A Security Analysis of Cyber-Physical Systems Architecture for Healthcare
Abstract
:1. Introduction
2. Related Works
2.1. Architectures for CPS in Healthcare
2.2. Architectural Qualities for Healthcare CPS
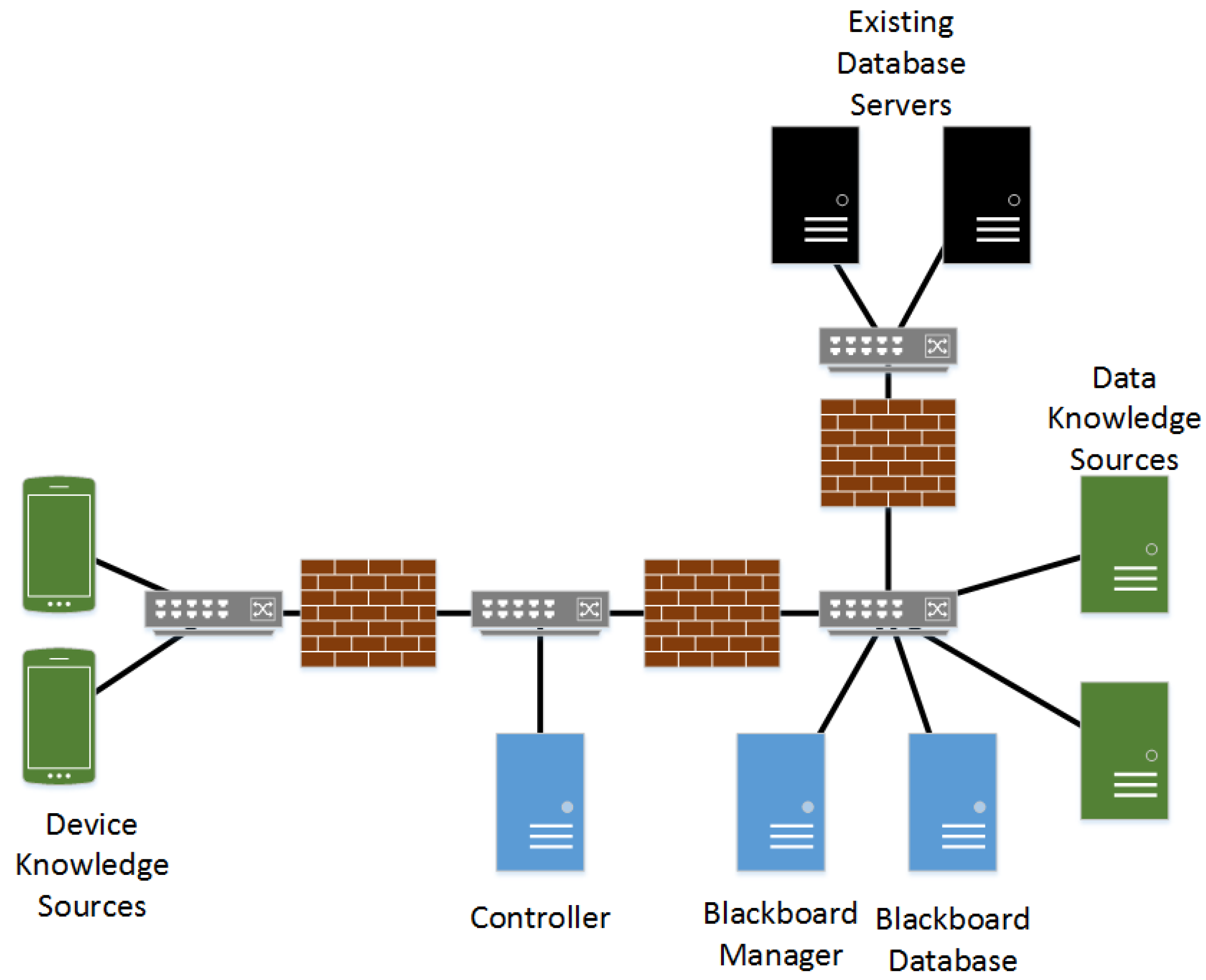
3. Case Study
4. Application
4.1. Architectural Quality Analysis
- Heterogeneity—Diversity of devices, especially in a healthcare environment, is a key way in which many facilities overcome problems with any one manufacturer’s design flaws.
- Reactivity—CPS are often deployed, both to monitor a situation as well as to react when one or more conditions change to help maintain some state or work towards a goal. For example, CPS enabled pacemakers have the potential to allow medical professionals to ensure faster heart rate convergence to ideal values [25]. However, without architectural level support for reactivity the CPS may be unable to adapt to the change in system priorities required to promptly notify physicians and implement their instructions.
- Adaptability—Physical variations like the number of floors, how much interference will be generated, locations of rooms, employee responsibilities, etc. will all vary for each installation of a CPS.
- Scalability—the size of each deployment of a CPS will vary significantly. Naturally, as the size of a CPS is scaled up so must the ability of the system to process data in parallel.
- Uncertainty—as many CPS are unable to fully capture the circumstances under which they are operating, a software architecture that is capable of dealing with an amount of uncertainty is desirable.
