1. Introduction
The area of sensor networks research has recently gained a great deal of attention [
1,
2,
3,
4,
5,
6,
7,
8,
9,
10]. Various sensors are used in both civilian and military tasks. Sensing devices can be deployed in either static or dynamic settings, where the positions of each sensor can be permanent or dynamically changing (such as in the case of sensors installed on air vehicles). Multiple sensor systems are commonly represented as networks, since besides collecting important information, sensing devices can transmit and exchange information via wireless communication between sensor nodes. Therefore, network (graph) structures are convenient and informative in terms of efficient representation of the structure and properties thereof. To analyze and optimize the performance of sensor networks, mathematical programming techniques are extensively used.
The purpose of this paper is to give a brief review of some of the recent developments in mathematical programming as applied to sensor network research. Various types of optimization problems can be formulated and solved in this context [
9,
11,
12]. Moreover, the pursued tasks can vary from optimizing the network performance to network interdiction, where the goal is to disrupt enemy networks by interfering with communication network integrity. We will outline the formulations and briefly describe the solution methods used to tackle these problems.
In many cases, the identified optimization problems are challenging from the computational viewpoint. In particular, the theoretical computational complexity of many of these problems was proven to be NP-hard. Therefore, efficient algorithms need to be developed to ensure that the near-optimal solutions are found quickly. This is essential to ensure that the decisions regarding efficient operations of sensor networks could be made in a real-time mode, which can be crucial in many applications. Moreover, the uncertain factors that commonly arise in real-world situations also need to be incorporated in the mathematical programming problems, which makes them even more challenging to formulate and solve. In this paper, we will address some of the challenges arising in this area.
In particular, we will describe several important classes of problems that have recently been addressed in the literature. We will start the discussion with the description of recent promising developments in the area of sensor network localization, which allow identifying global positions of all the nodes in a network using limited and sometimes noisy information. It turns out that semidefinite programming techniques can be efficiently used to tackle these problems. Next, we will discuss the problems of single and multiple sensor scheduling for area surveillance, including the setups under uncertainty. We will also address the issues of wireless communication network connectivity and integrity, as well as network interdiction problems.
2. Sensor Network Localization
The wide range of sensors applications reveal different requirements to the network topology identification [
13,
14,
15,
16]. For example network parameters can be influenced by land surface, transmission characteristics, energy consumption policy, etc. Ad hoc and dynamic networks also require identification of node coordinates. Such problems are intensively studied in the literature. Utilizing mathematical programming techniques often allows to find efficient solutions.
2.1. Positioning Using Angle of Arrival
In many cases, practical situations require one to be aware of a sensor’s physical coordinates. Installing GPS receivers in every sensor is not always optimal from the cost-related and other perspectives. Typically, only a few nodes (seed nodes, landmarks, etc) of the network are equipped with GPS and know their physical location. The rest of the nodes can only communicate with other nodes and determine relative location characteristics such as distance, angles, etc. Various localization techniques are used to obtain location of all the sensors in the network. The following method assumes that the network consists of two types of nodes: usual and more capable nodes - which knows its position. Niculescu and Nath propose a method by which nodes in an ad hoc network collaborate in finding their position and orientation, assuming that a small part of the network has a position capability. Also, every node in the network has a capability to determine the angle of the arriving signal (AOA).
