensitivity factors are introduced to select lines for placing FACTS devices. Although sensitivity-based approaches have advantages in computing efficiency, their computation accuracy is partly lost because of the nonlinearity of the power flow model is neglected. Moreover, they cannot simultaneously optimize the location and initial settings of FACTS devices.
The heuristic optimization approaches have been widely used in FACTS allocation problems. In [
25], three heuristic methods, for instance, the genetic algorithm (GA), the tabu search method (TS) and the simulated annealing (SA) are applied to optimal installation of FACTS to enhance the system security. A GA is applied for seeking the optimal placement of multi-type FACTS to maximize the loadability in a power system [
26]. In [
27,
28], the GA has been used to find the optimal location of FACTS for improving the security of a power system. A multi-objective GA is employed for optimal allocation of multi-type FACTS devices to maximize power systems security [
29]. In [
30], the effects of different types of FACTS devices on the performance of Hydro-Québec network have been analyzed. The optimal locations and rating of these FACTS controllers will be determined with a view to improving network security using an optimization algorithm based on a genetic algorithm. In [
31], PSO technique is used for optimal installations of TCSCs, SVCs and UPFCs to minimize the cost of FACTS installation and improving the system loadability. In [
32], PSO is employed for solving the security enhancement problem by optimal location of TCSCs. In [
33], two evolutionary optimization techniques namely, GA and PSO, are applied for seeking the best location with the optimal setting of TCSC under single line contingency to improve the system security by eliminating or minimizing line overloads and bus voltage violations. In [
34], a differential evolution (DE) algorithm is applied for finding the best location with parameter setting of UPFCs for enhancing power system security under single line contingencies. In [
35], a relatively new evolutionary optimization technique, namely the DE technique, is applied to find the optimal locations and parameter settings of TCSCs under determined contingency scenarios for enhancing power system security. An adaptive DE algorithm is proposed for allocating the TCSC incorporated with the reactive power management problem [
36]. In [
37], the self-adaptive firefly algorithm (SAFA) is presented to optimize the placement of TCSCs, SVCs and UPFCs for improving the power system performance through minimizing real power loss, improving voltage profiles and enhancing the voltage stability. In [
38], the imperialistic competitive algorithm (ICA) is employed for solving TCPST and TCSC allocation problem in a way that low values of overloads and voltage deviations result both during line outage contingencies and demand growth. In [
39], Biogeography-Based Optimization (BBO), Weight Improved PSO (WIPSO) and PSO are applied to solve the optimization problem of finding the optimal placements and capacities of TCSCs, SVCs and UPFCs for enhancing system security under increased system loading conditions. In [
