1. Introduction
Nowadays, digital multimedia like digital images plays an indispensable role in our daily lives. However, with the development of image processing techniques, it has become easier to refine and edit the images. The authenticity and integrity of digital images are suffering from a serious threat. To cope with this problem, the fragile watermarking scheme has recently been proposed. Generally, the fragile watermark used for image authentication can be divided into two types including semi-fragile watermark and complete fragile watermark (also known as fragile watermark). Compared to the semi-fragile watermarking method, the fragile watermarking is more susceptive to various alterations [
1]. Therefore, it is more effective for image authentication, especially for the images used in safety-critical applications. According to detection resolution, the fragile watermarking scheme is further split into two categories [
2]: the block-wise method and the pixel-wise method. In a block-based watermarking algorithm, the image is firstly partitioned into many sub-blocks. Each image block is inserted with the identification code produced from the block itself. In [
3], Walton presented a classical block-wise fragile watermarking algorithm. The least significant bit (LSB) of image sub-block is inserted by the check-sum of the most significant bits (MSBs). However, a false certification arises whereby one can exchange the image block without affecting its authentication information. To resolve this problem, Chang et al. [
4] suggested a hash function-based watermarking algorithm. In their scheme, the authentication data of each block is generated via a cryptographic hash function. The binary form of watermarking information is integrated and inserted into the LSB of the center pixel in the corresponding block. They claimed that this method can recognize and locate any manipulation to the watermarked images. However, later research in [
5] pointed out that this method is not secure enough for image authentication. In [
6], Chen and Wang introduced a fragile watermarking algorithm, where the authentication data was obtained by applying fuzzy c-means (FCM) clustering. To achieve image authentication in JPEG images, Zhang et al. [
7] introduced a reversible fragile watermarking method. Experimental results indicate that it can locate the forged blocks when the falsified area is not too large.
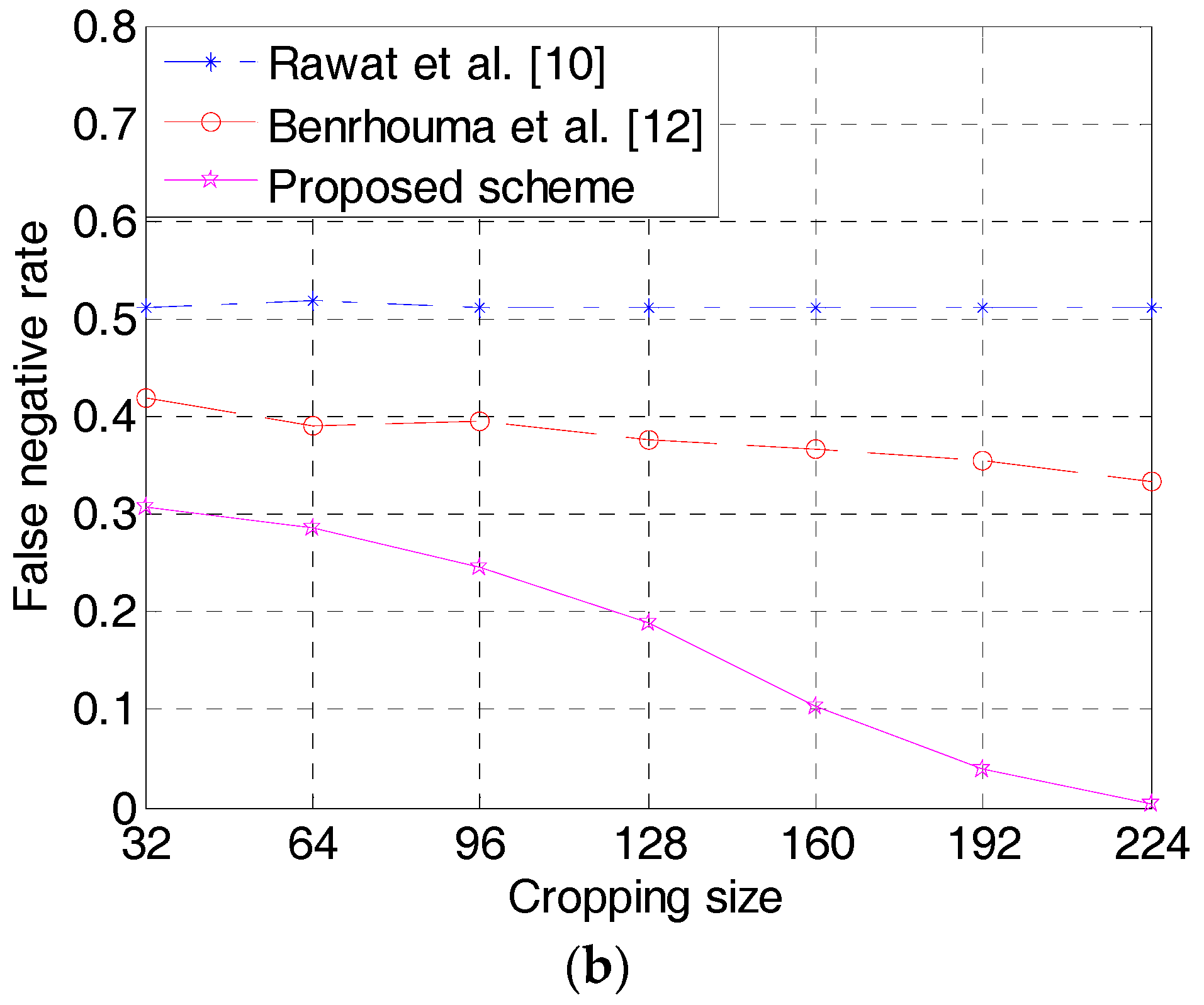
From the above analysis, it can be noted that the block-wise fragile watermarking algorithm has achieved great success in tamper identification and localization. However, the detection precision of the block-based watermarking method is limited to the block level [
8]. To solve this issue and improve the detection accuracy, many pixel-based fragile watermarking algorithms have been presented in recent years. In [
9], Liu et al. presented a simple fragile watermarking algorithm, where a binary authentication watermark was produced by a pixel-value difference between a chaotic image and the host image. Rawat and Raman [
10] presented a chaotic map-based method, but this algorithm has a potential security risk since it does not consider the image content in the watermark embedding process [
11]. Based on the security analysis, Teng et al. [
11] introduced an improved fragile watermarking method. The MSBs of the host image are taken into account in the process of watermark generation, which ensures the safety of the algorithm. The main problem existing in the above pixel-wise fragile watermarking schemes is that an extra binary watermark image is needed on the receiving end for tamper detection and localization. To achieve blind forgery detection, Benrhouma et al. [