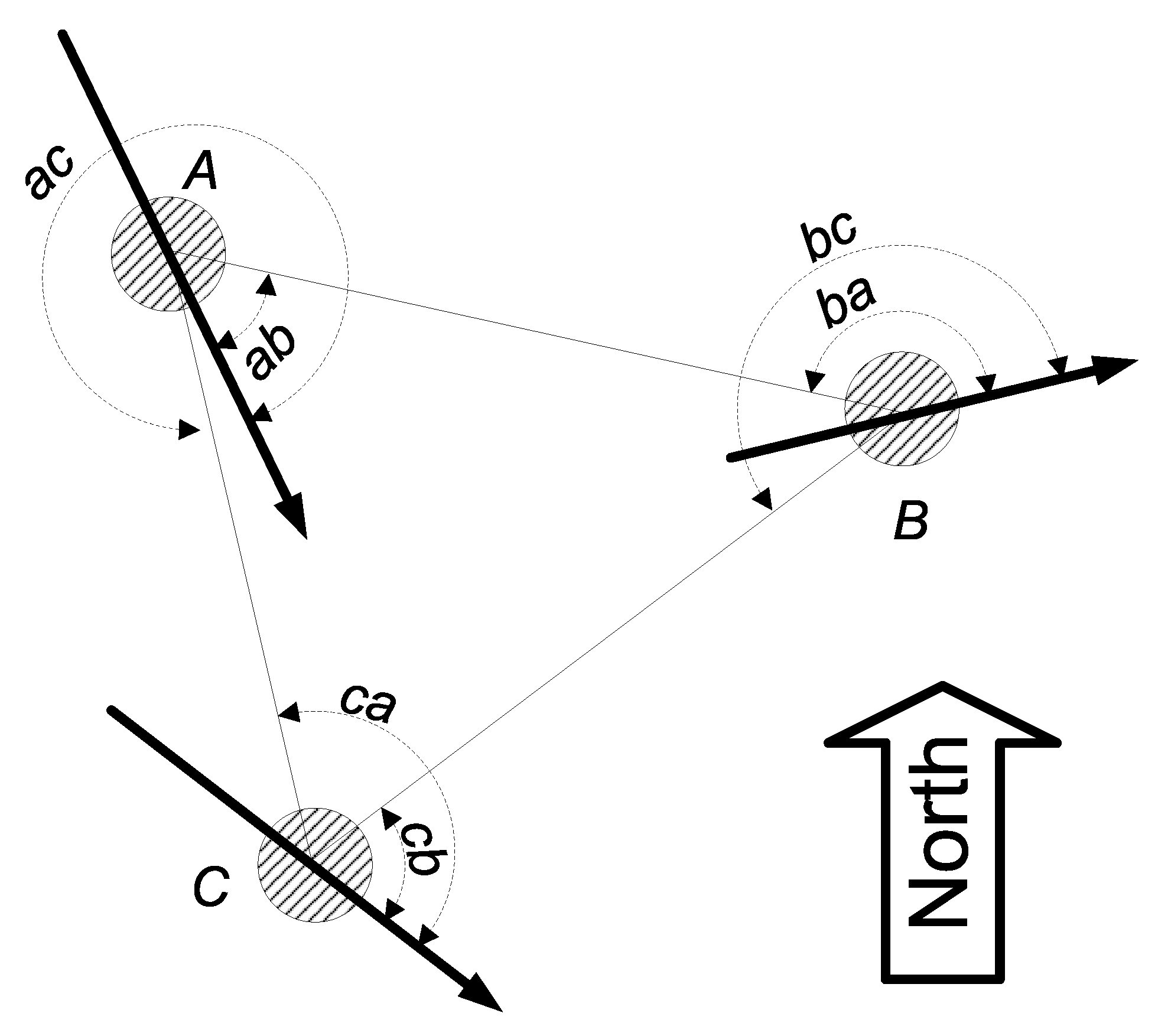
Each node in the network has one fixed main axis (which may not be the same for different nodes) and the node is able to measure all angles against this axis (
Figure 1).
Figure 1.
Nodes with AOA capability.
Figure 1.
Nodes with AOA capability.
