1. Introduction
Wireless sensor networks (WSNs) are widely applied in many domains ranging from military applications to civilian applications and gradually play more important roles in disaster relief, urgent search, health care, environmental monitoring, and so on. Generally, WSNs consist of large numbers of low-cost, densely deployed sensor nodes that organize themselves into a multi-hop wireless network. In WSNs, data collection and transmission can be automatically carried out so as to gain effective environmental information. Meanwhile, WSNs also face many challenges such as insufficient coverage, scalability, a lack of robustness, congestion, and mobility support [
1]. Furthermore, as sensor nodes are often deployed in hostile or inaccessible environments, battery charging and replacement are inconvenient and even impractical. As a result, WSNs are always faced with a seriously limited lifetime.
Medium access control (MAC) protocols have the function of deploying wireless channel resources efficiently for network nodes in WSNs in order to improve channel utilization and avoid data collision. There are different categories of MAC protocols, such as schedule-based, contention-based, hybrid, cross-layer, and real-time. Meanwhile, different MAC protocols are designed for different types of applications [
2]. Contention-based MAC protocols adopt specific back-off mechanisms to adjust the size of the contention window of each node before transmitting a message. The node with a smaller contention window size has a higher priority to access the wireless channel. Due to the back-off mechanism, the node preemptively occupying the channel sends data, when other nodes wait for another contention period until the channel is idle again. Thus, data collision is avoided to some extent. It is worth noting that the wireless network performance, i.e., throughput, delay, and energy efficiency, among other parameters, may vary with different back-off mechanisms.
In general, the major cause of energy waste in conventional MAC protocols is idle listening, which is a requisite period of some MAC protocols such as IEEE802.11 or code division multiple access (CDMA) protocol. During this period, the nodes have to keep listening to the channel for the potential message directed to them. Relevant studies have shown that the energy consumed in idle listening is comparable to that consumed in receiving or transmitting [
3]. As mentioned above, the WSNs are faced with a serious energy limitation, and these MAC protocols with long idle listening are not suitable for WSNs because of the high-energy consumption in idle listening. As a result, specially designed MAC protocols for WSNs are needed. Sensor-MAC (S-MAC) [
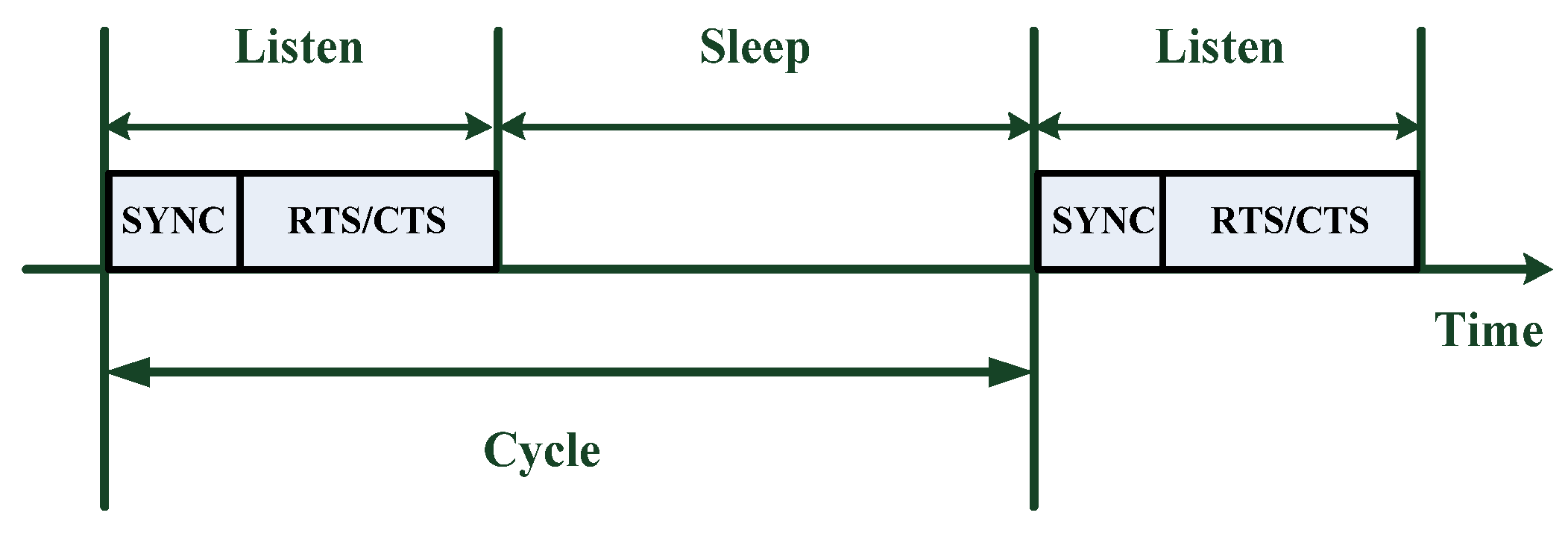