12] introduced a chaos-based watermarking algorithm. The authentication data is constructed by the local pixel contrast between neighborhood pixels and average pixel value of each block. To achieve image authentication for stereoscopic images, Zhou et al. [
13] put forward a binocular visual characteristic-based fragile watermarking method. In their method, the binocular just noticeable difference (BJND) [
14] mode is utilized to complete watermark embedding, and a two-stage detection method is performed to increase the detection accuracy.
In this paper, we propose a pixel-based fragile watermarking algorithm for image tamper identification and localization. By analyzing singular value decomposition (SVD), it is found that the matrix product between the first column of the left singular matrix and the transposition of the first column in the right singular matrix has a strong relationship with the image texture information. By setting an appropriate threshold, a binary authentication watermark is generated. After the watermarking message is encrypted via Arnold permutation, it is inserted into the LSB plane of the original image. In tamper detection, the falsified region is revealed by the difference map between the extracted and regenerated watermarks.
The rest of this paper is organized as follows. In
Section 2, we describe the SVD in brief and analyze its intrinsic characteristic utilized in this paper.
Section 3 introduces the presented fragile watermarking algorithm. Experiments and performance analysis are expatiated in
Section 4. The conclusions are given at the end of this paper.
2. Singular Value Decomposition (SVD)
As an effective method of algebraic feature extraction, SVD is widely applied in signal processing [
15]. For a
matrix
A with rank
r, SVD can be expressed as
where
and
are column vectors of singular value matrices
and
, and
and
are their matrix elements, respectively.
is a diagonal singular matrix made up of singular values
, where
. The singular values have good stability that it can resist slight disturbances in signal processing. Moreover, the SVD can be implemented to arbitrary matrices without any restriction and the larger singular values contain the most information of an image. Due to these properties, SVD has been gradually applied in digital watermarking schemes [
16,
17,
18].
Taking
for example, the SVD can be rewritten as
Because
, it is noted from Equation (2) that the first item
plays an important role in matrix
A. To reveal this relationship, let us consider an exceptional circumstance that all the elements in matrix
A are the same. Then, matrix
A can be derived as
where
is the only singular value in
, i.e.,
. It is generally known that for a matrix with size of
,
equals
in such a circumstance. According to Equation (3), the matrix
can be calculated as shown in Equation (4):
From Equation (4), it can be observed that is only related to its matrix size () when the original matrix A has the same matrix elements.
Generally, the local pixel values in each image block change slowly. In other words, they have similar neighboring pixels. Inspired by this, we can promote the conclusion to image processing. To verify this conjecture, the image is firstly partitioned into numerous
blocks, for example
. For each image block, SVD is applied and
is calculated.
