Towards Incidence Management in 5G Based on Situational Awareness
Abstract
:1. Introduction
2. Background
2.1. Information Security Incidence Management
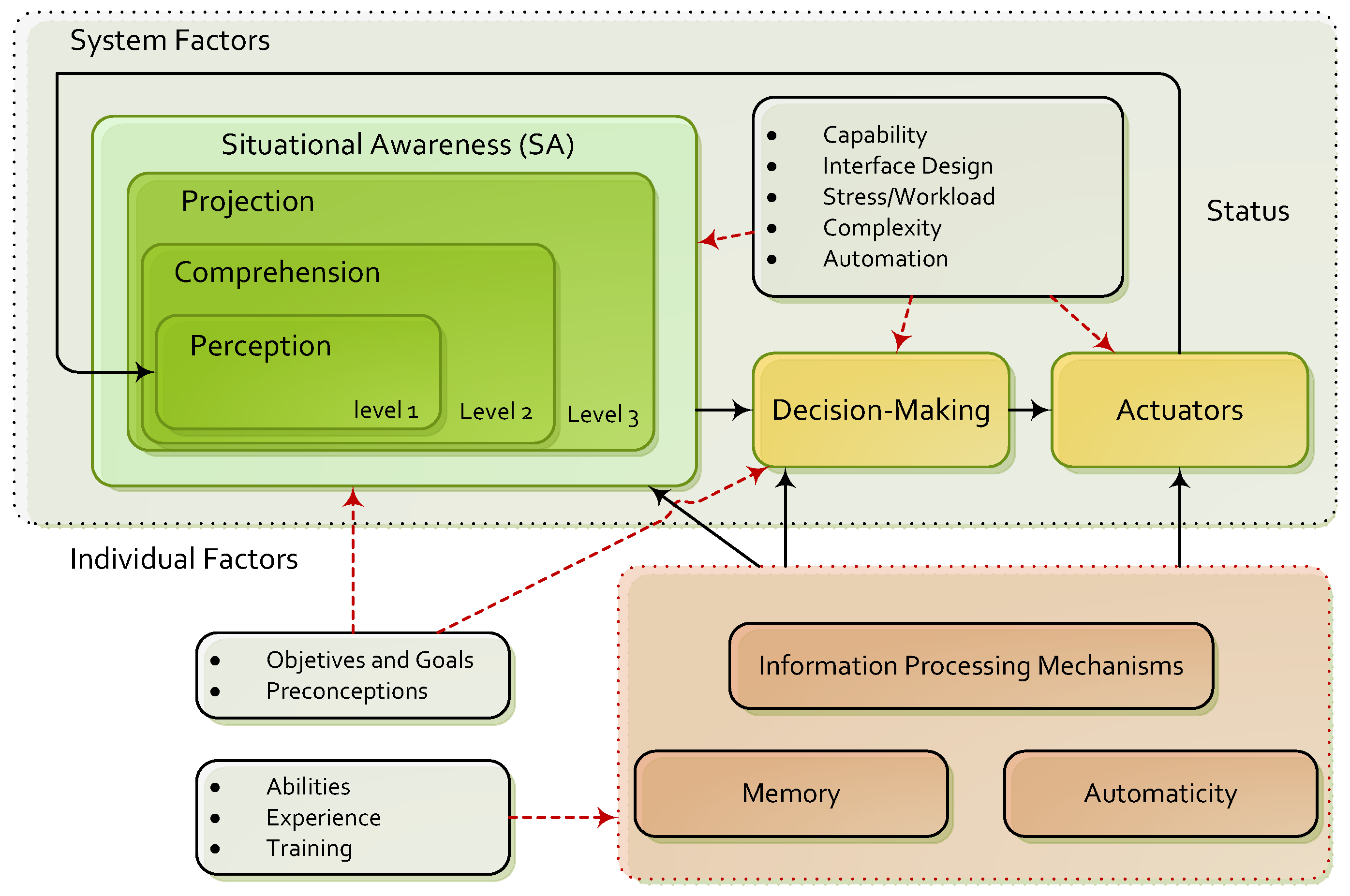
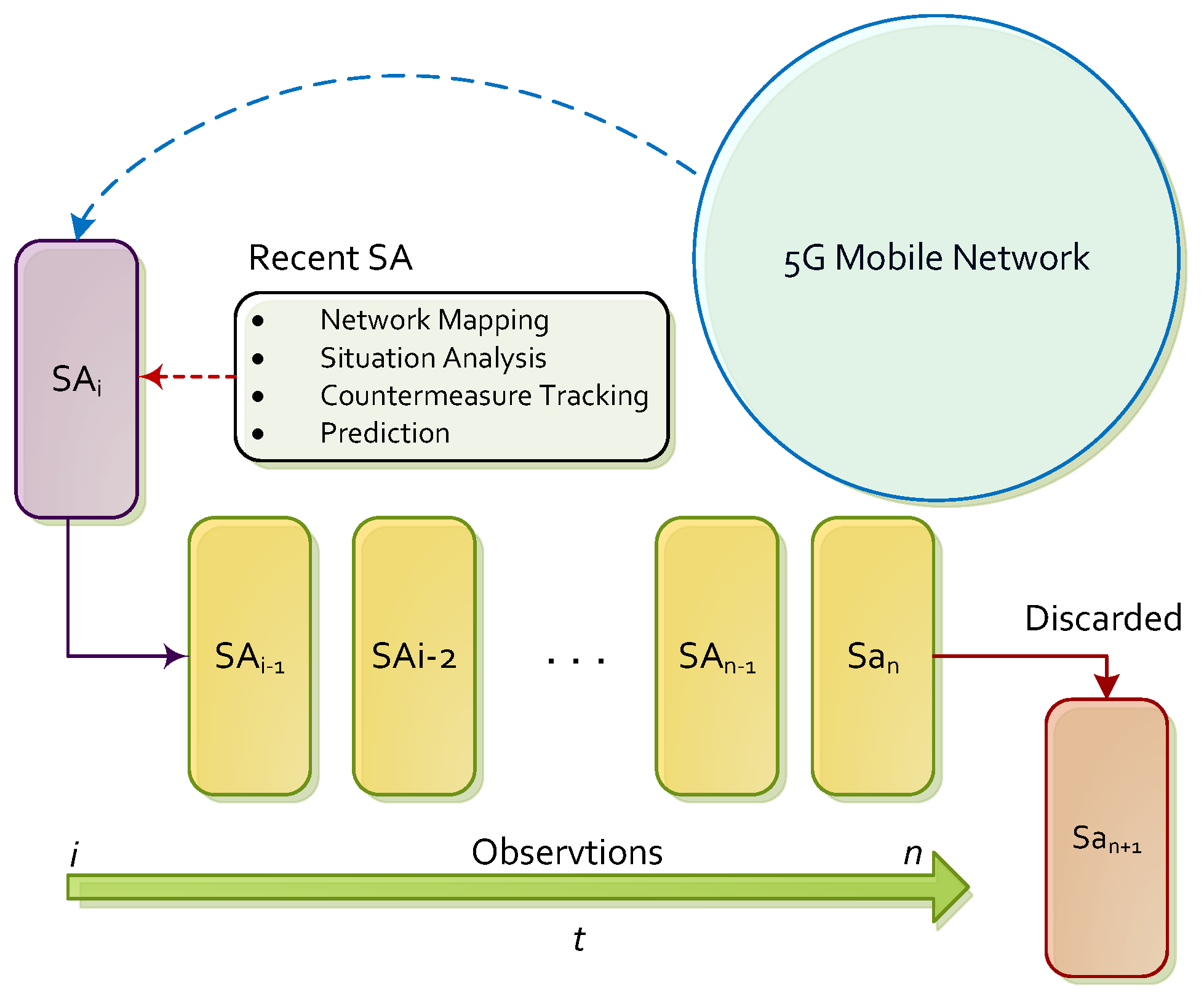
2.2. Situational Awareness and Information Security
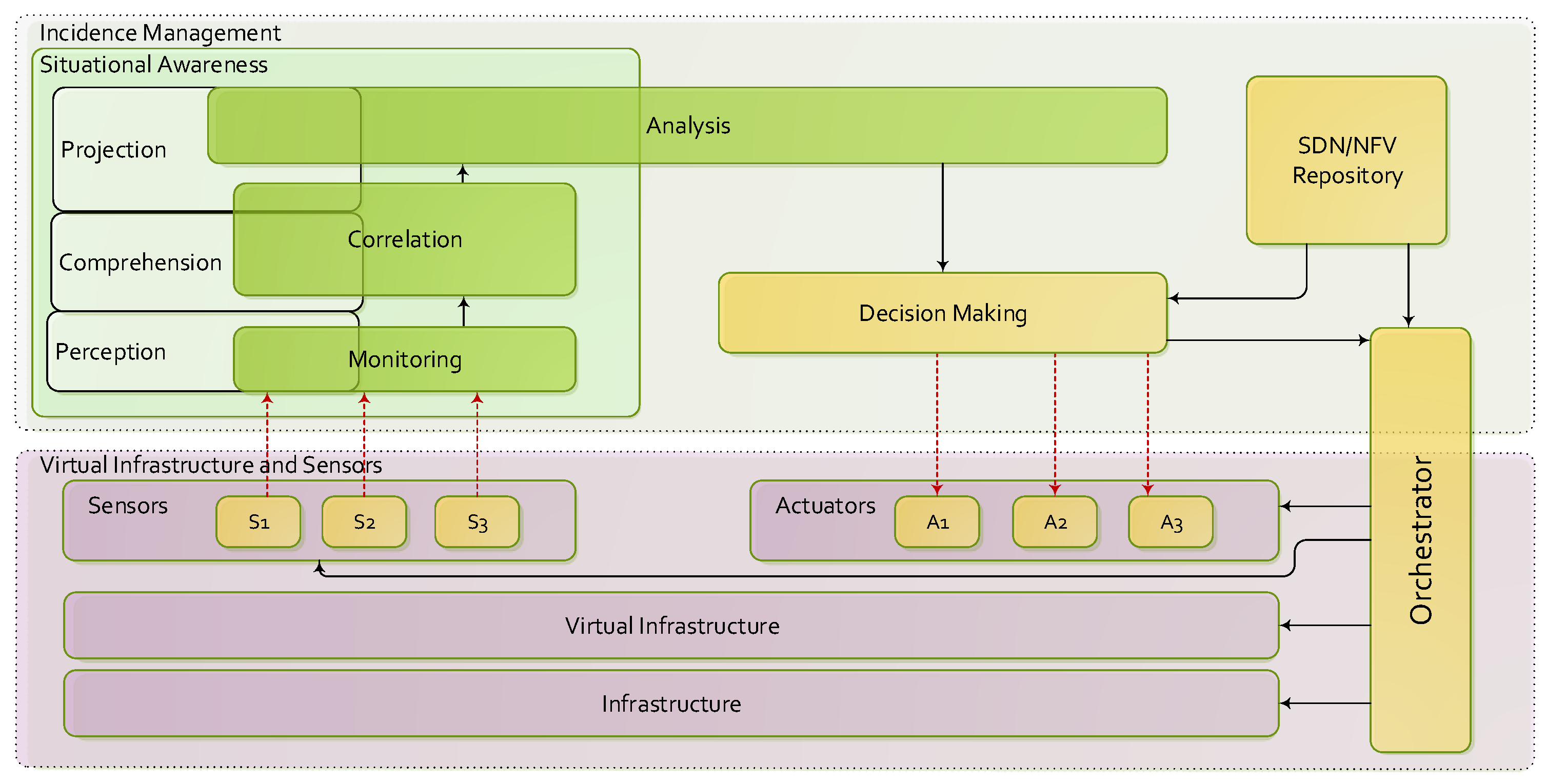
3. Incidence Management in 5G
4. Information Security Architecture for 5G
- The elements responsible for monitoring and executing mitigation actions (e.g., virtual functions) are compatible with the SDN/NFV paradigm. If the elements follow the traditional architectures, a compatibility layer is assumed. This additional layer can use the available configuration options to emulate a SDN/NFV enabled element.
- The communication between the different modules of the framework must be performed through secure channels.
- The information provided by the monitoring elements (low level metrics, alerts) are considered reliable.
- The Risk Analysis and the corresponding Situation Awareness procedures are strongly isolated from the data plane forwarding. In other words, the resources (network, storage and computing) used for the operation of the framework belong to administrative domain and, consequently, do not modify the capabilities of the 5G forwarding elements.
- The functional modules are extensible and can be implemented using distributed architectures in function of the available management resources and the size of the managed infrastructure.