- Robustness—it is particularly important in a healthcare environment to ensure that the CPS be ready to carry out its responsibilities even in light of erroneous or missing data elements. This can partially be achieved through the use of redundancy, but should also be supported through the flexibility of the system to implement sophisticated algorithms that can utilize multiple sources of data to determine which elements are erroneous.
4.1.1. Control Loop Architecture
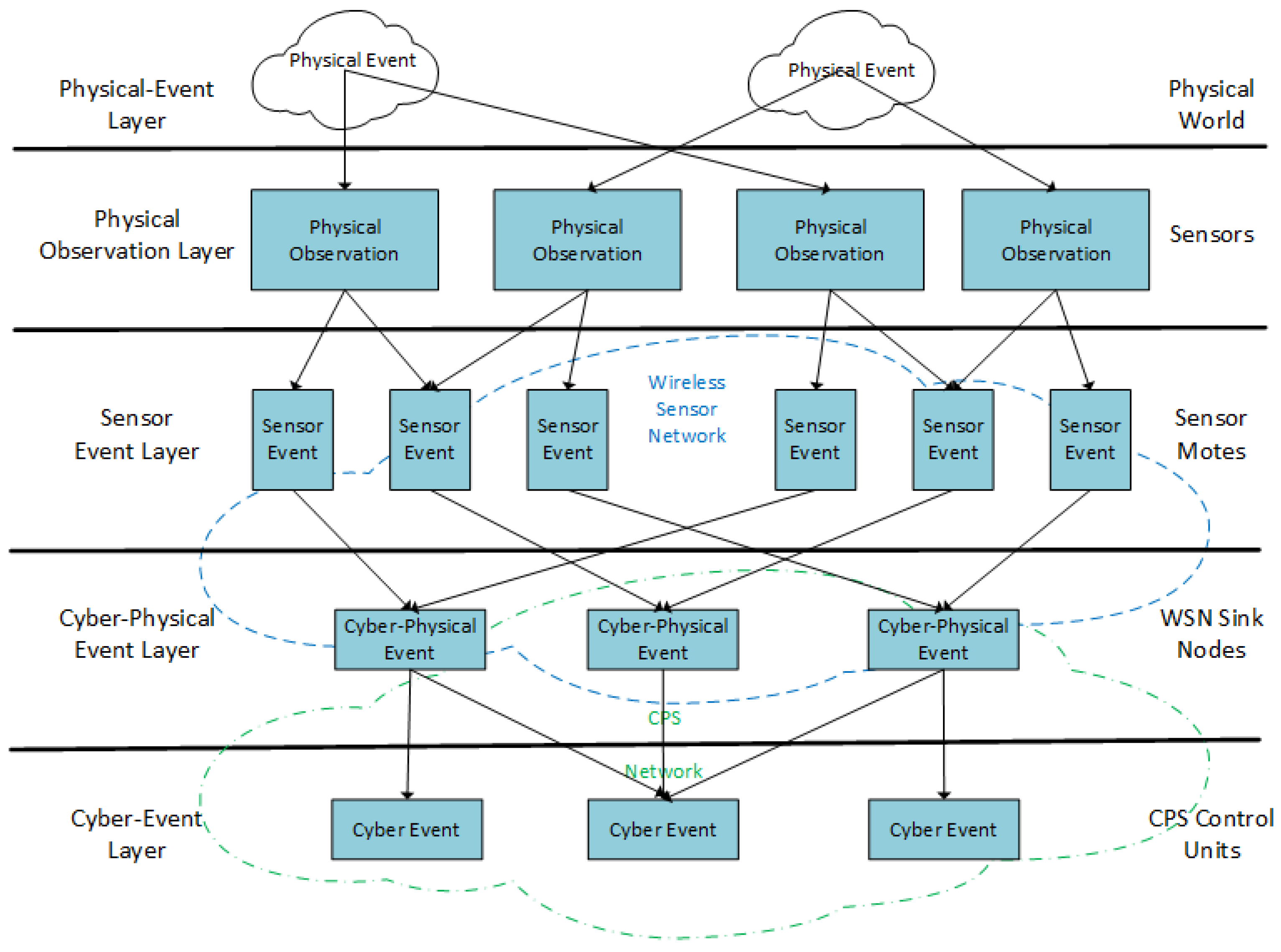
4.1.2. Layered Architecture
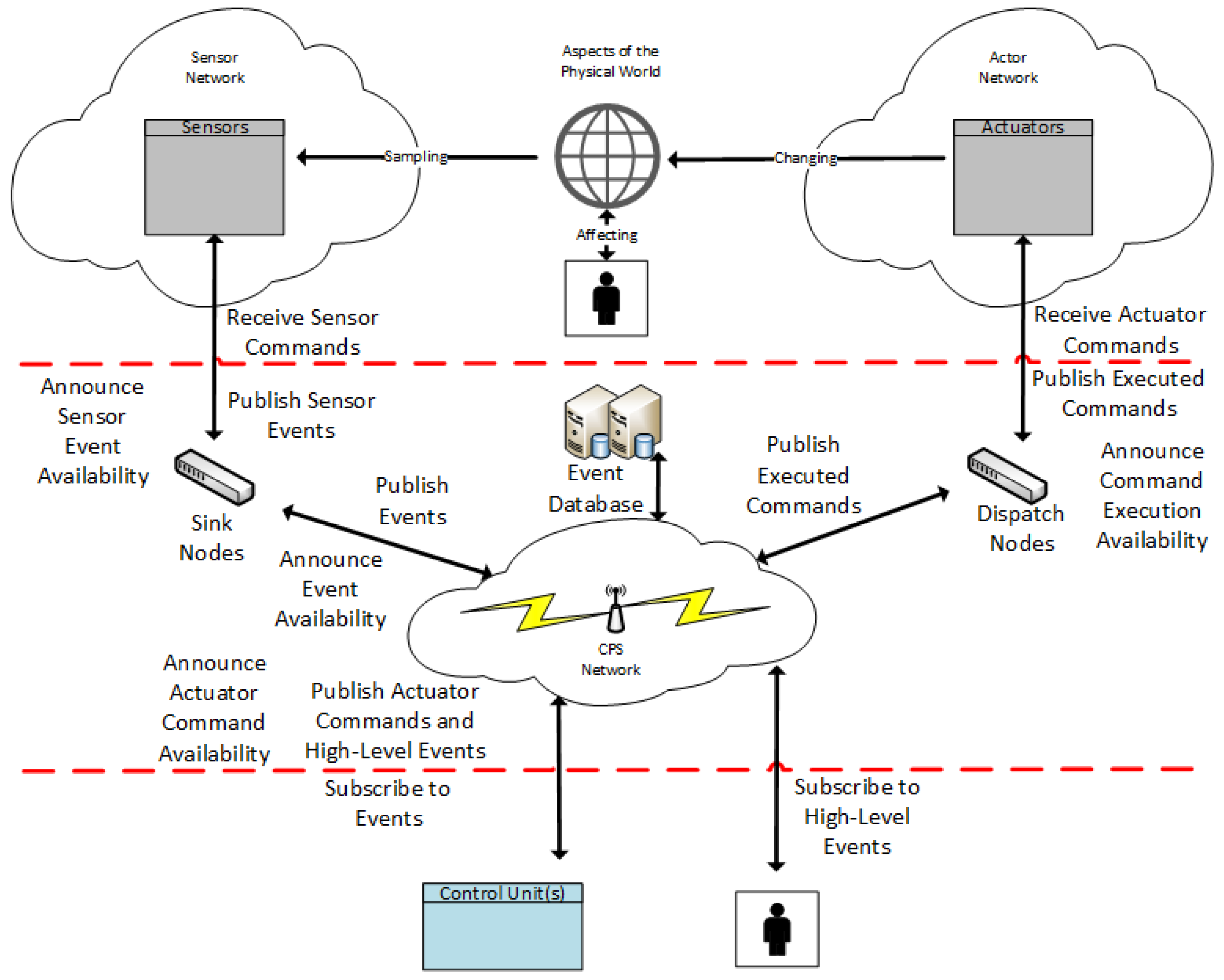