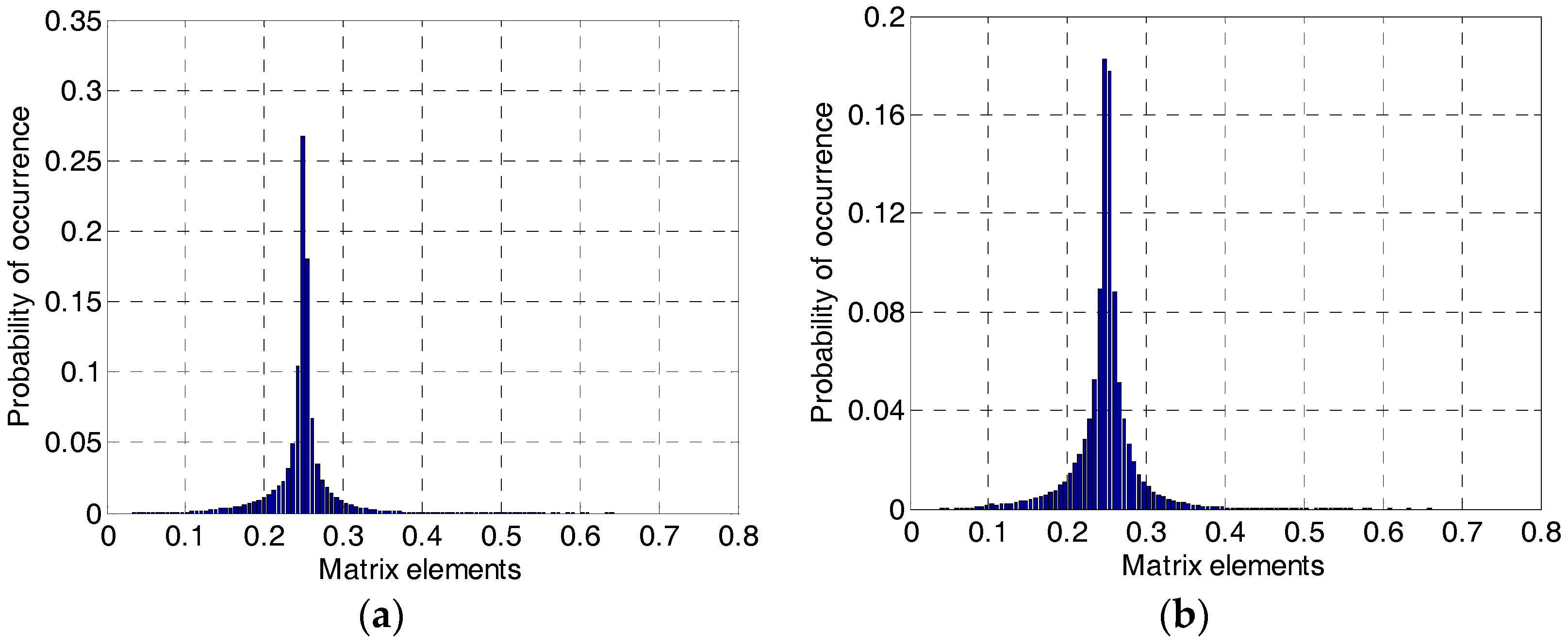
Figure 1 shows the probability distribution histogram of all the values in
, which takes grayscale images Lena and Barbara for example. From
Figure 1, we can see that the elements in matrix
satisfy the normal distribution approximately. In addition, most of the values are distributed around 0.25 (
), which is the reciprocal of the block size. This conclusion is consistent with the above analysis.
For an image, there are two kinds of image blocks including smooth blocks and texture blocks. In smooth blocks, the neighboring pixels have similar pixel values. On the contrary, the probability for similar neighboring pixels in texture blocks becomes much lower than that in the smooth region. In other words, the fluctuation of pixel values in texture blocks is much more serious than the smooth blocks. Based on this characteristic and the above analysis, we can draw the conclusion that the matrix product
in the smooth block should be closely associated with its block size, while in the texture block like edge region, this characteristic is severely weakened. According to this conclusion, we can segment an image into the texture region and smooth region by setting an appropriate threshold
T. This process can be illustrated in
Figure 2.
