An Energy Efficient MAC Protocol for Wireless Passive Sensor Networks
Abstract
:1. Introduction
2. Related Work
2.1. Several Existing MAC Protocols
2.2. Analysis of S-MAC Protocol’s Backoff Mechanism
2.2.1. A Description of S-MAC Protocol’s Backoff Algorithm
2.2.2. The Disadvantages of S-MAC Protocol’s Backoff Algorithm
2.3. Some Improved Classic Backoff Algorithms
- (1)
- Multiplicative Increase Linear Decrease (MILD) algorithm [18]. When data collision occurs in the network, the contention window becomes two times larger than the original window. The contention window will decrease linearly after sending out data successfully. When the number of nodes in the network is not yet large, the contention window is large. This algorithm cannot reduce the contention window rapidly and causes larger transmission delays that reduce the utilization rate of channel.
- (2)
- Multiplicative Increase Multiplicative Decrease (MIMD) algorithm [19]. When collision happens, the contention window is doubled. When data is sent out successfully, the contention window becomes half the size of the original window. MIMD solves the problem of initializing contention window, but there is still no way to satisfy the dynamic changes of network topology and traffic.
- (3)
- Slow Decrease (SD) algorithm [19]. The current contention window of nodes becomes times () as much as the original contention window while accomplishing data transmission. Moreover, this algorithm can improve throughput and fairness among nodes when the number of nodes is large. However, when there are fewer nodes, nodes need to successfully send multiple times to reduce contention window.
- (4)
- Gentle Distributed Coordination Function (GDCF) algorithm [20]. Parameter is introduced in this algorithm and it refers to the number of messages. The current contention window decreases by half of the original window only if nodes successively succeed in sending messages. The value of is related to the number of nodes in the network. When the number of nodes is unknown, is in the range of 4–16. The advantage of this algorithm is that it can provide priority services to the nodes working in the network. The contention window of nodes with smaller value of decreases rapidly, so nodes have higher priority to access the channel. In this algorithm, throughput is greater than in the Binary Exponential Backoff (BEB) algorithm when the number of nodes is large.
3. IS-MAC Protocol
3.1. Parameters Used in the Improved Algorithm
- (1)
- Current contention window : The size of contention window is not fixed, and it can be dynamically changed within a specific range. This parameter is used to record the value of current contention window.
- (2)
- Minimum of contention window : The lower limit of the range of the current contention window is fixed from the beginning.
- (3)
- Maximum of contention window : The upper limit of the range of the current contention window, , is fixed from the beginning.
- (4)
- The initial value of contention window : , values of and will be set in accordance with the network environment.
- (5)
- Counter for successful competition : This value is used to record the number of consecutive successful transmission and its initial value is 0. The counter plus one as long as the node sends out data successfully. On the contrary, the counter is reset the moment of transmission fails. The counter has an upper limit determined by network load.
- (6)
- Threshold of counter for successful competition : This is the maximum of . The current window will change on the basis of the network load when reaches its limit. It is fixed from the beginning.
- (7)
- Counter for failed competition : The purpose of this counter is to protect nodes that fail to compete and to prevent nodes from unsuccessfully accessing channel for a long time because of its increasing contention window. This value is used to record the number of consecutive failed transmission and its initial value is 0. The value of this counter increases by one while collision happens. Meanwhile, the counter is reset after successfully sending out data.
- (8)
- Threshold of counter for failed competition : This is the upper limit of . The current window will change in line with network load when reaches its limit. It is fixed from the beginning.
