Secure Cyber Deception Architecture and Decoy Injection to Mitigate the Insider Threat
Abstract
:1. Introduction
2. Related Work
2.1. OF–RHM & RHM
2.2. HIDE
2.3. MT6D
2.4. DESIR
2.5. SDN Fingerprint Hopping
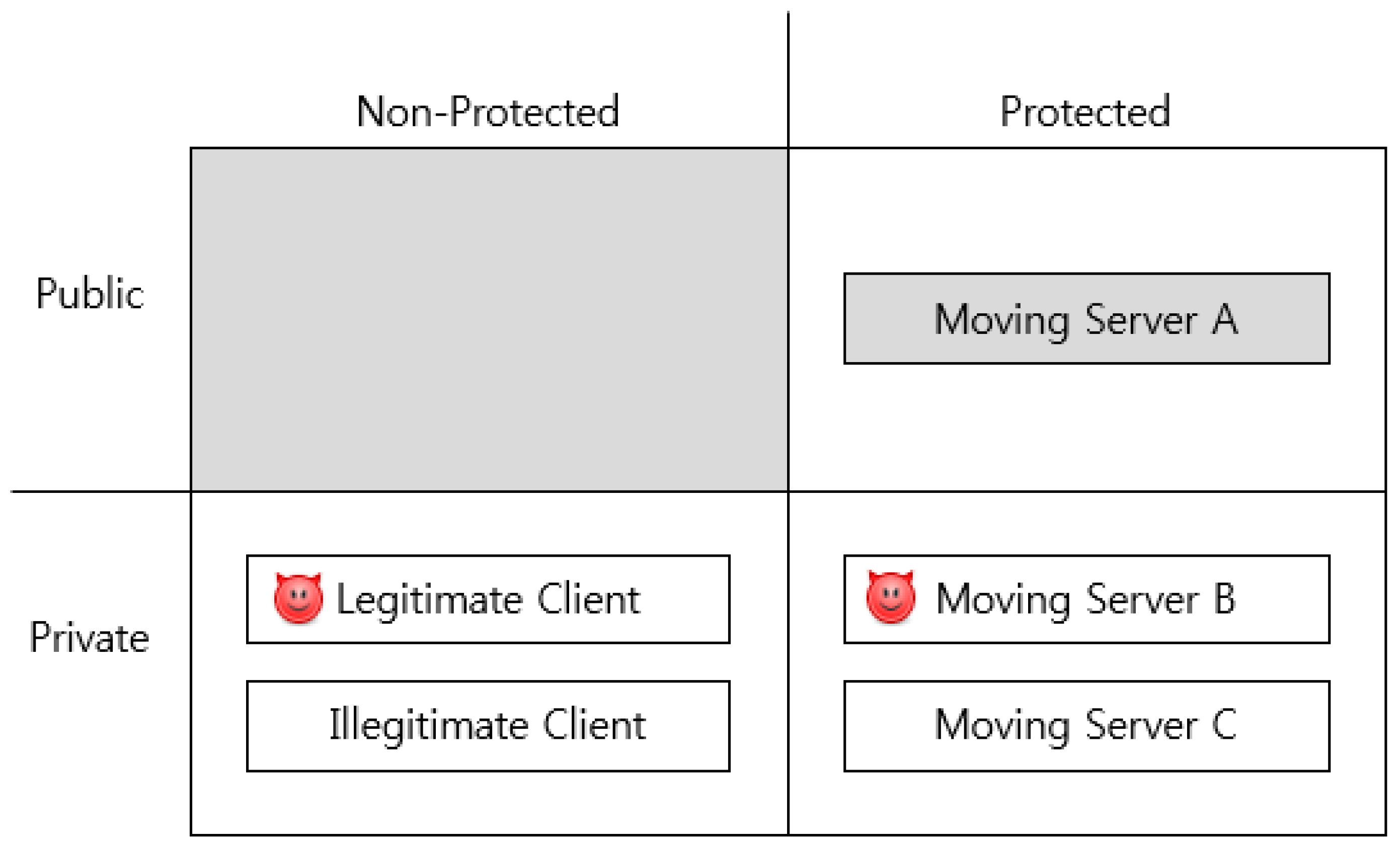
3. Threat Model
3.1. Protected Domain
3.2. Attack Model
4. Design
4.1. Security Requirement
- Requirement 1. The decoy traffic-injection mechanism should make it as difficult as possible to analyze the traffic to find the moving server by the insider who infected the legitimate client.
- Requirement 2. The decoy traffic-injection mechanism makes it difficult to analyze the traffic to find the moving server by an insider who penetrated the subnet on which the moving server exists.
- Requirement 3. The connection obfuscation mechanism makes it extremely difficult for an insider who infected the legitimate client to find the moving server through the network status and by active process monitoring.
- Requirement 4. The DHM should prevent the continuous tracking of the moving server through MAC (Media Access Control) address analysis and fingerprinting by the insider who penetrated the subnet on which the moving server exists.