4.1. Virtual Infrastructure and Sensors
4.2. Monitoring and Correlation
- Monitoring (Data Collection). The main objectives are the gathering and management of the information from all data sources, and facilitating their access to upper layers. Monitoring tasks would be able to actively poll different sources to collect real-time statistics, providing highly accurate and low overhead traffic measurement [41]. This module also controls the registration and access process of new sensors. The collected information is organized in efficient data structures, taking into account the large amount of data to be processed. In this regard, two scenarios were considered. In the first scenario, the sensor sends a report to the monitor when it detects relevant information (alerts, link failures, memory or CPU overload). In the second scenario, the monitor requests information (whenever necessary) to the sensors in order to facilitate the aggregation and analysis tasks (virtual topology, available links, among others).
- Correlation. It is responsible for the first abstraction level of information processing, in which, in order to have a global view of the network status, correlation and aggregation processes are executed. Information considered as redundant or non-sensitive is discarded. As an example, in case of multiple alerts received from each device belonging to the same affected area, a single alert is displayed with the affected topology. Due to the dynamism offered by virtual environments, in contrast to the rigidity of the physical elements, network topology is expressed as an extended or increased graph (), which models virtual nodes () and links () located in the physical infrastructure [42,43]. Likewise, as a result of correlation and aggregation operations, the received low-level metrics can be expressed or translated into high-level metrics, also known as Health of Network (HoN). For example, transmission data rate (Mbps), delay (ms) and jitter (ms) of data in streaming video, collected by the sensors at different points in the network, can be expressed as an overall perception of quality of service QoS/QoE, quantified by the measurement of the Mean Opinion Score (MOS).
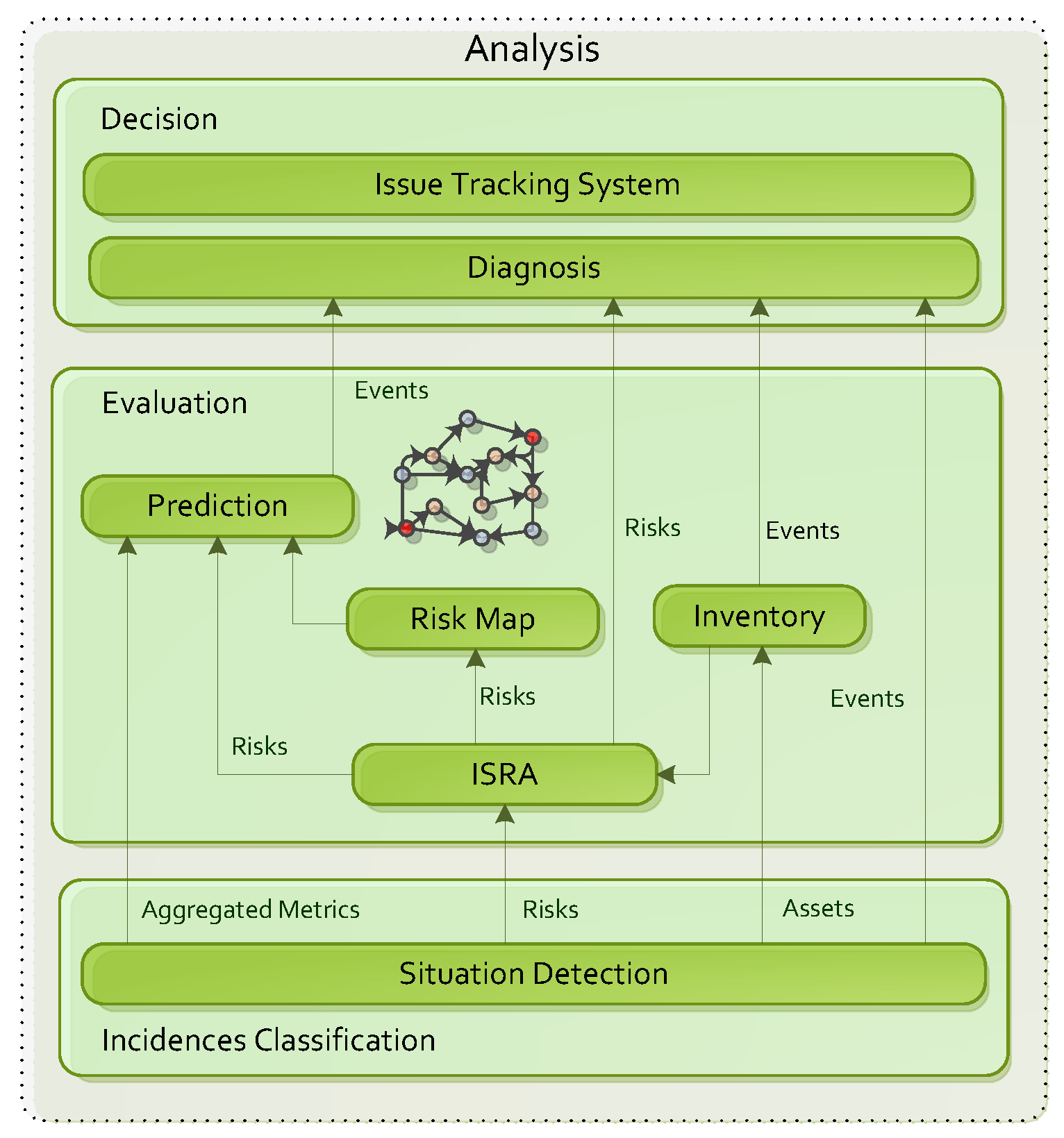
5. Analysis and Decision-Making
5.1. Analysis
- Discovery events—include all situations related to incorporation of new assets to the system. For example, this occurs when incorporating new nodes into the network, establishment of new connections between previously existing resources, or deployment of new virtualization layers. Each time a discovery event is communicated, the asset inventory is updated.
