1. Introduction
Future mobile network experience two challenges. First is the traditional problem—the performance or data-rate. Second is the new issues—the low latency and the cloud-based network services. According to the first topic, modern society has experienced a rapid data traffic volume increase, since the emergence of smartphones, which has created a dramatic increase in the number of mobile users and mobile services. In fact, data traffic volume increase caused by mobile equipment such as smartphones, portable PCs and tablets increased by 65% in 2015’s third quarter compared to that in 2014’s third quarter [
1]; moreover, its level is expected to reach 24.3 EB (Exabyte) in 2019 [
2]. With the emergence of drastically increased mobile data traffic, it is essential to have 5G network technology for innovation and evolution of original networks. Recognizing this demand, research on 5G networks is being conducted worldwide and Europe’s mobile and wireless communications enablers for twenty-twenty information society (METIS 2020), the 3rd Generation Partnership Project (3GPP), 5GPP, China’s IMT-2020 and Korea’s 5G forum and other various relevant groups are discussing the vision and requirements for 5G networks [
3,
4].
About the second issue—the low latency and the cloud-based network services, technologies for the datacenters of the IT companies, such as Google and Amazon, are deployed into the Telco’s mobile networks. The cloud computing of the IT companies enables the hardware and software separation in Telco’s networks, which means the traditional hardware product-oriented network architecture changes to the function-oriented flexible network architecture. By using cloud computing technologies, telecom companies can enable the access and core networking functionalities at the optimal place with dynamically managed capacity. This idea changed the fundamental of the mobile networks and the 5G uses these concepts as the underlying principle for the future network design. The 5G network is based on virtualization different from the original network system. It is based on software-defined networking (SDN) and network function virtualization (NFV). In particular, NFV technology enables networks to be maintained in a cost-efficient way by replacing previously necessary physical appliances with virtualized environments. 5G networks applying this technology have the advantage of comprising flexible networks by arranging virtualized network function (VNF), which is virtualized according to the user’s requirement. However, to apply NFV technology, IT virtualization and cloud technology is needed and to apply this technology, equipment with high specifications is required. This can result in difficulties in usability outside the cases of communications enterprises or data center management corporations [
5]. So, various researchers have been conducted on the topic of cost-optimal design of 5G virtualized networks recently [
6,
7,
8,
9].
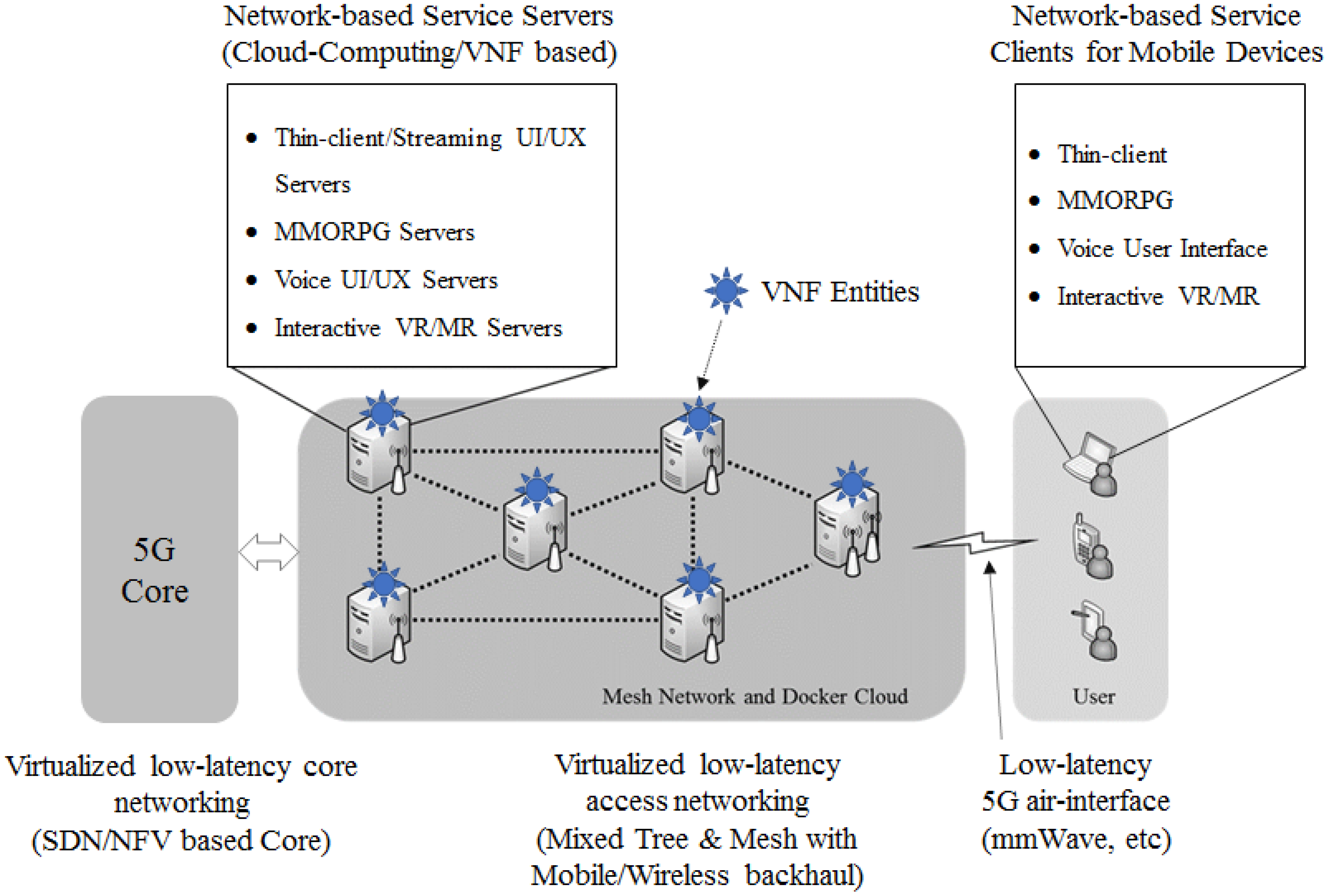
However, it is not enough to solve the requirements about the low latency service and the cloud computing based network services as in
Figure 1. The cloud computing based network service examples are the thin-clients (e.g., Google Chromium OS) [
10], the voice user interface intelligent services (e.g., Apple Siri, Google Now and Speech, Amazon Alexa and Echo), the multimedia MMORPG computer games and the interactive virtual and mixed reality services. The commonality of these services is that the user’s smartphone or computer equipment is mainly used for input and output with the user and most of the computing processing is done on the servers of the network. Therefore, the communication delay in the network must be very small and a network structure in which the user’s service can be dynamically driven at a desired place flexibly in order to allow users to freely use such a service anytime and anywhere. Recently, research on MEC (Mobile Edge Computing) has been actively started for such a network [
11]. This should be viewed as a resource for cloud computing and to ensure that the user’s services are running smoothly. Therefore, the network service software should be located dynamically to the location closest to the user and the transport layer of the network should also be capable of ultra-low latency. This makes it possible for users to experience the same processing as if they were using their network-based services.
Thus, we deal with the virtualized network function orchestration of cloud computing-based network services in mobile networks. We propose a new architecture which enables the flexible network service deployment and orchestration over the future mobile network like Beyond 4G and 5G mobile work. And, to evaluate the proposed architecture, we deploy a real cloud computing based QR code recognition application. Thus, we design and implement the new architecture and network applications in a real testbed system and proved the feasibility and performant of the proposed architecture. Especially, in consideration of the cost of 5G network settings, this paper discusses using low-cost equipment for virtualization in a network orchestration system to reduce CAPEX and OPEX further based on requirements.
