A Robust Image Watermarking Technique Based on DWT, APDCBT, and SVD
Abstract
:1. Introduction
2. APDCBT and SVD
2.1. APDCBT
2.2. SVD
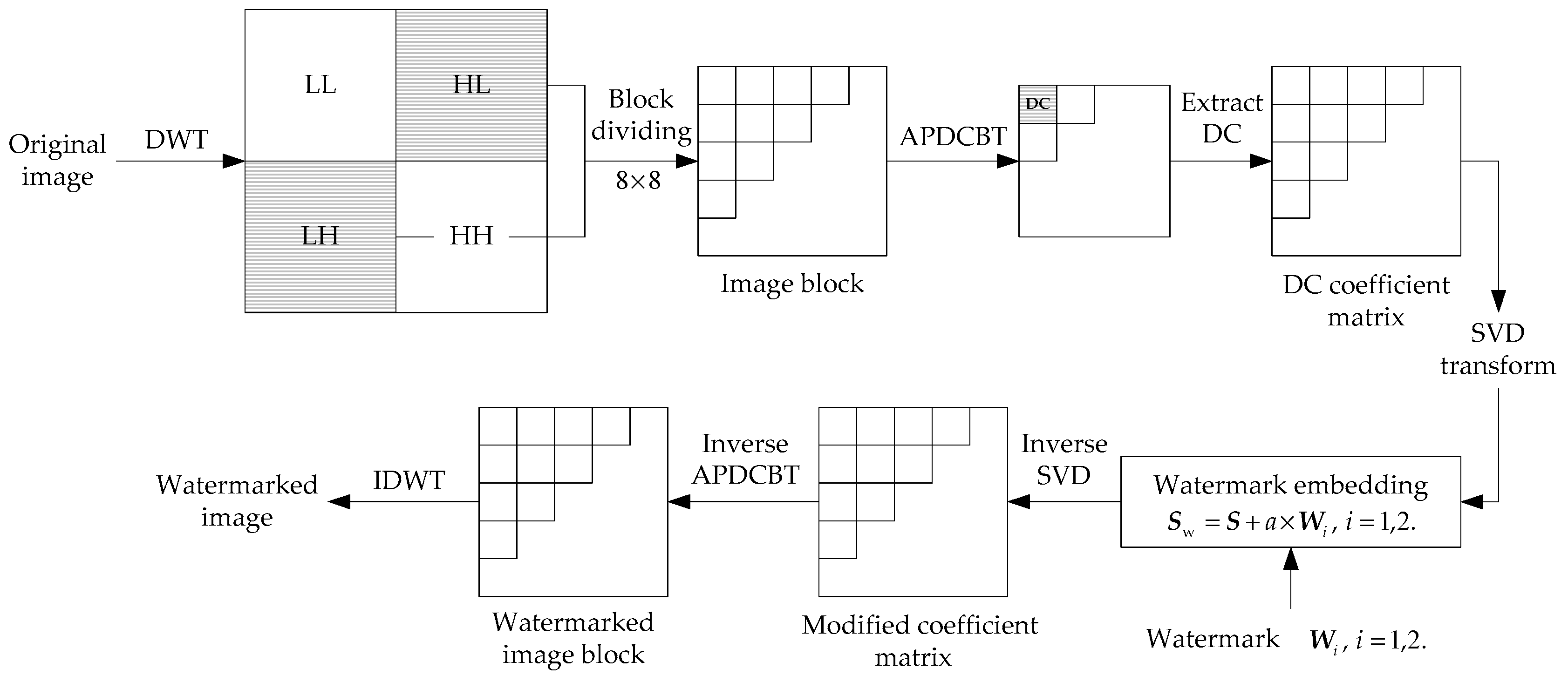
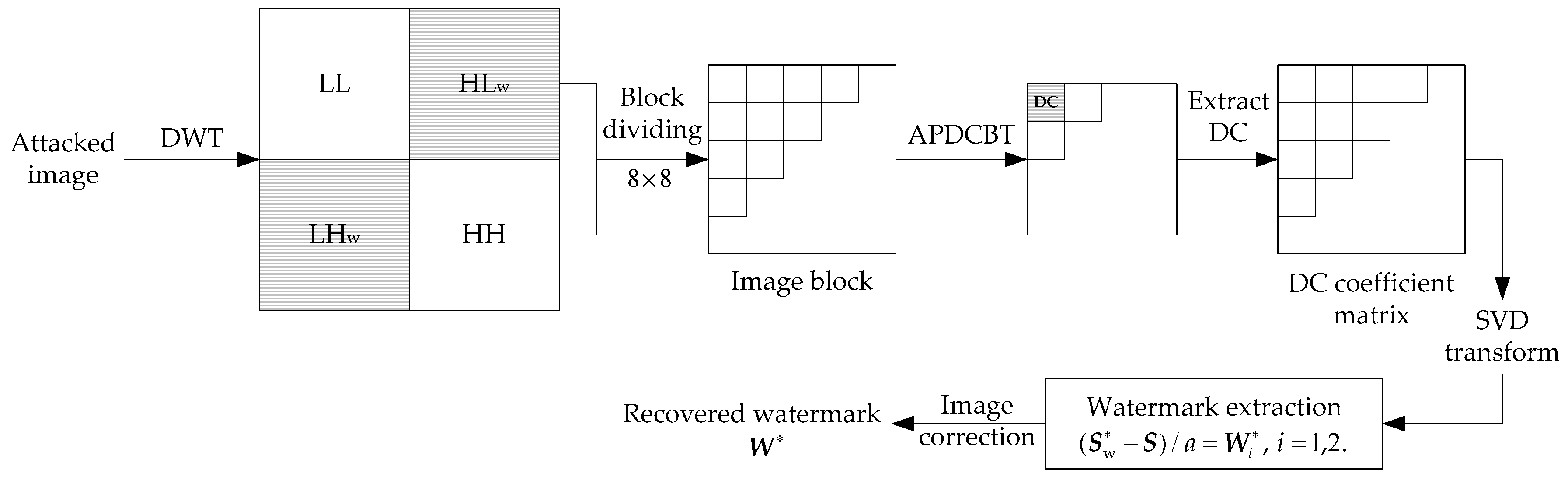
3. The Proposed Scheme
3.1. Watermark Insertion
3.2. Watermark Extraction
| Algorithm 1 Watermark Insertion |
| Variable Declaration: Lena: carrier image SDUW: watermark image I: read the carrier image : read the watermark images : scaling factor DWT, APDCBT, and SVD: transforms used in the algorithm Wavelet filter: Haar LL, LH, HL, and HH: sub-bands after the first-level DWT decomposition : coefficient matrix formed by DC coefficients in LH or HL sub-band : diagonal matrix for and : orthogonal matrices for : watermarked diagonal matrix : diagonal matrix for and : orthogonal matrices for : watermarked DC coefficient matrix LHw and HLw: the watermarked LH and HL sub-bands : watermarked image Watermark Embedding Procedure: 1. Read the Images and Perform DWT on Carrier Image ILena.bmp (carrier image with size of 512 × 512) SDUW.bmp (watermark image with size of 32 × 32) [LL, LH, HL, HH]DWT (I, ‘Haar’) 2. Perform Block-based APDCBT on HL Sub-band DC coefficientsAPDCBT (HL) 3. Get DC Coefficient Matrix and Perform SVD on // Form a new coefficient matrix using the DC coefficients obtained in Step 2, and perform SVD on coefficient matrix DC coefficients SVD () 4. Watermark Insertion SVD () Watermarked DC coefficients HLwinverse (Watermarked DC coefficients) // Apply Steps 1–4 to LH sub-band to embed the same watermark and obtain the watermarked LHw sub-band 5. Perform IDWT to Get the Watermarked Image inverse DWT (LL, LHw, HLw, HH) |
| Algorithm 2 Watermark Extraction |
| Variable Declaration: : attacked image obtained on the receiving end DWT, APDCBT, and SVD: transforms used in the algorithm Wavelet filter: Haar LL, LHw, HLw, and HH: new sub-bands after the first-level DWT decomposition : coefficient matrix formed by DC coefficients in LHw or HLw sub-band : scaling factor : diagonal matrix for and : orthogonal matrices for : watermarked diagonal matrix and : orthogonal matrices for T: threshold for watermark correction : extracted watermark images : extracted watermark without correction : extracted watermark after correction Watermark Extraction Procedure: 1. Read the Attacked Image and Perform DWT on It Received image.bmp [LL, LHw, HLw, HH]DWT (, ‘Haar’) 2. Perform Block-based APDCBT on HLw Sub-band and Get DC Coefficient Matrix Watermarked DC coefficientsAPDCBT (HLw) Watermarked DC coefficients 3. Perform SVD on SVD () 4. Watermark Extraction // Apply Steps 1-4 to LHw sub-band to extract the second watermark 5. Watermark Correction for i = 1:32 and j = 1:32 if then else end if end for // The extracted watermark after correction is obtained |
4. Performance Analysis
4.1. Imperceptibility
4.2. Robustness
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Verma, V.; Singh, M.J. Digital image watermarking techniques: A comparative study. Int. J. Adv. Electr. Electron. Eng. 2013, 2, 173–184. [Google Scholar]
- Hai, T.; Li, C.M.; Zain, J.M.; Abdalla, A.N. Robust image watermarking theories and techniques: A review. J. Appl. Res. Technol. 2014, 12, 122–138. [Google Scholar]
- Qin, C.; Ji, P.; Wang, J.W.; Chang, C.C. Fragile image watermarking scheme based on VQ index sharing and self-embedding. Multimed. Tools Appl. 2017, 76, 2267–2287. [Google Scholar] [CrossRef]
- Das, C.; Panigrahi, S.; Sharma, V.K.; Mahapatra, K.K. A novel blind robust image watermarking in DCT domain using inter-block coefficient correlation. AEU Int. J. Electron. Commun. 2014, 68, 244–253. [Google Scholar] [CrossRef]
- He, Z.F.; Zhang, Y.H. Fusion on the wavelet coefficients scale-related for double encryption holographic halftone watermark hidden technology. IEICE Trans. Inf. Syst. 2015, E98-D, 1391–1395. [Google Scholar] [CrossRef]
- Hu, Y.P.; Wang, Z.J.; Liu, H.; Guo, G.J. A geometric distortion resilient image watermark algorithm based on DWT-DFT. J. Softw. 2011, 6, 1805–1812. [Google Scholar] [CrossRef]
- Liu, R.Z.; Tan, T.N. An SVD-based watermarking scheme for protecting rightful ownership. IEEE Trans. Multimed. 2002, 4, 121–128. [Google Scholar]
