Energy Efficient Fuzzy Adaptive Verification Node Selection-Based Path Determination in Wireless Sensor Networks
Abstract
:1. Introduction
- The number of verification nodes on the path within hops from the e-CH where (the number of nodes in a cluster).
- The hop-count distance ratio of the routing path being considered and the longest path between the e-CH and the BS.
- The remaining energy status of the intermediate nodes on the path.
2. Background and Rationale
2.1. PVFS
2.2. FASIN
2.3. Rationale
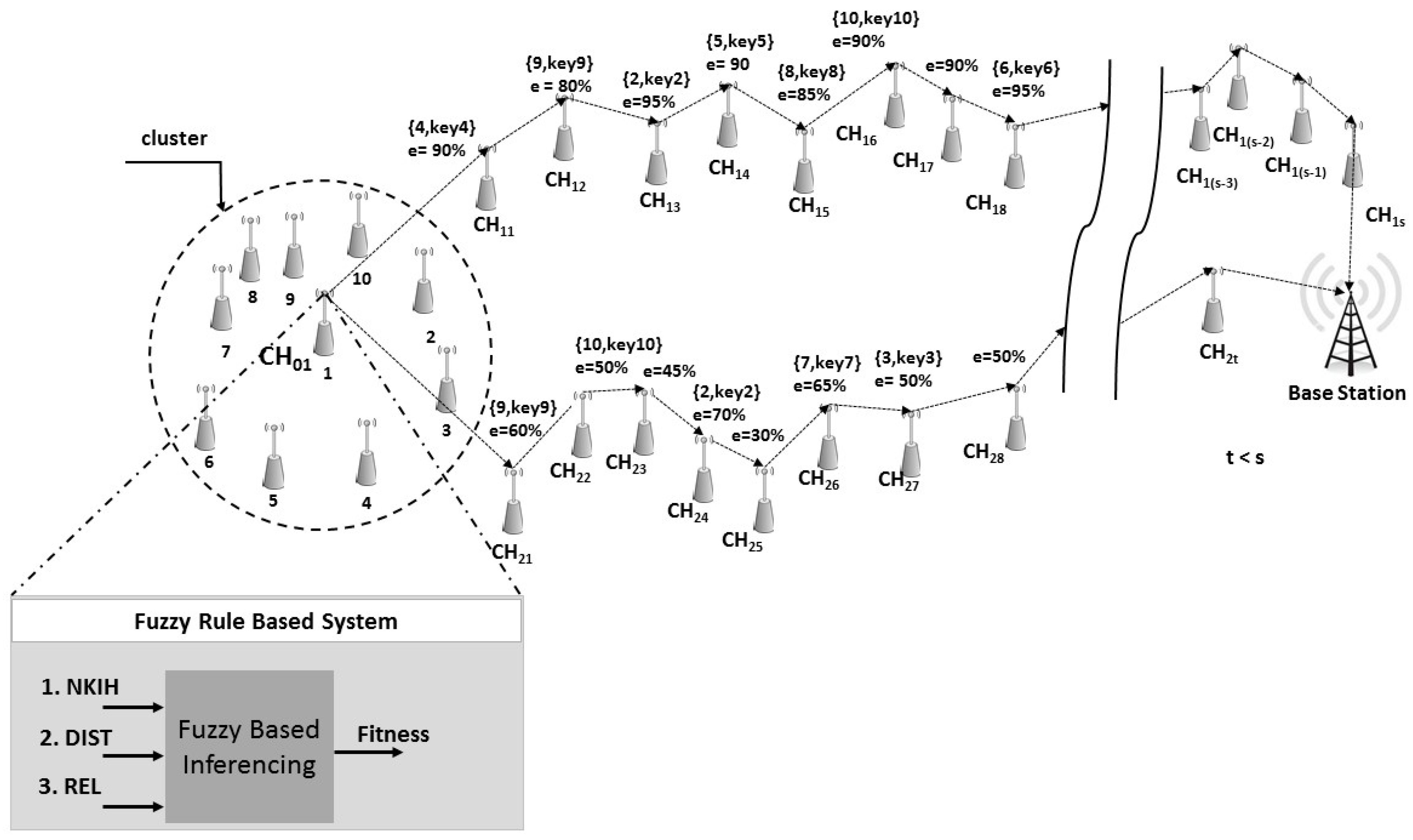
3. Dynamic Key Sharing and Fuzzy Adaptive Route Selection