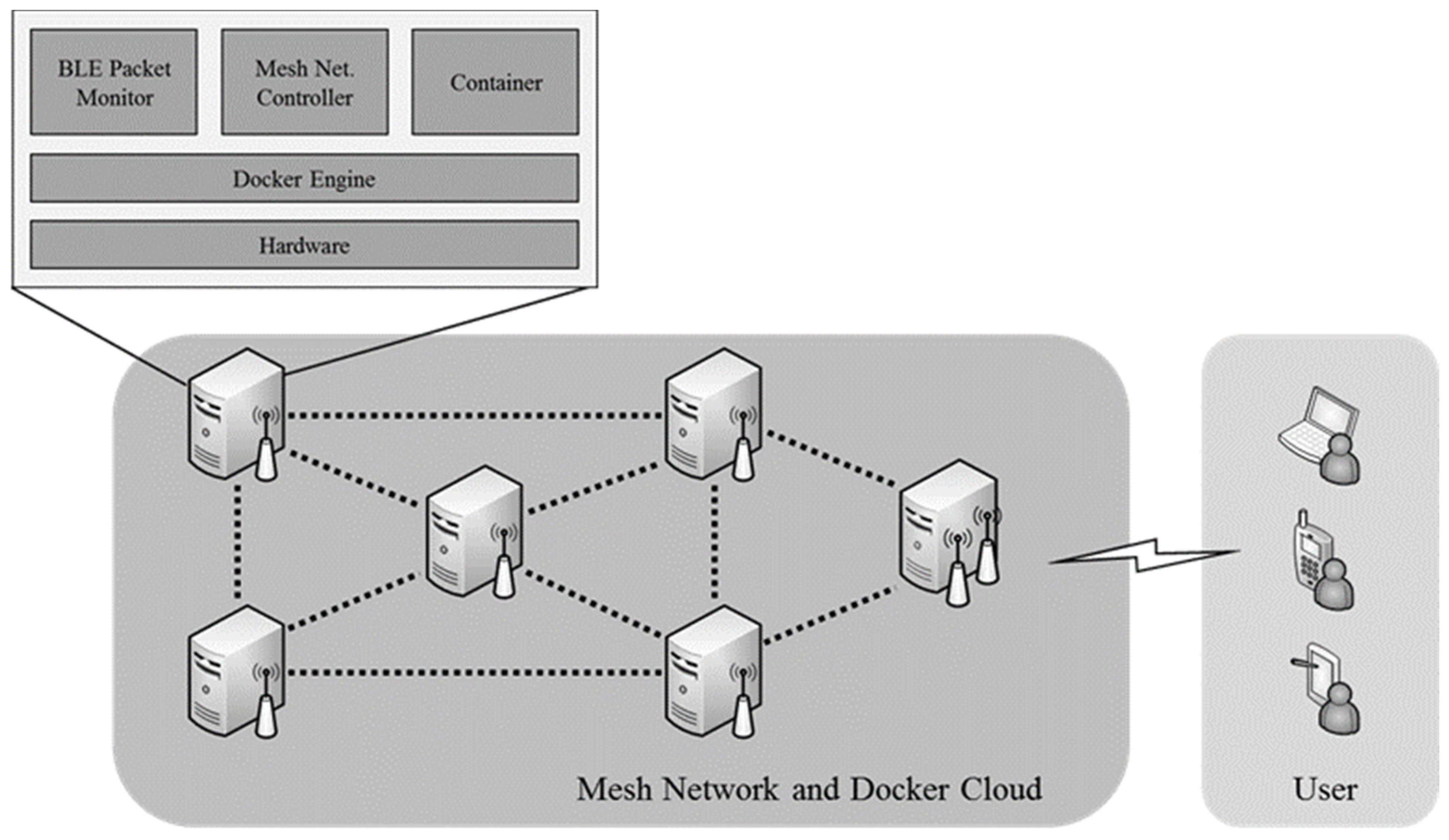
Short description about the real system testbed, tree and mesh networking technology for wireless network connections between the network and Docker, which is a light-weight open-source virtualization technology, is used [
12]. The mobile network is traditionally tree-based hierarchical network in both access and core network but as the millimeter wave (mmWave) technologies are used in 5G mobile networks, radio cell size is relatively smaller than conventional 3G/4G networks. Thus, mobile backhaul should be used to connect adjacent mmWave base-stations to reduce the wired backhaul CAPEX/OPEX. Thus, we consider mesh-network topology also for our contribution and a real testbed construction. In a real testbed system, by using the technologies mentioned above, a virtualized network function orchestration system for 5G mobile access networks is designed and implemented. The proposed system can be built with general hardware and open-source software based on virtualization technology and can provide high availability by providing seamless network function. Thereby, we can achieve network infrastructure with much lower cost and quickly adopt network/user service. Furthermore, through low adoption/development cost, we can activate network building in developing countries and provide computing environments more widely. Furthermore, by selecting the open hardware and software platform—Raspberry Pi, as the network device for the proposed system’s evaluation, we enable system composition at low cost [
13]. Moreover, the necessary characteristics for a virtualized network function orchestration system for 5G mobile access environments are defined and verified by establishing a system that can satisfy this need.
Also, this paper proposes a QR code recognition method that uses an image-matching method and advances existing research. However, the proposed virtualization based network architecture is not limited to the QR code reorganization services and it can be used in wide areas in mobile network services. This study does not operate existing QR identification software on the proposed platform. The existing QR code recognition recognizes the QR code through the software inside the terminal such as a smartphone—a stand-alone approach. However, we proposed a new QR code recognition technology based on cloud computing in the network in the proposed virtualization environment—a network computing approach. Through this, the recognition rate of the QR code recognition is greatly improved and the virtual network based service architecture can demonstrate that the performance of the actual application service can be improved. More about the proposed network based QR code recognition technology, this has the purpose of reducing the device’s workload to solve the existing recognition problem by performing distributed processing of many images through previously discussed cloud environments like Docker. Actually, the original QR code recognition order starts with recognizing the three finder patterns. However, finder pattern recognition methods have the problem of not recognizing a pattern’s specific ratio when QR codes are not scanned accurately from the front side. Above a certain angle, the pattern’s original ratio is broken and it cannot be recognized even in a high-definition image taken at close distance. We enhance the recognition performance with scalable computing and big-data approach at the edge side of the mobile networks.
The structure of this paper is as follows. The first and second sections introduce and explain the virtualized network function orchestration system and related research. The third section explains the system and its characteristics and the fourth section introduces and analyzes the evaluation of the function implemented in a real test bed. And, we conclude the paper in the fifth section with a summary and considerations for possible future works.
2. Related Works
Related research includes wireless mesh networks, which are connection-oriented and favorable for automatic network composition and Docker cloud platforms for implementing the virtualization. Additionally, since this paper evaluates the performance of multiple image search forms’ QR code recognition as the proposed orchestration system’s use case, it explains the QR code recognition method, which is relevant original research. This section explains the above related research and discusses its differences from the proposed method in this paper.
2.1. Wireless Mesh Networks
As mentioned previously, wireless mesh networks are the appropriate networking technology for connection-oriented network composition. In particular, wireless mesh networks have the characteristics of self-composition and self-recovery and have the advantage that they can communicate with other paths even if the original path is disconnected [
14]. Hence, with reduced cost and time in composing network deployment considering infrastructure-based wireless mesh networks, the network function orchestration system is shown to be appropriate.
However, in the status quo of mesh network composition, since the amount of information exchange for routing increases according to network size, there is a trend of overhead drastically increasing. In particular, in order to compose dynamic networks that are characteristic of mesh networks, every termination needs to be recognized and searched in the form. Hence, in order to reduce this overhead, research for developing wireless mesh network routing is currently active.
Routing research in wireless networks has been actively pursued, focusing on mobile ad hoc networks, routing protocols including dynamic source routing (DSR), ad hoc on-demand distance vector routing protocol (AODV) and optimized link state routing protocol (OLSR) have been developed [
15,
16]. In particular, the IEEE 802.11s wireless mesh networks standard uses the hybrid wireless mesh routing protocol (HWMP) [
13]. This routing protocol has a structure that combines AODV and tree-based routing and conducts double-layered routing. However, the above methods all require a large amount of time, or have the disadvantage of incurring more overhead with routing table update process.
Thus, this paper composes flexible networks by reducing network overhead, applying Better Approach to Mobile Ad hoc Networking (BATMAN) routing protocol. This method implements routing based on the information of nearby nodes, in contrast to the original mesh network routing method, which needs to recognize the information of all nodes.
BATMAN
BATMAN, invented by the Freifunk community, is a multi-hop routing protocol for mobile ad hoc mesh networks [
17]. This protocol was invented to overcome the limitations of the OLSR protocol and to replace it.
This protocol implements routing in double-layered fashion instead of triple-layered, enabling communication between terminals without an IP. From this point of view, it has the advantage that it is easy to connect with non-mesh terminals.
The BATMAN protocol does not have a routing table for each node, unlike the original protocol and also has information regarding nearby nodes; therefore, it does not suffer from onerous overhead during the routing table update procedure.
This protocol’s operation process is as follows. Each node broadcasts the originator message (OGM) and notifies nearby nodes of the existence of a note. The nodes that receive the message broadcast the OGM message again. The OGM has a size of 52 bytes in a small packet, including the message’s start address, the address where the packet has been delivered, TTL and the sequence number. Ultimately, each note, through OGM, can update the optimum node among the nearby nodes, know the optimum path between terminals and obtain information regarding link functions. Through the above procedure, without incurring excessive routing overhead, providing an optimum path is possible; and since table correction becomes faster owing to the terminal’s move, a much more flexible mobile mesh network can be constituted.