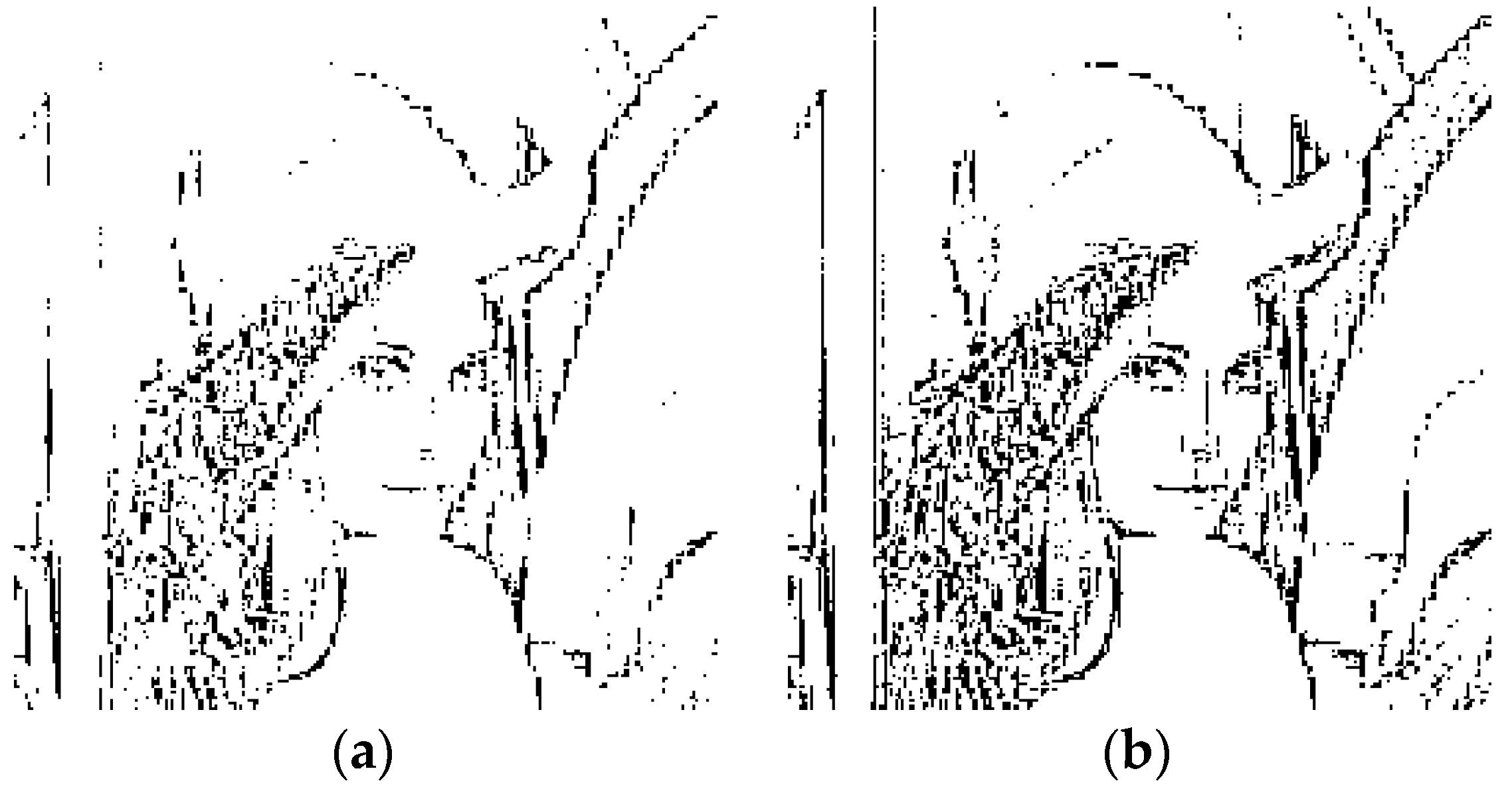
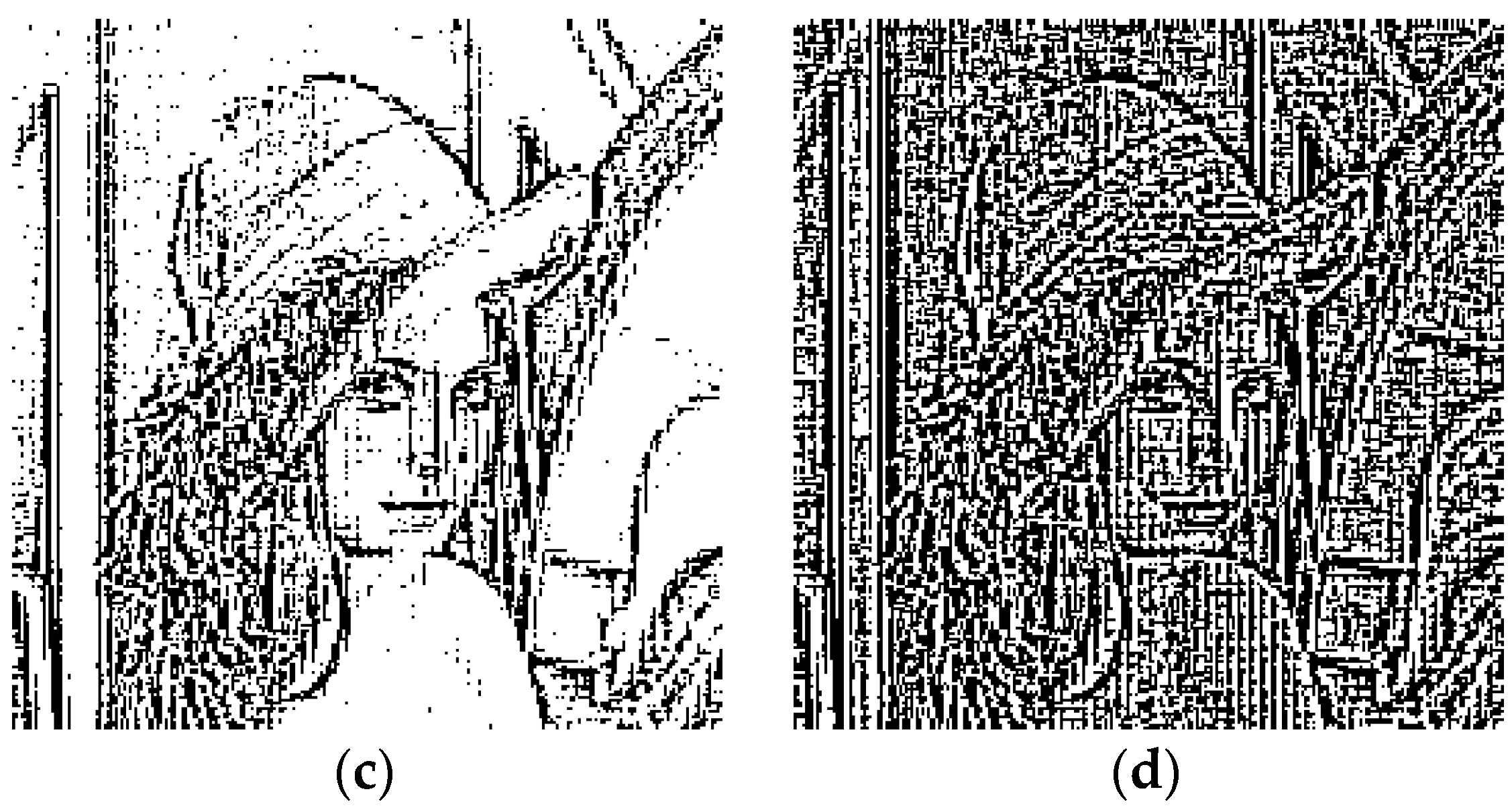
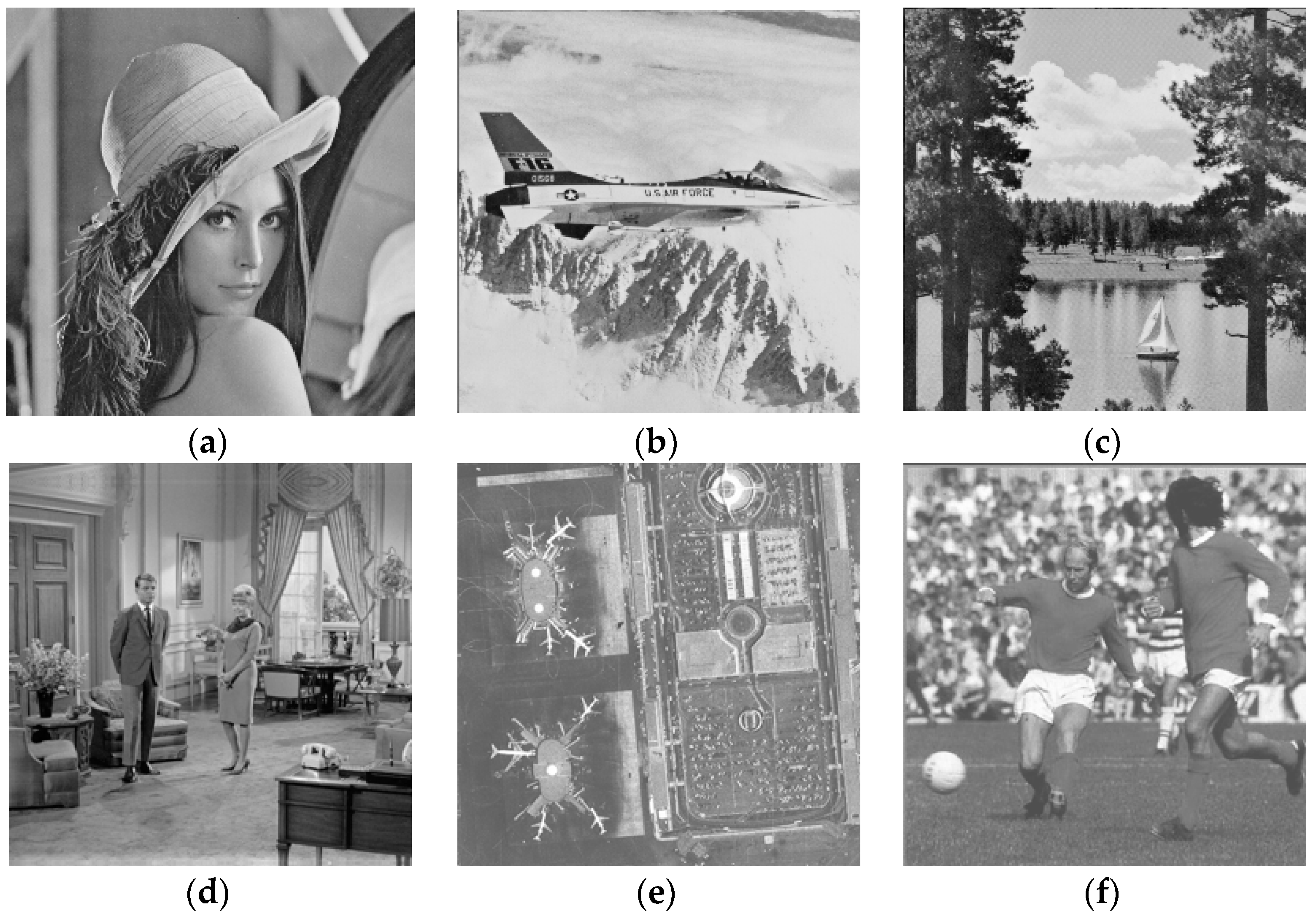
Figure 3 gives the binary segmentation images of image Lena with different thresholds, when the block size
. In the figures, the white area refers to the smooth region, while the black area represents the texture region. We can see that the texture features of an image can be well represented, especially when
as shown in
Figure 3d. This characteristic provides a theoretical basis for the design of the proposed watermarking scheme.