3.1. Problem Definition
3.1.1. Hot Spot Problem
3.1.2. False Data Injection and False MAC Injection
3.1.3. Network Portioning Due to Constant Use of Minimum Cost Forwarding Paths
3.2. Goals
3.2.1. Load Balancing
3.2.2. Fuzzy-Based Selection of Data Forwarding Path
3.2.3. Dynamic Authentication Key Sharing with the Verification Nodes
3.2.4. Identification of Unhealthy Nodes Near the BS
3.3. System Model and Assumptions
3.4. Threat Model
3.5. Dynamic Authentication Key Sharing
3.6. Fuzzy Adaptive Selection of Data Forwarding Routes
3.6.1. En-Route Filtering
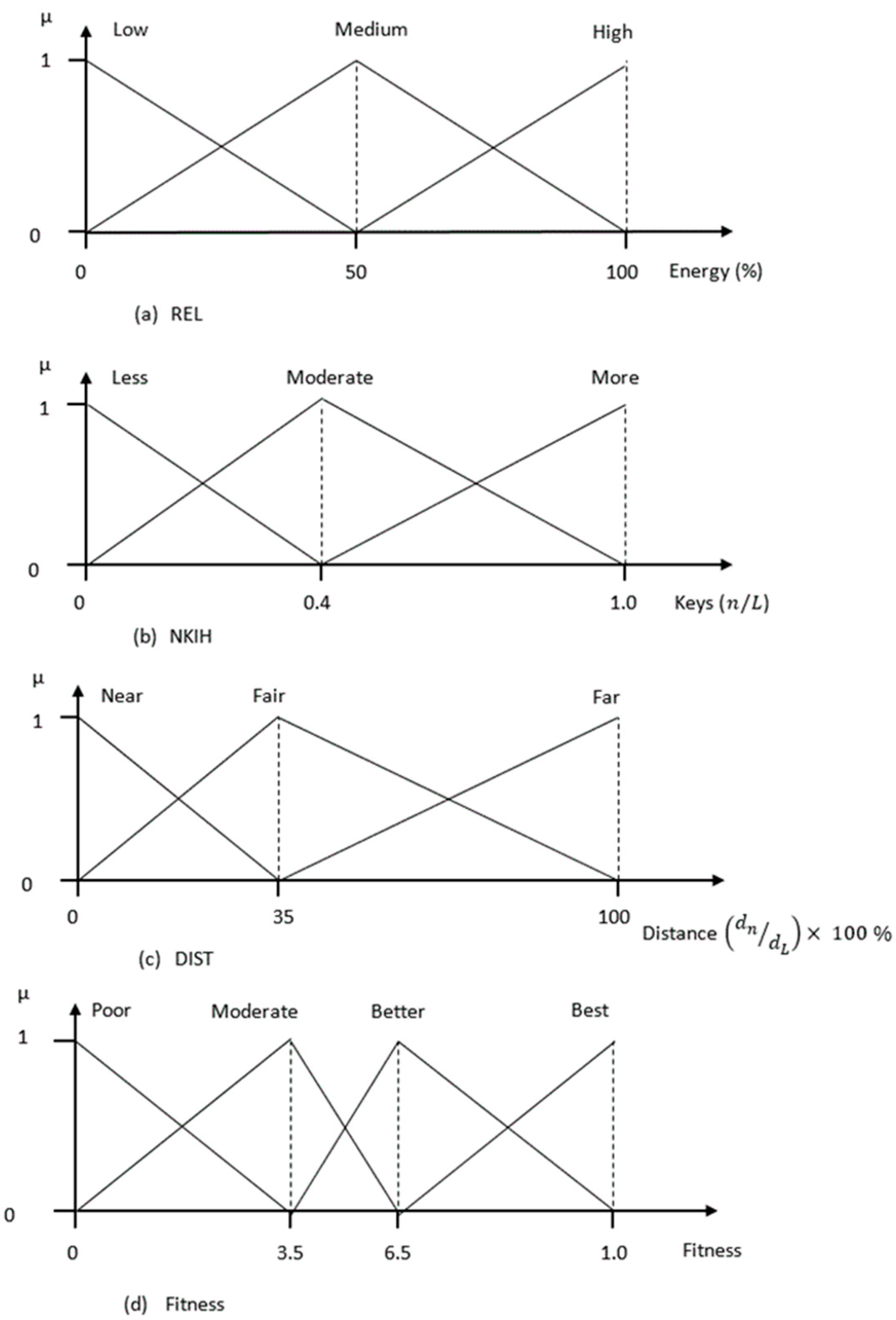
3.6.2. Input and Output Variables