2.2. Docker Virtualization Technology
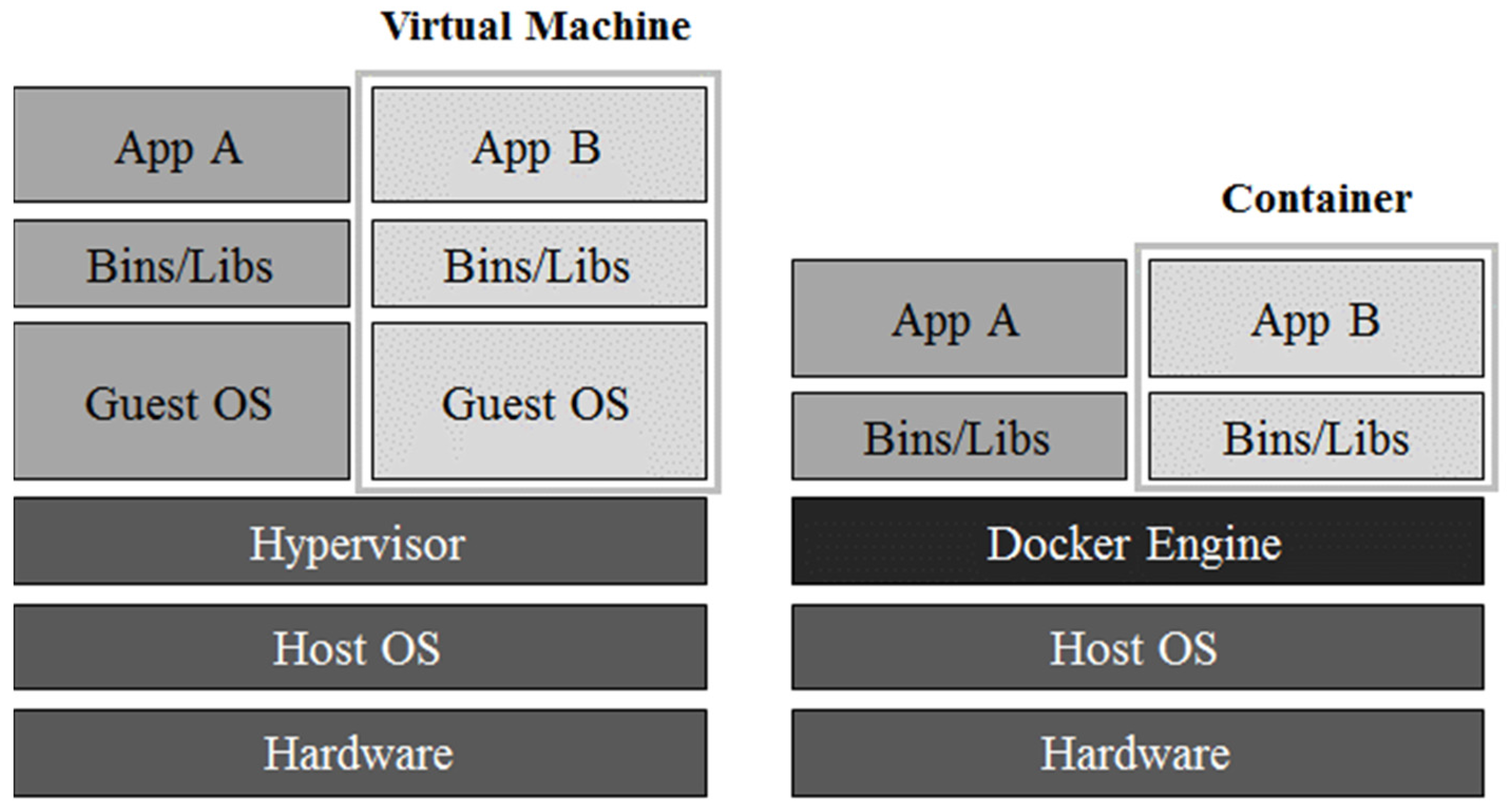
A docker is a light-weight, open-source virtualization technology. It provides light-weight virtualization by using a container based on LXC, which has a different form from the original virtual machine.
Figure 2 shows a hierarchy diagram of a virtual machine and Docker, which shows the hierarchical difference between the two technologies. As illustrated for the case of a virtual machine, resources are allocated based on a hypervisor and the new guest management system is then executed, which has the problem of performance reduction due to excessive overhead. On the other hand, in the case of a docker, by using the form of host management system and sharing the resources and adding the library and executable files that are needed for the implementation of application, instead of using the form of newly creating guest management system, a container is created. Thus, since a Docker creates less overhead than a virtual machine and requires smaller file size to create the container, it can be quickly installed. Based on these characteristics, a Docker is flexible in version management, capable of using resources efficiently and has the advantage of application portability.
However, it has the disadvantage that it cannot realize the migration function owing to the container composition provided by the virtual machine. Because of this, when a container is relocated, there is the problem that the container’s service starts from the beginning.
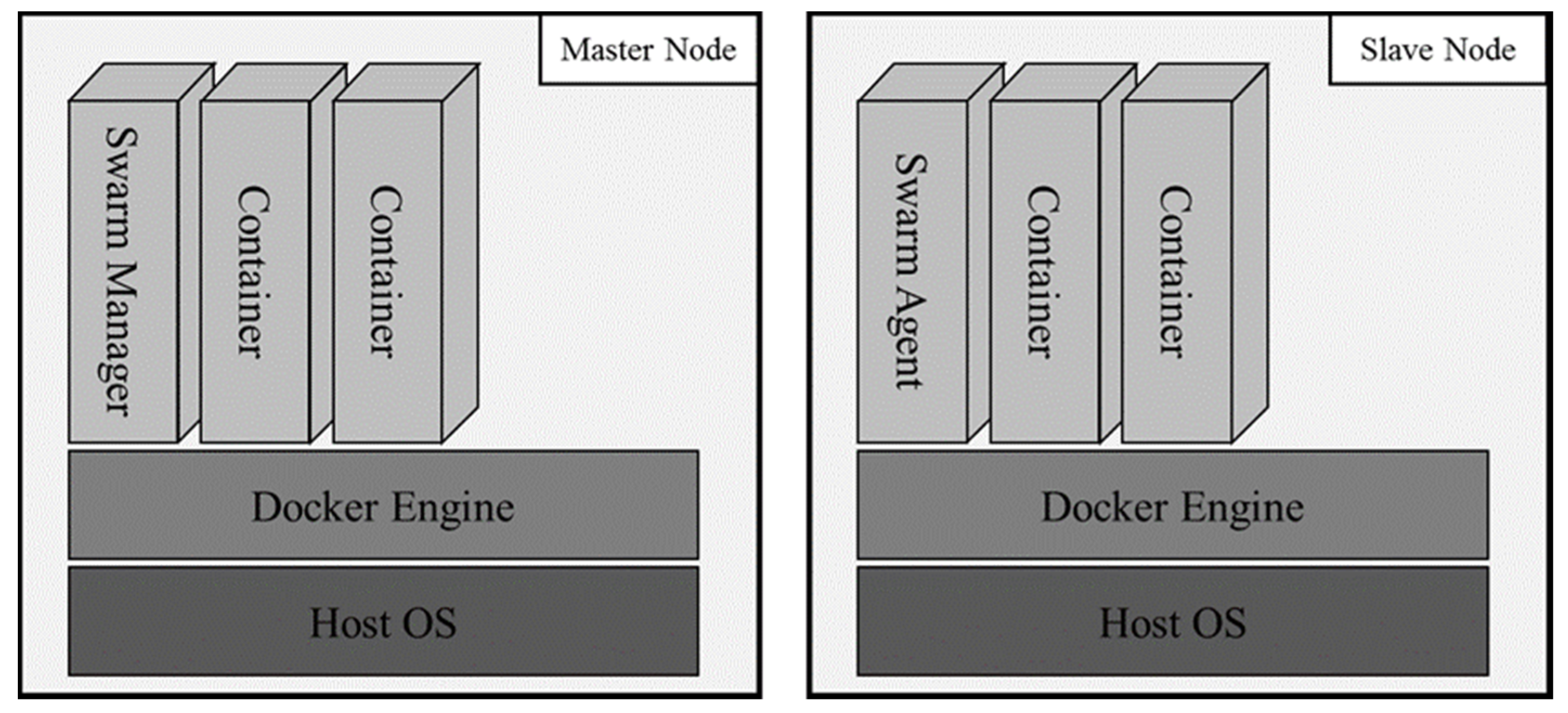
To locate and manage the virtualized network function in the proposed orchestration system, a Docker swarm, which is a cluster management tool, is used [
18].