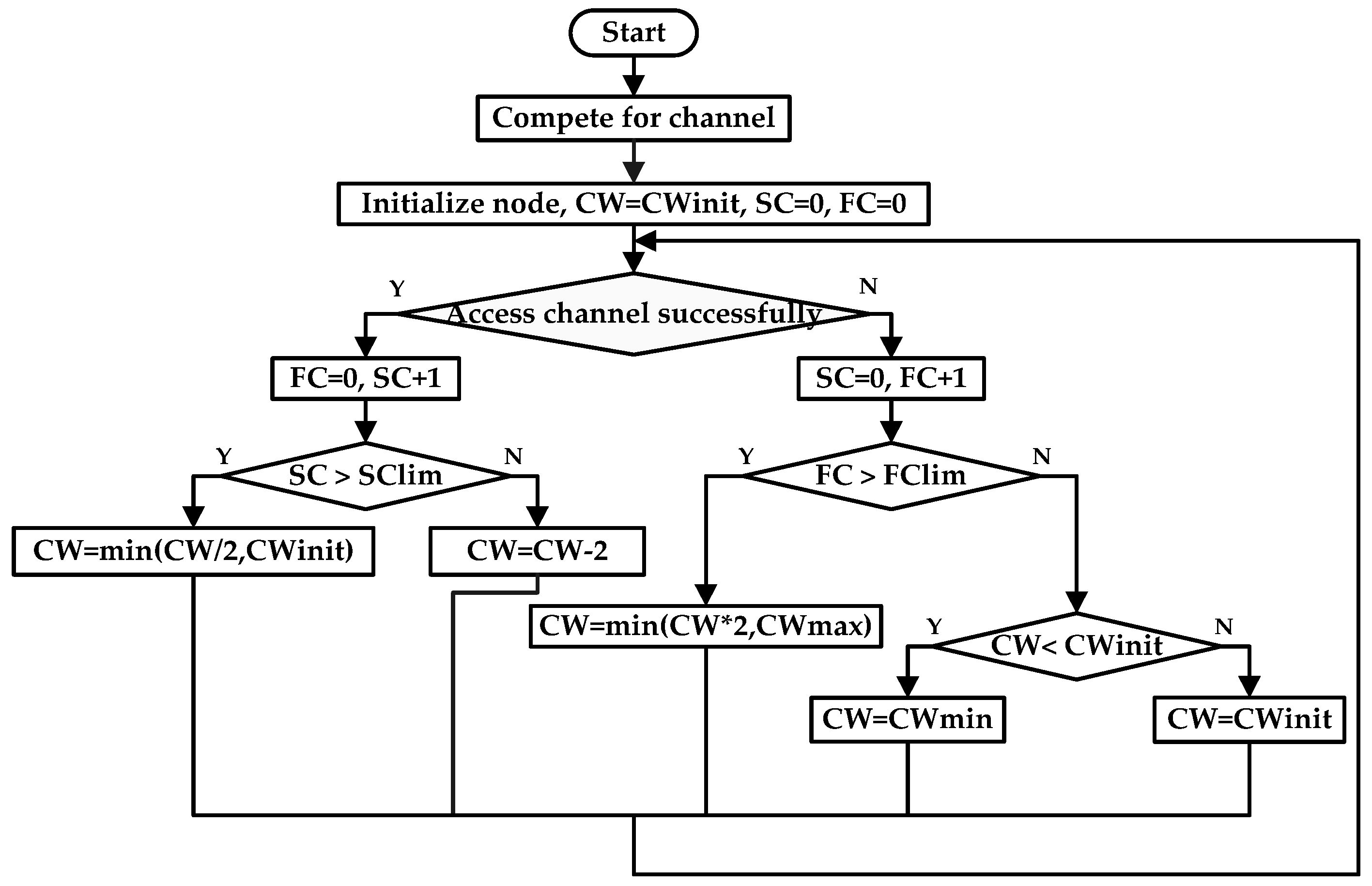
3.2. The Improved Backoff Algorithm
- (1)
- Node fails to access channel. is reset and plus one. It is divided into two cases as follows.
- When the number of continuous failed competition of channel is more than its corresponding threshold, the value of is greater than . The current contention window is too small and needs to be adjusted much larger via multiplicative increase. The new contention window is expressed as , which rapidly makes the contention window depart from area where collision happened just now.