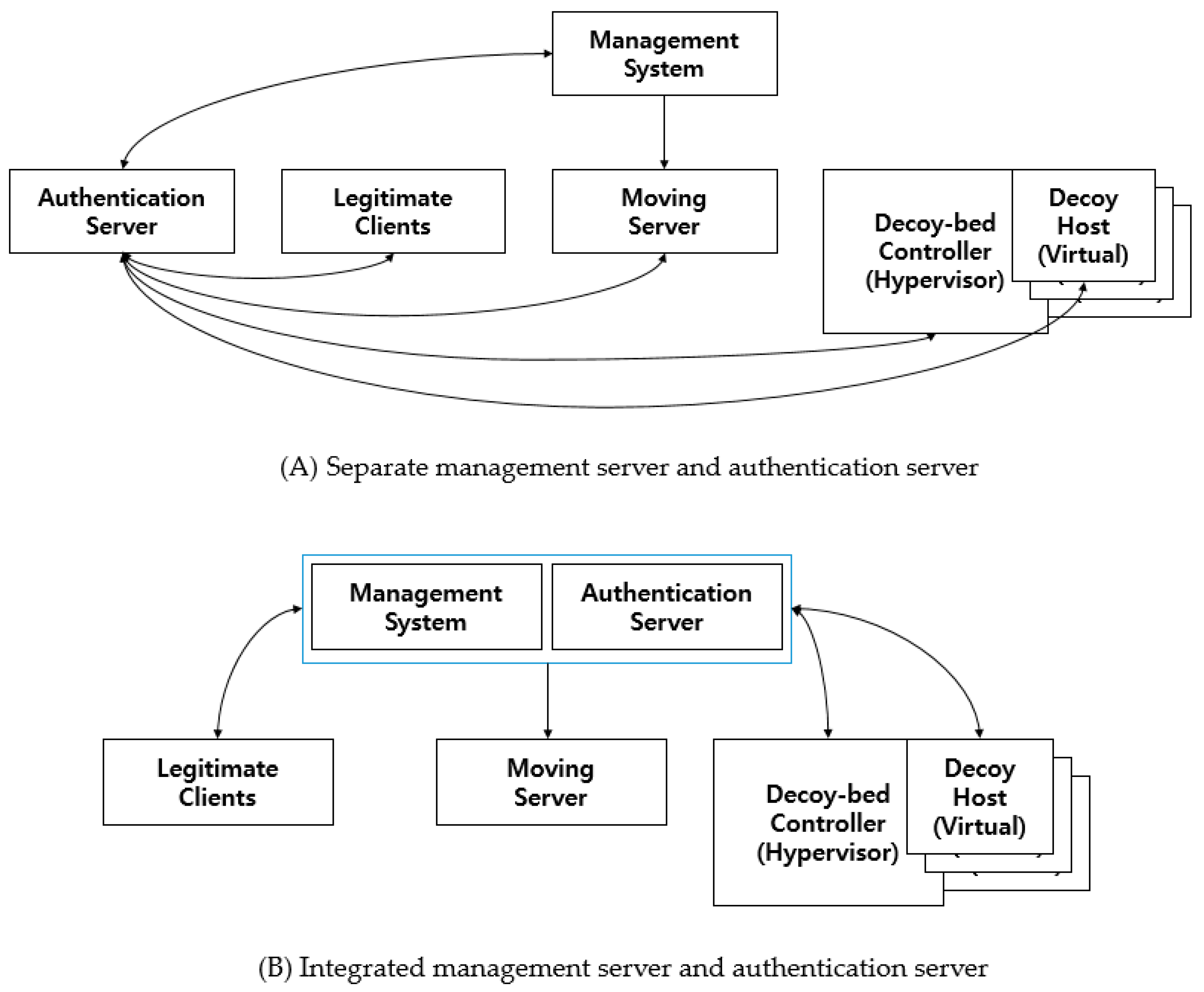
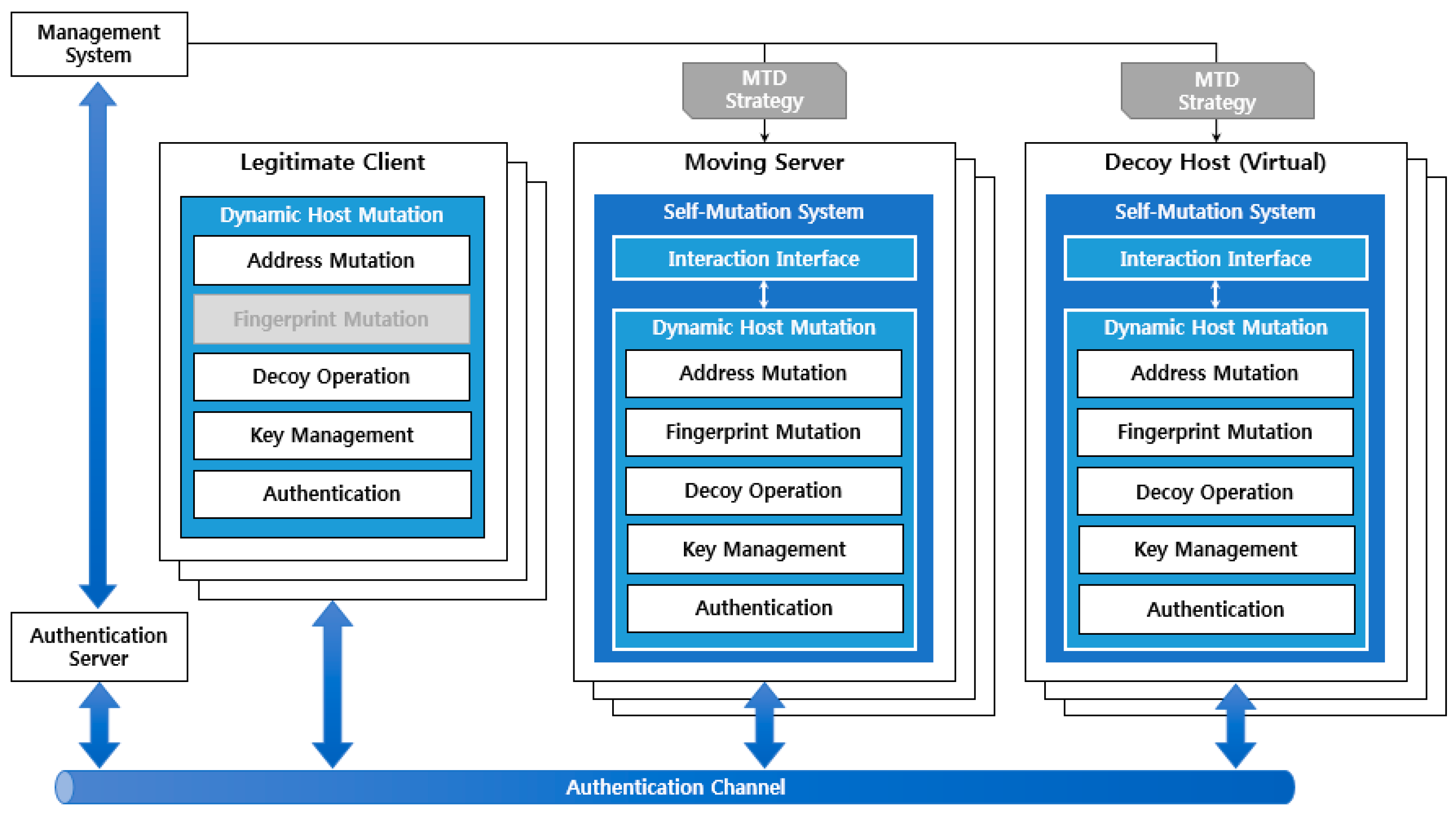
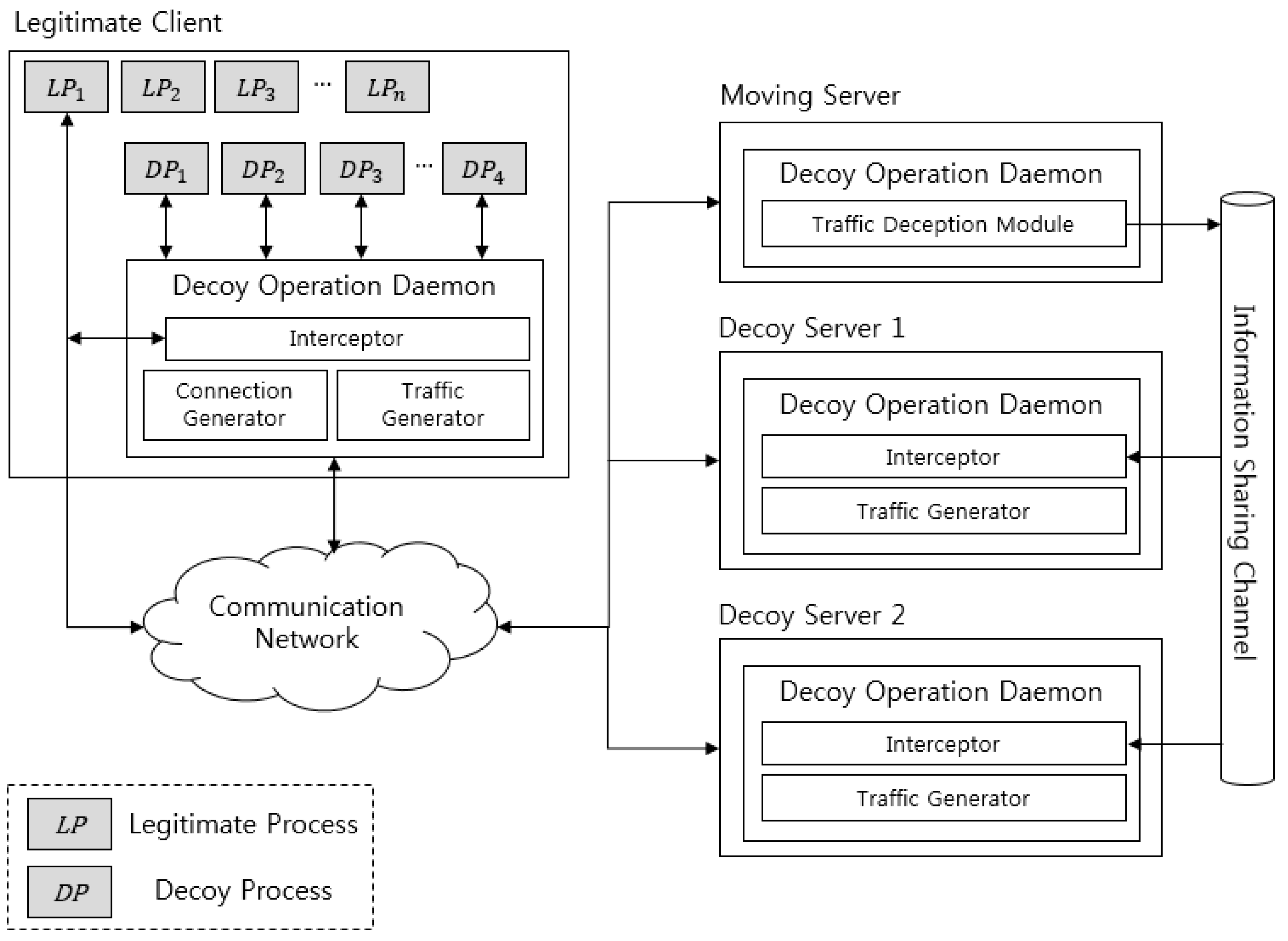
4.2. Architecture
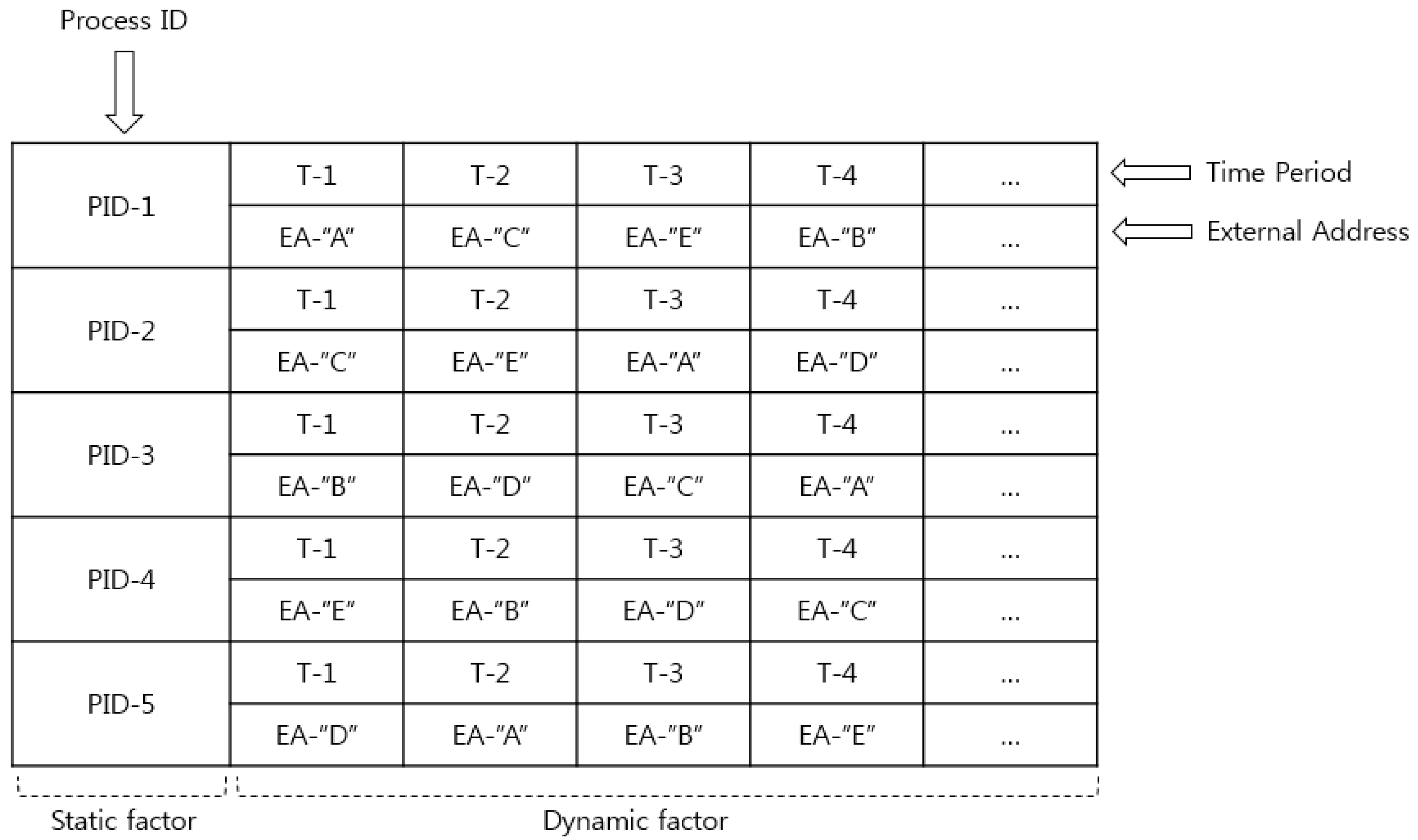