2.3. QR Code Recognition Method
QR codes were developed by the Denso Wave Incorporated in Japan in 1994 for the purpose of increasing information quantity and minimizing information damage to 1D barcodes such as European Article Number (EAN)/Universal Product Code (UPC), which are known as the original barcodes [
19]. QR codes are 2D barcodes designed to read in information once 30 to 700 times faster than original EAN/UPC barcodes. Furthermore, they can handle content including but not limited to numbers, English, Chinese characters, Korean characters, symbols, binary and control codes. Furthermore, they can express letters or numbers up to 7089 in a single code. 2D codes include error-restoring functions so that they are not adversely affected, even faced with some information damage, owing to their ability to supplement the deficiencies of original bar code.
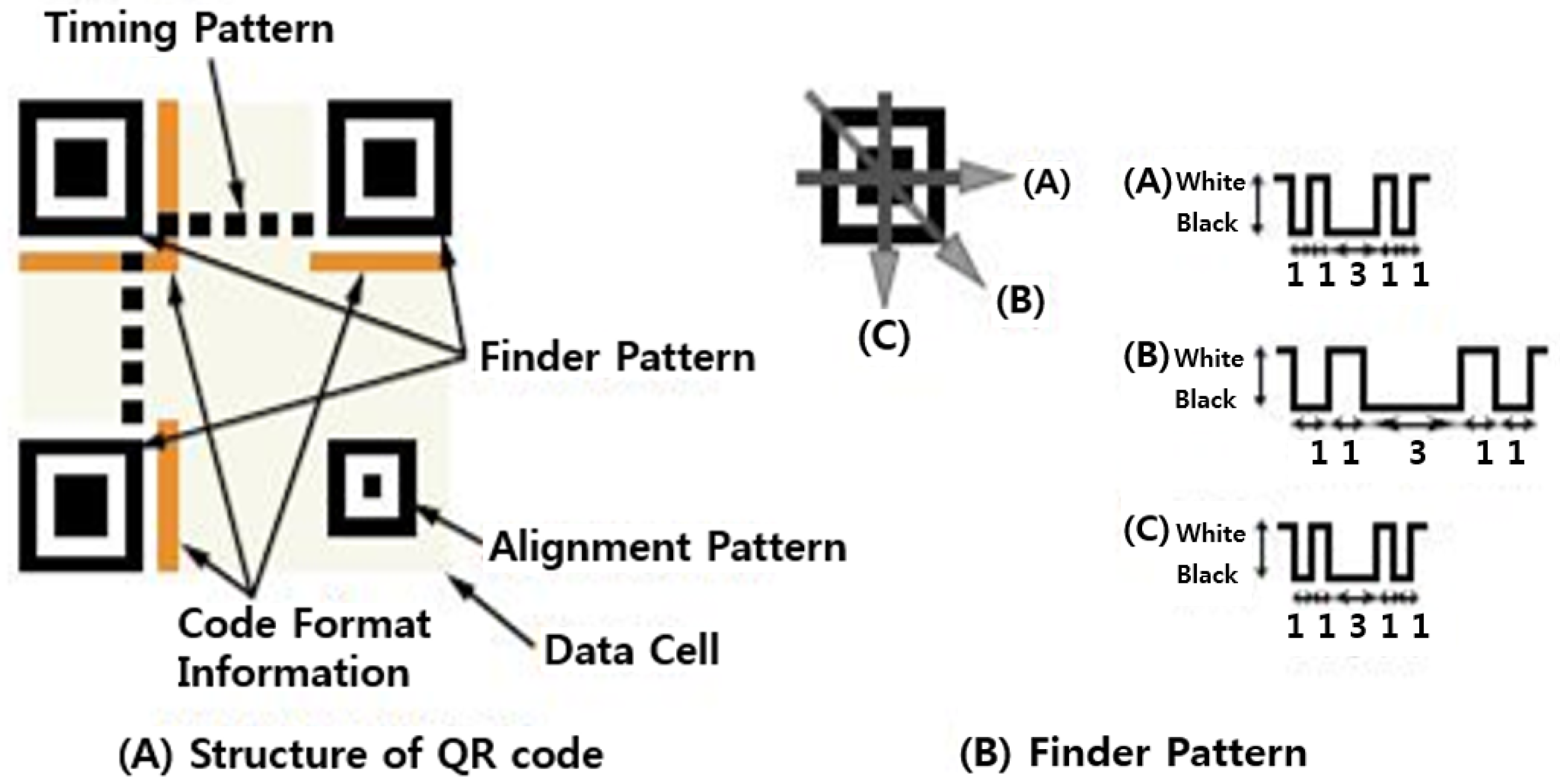
One characteristic of QR codes is that it is possible to recognize them in any direction. The reason for this is that they have three finder pattern symbols as shown in
Figure 4, which enables recognizing QR codes using these patterns [
19]. Since these patterns have a white-to-black ratio of 1:3:1:1 in any direction, QR codes are recognizable in any direction.
With the above advantages, QR codes are usefully utilized in various situations, such as printed fliers, name cards, payment systems and factory or distribution businesses. As the boundary of usage has increased to various new fields, ways of recognizing QR codes have been studied extensively [
20,
21,
22].
The original QR code recognition order starts with recognizing the three finder patterns. With three patterns around the center, reading proceeds by finding information including the size of the module and its format and then decoding the QR code based on this. Researchers in recognition methods have developed recognition methods by focusing first on ways to recognize finder patters.
However, finder pattern recognition methods have the problem of not recognizing a pattern’s specific ratio when QR codes are not scanned accurately from the front side. Above a certain angle, the pattern’s original ratio is broken and it cannot be recognized even in a high-definition image taken at close distance.
3. Proposed Virtualized Network Function Orchestration System
Before going into details, the definitions of the characteristics needed in the proposed system are explained. First, the system must be in a form that can expand easily to a connection-oriented system. Since this is not a wired network composition, in wireless situations, seamless connection between network devices is important and scalability based on the situation must be confirmed. Secondly, the system needs to provide ensured service to users. Since every network function is activated in a container which is a virtual environment, before the container is concluded, the virtualized network function recovery procedure is necessary, moving it to another network device. Lastly, according to the device’s condition, the system must decide the network function arrangement; through this, it should distribute the workload. Considering these characteristics, the proposed orchestration system is discussed below.
This section explains the composition method and procedure of the proposed virtualized network function orchestration system. In addition, as a solution to the recognition problem related to QR codes’ scanning angles, we explain a QR code recognition method based on the multiple-image search method. This is a suitable recognition method for environments that can locate the service spread, using the proposed orchestration system. By applying this recognition method to user service using a virtualized network function orchestration system, the system’s distributed arrangement function is checked.
3.1. Network Automatic Configuration Method Based on Bluetooth Low Energy (BLE)
This paper proposes a networking method based on Bluetooth beacons for automatic mesh network configuration between a network’s devices. Firstly, mesh networks are suitable for dynamic wireless network configuration and are effective for configuring a connection-oriented configuration, as explained above. This configuration has the purpose of automatic network configuration that can dynamically configure when a network is needed rather than a network that needs to previously register the same Service Set Identifier (SSID) and channel information for a particular purpose. To dynamically configure the network upon request or input, a Bluetooth beacon is used. Additionally, allowed network devices with Bluetooth beacons can easily enter a network, which leads to advantages in network configuration and expansion in mobile environments. By transmitting network information and activating a nearby terminal’s network devices using a beacon, network configuration following a user’s requests is made possible.
First, through Bluetooth beacons, a device transmitting network information is activated as the master node and other devices on the same network are categorized as member nodes. The determination of master and member nodes is made by the network device that created a mesh network in the first place and, following the user’s requests or input, various network devices can be activated as the master node. This node, to receive the user’s request, creates an access point for the user’s access, excluding the access point for the mesh network. For this, the master node needs to have one more network interface that allows it to obtain the response from this node and provide the requested service. Next, to transmit the data through the service request, a network device needs two things: a network interface card for network configuration and a network interface card for user acceptance.
Next, in clustering using a Docker swarm, the network’s mater node becomes the Docker swarm’s master and member nodes are activated in the role of agents. However, the situation wherein network devices are simultaneously on is then excluded and it is assumed that one device can be activated as the master first.