4], which is initiated based upon the 802.11 protocol, is a typical kind of contention-based MAC protocol designed for WSNs. In March 2010, the newest version of S-MAC was proposed. In order to reduce energy consumption, S-MAC protocol adopts a periodic listening/sleep working mechanism. This working mode has a low duty cycle. Sensor nodes periodically alternate between listening and sleep states. When listening, nodes are able to transmit or receive data; when sleeping, nodes turn off their radio to save energy. The core of the S-MAC protocol is to shorten the idle listening time and further reduce power consumption by controlling non-working nodes to go into a sleep state [
5]. T-MAC [
6] was proposed to improve the poor performance of S-MAC when traffic load is variable. In T-MAC, the idle listen period ends when no activation event has occurred in the channel for a fixed time threshold. Nodes will keep on updating their timeout values whenever an activation event occurs. When no events occur in a timeout period, the nodes will go to sleep. To eliminate energy waste caused by a continuous renewal of node timeout values in T-MAC, the concept of advertising for data contention is introduced in advertisement-based MAC (ADV-MAC) [
7], advertisement-based time-division multiple access (ATMA) [
8], and adaptive MAC (AdAMAC) [
9]. Several protocols have also been proposed to minimize packet latency, such as demand wakeup MAC (DW-MAC) [
10] and multi-divided deliver MAC (MDD-MAC) [
11]. DW-MAC introduces a low overhead scheduling algorithm that allows nodes to wake up on demand during the sleep period. MDD-MAC proposes a rotation method between sending and receiving data during the active period. The reinforcement learning mechanism [
