A Block-Based Division Reversible Data Hiding Method in Encrypted Images
Abstract
:1. Introduction
2. Related Work
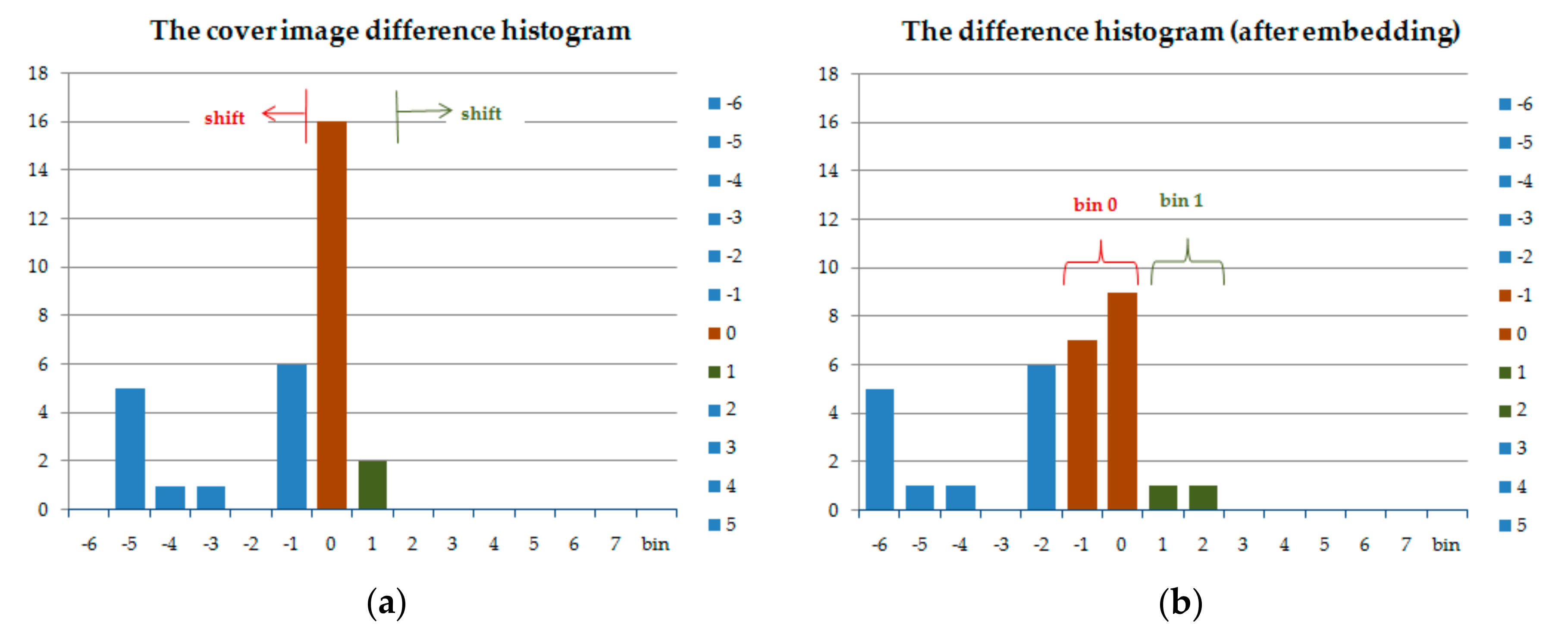
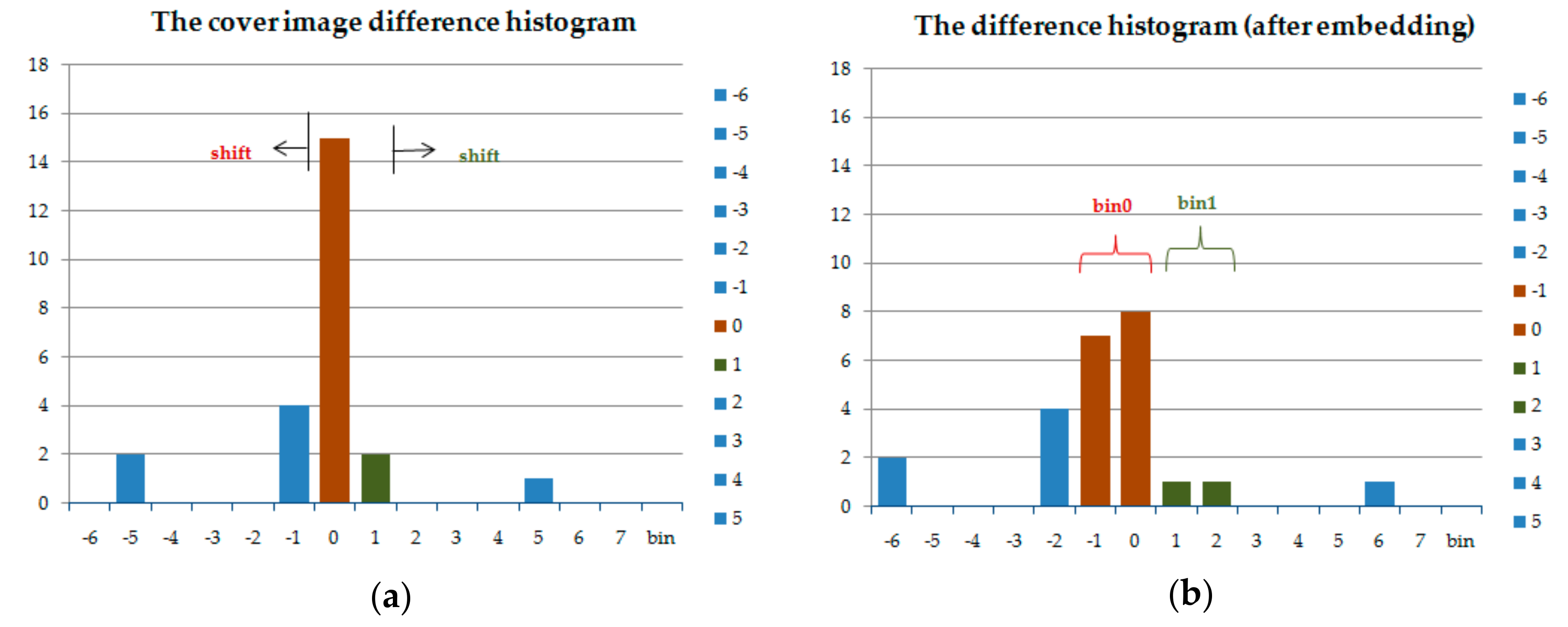