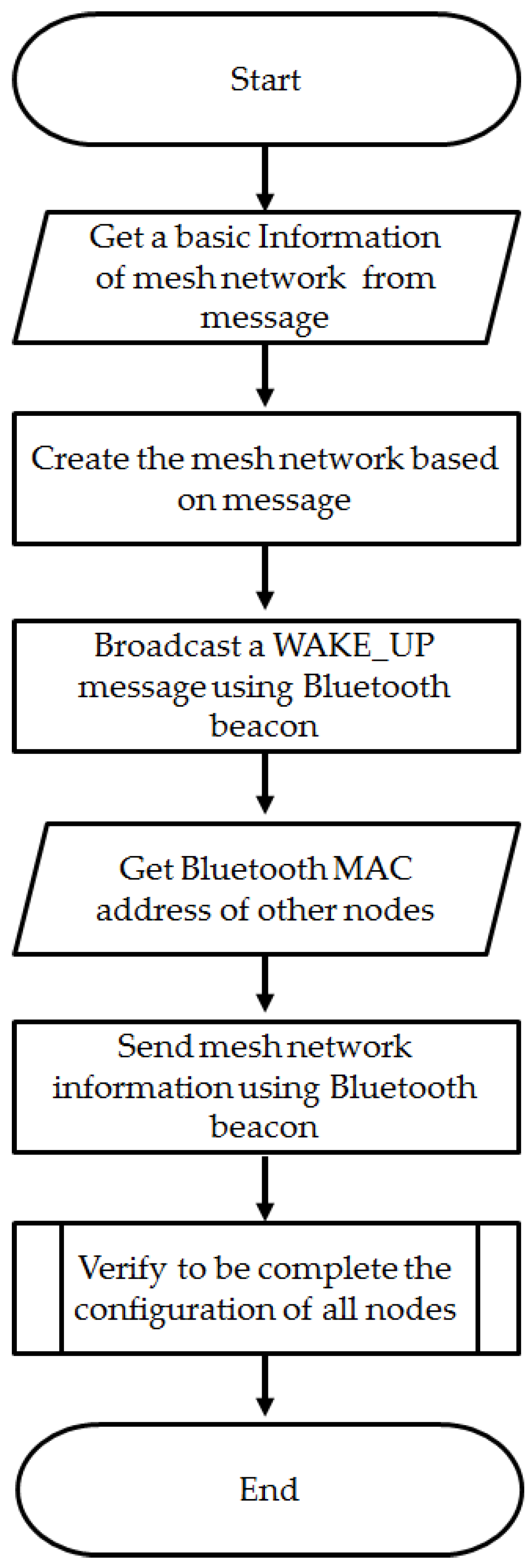
Every node, as in
Figure 5, has a monitoring module to recognize beacon information and a mesh network controller module to establish the network with the information received through the beacon. Each module’s operational process is explained in detail below.
Bluetooth-Beacon-Based Mesh Network Controller
To realize the proposed Bluetooth-beacon-based mesh network controller, a BLE packet monitor and mesh network controller that recognize the Bluetooth beacon packet are needed.
Figure 6 and
Figure 7 shows the master node’s and member node’s mesh network controllers’ operational process, respectively. As mentioned above, the network device that first received the network information input is activated as the master node.
First, the master node’s controller (
Figure 6) configures the mesh network that used the BATMAN protocol based on the information received by using the device’s wireless network interface. The proposed mesh network configuration needs information regarding SSID, channel and IP address as well. This procedure composes the network in a faster way and enables configuring the network using low-energy Bluetooth, which is more energy-efficient than using a wireless beacon. In order to communicate through a Bluetooth beacon, each network device activates its BLE-packet-monitoring module. Thereby, it sends a message that wakes up similar nodes with the Bluetooth beacon packet and then broadcasts. By receiving the beacon packet that responded to the WAKE_UP message, the device obtains the Bluetooth MAC address. Through the obtained address, it transmits the mesh network information stored in the mesh network controller and implements a confirmation procedure as to whether every device received the response or not.
The response confirmation procedure and following procedures differ according to the user’s input. The implementation procedure is divided into two cases: the situation of continuously providing a network connection and the situation of providing the network connection for a limited time. According to the previous procedure, when the response was confirmed for every device that received the message, for the support of the new device’s network configuration, a WAKE_UP message is transmitted and the procedure of providing network information once again is implemented. In the case where all responses do not return, the procedure resubmits network information to the Bluetooth MAC address that is obtained in previous step. Before the master node’s controller device concludes, this procedure takes the role of transmitting the Bluetooth beacon signal to the near side continuously. In the opposite case, even if all responses have been received, if a certain amount of time passes, the WAKE_UP message is not created. When the response is not received, the procedure is the same as the previous procedure. This procedure, after a certain amount of time, ends the controller and is suitable for structures that do not require network expansion.
In the first instance, network information can be broadcast in a Bluetooth beacon packet since the network environment provides service to users but it does not allow the inflow of every node and through this procedure mutual cognition can be performed.
A member node, as shown in
Figure 7, scans the WAKE_UP message through its BLE-packet-monitoring module. When the WAKE_UP message arrives through a received packet, it obtains the master node’s MAC address and responds. When a Bluetooth beacon packet that contains a network address arrives at the same address, by using this result (in the same condition as for the master node), the mesh network is configured through the device’s wireless network interface. When the configuration is finished, a completion message is sent and the process concludes.
Figure 8 shows the mutual recognition and information exchange process of the proposed mesh network controller. The following content shows the order of each node’s operational process.
As process 1.1, the master node transmits information from the user to the mesh network controller and, based on this information, the module in process 1.2 broadcasts the message that awakens nearby similar nodes as process 2.1 through a Bluetooth beacon packet. Next, it receives the beacon packet that responds from the master node’s BLE-packet-monitoring module to the Bluetooth MAC address and, as in process 3.1, it transmits the information for the mesh network controller to the Bluetooth MAC address received from the incoming packet.
As in process 3.1, a member node transmits the received information to the mesh network controller through its BLE-packet-monitoring module and as in process 3.2, it participates in the network by composing a mesh network through the received information. After network configuration, the member node’s mesh network controller transmits a ‘setup completed’ message to the master node’s module. This process is shown in
Figure 8 as process 3.3.
3.2. Cluster Management Method for the Arrangement of VNFs
This paper proposes a form of arranging service in a dynamic way as a 5G network with cluster composition for virtualized network function arrangement based on dynamic network composition. As explained above, since a Docker is lighter than the existing virtual machine, it is suitable for use in the proposed method to compose a system using open-source hardware. However since a container is activated with the process, it cannot provide functions like virtual machines when relocation or movement is conducted. Virtual machines, when restarted from the stopped condition, can provide continuity by starting from the stopped point; but in the case of a container, since it needs to start from the very beginning, it cannot provide continuity, which is a deficiency. The proposed virtualized network function orchestration system explains the method of providing continuity for the container and through this, it presents a method that has low overhead and provides service continuity. The proposed method based on the Docker virtualized platform, network resource sharing between devices using a Docker swarm and load monitoring, locates network functions. When actions such as relocation are committed, a method is proposed for restarting from the point at which the process stopped by reporting the action status.
As seen in the network configuration method above, the roles of the master and member nodes is the same and the Docker swarm manager container is created at the master node while, at member nodes, the Docker swarm agent container is distributed. While the existing Docker swarm recognition method is a Docker-hub-based online method, the proposed method achieves recognition offline through IP, replacing the IP information given during network setting.