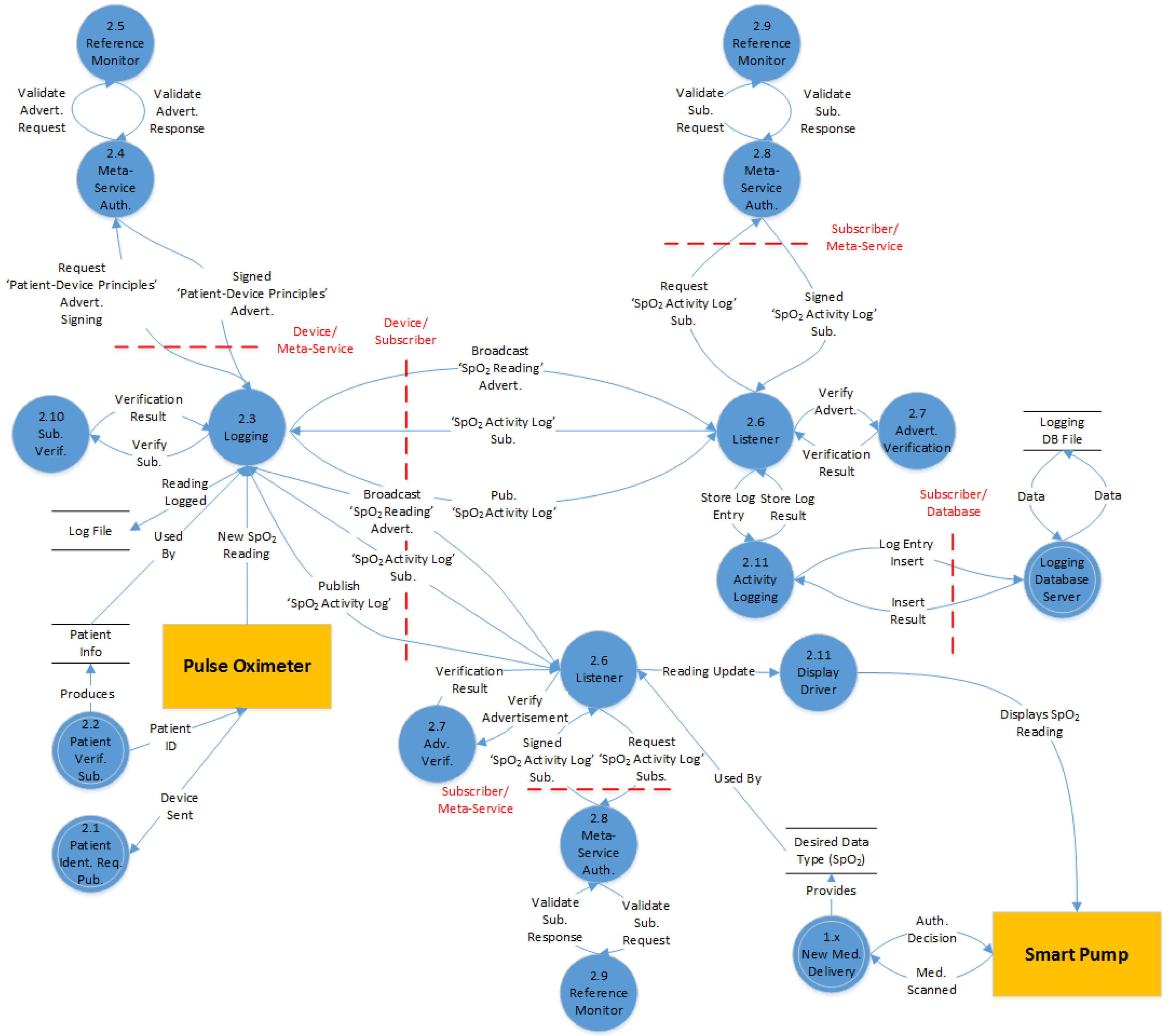
4.1.3. Publish-and-Subscribe Architecture
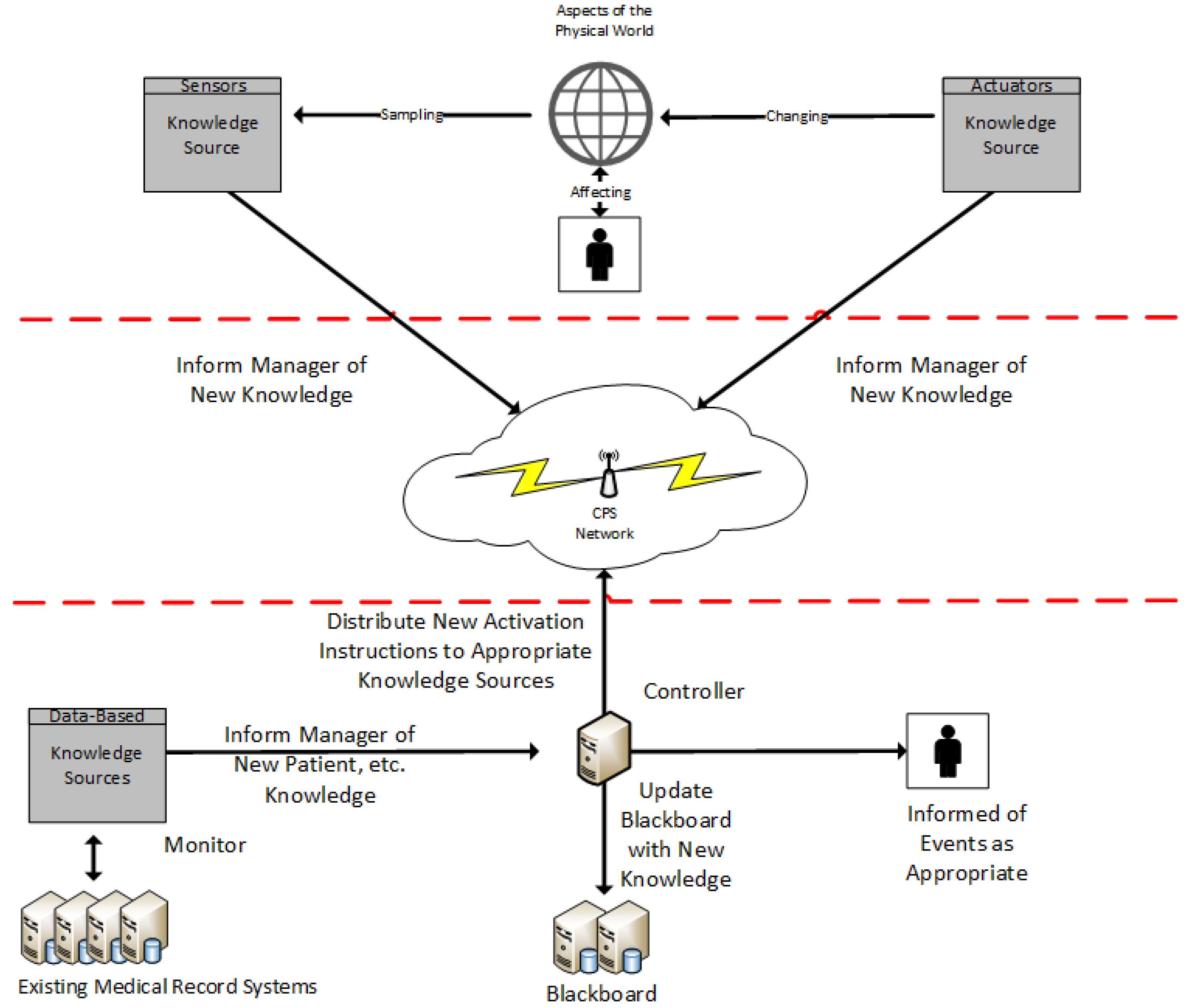
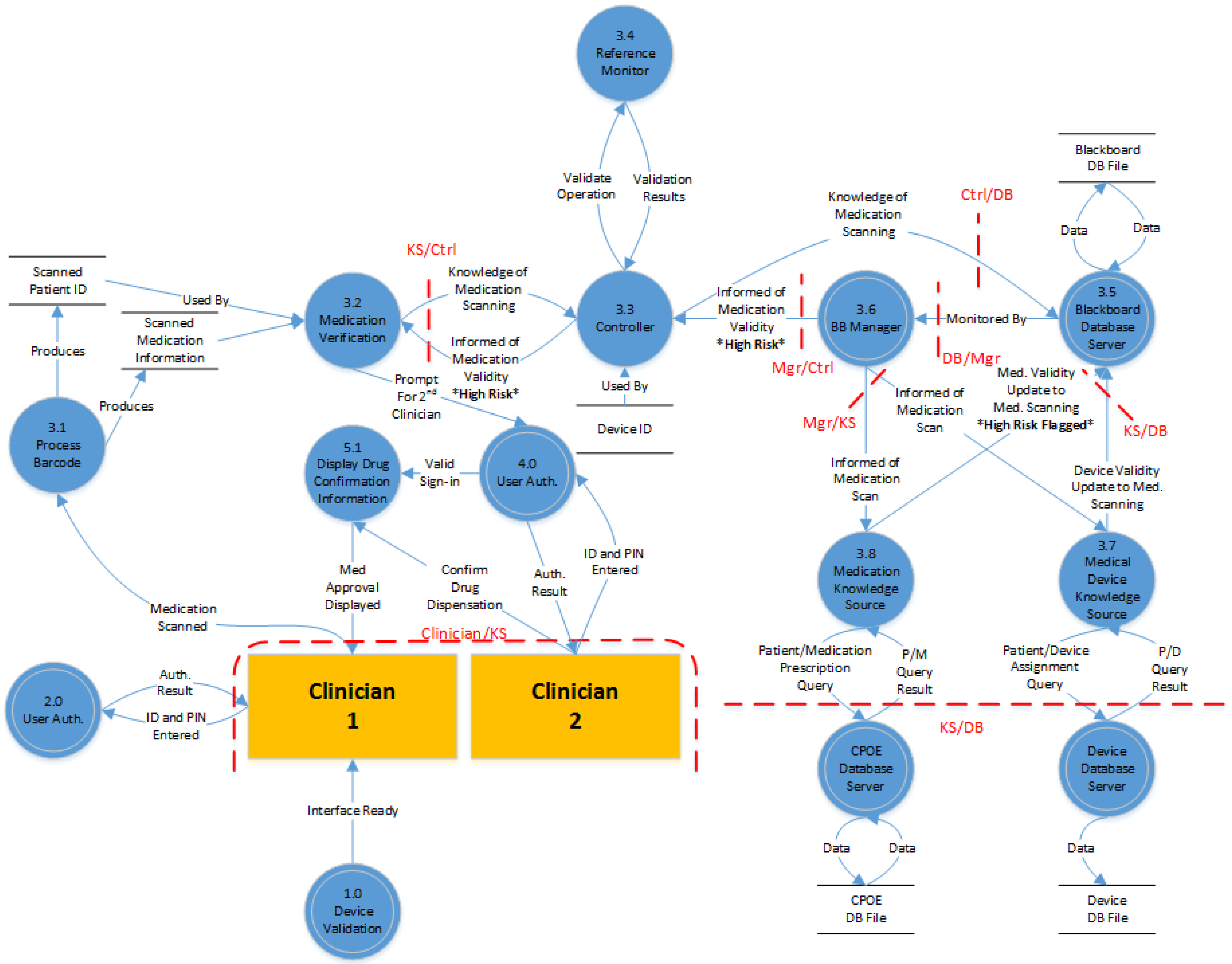
4.1.4. Blackboard Architecture
4.1.5. Qualitative Analysis of Candidate Architectures
4.2. Expected Functionality of CPS-Enabled Pumps
- Clinician authentication
- Delivery of a new medication
- Medication dosage is outside of soft/hard limit
- Logging of device activity
- Alarm/shutdown for detected device error
- Dispensation of a high risk medication
- Dispensation requires vital signs data gathered by another medical device.