40], a PSO-based adaptive gravitational search algorithm hybrid algorithm is proposed for finding out the best locations with the settings of UPFCs and interline power flow controllers (IPFCs) for improving the voltage stability of the power transmission systems. Although the heuristic optimization approaches are very flexible and easy to deal with discrete and constraint optimization problems, they have high computational burden due to the huge search space of the solution to FACTS allocation problems.
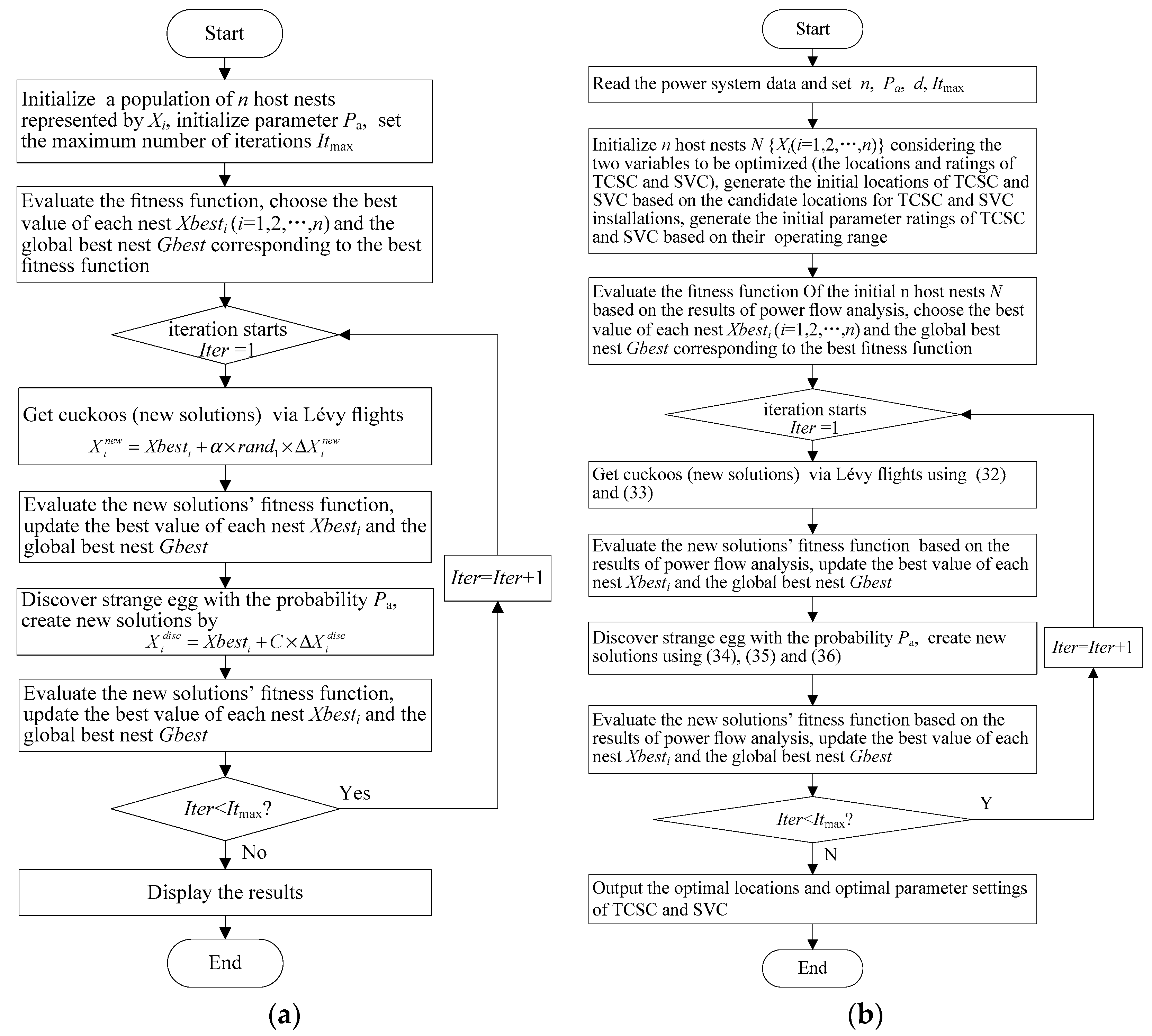
Recently, a novel meta-heuristic called cuckoo search algorithm (CSA) inspired by some cuckoo species’ obligate brood parasitic behavior, was developed by Yang and Deb [
41]. A cuckoo bird lays and dumps its egg in a randomly selected nest of other species and the egg is either hatched and carried over to the next generations or abandoned by the host bird [
42]. CSA has a few parameters needed to be tuned, and the inexperienced user can easily interact with it. It has two crucial search capabilities, which are local search and global search controlled by a fraction probability or discovery rate,
Pa internal parameter and therefore converges to the global optimum for a multimodal optimization [
43]. It uses Lévy flights motion with infinite mean and variance rather than standard random walks motion for global search. Such behavior has been emulated to perform optimization and global optimal search with promising results [
44,
45]. It is an efficient meta-heuristic algorithm that balances between the local search strategy (exploitation) and the whole space (exploration) [
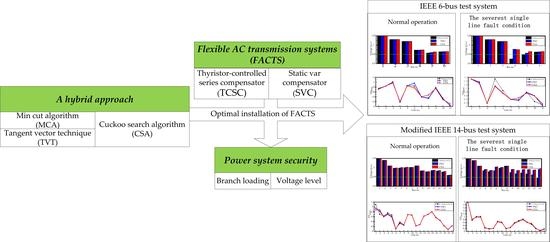
46]. To the best knowledge of the authors, the application of CSA to optimal installation of FACTS devices for enhancing power system static security by removing or alleviating the overloads and voltage violations under normal operation and even the most critical single line contingency condition is quite rare. This paper focuses on the problem of how to maximize power system static security in terms of branch loading and voltage level under normal operation and even the most critical single line contingency conditions. Additionally, two classical types of FACTS devices, namely TCSCs and SVCs are chosen for the study. This paper proposes a hybrid approach to find out the optimal locations and settings of TCSCs and SVCs for solving this problem. Our proposed approach requires a two-step strategy. Firstly, the MCA and TVT are applied to determine the proper candidate locations of TCSCs and SVCs, respectively, and then the CSA is employed for solving this problem by simultaneously optimizing the locations and settings for installations of TCSCs and SVCs. Our proposed hybrid approach has been demonstrated on the IEEE 6-bus and modified IEEE 14-bus test systems. The major contributions of this study are as follows:
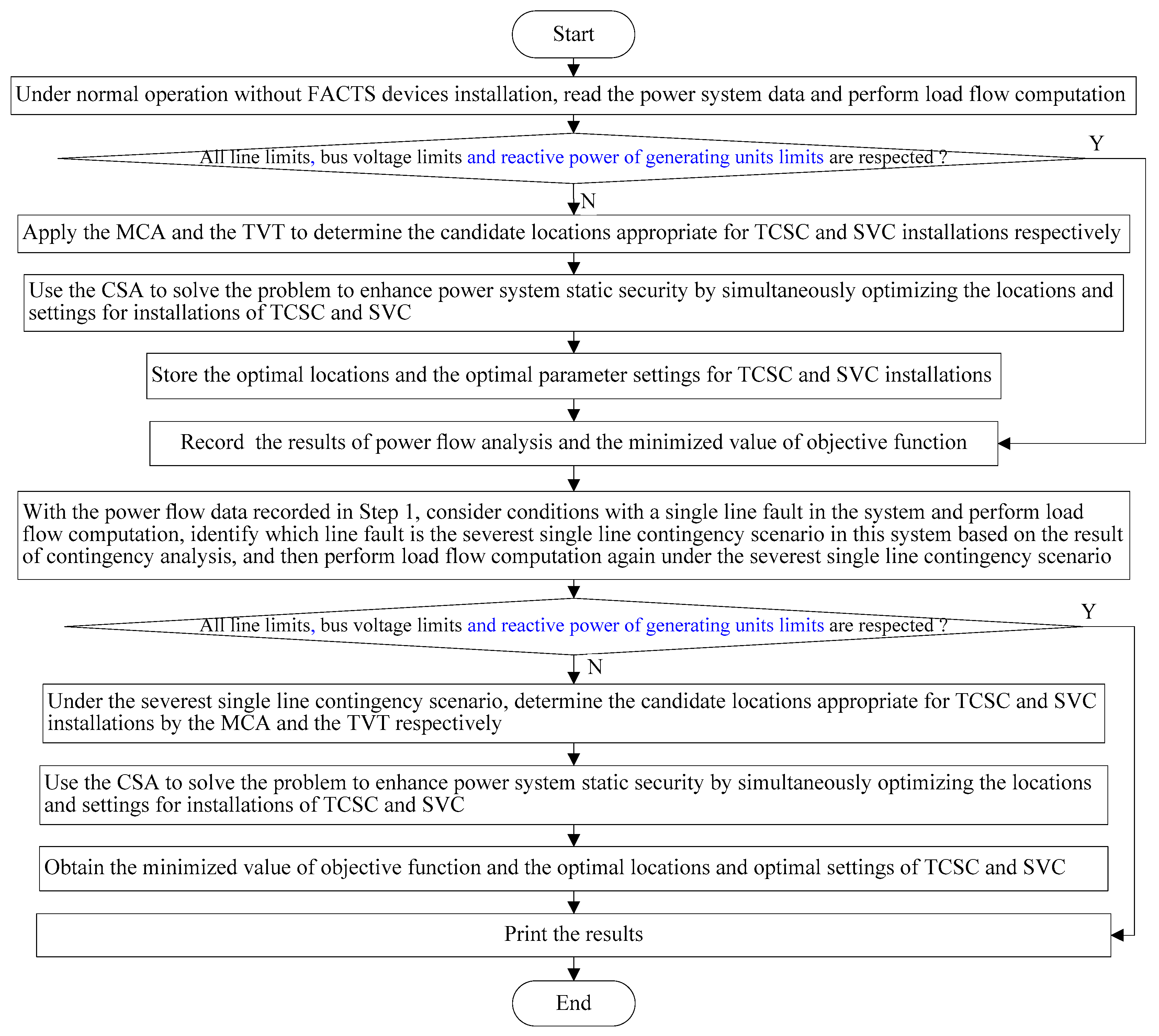
A hybrid approach to solve the problem of maximizing power system static security in terms of branch loading and voltage level via optimal installations of TCSCs and SVCs under normal operation and even the most critical single line contingency condition is proposed.