2.1. Histogram Shifting
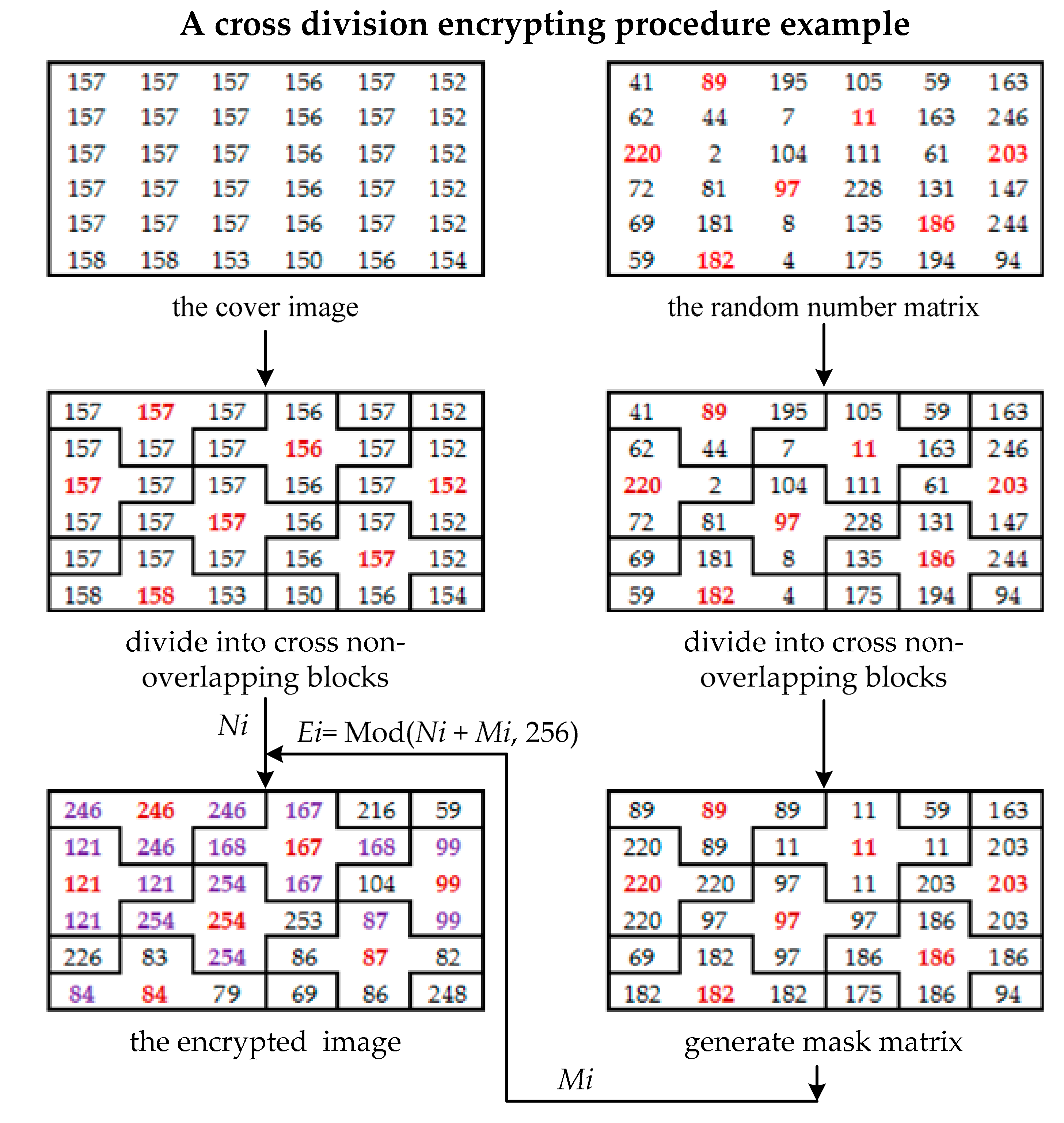
2.2. The Method of Li et al.
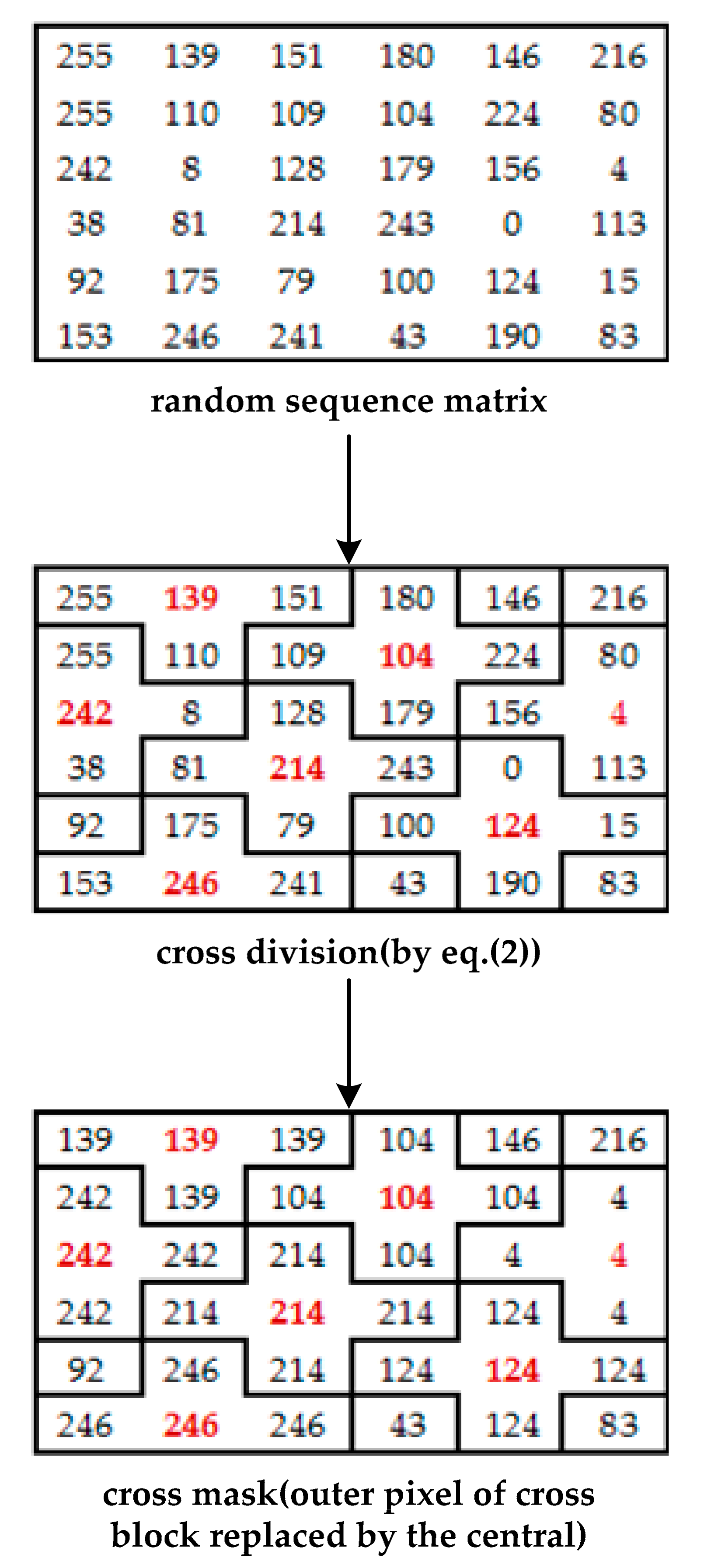
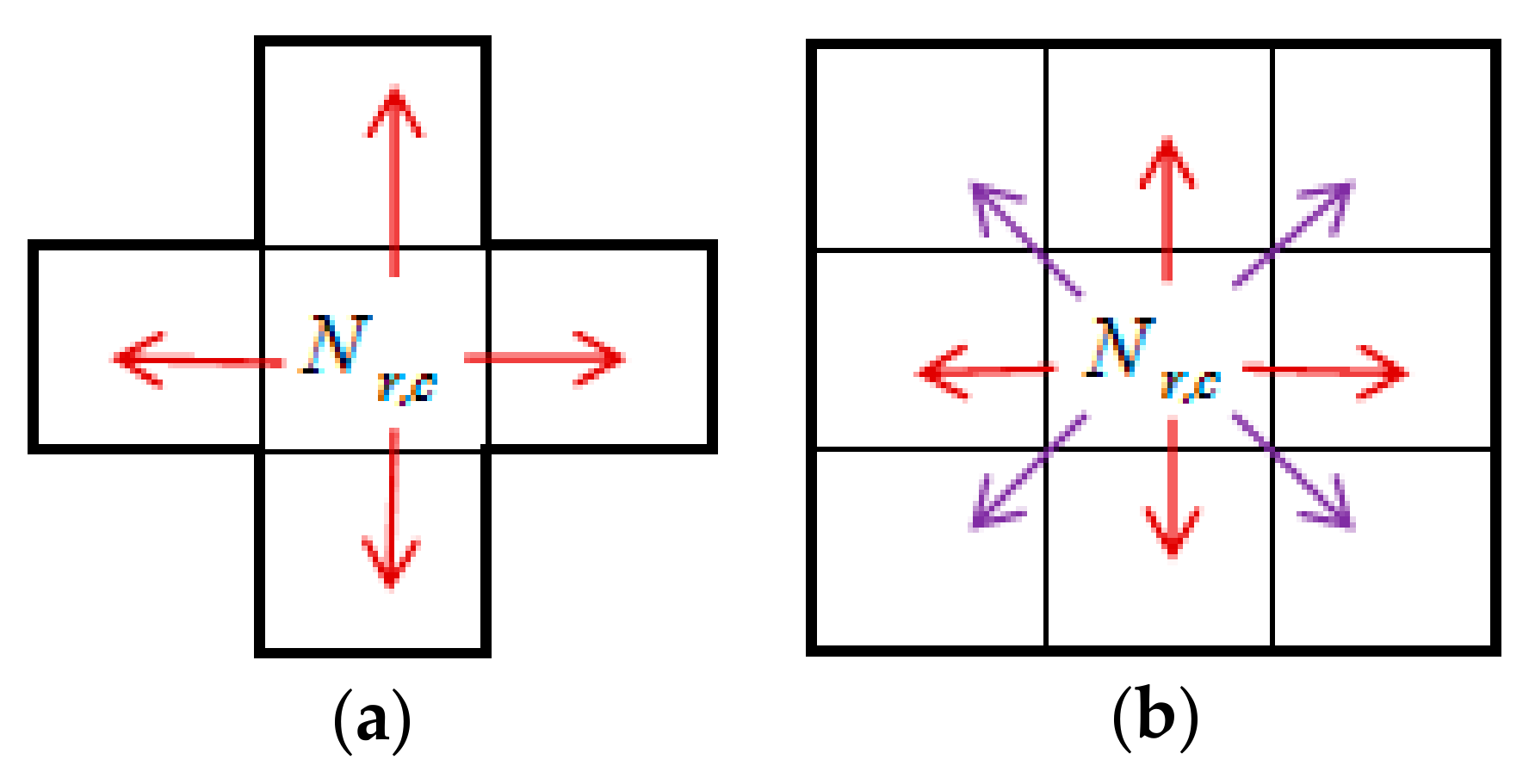
- Step 1: The cover image is established using a cross-shaped mask with a non-overlapping cross division (Figure 2). Assuming the central pixels of the divided image in the cross-division block as Nr,c (where r is row and c is column), the neighboring pixels are Nr,c−1, Nr,c+1, Nr−1,c, and Nr+1,c. Equation (2) is used for expressing the relationship between pixels:where d1 and d2 represent the image’s height and width.