- = The number of verification keys within hops from the event cluster where
- = The hop-count distance ratio between the routing path being considered and the longest path between the e-CH and the BS;
- The average of the residual energy levels of the nodes on the data forwarding path [31].
3.6.3. Fuzzy Membership Function
3.6.4. Fitness Evaluation and Path Selection
| Algorithm 1. PathSelect(c paths). |
|
- Substitution: the number of current filtering nodes to be substituted with the newly chosen filtering nodes.
- Exclusion: determination of whether or not to exclude the upstream CHs from being considered as potential filtering nodes in the future whenever their remaining energy is less than a threshold value ɳ.
Algorithm 2. SelectVN(Pi). - N: set of intermediate nodes likely to be chosen as verification nodes
- RELi: remaining energy of node CHi
- Disti: distance of node CHi from the e-CH
- S ⊆ N: set of verification nodes to be substituted
- output: output of the fuzzy inferencing for verification node selection
- μ: constant
- if output = (exclusion ˄ substitution) then
- for each CHi ∈ N do
- if RELi/Disti < μ then
- N:= N – CHi;
- end if
- end for
- end if
- if output = (substitution ˅ exclusion) then
- for each CHj ∈ S do
- find a CHi ∈ N such that RELj/Distj < RELi/Disti; and
- Choose CHi as a verification node;
- end for
- end if
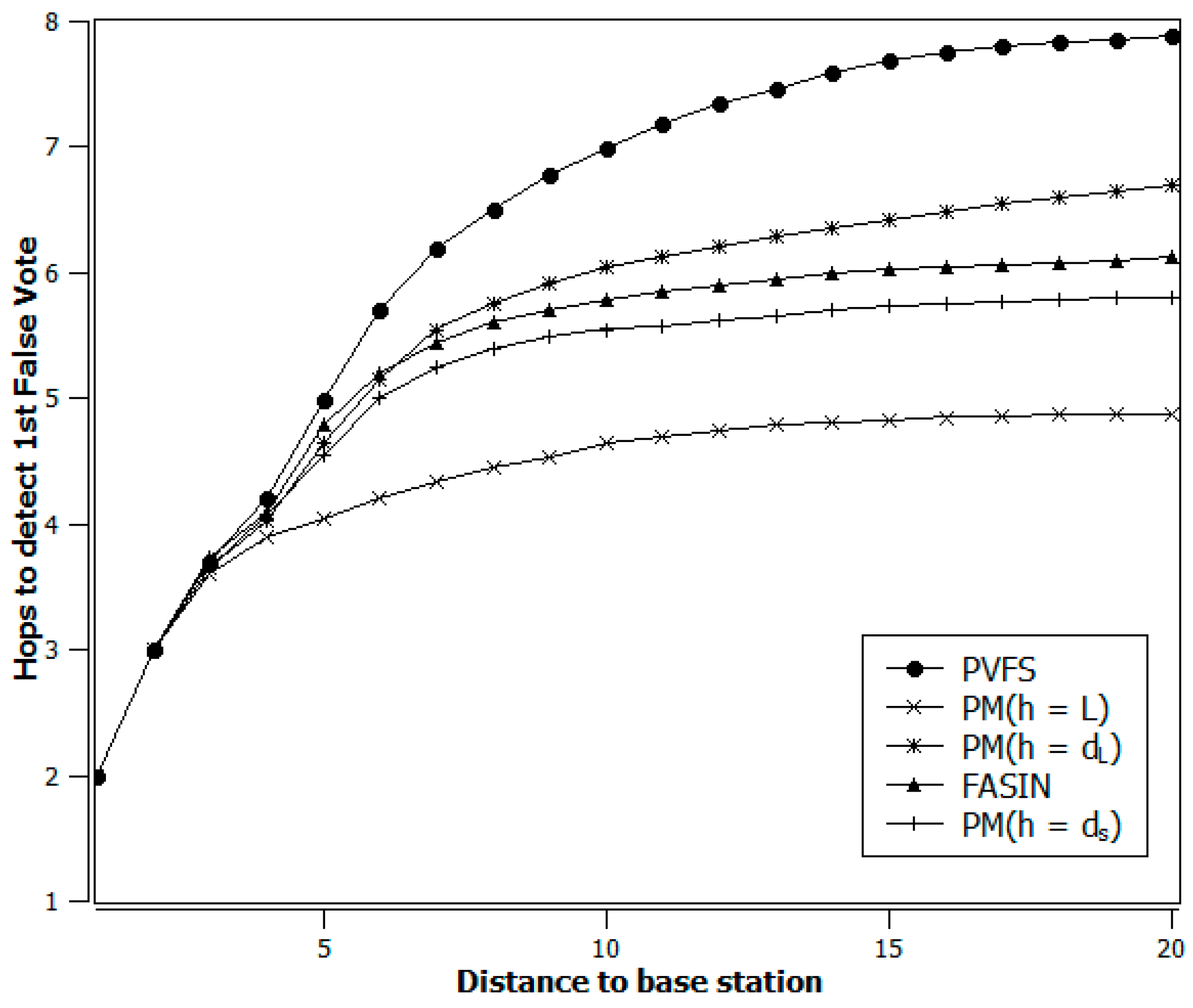
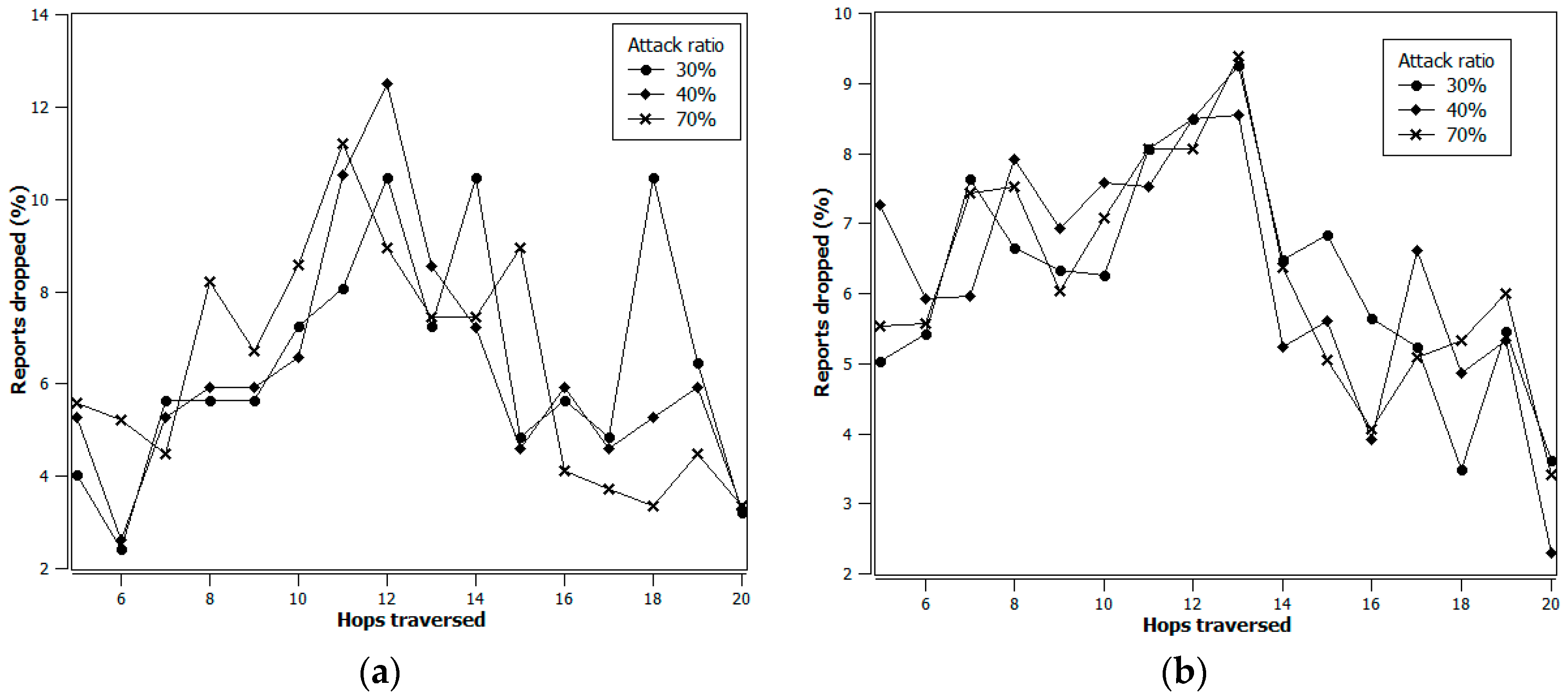
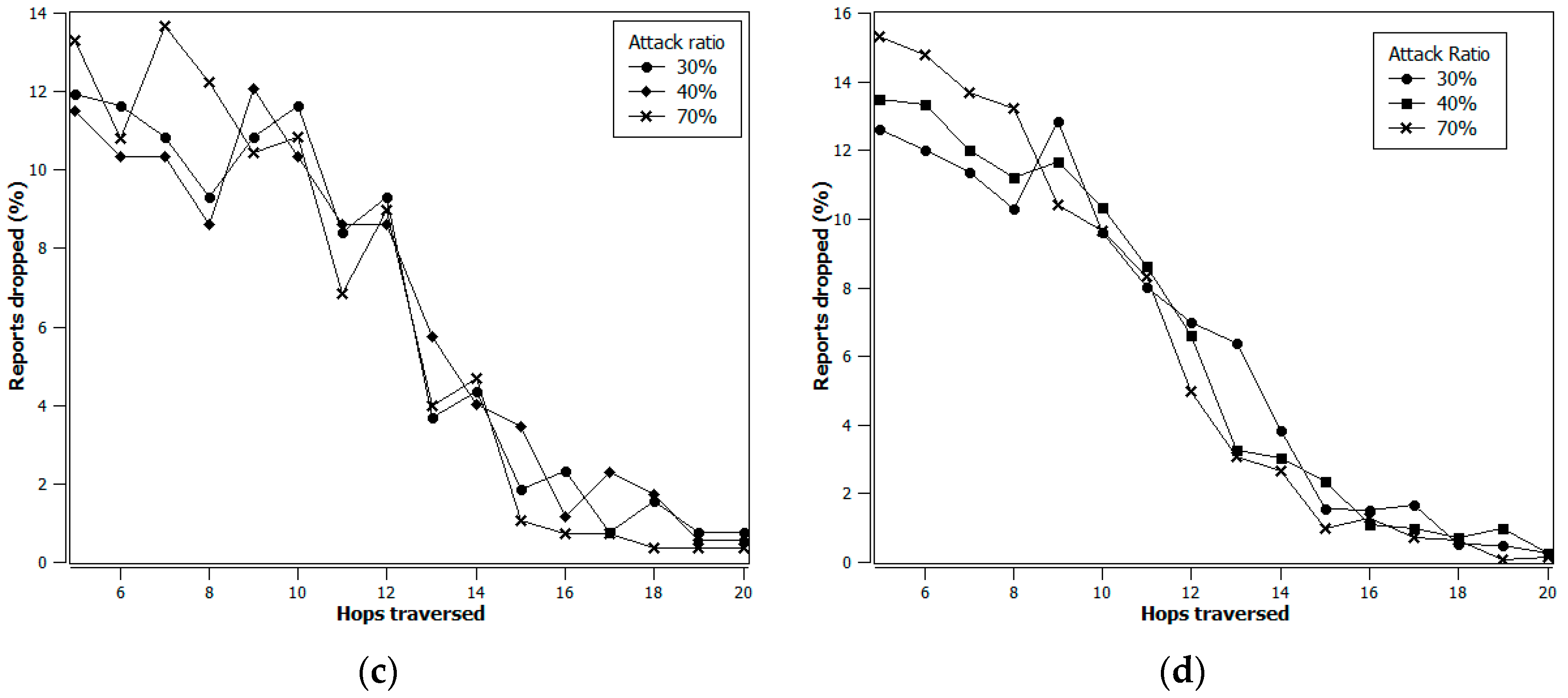
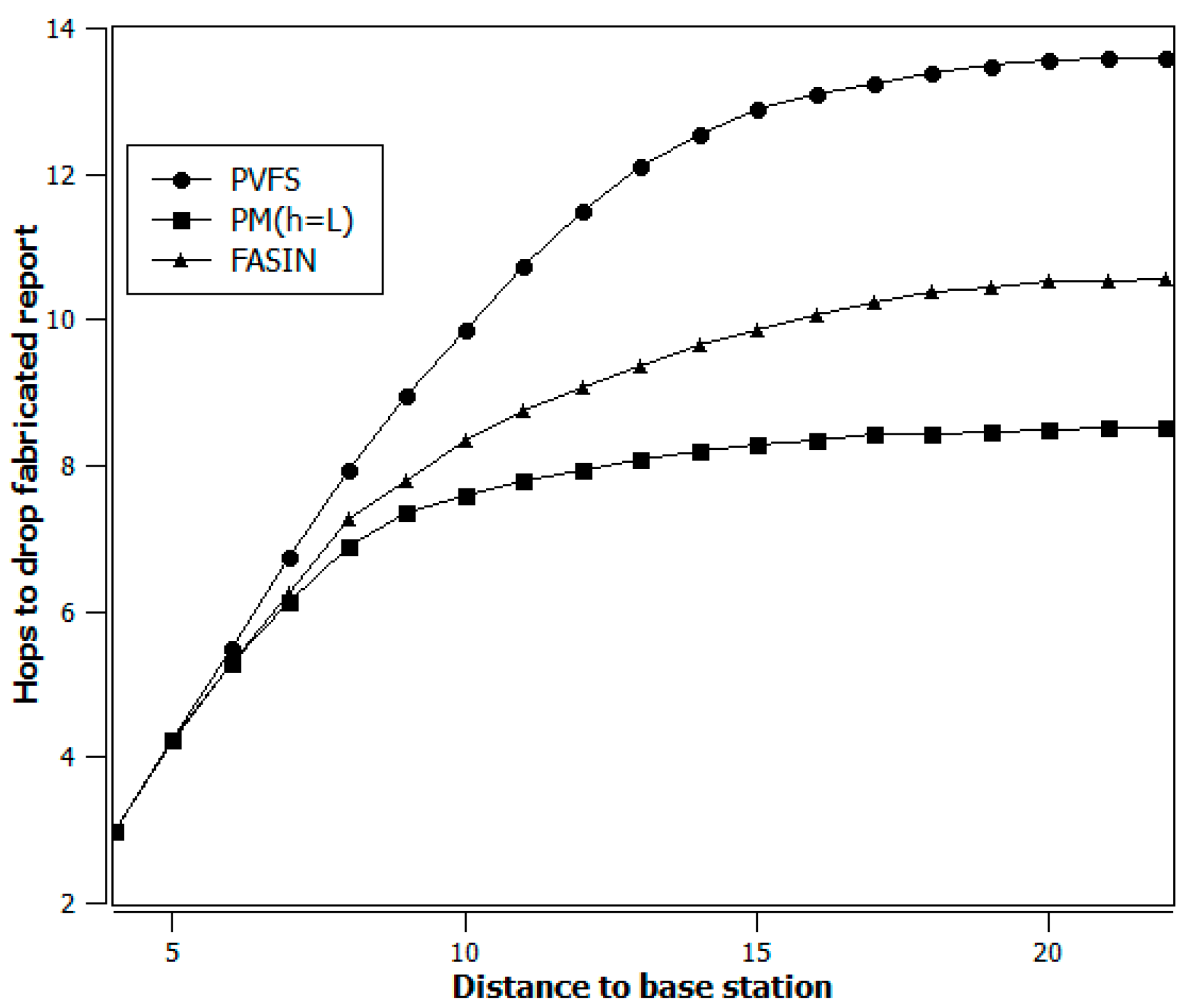
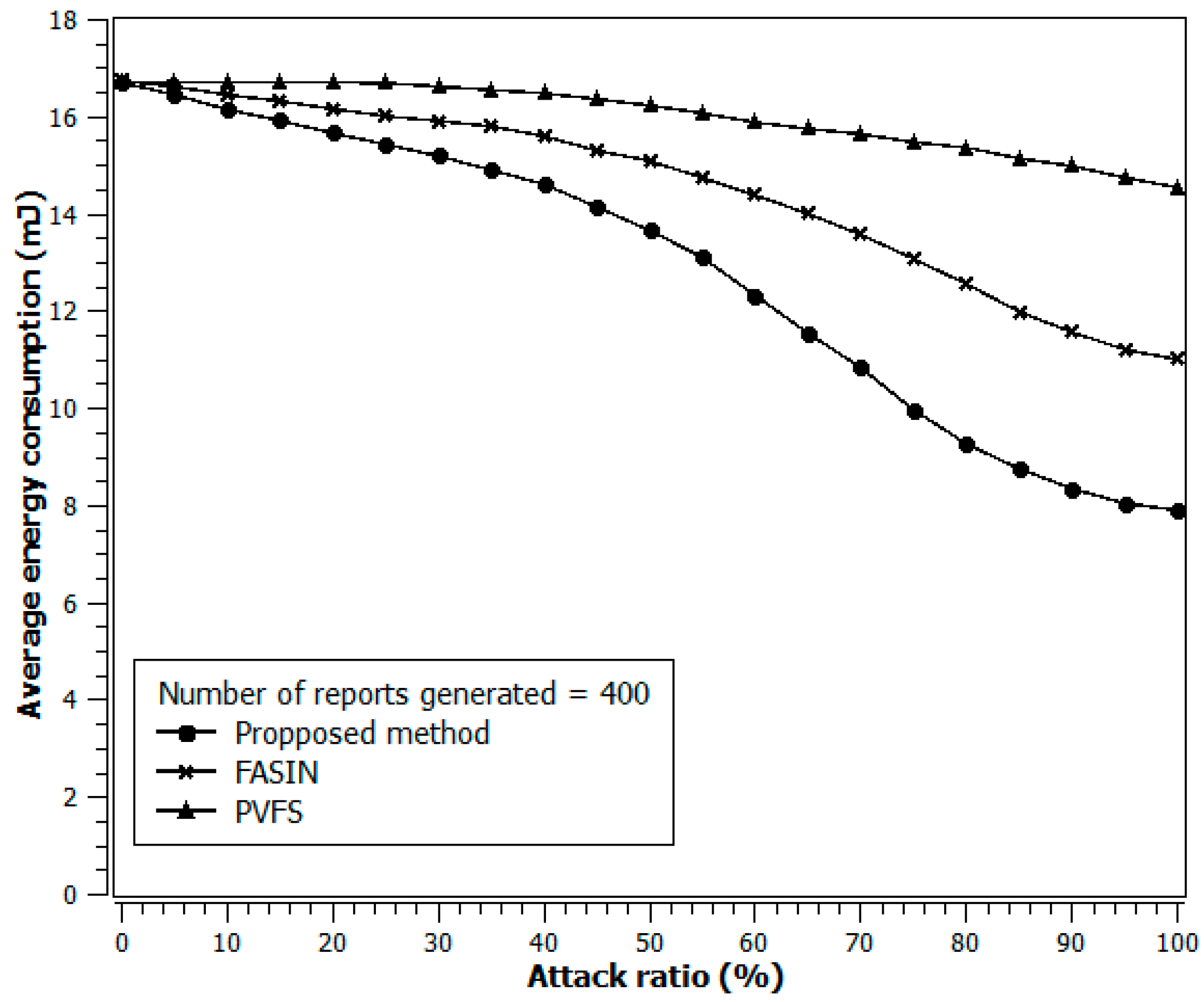
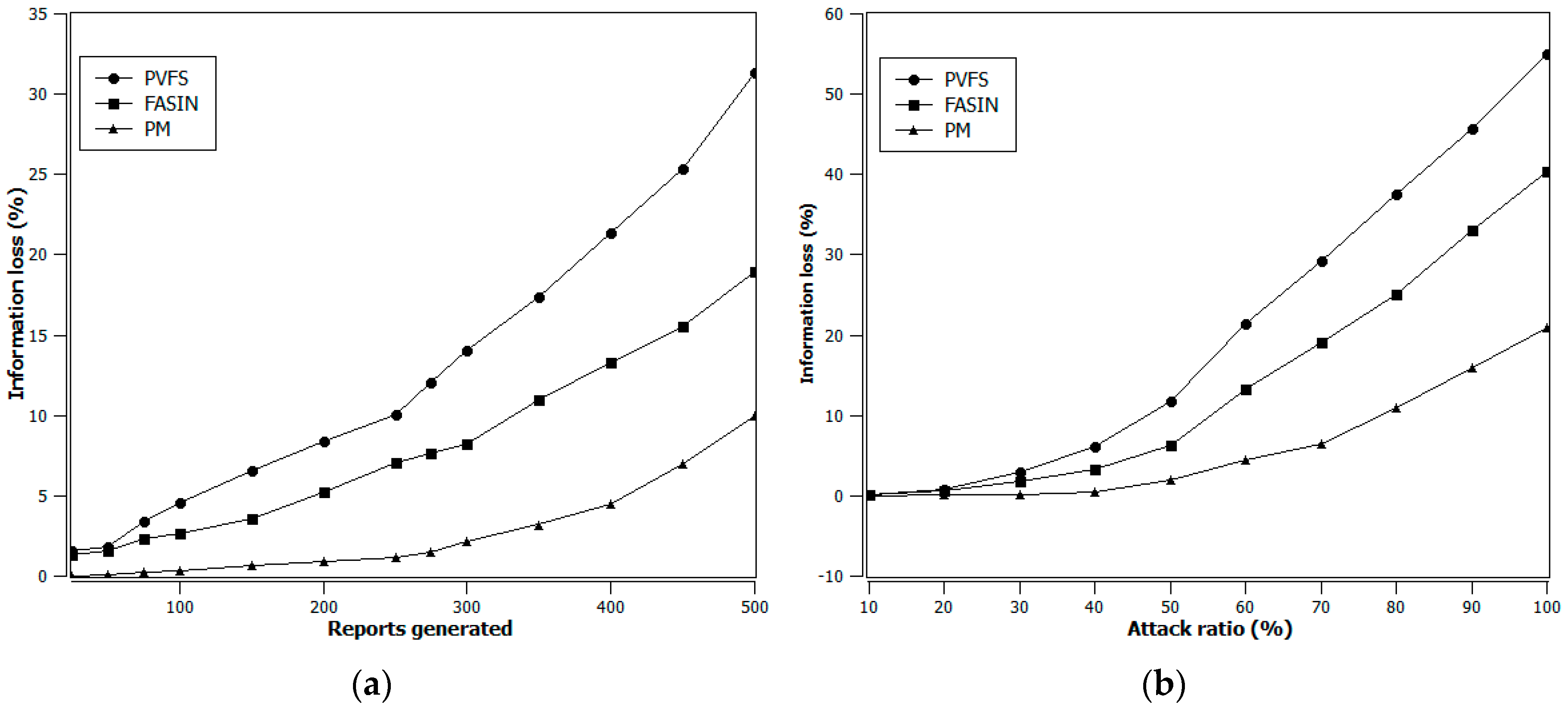
4. Simulation Results
- The data forwarding path is being selected dynamically, and
- The intermediate verification nodes’ average distance from the e-CH improves over time based on security threat and energy status.
