An Anonymous Offline RFID Grouping-Proof Protocol
Abstract
:1. Introduction
1.1. Motivation
1.2. Our Contributions
- (1)
- (2)
- We establish a scheme to seal the identity of the tag into the grouping-proof message by the group key and session key. So the proof data include two types of tag information: the group member identity and the individual identity.
- (3)
- We propose an ECC based offline anonymous grouping-proof protocol with two tags, denoted as EAGP. Based on EAGP, we extend the protocol into n tags condition , expressed as EAGP. The EAGP has two verification stages. The first stage is used to verify the legality of the tag’s group member identity and check the grouping-proof briefly. The second stage is used to verify the identity of the tag and further confirm the grouping-proof.
- (4)
- We carry out the security analysis, performance analysis and correctness proof about the EAGP, and obtain a conclusion that this protocol can resist DoP attack [21] and impersonation attack. It can also protect the tag’s information when the reader was compromised. Moreover, EAGP has good scalability in multiple tags condition.
2. Related Work
3. Preliminaries
3.1. The Ellipse Curve Cryptography
3.2. Elliptic Curve Discrete Logarithm Problem (ECDLP)
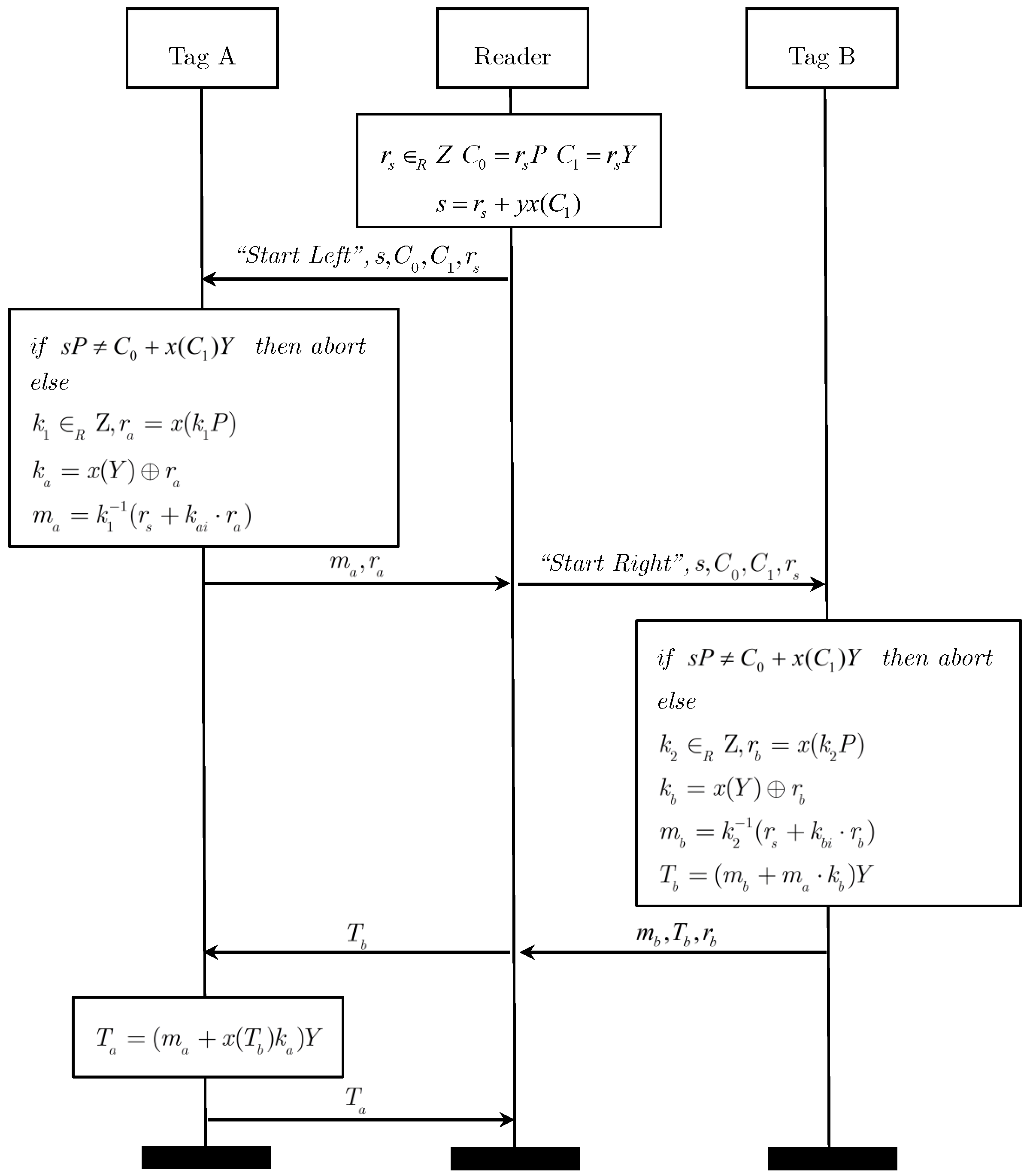
4. Investigation of Kang’s Protocol
- (1)
- According to the random number broadcasted by the reader, tag A generates random number , calculates and sends it to tag B via the reader.
