EH-GC: An Efficient and Secure Architecture of Energy Harvesting Green Cloud Infrastructure
Abstract
:1. Introduction
2. Related Works
2.1. Requirements for Green Cloud Computing
2.2. Pyroelectric Energy Conversion
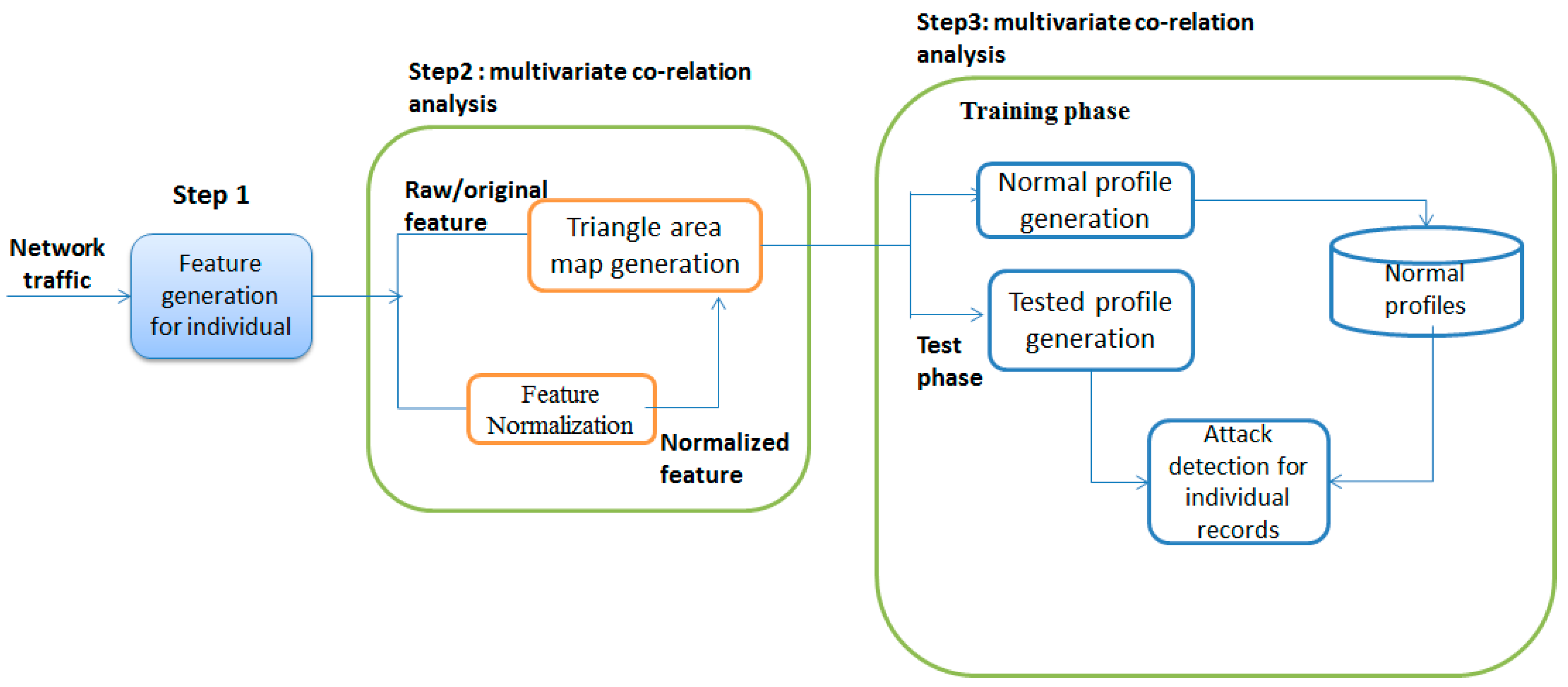
2.3. Multi-Variate Corrélation Analysis Technique
- Step 1:
- Basic features are generated in a well-defined time interval.
- Step 2:
- MCA incorporates a multivariate correlation investigation, in which triangle area map generation is connected to separate the relationships between two particular features inside every movement case originating from the initial step.
- Step 3:
- MCA contains the decision-making based on the training and testing phase.
