Security Scheme Based on Parameter Hiding Technic for Mobile Communication in a Secure Cyber World
Abstract
:1. Introduction
2. LTE
2.1. The LTE Network
2.2. LTE Initial Attach for UE and Threats
3. Proposed Security Scheme
3.1. Secret Sharing
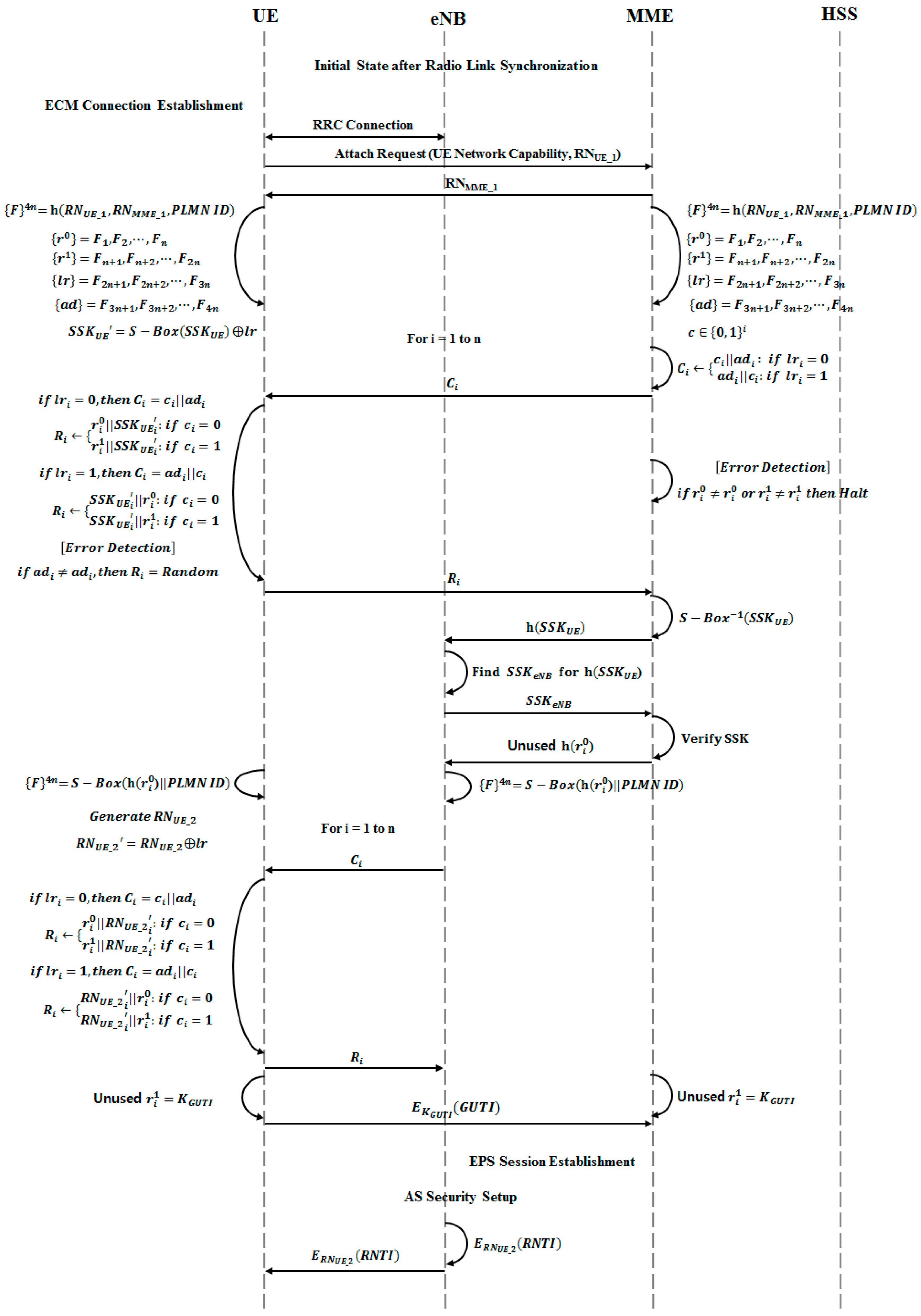
3.2. Initial Attach with IMSI
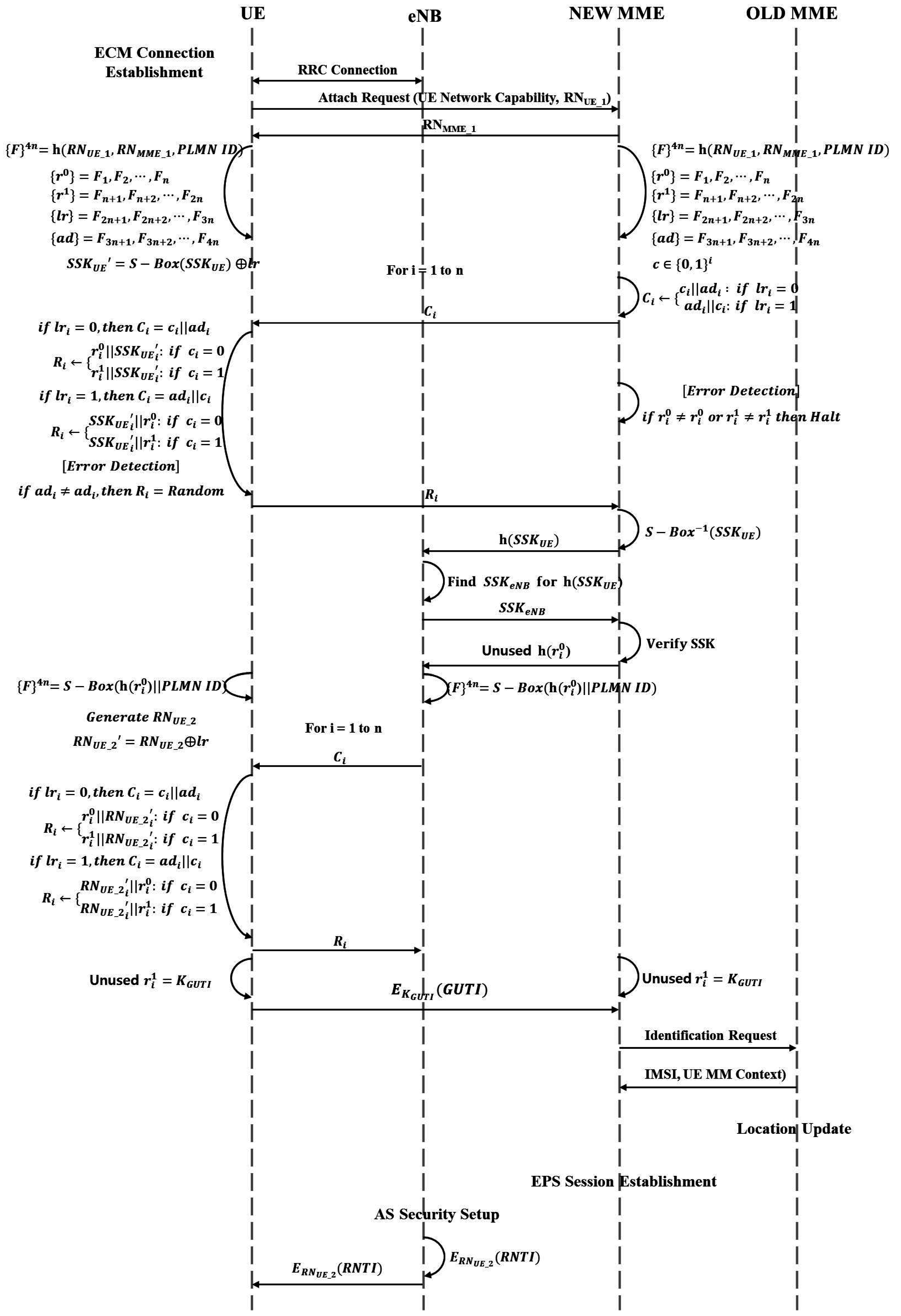
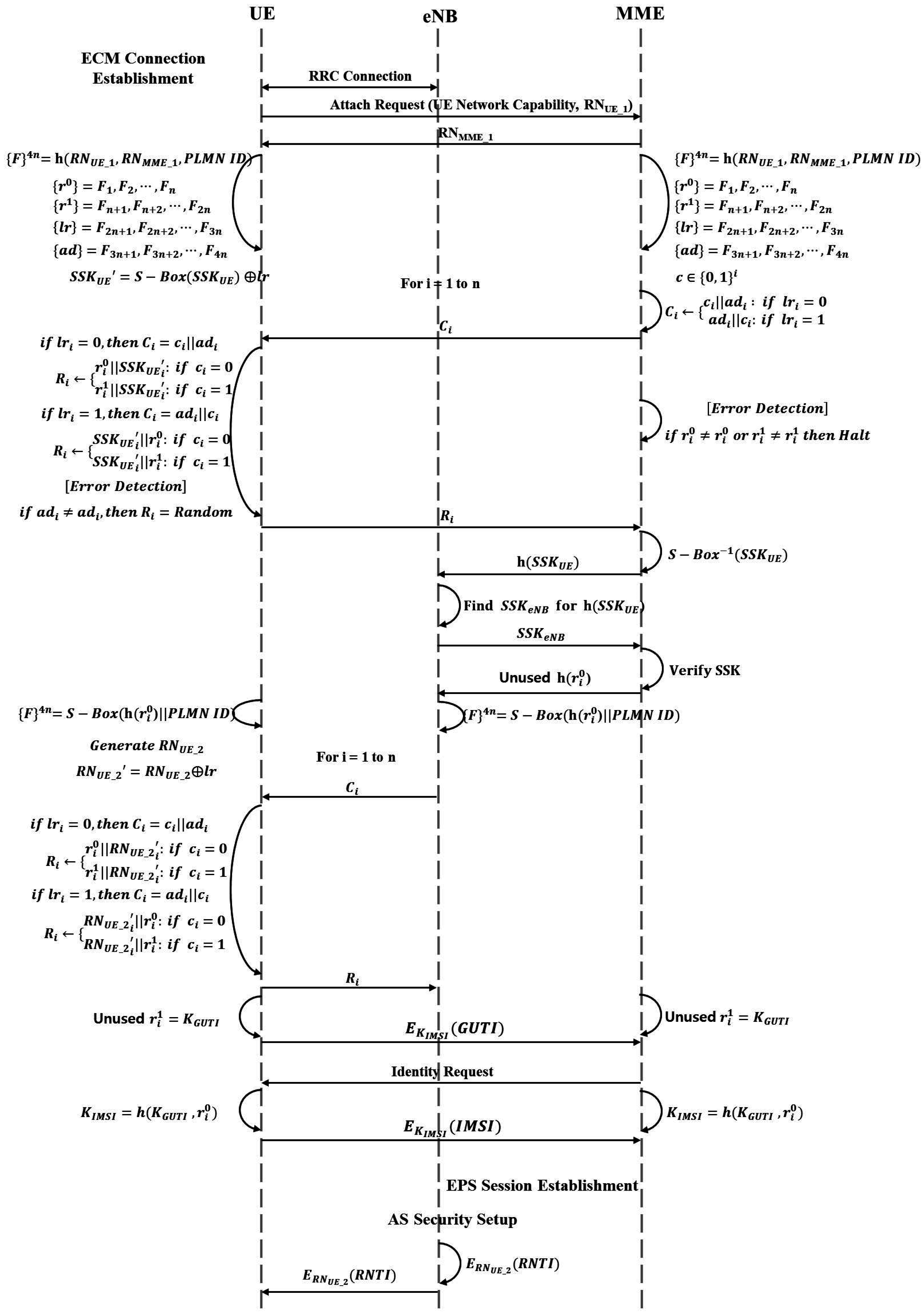
3.3. Initial Attach with GUTI
3.3.1. MME Unchanged
3.3.2. MME Changed
3.3.3. MME Changed and IMSI Needed
4. Security Analysis
4.1. Mutual Authentication
4.2. Error Detection and Verification
4.3. Mafia and Terrorist Attack
4.4. Key Definition, Encryption, and Decryption
5. Performance Analysis
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Martin, S.; Nicolae, P.; Rosario, G. 5G: Towards Secure Ubiquitous Connectivity Beyond 2020; SICS: Kista, Sweden, 2015. [Google Scholar]
- Forsberg, D.; Horn, G.; Moeller, W.-D.; Niemi, V. LTE Security; John Wiley & Sons: Hoboken, NJ, USA, 2012. [Google Scholar]
- Gohar, M.; Koh, S. Inter-domain mobility management based on the proxy mobile IP in mobile networks. J. Inf. Process. Syst. 2016, 12, 196–213. [Google Scholar]