5. Related Work
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Han, X.; Cao, X.; Lloyd, E.L.; Shen, C. Fault-Tolerant Relay Node Placement in Heterogeneous Wireless Sensor Networks. IEEE Trans. Mob. Comput. 2010, 9, 643–656. [Google Scholar]
- Xu, J.; Zhou, X.; Han, J.; Li, F.; Zhou, F. Data Authentication Model Based on Reed-Solomon Error-Correcting Codes in Wireless Sensor Networks. IETE Tech. Rev. 2013, 30, 191–199. [Google Scholar] [CrossRef]
- Ding, C.; Yang, L.; Wu, M. Localization-Free Detection of Replica Node Attacks in Wireless Sensor Networks using Similarity Estimation with Group Deployment Knowledge. Sensors 2017, 17, 160. [Google Scholar] [CrossRef] [PubMed]
- Ye, F.; Chen, J.; Li, Y. Improvement of DS Evidence Theory for Multi-Sensor Conflicting Information. Symmetry 2017, 9, 69. [Google Scholar]
- Ye, F.; Luo, H.; Lu, S.; Zhang, L. Statistical En-Route Filtering of Injected False Data in Sensor Networks. IEEE J. Sel. Areas Commun. 2005, 23, 839–850. [Google Scholar]
- Lee, H.Y.; Cho, T.H. Fuzzy Adaptive Selection of Filtering Schemes for Energy Saving in Sensor Networks. IEICE Trans. Commun. 2007, 90, 3346–3353. [Google Scholar] [CrossRef]
- Li, F.; Srinivasan, A.; Wu, J. PVFS: A Probabilistic Voting-Based Filtering Scheme in Wireless Sensor Networks. Int. J. Secur. Netw. 2008, 3, 173–182. [Google Scholar] [CrossRef]
- Hu, Y.; Perrig, A.; Johnson, D.B. Packet Leashes: A Defense against Wormhole Attacks in Wireless Networks. In Proceedings of the INFOCOM 2003, Twenty-Second Annual Joint Conference of the IEEE Computer and Communications Societies, San Francisco, CA, USA, 30 March–3 April 2003; pp. 1976–1986. [Google Scholar]
- Misra, S.; Das, S.; Obaidat, M. Context-Aware Quality of Service in Wireless Sensor Networks. IEEE Commun. Mag. 2014, 52, 16–23. [Google Scholar] [CrossRef]
- Wang, Z.; Zeng, P.; Zhou, M.; Li, D.; Wang, J. Cluster-Based Maximum Consensus Time Synchronization for Industrial Wireless Sensor Networks. Sensors 2017, 17, 141. [Google Scholar] [CrossRef] [PubMed]
- Akram, M.; Cho, T.H. Energy Efficient Fuzzy Adaptive Selection of Verification Nodes in Wireless Sensor Networks. Ad Hoc Netw. 2016, 47, 16–25. [Google Scholar] [CrossRef]
- Yu, Z.; Guan, Y. A Dynamic En-Route Scheme for Filtering False Data Injection in Wireless Sensor Networks. In Proceedings of the 25th IEEE International Conference on Computer Communications (INFOCOM 2006), Barcelona, Spain, 23–29 April 2006; pp. 294–295. [Google Scholar]
- Uluagac, A.S.; Beyah, R.A.; Copeland, J.A. TIme-Based Dynamic Keying and En-Route Filtering (TICK) for Wireless Sensor Networks. In Proceedings of the 2010 IEEE in Global Telecommunications Conference (GLOBECOM 2010), Miami, FL, USA, 6–10 December 2010; pp. 1–6. [Google Scholar]
- Kraub, C.; Schneider, M.; Bayarou, K.; Eckert, C. STEF: A Secure Ticket-Based En-Route Filtering Scheme for Wireless Sensor Networks. In Proceedings of the Second International Conference on Availability, Reliability and Security, Washington, DC, USA, 10–13 April 2007; pp. 310–317. [Google Scholar]
- Yang, H.; Lu, S. Commutative Cipher Based En-Route Filtering in Wireless Sensor Networks. In Proceedings of the IEEE 60th Vehicular Technology Conference, VTC2004-Fall, Los Angeles, CA, USA, 26–29 September 2004; pp. 1223–1227. [Google Scholar]
- Zhu, S.; Setia, S.; Jajodia, S.; Ning, P. An Interleaved Hop-by-Hop Authentication Scheme for Filtering of Injected False Data in Sensor Networks. In Proceedings of the 2004 IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 12 May 2004; pp. 259–271. [Google Scholar]
- Eschenauer, L.; Gligor, V.D. A Key-Management Scheme for Distributed Sensor Networks. In Proceedings of the 9th ACM Conference on Computer and Communications Security, Washington, DC, USA, 18–22 November 2002; pp. 41–47. [Google Scholar]
- Eltoweissy, M.; Moharrum, M.; Mukkamala, R. Dynamic Key Management in Sensor Networks. IEEE Commun. Mag. 2006, 44, 122–130. [Google Scholar] [CrossRef]
- Yang, H.; Ye, F.; Yuan, Y.; Lu, S.; Arbaugh, W. Toward Resilient Security in Wireless Sensor Networks. In Proceedings of the 6th ACM International Symposium on Mobile Ad Hoc Networking and Computing, Urbana-Champaign, IL, USA, 25–27 May 2005; pp. 34–45. [Google Scholar]
- Lee, H.Y.; Cho, T.H. Key Inheritance-Based False Data Filtering Scheme in Wireless Sensor Networks. In Proceedings of the International Conference on Distributed Computing and Internet Technology, Bhubaneswar, India, 20–23 December 2006; pp. 116–127. [Google Scholar]
- Kim, M.S.; Cho, T.H. A Multipath En-Route Filtering Method for Dropping Reports in Sensor Networks. IEICE Trans. Inf. Syst. 2007, 90, 2108–2109. [Google Scholar] [CrossRef]
- Lee, H.; Cho, T. False Negative-Resilient Report Generation for the Statistical Filtering in Sensor Networks. In Proceedings of the International Conference on Network and Mobile Computing (NMC’06), Negeri Sembilan, Malaysia, 28–29 August 2006; p. 27. [Google Scholar]
- Lee, H.Y.; Cho, T.H. A Scheme for Adaptively Countering Application Layer Security Attacks in Wireless Sensor Networks. IEICE Trans. Commun. 2010, 93, 1881–1889. [Google Scholar] [CrossRef]
- Wei, C.; Yang, J.; Gao, Y.; Zhang, Z. Cluster-Based Routing Protocols in Wireless Sensor Networks: A Survey. In Proceedings of the 2011 International Conference On Computer Science and Network Technology (ICCSNT), Harbin, China, 24–26 December 2011; pp. 1659–1663. [Google Scholar]