2.4. Existing Researches
3. EH-GC: Energy Harvesting Architecture in Green Cloud Infrastructure
3.1. EH-GC Architecture Overview
3.1.1. Green Broker and CSP
3.1.2. Green Service Layer
3.1.3. Virtualization Layer
3.1.4. Data Center Layer
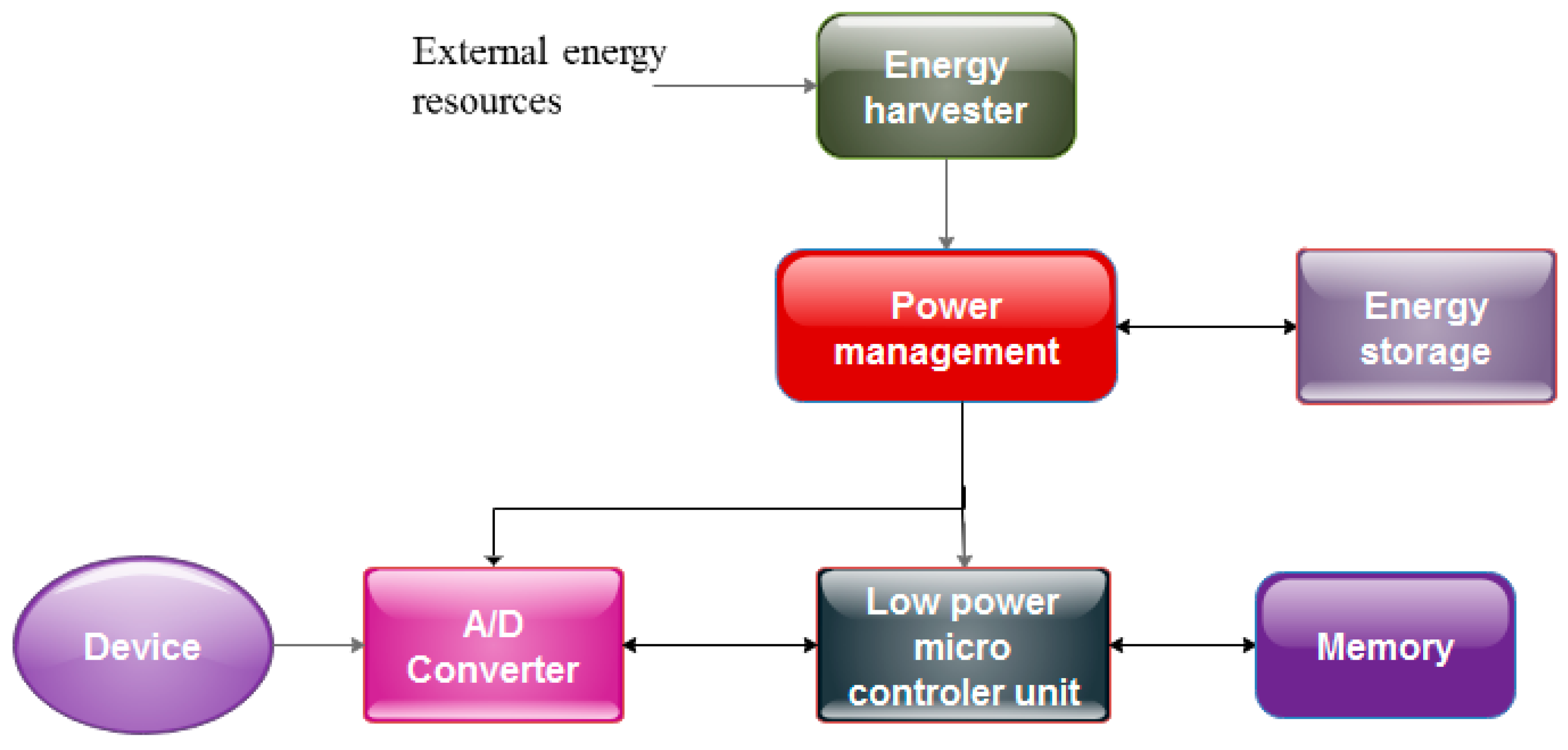
3.1.5. Energy Harvesting
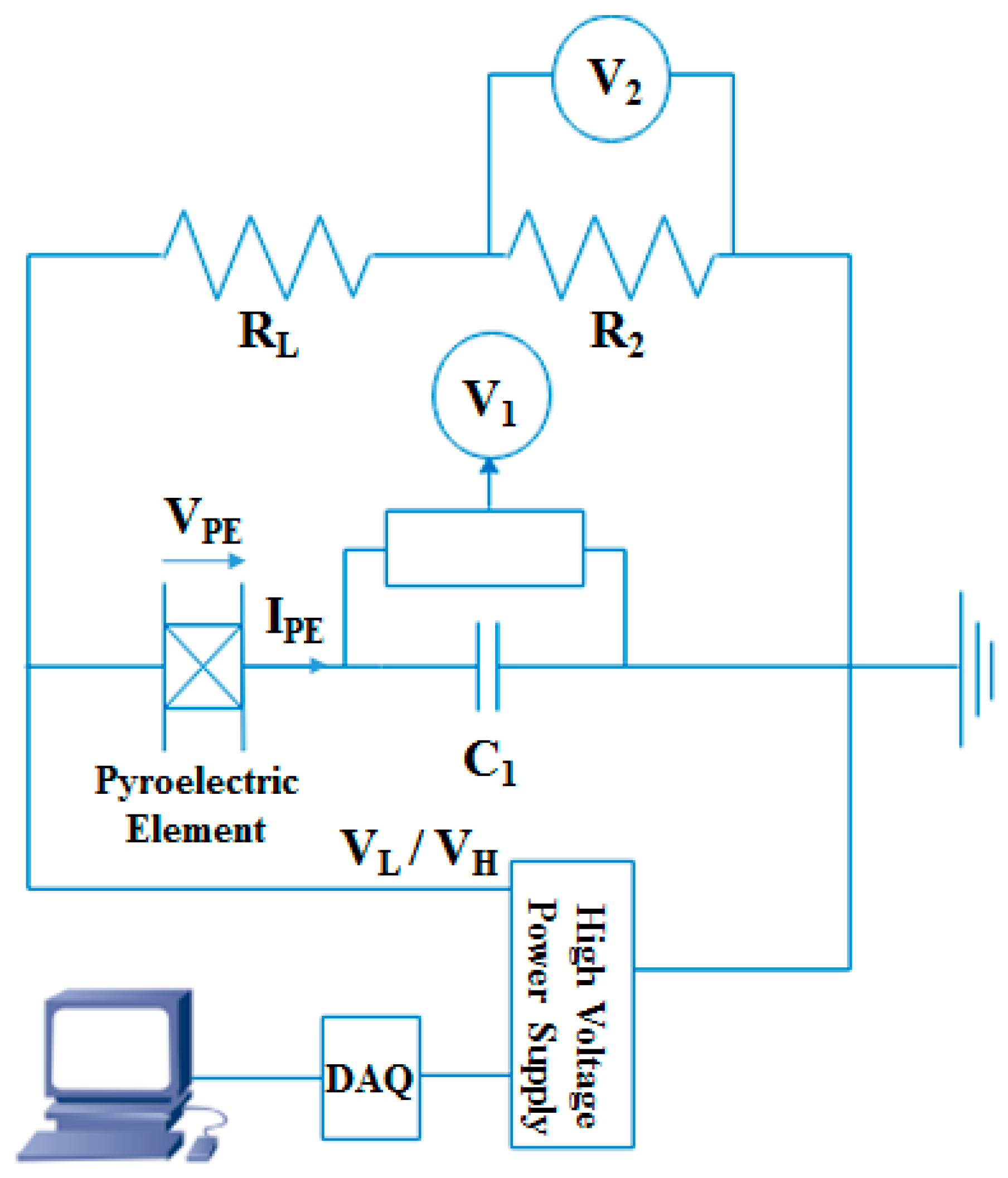
3.2. Pyroelectric Energy Harvesting
3.2.1. Olsen Cycle and Leakage Current
3.2.2. Electric Subsystem
3.3. Genetic Algorithm for VM Allocation
3.3.1. System Mode
- Steps 1:
- Initialize VMs and Hosts with CPU utilization and define SLA for VMs and Host features;
- Steps 2:
- Initialize genetic algorithm GA with SLA parameters = {Energy, Response time, Throughput};
- Steps 3:
- Use fitness function fn of GA and if ;
- Steps 4:
- , the fitness function is valid and feasible, and the return VM allocation is true;
- Steps 5:
- Otherwise, drop the VMs and check the performance metrics, and then increment the SLA violation;
- Steps 6:
- Return migration list and SLA violation;
3.3.2. SLA Violation Metrics
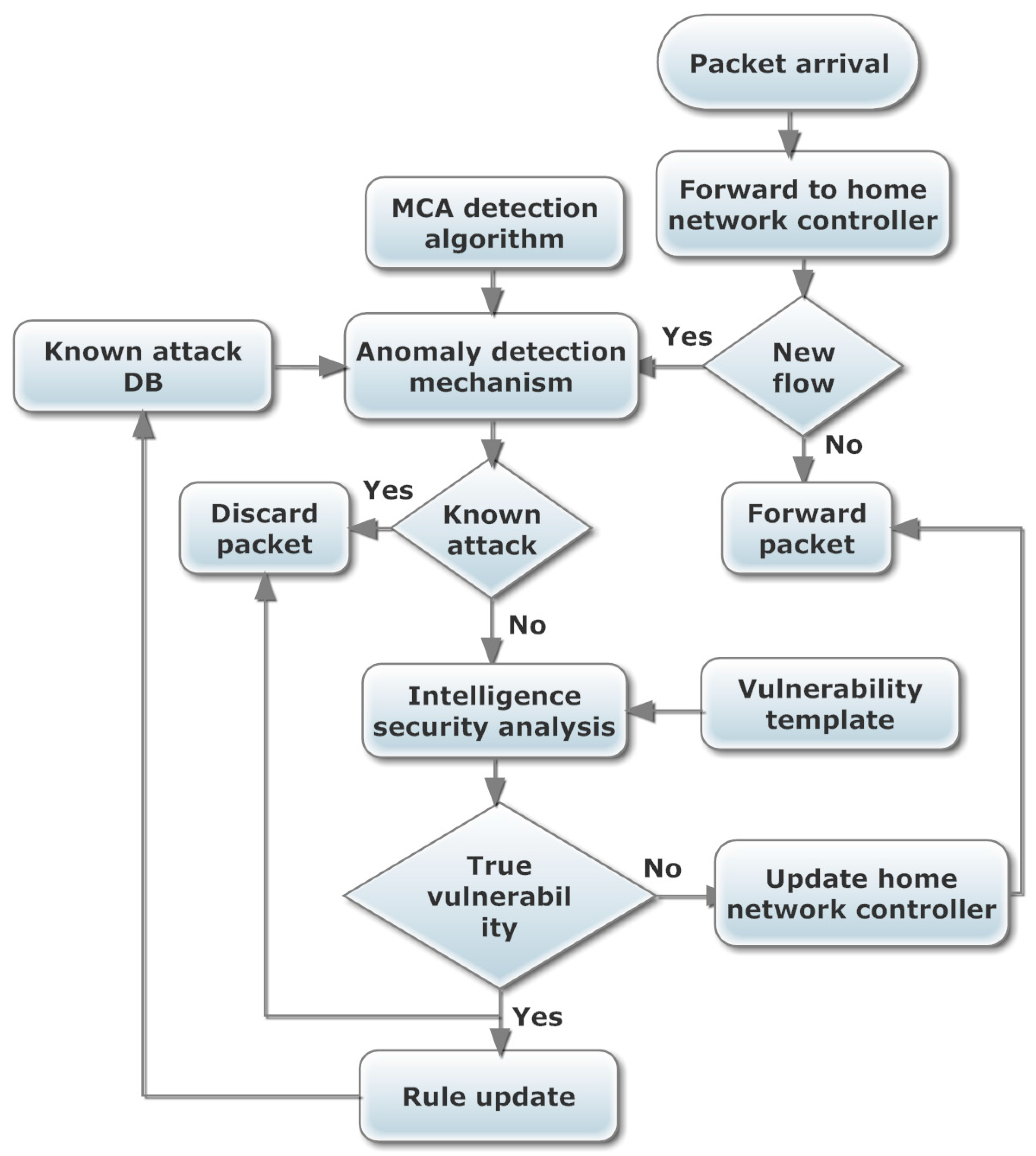
3.4. DoS Detection in Data Center Network Using MCA Analysis
3.4.1. MCA Detection Analysis
3.4.2. Detection Mechanism
3.4.3. Normal Profile Generation
| Algorithm 1 Normal Profile Generation Algorithm |
| Input: with elements |
Generate covariance matrix for using (12) for to do /* mahalanobis distance between and computed using (14) */ end for return |
3.4.4. Threshold Selection
3.4.5. Attack Detection
| Algorithm 2 Mahalanobis Distance-Based Attack Detection Algorithm | |
| Input: Observed traffic record , normal profile and parameter | |
| Generate for the observed traffic record | |
| if then | |
| return Normal | |
| else | |
| return Attack | |
| end if | |
4. Experimental Evaluation
4.1. Genetic Algorithm for VM Allocation
4.2. DoS Detection Using MCA Analysis
4.3. Pyroelectric Energy Harvesting
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Singh, S.; Jeong, Y.S.; Park, J.H. A survey on cloud computing security: Issues, threats, and solutions. J. Netw. Comput. Appl. 2016, 75, 200–222. [Google Scholar] [CrossRef]