- (2)
- Tag B calculates and sends to tag A via the reader.
- (3)
- Tag A calculates and send it to the reader.
- (4)
- Finally, the reader passes these data as grouping-proof to the verifier for validation.
- (1)
- The key distribution: in Kang’s protocol, tag A and tag B need to store the reader’s public key. If the reader is changed, the new public key needs to be written into all the tags. If the amount of tags is very big, the overhead is too serious.
- (2)
- The DoP attack: the reader in Kang’s protocol can not validate the proof and is unable to check the legality of tags. If the reader suffered from DoP attack or some unrelated tags taken part into the proof process, before the proof be sent to the verifier, the failure can not be identified immediately which will reduce the system real-time performance.
- (3)
- Communication overhead: the using of authentication stage increases the number of communication times between the tag and the reader, which leads to the additional overhead of communication.
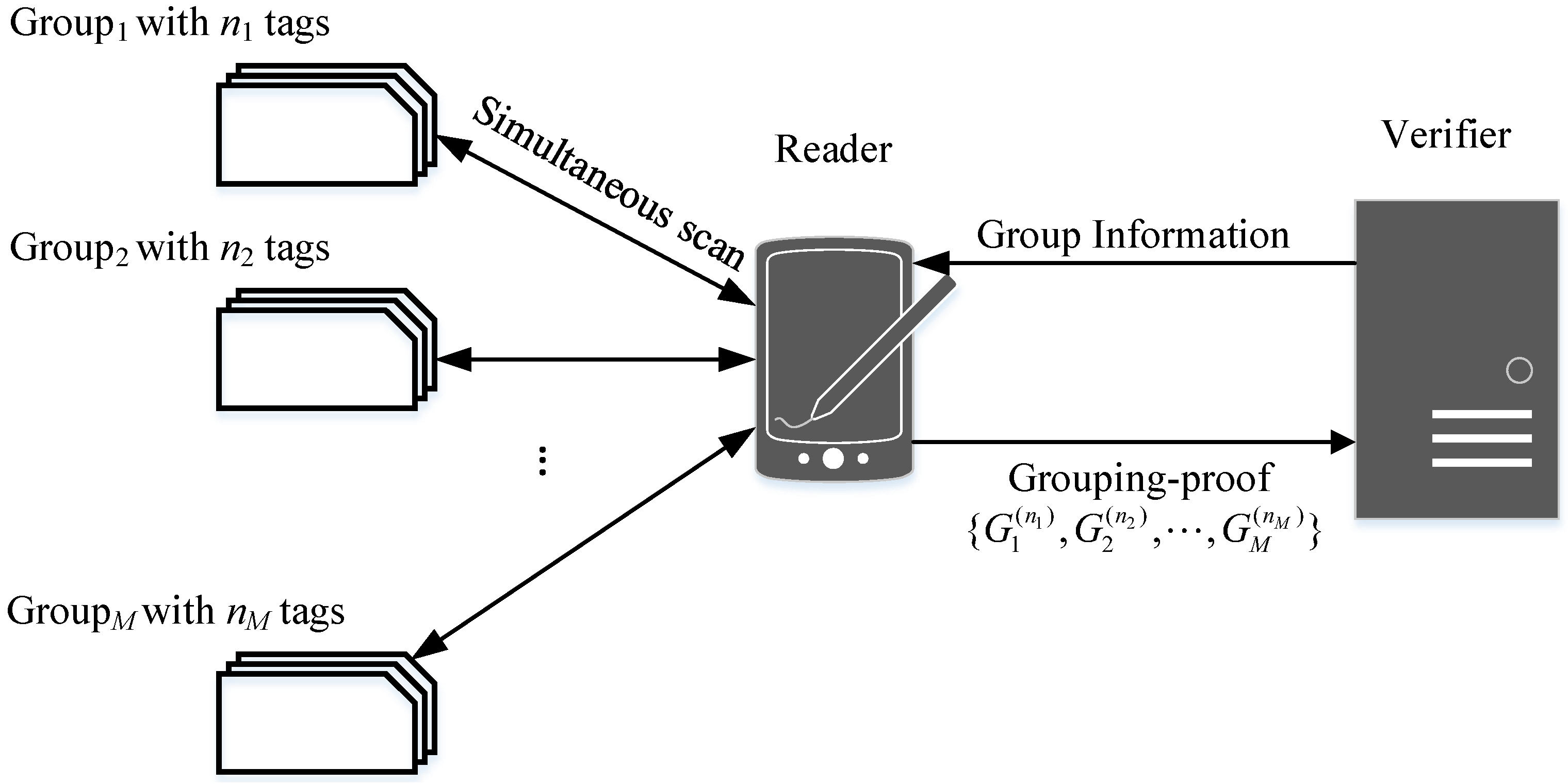
5. The System Model and Security Requirement
5.1. The System Model
- Tag: the tags in our protocol are passive low-cost devices which have a relative small storage and limited computational capacity. The tags are divided into several groups.