- Step 2: Encrypt the cover image using the RC4 cryptosystem and an additive homomorphism:where Er,c, Nr,c, and Mr,c represent the encrypted pixel, the original pixel, and the mask value, respectively.
- Step 3: Calculate the difference between the central pixels and their neighboring pixels in the non-overlapping cross-division block. After that, histogram shifting (described in Section 2.1) is used to embed secret messages into neighboring pixels.
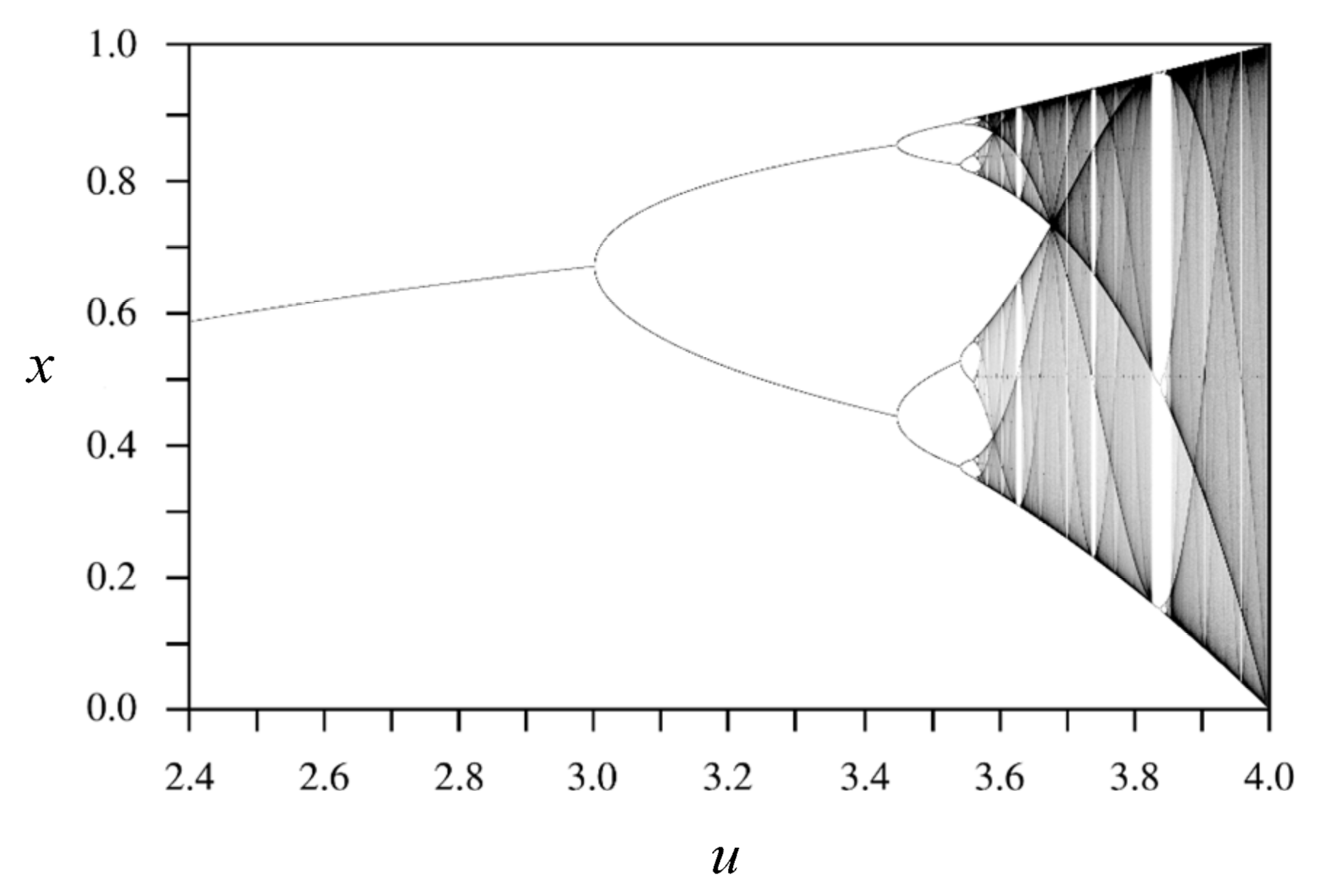
2.3. Logistic Map
3. Proposed Method
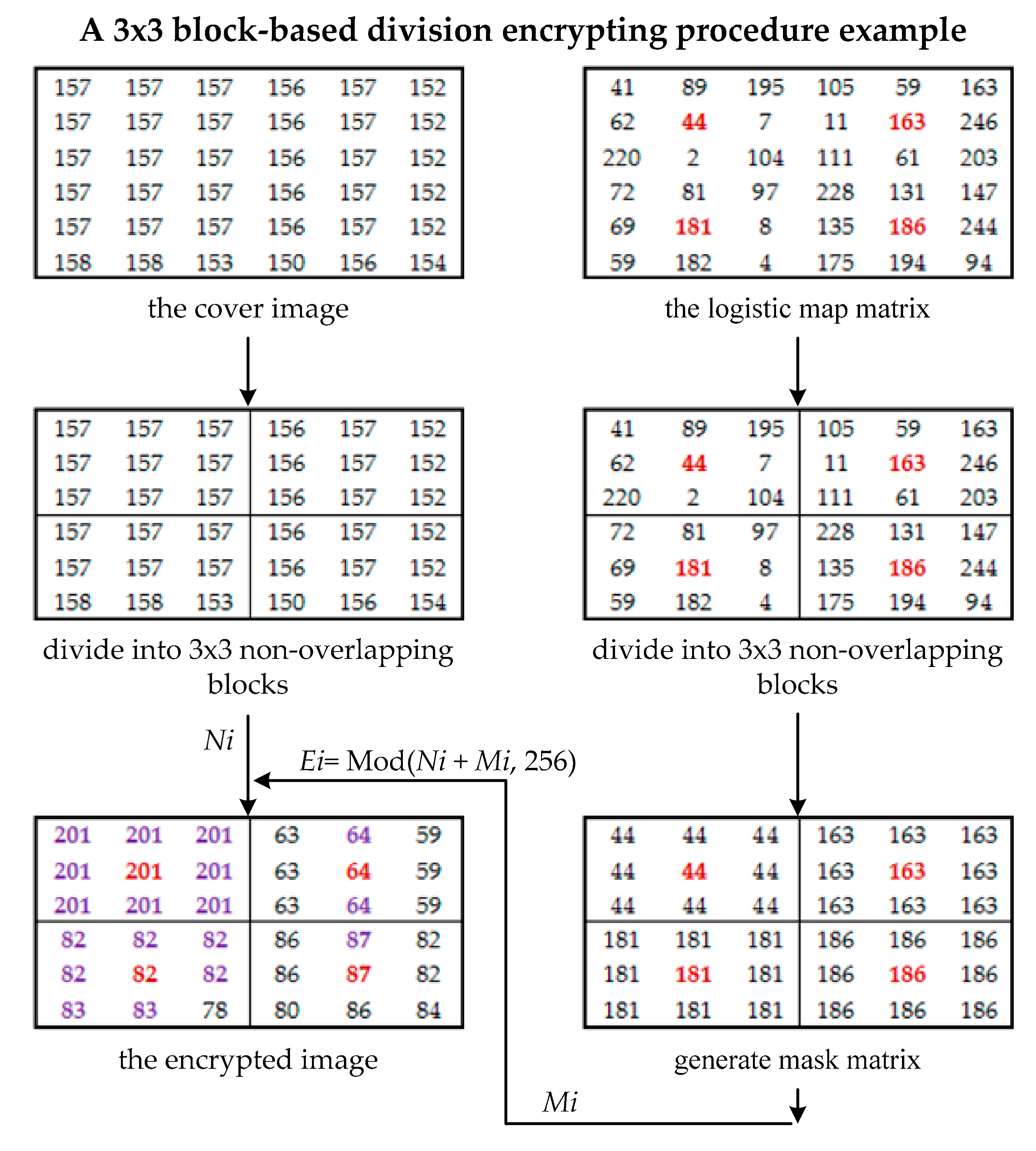
3.1. Block-Based Division Method
3.2. Encryption Procedure
- Step 1: The cover image is divided into 3 × 3 non-overlapping blocks.