- Shehabi, A.; Smith, S.; Sartor, D.; Brown, R.; Herrlin, M.; Koomey, J.; Masanet, E.; Horner, N.; Azevedo, I.; Lintner, W. United States Data Center Energy Usage Report; LBNL-1005775; Lawrence Berkeley National Laboratory: Berkeley, CA, USA, 2016; Volume 4, pp. 1–4. [Google Scholar]
- Ren, C.; Wang, D.; Urgaonkar, B.; Sivasubramaniam, A. Carbon-aware energy capacity planning for datacenters. In Proceedings of the 2012 IEEE 20th International Symposium on Modeling, Analysis and Simulation of Computer and Telecommunication Systems, Washington, DC, USA, 7–9 August 2012; pp. 391–400. [Google Scholar]
- Gao, P.X.; Curtis, A.R.; Wong, B.; Keshav, S. It’s not easy being green. ACM SIGCOMM Comput. Commun. Rev. 2012, 42, 211–222. [Google Scholar] [CrossRef]
- Cook, G. How Clean Is Your Cloud? 2012. Available online: http://www.greenpeace.org/international/Global/international/publications/climate/2012/iCoal/HowCleanisYourCloud.pdf (accessed on 2 April 2017).
- Mink, A.L. US Federal Agencies and Cloud: A Common Decision Framework for Determining Which Legacy IT Systems Should Migrate to Cloud. Ph.D. Dissertation, George Mason University, Fairfax, VA, USA, 2015. Available online: http://mars.gmu.edu/handle/1920/9705 (accessed on 16 April 2017).
- Subashini, S.; Kavitha, V. A survey on security issues in service delivery models of cloud computing. J. Netw. Comput. Appl. 2011, 34, 1–11. [Google Scholar] [CrossRef]
- Garrison, G.; Wakefield, R.L.; Kim, S. The effects of IT capabilities and delivery model on cloud computing success and firm performance for cloud supported processes and operations. Int. J. Inf. Manag. 2015, 35, 377–393. [Google Scholar] [CrossRef]
- Nelson, P. Cybercriminals Moving into Cloud Big Time, Report Says. Available online: http://www.networkworld.com/article/2900125/malware-cybercrime/criminals-moving-into-cloud-big-time-says-report.html (accessed on 7 April 2017).
- Singh, S.; Sharma, P.K.; Park, J.H. SH-SecNet: An Enhanced Secure Network Architecture for the Diagnosis of Security Threats in a Smart Home. Sustainability 2017, 9, 513–532. [Google Scholar] [CrossRef]
- Osanaiye, O.; Choo, K.-K.R.; Dlodlo, M. Distributed Denial of Service (DDoS) Resilience in Cloud: Review and Conceptual Cloud DDoS Mitigation Framework. J. Netw. Comput. Appl. 2016, 67, 147–165. [Google Scholar] [CrossRef]