3. Proposed Watermarking Scheme
As mentioned above, the matrix product
in each image block is closely related to the image texture information. The more similar the pixel values in each block are, the more obvious this characteristic will be. In this section, we make full use of this property to introduce an effective fragile watermarking for image authentication. The binary texture image obtained in
Section 2 is served as the authentication information and inserted into the host image.
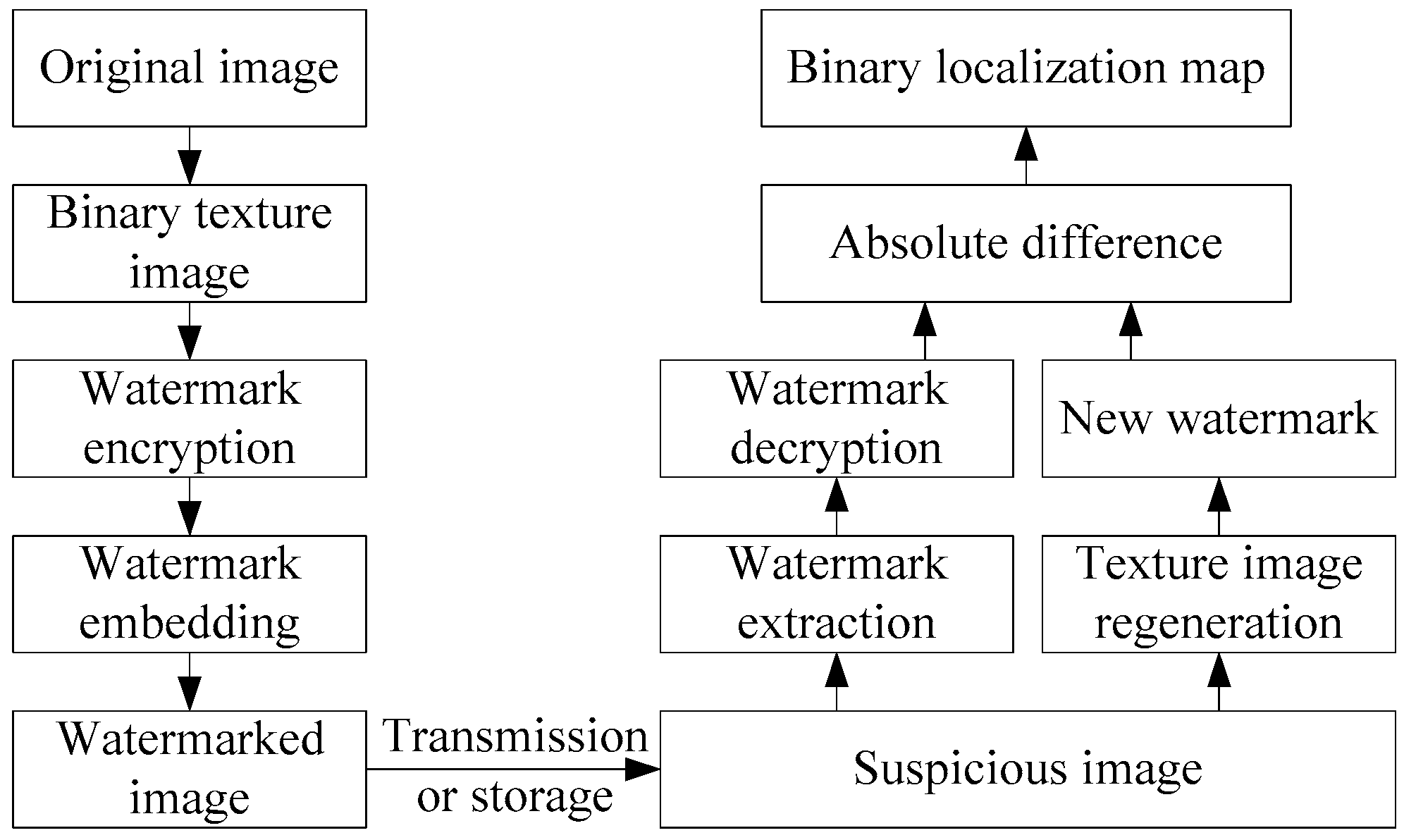
Figure 4 illustrates the flow chart of the presented watermarking algorithm, which consists of two main stages: watermark insertion on the sending side and the authentication process on the receiving side. The concrete procedures of watermark insertion are introduced as follows.