Every node in an ad hoc network can only communicate with its immediate neighbors within the radio range, and its neighbors may not always be landmarks, i.e., the nodes that know their position. Niculescu Nath propose in [
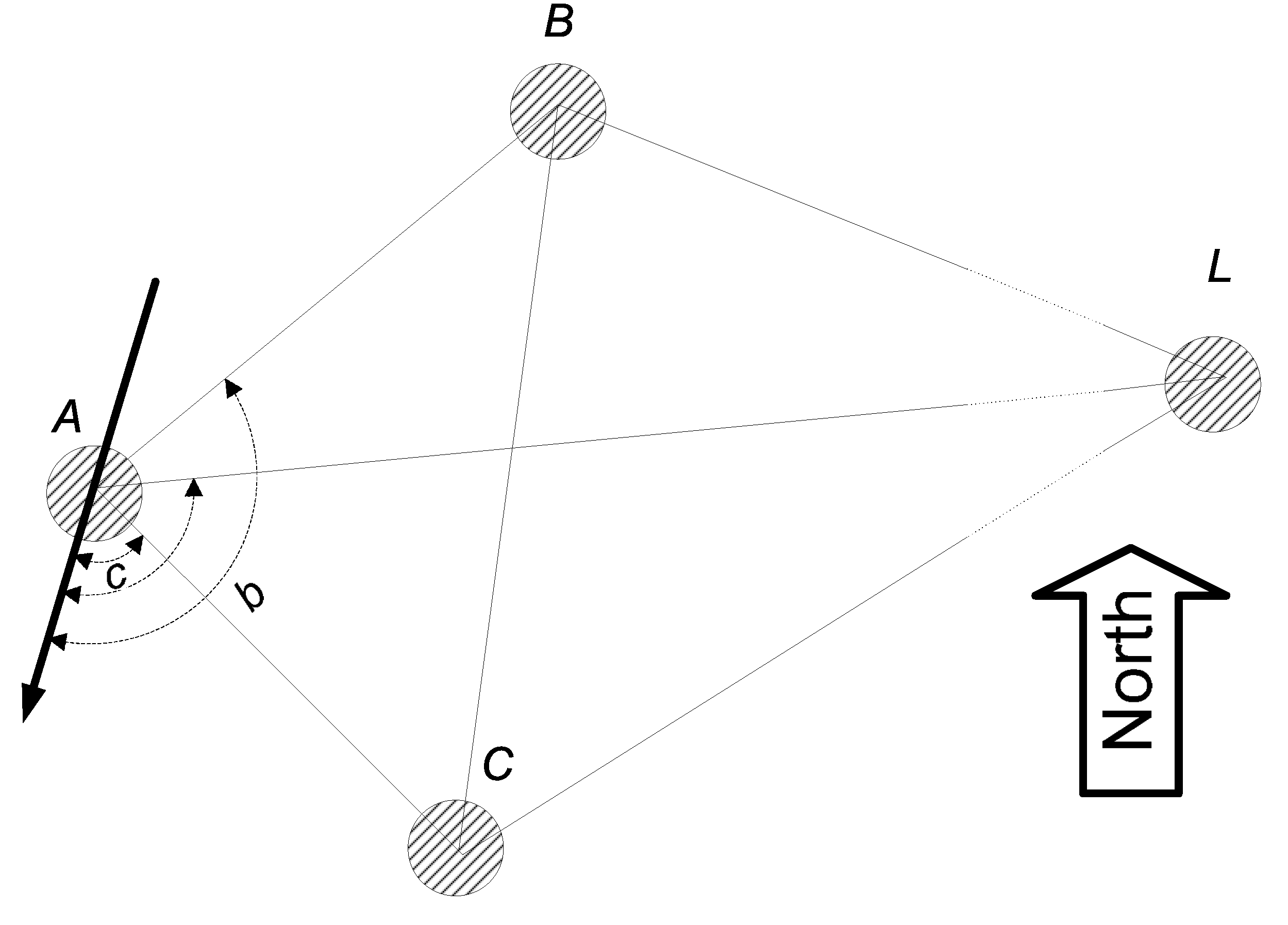
17] a method to forward orientation in such way, that the nodes which are not in direct contact with landmarks can determine its orientation with respect to the landmarks. Orientation means bearing, radial, or both. Bearing is an angle measurement with respect to another object. A radial is the angle under which the object is seen from another point. The authors examine two algorithms: Distance Vector Bearing (DV-Bearing), which allows each node to get a bearing to landmark, and DV-Radial, which allows a node to get a bearing and radial to a landmark. The propagation in both algorithms works the following way: nodes adjacent to landmarks determine their bearing/radial directly from landmark and send to the network the information about their position. The method of computing node’s bearing and radial at each step is shown in
Figure 2.
DV-Bearing algorithm works the following way. Nodes A, B, and C are neighbors and they can communicate with each other. Suppose that the node A needs to find its bearing to node L, which is not within radio range of node A but within radio range of nodes B and C. Since A, B, and C can locate each other than the node A can determine all the angles in triangles and . But that would allow to calculate the angle and consequently the bearing of A to L, which is equal to . Once node A knows three bearings to landmarks, which are not at the same line, then it can calculate its own location by triangulation.