In order to reduce the search space for the solution to the problem, the MCA and the TVT are applied to determine the proper candidate locations of TCSCs and SVCs, respectively. The number of lines and buses which need to be investigated to determine the best locations of TCSC and SVC is significantly decreased, hence, the computational burden of CSA to solve the problem is lessened.
A novel CSA-based procedure to solve the problem to enhance power system static security by simultaneously optimizing the locations and settings for installations of TCSCs and SVCs is proposed.
The proposed hybrid approach is capable of finding out the best locations and settings of TCSCs and SVCs in an effective way for enhancing power system static security by removing or alleviating the overloads and voltage violations under normal operation and even the most critical single line contingency conditions.
This paper is arranged as follows:
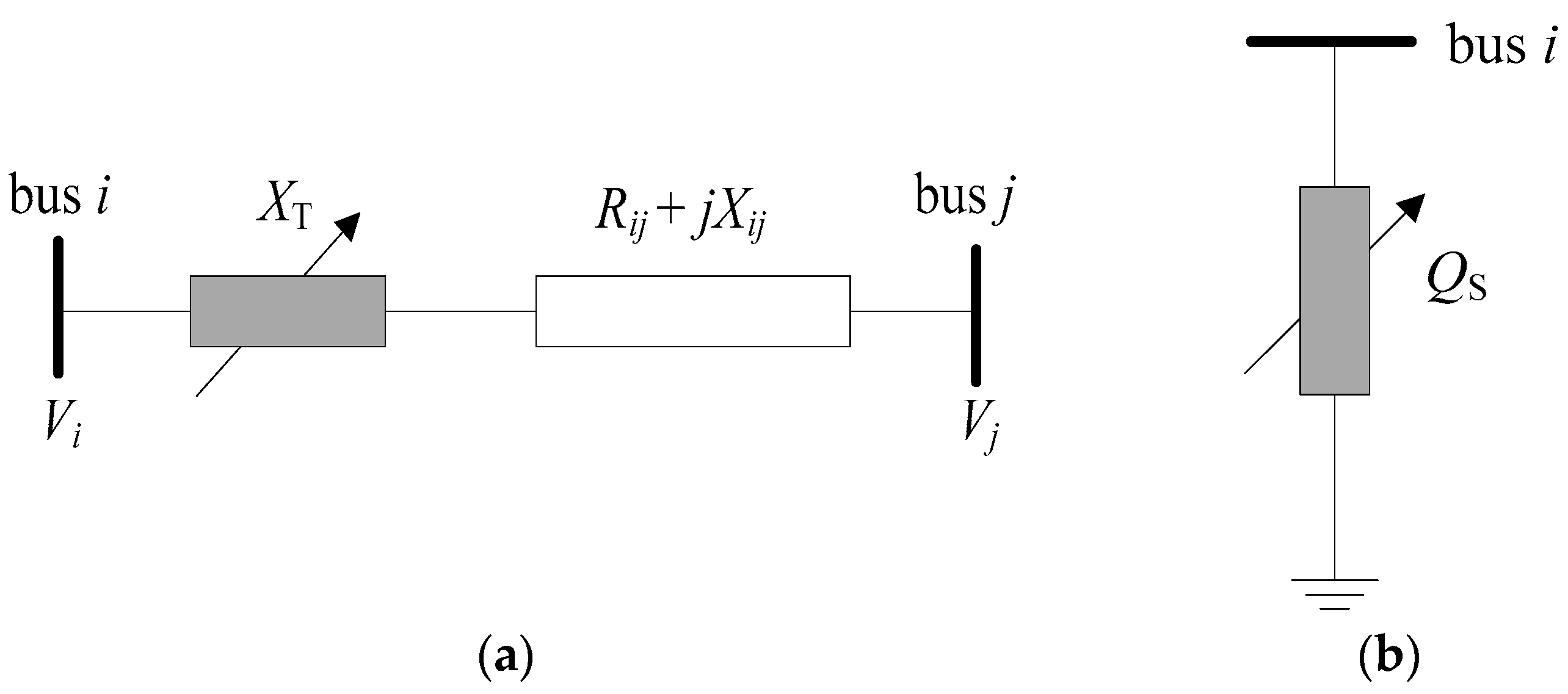
Section 2 introduces the models of TCSCs and SVCs. Our proposed mathematical problem formulation for enhancing the power system static security via optimal installations of TCSCs and SVCs is also presented.
Section 3 explains the MCA and the TVT for determining the proper candidate locations for TCSC and SVC installation, respectively.
Section 4 describes the CSA and its application for optimal locations and settings of TCSCs and SVCs.
Section 5 gives the overall procedure of implementation of the proposed hybrid approach.
Section 6 demonstrates the simulation results and discussion. Finally,
Section 7 summarizes the conclusions and the data of transmission line for modified IEEE 14-bus test system is detailed in
Table A1.