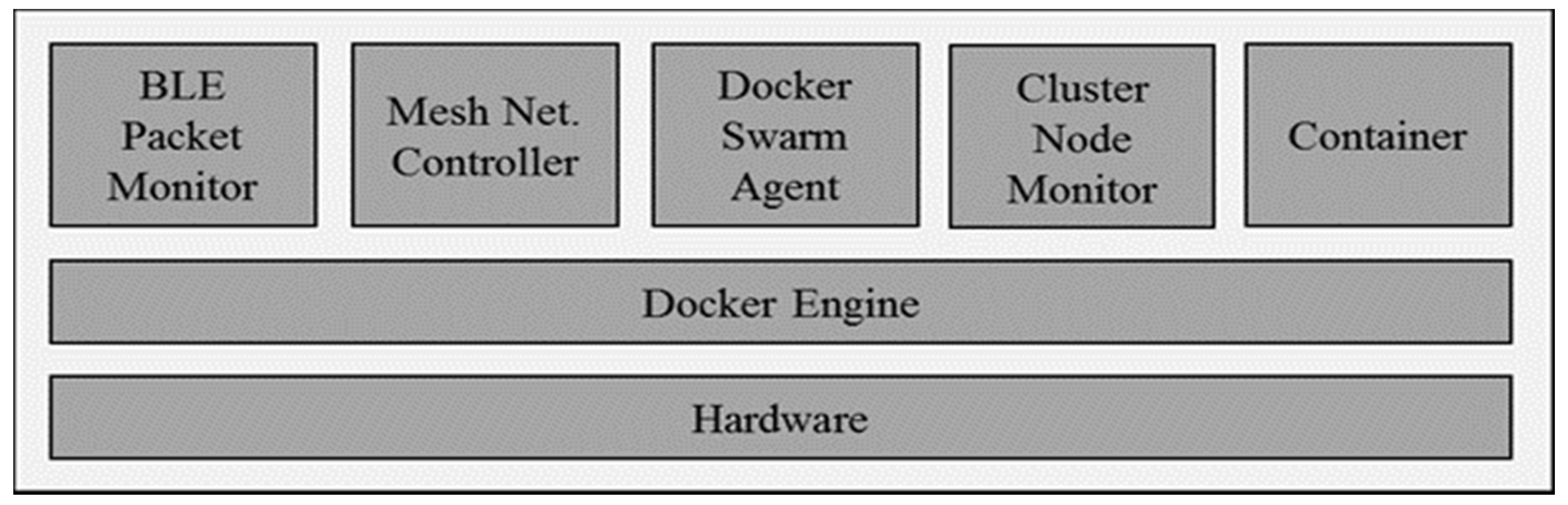
As shown in
Table 1, through the Docker swarm API, although the master can obtain other network device information, it is not suitable to judge the network status using the number of containers. In the status quo, the information that we can gain from the Docker swarm is limited; so, in order to achieve flexible container location and movement, a module that can check CPU usage at each node is needed. Therefore, as shown in
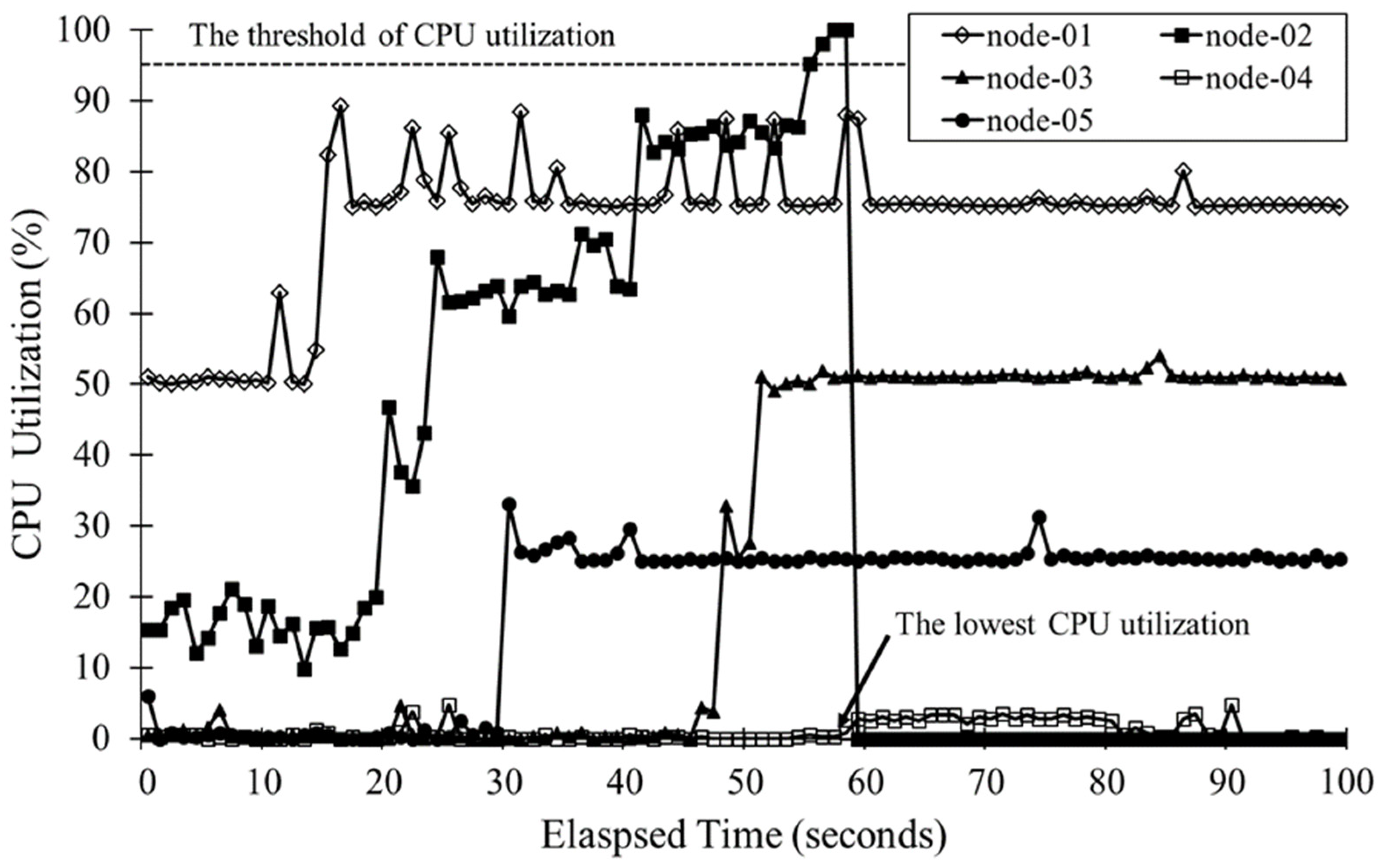
Figure 9, member nodes help in the configuration of a cluster with the previously proposed module and Docker swarm agent and, through cluster node monitoring, it can monitor CPU usage and report to the master node when there is an error.
When a member node notifies that CPU usage is over a given limit, by collecting the status of each node, the master node moves the container to the node at which the error occurred to the optimal node so that it can continually provide network function.
To achieve this, the master node is operated as depicted in
Figure 10 (as previously proposed), with a Docker swarm master and a cluster service controller.
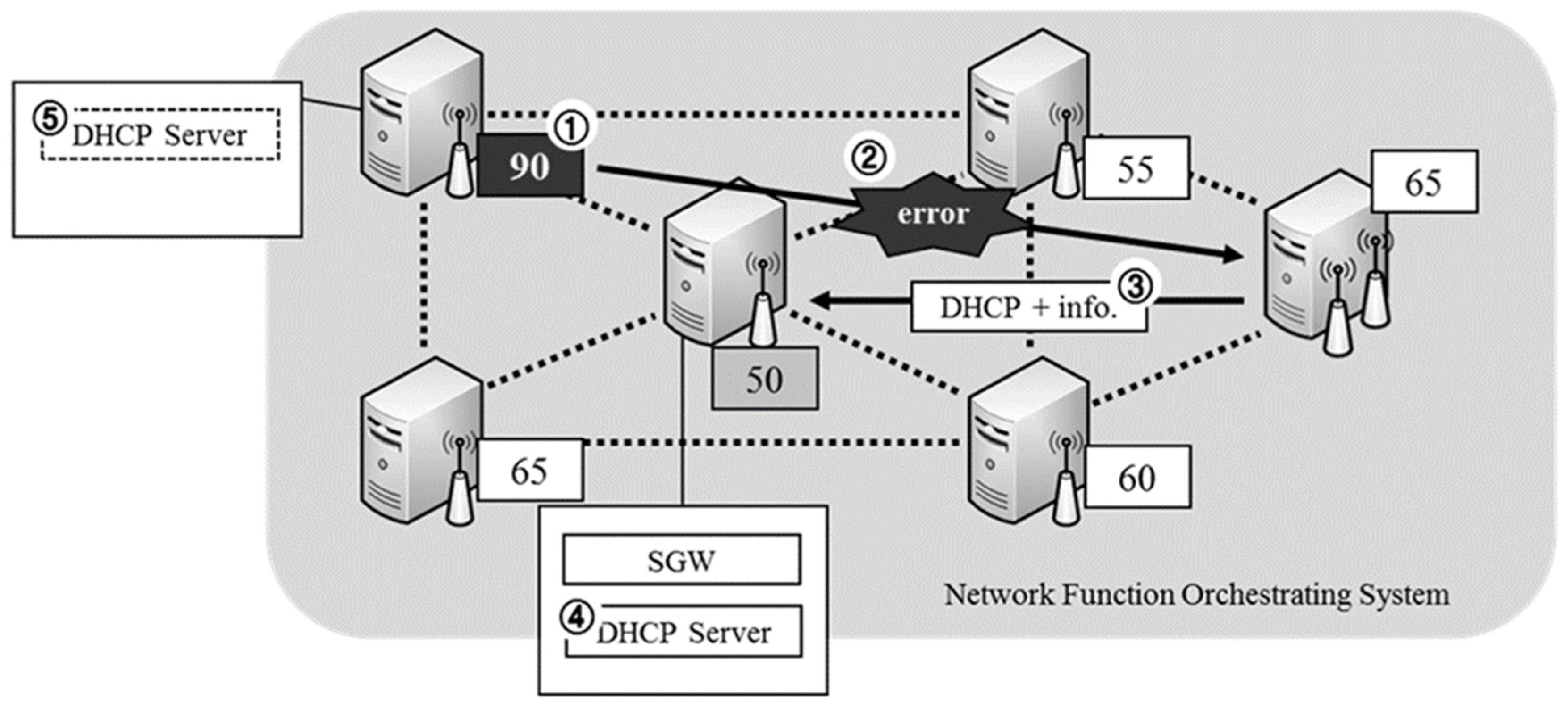
The proposed operating procedure is shown in
Figure 11. Firstly, every node implements the cluster node monitoring module and checks its own CPU usage at set times. The master node waits for error message reports from member nodes and prepares for incoming messages by opening a port. If, as in process 1, the CPU loading rate exceeds a threshold value at some nodes, process 2’s error message is reported to the master node. In the error message, the container’s last status needs to be written and sent. At this time, the master node sends the request message regarding CPU loading information to the all nodes and then receives messages from the responding nodes, leading to a search for the node with the lowest CPU usage. Through this procedure, the master node searches for the optimal node and locates the error node container. Then, by delivering the status information to the container, it implements service without any suspension. When the error is located as in process 4, the master node terminates the container at the node at which the error occurred and concludes the service recovery procedure.