12] is introduced to MAC protocols in WSNs to avoid idle listening and overhearing.
Compressed handshake MAC (CH-MAC) [
13] is presented to reduce unnecessary and redundant handshake frame so as to reduce the end-to-end delay and energy consumption. CH-MAC is a synchronized duty cycle MAC protocol. Similar to S-MAC, each cycle in CH-MAC is divided into the active period and the sleep period. The active period also consists of two periods: data and avoid. In the data period, a node with pending data contends for a wireless channel using a four-way handshake as in S-MAC. However, the RTS and CTS are replaced by a T frame. Data communication is initiated by an intended receiver node. Receiver will send a T frame with an upcoming request if the medium is idle. Upon receiving the T frame, the sender node will then reply with a data frame, which will be acknowledged by a receiver’s ACK. Once the sender node receives the ACK, it will go to sleep. By reducing the handshake time, CH-MAC can shorten the time during which a pair of nodes occupy the medium and can improve the end-to-end delay. Besides, CH-MAC can also decrease the transmission energy consumption by cutting down the RTS packet transmission. Furthermore, CH-MAC sets up an initiative sleeping mechanism. In the avoid period, after finishing the data transmission, a node goes to sleep immediately and wakes up when the next hop neighbor finishes its data transmission. This method will slightly reduce energy consumption and solve the hidden terminal problem.