- Removal events. Unlike discovery events, removal events indicate situations related to the elimination of 5G resources. These are the cases of deletion of assets, removal of connections between nodes, or elimination of virtualization resources. As in discovery events, each time a removal event is communicated, the asset inventory is upgraded.
- Modification events. They include every situation related with the modification (not removal) of an existing resource. For example, this occurs when varying the location of the asset (i.e., changes to IP address, MAC address, etc.), and changes between communication protocols or software updates. As in the previous cases, modification events involve changes to the asset inventory.
- Notification events. They report specific situations in the network that are not related to changes in the assets inventory, such as periodic reviews of the bandwidth status, presence of unused resources or requests for special configurations.
5.1.1. Detection
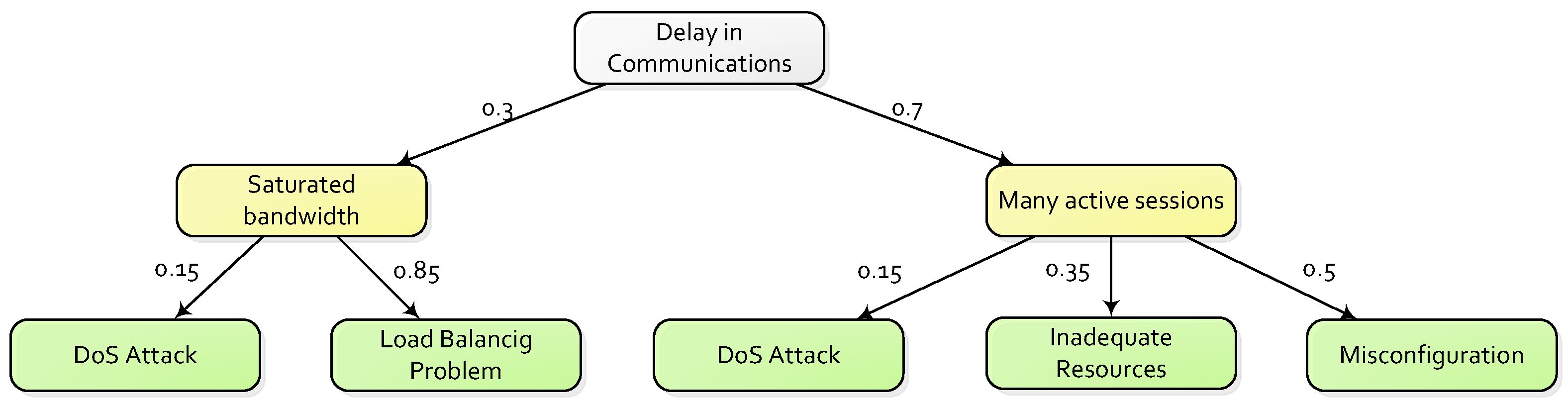
5.1.2. Risk Assessment
5.1.3. Asset Inventory
5.1.4. Risk Map
5.1.5. Prediction
5.1.6. Diagnosis
5.1.7. Countermeasure Tracking
5.2. Decision-Making and Actuators
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Andrews, J.G.; Buzzi, S.; Choi, W.; Hanly, S.V.; Lozano, A.; Soong, A.C.K.; Zhang, J.C. What Will 5G Be? IEEE J. Sel. Areas Commun. 2014, 32, 1065–1082. [Google Scholar] [CrossRef]
- Agyapong, P.K.; Iwamura, M.; Staehle, D.; Kiess, W.; Benjebbour, A. Design Considerations for a 5G Network Architecture. IEEE Commun. Mag. 2014, 52, 65–75. [Google Scholar] [CrossRef]
- NGMN Alliance. NMGN 5G White Paper. 2015. Available online: https://www.ngmn.org/uploads/media/NGMN_5G_White_Paper_V1_0.pdf (accessed on 19 December 2016).