Step 1. The LSB plane of the original image is firstly initialized to zeros.
Step 2. The processed image is partitioned into many sub-blocks with a size of . The proposed algorithm is based on the fact that the image block has similar pixel values. However, with the increase of the block size, the probability for similar neighboring pixels is decreased. The characteristic mentioned above will be weakened, which will further affect the image segmentation effect. Generally, an incomplete image feature will lead to a higher false positive ratio in tamper detection. To ensure the effectiveness of the proposed method, we choose in this paper to illustrate the proposed algorithm. The block size is also adopted as an encryption key, which will be used on the receiving end.
Step 3. For each block, the SVD is performed and the matrix is calculated.
Step 4. By setting appropriate threshold
T, a binary image consisting of the texture information is obtained. From
Figure 3, we can see that the texture feature of the host image is better described than other thresholds when the threshold
. Therefore, the threshold
is set as 0.25 in this paper.
Step 5. To ensure the security of the proposed algorithm, an encryption algorithm known as Arnold transform [
19] is applied twice in the watermark embedding process. The binary texture image is firstly encrypted with a secret key
, and the host image is permuted with a secret key
(
).
Step 6. The embedding process is completed after the permuted LSB plane is replaced by the encrypted watermarking bits.
Step 7. After inverse Arnold transform with secret key , we obtain the watermarked image.
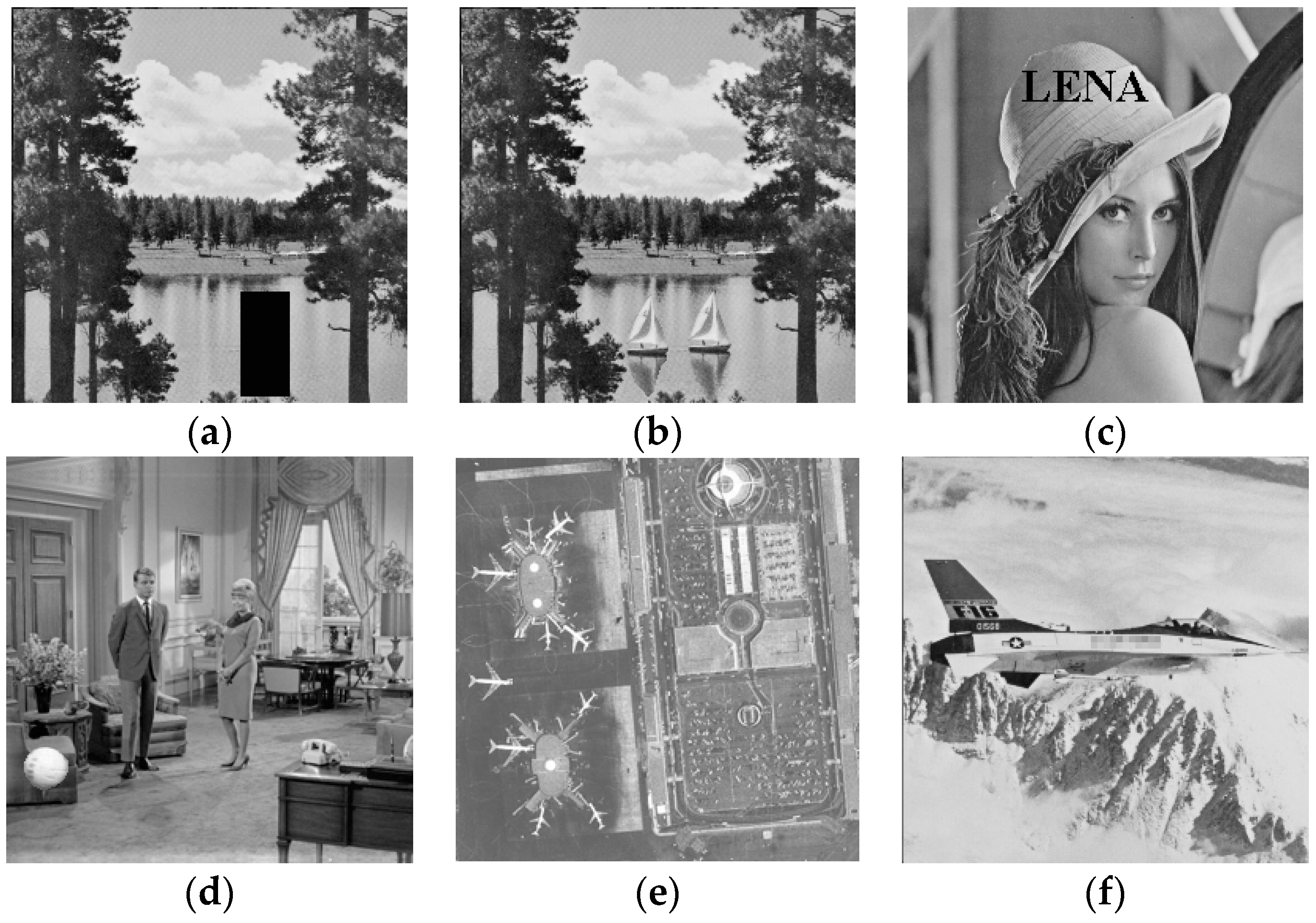
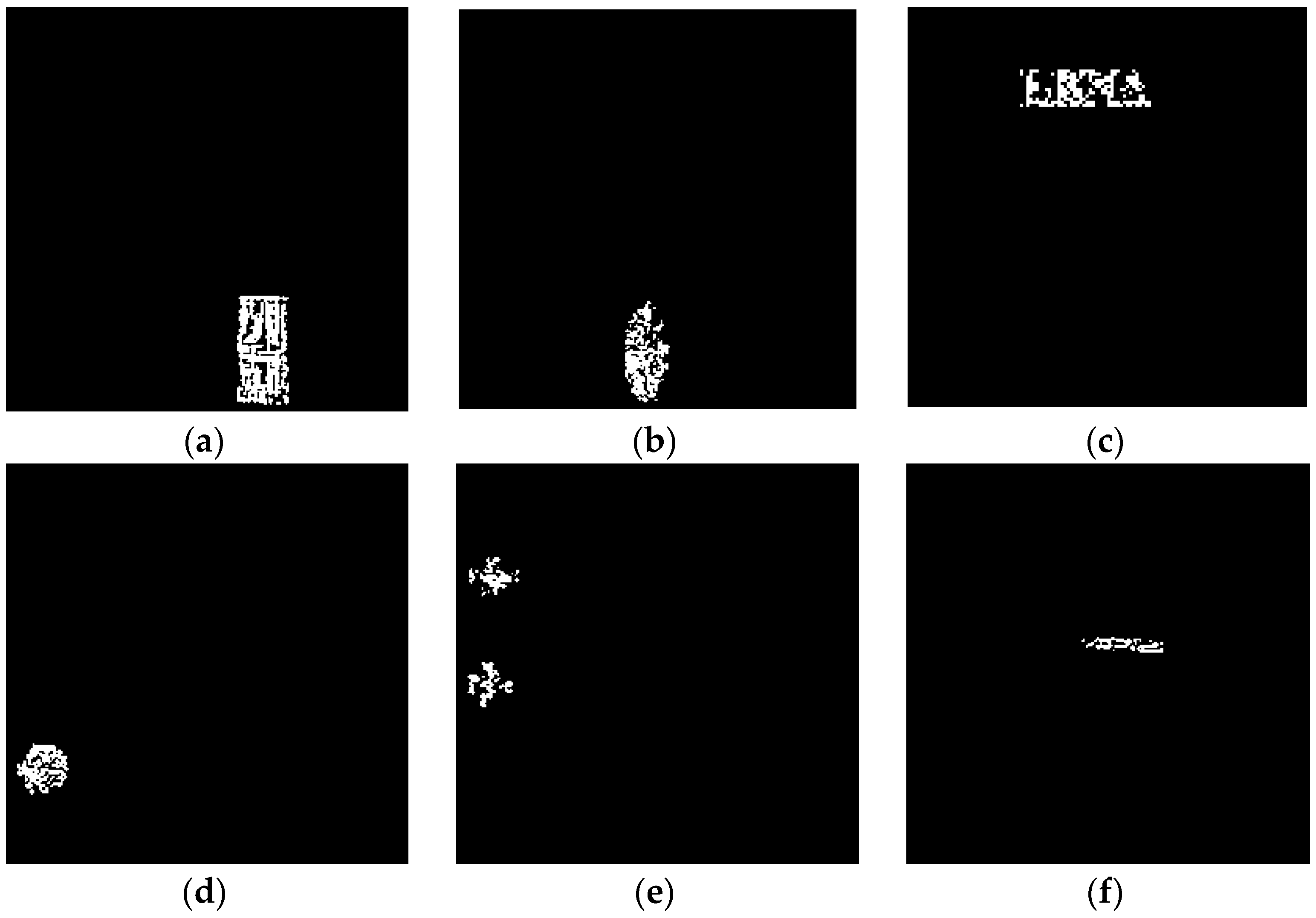
In image transmission or storage, the content of the digital image might be destroyed by malicious attacks, which makes its texture information inconsistent with the original image. We take advantage of this property to realize tamper detection and localization. The watermarked image is firstly permuted by Arnold transform with secret key . Then, the encrypted watermark is extracted from the LSB plane of suspicious image. With the help of secret key , we obtain the decrypted watermark. In addition, a new texture image is regenerated via the same first four steps in the watermark embedding process. By taking the absolute difference between the regenerated texture image and extracted information, a binary localization map is obtained. From this detection map, the tampered region can be determined.