By using this composition method, it is possible to flexibly locate containers according to the network devices’ statuses; and by providing a recovery procedure that moves the virtual network function of the device at which the error occurred, it can prove the availability of service. Additionally, based on the entire network’s information acquisition, since it is possible to locate the network’s function according to device status, when locating, it is possible to distribute the load of the entire network considering network device information.
This method is a way to provide network function but it can also be used as a method to provide user services. When it provides video streaming service as the user service, as in the previous operation, when a network device experiences an error, service can be recovered by moving service to another device. The idea involves not only restarting streaming services; by also sending information with the same amount of storage as the service information, it can provide service continuously.
3.3. Cluster Management Method for the Arrangement of VNFs Image-Matching-Based QR Code Recognition Method
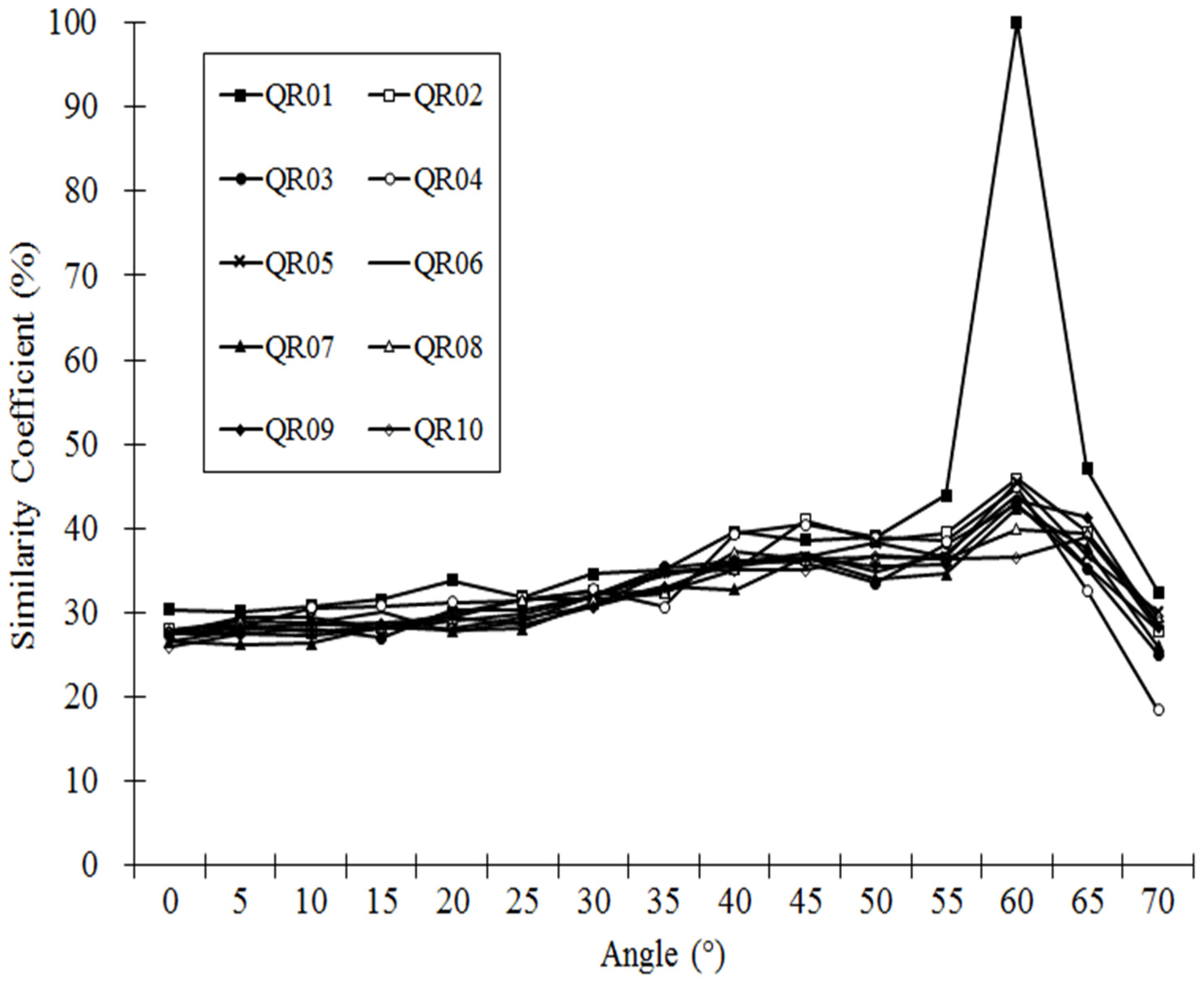
This paper proposes a virtualized network function orchestration system’s user service use case, proposing a QR code recognition method using a multiple-image-matching method. This method, based on the cloud, is a way to check a database that saves images according to different angles of scanning QR codes and the similarity of the imaged QR codes. Since QR codes have an image for each scanning angle, QR codes can be recognized even from angles at which they normally cannot be recognized.
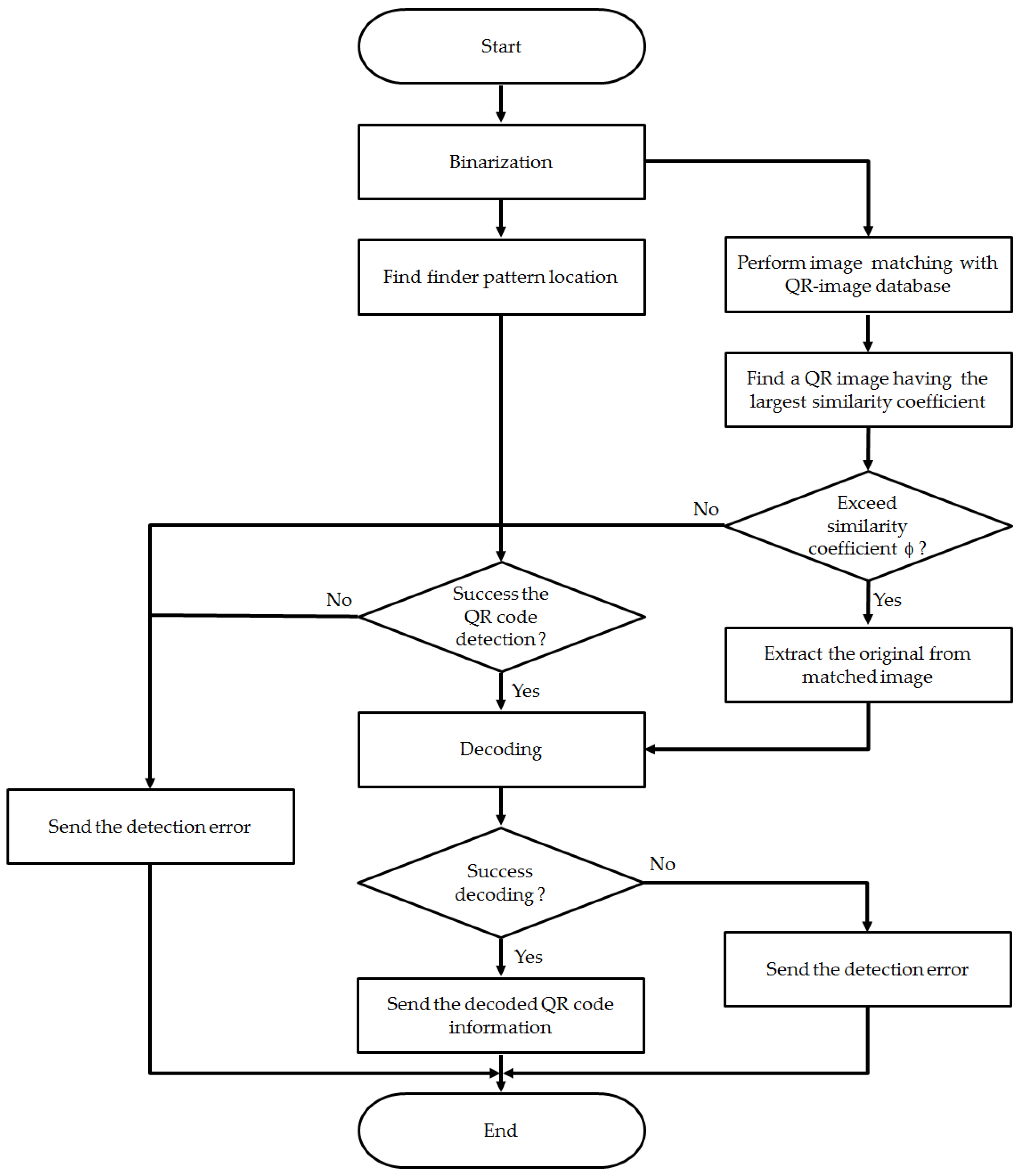
The specific operation method is as follows. As in
Figure 12, when a QR code scanned by the user is received, the image’s noise needs to be removed from the binarization. By extracting QR codes in certain sphere, the method checks for similarity by comparing with QR code images in a database. Then, the image that has the largest similarity must be found and a check is done as to whether the value exceeds a similarity threshold value (φ).