The DV-Radial algorithm works the same way but with only one difference that node A needs to know not only bearings of nodes B and C to node L, but also the radials of B and C from L. The knowledge of radials improves accuracy of the algorithm. When all angles are measured against the same direction (for example, when compass is available) then these two methods become identical.
Figure 2.
Node A computes its bearing to L using information from B and C
Figure 2.
Node A computes its bearing to L using information from B and C
2.2. Semidefinite Programming (SDP) for Sensor Network Localization
The section considers localization problem when information on distances for anchor nodes and unknown sensors nodes are given. Suppose we consider localization problem on the plane. We have
m known points
,
and
n unknown nodes
,
. Let us consider three sets of node pairs
,
,
. For pairs in
we know exact distances
between
and
and
between
and
.
is a set of pairs with known lower bounds
and
. Finally,
is a set of upper bounds
and
. Naturally our goal is to minimize estimation error which immediately lead us to the following non-convex optimization problem
where
and
are defined as
The norm of vector
x is defined as
. In [
18,
19] the authors study semidefinite relaxations of the problem.
The formulated problem can be rewritten by introducing matrix notation and slack variables as
Here
is a
matrix. In order to cope with nonconvexity equality,
is replaced with
or equivalently
The last relation leads to a standard SDP formulation:
Papers [
18,
19] provide a criterion of solution existence and uniqueness, as well as statistical interpretation of the formulation in case when distance values are random values with normally distributed measurement errors. The SDP problems are solved using interior point algorithms. The numerical experiments results demonstrate the efficiency of the proposed approach.
3. Sensor Scheduling
Surveillance is an important task that can be effectively performed by an intelligent network of sensors. For example, satellites can be equipped with cameras to monitor Earth surface for different events, such as forest fire, border crossing or enemy hostile activity. Another example is traffic monitoring at the roads and intersections. Many scientific publications have recently appeared in the literature due to increasing interest to the problem of finding optimal schedule for sensors [
20,
21,
22,
23,
24,
25]. Most common technological and budget constraint is a low number of sensors to monitor all the objects of interest simultaneously. Thus, finding the schedule that reduces potential loss of limited observations is a task of high importance. This section provides a review of recently developed optimization based methods for building optimal schedule of sensor surveillance.
3.1. Single Sensor Scheduling
The simplest case is to model one sensor that observes a group of sites at discrete time points. Some physical systems require virtually zero time for changing a site being observed. For example, the time of a camera refocusing, which is installed on a satellite, is negligibly small. This assumption leads to the model proposed by Yavuz and Jeffcoat in [
26].
Assume that we need to observe
n sites during
T time periods. During every period a sensor is allowed to watch only at one of
n sites. The scheduling decision can be modeled using binary variables
t is a discrete variable and
. If a site
i is not observed for some period of time, it leads to the penalty that is proportional to the time of not observing this site. This penalty can be modeled using another group of decision variables. Let
denotes the time of last visiting site
i before time moment
t. Let us note that variables
completely determine values of
. Fixed penalty
and variable penalty
are associated with site
i at time moment
t. Thus, the penalty at time
t associated with site
i is
[
26] suggests minimizing maximum loss over all sites and time intervals. Thus the objective function is defined as
. This objective function can be linearized and consequently the problem looks as following
Constraints (6) ensure that the sensor visits only one site at a time. Constraints (7) -(8 ) set the dependence on . That is is set to t if and only if the sensor is observing site i at time t otherwise .
Single Sensor Scheduling problem is NP-hard [
27] therefore various greedy heuristics have been proposed. The idea behind greedy algorithm is simple. At time
we find the site with the smallest penalty then at next time period we find another site with the smallest penalty. This sequence is repeated for all
T time intervals. Thus the complexity of suggested approach is
. Yavuz and Jeffcoat has also suggested the “look ahead” modification of greedy heuristic which takes more computational time but computational experiment demonstrate that the solution is improved compared to the initial simple greedy optimization.
3.2. Stochastic approach
The stochastic nature of scheduling surveillance reduces the predictability of sensors behavior and therefore plays an important role for military tasks. Here we assume that sites are chosen randomly based on probability of transition from i-th to j-th site . Then sensor scheduling can be considered as a Markov chain stochastic process and characterized by steady state probabilities .