4.3. Adapting Architectures with Secure Patterns
4.3.1. The EventGuard Pattern
4.3.2. The Secure Blackboard Pattern
4.4. Threat Modeling
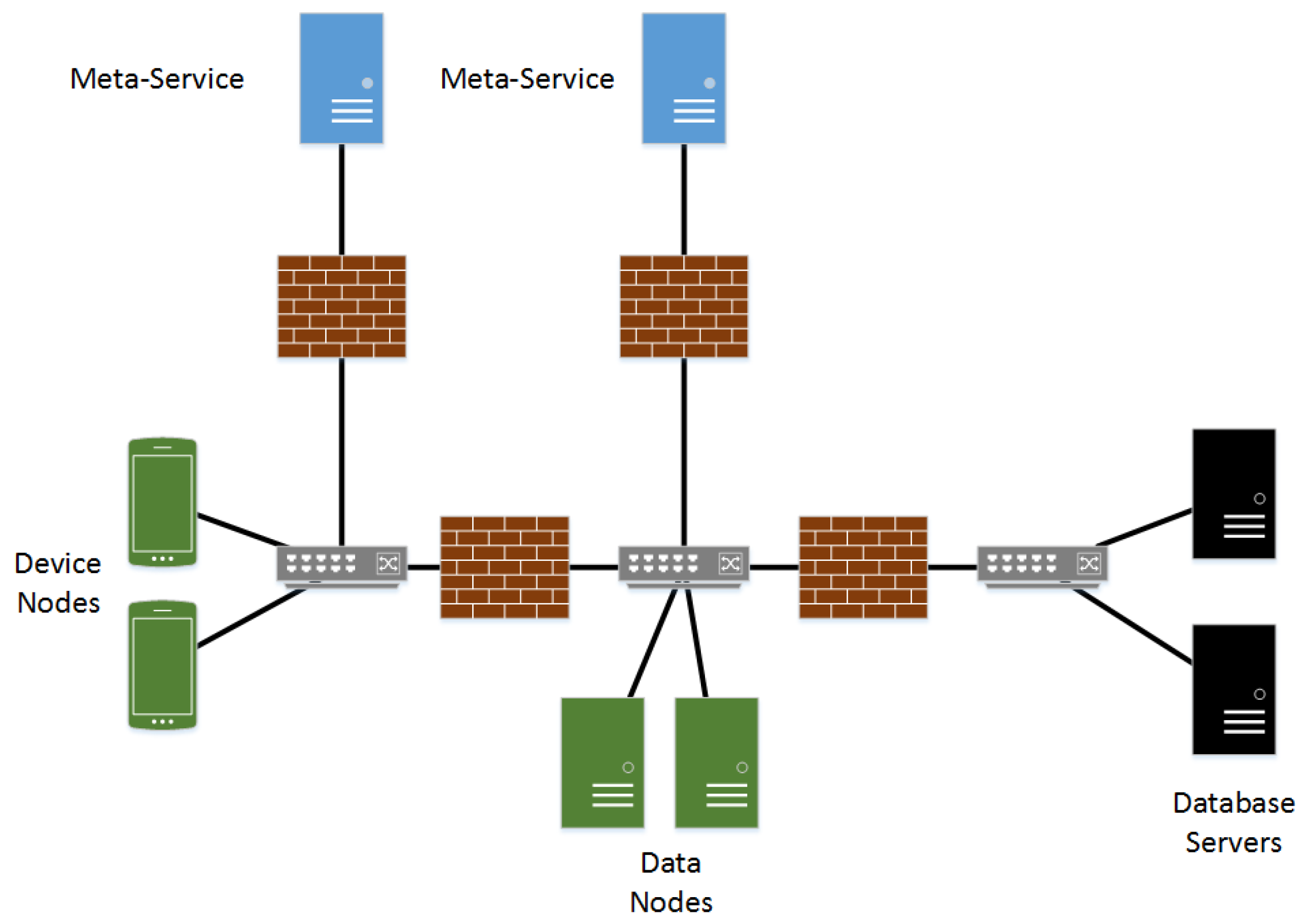
4.4.1. Flow Diagrams
4.4.2. STRIDE Threat Model
- Spoofing—An attacker utilizes illegally accessed credentials of some valid user to attack a system.
- Tampering—Malicious modification of data within a system. This may happen in transport, or it may involve stored data.
- Repudiation—An attack on the system that involves executing some action and then being able to deny being the source of the attack. This includes exploits that are able to be executed anonymously.
- Information disclosure—An especially dangerous type of attack in medical systems. It involves allowing an individual the ability to read sensitive information without permission.
- Denial of service—An attacker is able to make critical components of the architecture unavailable to valid users for some amount of time.
- Elevation of privilege—Utilizing a valid user account an attacker is able to attain administrative credentials or any similar exploit (An anonymous user attaining permissions of a regular user for example).
- Damage: How much damage would result?
- Reproducibility: How difficult is the execution?
- Exploitability: What is needed to execute the attack?
- Affected users: How many people would likely be affected?
- Discoverability: How hard is it to find the vulnerability?
5. Conclusions
5.1. Publish-and-Subscribe Architecture
5.2. Blackboard Architecture
5.3. Discussion
5.4. Future Work
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Marculescu, R.; Bogdan, P. Cyberphysical Systems: Workload Modeling and Design Optimization. IEEE Design Test Comput. 2011, 28, 78–87. [Google Scholar] [CrossRef]
- Mohamed, N.; Al-Jaroodi, J. A survey on service-oriented middleware for wireless sensor networks. Serv. Oriented Comput. Appl. 2011, 5, 71–85. [Google Scholar] [CrossRef]
- Agency for Healthcare Research and Quality. HCUP Fact Facts; Agency for Healthcare Research and Quality: Rockville, MD, USA, 2015.