- Reader: the RFID reader is a powerful device which is controlled by an untrusted third party. For security reasons, the privacy information of tag and verifier is unknown to the reader.
- Verifier: an offline trusted third party (TTP) which maintains all the keys and identities of groups.
5.2. The Adversary Model
5.3. The Security Requirement of Grouping-Proof System
- AnonymityThe anonymity of tags and readers, which means the adversary cannot get the identity of a tag or a reader by eavesdropping the protocol message.
- Location PrivacyThe adversary cannot track the location of a reader and tags through the protocol messages.
- Resist to replay attackThe adversary cannot use the message in previous sessions to cheat the reader or tags to generate grouping-proof.
- Defense the DoP AttackThe adversary cannot use illegal tag involved in the protocol to disturb the proof validation execute by the verifier [21].
- Tag secret information protectionIf the reader is hacked in, the adversary can’t use the information stored in it to extract any secret information of tags.
6. Description of EAGP
6.1. EAGP
6.1.1. Initial Phase
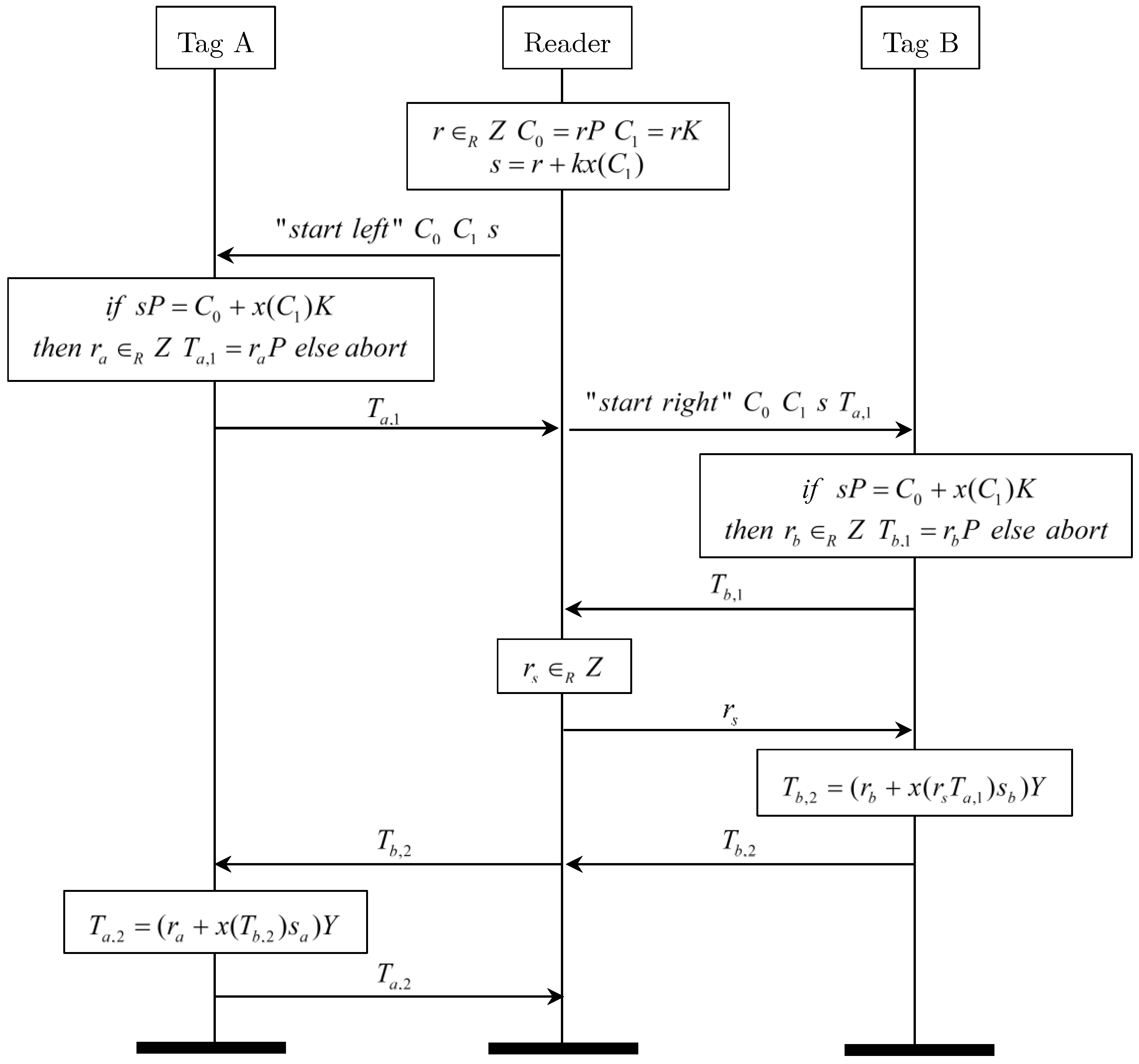
6.1.2. Grouping-Proof Generation Phase
- (1)
- Reader generates a random number , calculates , , and . Then, the is sent to the tag A along with the message of “start left”.
- (2)
- Tag A verifies the equation . If it does not hold, the protocol is terminated. Otherwise, it generates a random number , calculates , generates the session secret key . Then, it seals its secret key into message as follows:Finally, tag A sends to the reader.
- (3)
- Reader sends along with the message of “start right” to tag B.
- (4)
- Tag B verifies the equation . If it does not hold, the protocol is terminated. Otherwise, it generates a random number , calculates and sends to the reader.
- (5)
- Reader sends the message to tag A.
- (6)
- Tag A calculates , and sends it to the reader.
- (7)
6.1.3. Verification Phase
- (1)
- Reader verification step:The utilization of group key y can prove that tag A and B belong to the same group and be scanned by the reader simultaneously.
- (2)
- Verifier verification step:The second verification stage is executed by the verifier to authenticate the tag’s identity in grouping-proof. The procedure of tag A is described as follows, the verification of tag B is the same as it:
- Calculate the following equations
- If is valid, the validation is successful, and the verifier stores the proof in the server as a record. Otherwise, the validation fails and the proof is abandoned.