4.3. Decoy Injection
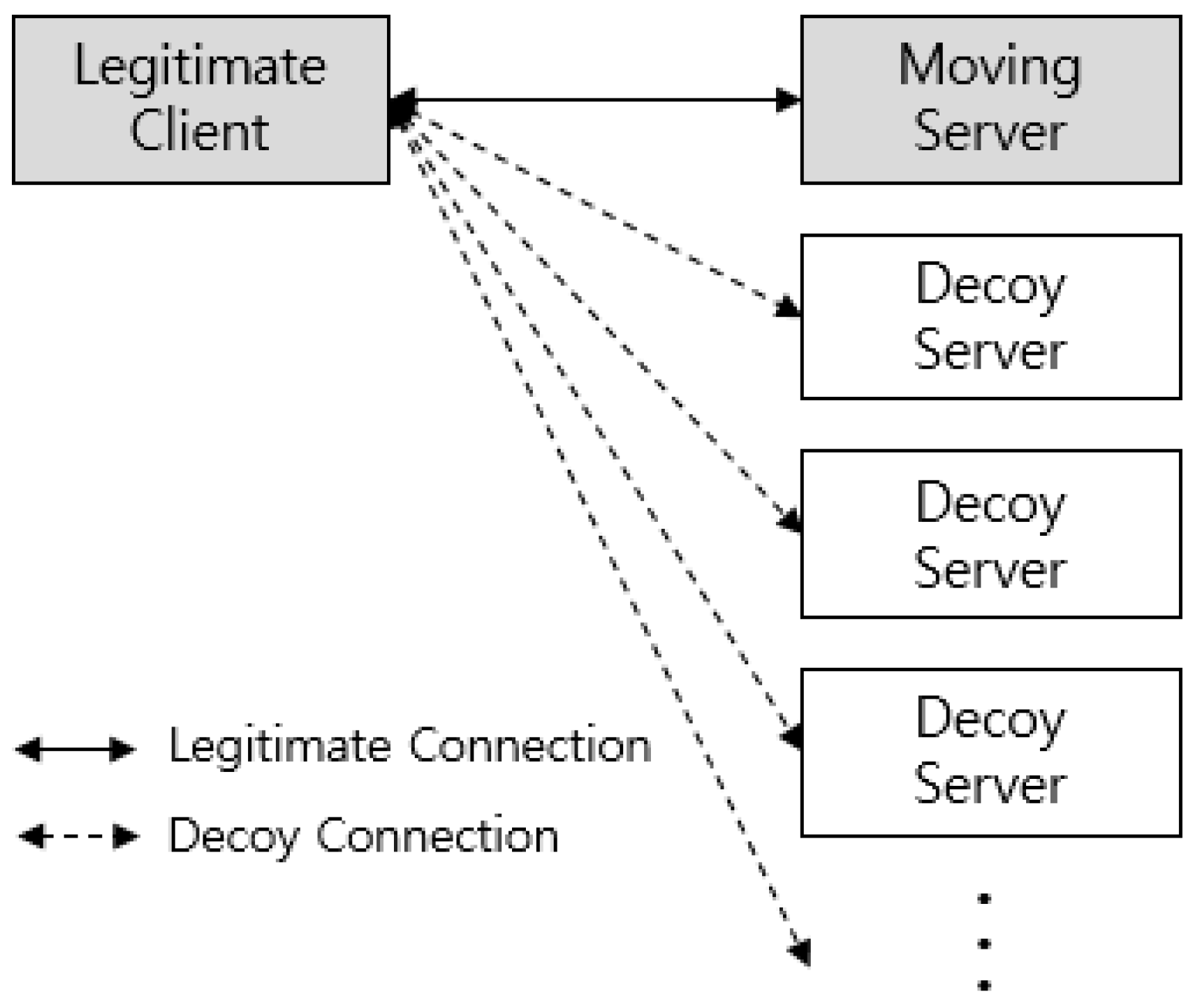
4.3.1. Connection Obfuscation
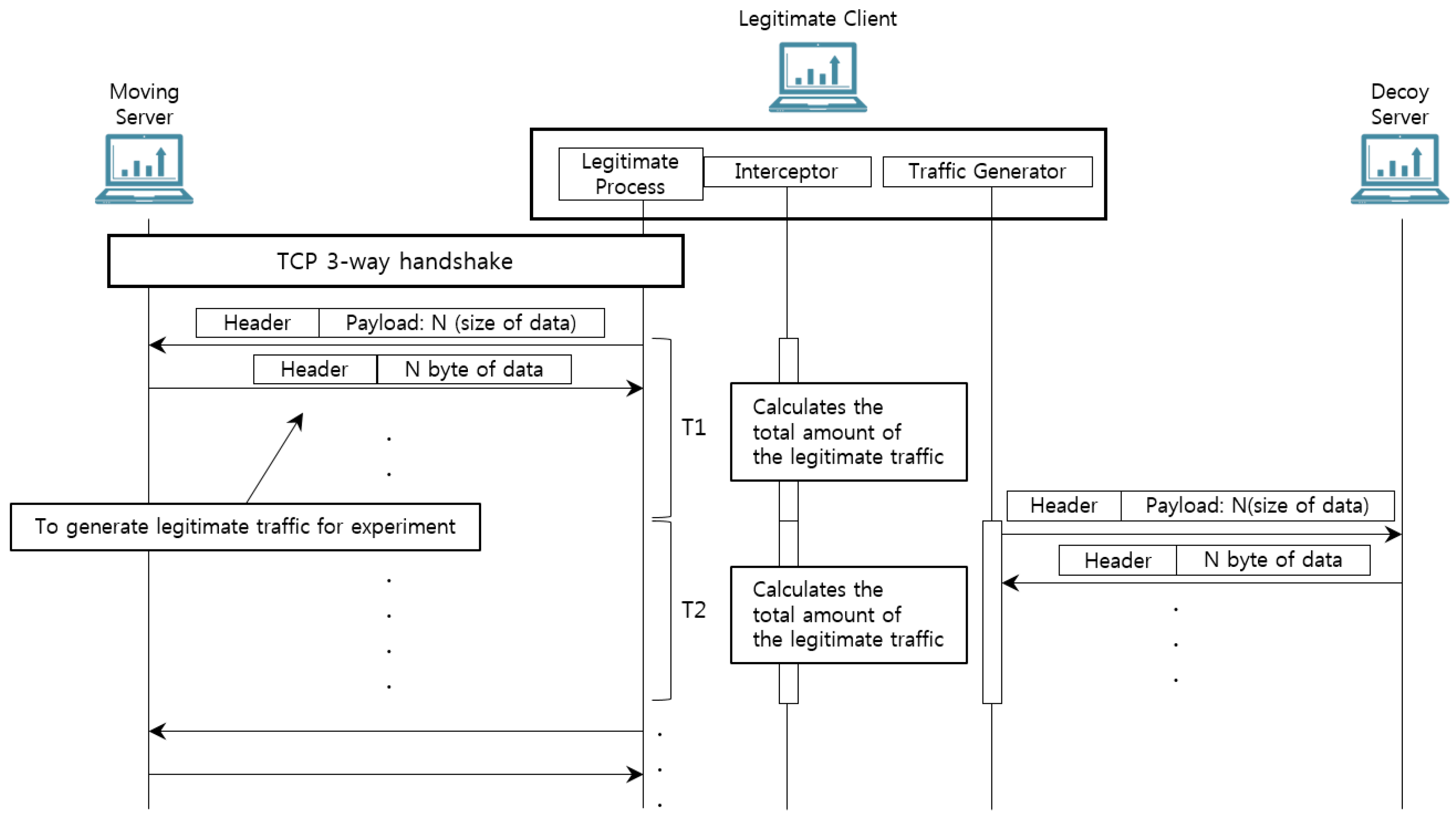