- Ortman, J.; Velkoff, V. An Aging Nation: The Older Population in the United States; US Census Bureau: Washington, DC, USA, 2014; p. 6.
- World Health Organization. World Report on Disability; World Health Organization: Geneva, Switzerland, 2011. [Google Scholar]
- Hague, S.; Aziz, S.; Rahman, M. Review of Cyber-Physical System in Healthcare. Int. J. Distrib. Sens. Netw. 2014. [Google Scholar] [CrossRef]
- Tan, Y.; Goddard, S.; Pérez, L.C. A Prototype Architecture for Cyber-Physical Systems; ACM SIGBED Review: New York, NY, USA, 2008; Volume 5. [Google Scholar]
- Shnayder, V.; Chen, B.; Lorincz, K.; Jones, T.R.F.F.; Welsh, M. Sensor Networks for Medical Care. In Proceedings of the 3rd International Conference on Embedded Networked Sensor Systems, San Diego, CA, USA, 2–4 November 2005.
- Konstantas, D. Continuous Monitoring of Vital Constants for Mobile Users: The MobiHealth Approach. In Proceedings of the 25th International Conference of the IEEE Engineering and Medicine and Biology Society, Cancún, Mexico, 17–21 September 2003.
- Wood, A.D.; Stankovic, J.A.; Virone, G.; Selavo, L.; Selavo, L.; Cao, Q.; Doan, T.; Wu, Y.; Fang, L.; Stoleru, R. Context-aware wireless sensor networks for assisted living and residential monitoring. Netw. IEEE 2008, 22, 26–33. [Google Scholar] [CrossRef]
- Sasi, D.; Min, D. Medical Cyber Physical Systems and Bigdata Platforms. In Proceedings of the Medical Cyber Physical Systems Workshop, Philadelphia, PA, USA, 8 April 2013.
- Lu, C.; Fu, L. Robust location-aware activity recognition using wireless sensor network in an attentive home. IEEE Trans. Autom. Sci. Eng. 2009, 6, 598–609. [Google Scholar]
- Winograd, T. Architectures for Context. Hum. Comput. Interact. 2001, 16, 401–419. [Google Scholar] [CrossRef]
- Wu, P.; Peng, H.-K.; Zhu, J.; Zhang, Y. Senscare: Semi-Automatic Activity Summarization System for Elderly Care. In Mobile Computing, Applications, and Services; Springer: Berlin/Heidelberg, Germany, 2011; pp. 1–19. [Google Scholar]
- Kim, J.; Mosse, D. Generic Framework for Design, Modeling and Simulation of Cyber Physical Systems; ACM SIGBED Review: New York, NY, USA, 2008. [Google Scholar]
- Derler, P.; Lee, E.A.; Vincentelli, A.S. Modeling cyber-physical systems. Proc. IEEE 2012, 100, 13–28. [Google Scholar] [CrossRef]
- Sztipanovits, J.; Koutsoukos, X.; Karsai, G.; Kottenstette, N.; Antsaklis, P.; Gupta, V.; Goodwine, B.; Baras, J.; Wang, S. Toward a science of cyber-physical system integration. Proc. IEEE 2012, 100, 29–44. [Google Scholar] [CrossRef]
- Wolf, M.; van der Schaar, M.; Kim, H.; Xu, J. Caring Analytics for Adults with Special Needs. IEEE Des. Test 2015, 32, 35–44. [Google Scholar] [CrossRef]
- Radhakisan, B.; Gill, H. Cyber-physical systems. Impact Control Technol. 2011, 12, 161–166. [Google Scholar]
- Loria, G. HIPAA Breaches: Minimizing Risks and Patient Fears. Available online: http://www.softwareadvice.com/medical/industryview/hipaa-breaches-report-2015/ (accessed on 12 June 2016).
- Ohashi, K.; Dalleur, O.; Dykes, P.C.; Bates, D.W. Benefits and risks of using smart pumps to reduce medication error rates: A systematic review. Drug Saf. 2014, 37, 1011–1020. [Google Scholar] [CrossRef] [PubMed]
- Fields, M.; Peterman, J. Intravenous Medication Safety System Averts High-risk Medication Errors and Provides Actionable Data. Nurs. Adm. Q. 2005, 29, 78–87. [Google Scholar] [CrossRef] [PubMed]
- Trbovich, P.L.; Pinkney, S.; Cafazzo, J.A.; Easty, A.C. The impact of traditional and smart pump infusion technology on nurse medication administration performance in a simulated inpatient unit. Qual. Saf. Health Care 2010, 19, 430–434. [Google Scholar] [CrossRef] [PubMed]
- Infusion Pump Risk Reduction Strategies for Clinicians; Food and Drug Administration: Silver Spring, MD, USA, 2015. Available online: http://www.fda.gov/MedicalDevices/ProductsandMedicalProcedures/GeneralHospitalDevicesandSupplies/InfusionPumps/ucm205406.htm (accessed on 6 June 2016).