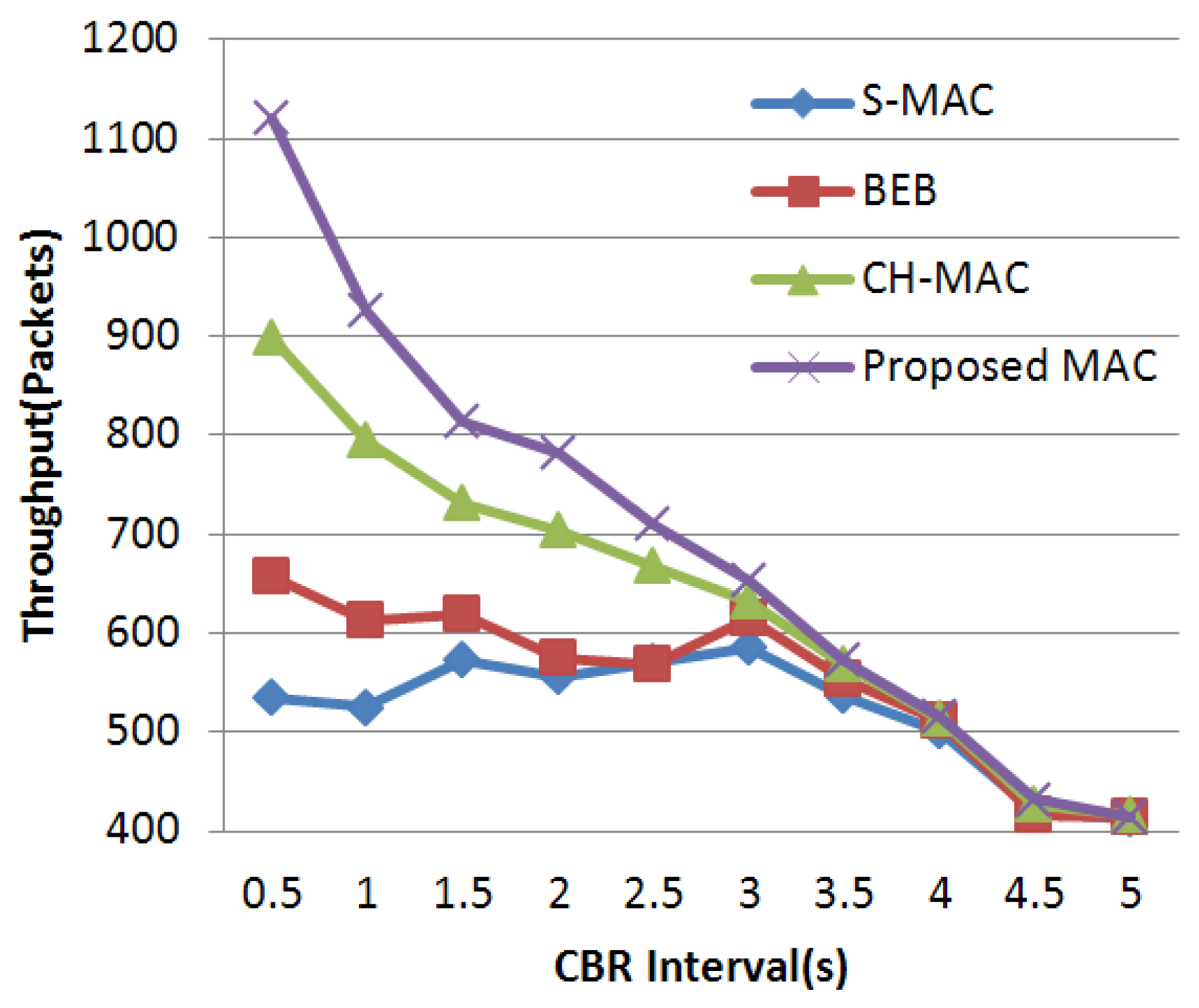
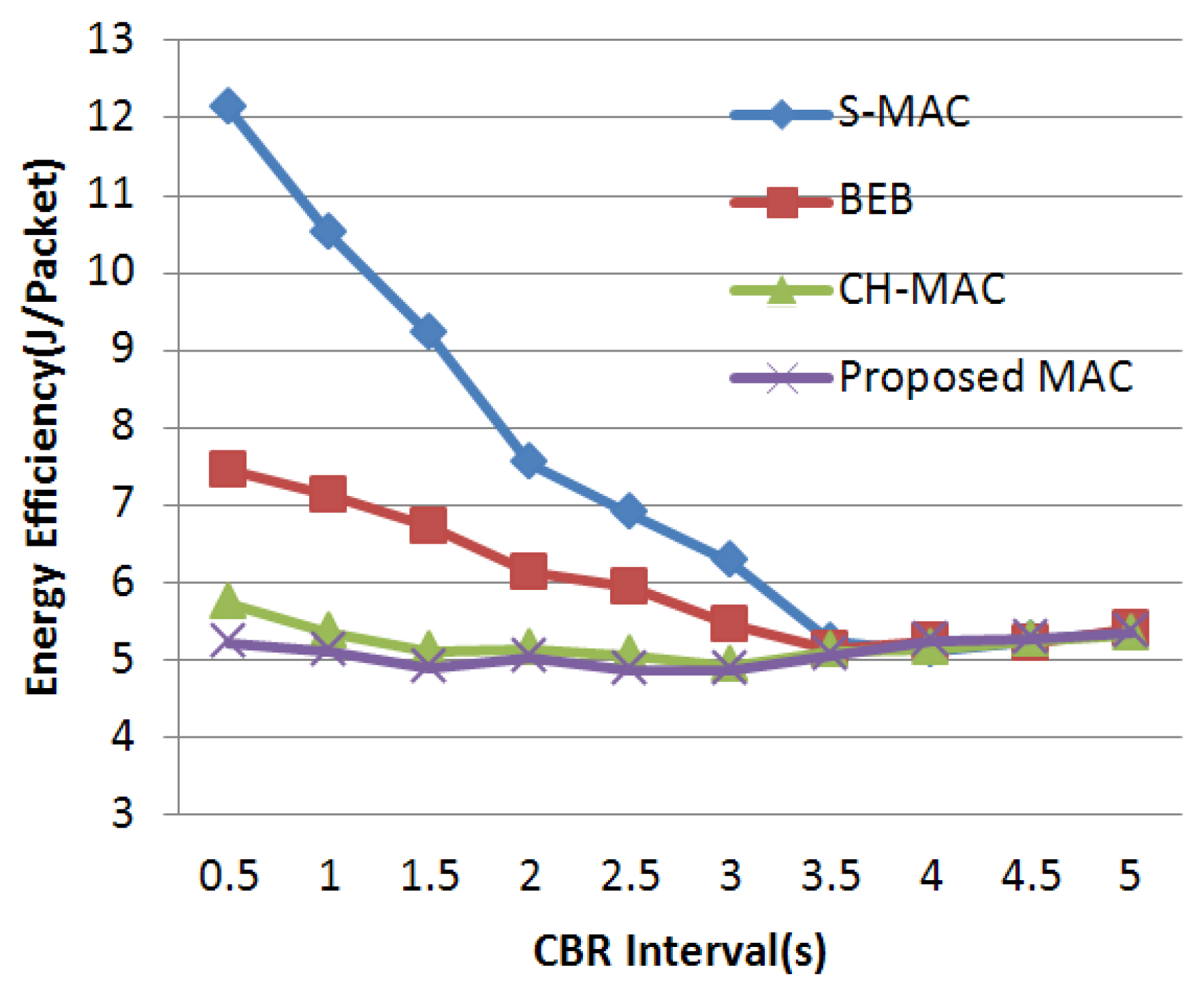
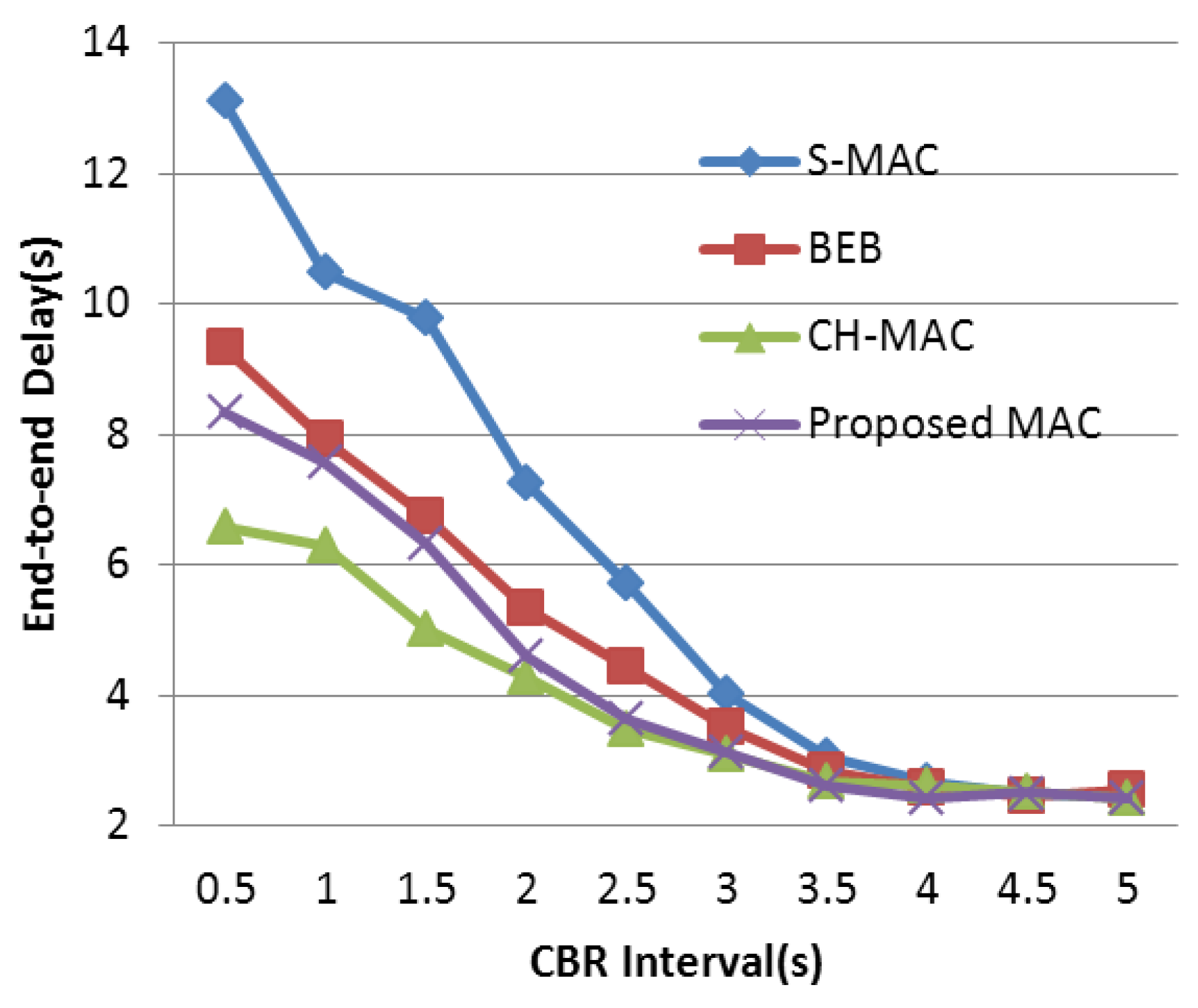
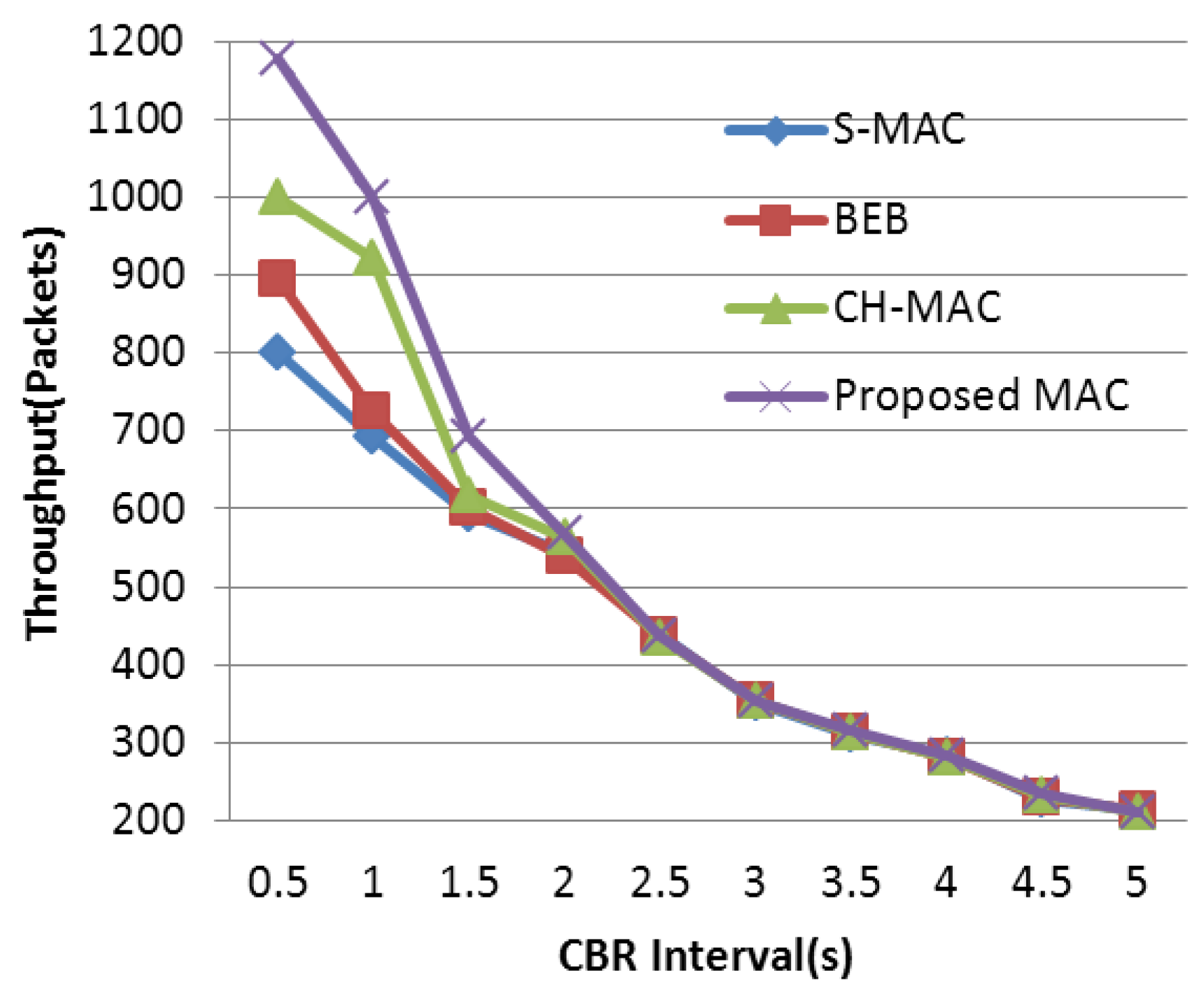
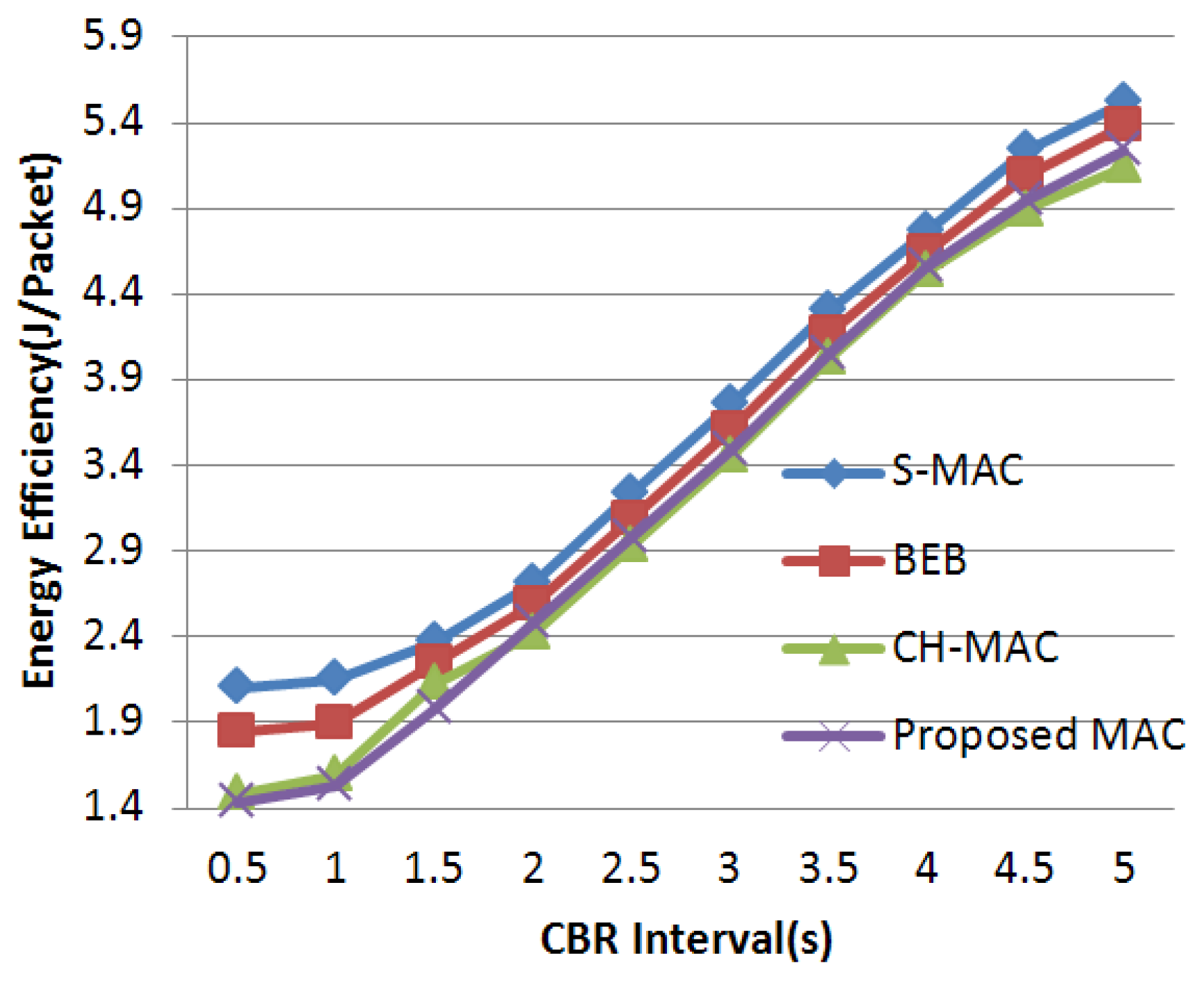
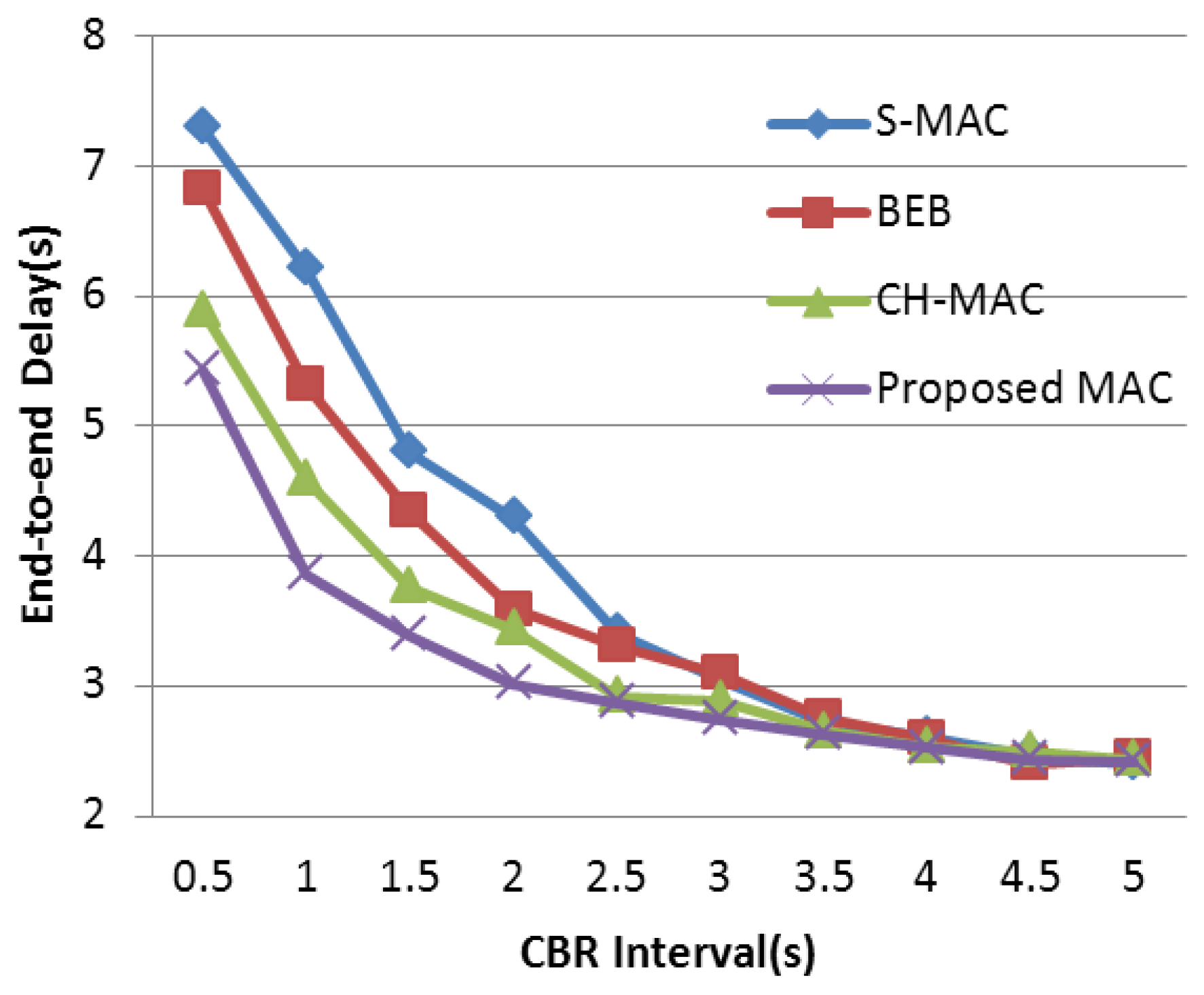
As mentioned above, many S-MAC-based protocols are proposed to further improve the performance in WSNs. It is important to find an appropriate target to make an improvement. It is worth noting that the back-off mechanism of S-MAC is quite simple. The size of the contention window in S-MAC is fixed, and all nodes share the same contention window sizes whether they have successfully obtained the channel or not. When the WSN is under light load, the mechanism is fairly efficient because, under this circumstance, the probability of data collision is quite small, and a fixed-size but narrow contention window can decrease the transmission delay. Thus, a short delay and a relatively high throughput are acquired. However, when the network load is heavy, the common fixed-size contention window makes nodes and their neighbors in the network more likely to send data at the same time. Under this circumstance, the fixed-size contention window becomes the bottleneck leading to a serious collision and aggravating the efficiency of wireless channel access. To cope with this performance deterioration, the back-off mechanism of S-MAC should be emphatically improved in order to