A Survey on Security in Mobile Peer-to-Peer Architectures—Overlay-Based vs. Underlay-Based Approaches
Abstract
:1. Introduction
2. Foundations of Peer-to-Peer
2.1. Introduction
2.2. Architectures
2.2.1. Ring
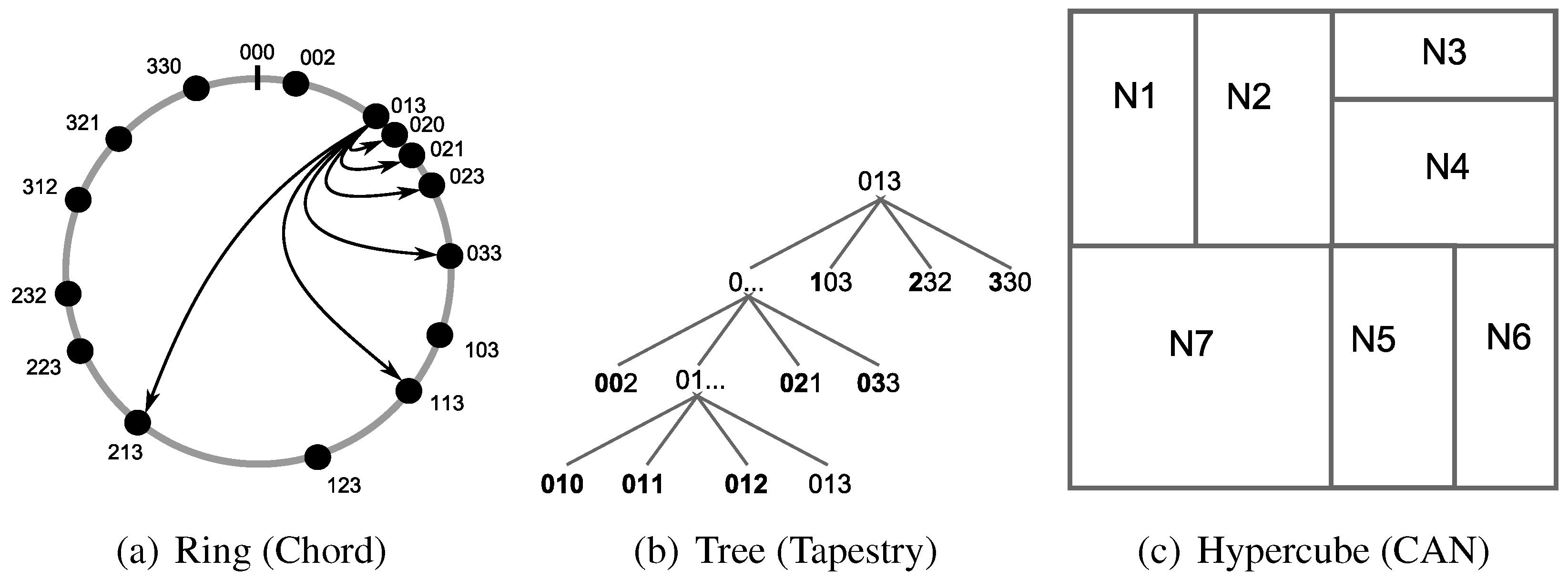
2.2.2. Tree
2.2.3. Hypercube
2.2.4. Hybrid
2.3. Challenges

3. Foundations of MANETs
3.1. Introduction
3.2. Architectures
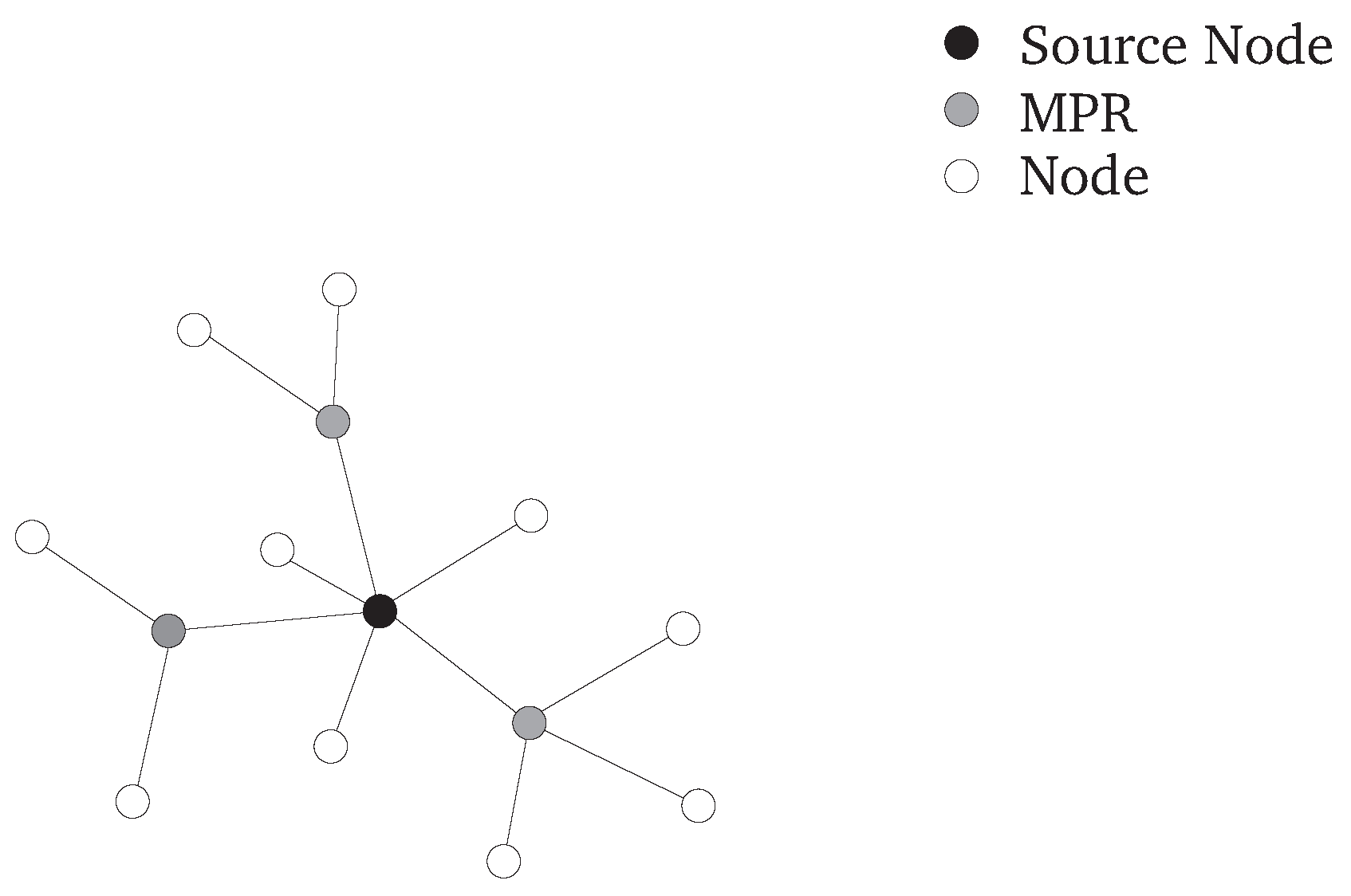

3.3. Challenges
4. Mobile Peer-to-Peer Architectures
4.1. Introduction
4.2. Architecture
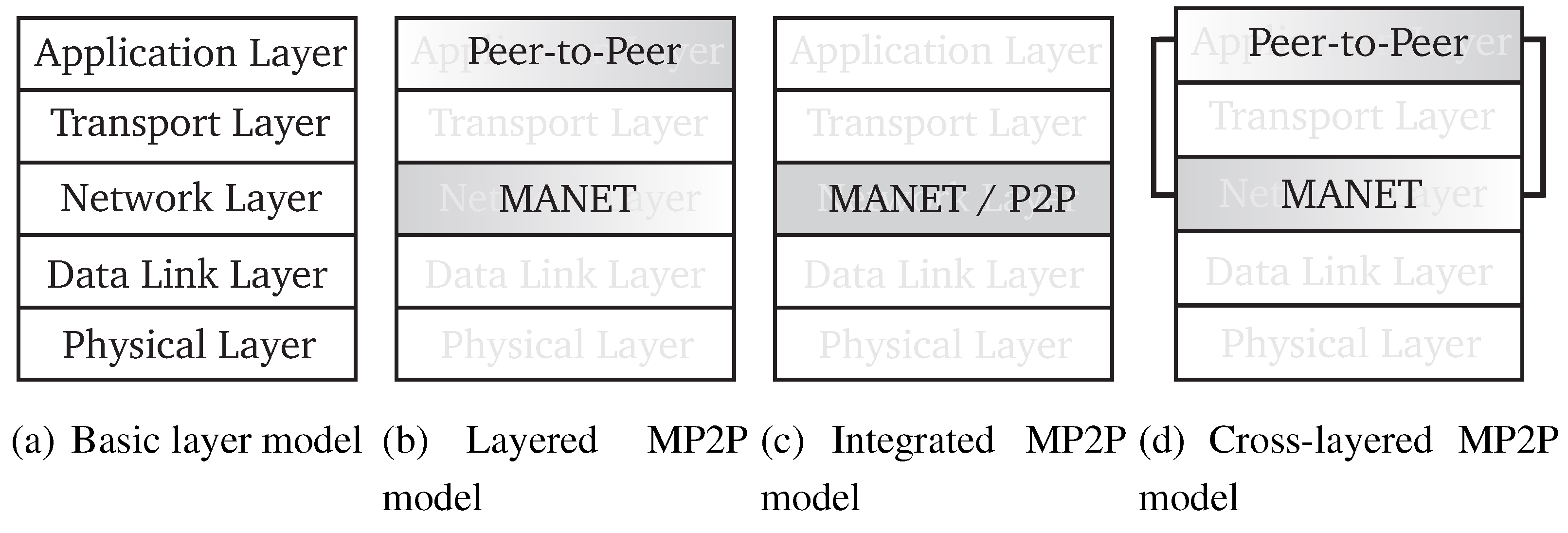
4.2.1. Layered
4.2.2. Integrated
4.2.3. Cross Layered
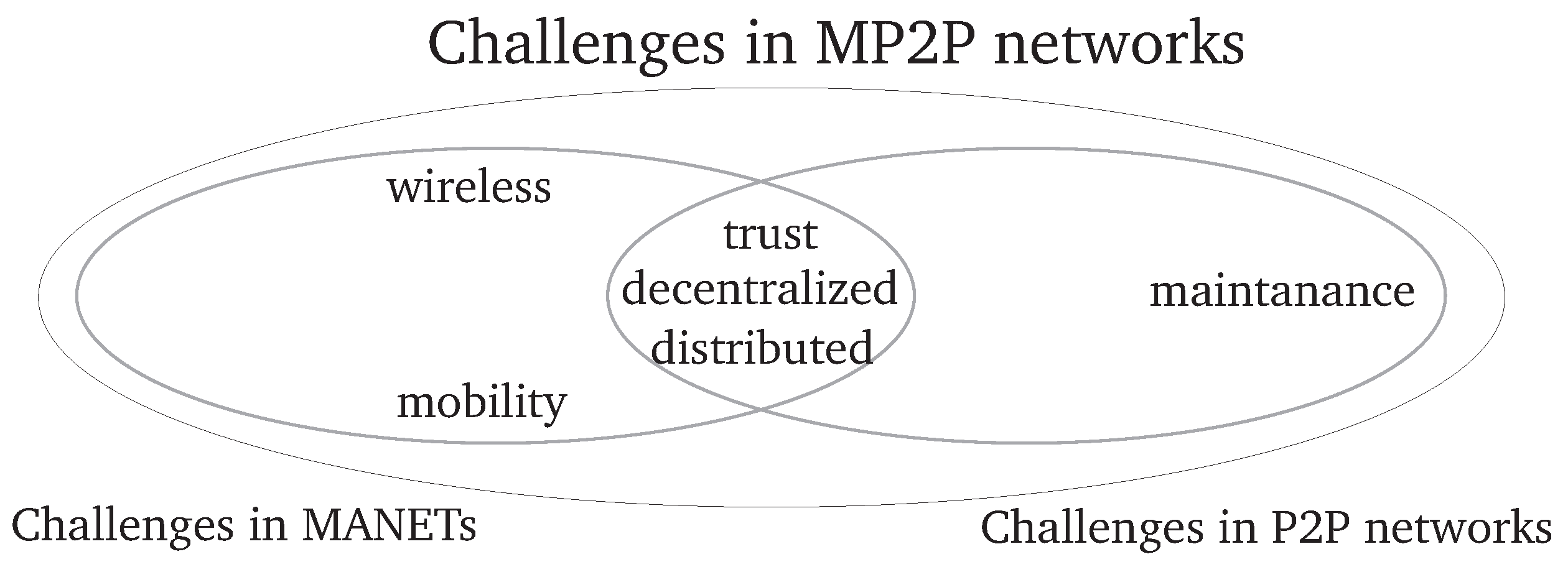
4.3. Challenges
5. Attacks and Countermeasures
5.1. Attacking P2P