6.2. Extension to Tags
6.2.1. Initial Phase
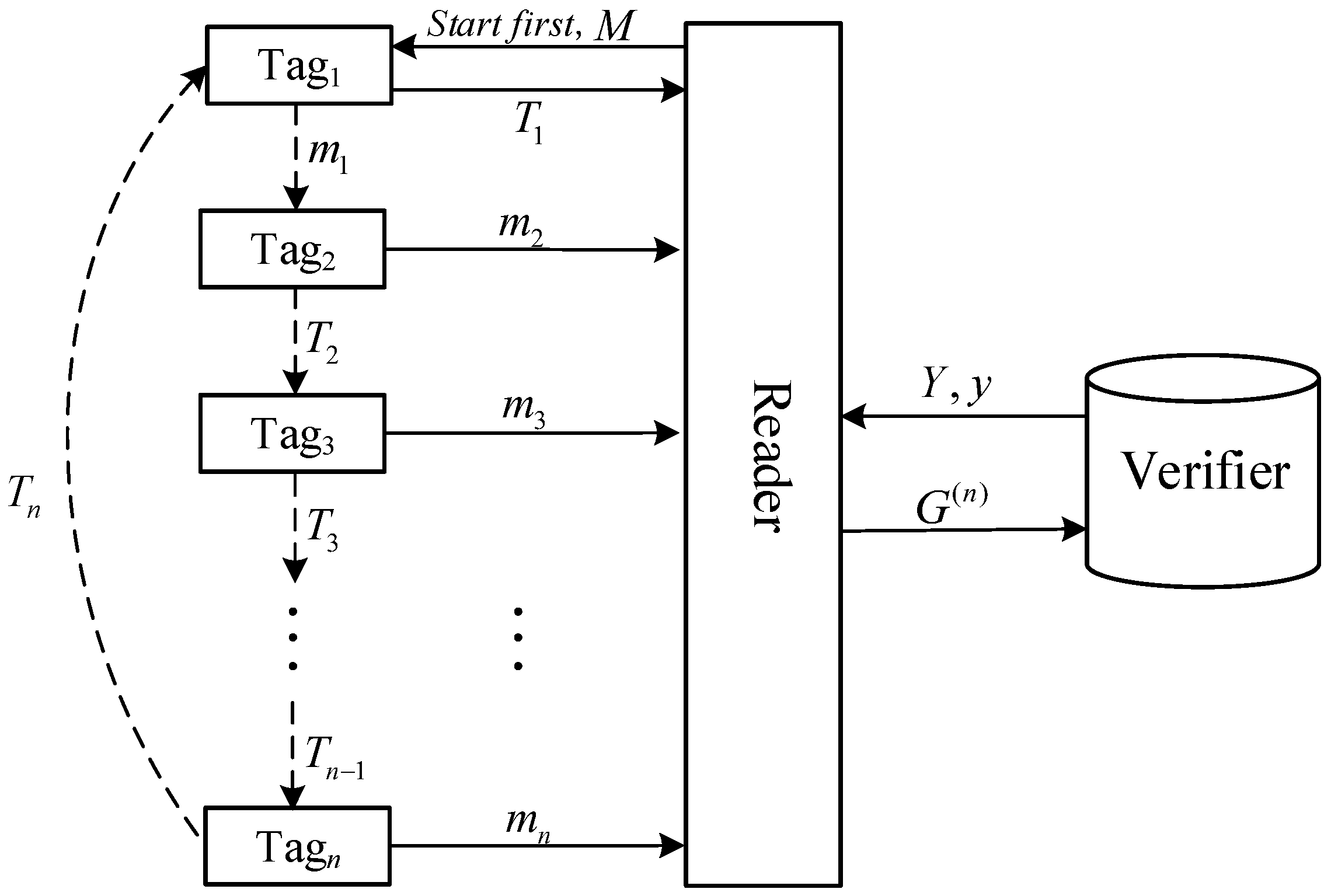
6.2.2. Grouping-Proof Generation Phase
- (1)
- Reader selects as the first tag to calculate the grouping-proof. It generates message as Figure 3, and sends it to with the “Start first” query.
- (2)
- authorizes the reader, generates message by Equation (2) and sends it to by the reader.
- (3)
- selects a random number , calculates ,then sends to the reader, to via the reader, where
- (4)
- generates and the same way as , calculates as below.sends to the reader, to via the reader.
- (5)
- generates and , calculates as below.Then sends to the reader, to via the reader.
- (6)
- The last tag calculates , and sends to via the reader.
- (7)
- calculates by Equation (16), and sends it to the reader.
- (8)
- The reader generates the grouping-proof shown in Equation (17).