- Panwar, N.; Sharma, S.; Singh, A.K. A Survey on 5G: The Next Generation of Mobile Communication. Phys. Commun. 2016, 18, 64–84. [Google Scholar] [CrossRef]
- Boccardi, F.; Heath, R.W.; Lozano, A.; Marzetta, T.; Popovski, P. Five Disruptive Technology Directions for 5G. IEEE Commun. Mag. 2014, 52, 74–80. [Google Scholar] [CrossRef]
- Imran, A.; Zoha, A. Challenges in 5G: How to Empower SON with Big Data for Enabling 5G. IEEE Netw. 2014, 28, 27–33. [Google Scholar] [CrossRef]
- International Organization for Standardization and the International Electrotechnical Commission. ISO/IEC 27002: Information Technology, Security Techniques, Code of Practice for Information Security Management. 2005. Available online: http://www.iso.org/iso/catalogue_detail?csnumber=54533 (accessed on 19 December 2016).
- National Institute of Standards and Technology. NIST-SP800 Series Special Publications on Computer Security. Available online: http://csrc.nist.gov/publications/PubsSPs.html#SP800 (accessed on 19 December 2016).
- Forum of Incident Response and Security Teams. CVSS: Common Vulnerability Scoring System. Available online: https://www.first.org/cvss/specification-document (accessed on 19 December 2016).
- MAGERIT: Risk Analysis and Management Methodology for Information Systems. Available online: http://administracionelectronica.gob.es/pae_Home/pae_Documentacion/pae_Metodolog/ (accessed on 19 December 2016).
- Parvizi, R.; Oghbaei, F.; Khayami, S.R. Using COBIT and ITIL Frameworks to Establish the Alignment of Business and IT Organizations as One of the Critical Success Factors in ERP Implementation. In Proceedings of the 5th IEEE Conference on Information and Knowledge Technology (IKT), Shiraz, Iran, 28–30 May 2013; pp. 274–278.
- Webb, J.; Ahmad, A.; Maynard, S.B.; Shanks, G.; Popovski, P. A Situation Awareness Model for Information Security Risk Management. Comput. Secur. 2014, 44, 1–15. [Google Scholar] [CrossRef]
- Endsley, N.R. Design and Evaluation for Situation Awareness Enhancement. In Proceedings of the Human Factors and Ergonomics Society Annual Meeting, Anaheim, CA, USA, 24–28 October 1988; Volume 32, pp. 97–101.
- Leau, Y.B.; Ahmad, A.; Manickam, S. Network Security Situation Prediction: A Review and Discussion. In Proceedings of the 4th International Conference on Soft Computing, Intelligent Systems, and Information Technology (ICSIIT), Bali, Indonesia, 11–14 March 2015; pp. 424–435.
- Marquezan, C.C.; Mahmood, K.; Zafeiropoulos, A.; Krishna, R.; Huang, X.; An, X.; Corujo, D.; Leitão, F.; Rosas, M.L.; Einsiedler, H. Context Awareness in Next Generation of Mobile Core Networks. arXiv, 2016; arXiv:1611.05353. [Google Scholar]
- Belmonte Martin, A.; Marinos, L.; Rekleitis, E.; Spanoudakis, G.; Petroulakis, N.E. Threat Landscape and Good Practice Guide for Software Defined Networks/5G; European Union Agency for Network and Information Security (ENISA): Heraklion, Greece, 2015. Available online: http://openaccess.city.ac.uk/15504/7/SDN%20Threat%20Landscape.pdf (accessed on 19 December 2016).
- 5G-Ensure Project. Enablers for Network and System Security and Resilience. Project Reference: 671562. Funded under: H2020-ICT-2014-2. Available online: http://www.5gensure.eu/ (accessed on 19 December 2016).