- Lai, C.C.; Tsai, C.C. Digital image watermarking using discrete wavelet transform and singular value decomposition. IEEE Trans. Instrum. Meas. 2010, 59, 3060–3063. [Google Scholar] [CrossRef]
- Gupta, A.K.; Raval, M.S. A robust and secure watermarking scheme based on singular values replacement. Sadhana 2012, 37, 425–440. [Google Scholar] [CrossRef]
- Singh, A.K.; Kumar, B.; Dave, M.; Mohan, A. Robust and imperceptible dual watermarking for telemedicine applications. Wirel. Pers. Commun. 2015, 80, 1415–1433. [Google Scholar] [CrossRef]
- Singh, A.K. Improved hybrid algorithm for robust and imperceptible multiple watermarking using digital images. Multimed. Tools Appl. 2017, 76, 8881–8900. [Google Scholar] [CrossRef]
- Singh, A.K.; Dave, M.; Mohan, A. Hybrid technique for robust and imperceptible image watermarking in DWT–DCT–SVD domain. Natl. Acad. Sci. Lett. 2014, 37, 351–358. [Google Scholar] [CrossRef]
- Singh, A.; Tayal, A. Choice of wavelet from wavelet families for DWT-DCT-SVD image watermarking. Int. J. Comput. Appl. 2012, 48, 9–14. [Google Scholar] [CrossRef]
- Roy, S.; Pal, A.K. An SVD based location specific robust color image watermarking scheme using RDWT and Arnold Scrambling. Wirel. Pers. Commun. 2018, 98, 2223–2250. [Google Scholar] [CrossRef]
- Laur, L.; Rasti, P.; Agoyi, M.; Anbarjafari, G. A robust color image watermarking scheme using entropy and QR decomposition. Radioengineering 2015, 24, 1025–1032. [Google Scholar] [CrossRef]
- Mishra, A.; Agarwal, C.; Sharma, A.; Bedi, P. Optimized gray-scale image watermarking using DWT-SVD and firefly algorithm. Expert Syst. Appl. 2014, 41, 7858–7867. [Google Scholar] [CrossRef]
- Yang, X.S. Multiobjective firefly algorithm for continuous optimization. Eng. Comput. 2013, 29, 175–184. [Google Scholar] [CrossRef]
- Ali, M.; Ahn, C.W. Comments on “Optimized gray-scale image watermarking using DWT-SVD and firefly algorithm”. Expert Syst. Appl. 2015, 42, 2392–2394. [Google Scholar] [CrossRef]
- Makbol, N.M.; Khoo, B.E. A new robust and secure digital image watermarking scheme based on the integer wavelet transform and singular value decomposition. Digit. Signal Process. 2014, 33, 134–147. [Google Scholar] [CrossRef]