6.2.3. Verification Phase
7. Security Analysis and Comparison
7.1. Security Analysis
7.1.1. The Anonymous of Tag and Reader
7.1.2. The Location Privacy of Tag and Reader
7.1.3. Defense Against DoP Attack
7.1.4. Tag Secret Information Protect
7.1.5. Resist to Impersonation Attack
- Impersonate tagThere are two situations where the adversary impersonate a tag: (1) the adversary does not know any secret key, that means it cannot deduce legal . In this situation, the grouping-proof generated in presence of attack cannot pass the reader validation Equation (21). This attack can be detected before the proof is sent to the verifier, protecting the system from DoP attack. (2) The adversary gets the group’s public key Y. From Y, the adversary can deduce the session key . Then the adversary can generate the grouping-proof that can satisfy Equations (21). However, due to the lack of tag ’s authentication secret key , to forge the legal need solve the ECDLP described in Section II, thus the probability is negligible. So it is nearly impossible to pass the verifier validation. In conclusion, EAGP can resist the tag impersonation attack in both situations.
- Impersonate readerIf the adversary impersonate the reader, it needs the group key y to generate s, which is used by tag to authenticate the reader. Without the correct s, the tag will abort the protocol, and the adversary cannot get any information about .From the above, it is difficult for the adversary to impersonate tag or reader. The EAGP can resist impersonation attack.
7.1.6. Resist to Eavesdrop Attack
7.1.7. Resist to Replay Attack
- (1)
- The adversary sends to the reader.
- (2)
- The adversary sends as to via the reader.
- (3)
- calculates
7.2. Security Comparison
8. Performance Analysis
9. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
Appendix A. Correctness Proof of EAGP
References
- Juels, A. “Yoking-proofs” for RFID tags. In Proceedings of the IEEE Annual Conference on Pervasive Computing and Communications Workshops, Orlando, FL, USA, 14–17 March 2004; pp. 138–143. [Google Scholar]
- Chen, Y.-Y.; Tsai, M.-L. An RFID solution for enhancing inpatient medication safety with real-time verifiable grouping-proof. Int. J. Med. Inform. 2014, 83, 70–81. [Google Scholar] [CrossRef] [PubMed]
- Chen, C.-L.; Wu, C.-Y. Using RFID yoking proof protocol to enhance inpatient medication safety. J. Med. Syst. 2012, 36, 2849–2864. [Google Scholar] [CrossRef] [PubMed]
- Peris-Lopez, P.; Orfila, A.; Hernandez-Castro, J.C.; van der Lubbe, J.C.A. Flaws on RFID grouping-proofs. Guidelines for future sound protocols. J. Netw. Comput. Appl. 2011, 34, 833–845. [Google Scholar] [CrossRef] [Green Version]
- Zhibin, Z.; Qin, L.; Guojun, W.; Weijia, J. Secure Medication Scheme Using the Grouping-proof Technology. J. Chin. Comput. Syst. 2015, 36, 2349–2353. [Google Scholar]
- Huang, H.; Ku, C. A RFID grouping proof protocol for medicationsafety of inpatient. J. Med. Syst. 2009, 33, 467–474. [Google Scholar] [CrossRef] [PubMed]
- Chien, H.-Y.; Yang, C.-C.; Wu, T.-C.; Lee, C.-F. Two RFID-based solutions to enhance inpatient medication safety. J. Med. Syst. 2011, 35, 369–375. [Google Scholar] [CrossRef] [PubMed]
- Xie, K.; Cao, J.; Wang, X.; Wen, J. Optimal resource allocation for reliable and energy efficient cooperative communications. IEEE Trans. Wirel. Commun. 2013, 12, 4994–5007. [Google Scholar] [CrossRef]
- Pizzolante, R.; Carpentieri, B.; Castiglione, A.; Castiglione, A.; Palmieri, F. Text Compression and Encryption through Smart Devices for Mobile Communication. In Proceedings of the 2013 Seventh International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing, Taichung, Taiwan, 3–5 July 2013; pp. 672–677. [Google Scholar]