- 5G Ensure. Deliverable D 2.3, Risk Assessment, Mitigation and Requirements (Draft). August 2016. Available online: http://www.5gensure.eu/deliverables (accessed on 19 December 2016).
- Aven, T. Risk Assessment and Risk Management: Review of Recent Advances on their Foundation. Eur. J. Oper. Res. 2016, 256, 1–13. [Google Scholar] [CrossRef]
- Shameli-Sendi, A.; Aghababaei-Barzegar, R.; Cheriet, M. Taxonomy of Information Security Risk Assessment (ISRA). Comput. Secur. 2016, 57, 14–30. [Google Scholar] [CrossRef]
- Hansson, S.O.; Aven, T. Is Risk Analysis Scientific? Risk Anal. 2014, 34, 1173–1183. [Google Scholar] [CrossRef] [PubMed]
- Doty, P. US Homeland Security and Risk Assessment. Gov. Inf. Q. 2015, 32, 342–352. [Google Scholar] [CrossRef]
- Yang, M.; Khan, F.; Lye, L.; Amyotte, P. Risk Assessment of Rare Events. Process Saf. Environ. Prot. 2015, 98, 102–108. [Google Scholar]
- Ab Rahman, N.H.; Choo, K.K.R. A Survey of Information Security Incident Handling in the Cloud. Comput. Secur. 2015, 49, 45–69. [Google Scholar]
- Knowles, W.; Prince, D.; Hutchison, D.; Disso, J.; Ferdinand, P.J.; Jones, K. A Survey of Cyber Security Management in Industrial Control Systems. Int. J. Crit. Infrastruct. Prot. 2015, 9, 52–80. [Google Scholar] [CrossRef]
- Ni, S.; Zhuang, Y.; Gu, J.; Huo, Y. A Formal Model and Risk Assessment Method for Security-critical Real-time Embedded Systems. Comput. Secur. 2016, 58, 199–215. [Google Scholar]
- Cherdantseva, Y.; Burnap, P.; Blyth, A.; Eden, P.; Jones, K.; Soulsby, H.; Stoddart, K. A Review of Cyber Security Risk Assessment Methods for SCADA Systems. Comput. Secur. 2016, 56, 1–27. [Google Scholar]
- Quick, D.; Martini, B.; Choo, K.K.R. Cloud Storage Forensics. In Syngress; Elsevier: Amsterdam, The Netherlands, 2013; pp. 1–208. ISBN 978-0-12-419970-5. Available online: http://www.sciencedirect.com/science/book/9780124199705 (accessed on 19 December 2016).
- Ab Rahman, N.H.; Glisson, W.B.; Yang, Y.; Choo, K.K.R. Forensic-by-Design Framework for Cyber-Physical Cloud Systems. IEEE Cloud Comput. 2016, 3, 50–59. [Google Scholar] [CrossRef]
- Ab Rahman, N.H.; Cahyani, N.D.W.; Choo, K.K.R. Cloud incident handling and Forensic-by-Design: Cloud Storage as a Case Study. Concurr. Comput. Pract. Exp. 2016, 1–16. [Google Scholar] [CrossRef]
- Endsley, M.R.; Selcon, S.J.; Hardiman, T.D.; Croft, D.G. A Comparative Analysis of SAGAT and SART for Evaluations of Situation Awareness. In Proceedings of the Human Factors and Ergonomics Society Annual Meeting, Chicago, IL, USA, 5–9 October 1998; Volume 1, pp. 82–86.
- Adam, E.C. Fighter Cockpits of the Future. In Proceedings of the 12th IEEE Digital Avionics Systems Conference (DASC), Fort Worth, TX, USA, 25–28 October 1993; pp. 318–323.