- When the number of continuous failed competition of the channel is less than its corresponding threshold, the value of is less than . If the current contention window is smaller than , then the new contention window becomes . If the current contention window is larger than , then the new contention window is .
- (2)
- Node succeeds in accessing channel. is reset and plus one. It is also divided into two cases as follows.
- When the number of continuous successful competition of channel is more than its corresponding threshold, the value of is greater than . It is considered that the current contention window is too large. There are not so many nodes in the network or there is not so high data traffic. Therefore, the competition of the channel is not intense. In this case, it is not essential to set such a large contention window, so the current contention window value needs to be appropriately adjusted. The new contention window is expressed as . The contention window will be maintained within a certain area in case of its frequent changes.
- When the number of continuous successful competition of channel is less than its corresponding threshold, the value of is less than . The traffic load is relatively large right now, and the competition of channel is intense. Therefore, the current contention window merely requires minor adjustment, so it will be reduced by two to get the new contention window, .
4. Experiments and Analysis
4.1. Network Model and Parameters Configuring
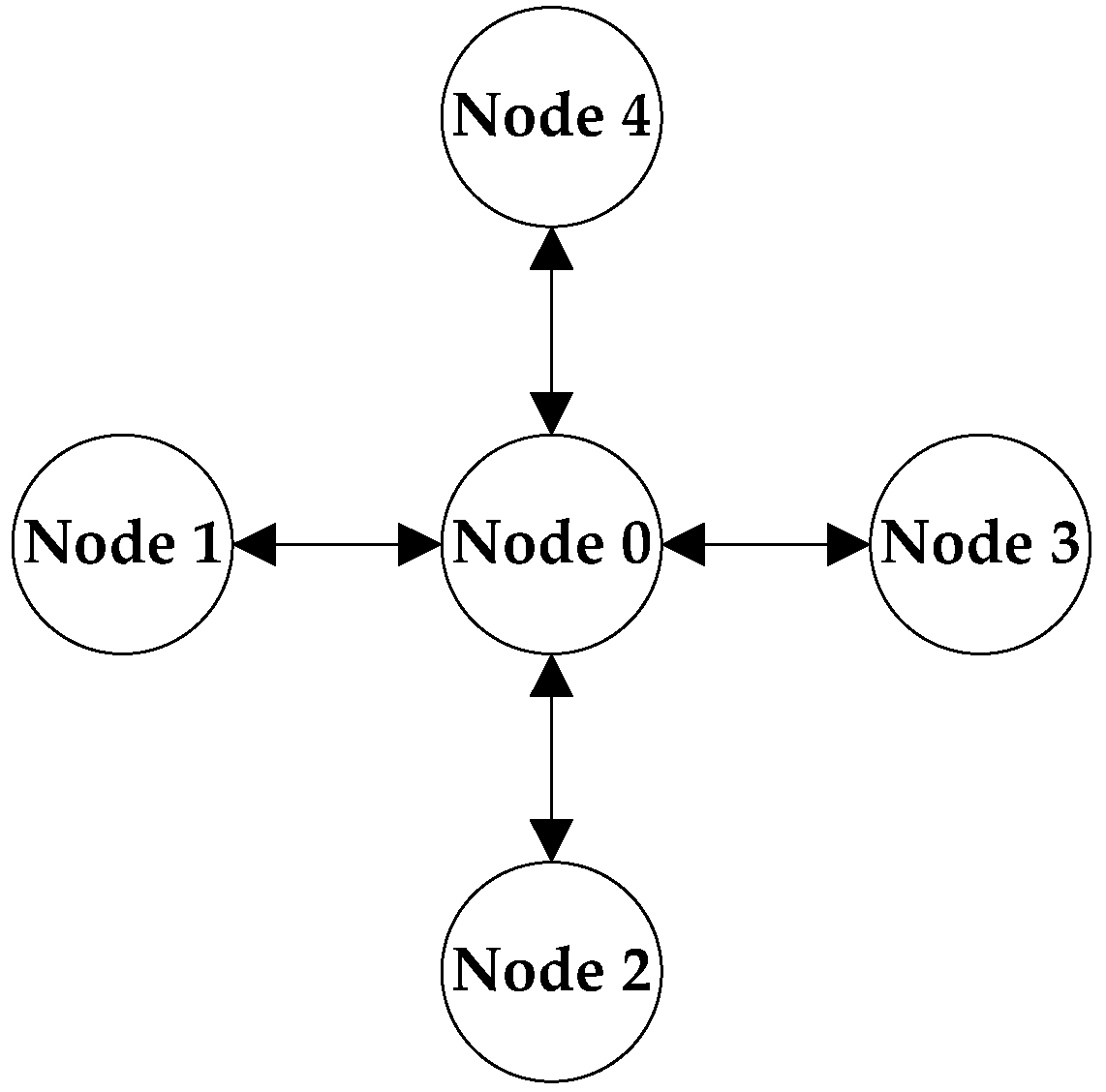
4.1.1. Network Model Selection
4.1.2. Network Model Establishment and Parameters Configuring
4.2. Simulation Results
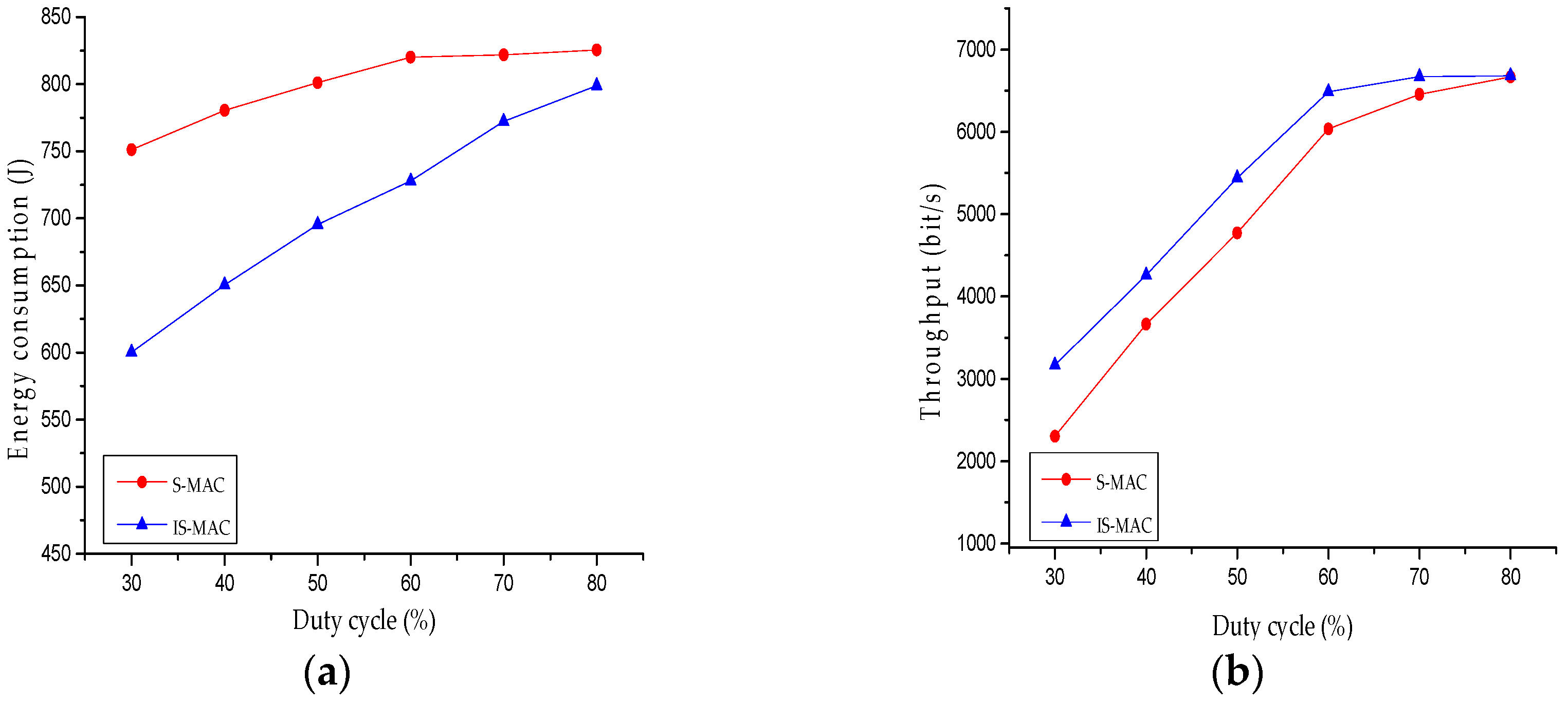
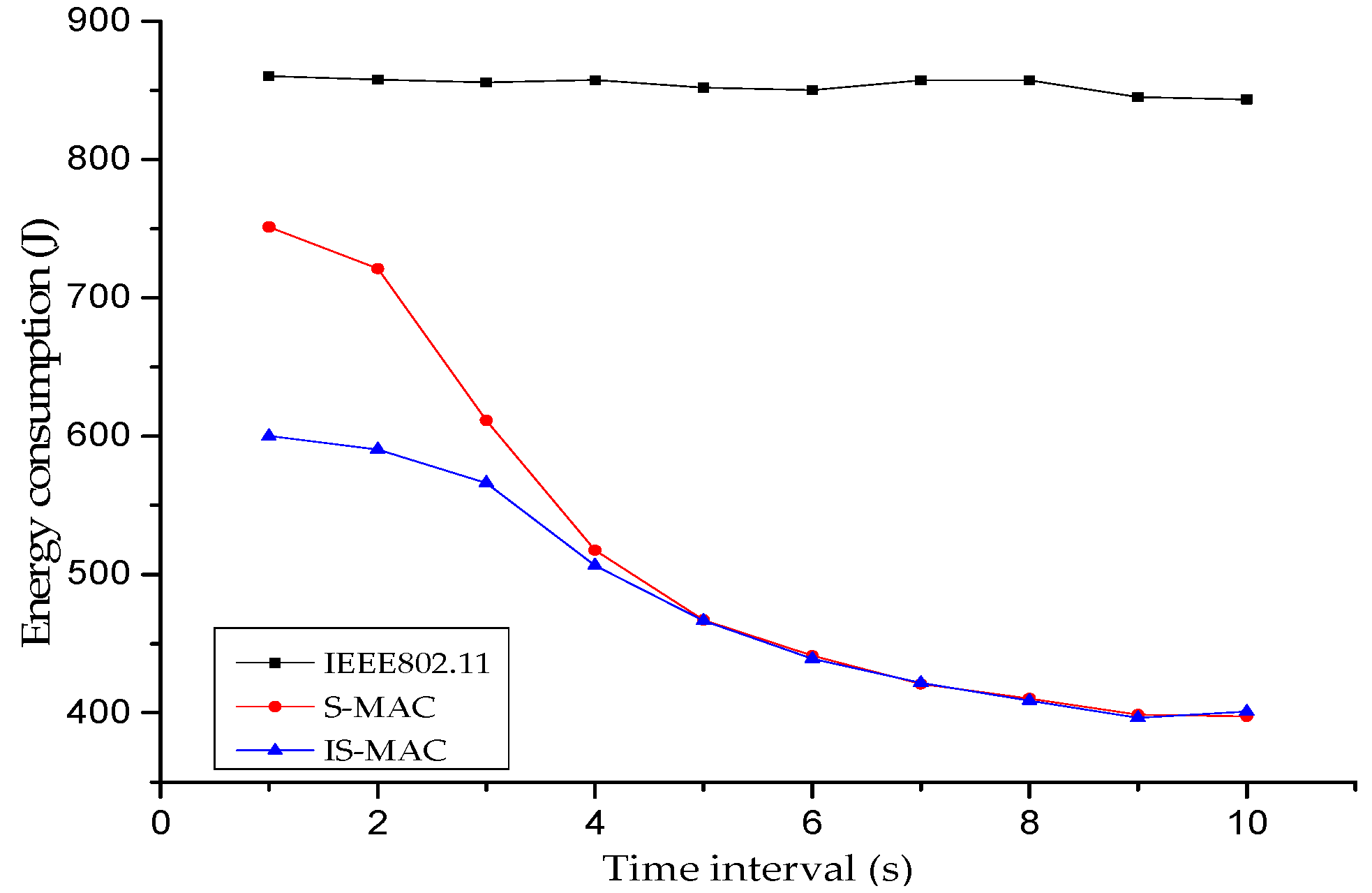
4.2.1. Energy Consumption
4.2.2. Throughput
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Yang, X.; Deng, D.T.; Liu, M.F. An Overview of Routing Protocols on Wireless Sensor Networks. In Proceedings of the 4th International Conference on Computer Science and Network Technology, Harbin, China, 19–20 December 2015. [Google Scholar]
- Padalkar, S.; Korlekar, A.; Pacharaney, U. Data Gathering in Wireless Sensor Networks for Energy Efficiency with and without Compressive Sensing at Sensor Node. In Proceedings of the International Conference on Communication and Signal Processing, Melmaruvathur, India, 6–8 April 2016. [Google Scholar]
- Akan, O.B.; Isik, M.T.; Baykal, B. Wireless Passive Sensor Networks. IEEE Commun. Mag. 2009, 47, 92–99. [Google Scholar] [CrossRef]
- Tudose, D.S.; Marin, A.; Geantǎ, M. Adaptive Duty-cycling Algorithms for Efficient Energy Harvesting in Wireless Sensor Networks. In Proceedings of the 15th RoEduNet Conference of Networking in Education and Research, Bucharest, Romania, 7–9 September 2016. [Google Scholar]
- Correia, R.; Carvalho, N.B.; Kawasaki, S. Continuously Power Delivering for Passive Backscatter Wireless Sensor Networks. IEEE Trans. Microw. Theory Tech. 2016, 64, 3723–3731. [Google Scholar] [CrossRef]