- Rahman, M.A.; Lee, Y.-D.; Koo, I. An efficient transmission mode selection based on reinforcement learning for cooperative cognitive radio networks. Hum.-Centric Comput. Inf. Sci. 2016, 6, 2. [Google Scholar] [CrossRef]
- Gaur, M.S.; Pant, B. Trusted and secure clustering in mobile pervasive environment. Hum.-Centric Comput. Inf. Sci. 2015, 5, 32. [Google Scholar] [CrossRef]
- Dahane, A.; Berrached, N.-E.; Loukil, A. A virtual laboratory to practice mobile wireless sensor networks: A case study on energy efficient and safe weighted clustering algorithm. J. Inf. Process. Syst. 2015, 11, 205–228. [Google Scholar]
- Amsavalli, A.; Kashwan, K.R. Smart patch antenna array for uplink in 4G mobile communication based on LMS algorithm for DS-CDMA technique. J. Converg. Inf. Technol. 2014, 9, 16–24. [Google Scholar]
- 3GPP. Technical Specification Group Services and System Aspects; Rationale and Track of Security Decisions in Long Term Evolved (LTE) RAN/3GPP System Architecture Evolution (SAE); Release 9; 3GPP TR 33.821; 3GPP: Sophia Antipolis, France, 2010. [Google Scholar]
- 3GPP. Telecommunication Management; Security Management Concept and Requirements; Release 10; 3GPP TS 32.371; 3GPP: Sophia Antipolis, France, 2012. [Google Scholar]