guarantee the network performance under heavy load. In this paper, we propose a well-designed MAC protocol adopting an adaptive contention window which has higher adaptability in a heavy-load network. Based on the contention condition, conflict probability is significantly controlled by altering the back-off window size. Ultimately, higher throughput and energy efficiency are obtained.
The remaining portions of this paper are organized as follows. In
Section 2, we present a literature review of the related work. In
Section 3, our proposed MAC protocol is shown in detail. In
Section 4, the simulation results based on network simulator version 2 (NS-2) are given out. Finally, we conclude with a summary and some directions for future work.
3. Proposed Back-Off Scheme
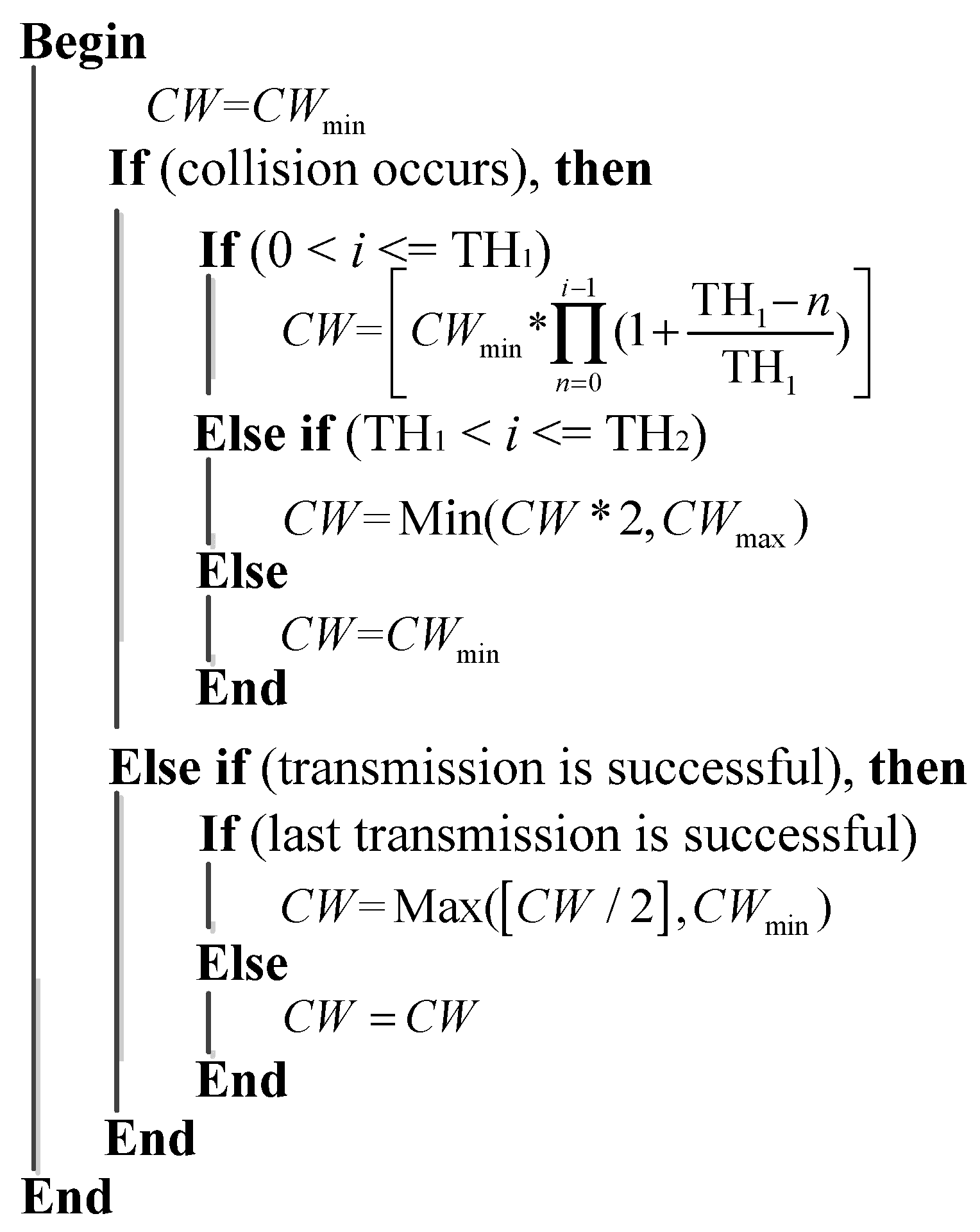
In order to improve the delivery performance under heavy load in WSNs, we propose a new back-off scheme to decrease the probability of data collision. In our designed protocol, the number of historical collisions is chosen as the parameter to reflect the channel status and nodes’ usage of the wireless channel. This parameter is easy to acquire and can reduce the complexity of the algorithm when compared with research mentioned above. A larger collision number reflects a higher competitive level in the wireless channel, and a larger contention window is needed under this condition to prolong the access time in order to relieve the competition. In BEB, its contention window