- Chen, G.; Li, C.; Ye, M.; Wu, J. An Unequal Cluster-Based Routing Protocol in Wireless Sensor Networks. Wirel. Netw. 2009, 15, 193–207. [Google Scholar] [CrossRef]
- Safa, H.; Artail, H.; Tabet, D. A Cluster-Based Trust-Aware Routing Protocol for Mobile Ad Hoc Networks. Wirel. Netw. 2010, 16, 969–984. [Google Scholar] [CrossRef]
- Singh, S.K.; Kumar, P.; Singh, J.P. A Survey on Successors of LEACH Protocol. IEEE Access 2017, 5, 4298–4328. [Google Scholar] [CrossRef]
- Ray, A.; De, D. Energy Efficient Clustering Protocol Based on K-Means (EECPK-Means)-Midpoint Algorithm for Enhanced Network Lifetime in Wireless Sensor Network. IET Wirel. Sens. Syst. 2016, 6, 181–191. [Google Scholar] [CrossRef]
- Nam, S.M.; Cho, T.H. Context-Aware Architecture for Probabilistic Voting-Based Filtering Scheme in Sensor Networks. IEEE Trans. Mob. Comput. 2017, 16, 2751–2763. [Google Scholar] [CrossRef]
- Zhang, L.; Yin, N.; Fu, X.; Lin, Q.; Wang, R. A Multi-Attribute Pheromone Ant Secure Routing Algorithm Based on Reputation Value for Sensor Networks. Sensors 2017, 17, 541. [Google Scholar] [CrossRef] [PubMed]
- Lee, H.Y.; Cho, T.H. Fuzzy-Based Path Selection Method for Improving the Detection of False Reports in Sensor Networks. IEICE Trans. Inf. Syst. 2009, 92, 1574–1576. [Google Scholar] [CrossRef]
- Farooq, M.O.; Dogar, A.B.; Shah, G.A. MR-LEACH: Multi-Hop Routing with Low Energy Adaptive Clustering Hierarchy. In Proceedings of the 2010 Fourth International Conference on Sensor Technologies and Applications (SENSORCOMM), Venice, Italy, 18–25 July 2010; pp. 262–268. [Google Scholar]
- Heinzelman, W.B.; Chandrakasan, A.P.; Balakrishnan, H. An Application-Specific Protocol Architecture for Wireless Microsensor Networks. IEEE Trans. Wirel. Commun. 2002, 1, 660–670. [Google Scholar] [CrossRef]
- Muruganathan, S.D.; Ma, D.C.; Bhasin, R.I.; Fapojuwo, A.O. A Centralized Energy-Efficient Routing Protocol for Wireless Sensor Networks. IEEE Commun. Mag. 2005, 43, S8–S13. [Google Scholar] [CrossRef]
- Ganesan, D.; Govindan, R.; Shenker, S.; Estrin, D. Highly-Resilient, Energy-Efficient Multipath Routing in Wireless Sensor Networks. ACM SIGMOBILE Mob. Comput. Commun. Rev. 2001, 5, 11–25. [Google Scholar] [CrossRef]
- Coppersmith, D.; Jakobsson, M. Almost Optimal Hash Sequence Traversal. In Proceedings of the International Conference on Financial Cryptography, Bermuda, UK, 11–14 March 2002; pp. 102–119. [Google Scholar]
- Perrig, A.; Canetti, R.; Song, D.; Tygar, J.D. Efficient and Secure Source Authentication for Multicast. In Proceedings of the Network and Distributed System Security Symposium, NDSS, San Diego, CA, USA, 7–9 February 2001; pp. 35–46. [Google Scholar]
- Liu, C.; Cao, G. Spatial-Temporal Coverage Optimization in Wireless Sensor Networks. IEEE Trans. Mob. Comput. 2011, 10, 465–478. [Google Scholar] [CrossRef]
- Du, W.; Deng, J.; Han, Y.S.; Varshney, P.K.; Katz, J.; Khalili, A. A Pairwise Key Predistribution Scheme for Wireless Sensor Networks. ACM Trans. Inf. Syst. Secur. 2005, 8, 228–258. [Google Scholar] [CrossRef]
- Blom, R. An Optimal Class of Symmetric Key Generation Systems. In Proceedings of the Workshop on the Theory and Application of Cryptographic Techniques, Paris, France, 9–11 April 1984; pp. 335–338. [Google Scholar]
- Blundo, C.; De Santis, A.; Herzberg, A.; Kutten, S.; Vaccaro, U.; Yung, M. Perfectly-Secure Key Distribution for Dynamic Conferences. In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 16–20 August 1992; pp. 471–486. [Google Scholar]
- Liu, D.; Ning, P. Location-Based Pairwise Key Establishments for Static Sensor Networks. In Proceedings of the 1st ACM Workshop on Security of Ad Hoc and Sensor Networks, Washington, DC, USA, 27–30 October 2003; pp. 72–82. [Google Scholar]
- Liu, D.; Ning, P.; Li, R. Establishing Pairwise Keys in Distributed Sensor Networks. ACM Trans. Inf. Syst. Secur. 2005, 8, 41–77. [Google Scholar] [CrossRef]
- Ah Kioon, M.C.; Wang, Z.S.; Deb Das, S. Security Analysis of Md5 Algorithm in Password Storage. Appl. Mech. Mater. 2013, 347–350, 2706–2711. [Google Scholar] [CrossRef]
- Lu, R.; Lin, X.; Zhu, H.; Liang, X.; Shen, X. BECAN: A Bandwidth-Efficient Cooperative Authentication Scheme for Filtering Injected False Data in Wireless Sensor Networks. IEEE Trans. Parallel Distrib. Syst. 2012, 23, 32–43. [Google Scholar]
- Johnson, D.B. A Note on Dijkstra’s Shortest Path Algorithm. J. ACM 1973, 20, 385–388. [Google Scholar] [CrossRef]
- Yang, X.; Lin, J.; Yu, W.; Moulema, P.; Fu, X.; Zhao, W. A Novel En-Route Filtering Scheme Against False Data Injection Attacks in Cyber-Physical Networked Systems. IEEE Trans. Comput. 2015, 64, 4–18. [Google Scholar] [CrossRef]
- Nam, S.M.; Cho, T.H. A Fuzzy Rule-Based Path Configuration Method for LEAP in Sensor Networks. Ad Hoc Netw. 2015, 31, 63–79. [Google Scholar] [CrossRef]
- Al-Riyami, A.; Zhang, N.; Keane, J. An Adaptive Early Node Compromise Detection Scheme for Hierarchical WSNs. IEEE Access 2016, 4, 4183–4206. [Google Scholar] [CrossRef]
- Ye, F.; Chen, A.; Lu, S.; Zhang, L. A Scalable Solution to Minimum Cost Forwarding in Large Sensor Networks. In Proceedings of the Tenth International Conference on Computer Communications and Networks, Scottsdale, AZ, USA, 15–17 October 2001; pp. 304–309. [Google Scholar]
- Al-Karaki, J.N.; Kamal, A.E. Routing Techniques in Wireless Sensor Networks: A Survey. IEEE Wirel. Commun. 2004, 11, 6–28. [Google Scholar] [CrossRef]