If the similarity exceeds the threshold value, decoding using the original image corresponding to the image found in the database is conducted and the result is then transmitted to the user. On the contrary, if a queried image has a similarity lower than the threshold value, then the system transmits a recognition failure message.
The proposed recognition method has value for making QR codes recognizable in a range of scanning angles the existing method cannot recognize. However, when a code is recognized not when a scanned image exceeds a certain angle but when using a recognition method that proposes the front of the image, it has a configuration that provides a lower level of function than the existing method. To solve this problem, a recognition method that combines the existing recognition method and the proposed recognition method can be used.
Figure 13 shows a composition that combines the existing recognition method and the proposed recognition method. When it receives a QR code scanned image from the user, it conducts recognition practically by extracting QR codes from binarization. By using the existing method, it can recognize the finder pattern and by using the proposed recognition method, it checks similarity against entries in a database. The two procedures are conducted simultaneously and when one of the two succeeds in recognition, decoding is performed and the result is transmitted to the user. If both recognition methods fail, the system sends a recognition failure message to the user; when it fails during the decoding procedure, it sends a decoding error message to the user. Through using this combined method, QR codes taken from the front are recognized using the existing recognition method and QR codes scanned in excess of a certain angle are recognized through the proposed recognition method. Thereby, it can provide an improved recognition ratio by solving the problem of recognition at an angle and can overcome the challenge of horizontal angle image recognition, which was the limitation of the proposed method, by using the existing method.
As the number of QR codes increases and more images are saved in the database, there is a drastic increase in the workload of checking overall image similarity.
Thus, this is a suitable method when there are many devices capable of operation so that distributed operation is possible. In particular, it is the suitable for application as the proposed orchestration system’s user service.
5. Conclusions and Further Research
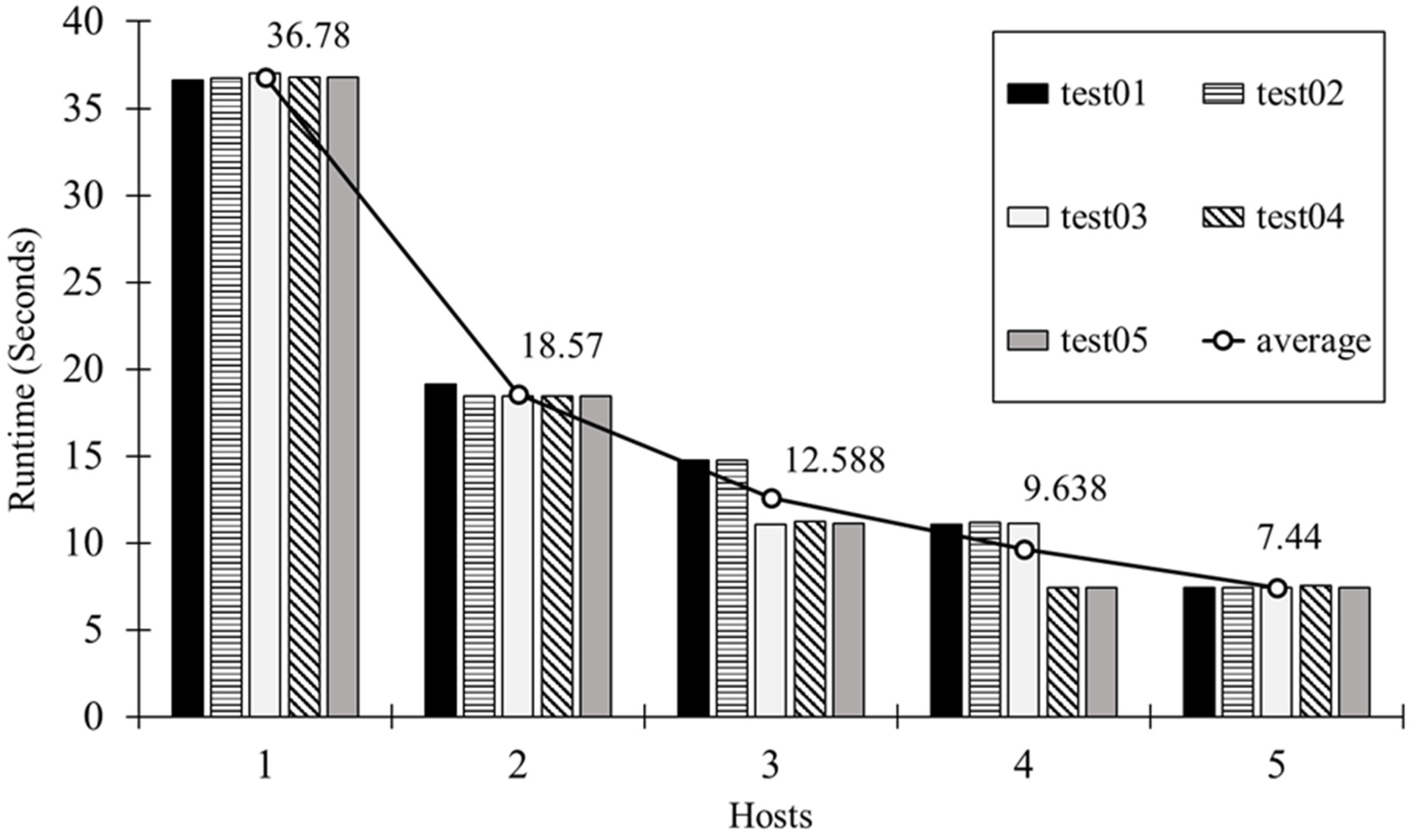
This paper proposed a network orchestration system based on network virtualization technology. Actual performance testing used open-source hardware as a network and set Docker-based virtual network function. This showed maintenance of service availability by repositioning network function based on the CPU usage of the nodes. Moreover, in order to solve the restart problem when the network is reset, this paper proposed a faster way of recovering to the environment before the reset. This improved the container structure, which, unlike virtual machines, could not provide continued service and allowed the container to enjoy the same continuity in the system.
Furthermore, this paper proposed a network orchestration system user service that improved a two-dimensional QR code identification method and tested its performance. Firstly, the proposed QR code identification method is different from the existing method as it conducts an image-matching process which facilitates the advantages of using a massive number of images, such as in a cloud system. A Nexus 4 smart phone was used to test and compare performance with those of existing applications. Better performance for the proposed method was observed, as it can identify images at a maximum scanning angle of 60° while the existing system allows a maximum angle of only 40°. Under the proposed system environment, an image database was set using different databases based on network device status information to improve processing speed. This showed that the information on a number of machines was used to set separate databases, allowing the best network conditions for using network status information to conduct network orchestration.
In conclusion, as mobile data traffic has significantly improved, expanding the scale of networks and their complexity and making research on 5G networks possible, the proposed method provides advantages for network orchestration systems in devising a 5G mobile access network with low cost using cheaper machines and open-source networks. Moreover, it provides advantages in terms of constant network provision.
In the future, this research could be used as a basis for measures to establish the most optimal virtual network function using network status information based on different requirements. In addition, with its low operating/development cost, such a system is expected to contribute to active establishment of computing environments for less economically developed countries.