- Ansari, I.A.; Pant, M.; Ahn, C.W. Robust and false positive free watermarking in IWT domain using SVD and ABC. Eng. Appl. Artif. Intell. 2016, 49, 114–125. [Google Scholar] [CrossRef]
- Singh, D.; Singh, S.K. DWT-SVD and DCT based robust and blind watermarking scheme for copyright protection. Multimed. Tools Appl. 2017, 76, 13001–13024. [Google Scholar] [CrossRef]
- Fazli, S.; Moeini, M. A robust image watermarking method based on DWT, DCT, and SVD using a new technique for correction of main geometric attacks. Optik 2016, 127, 964–972. [Google Scholar] [CrossRef]
- Hou, Z.X.; Wang, C.Y.; Yang, A.P. All phase biorthogonal transform and its application in JPEG-like image compression. Signal Process. Image Commun. 2009, 24, 791–802. [Google Scholar] [CrossRef]
- Wang, C.Y.; Jiang, B.C.; Xie, S.Z. Properties of all phase biorthogonal transform matrix and its application in color image compression. J. Comput. Inf. Syst. 2013, 9, 7227–7234. [Google Scholar]
- Yang, F.F.; Wang, C.Y.; Huang, W.; Zhou, X. Embedding binary image watermark in DC components of all phase discrete cosine biorthogonal transform. Int. J. Secur. Appl. 2015, 9, 125–136. [Google Scholar] [CrossRef]
- Khalifa, O.O.; Yusof, Y.B.; Olanrewaju, R.F. Performance evaluations of digital watermarking systems. In Proceedings of the 8th IEEE Conference on Information Science and Digital Content Technology, Jeju Island, Korea, 26–28 June 2012; pp. 533–536. [Google Scholar]





| Items | Liu and Tan [7] | Fazli and Moeini [22] | Proposed |
|---|---|---|---|
| Watermark image | gray | binary | binary |
| Capacity | 32 × 32 | 32 × 32 × 4 | 32 × 32 × 2 |
| PSNR (dB) | 53.83 | 101.97 | 101.97 |
| NCC | 1 | 0.9603 | 0.9724 |
| Attack | Liu and Tan [7] | Fazli and Moeini [22] | Proposed |
|---|---|---|---|
| Embedding intensity | 0.05 | 0.05 | 0.05 |
| Salt and pepper noise (0.005) | 09628 | 0.9993 | 0.9988 |
| Salt and pepper noise (0.01) | 0.9158 | 1 | 0.9985 |
| Gaussian noise (0, 0.005) | 0.8606 | 1 | 0.9986 |