The goal of stochastic approach is finding such steady state probabilities that minimize maximum loss. Let
be the visit period of site
i. Then the penalty of information loss at site
i is
at time
t. Let us consider a sufficiently small planning horizon with time-invariant site dynamics, this allows us to reduce
to
and denote this approach as static. Visiting site
i for every
periods is equal to spending
of the sensor’s time at the site
i. The optimal schedule is achieved when
; i.e., all the available time is utilized. Also, sensor never stays at any site for two consecutive periods of time. Thus
(or
) should be satisfied for each site. Then the non-linear model for obtaining optimal stationary probabilities is formulated as
A heuristic is proposed to solve this nonlinear continuous problem. Utilizing constraints (
14), the authors define a lower bound on the objective function value with
Then, we set
and calculate
and
for all
i. Note that
for the sites with
and
for the remaining constraints. If the determined probabilities add up to one then the optimal solution is found, and the procedure terminates. If the sum of probabilities is less than one, then one can shift some
π-s up to make
. In the case when
the found
C is infeasible and we can apply iterative procedures (such as bisection) to find
C such that
.
The static approach minimizes average penalty that is determined by steady probabilities and, thus, does not address the cases of long lasting absence at a site. Taking into account the fact that some random outcomes may result in extremely long penalties it is reasonable to increase the probabilities of visiting the sites that were visited long time ago. On the other hand, the probability of observing the sites, which were recently visited, should be decreased. Recall that represents the last time when the site i was visited by the time t. The probability of visiting a site must depend on the difference , thus it will increase probability of visiting overdue sites.
To create a preference for visiting site
i at time
t the following adjustment factors are proposed
It is bigger than one for overdue sites and less than one for the sites that have been visited within their expected visiting periods. The parameter
k is a user-defined parameter, which determines the weight of the adjustment factor. The probabilities of visiting each site at specific time point
t are based on previous history and can be computed as
, where
.
Finally, a hybrid method was proposed based on a combination of greedy algorithm and the stochastic method, discussed above. The first step calculates the penalty of not visiting site i: Next step calculates preference values to visit each site: where And then the probabilities of visit are equal to: , where .
3.3. Multiple Sensors Scheduling Using Percentile Type Constraints
Boyko
et al have proposed to reformulate problem (
4) -(
11) for the case of
m sensors [
28].
For every site i and every time point t we can calculate penalty associated with the last time a sensor visited this site . Let us pick % of worst cases among these penalty values. Then, instead of minimizing maximum loss we can minimize the the average taken over this % percent of worst penalty values. Despite the fact that this formulation is deterministic it is equivalent to computing Conditional Value-at Risk (CVaR) for a set of random outcomes having equal probabilities .
CVaR [
29,
30] is closely related to a well-known quantitative risk measure referred to as Value-at-Risk (VaR). By definition with respect to a specified probability level
(in many applications the value of
is set rather high, e.g. 95%), the
α-VaR is the lowest amount
ζ such that with probability
, the loss will not exceed
ζ, whereas for continuous distributin the
α-CVaR is the conditional expectation of losses
above that amount
ζ. As it can be seen, CVaR is a more conservative risk measure than VaR, which means that minimizing or restricting CVaR in optimization problems provides more robust solutions with respect to the risk of high losses (see
figure 3).
Figure 3.
Graphical representation of VaR and CVaR.
Figure 3.
Graphical representation of VaR and CVaR.
The reader can find the formal definition of CVaR for various distribution cases in [
29,
30]. Rockafellar and Uryasev [
31,
32] showed that minimizing CVaR-type objective function of linear argument can be reduced to LP. In the sensors scheduling problem the loss function is introduced as
Thus the initial multiple sensors scheduling problem can be considered as the CVaR-based formulation
Even though the parameters
i and
t of the loss function (
24) are deterministic by nature, the stochastic framework was applied to this model in order to compute a percentile-type measure.
The parameters that quantify fixed and variable information losses are in many cases
uncertain by nature. The following mathematical programming formulations allow quantifying and restricting the risks of worst-case losses associated with the aforementioned uncertain parameters. It is made by utilizing quantitative risk measures that allow one to control the robustness of the optimal solutions. Assuming that
and
are random values we can formulate stochastic program utilizing the notion of CVaR.