- Hong, Y.W.P.; Hsu, T.C.; Chennakesavula, P. Wireless Power Transfer for Distributed Estimation in Wireless Passive Sensor Networks. IEEE Trans. Signal Process. 2016, 64, 5382–5395. [Google Scholar] [CrossRef]
- Fernandes, R.D.; Boaventura, A.S.; Carvalho, N.B.; Matos, J.N. Increasing the Range of Wireless Passive Sensor Nodes Using Multisines. In Proceedings of the IEEE International Conference on RFID-Technologies and Applications, Sitges, Spain, 15–16 September 2011. [Google Scholar]
- Ojo, M.; Adami, D.; Giordano, S. Performance Evaluation of Energy Saving MAC Protocols in WSN Operating Systems. In Proceedings of the International Symposium on Performance Evaluation of Computer and Telecommunication Systems, Montreal, QC, Canada, 24–27 July 2016. [Google Scholar]
- Le Guennec, L.; Rachkidy, N.E.; Guitton, A.; Misson, M.; Kelfoun, K. MAC Protocol for Volcano Monitoring Using a Wireless Sensor Network. In Proceedings of the 6th International Conference on the Network of the Future, Montreal, QC, Canada, 30 September–2 October 2015. [Google Scholar]
- Kakria, A.; Aseri, T.C. Survey of Synchronous MAC Protocols for Wireless Sensor Networks. In Proceedings of the Recent Advances in Engineering and Computational Sciences, Chandigarh, India, 6–8 March 2014. [Google Scholar]
- Munadi, R.; Sulistyorini, A.E.; Fauzi S, F.U.; Adiprabowo, T. Simulation and Analysis of Energy Consumption for S-MAC and T-MAC Protocols on Wireless Sensor Network. In Proceedings of the IEEE Asia Pacific Conference on Wireless and Mobile, Bandung, Indonesia, 27–29 August 2015. [Google Scholar]