- Somani, G.; Gaur, M.S.; Sanghi, D.; Conti, M.; Buyya, R. DDoS attacks in cloud computing: issues, taxonomy, and future directions. Comput. Commun. 2017, 105, 30–48. [Google Scholar] [CrossRef]
- Keegan, N.; Ji, S.Y.; Chaudhary, A.; Concolato, C.; Yu, B.; Jeong, D.H. A survey of cloud-based network intrusion detection analysis. Hum. Centric Comput. Inf. Sci. 2016, 6, 1–16. [Google Scholar] [CrossRef]
- Kar, J.; Mishra, M.R. Mitigating Threats and Security Metrics in Cloud Computing. J. Inf. Process. Syst. 2016, 12, 226–233. [Google Scholar]
- Rahman, N.H.A.B.; Cahyani, N.D.W.; Choo, K.-K.R. Cloud incident handling and forensic-by-design: Cloud storage as a case study. Concurr. Comput. Pract. Exp. 2016. [Google Scholar] [CrossRef]
- Alam, Q.; Malik, S.U.R.; Akhunzada, A.; Choo, K.-K.R.; Tabbasum, S.; Alam, M.A. Cross Tenant Access Control (CTAC) Model for Cloud Computing: Formal Specification and Verification. IEEE Trans. Inf. Forensics Secur. 2017, 12, 1259–1268. [Google Scholar] [CrossRef]
- Huang, C.J.; Guan, C.T.; Chen, H.M.; Wang, Y.W.; Chang, S.C.; Li, C.Y.; Weng, C.H. An adaptive resource management scheme in cloud computing. Eng. Appl. Artif. Intell. 2013, 26, 382–389. [Google Scholar] [CrossRef]
- El Amraoui, A.; Manier, M.A.; El Moudni, A.; Benrejeb, M. A genetic algorithm approach for a single hoist scheduling problem with time windows constraints. Eng. Appl. Artif. Intell. 2013, 26, 1761–1771. [Google Scholar] [CrossRef]
- Rodríguez, G.; Soria, Á.; Campo, M. Artificial intelligence in service-oriented software design. Eng. Appl. Artif. Intell. 2016, 53, 86–104. [Google Scholar] [CrossRef]
- Zhu, W.; Lee, C. A Security Protection Framework for Cloud Computing. J. Inf. Process. Syst. 2016, 12, 538–547. [Google Scholar]
- Thombare, D.G.; Verma, S.K. Technological development in the Stirling cycle engines. Renew. Sustain. Energy Rev. 2008, 12, 1–38. [Google Scholar] [CrossRef]
- Sebald, G.; Pruvost, S.; Guyomar, D. Energy harvesting based on Ericsson pyroelectric cycles in a relaxor ferroelectric ceramic. Smart Mater. Struct. 2007, 17, 1–6. [Google Scholar] [CrossRef]
- Basagni, S.; Naderi, M.Y.; Petrioli, C.; Spenza, D. Wireless Sensor Networks with Energy harvesting. 2013. Available online: https://pdfs.semanticscholar.org/ab43/3e2af3da6cee743bf82727631a80831b81cb.pdf (accessed on 1 April 2017).