7. Conclusions
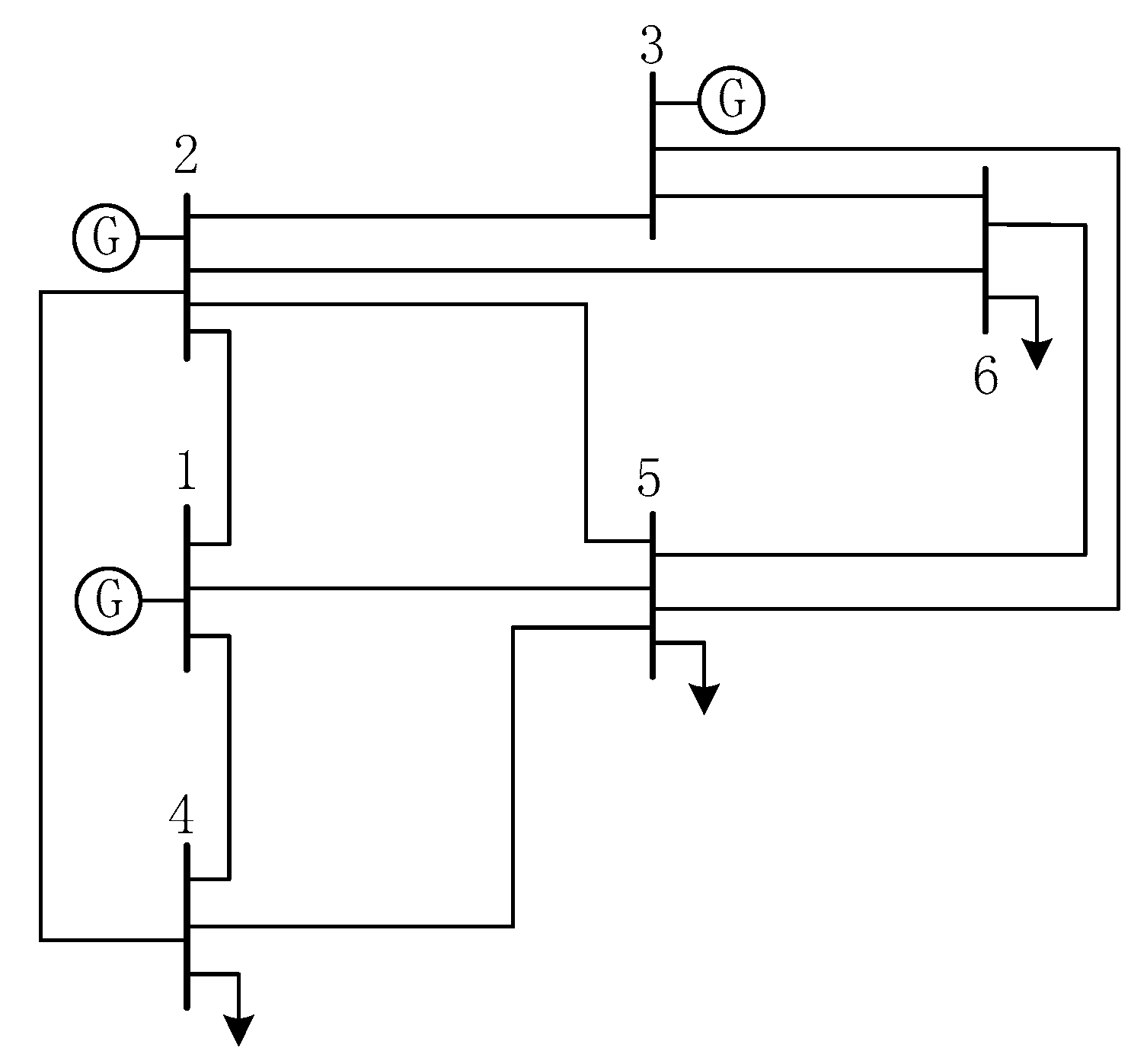
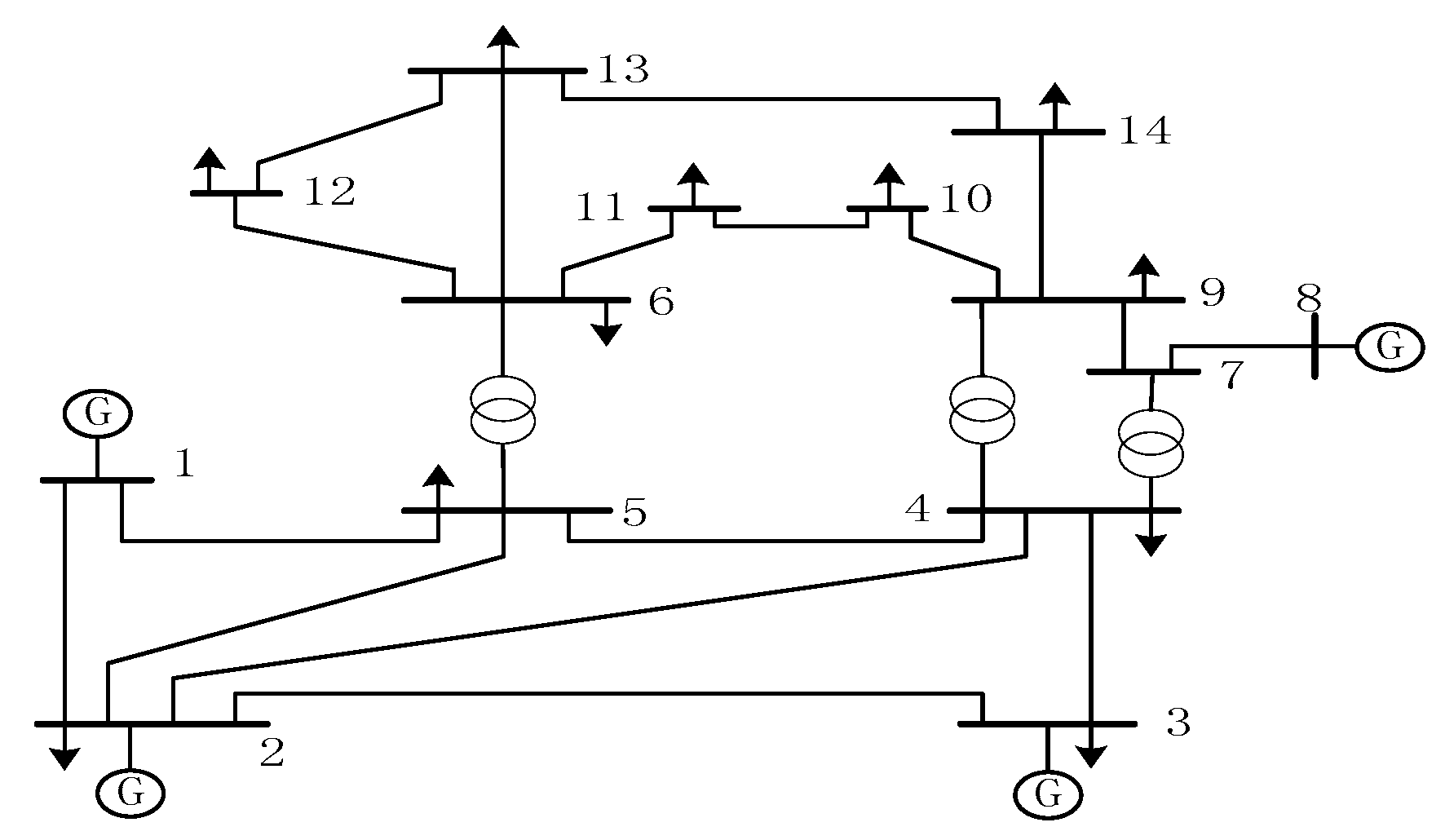
Sustained development of the economy will result in continuous growing demand for electricity regionally or integrally. Additionally, due to open access to the transmission networks, several factors such as an increasing various power transactions, unplanned power exchanges and unexpected outages will cause hugely changing power flows through lines and voltage violations on buses in the deregulated power systems. In this case, serious threats to the power system security might occur. Therefore, it is a good choice to