- 3GPP. Policy and Charging Control Architecture; Release 10; 3GPP TS 23.203; 3GPP: Sophia Antipolis, France, 2009. [Google Scholar]
- Kim, S. A Design of MILENAGE Algorithm-Based Mutual Authentication Protocol for the Protection of Initial Identifier in LTE. Master’s Thesis, Soongsil University, Seoul, Korea, 2013. [Google Scholar]
- Jang, U.; Lim, H.; Kim, H. Privacy-enhancing security protocol in LTE initial attack. Symmetry 2014, 6, 1011–1025. [Google Scholar] [CrossRef]
- Forsberg, D.; Horn, G.; Moeller, W.-D.; Niemi, V. Security in Intra-LTE State Transitions and Mobility. In LTE Security; John Wiley & Sons: Hoboken, NJ, USA, 2013; pp. 147–164. [Google Scholar]
- Shahzad, A.; Lee, M.; Lee, C.; Xiong, N.; Kim, S.; Lee, Y.-K.; Kim, K.; Woo, S.-M.; Jeong, G. The protocol design and New approach for SCADA security enhancement during sensors broadcasting system. Multimed. Tools Appl. 2015, 1–28. [Google Scholar] [CrossRef]
- Shahzad, A.; Lee, M.; Kim, S.; Kim, K.; Choi, J.Y.; Cho, Y.; Lee, K.K. Design and development of layered security: Future enhancements and directions in transmission. Sensors 2016, 16, 37. [Google Scholar] [CrossRef] [PubMed]
- Bikos, A.N.; Sklavos, N. LTE/SAE security issues on 4G wireless networks. IEEE Sec. Priv. 2013, 11, 55–62. [Google Scholar] [CrossRef]