- Dahal, N.; Abuomar, O.; King, R.; Madani, V. Event Stream Processing for Improved Situational Awareness in the Smart Grid. Expert Syst. Appl. 2015, 42, 6853–6863. [Google Scholar]
- Naderpour, M.; Nazir, S.; Lu, J. The Role of Situation Awareness in Accidents of Large-scale Technological Systems. Process Saf. Environ. Prot. 2015, 97, 13–24. [Google Scholar]
- Moradi-Pari, E.; Tahmasbi-Sarvestani, A.; Fallah, Y.P. A Hybrid Systems Approach to Modeling Real-time Situation-Awareness Component of Networked Crash Avoidance Systems. IEEE Syst. J. 2016, 10, 169–178. [Google Scholar] [CrossRef]
- Seppänen, H.; Virrantaus, K. Shared Situational Awareness and Information Quality in Disaster Management. Saf. Sci. 2015, 77, 112–122. [Google Scholar] [CrossRef]
- Chatzimichailidou, M.K.; Stanton, N.A.; Dokas, I.M. The Concept of Risk Situation Awareness Provision: Towards a New Approach for Assessing the DSA about the Threats and Vulnerabilities of Complex Socio-technical Systems. Saf. Sci. 2015, 79, 126–138. [Google Scholar] [CrossRef]
- Franke, U.; Brynielsson, J. Cyber Situational Awareness—A Systematic Review of the Literature. Comput. Secur. 2014, 46, 18–31. [Google Scholar] [CrossRef]
- Schmittling, R.; Munns, A. Performing a Security Risk Assessment. ISACA J. 2010, 1, 10–18. [Google Scholar]
- Naderpour, M.; Lu, J.; Zhang, G. A Situation Risk Awareness Approach for Process Systems Safety. Saf. Sci. 2014, 64, 173–189. [Google Scholar] [CrossRef]
- Tahaei, H.; Salleh, R.; Khan, S.; Izard, R.; Choo, K.K.R.; Anuar, N.B. A multi-objective Software Defined Network Traffic Measurement. Measurement 2016, 95, 317–327. [Google Scholar] [CrossRef]
- Shanbhag, S.; Kandoor, A.R.; Wang, C.; Mettu, R.; Wolf, T. VHub: Single-stage Virtual Network Mapping Through Hub Location. Comput. Netw. 2015, 77, 169–180. [Google Scholar] [CrossRef]
- Chowdhury, N.M.K.; Rahman, M.R.; Boutaba, R. Virtual Network Embedding with Coordinated Node and Link Mapping. In Proceedings of the 28th IEEE Conference on Computer Communications (INFOCOM), Rio de Janeiro, Brasil, 19–25 April 2009; pp. 783–791.
- Awan, M.S.K.; Burnap, P.; Rana, O. Identifying Cyber Risk Hotspots: A Framework for Measuring Temporal Variance in Computer Network Risk. Comput. Secur. 2016, 57, 31–46. [Google Scholar] [CrossRef]
- Shin, J.; Son, H.; Ur, R.K.; Heo, G. Development of a Cyber Security Risk Model Using Bayesian Networks. Reliab. Eng. Syst. Saf. 2015, 134, 208–217. [Google Scholar] [CrossRef]
- International Organization for Standardization and the International Electrotechnical Commission. ISO/IEC 7498-2, Information Processing Systems—Open Systems Interconnection—Basic Reference Model Part 2: Security Architecture. Available online: http://www.iso.org/iso/catalogue_detail.htm?csnumber=14256 (accessed on 19 December 2016).
- Gonzalez-Granadillo, G.; Garcia-Alfaro, J.; Alvarez, E.; El-Barbori, M.; Debar, H. Selecting Optimal Countermeasures for Attacks against Critical Systems Using the Attack Volume Model and the RORI Index. Comput. Electr. Eng. 2015, 47, 13–34. [Google Scholar] [CrossRef]
- Alenezi, M.N.; Reed, M.J. Uniform DoS Traceback. Comput. Secur. 2014, 45, 17–26. [Google Scholar] [CrossRef]

© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license ( http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Barona López, L.I.; Valdivieso Caraguay, Á.L.; Maestre Vidal, J.; Sotelo Monge, M.A.; García Villalba, L.J. Towards Incidence Management in 5G Based on Situational Awareness. Future Internet 2017, 9, 3. https://doi.org/10.3390/fi9010003
Barona López LI, Valdivieso Caraguay ÁL, Maestre Vidal J, Sotelo Monge MA, García Villalba LJ. Towards Incidence Management in 5G Based on Situational Awareness. Future Internet. 2017; 9(1):3. https://doi.org/10.3390/fi9010003
Chicago/Turabian StyleBarona López, Lorena Isabel, Ángel Leonardo Valdivieso Caraguay, Jorge Maestre Vidal, Marco Antonio Sotelo Monge, and Luis Javier García Villalba. 2017. "Towards Incidence Management in 5G Based on Situational Awareness" Future Internet 9, no. 1: 3. https://doi.org/10.3390/fi9010003