Here we use S scenarios ( and , ) sampled from the distribution of penalty coefficients.
The mixed integer linear formulation was solved by ILOG CPLEX. The problems were also reformulated in terms of cardinality constraints and solved by AOrDa Portfolio Safeguard software package. Both solver find a good quality approximate solutions for large size problems.
4. Communication Network Interdiction
An important issue in military applications is to neutralize the communication in the sensors network of the enemy. This problem is known as jamming or eavesdropping a wireless communication network. This section introduces optimization formulations that allow to place jamming devices delivering maximal harm to the adverse sensors network. We start from a deterministic case when node locations are known.
The goal of jamming is to find a set of locations for placing jamming devices that suppresses the functionality of the network. Assume that
n jamming devices are used to jam
m communicating sensors. The assumption is made that the sensors and jammers can be located on a fixed set of locations
V. The jamming effectiveness of device
j is calculated as
where
d is a decreasing function of the distance from the jamming device to the node being jammed.
The cumulative level of jamming energy received at node
i is defined as
where
n is the number of jamming devices. Then, jamming problem can be formulated as the minimization of the number of jamming devices placed, subject to a set of covering constraints:
Seeking the optimal placement coordinates for jamming devices given the coordinates leads to non-convex formulations for most functions d. Thus, integer programming models for the problem are proposed.
A fixed set
of possible locations for the jamming devices and the set of communication nodes are introduced by Commander
et al in [
33]. Define the decision variable
as
Then we have the optimal network covering formulation given as
Here the objective is to minimize the cost of jamming devices used while achieving some minimum level of coverage at each node. If
then the number of jammers is minimized.
If the goal is to suppress sensors communications we can minimize jamming cost with respect to the required level of connectivity index. Communication between nodes
i and
j is assumed to be destroyed if at least one of the nodes is jammed. Further, let
if there exists a path from node
i to node
j in the jammed network and let
be an indicator that
i-th node is jammed. This can be formulated as
where
denote the cumulative level of jamming at node
i,
is some large constant. This problem can be formulated as a mixed integer linear problem and justification is provided in [
33].
Finally, Commander et al provide percentile-based formulation for deterministic jamming problems. Suppose it is determined that jamming some fraction of the nodes is sufficient for effectively dismantling the network. This can be accomplished by the inclusion of α-VaR constraints in the original model. Let be an indicator whether node i is jammed ().
Then to find the minimum number of jamming devices that will allow covering
of the network nodes with prescribed levels of jamming
, we must solve the following integer program
The
α-CVaR optimization model for network covering can be formulated as a mixed integer linear program using a standard linearization framework:
The VaR and CVaR models can also be written for connectivity suppression models in the similar fashion. We refer the reader to [
33] for details.
The deterministic formulations of the wireless network jamming problem are extended in [
34] to tackle the stochastic jamming problem formulations using percentile type constraints. These formulations consider the case when the exact topology of the network to be jammed is not known, but we know the distribution of network parameters.
Since the exact locations of the network nodes are unknown, it is assumed that a set of intelligence data has been collected and from that a set
of the most likely scenarios have been compiled. Scenario
contains both the node locations
and the set of jamming thresholds
. For each scenario
, the set
needs to be jammed. Taking into account all the scenarios we can write a mathematical program for node covering problem:
It is unlikely to find the solution that can provide effective jamming strategy for all scenarios. Therefore, the notion of percentile-based risk measures can be utilized to develop formulations of the robust jamming problems incorporating these risk constraints. The robust node covering problem with Value-at-Risk constraints can be formulated as
The loss function can be considered as the difference between the energy required to jam network node
i, namely
, and the cumulative amount of energy received at node
i due to
x over each scenario. With this the robust node covering problem with CVaR constraints is formulated as follows.
The CVaR constraint (
59) implies that for the
of the worst (least) covered nodes, the average value of
is less than or equal to 0.
Numerical experiments demonstrate that problems of moderate size can be solved by ILOG CPLEX. Finding effective heuristics and approximations for sensors network jamming problems of large dimensions is an interesting and important research direction.