- Niemi, V.; Blommaert, M. 3GPP security hot topics: LTE/SAE and home eNB. In Proceedings of the 4th ETSI Security Workshop, Sophia Antipolis, France, 13–14 January 2009.
- Salam, M.I.; Yau, W.-C.; Chin, J.-J.; Heng, S.-H.; Ling, H.-C.; Phan, R.C.-W.; Poh, G.S.; Tan, S.-Y.; Yap, W.-S. Implementation of searchable symmetric encryption for privacy-preserving keyword search on cloud storage. Hum.-Centric Comput. Inf. Sci. 2015, 5, 19. [Google Scholar] [CrossRef]
- Peng, K. A secure network for mobile wireless service. J. Inf. Process. Syst. 2013, 9, 247–258. [Google Scholar] [CrossRef]
- Joo, J.W.; Lee, J.K.; Park, J.H. Security considerations for a connected car. J. Converg. 2015, 6, 1–9. [Google Scholar]
- Netmanias. EMM Procedure: 1. Initial Attach for Unknown UE (Part 1)—Case of Initial Attach; NMC Consulting Group Technical Specifications; Netmanias: Seattle, WA, USA, 2012. [Google Scholar]
- Netmanias. EMM Procedure: 1. Initial Attach for Unknown UE (Part 2)—Call Flow of Initial Attach; NMC Consulting Group Technical Specifications; Netmanias: Seattle, WA, USA, 2011. [Google Scholar]
- Prasad, A. 3GPP SAE-LTE Security. In Proceedings of the Niksun Wwsmc, Princeton, NJ, USA, 25–27 July 2011.