- Moreno, R.C.; James, B.A.; Navid, A.; Pilon, L. Pyroelectric energy converter for harvesting waste heat: Simulations versus experiments. Int. J. Heat Mass Transf. 2012, 55, 4301–4311. [Google Scholar] [CrossRef]
- Lee, F.Y.; Navid, A.; Pilon, L. Pyroelectric waste heat energy harvesting using heat conduction. Appl. Therm. Eng. 2012, 37, 30–37. [Google Scholar] [CrossRef]
- Tan, Z.; Jamdagni, A.; He, X.; Nanda, P.; Liu, R.P. A system for denial-of-service attack detection based on multivariate correlation analysis. IEEE Trans. Parallel Distrib. Syst. 2014, 25, 447–456. [Google Scholar]
- Karthik, C.; Sharma, M.; Maurya, K.; Chandrasekaran, K. Green intelligence for cloud data centers. In Proceedings of the 2016 3rd International Conference on Recent Advances in Information Technology (RAIT), Kolkata, India, 5 March 2016; pp. 591–597. Available online: http://ieeexplore.ieee.org/xpl/mostRecentIssue.jsp?punumber=7503253 (accessed on 3 April 2017).
- Jing, S.Y.; Ali, S.; She, K.; Zhong, Y. State-of-the-art research study for green cloud computing. J. Supercomput. 2013, 65, 445–468. [Google Scholar] [CrossRef]
- Beloglazov, A.; Abawajy, J.; Buyya, R. Energy-aware resource allocation heuristics for efficient management of data centers for cloud computing. Future Gener. Comput. Syst. 2012, 28, 755–768. [Google Scholar] [CrossRef]