5.1.1. Attacks on the P2P Routing Algorithm
5.1.2. Attacks on the P2P Routing Tables
5.1.3. Sybil Attacks on P2P Networks
5.2. P2P Countermeasures
5.2.1. Countermeasures for P2P Routing Attacks
5.2.2. Countermeasures for Routing Table Manipulation
5.2.3. Countermeasures for Sybil Attacks
5.3. Attacking MANETs
5.3.1. Malicious Behavior during Route Discovery and Maintenance
5.3.2. Malicious Behavior during Data Transmission
5.3.3. Sybil Attacks on MANETs
5.4. MANET Countermeasures
5.4.1. Countermeasures for Attacks during Routing and Data Transmission Phase
5.4.2. Countermeasures for Sybil Attacks
5.5. Attacking MP2P
5.6. Countermeasures in MP2P
6. Future Work and Conclusion
6.1. Future Work: A Cross Layer Approach to Increase the Robustness of a MP2P System

6.1.2. Open Problems
6.2. Conclusion
References
- Steinmetz, R.; Wehrle, K.; Götz, S.; Schollmeier, R.; Rieche, S.; Eberspächer, J.; Heckmann, O.; Darlagiannis, V.; Mauthe, A.; Koppen, C. Peer-to-Peer Systems and Applications; Springer: Berlin, Germany, 2005. [Google Scholar]
- Clarke, I.; Sandberg, O.; Wiley, B.; Hong, T. Freenet: A distributed anonymous information storage and retrieval system. In Proceedings of the ICSI Workshop on Design Issues in Anonymity and Unobservability, Berkeley, CA, USA, 25–26 July 2000.
- Kirk, P. Gnutella—A Protocol for a Revolution. 2010. Available online: http://rfc-gnutella.sourceforge.net/ (accessed on 29 September 2010).
- Kazaa. Download KaZaA. 2010. Available online: www.kazaa.com/ (accessed on 29 September 2010).
- Kanchanasut, K.; Tunpan, A.; Awal, M.A.; Das, D.K.; Wongsaardsakul, T.; Tsuchimoto, Y. A Multimedia Communication System for Collaborative Emergency Response Operation in Disaster-affected Areas; TR_2007-1; Technical Report, Internet Education and Research Laboratory (intERLab), Asian Institute of Technology (AIT): Bangkok, Thailand, 2007. [Google Scholar]
- Industrieanlagen-Betriebsgesellschaft mbH. IABG–InfoCom–HiMoNN—An efficient and highly mobile Ad-hoc Network Node. 2010. Available online: www.iabg.de/infokom/fachthemen/himonn_en.php (accessed on 29 September 2010).