4.3.2. Decoy Traffic Injection
4.3.3. Limitation
5. Security Analysis
- -
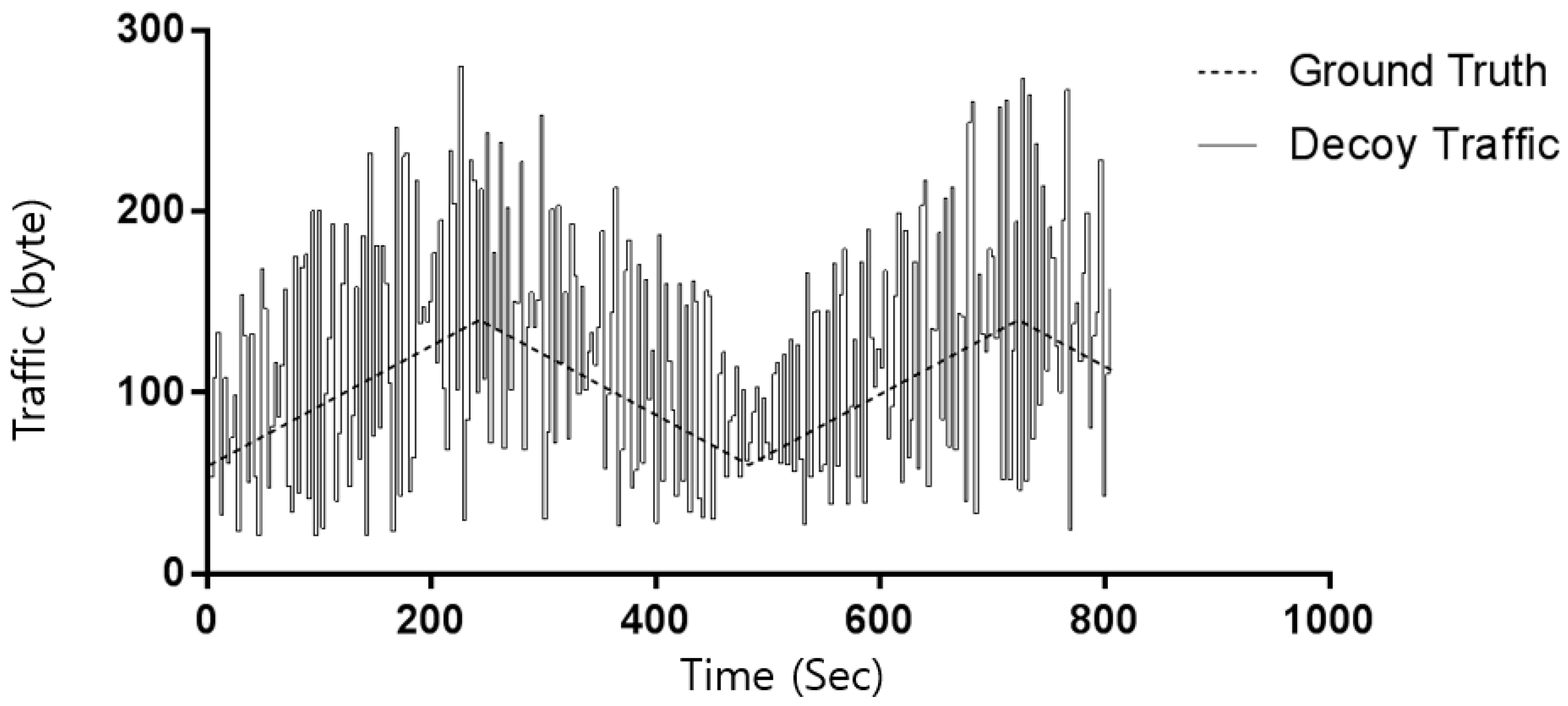
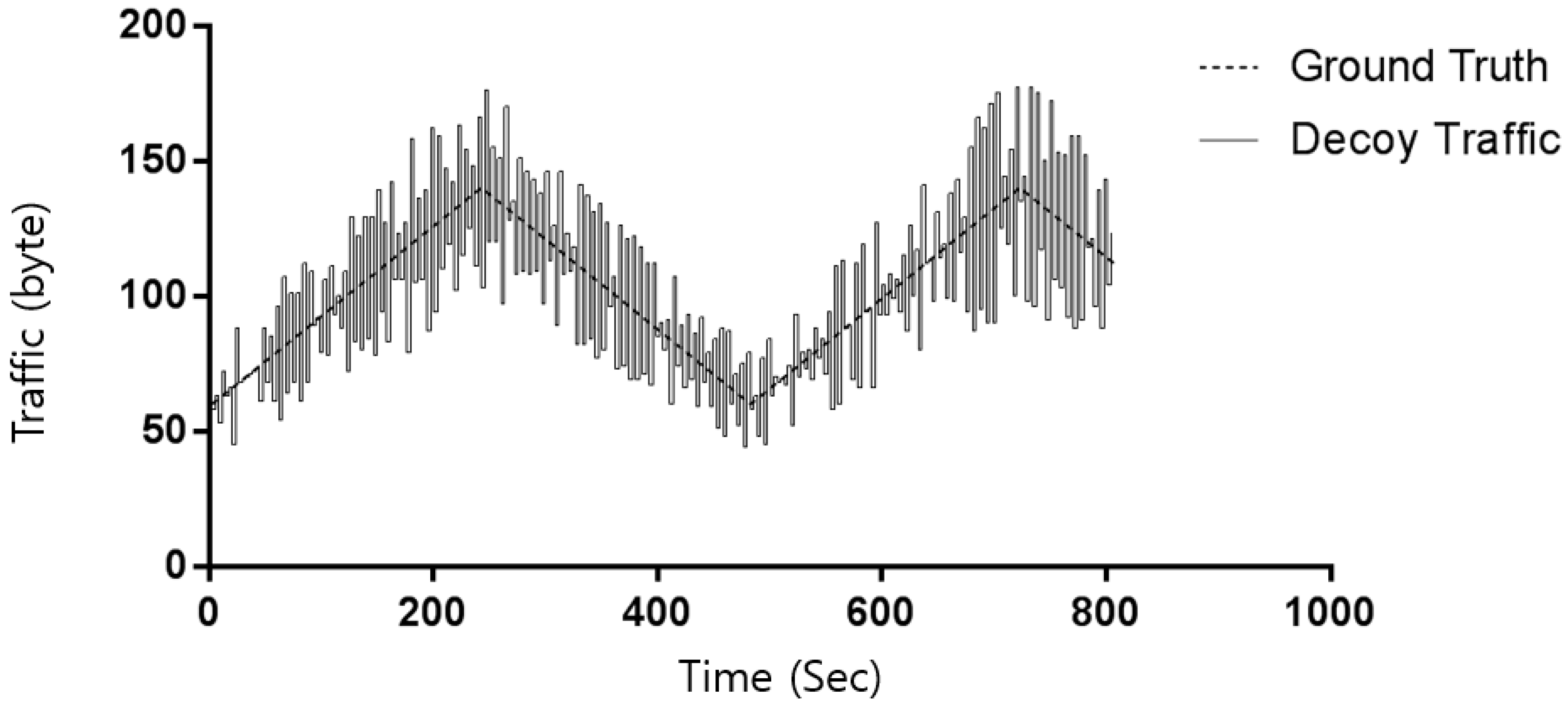
- Reqs. 1 and 2: In order to increase the cost of the traffic analysis necessary to detect the moving server, the proposed traffic-injection mechanism increases the amount of traffic that an attacker must analyze. In addition, because the decoy traffic is imitated by legitimate traffic, the analysis results of the insider are uncertain.