- Goyal, Y.; Arya, M.S.; Nagpal, S. Energy efficient hybrid policy in green cloud computing. In Proceedings of the 2015 International Conference on Green Computing and Internet of Things (ICGCIoT), Delhi, India, 8–10 October 2015; pp. 1065–1069. [Google Scholar]
- Yang, J.; Jiang, B.; Lv, Z.; Choo, K.-K.R. A task scheduling algorithm considering game theory designed for energy management in cloud computing. Future Gener. Comput. Syst. 2017. [Google Scholar] [CrossRef]
- Teing, Y.Y.; Dehghantanha, A.; Choo, K.-K.R.; Abdullah, M.A.; Muda, Z. Greening Cloud-Enabled Big Data Storage Forensics: Syncany as a Case Study. IEEE Trans. Sustain. Comput. 2017. [Google Scholar] [CrossRef]
- Osanaiye, O.; Cai, H.; Choo, K.-K.R.; Dehghantanha, A.; Xu, Z.; Dlodlo, M. Ensemble-based Multi-Filter Feature Selection Method for DDoS Detection in Cloud Computing. EURASIP J. Wirel. Commun. Netw. 2016, 2016, 1–10. [Google Scholar] [CrossRef]
- Kumari, S.; Xiong, L.; Wu, F.; Das, A.K.; Choo, K.-K.R.; Shen, J. Design of a Provably Secure Biometrics-based Multi-cloud-server Authentication Scheme. Future Gener. Comput. Syst. 2017, 68, 320–330. [Google Scholar] [CrossRef]
- Lang, S.B. Sourcebook of Pyroelectricity; Gordon Breach: New York, NY, USA, 1974; pp. 1–489. [Google Scholar]
- Olsen, R.B.; Briscoe, J.M.; Bruno, D.A.; Butler, W.F. A pyroelectric energy converter which employs regeneration. Ferroelectrics 1981, 38, 975–978. [Google Scholar] [CrossRef]