- One Laptop per Child (OLPC), A Low-cost, Connected Laptop for the World’s Children’s Education. 2010. Available online: http://laptop.org/en/ (accessed on 29 September 2010).
- CAR 2 CAR Communication Consortium. Mission & Objective. 2010. Available online: www.car-to-car.org/ (accessed on 29 September 2010).
- Clausen, T.; Jacquet, P. Optimized Link State Routing Protocol (OLSR). RFC 2003, RFC 3626. [Google Scholar]
- Perkins, C.; Belding-Royer, E.; Das, S. Ad hoc On-Demand Distance Vector (AODV) Routing. RFC 2003, RFC 3561. [Google Scholar]
- Haas, Z. A new routing protocol for the reconfigurable wireless networks. In Proceedings 6th International Conference on Universal Personal Communications, San Diego, CA, USA, 12–16 October 1997.
- MacQuire, A.; Brampton, A.; Rai, I.A.; Mathy, L. Performance Analysis of Stealth DHT with Mobile Nodes. In Proceedings of the 4th Annual IEEE International Conference on Pervasive Computing and Communications Workshops, Pisa, Italy, 13–17 March 2006.
- Castro, M.; Villanueva, E.; Ruiz, I.; Sargento, S.; Kassler, A.J. Performance Evaluation of Structured P2P over Wireless Multi-hop Networks. In Proceedings of the 2nd International Conference on Sensor Technologies and Applications, Cap Esterel, France, 25–31 August 2008.
- Gopalan, A.; Znati, T. PeerNet: A peer-to-peer framework for service and application deployment in MANETs. In Proceedings of the 1st International Symposium on Wireless Pervasive Computing, Phuket, Thailand, 16–18 January 2006.
- Millar, G.P.; Ramrekha, T.A.; Politis, C. A Peer-to-Peer Overlay Approach for Emergency Mobile Ad Hoc Network Based Multimedia Communications. In Proceedings of the 5th International ICST Mobile Multimedia Communications Conference, London, UK, 7–9 September 2009.
- Fuhrmann, T. Performance of scalable source routing in hybrid MANETs. In Proceedings of the 4th Annual Conference on Wireless on Demand Network Systems and Services, Obergurgl, Austria, 24–26 January 2007.
- Caesar, M.; Castro, M.; Nightingale, E.B.; O’Shea, G.; Rowstron, A. Virtual ring routing: Network routing inspired by DHTs. ACM SIGCOMM Comput. Commun. Rev. 2006, 36, 351–362. [Google Scholar] [CrossRef]
- Pucha, H.; Das, S.M.; Hu, Y. Ekta: An Efficient DHT Substrate for Distributed Applications in Mobile Ad Hoc Networks. In Proceedings of the 6th IEEE Workshop on Mobile Computing Systems and Applications, English Lake District, UK, 2–3 December 2004.
- Hu, Y.C.; Das, S.M.; Pucha, H. Exploiting the Synergy between Peer-to-Peer and Mobile Ad Hoc Networks. In Proceedings of the 9th conference on Hot Topics in Operating Systems, Lihue, HI, USA, 18–21 May 2003.
- Delmastro, F. From Pastry to CrossROAD: CROSS-Layer Ring Overlay for Ad Hoc Networks. In Proceedings of the 3rd IEEE International Conference on Pervasive Computing and Communications Workshops, Koloa, HI, USA, 8–12 March 2005.
- Zahn, T.; Schiller, J. MADPastry: A DHT Substrate for Practicably Sized MANETs. In Proceedings of the 5th IEEE Workshop on Applications and Services in Wireless Networks, Paris, France, 29 June–1 July 2005.
- Sit, E.; Morris, R. Security Considerations for Peer-to-Peer Distributed Hash Tables. In Proceedings of the 1st International Workshop on Peer-to-Peer Systems, Cambridge, MA, USA, 7–8 March 2002.