- Cao, J.; Ma, M.; Li, H.; Zhang, Y.; Luo, Z. A survey on security aspects for LTE and LTE-A networks. IEEE Commun. Surv. Tutor. 2014, 16, 283–302. [Google Scholar] [CrossRef]
- Netmanias. LTE Security I: LTE Security Concept and Authentication; NMC Consulting Group Technical Specifications; Netmanias: Seattle, WA, USA, 2012. [Google Scholar]
- Netmanias. LTE Security II: NAS and AS Security; NMC Consulting Group Technical Specifications; Netmanias: Seattle, WA, USA, 2012. [Google Scholar]
- Wang, J.; Zhang, Z.; Ren, Y.; Kim, J.-U. Issues toward networks architecture security for LTE and LTE-A networks. Int. J. Sec. Its Appl. 2014, 8, 17–24. [Google Scholar] [CrossRef]
- Escudero-Andreu, G.; Raphael, C.P.; Parish, D.J. Analysis and design of security for next generation 4G cellular networks. In Proceedings of the 13th Annual Post Graduate Symposium on the Convergence of Telecommunications, Networking and Broad-Casting (PGNET), Liverpool, UK, 25–26 June 2012.
- Kwon, T.; Lee, J.; Choi, H.; Yi, O.; Ju, S. Efficiency of LEA compared with AES. J. Converg. 2015, 6, 16–25. [Google Scholar]

| UE | User Equipment (e.g., Smart Phone) |
|---|---|
| eNB | Evolved Node B |
| MME | Mobility Management Entity |
| HSS | Home Subscriber Server |
| IMSI | International Mobile Subscriber Identity |
| RNTI | Radio Network Temporary Identities |
| GUTI | Global Unique Temporary Identifier |
| PLMN ID | Public Land Mobile Network ID (MCC + MNC) |
| MCC | Mobile Country Code |
| MNC | Mobile Network Code |
| RN | Random Number |
| h() | Hash Function |
| F | 4 n bits String by h() |
| C | Challenge Bits |
| SSK | Secret Sharing Key |
| S-Box | Substitution-Box |
| Vurnerable Information and Layer | Original Initial Attach | Proposed Initial Attach |
|---|---|---|
| Mutual Authentication between UE and eNB | Not Supported | Supported |
| Mutual Authentication between UE and MME | Not Supported | Supported |
| Mutual Authentication between eNB and MME | Not Supported | Supported |
| IMSI | Plain Text Transmission | Cipher Text Transmission |
| RNTI | Plain Text Transmission | Cipher Text Transmission |
| GTUI | Plain Text Transmission | Cipher Text Transmission |
| Variable | Values | Description |
|---|---|---|
| Cell | 1 | - |
| Number of UE | 1, 50, 100 | - |
| Test time | 9000 s | Initial data (0~150 s) not reflected |
| Initial Attach Attempt Cycle | 150 s | The UE service uses initial attempt only |
| Portability Model | Deactivation | - |
| Device | Original Initial Attach | ||
|---|---|---|---|
| Time (s) | Delay (s) | Traffic Received (bits/s) | |
| 1 | - | 0.004700 | 1.234 |
| 50 | - | 0.007260 | 1.249 |
| 100 | - | 0.010292 | 1.039 |
| Device | Proposed Initial Attach | ||
|---|---|---|---|
| Time (s) | Delay (s) | Traffic Received (bits/s) | |
| 1 | 0.0113 | 0.007715 | 1.159 |
| 50 | 0.0105 | 0.010539 | 1.331 |
| 100 | 0.0114 | 0.014576 | 1.108 |
| Device | Summary (Based on VoIP 100%) | ||
|---|---|---|---|
| Time (s) | Delay (s) | Traffic Received (bits/s) | |
| 1 | 36% | 40% | 1% |
| 50 | 34% | 32% | 0.9% |
| 100 | 36% | 28% | 0.9% |
| Total Avg. | 35.5% | 33.0% | 0.93% |
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Park, J.H.; Kim, H.; Kang, J. Security Scheme Based on Parameter Hiding Technic for Mobile Communication in a Secure Cyber World. Symmetry 2016, 8, 106. https://doi.org/10.3390/sym8100106
Park JH, Kim H, Kang J. Security Scheme Based on Parameter Hiding Technic for Mobile Communication in a Secure Cyber World. Symmetry. 2016; 8(10):106. https://doi.org/10.3390/sym8100106
Chicago/Turabian StylePark, Jong Hyuk, Hyungjoo Kim, and Jungho Kang. 2016. "Security Scheme Based on Parameter Hiding Technic for Mobile Communication in a Secure Cyber World" Symmetry 8, no. 10: 106. https://doi.org/10.3390/sym8100106