- Lines, M.E.; Glass, A.M. Principles and Applications of Ferroelectrics and Related Materials; Oxford University Press: Oxford, UK, 1977; pp. 1–604. [Google Scholar]
- De Maesschalck, R.; Jouan-Rimbaud, D.; Massart, D.L. The mahalanobis distance. Chemom. Intell. Lab. Syst. 2000, 50, 1–18. [Google Scholar] [CrossRef]
- Calheiros, R.N.; Ranjan, R.; Beloglazov, A.; De Rose, C.A.; Buyya, R. CloudSim: A toolkit for modeling and simulation of cloud computing environments and evaluation of resource provisioning algorithms. Softw. Pract. Exp. 2011, 41, 23–50. [Google Scholar] [CrossRef]
- Stolfo, S.J.; Fan, W.; Lee, W.; Prodromidis, A.; Chan, P.K. Cost-based modeling for fraud and intrusion detection: Results from the JAM project. In Proceedings of the DARPA Information Survivability Conference and Exposition, Hilton Head, SA, USA, 25–27 January 2000; Volume 2, pp. 130–144. [Google Scholar]
- Navid, A.; Lynch, C.S.; Pilon, L. Purified and porous poly (vinylidene fluoride-trifluoroethylene) thin films for pyroelectric infrared sensing and energy harvesting. Smart Mater. Struct. 2010, 19, 055006–055019. Available online: http://iopscience.iop.org/article/10.1088/0964-1726/19/5/055006/pdf (accessed on 1 April 2017). [CrossRef]
- Vanderpool, D.; Yoon, J.H.; Pilon, L. Simulations of a prototypical device using pyroelectric materials for harvesting waste heat. Int. J. Heat Mass Transf. 2008, 51, 5052–5062. [Google Scholar] [CrossRef]