- Castiglione, A.; Palmieri, F.; Fiore, U.; Castiglione, A.; De Santis, A. Modeling energy-efficient secure communications in multi-mode wireless mobile devices. J. Comput. Syst. Sci. 2015, 81, 1464–1478. [Google Scholar] [CrossRef]
- Sundaresan, S.; Doss, R.; Zhou, W. Offline grouping proof protocol for RFID systems. In Proceedings of the 2013 IEEE 9th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Lyon, France, 7–9 October 2013; pp. 247–252. [Google Scholar]
- Liu, H.; Ning, H.; Zhang, Y.; He, D.; Xiong, Q.; Yang, L. Grouping-Proofs-Based Authentication Protocol for Distributed RFID Systems. IEEE Trans. Parallel Distrib. Syst. 2013, 24, 1321–1330. [Google Scholar] [CrossRef]
- Chien, H.-Y.; Liu, S.-B. Tree-based RFID yoking proof. In Proceedings of the International Conference on Networks Security, Wireless Communications and Trusted Computing, Wuhan, China, 25–26 April 2009; pp. 550–553. [Google Scholar]
- Lien, Y.; Leng, X.; Mayes, K.; Chiu, J.-H. Reading order independent grouping proof for RFID tags. In Proceedings of the Intelligence and Security Informatics, Taipei, China, 17–20 June 2008; pp. 128–136. [Google Scholar]
- Piramuthu, S. On existence proofs for multiple RFID tags. In Proceedings of the 2006 ACS/IEEE Pervasive Services, Lyon, France, 26–29 June 2006; pp. 317–320. [Google Scholar]
- Li, N.; Mu, Y.; Susilo, W.; Varadharajan, V. Anonymous yoking-group proofs. In Proceedings of the Proceedings of the 10th ACM Symposium on Information, Computer and Communications Security, Singapore, 14–17 April 2015; pp. 615–620. [Google Scholar]
- Ma, C.; Lin, J.; Wang, Y.; Shang, M. Offline RFID grouping proofs with trusted timestamps. In Proceedings of the 2012 IEEE 11th International Conference on Trust, Security and Privacy in Computing and Communications, Liverpool, UK, 25–27 June 2012; pp. 674–681. [Google Scholar]
- Cho, J.S.; Yeo, S.S.; Hwang, S.; Rhee, S.Y.; Kim, S.K. Enhanced Yoking Proof Protocols for RFID Tags and Tag Groups. In Proceedings of the Advanced Information Networking and Applications—Workshops, Okinawa, Japan, 25–28 March 2008; pp. 1591–1596. [Google Scholar]
- Kang, H.-Y. Analysis and Improvement of ECC-based Grouping-proof Protocol for RFID. Int. J. Control Autom. 2016, 9, 343–352. [Google Scholar]
- Castiglione, A.; de Santis, A.; Masucci, B.; Palmieri, F.; Castiglione, A.; Li, J.; Huang, X. Hierarchical and Shared Access Control. IEEE Trans. Inf. Forensics Secur. 2016, 11, 850–865. [Google Scholar] [CrossRef]
- Lo, N.-W.; Yeh, K.-H. Anonymous coexistence proofs for RFID tags. J. Inf. Sci. Eng. 2010, 26, 1213–1230. [Google Scholar] [CrossRef]
- Burmester, M.; De Medeiros, B.; Motta, R. Provably secure grouping-proofs for RFID tags. In International Conference on Smart Card Research and Advanced Applications; Springer: Berlin/Heidelberg, Germay, 2008; pp. 176–190. ISBN 978-3-540-85892-8. [Google Scholar]
- Canetti, R. Universally composable security: A new paradigm for cryptographic protocols. In Proceedings of the 42nd IEEE Symposium on Foundations of Computer Science, Las Vegas, NV, USA, 14–17 October 2001; pp. 136–145. [Google Scholar]
- Burmester, M.; Munilla, J. An Anonymous RFID Grouping-Proof with Missing Tag Identification. In Proceedings of the 10th IEEE International Conference on Radio-Frequency Identification, Orlando, FL, USA, 3–5 May 2016; pp. 3–5. [Google Scholar]
- Wolkerstorfer, J. Is elliptic-curve cryptography suitable to secure RFID tags. In Proceedings of the Handout of the Ecrypt Workshop on RFID and Lightweight Crypto, Graz, Austria, 14–15 July 2005. [Google Scholar]
- Batina, L.; Guajardo, J.; Kerins, T.; Mentens, N.; Tuyls, P.; Verbauwhede, I. An Elliptic Curve Processor Suitable For RFID-Tags. IACR Cryptol. ePrint Arch. 2006, 2006, 227. [Google Scholar]