- Lee, G.; Kong, J.; Lee, M.; Byeon, O. A Cluster-Based Energy-Efficient Routing Protocol without Location Information for Sensor Networks. J. Inf. Process. Syst. 2005, 1, 49–54. [Google Scholar] [CrossRef]
- Serrano, N.; Seraji, H. Landing Site Selection using Fuzzy Rule-Based Reasoning. In Proceedings of the 2007 IEEE International Conference On Robotics and Automation, Roma, Italy, 10–14 April 2007; pp. 4899–4904. [Google Scholar]
- Jelušič, P.; Žlender, B. Discrete Optimization with Fuzzy Constraints. Symmetry 2017, 9, 87. [Google Scholar] [CrossRef]
- Lee, K.H. First Course on Fuzzy Theory and Applications; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2006. [Google Scholar]
- Balázs, K.; Kóczy, L.T.; Botzheim, J. Comparison of Fuzzy Rule-Based Learning and Inference Systems. In Proceedings of the 9th International Symposium of Hungarian Researchers on Computational Intelligence and Informatics, CINTI, Budapest, Hungary, 5–8 November 2008; pp. 61–75. [Google Scholar]
- Moon, S.Y.; Cho, T.H. Key Index-Based Routing for Filtering False Event Reports in Wireless Sensor Networks. IEICE Trans. Commun. 2012, 95, 2807–2814. [Google Scholar] [CrossRef]
- Heinzelman, W.R.; Chandrakasan, A.; Balakrishnan, H. Energy-Efficient Communication Protocol for Wireless Microsensor Networks. In Proceedings of the 33rd Annual Hawaii International Conference on System Sciences, Maui, HI, USA, 7 January 2000; Volume 2, p. 10. [Google Scholar]
- Sun, C.I.; Lee, H.Y.; Cho, T.H. A Path Selection Method for Improving the Detection Power of Statistical Filtering in Sensor Networks. J. Inf. Sci. Eng. 2009, 25, 1163–1175. [Google Scholar]
- Kim, J.M.; Han, Y.S.; Lee, H.Y.; Cho, T.H. Path Renewal Method in Filtering Based Wireless Sensor Networks. Sensors 2011, 11, 1396–1404. [Google Scholar] [CrossRef] [PubMed]
- Lee, H.; Cho, T. Fuzzy-Based Reliable Data Delivery for Countering Selective Forwarding in Sensor Networks. In Proceedings of the 4th international conference on Ubiquitous Intelligence and Computing, Hong Kong, China, 11–13 July 2007; pp. 535–544. [Google Scholar]
- Younis, O.; Fahmy, S. HEED: A Hybrid, Energy-Efficient, Distributed Clustering Approach for Ad Hoc Sensor Networks. IEEE Trans. Mob. Comput. 2004, 3, 366–379. [Google Scholar] [CrossRef]
- Uluagac, A.S.; Beyah, R.A.; Copeland, J.A. Secure Source-Based Loose Synchronization (SOBAS) for Wireless Sensor Networks. IEEE Trans. Parallel Distrib. Syst. 2013, 24, 803–813. [Google Scholar] [CrossRef]
- Perrig, A.; Szewczyk, R.; Tygar, J.D.; Wen, V.; Culler, D.E. SPINS: Security Protocols for Sensor Networks. Wirel. Netw. 2002, 8, 521–534. [Google Scholar] [CrossRef]
- Nasser, N.; Chen, Y. SEEM: Secure and Energy-Efficient Multipath Routing Protocol for Wireless Sensor Networks. Comput. Commun. 2007, 30, 2401–2412. [Google Scholar] [CrossRef]
- Chen, Y.; Nasser, N. Energy-Balancing Multipath Routing Protocol for Wireless Sensor Networks. In Proceedings of the 3rd International Conference on Quality of Service in Heterogeneous Wired/Wireless Networks, Waterloo, ON, Canada, 7–9 August 2006; p. 21. [Google Scholar]
- Liu, B.; Pham, V.; Nguyen, N. An Efficient Algorithm of Constructing Virtual Backbone Scheduling for Maximizing the Lifetime of Dual-Radio Wireless Sensor Networks. Int. J. Distrib. Sens. Netw. 2015, 11, 475159. [Google Scholar] [CrossRef]
- Liu, B.; Pham, V.; Nguyen, N. A Virtual Backbone Construction Heuristic for Maximizing the Lifetime of Dual-Radio Wireless Sensor Networks. In Proceedings of the 2015 International Conference on Intelligent Information Hiding and Multimedia Signal Processing (IIH-MSP), Adelaide, Australia, 23–25 September 2015; pp. 64–67. [Google Scholar]
- Nguyen, N.; Liu, B.; Pham, V.; Luo, Y. On Maximizing the Lifetime for Data Aggregation in Wireless Sensor Networks using Virtual Data Aggregation Trees. Comput. Netw. 2016, 105, 99–110. [Google Scholar] [CrossRef]
| Rule No. | IF | THEN | ||
|---|---|---|---|---|
| NKIH | DIST | REVN | Fitness | |
| 01 | Less | Near | Low | Poor |
| 03 | Less | Near | High | Moderate |
| 13 | Moderate | Fair | Low | Poor |
| 14 | Moderate | Fair | Medium | Better |
| 15 | Moderate | Fair | High | Best |
| 20 | More | Near | Medium | Best |
| 21 | More | Near | High | Best |
| 23 | More | Fair | Medium | Better |
| 24 | More | Fair | High | Best |
| Parameters | Value |
|---|---|
| Number of nodes | 4000 |
| Network size | 1000 × 1000 m2 |
| Base station location | 0 × 0 m |
| Number of clusters | 400 |
| Nodes in a cluster (cluster size) | 10 |
| Votes required to endorse a report (s) | 5 |
| False votes threshold to drop a report (Tf) | 3 |
| Votes required to accept a report as true report (Tt) | 4 |
| Size of report | 36 bytes |
| Size of MAC | 4 bytes |
| Energy consumed to: | |
| Generate a MAC | 15 μJ |
| Verify a report | 75 μJ |
| Transmit/receive a byte | 16.25/12.5 μJ |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Akram, M.; Cho, T.H. Energy Efficient Fuzzy Adaptive Verification Node Selection-Based Path Determination in Wireless Sensor Networks. Symmetry 2017, 9, 220. https://doi.org/10.3390/sym9100220
Akram M, Cho TH. Energy Efficient Fuzzy Adaptive Verification Node Selection-Based Path Determination in Wireless Sensor Networks. Symmetry. 2017; 9(10):220. https://doi.org/10.3390/sym9100220
Chicago/Turabian StyleAkram, Muhammad, and Tae Ho Cho. 2017. "Energy Efficient Fuzzy Adaptive Verification Node Selection-Based Path Determination in Wireless Sensor Networks" Symmetry 9, no. 10: 220. https://doi.org/10.3390/sym9100220