- Incropera, F.P.; DeWitt, D.P.; Bergman, T.L.; Lavine, A.S. Introduction to Heat and Mass Transfer; John Wiley & Sons Inc.: New York, NY, USA, 2002; pp. 1–1039. [Google Scholar]

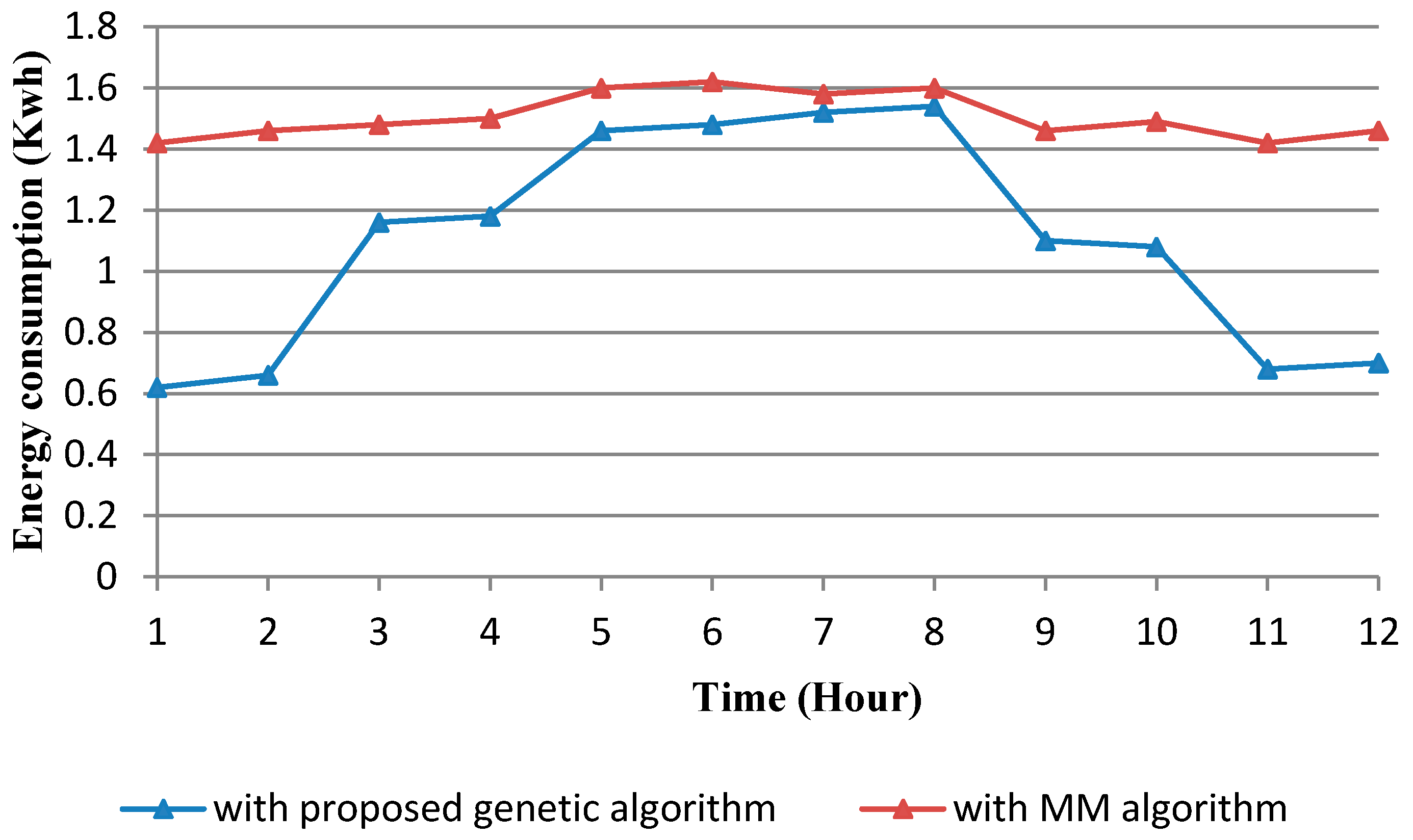
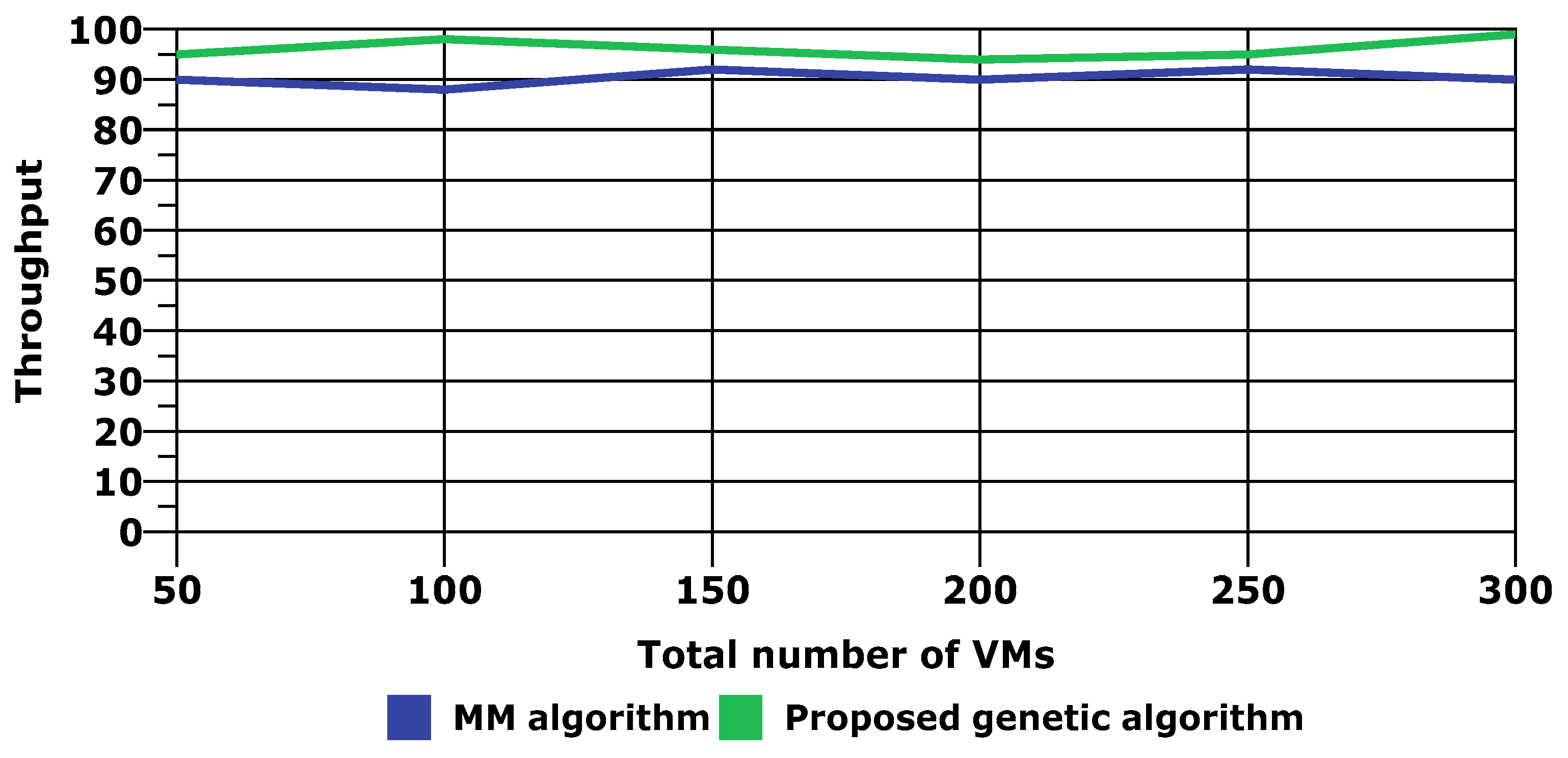
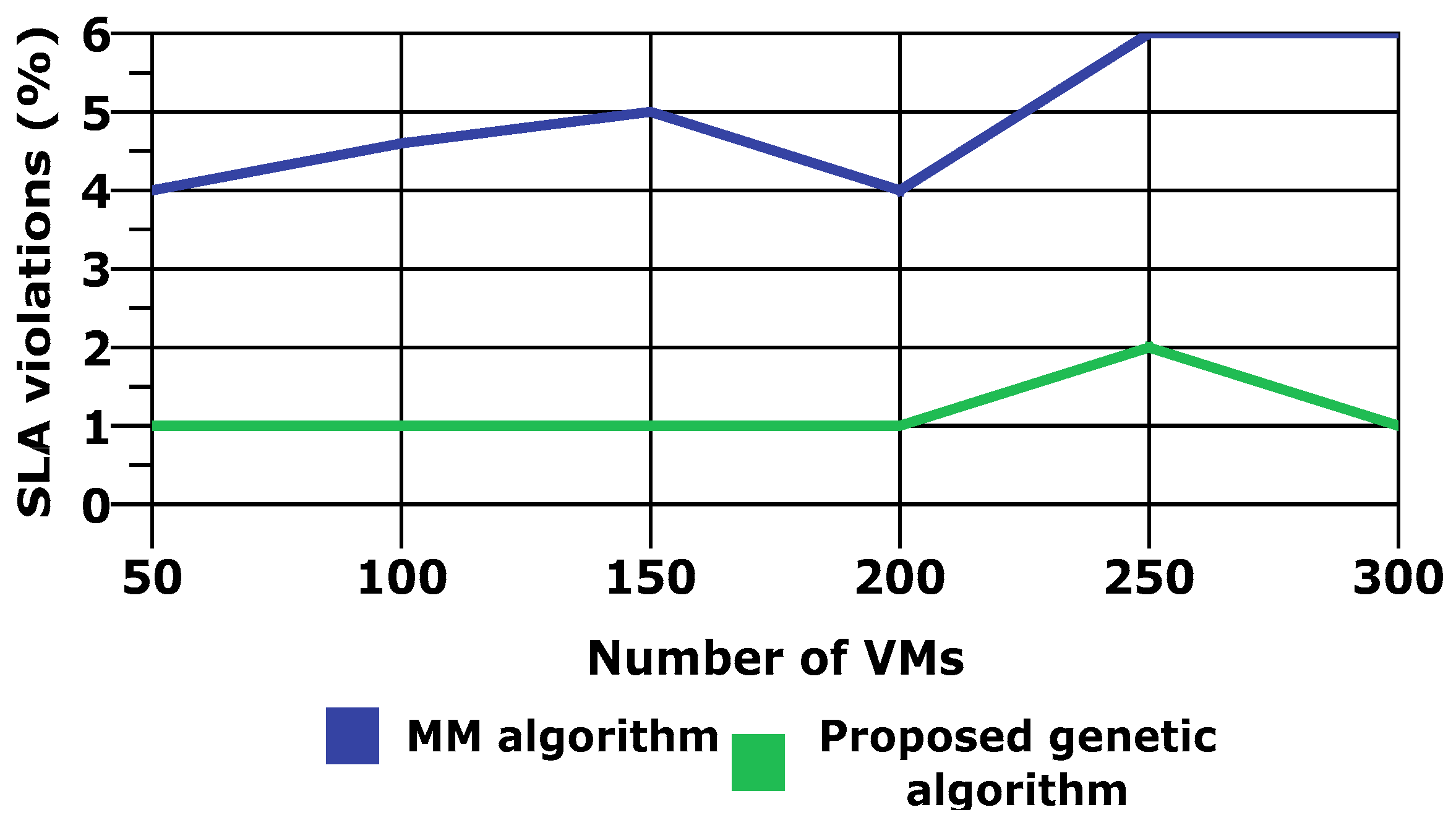
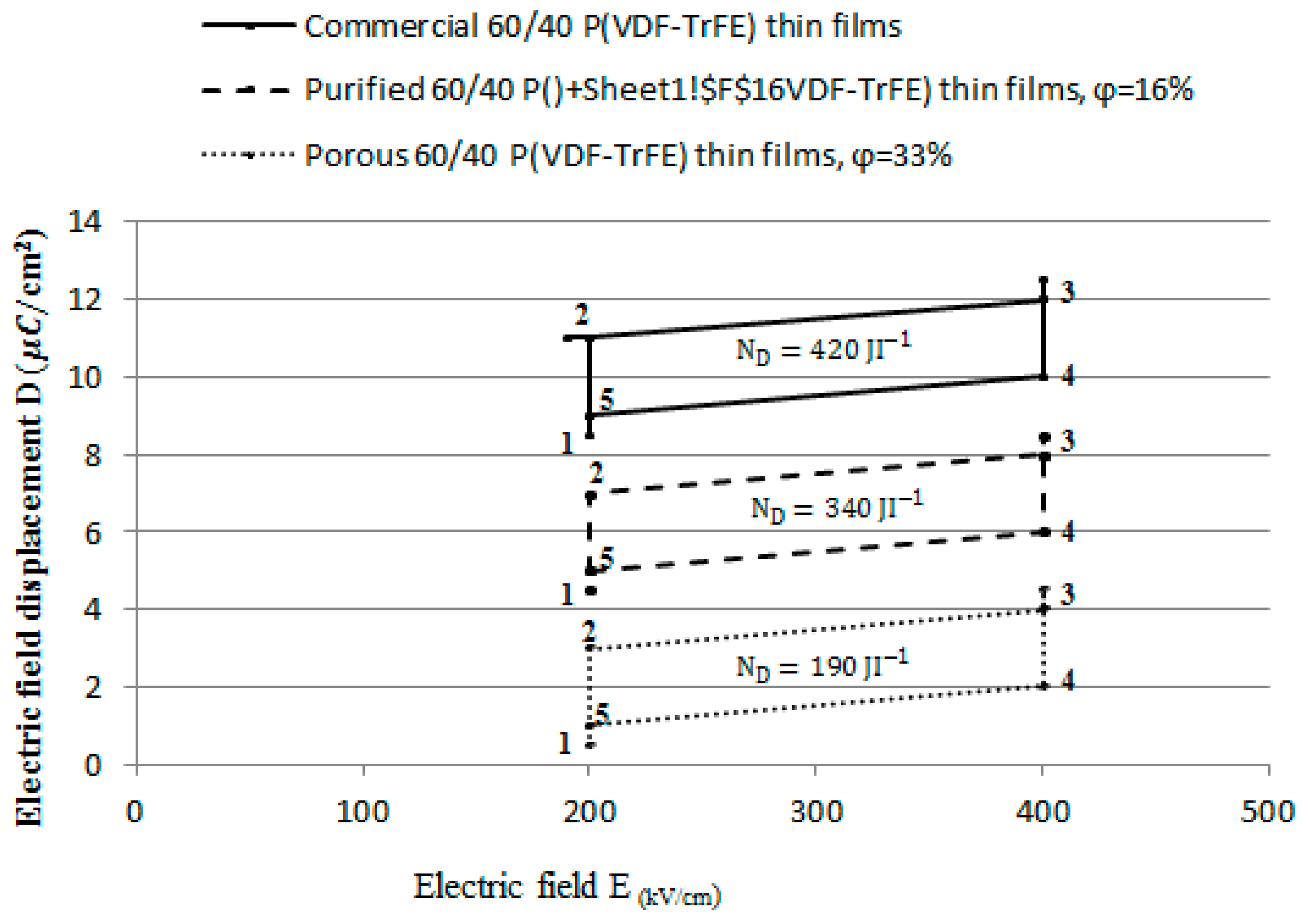
| Performance Parameter | Percentage Improvement |
|---|---|
| Energy consumption | 26.64% |
| Throughput | 6% |
| SLA voilation | 76% |
| Evaluation Metrics | Accuracy | False Positive Rate | Detection Rate |
|---|---|---|---|
| Value | 94.15% | 1.30% | 94.90% |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Singh, S.; Sharma, P.K.; Moon, S.Y.; Park, J.H. EH-GC: An Efficient and Secure Architecture of Energy Harvesting Green Cloud Infrastructure. Sustainability 2017, 9, 673. https://doi.org/10.3390/su9040673
Singh S, Sharma PK, Moon SY, Park JH. EH-GC: An Efficient and Secure Architecture of Energy Harvesting Green Cloud Infrastructure. Sustainability. 2017; 9(4):673. https://doi.org/10.3390/su9040673
Chicago/Turabian StyleSingh, Saurabh, Pradip Kumar Sharma, Seo Yeon Moon, and Jong Hyuk Park. 2017. "EH-GC: An Efficient and Secure Architecture of Energy Harvesting Green Cloud Infrastructure" Sustainability 9, no. 4: 673. https://doi.org/10.3390/su9040673