- Mihai, G.; Alina, D.A.; Ion, B. Performance analysis on T-MAC protocol over a body area network. In Proceedings of the 3rd International Symposium on Electrical and Electronics Engineering, Galati, Romania, 16–18 September 2010. [Google Scholar]
- Kebkal, O.; Kebkal, K.; Bannasch, R. Long-baseline Hydro-acoustic positioning using D-MAC communication protocol. In Proceedings of the OCEANS, 2012—Yeosu, Yeosu, Korea, 21–24 May 2012; pp. 1–7. [Google Scholar]
- Bdiri, S.; Derbel, F.; Kanoun, O. Wireless sensor nodes using energy harvesting and B-Mac protocol. In Proceedings of the 10th International Multi-Conferences on Systems, Signals and Devices, Hammamet, Tunis, 18–21 March 2013. [Google Scholar]
- Shurman, M.; Al-Shua’b, B.; Alsaedeen, M.; Al-Mistarihi, M.F.; Darabkh, K.A. N-BEB: New Backoff Algorithm for IEEE 802.11 MAC protocol. In Proceedings of the 37th International Convention on Information and Communication Technology, Opatija, Croatia, 26–30 May 2014. [Google Scholar]
- Dai, G.; Miao, C.; Ying, K.; Wang, K.; Chen, Q. An Energy Efficient MAC Protocol for Linear WSNs. Chin. J. Electron. 2015, 24, 725–728. [Google Scholar] [CrossRef]
- Pandit, S.; Singh, G. Backoff Algorithm in Cognitive Radio MAC Protocol for Throughput Enhancement. IEEE Trans. Veh. Technol. 2015, 64, 1991–2000. [Google Scholar] [CrossRef]