- Castro, M.; Druschel, P.; Ganesh, A.; Rowstron, A.; Wallach, D. Secure routing for structured peer-to-peer overlay networks. In Proceedings of the 5th Symposium on Operating Systems Design and Implementation, Boston, MA, USA, 9–11 December 2002.
- Srivatsa, M.; Liu, L. Vulnerabilities and Security Threats in Structured Overlay Networks: A Quantitative Analysis. In Proceedings of the 20th Annual Computer Security Applications Conference, Tucson, AZ, USA, 6–10 December 2004.
- Artigas, M.S.; López, P.G.; Gómez-Skarmeta, A.F. Bypass: Providing secure DHT routing through bypassing malicious peers. In Proceedings of the IEEE Symposium on Computers and Communications, Marrakech, Morocco, 6–9 July 2008.
- Hildrum, K.; Kubiatowicz, J. Asymptotically Efficient Approaches to Fault-Tolerance in Peer-to-Peer Networks. In Proceedings of the 17th international Symposium on Distributed Computing, Sorrento, Italy, 1–3 October 2003.
- Harvesf, C.; Blough, D.M. The Effect of Replica Placement on Routing Robustness in Distributed Hash Tables. In Proceedings of the 6th IEEE International Conference on Peer-to-Peer Computing, Cambridge, UK, 6–8 September 2006.
- Douceur, J. The Sybil Attack. In Proceedings of the 1st International Workshop on Peer-to-Peer Systems, Cambridge, MA, USA, 7–8 March 2002.
- Borisov, N. Computational Puzzles as Sybil Defenses. In Proceedings of the 6th IEEE International Conference on Peer-to-Peer Computing, Cambridge, UK, 6–8 September 2006.
- Yu, H.; Kaminsky, M.; Gibbons, P.B.; Flaxman, A. SybilGuard: Defending Against Sybil Attacks via Social Networks. In Proceedings of the conference on Applications, technologies, architectures, and protocols for computer communications, Pisa, Italy, 11–15 September 2006.
- Danezis, G.; Lesniewski-Laas, C.; Kaashoek, M.F.; Anderson, R.J. Sybil-Resistant DHT Routing. In Proceedings on the 10th European Symposium on Research in Computer Security, Milan, Italy, 12–14 September 2005.
- Cheng, A.; Friedman, E. Sybilproof Reputation Mechanisms. In Proceedings of the ACM SIGCOMM workshop on Economics of peer-to-peer systems, Philadelphia, PA, USA, 22 August 2005.
- Ji, W.; Yang, S.; Chen, B. A Group-based Trust Metric for P2P Networks: Protection against Sybil Attack and Collusion. In Proceedings of the International Conference on Computer Science and Software Engineering, Wuhan, China, 12–14 December 2008.
- Ning, P.; Sun, K. How to misuse AODV: A case study of insider attacks against mobile ad-hoc routing protocols. Ad Hoc Netw. 2005, 3, 795–819. [Google Scholar] [CrossRef]
- Sanzgiri, K.; Levine, B.N.; Shields, C.; Dahill, B.; Belding-Royer, E.M. A Secure Routing Protocol for Ad Hoc Networks. In Proceedings of the 10th IEEE International Conference on Network Protocols, Paris, France, 12–15 November 2002.
- Hu, Y.C.; Johnson, D.B.; Perrig, A. SEAD: Secure efficient distance vector routing for mobile wireless ad hoc networks. In Proceedings of the 4th IEEE Workshop on Mobile Computing Systems and Applications, Callicoon, NY, USA, 20–21 June 2002.
- Papadimitratos, P.; Haas, Z.J. Secure Routing for Mobile Ad hoc Networks. In Proceedings of the SCS Communication Networks and Distributed Systems Modeling and Simulation Conference, San Antonio, TX, USA, 27–31 January 2002.