adjustment mechanism is too rough that it only depends on the data transmission status to double or halve the contention window size. On the one hand, when data collision occurs, the contention window is doubled in BEB. However, this exponential increase is too rapid when traffic load is not heavy, which leads to unnecessary delay. It is better to retard this increase process under this circumstance. If traffic load is heavy, this exponential increase in BEB can effectively avoid data collision. On the other hand, when data transmission is successful, the contention window is halved directly in BEB. It is better to refer to the last transmission, which can partially reflect channel status. Based on these core ideas, the detailed back-off algorithm is described in
Figure 3.
In the algorithm mentioned above, [] represents a function of getting an integral value ([
x] denotes the largest integer that is no more than a positive real number
x). From the beginning, the contention window is set to
as a default. Once data collision occurs during transmission, the contention window will be adjusted. In detail, if the collision number (denoted as
i) is less than the first threshold (denoted as
), the contention window size will be calculated by Equation (2):
where
n is a variable ranging from 0 to
. Obviously, after the multiplication, a larger collision number brings with a larger contention window size. It is worth noting that
is a relatively smaller constant. By adopting this formula, the window size will increase smoothly as the collision number increases. When the collision number surpasses the first threshold and is less than the second threshold (denoted as
), which represents a more serious competition, this formula will be abandoned and the current contention window size will be doubled in order to obtain a fast adjustment. Especially, if the transmission is still failed even when collision number has reached
, the contention window will be set to
directly. There are two main reasons for setting the contention window to
. The first reason is that, if a node’s contention window is persistently large, it has to wait for a long time to transmit its packets. As a result, its data buffer is likely to be full. Under this circumstance, the node has to drop its upcoming packets, which is adverse for network throughput. The second reason is that this operation can balance the contention window size between different nodes, which can improve the fairness between different nodes as well as the average transmission delay. In the BEB mechanism, after a successful data delivery, the contention window size will be reset to
regardless of the channel status. In our mechanism, the window size, after a successful transmission, will be halved if the node’s last transmission is successful or will remain if its last transmission fails, considering that a sharp decrease in the contention window size will lead to a higher collision probability under a heavy network load.