- Lee, Y.K.; Batina, L.; Verbauwhede, I. Untraceable RFID authentication protocols: Revision of EC-RAC. In Proceedings of the RFID, 2009 IEEE International Conference, Orlando, FL, USA, 27–28 April 2009; pp. 178–185. [Google Scholar]
- Batina, L.; Lee, Y.K.; Seys, S. Extending ECC-based RFID authentication protocols to privacy-preserving multi-party grouping proofs. Pers. Ubiquitous Comput. 2012, 16, 323–335. [Google Scholar] [CrossRef]
- Lv, C.; Li, H.; Ma, J.; Niu, B.; Jiang, H. Security Analysis of a Privacy-preserving ECC-based Grouping-proof Protocol. J. Converg. Inf. Technol. 2011, 6, 113–119. [Google Scholar] [CrossRef]
- Menezes, A. Evaluation of Security Level of Cryptography: The Elliptic Curve Discrete Logarithm Problem (ECDLP); University of Waterloo: Waterloo, ON, Canada, 2001. [Google Scholar]
- Lin, Q.; Zhang, F. ECC-based grouping-proof RFID for inpatient medication safety. J. Med. Syst. 2012, 36, 3527–3531. [Google Scholar] [CrossRef] [PubMed]
- He, D.; Kumar, N.; Chilamkurti, N.; Lee, J.H. Lightweight ECC Based RFID Authentication Integrated with an ID Verifier Transfer Protocol. J. Med. Syst. 2014, 38, 116. [Google Scholar] [CrossRef] [PubMed]
| Notation | Description |
|---|---|
| P | Base point in the elliptic curve group |
| The private/public key of reader | |
| The private/public key of tag A and tag B | |
| The private/public key of verifier | |
| The x-coordinate of point T |
| Notation | Description |
|---|---|
| The random number generated by reader, tag A and tag B. | |
| P | The base point on the elliptic curve . |
| The public/private key of Group G. | |
| Temporary grouping-proof key of tag A and tag B. | |
| Secret key of tag A and tag B. | |
| Public key of tag A and tag B. | |
| The x-coordinate of point T. |
| Notation | Description |
|---|---|
| The random number generated by reader and . | |
| P | The base point on the elliptic curve . |
| The public/private Key of Group G. | |
| Temporary grouping-proof key of . | |
| Secret/Public key of . | |
| The x-coordinate of point T. |
| Anonymity | Location Privacy | DoP Attack | Tag Information Protect | Tag Impersonation | Reader Impersonation | Replay Attack | |
|---|---|---|---|---|---|---|---|
| Juels [1] | × | × | × | √ | × | × | × |
| Burmester [22] | √ | √ | × | √ | √ | × | √ |
| Burmester [24] | √ | √ | × | × | √ | √ | √ |
| Batina [28] | √ | √ | × | √ | × | × | × |
| Chao [29] | √ | √ | × | √ | × | × | √ |
| Lin [31] | √ | √ | × | √ | × | × | × |
| Kang [19] | √ | √ | × | √ | × | √ | √ |
| EAGP | √ | √ | √ | √ | √ | √ | √ |
| Send | Receive | Total Times | ||||
|---|---|---|---|---|---|---|
| Total Data (bit) | Transmission Times | Total Data (bit) | Transmission Times | |||
| Kang’s | tag A | 640 | 2 | 1120 | 2 | 8 |
| tag B | 640 | 2 | 1280 | 2 | ||
| Reader | 2400 | 4 | 1280 | 4 | ||
| EAGP | tag A | 640 | 2 | 1280 | 2 | 6 |
| tag B | 640 | 1 | 1120 | 1 | ||
| Reader | 2240 | 3 | 1280 | 3 | ||
| EAGP | Tag | 640 | 2 | 1280 | 2 | |
| Tag | 640 | 1 | 1120 | 1 | ||
| Tag | 640 | 1 | 1120 | 1 | ||
| Reader | 640n | |||||
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhou, Z.; Liu, P.; Liu, Q.; Wang, G. An Anonymous Offline RFID Grouping-Proof Protocol. Future Internet 2018, 10, 2. https://doi.org/10.3390/fi10010002
Zhou Z, Liu P, Liu Q, Wang G. An Anonymous Offline RFID Grouping-Proof Protocol. Future Internet. 2018; 10(1):2. https://doi.org/10.3390/fi10010002
Chicago/Turabian StyleZhou, Zhibin, Pin Liu, Qin Liu, and Guojun Wang. 2018. "An Anonymous Offline RFID Grouping-Proof Protocol" Future Internet 10, no. 1: 2. https://doi.org/10.3390/fi10010002