- Wu, H.; Cheng, S.; Peng, Y.; Long, K.P.; Ma, J. IEEE 802.11 Distributed Coordination Function (DCF): Analysis and Enhancement. In Proceedings of the IEEE International Conference on Communications, New York, NY, USA, 28 April–2 May 2002. [Google Scholar]
- Pang, Q.X.; Liew, S.C.; Lee, J.Y.B. Performance Evaluation of an Adaptive Backoff Scheme for WLAN. Wirel. Commun. Mob. Comput. 2004, 4, 867–879. [Google Scholar] [CrossRef]
- Ziouva, E.; Antonakopoulos, T. CSMA/CA Performance under High Traffic Condition: Throughput and Delay Analysis. Comput. Commun. 2002, 25, 313–321. [Google Scholar] [CrossRef]


| Name | Value |
|---|---|
| 3 | |
| 63 | |
| 5 | |
| 5 |
| Name | Value |
|---|---|
| Initial energy | 1000 J |
| Receiving energy | 0.3682 W |
| Transmitting energy | 0.386 W |
| Idle energy | 0.7442 W |
| Sleep energy | 5 × 10−5 W |
| Duty cycle | 30% |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yu, Q.; Li, G.; Hang, X.; Fu, K.; Li, A.T. An Energy Efficient MAC Protocol for Wireless Passive Sensor Networks. Future Internet 2017, 9, 14. https://doi.org/10.3390/fi9020014
Yu Q, Li G, Hang X, Fu K, Li AT. An Energy Efficient MAC Protocol for Wireless Passive Sensor Networks. Future Internet. 2017; 9(2):14. https://doi.org/10.3390/fi9020014
Chicago/Turabian StyleYu, Qingyao, Guangming Li, Xiaojie Hang, Kun Fu, and And Tianqi Li. 2017. "An Energy Efficient MAC Protocol for Wireless Passive Sensor Networks" Future Internet 9, no. 2: 14. https://doi.org/10.3390/fi9020014