optimally locate FACTS devices on the existing networks other than build new transmission lines for enhancing power network security. This paper proposes a hybrid approach to solve the problem of maximizing power system static security in terms of branch loading and voltage level via optimal installations of TCSCs and SVCs under normal operation and even the most critical single line contingency condition has been proposed. Our proposed approach requires a two-step strategy. In the first step, the MCA and the TVT are applied to determine the proper candidate locations of TCSCs and SVCs, respectively. In the second step, the CSA is employed to solve this problem by simultaneously optimizing the locations and settings for installations of TCSC and SVC. The proposed hybrid approach was verified on the IEEE 6-bus and modified IEEE 14-bus test systems.
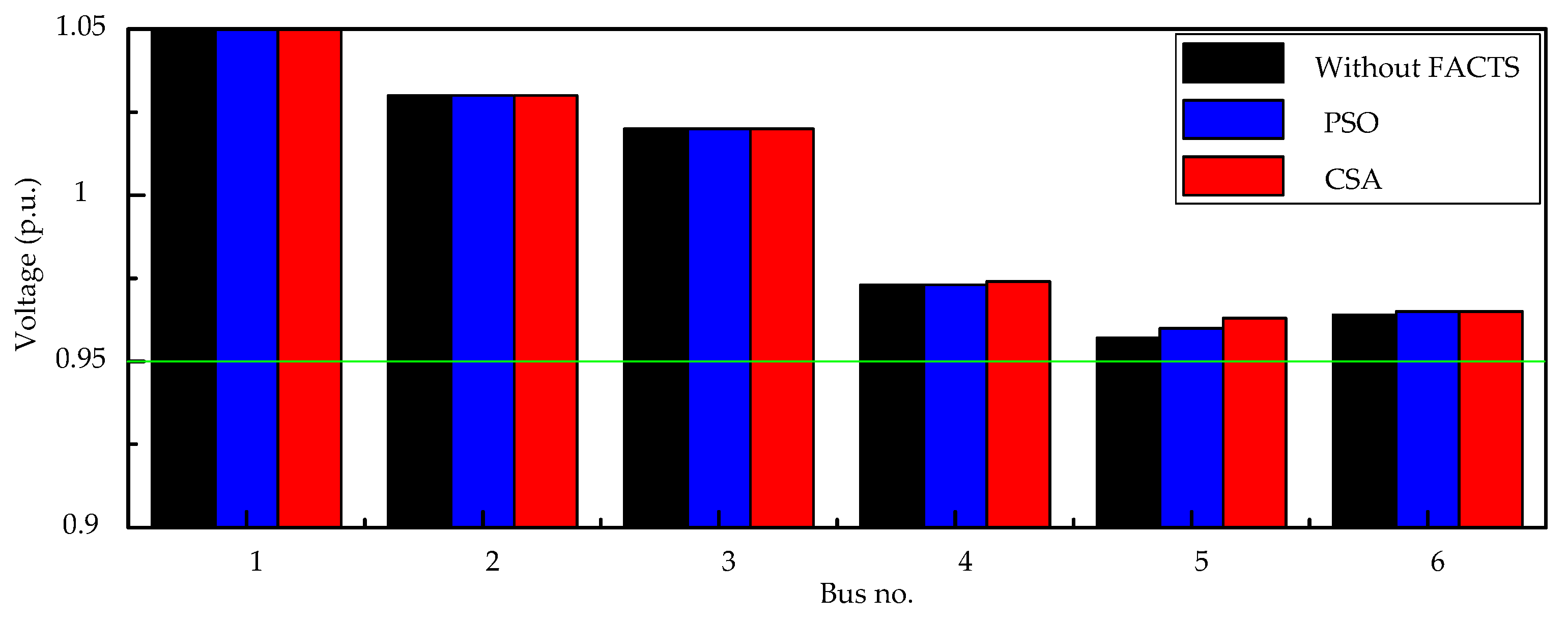
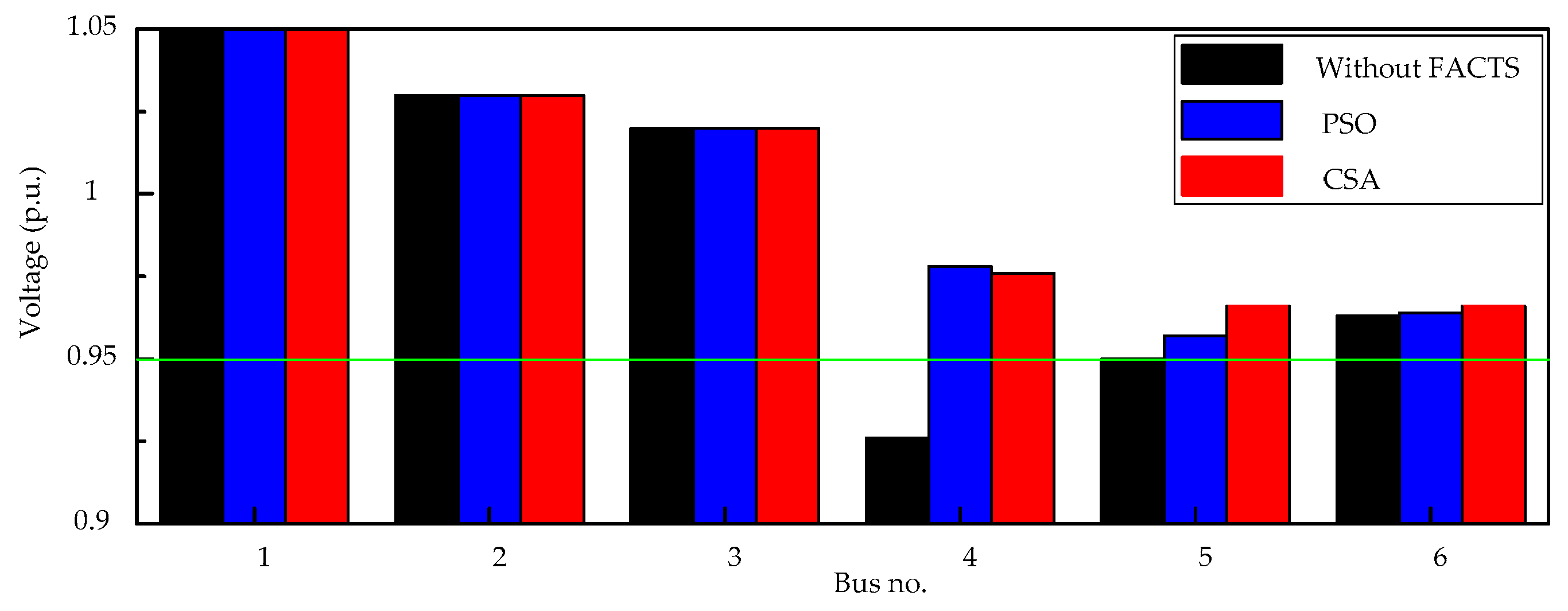
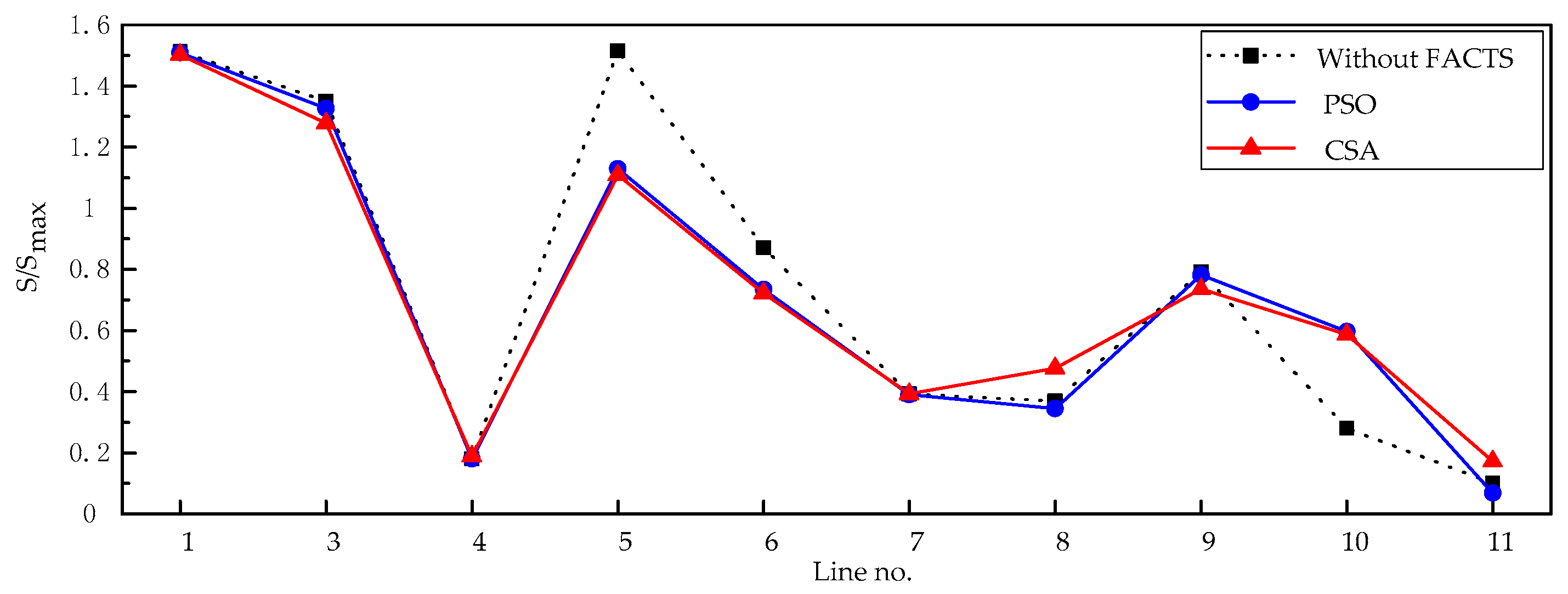
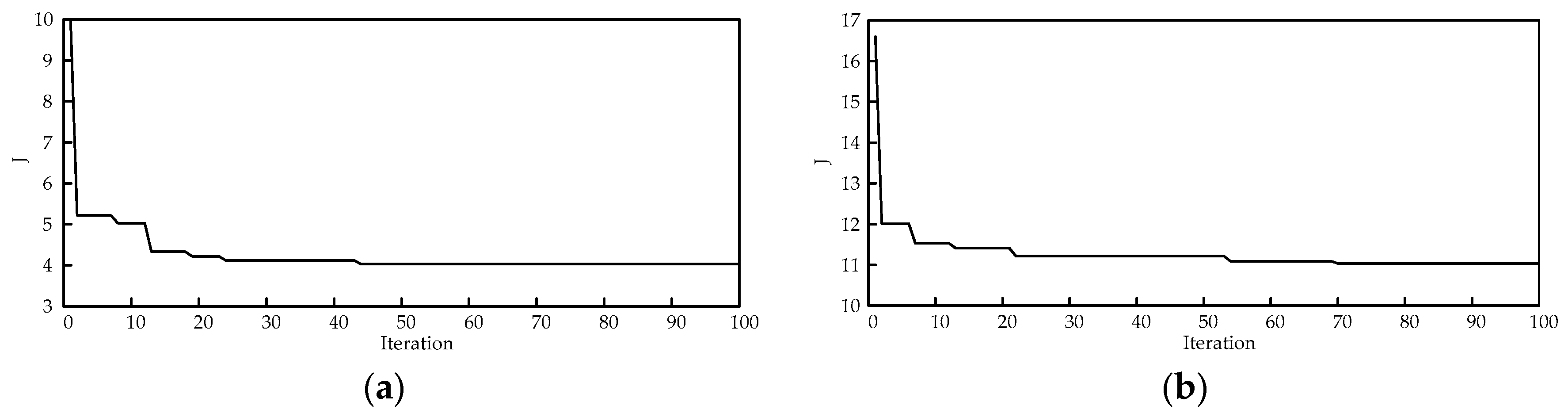
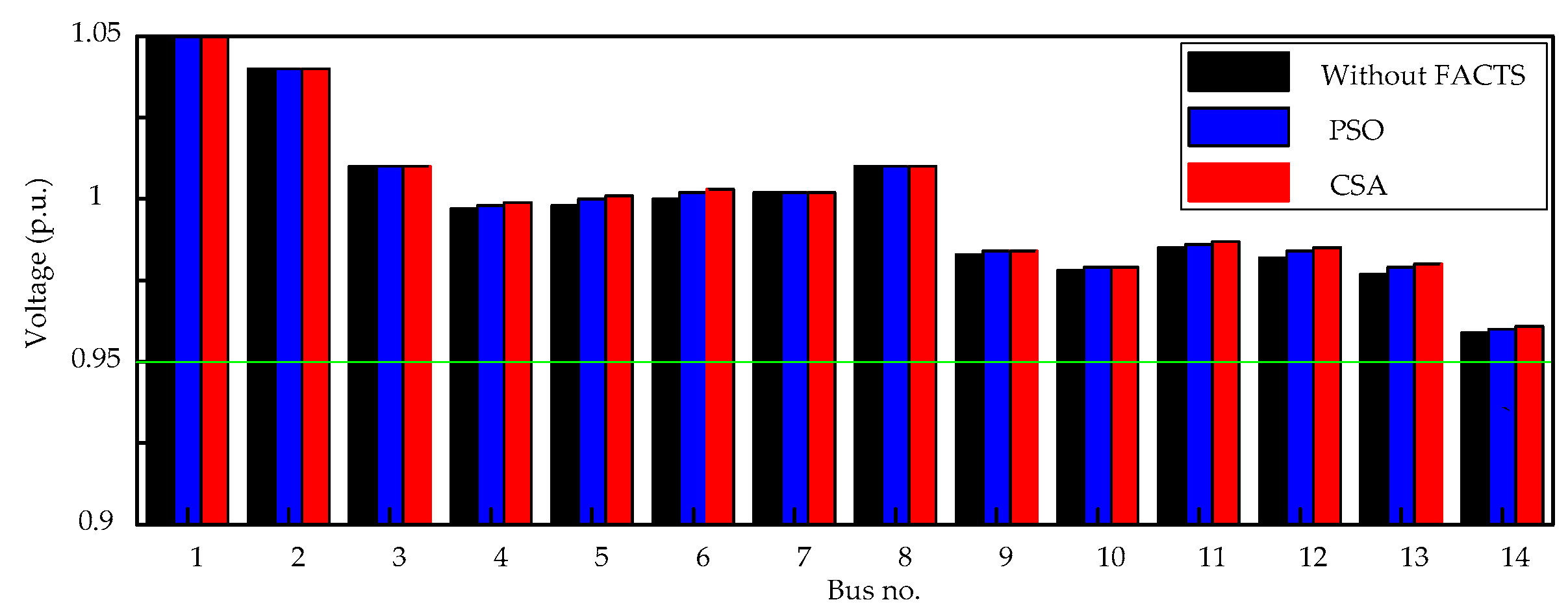
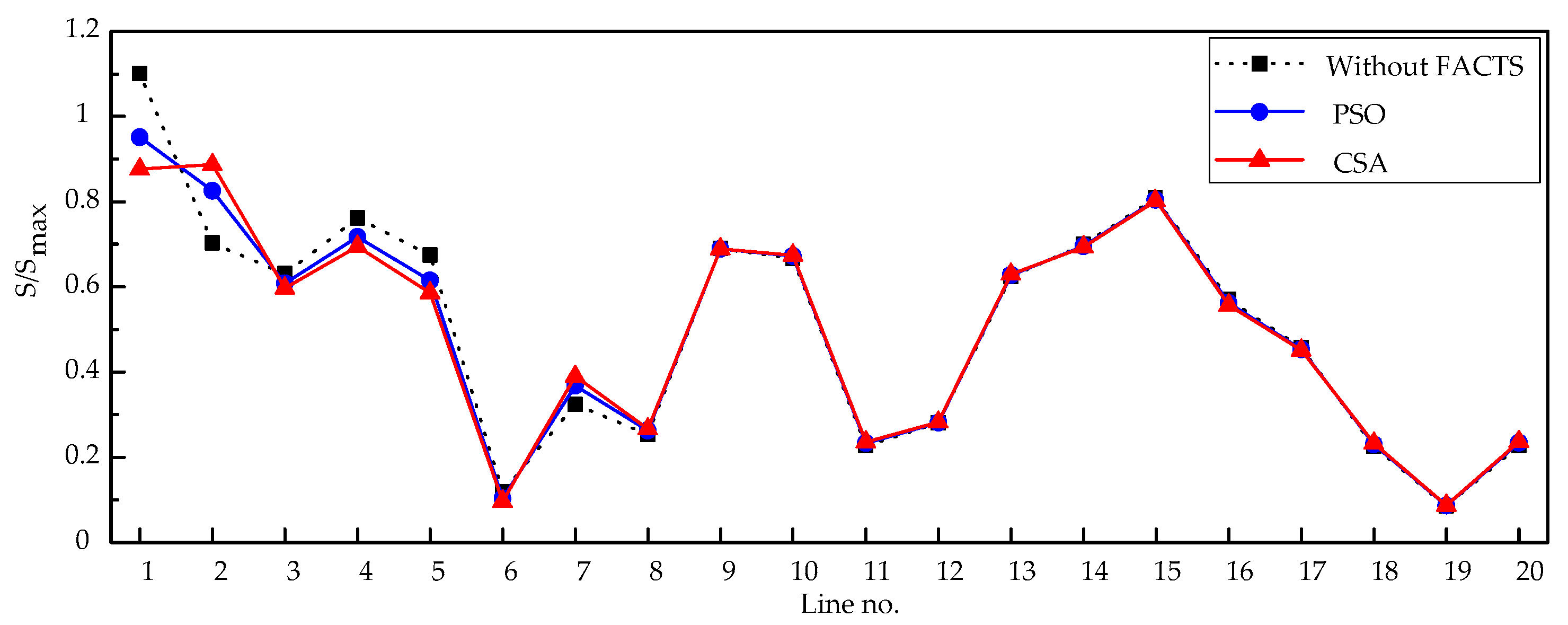
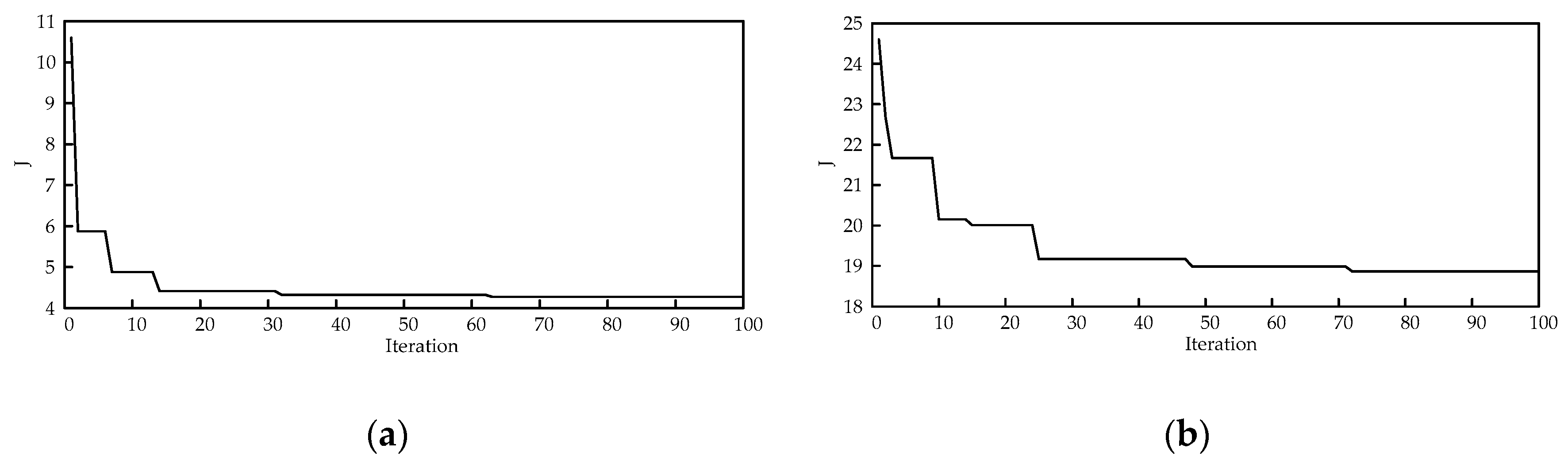
The results show that the MCA and the TVT are effective methods for determining the suitable candidate locations of TCSC and SVC, respectively, so as to reduce the search space for solution to the problem. The number of lines and buses which need to be investigated to determine the best locations of TCSCs and SVCs will be significantly decreased. Moreover, the results indicate that CSA outperforms PSO, proving its effectiveness and potential. Therefore, it can be concluded that the proposed hybrid approach is capable of finding out the best locations and settings of TCSCs and SVCs in such an effective way for enhancing power system static security by removing or alleviating the overloads and voltage violations under normal operation and even the most critical single line contingency conditions. Using this hybrid approach, the search space for solutions to the problem becomes limited, hence the computational burden has been lessened.
As future work, the methodology can be improved further if the performance of CSA is improved through its hybridization with other meta-heuristic algorithms. With the rapid increasing penetration of renewable energy sources [
59] in the electricity market, particularly wind energy, the installation costs of FACTS devices and the effect of wind power generation need to be investigated in further research.