- -
- Req. 3: In Section 4.3.1, we analyzed various types of network state information and process information that an insider can use to detect the moving server. Based on the analysis results, we propose the connection-obfuscation mechanism based on the MTD concept of continuously changing the information used by the insider.
- -
- Req. 4: MTD technology to operate the gateway in front of the network switch is fatal to the threat of an attacker who has penetrated the subnet on which the moving server is located. Because the proposed DHM architecture is implemented in an end-point host, it is not easy for an insider to detect the moving server when it is protected by decoy servers and end-point hopping, even if there is an insider on the subnet. In addition, DHM can further increase the complexity of an attack by adding MAC address and OS fingerprinting information (e.g., TTL values, window sizes) to end-point hopping rules through mutual authentication between the entities participating in MTD.
6. Experiment
7. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- NSTC. Trustworthy Cyberspace: Strategic Plan for the Federal Cybersecurity R&D Program. National Science and Technology Council: Washington, DC, USA, 2011. [Google Scholar]
- Cai, G.; Wang, B.; Wang, X.; Yuan, Y.; Li, S. An introduction to network address shuffling. In Proceedings of the IEEE International Conference on Advanced Communication Technology (ICACT), Pyeongchang, Korea, 31 January–3 February 2016. [Google Scholar]
- Antonatos, S.; Akritidis, P.; Markatos, E.P.; Anagnostakis, K.G. Defending against hitlist worms using network address space randomization. Comput. Netw. 2007, 51, 3471–3490. [Google Scholar] [CrossRef]
- Kewley, D.; Fink, R.; Lowry, J.; Dean, M. Dynamic approaches to thwart adversary intelligence gathering. In Proceedings of the DARPA Information Survivability Conference & Exposition II, Anaheim, CA, USA, 12–14 June 2001. [Google Scholar]
- Rahman, M.A.; Manshaei, M.H.; Al-Shaer, E. A game-theoretic approach for deceiving remote operating system fingerprinting. In Proceedings of the IEEE Communications and Network Security (CNS), National Harbor, MD, USA, 14–16 October 2013. [Google Scholar]
- Kaynar, K.; Sivrikaya, F. Distributed attack graph generation. IEEE Trans. Dependable Secur. Comput. 2016, 13, 519–532. [Google Scholar] [CrossRef]
- Cook, K.; Shaw, T.; Hawrylak, P.; Hale, J. Scalable Attack Graph Generation. In Proceedings of the 11th ACM Annual Cyber and Information Security Research Conference, Oak Redge, TN, USA, 5–7 April 2016. [Google Scholar]
- Johnson, P.; Vernotte, A.; Ekstedt, M.; Lagerström, R. pwnpr3d: An attack-graph-driven probabilistic threat-modeling approach, Availability. In Proceedings of the IEEE International Conference on the Reliability and Security (ARES), Salzburg, Austria, 31 August–2 September 2016. [Google Scholar]
- Jafarian, J.H.; Al-Shaer, E.; Duan, Q. Openflow random host mutation: Transparent moving target defense using software defined networking. In Proceedings of the ACM Workshop on Hot Topics in Software Defined Networks, Helsinki, Finland, 13 August 2012. [Google Scholar]
- Al-Shaer, E.; Duan, Q.; Jafarian, J.H. Random Host Mutation for Moving Target Defense. In SecureComm 2012: Security and Privacy in Communication Networks; Springer: Berlin/Heidelberg, Germany, 2012; pp. 310–327. [Google Scholar]
- Jafarian, J.H.; Niakanlahiji, A.; Al-Shaer, E.; Duan, Q. Multi-Dimensional Host Identity Anonymization for Defeating Skilled Attackers. In Proceedings of the ACM CCS Workshop on Moving Target Defense, Vienna, Austria, 24 October 2016. [Google Scholar]
- Dunlop, M.; Groat, S.; Urbanski, W.; Marchany, R.; Tront, J. Mt6d: A moving target ipv6 defense. In Proceedings of the IEEE Military Communications Conference, Baltimore, MD, USA, 7–10 November 2011. [Google Scholar]
- Sun, J.; Sun, K. DESIR: Decoy-enhanced seamless IP randomization. In Proceedings of the 35th Annual IEEE International Conference on Computer Communications (INFOCOM), San Francisco, CA, USA, 10–14 April 2016. [Google Scholar]
- Zhao, Z.; Liu, F.; Gong, D. An SDN-Based Fingerprint Hopping Method to Prevent Fingerprinting Attacks. Secur. Commun. Netw. 2017, 2017. [Google Scholar] [CrossRef]
- Jafarian, J.H.; Al-Shaer, E.; Duan, Q. Spatio-temporal address mutation for proactive cyber agility against sophisticated attackers. In Proceedings of the ACM CCS Workshop on Moving Target Defense, Scottsdale, AZ, USA, 7 November 2014. [Google Scholar]
- Jafarian, J.H.; Al-Shaer, E.; Duan, Q. Adversary aware IP address randomization for proactive agility against sophisticated attackers. In Proceedings of the IEEE International Conference on Computer Communications (INFOCOM), Kowloon, Hong Kong, China, 26 April–1 May 2015. [Google Scholar]
- Jafarian, J.H.; Al-Shaer, E.; Duan, Q. An effective address mutation approach for disrupting reconnaissance attacks. IEEE Trans. Inf. Forensics Secur. 2015, 10, 2562–2577. [Google Scholar] [CrossRef]
- Clark, A.; Sun, K.; Poovendran, R. Effectiveness of IP address randomization in decoy-based moving target defense. In Proceedings of the IEEE 52nd Annual Conference on Decision and Control (CDC), Florence, Italy, 10–13 December 2013. [Google Scholar]