| Gaussian noise (0, 0.01) | 0.8235 | 1 | 0.9993 |
| Scaling (2, 0.5) | 0.9838 | 0.9621 | 0.9638 |
| Scaling (0.5, 2) | 0.9123 | 0.9603 | 0.9672 |
| Median filtering (3 × 3) | 0.9321 | 0.9638 | 0.9793 |
| Median filtering (5 × 5) | 0.8510 | 0.9621 | 0.9724 |
| Average filtering (3 × 3) | 0.8987 | 0.9793 | 0.9741 |
| Average filtering (5 × 5) | 0.8153 | 0.9586 | 0.9690 |
| Rotation (5°) | 0.8223 | 1 | 0.9897 |
| Rotation (15°) | -- | 0.9948 | 1 |
| Contrast enhancement (1.2) | 0.9889 | 1 | 1 |
| Contrast enhancement (1.5) | 0.9844 | 1 | 1 |
| Brightness adjustment (+50) | 1 | 0.9672 | 0.9741 |
| Brightness adjustment (+100) | 0.7598 | 0.9603 | 0.9707 |
| Attack | Liu and Tan [7] | Fazli and Moeini [22] | Proposed |
|---|---|---|---|
| Gaussian noise (0, 0.01) + median filtering (3 × 3) | 0.9401 | 0.9995 | 0.9971 |
| Gaussian noise (0, 0.01) + average filtering (3 × 3) | 0.9716 | 1 | 0.9964 |
| Salt and pepper noise (0.01) + median filtering (3 × 3) | 0.9332 | 0.9631 | 0.9793 |
| Salt and pepper noise (0.01) + average filtering (3 × 3) | 0.9647 | 0.9993 | 0.9867 |
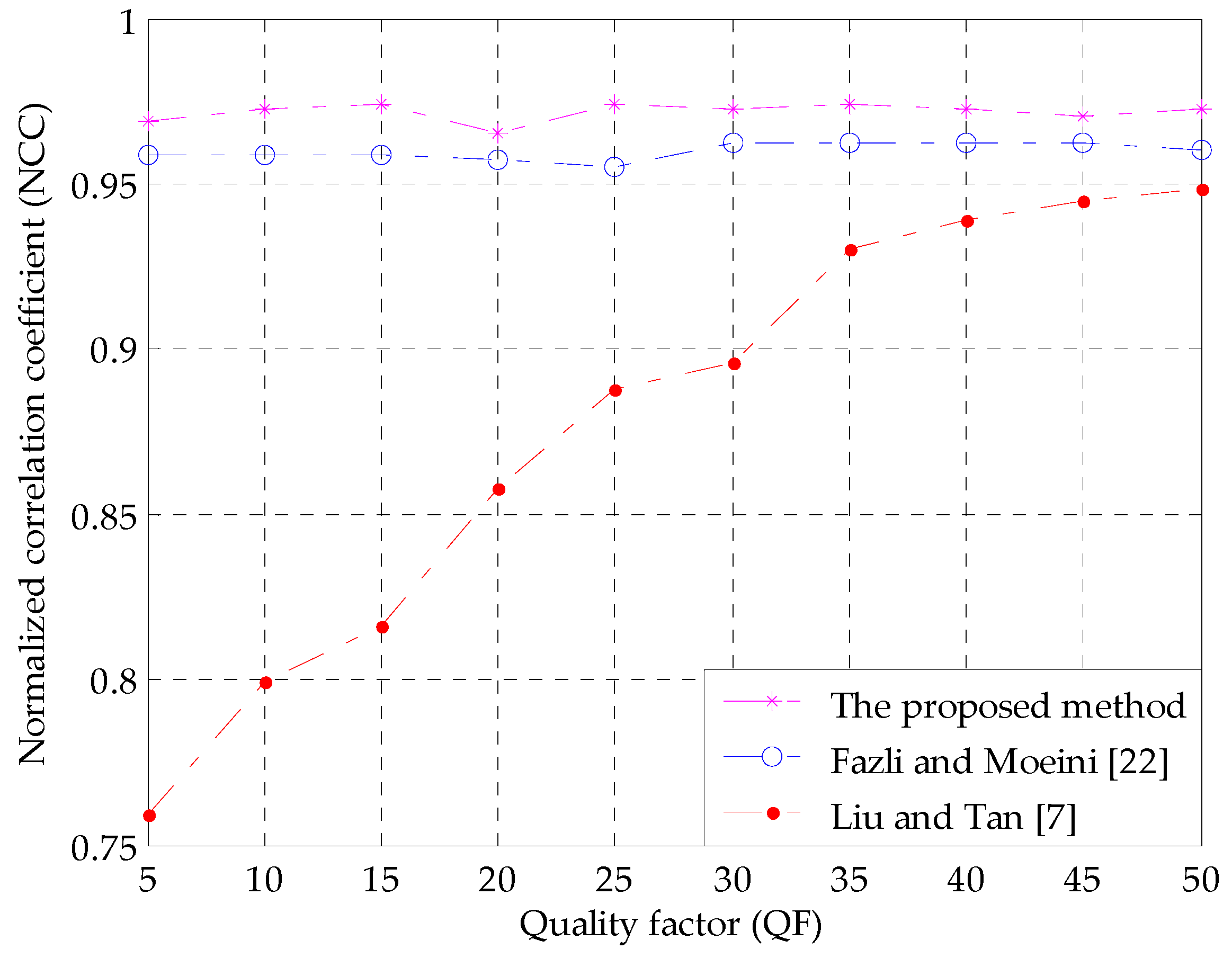
| Scaling (2, 0.5) + JPEG compression (QF = 50) | 0.9462 | 0.9621 | 0.9707 |
| Scaling (0.5, 2) + JPEG compression (QF = 50) | 0.8942 | 0.9621 | 0.9724 |
| JPEG compression (QF=50) + cropping (25%) | 0.9485 | 0.8086 | 0.8569 |
| Median filtering (3 × 3) + JPEG compression (QF = 50) | 0.9455 | 0.9569 | 0.9707 |
| Average filtering (3 × 3) + JPEG compression (QF = 50) | 0.8885 | 0.9707 | 0.9759 |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhou, X.; Zhang, H.; Wang, C. A Robust Image Watermarking Technique Based on DWT, APDCBT, and SVD. Symmetry 2018, 10, 77. https://doi.org/10.3390/sym10030077
Zhou X, Zhang H, Wang C. A Robust Image Watermarking Technique Based on DWT, APDCBT, and SVD. Symmetry. 2018; 10(3):77. https://doi.org/10.3390/sym10030077
Chicago/Turabian StyleZhou, Xiao, Heng Zhang, and Chengyou Wang. 2018. "A Robust Image Watermarking Technique Based on DWT, APDCBT, and SVD" Symmetry 10, no. 3: 77. https://doi.org/10.3390/sym10030077