- Bogdan, P.; Jain, S.; Marculescu, R. Pacemaker control of Heart Rate Variability: A Cyber Physical System Perspective. ACM Trans. Embed. Comput. Syst. 2013, 12. [Google Scholar] [CrossRef]
- Tan, Y.; Vuran, M.C.; Goddard, S. Spatio-Temporal Event Model for Cyber-Physical Systems. In Proceedings of the IEEE International Conference on Distributed Computing Systems Workshops, Montreal, QC, Canada, 22–26 June 2009; pp. 44–50.
- Mudhakar, S.; Liu, L. Securing Publish-Subscribe Overlay Services with Eventguard. In Proceedings of the 12th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 7–10 November 2005; ACM: New York, NY, USA, 2005; pp. 289–298. [Google Scholar]
- Ortega-Arjona, J.; Fernandez, E. The Secure Blackboard Pattern. In Proceedings of the 15th Conference on Pattern Languages of Programs, Bavaria, Germany, 7–11 July 2010; ACM: New York, NY, USA, 2008; pp. 22–30. [Google Scholar]
- Meier, J.D.; Mackman, A.; Dunner, M.; Vasireddy, S.; Escamilla, R.; Murukan, A. Improving Web Application Security: Threats and Countermeasures; Microsoft Press: Redmond, DC, USA, 2003; pp. 45–66. [Google Scholar]
- Shostack, A. Experiences Threat Modeling at Microsoft. In Modeling Security Workshop; Lancaster University: Lancaster, UK, 2008. [Google Scholar]

| Control Loop | Layered | Publish and Subscribe | Blackboard | |
|---|---|---|---|---|
| Heterogeneity | − | + | + | + |
| Reactivity | + − | − | + | + |
| Adaptability | − | − | + | + |
| Scalability | + − | + | + − | + |
| Uncertainty | − | + | + − | + |
| Robustness | + − | + | + − | + |
| STRIDE Threat List | |||
|---|---|---|---|
| Attack | Control/Reasoning | DREAD Ranking | |
| Spoofing | |||
| An attacker compromises a device and utilizes previously authorized advertisements to publish information about patients the device is no longer assigned to. This may be a threat to patient data validity, but may also cause patient harm if spoofed data is relied upon by another medical device. | Compromising a device and obtaining the list of keys and signatures for its authorized advertisements is not easy and most likely would require disassembly of the device. However, flaws in the listener daemon could be utilized as part of an attack well. There is no mechanism to revoke approved publication rights either from the meta-service level, or by a more knowledgeable node. For example, the node that can communicate directly with the device assignment database likely will have the most up to date information on which patients a node should publish information about, yet has no ability to revoke a device’s approved publication signing rights about any patient it’s ever been approved to provide information for. Most likely it would be up to individual device manufacturers to issue unadvertise requests for previous patients when a medication for a new patient is scanned and approved. This can be a dangerous and unreliable way to implement protections. | Damage: | Critical |
| Reproducibility: | Important | ||
| Exploitability: | Important | ||
| Affected Users: | Important | ||
| Discoverability: | Critical | ||
| Overall: | Important | ||
| STRIDE Threat List | |||
|---|---|---|---|
| Attack | Control/Reasoning | DREAD Ranking | |
| Denial of Service | |||
| An attacker may attempt to deny service to health devices using a distributed denial of services attack. A successful attack could interrupt communications between devices and the blackboard database for an extended period. No permanent damage to data is likely, but any device that cannot function independently of CPS communication may fail and lead to patient injury. | This likely will be difficult to execute as both the physical and wireless public networks are closed systems without internet access. The likelihood of an attacker being able to introduce enough devices to the network to deny connections is unlikely. Techniques such disabling unused network ports, and limiting both the number of devices and which MAC addresses can be added to switching tables for networking equipment can help to limit this. Wireless network access can be restricted using a password-based encryption mechanism as well. Some networking equipment can not only restrict this access, but can generate a security violation if a device count/disallowed MAC is connected which can be used to alert network administrators. | Damage: | Medium |
| Reproducibility: | Important | ||
| Exploitability: | Medium | ||
| Affected Users: | Critical | ||
| Discoverability: | Critical | ||
| Overall: | Important | ||
| Publish and Subscribe | Blackboard | |
|---|---|---|
| Spoofing | 3 | 0 |
| Tampering | 3 | 0 |
| Repudiation | 0 | 0 |
| Information Disclosure | 1 | 1 |
| Denial of Service | 2 | 1 |
| Elevation of Privilege | 0 | 0 |
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Seifert, D.; Reza, H. A Security Analysis of Cyber-Physical Systems Architecture for Healthcare. Computers 2016, 5, 27. https://doi.org/10.3390/computers5040027
Seifert D, Reza H. A Security Analysis of Cyber-Physical Systems Architecture for Healthcare. Computers. 2016; 5(4):27. https://doi.org/10.3390/computers5040027
Chicago/Turabian StyleSeifert, Darren, and Hassan Reza. 2016. "A Security Analysis of Cyber-Physical Systems Architecture for Healthcare" Computers 5, no. 4: 27. https://doi.org/10.3390/computers5040027