- Ma, D.; Lei, C.; Wang, L.; Zhang, H.; Xu, Z.; Li, M. A Self-adaptive Hopping Approach of Moving Target Defense to thwart Scanning Attacks. In Information and Communications Security; Springer: Berlin/Heidelberg, Germany, 2016; pp. 39–53. [Google Scholar]
- Shi, L.; Jia, C.; Lü, S.; Liu, Z. Port and address hopping for active cyber-defense. In Intelligence and Security Informatics; Springer: Berlin/Heidelberg, Germany, 2007; pp. 295–300. [Google Scholar]
- Luo, Y.B.; Wang, B.S.; Wang, X.F.; Hu, X.F.; Cai, G.L.; Sun, H. RPAH: Random port and address hopping for thwarting internal and external adversaries. In Proceedings of the IEEE Trust-com/BigDataSE/ISPA, Helsinki, Finland, 20–22 August 2015. [Google Scholar]
- Nagpal, B.; Chauhan, N.; Singh, N. A Survey on the Detection of SQL Injection Attacks and Their Countermeasures. J. Inf. Process. Syst. 2017, 13, 689–702. [Google Scholar]
- Rathore, S.; Sharma, P.K.; Park, J.H. XSSClassifier: An Efficient XSS Attack Detection Approach Based on Machine Learning Classifier on SNSs. J. Inf. Process. Syst. 2017, 13, 1014–1028. [Google Scholar] [CrossRef]
- Albayram, Y.; Khan, M.M.H.; Bamis, A.; Kentros, S.; Nguyen, N.; Jiang, R. Designing challenge questions for location-based authentication systems: A real-life study. Hum. Centric Comput. Inf. Sci. 2015, 5, 1–28. [Google Scholar] [CrossRef]
- Im, H.; Kang, K.; Park, J.H. Certificateless based public key infrastructure using a DNSSEC. J. Converg. 2015, 6, 26–33. [Google Scholar]
- Bowen, B.M.; Kemerlis, V.P.; Prabhu, P.; Keromytis, A.D.; Stolfo, S.J. Automating the injection of believable decoys to detect snooping. In Proceedings of the ACM Conference on Wireless Network Security, Hoboken, NJ, USA, 22–24 March 2010. [Google Scholar]
- Bowen, B.M.; Kemerlis, V.P.; Prabhu, P.; Keromytis, A.D.; Stolfo, S.J. A system for generating and injecting indistinguishable network decoys. J. Comput. Secur. 2012, 20, 199–221. [Google Scholar] [CrossRef]
- Fan, W.; Fernández, D.; Du, Z. Versatile virtual honeynet management framework. IET Inf. Secur. 2016, 11, 38–45. [Google Scholar] [CrossRef]
- Achleitner, S.; Porta, T.L.; McDaniel, P.; Sugrom, S.; Krishnamurthy, S.V.; Chadha, R. Cyber Deception: Virtual Networks to Defend Insider Reconnaissance. In Proceedings of the ACM CCS International Workshop on Managing Insider Security Threats, Vienna, Austria, 28 October 2016. [Google Scholar]

| Research | Network Address Mutation | Fingerprint Mutation | Decoy Node Operation |
|---|---|---|---|
| OF–RHM & RHM | ○ | ||
| HIDE | ○ | ○ | ○ |
| MT6D | ○ | ||
| DESIR | ○ | ○ | |
| SDN-Based Fingerprint Hopping | ○ | ○ |
| Subsystem | Module | Description |
|---|---|---|
| Network Address Mutation | Crypto Function-Based Address Generation | Address generation function using a cryptographic algorithm for address synchronization without interactions between entities. |
| The algorithm that generates the same output using the same input and correct output values only for entities sharing symmetric keys. | ||
| IP Collision Detection | Conflict detection for addresses generated by each host. | |
| Connection Migration | Connection migration to prevent a service disruption while a host address is being changed. | |
| Network Address Shuffling | Efficient MAC learning and updating ARP table while a host address is being changed. | |
| Activity Monitor | Monitoring the status of connections between a server and clients. | |
| Fingerprint Mutation | OS Fingerprint Mutation | Translating various fingerprints collected through network scanning by an attacker. |
| Fault Management | Forecasting any faults due to a fingerprint mutation. | |
| Decoy Operation | Node Generation | Creating virtual nodes to increase the active address space to prevent recognition of the target by an attacker. |
| Traffic Generation | Creating decoy traffic to prevent recognition of the target when an attacker who penetrates the internal network analyzes network traffic. | |
| Connection Generator | Creating decoy connections to prevent recognition of the target by analyzing network status by an attacker who penetrates the internal network. | |
| Context Awareness | Collecting attributes to create decoy nodes similar to moving servers. | |
| Host Authentication | Certificate Based Auth. | Entity authentication based on certificates. |
| Symmetric Key Based Auth. | Entity authentication based on a symmetric key. | |
| Key Management | Key Distribution | Session key distribution used for address generation. |
| Key Update | Ensuring session key safety. | |
| Key Revocation |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Park, K.; Woo, S.; Moon, D.; Choi, H. Secure Cyber Deception Architecture and Decoy Injection to Mitigate the Insider Threat. Symmetry 2018, 10, 14. https://doi.org/10.3390/sym10010014
Park K, Woo S, Moon D, Choi H. Secure Cyber Deception Architecture and Decoy Injection to Mitigate the Insider Threat. Symmetry. 2018; 10(1):14. https://doi.org/10.3390/sym10010014
Chicago/Turabian StylePark, Kyungmin, Samuel Woo, Daesung Moon, and Hoon Choi. 2018. "Secure Cyber Deception Architecture and Decoy Injection to Mitigate the Insider Threat" Symmetry 10, no. 1: 14. https://doi.org/10.3390/sym10010014