- Zapata, M.G.; Asokan, N. Securing Ad Hoc Routing Protocols. In Proceedings of the 1st ACM workshop on Wireless Security, Atlanta, GA, USA, 28 September 2002.
- Yi, S.; Naldurg, P.; Kravets, R. Security-Aware Ad hoc Routing for Wireless Networks. In Proceedings of the 2nd ACM International Symposium on Mobile Ad Hoc Networking & Computing, Long Beach, CA, USA, 4–5 October 2001.
- Marti, S.; Giuli, T.J.; Lai, K.; Baker, M. Mitigating Routing Misbehavior in Mobile Ad Hoc Networks. In Proceedings of the 6th Annual International Conference on Mobile Computing and Networking, Boston, MA, USA, 6–11 August 2000.
- Kurosawa, S.; Nakayama, H.; Kato, N.; Jamalipour, A.; Nemoto, Y. Detecting Blackhole Attack on AODV-based Mobile Ad Hoc Networks by Dynamic Learning Method. Int. J. Netw. Secur. 2007, 5, 338–346. [Google Scholar]
- Buchegger, S.; Boudec, J.Y.L. Performance Analysis of the CONFIDANT Protocol (Cooperation Of Nodes: Fairness In Dynamic Adhoc NeTworks). In Proceedings of the 3rd ACM International Symposium on Mobile Ad Hoc Networking & Computing, Lausanne, Switzerland, 9–11 June 2002.
- Bhalaji, N.; Shanmugam, A. Reliable Routing against Selective Packet Drop Attack in DSR based MANET. J. Softw. 2009, 4, 536–543. [Google Scholar] [CrossRef]
- Newsome, J.; Shi, E.; Song, D.; Perrig, A. The Sybil Attack in Sensor Networks: Analysis & Defenses. In Proceedings of the 3rd International Symposium on Information Processing in Sensor Networks, Berkeley, CA, USA, 26–27 April 2004.
- Piro, C.; Shields, C.; Levine, B.N. Detecting the Sybil Attack in Mobile Ad hoc Networks. In Proceedings of the 2nd International Conference on Security and Privacy in Communication Networks, Baltimore, MD, USA, 28 August–1 September 2006.
- Tangpong, A.; Kesidis, G.; Hsu, H.Y.; Hurson, A. Robust Sybil Detection for MANETs. In Proceedings of the Proceedings of 18th International Conference on Computer Communications and Networks, San Francisco, CA, USA, 2–6 August 2009.
- Čapkun, S.; Hubaux, J.P.; Buttyan, L. Mobility Helps Peer-to-Peer Security. IEEE Trans. Mob. Comput. 2006, 5, 43–51. [Google Scholar] [CrossRef]
- Kutzner, K.; Wallenta, C.; Fuhrmann, T. Securing the Scalable Source Routing Protocol. In Proceedings of the World Telecommunications Congress, Budapest, Hungary, 1–3 May 2006.
- Walkerdine, J.; Lock, S. Towards Secure Mobile P2P Systems. In Proceedings of the 2nd International Conference on Internet and Web Applications and Services, Le Mourne, Mauritius, 13–19 May 2007.
© 2010 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license ( http://creativecommons.org/licenses/by/3.0/).
Share and Cite
Gottron, C.; König, A.; Steinmetz, R. A Survey on Security in Mobile Peer-to-Peer Architectures—Overlay-Based vs. Underlay-Based Approaches. Future Internet 2010, 2, 505-532. https://doi.org/10.3390/fi2040505
Gottron C, König A, Steinmetz R. A Survey on Security in Mobile Peer-to-Peer Architectures—Overlay-Based vs. Underlay-Based Approaches. Future Internet. 2010; 2(4):505-532. https://doi.org/10.3390/fi2040505
Chicago/Turabian StyleGottron, Christian, André König, and Ralf Steinmetz. 2010. "A Survey on Security in Mobile Peer-to-Peer Architectures—Overlay-Based vs. Underlay-Based Approaches" Future Internet 2, no. 4: 505-532. https://doi.org/10.3390/fi2040505