- Step 2: The initial values of x0 () and u (bifurcation parameter, ) are given by Equation (4), and the logistic map equation is used for the original image’s pixels, which are further transformed into the range corresponding to grey-scale pixels (e.g., the remainder of xi is multiplied by 256 and then rounded to integer), and the block-based mask is developed.
3.3. Embedding Procedure
3.4. Extraction Procedure
- Step 1: Generate the difference histogram of the stego image.
- Step 2: The difference histogram is shifted conversely to extract the secret data.
- Step 3: Therefore, the original image is recovered exactly.
- Step 4: Reorganize the extracted data to retrieve the embedded additional message perfectly.
4. Experimental Results
5. Conclusions
Author Contributions
Conflicts of Interest
References
- Tian, J. Reversible data embedding using difference expansion. IEEE Trans. Circuits Syst. Video Technol. 2003, 13, 890–896. [Google Scholar] [CrossRef]
- Alattar, A.M. Reversible watermark using the difference expansion of a generalized integer transform. IEEE Trans. Image Process. 2004, 13, 1147–1156. [Google Scholar] [CrossRef] [PubMed]
- Thodi, D.M.; Rodriguez, J.J. Expansion embedding techniques for reversible watermarking. IEEE Trans. Image Process. 2007, 16, 721–730. [Google Scholar] [CrossRef] [PubMed]
- Ni, Z.; Shi, Y.Q.; Ansari, N.; Su, W. Reversible data hiding. IEEE Trans. Circuits Syst. Video Technol. 2006, 16, 354–362. [Google Scholar]
- Coltuc, D. Improved embedding for prediction-based reversible watermarking. IEEE Trans. Inf. Forensics Secur. 2011, 6, 873–882. [Google Scholar] [CrossRef]
- Gao, X.; An, L.; Yuan, Y.; Tao, D.; Li, X. Lossless data embedding using generalized statistical quantity histogram. IEEE Trans. Circuits Syst. Video Technol. 2011, 21, 1061–1070. [Google Scholar]
- Li, X.; Yang, B.; Zeng, T. Efficient reversible watermarking based on adaptive prediction-error expansion and pixel selection. IEEE Trans. Image Process. 2011, 20, 3524–3533. [Google Scholar] [PubMed]
- Wu, H.-T.; Huang, J. Reversible image watermarking on prediction errors by efficient histogram modification. Signal Process. 2012, 92, 3000–3009. [Google Scholar] [CrossRef]
- Hong, W.; Chen, T.S.; Shiu, C.W. Reversible data hiding for high quality images using modification of prediction errors. J. Syst. Softw. 2009, 82, 1833–1842. [Google Scholar] [CrossRef]
- Wang, S.; Li, C.; Kuo, W. Reversible data hiding based on two-dimensional prediction errors. IEEE Trans. Image Process. 2013, 7, 805–816. [Google Scholar] [CrossRef]
- Li, X.; Zhang, W.; Gui, X.; Yang, B. A novel reversible data hiding scheme based on two-dimensional difference-histogram modification. IEEE Trans. Inf. Forensics Secur. 2013, 8, 1091–1100. [Google Scholar]
- Ou, B.; Li, X.; Zhao, Y.; Ni, R.; Shi, Y. Pairwise prediction-error expansion for efficient reversible data hiding. IEEE Trans. Image Process. 2013, 22, 5010–5021. [Google Scholar] [CrossRef] [PubMed]
- Fu, D.; Jing, Z.; Zhao, S.; Fan, J. Reversible data hiding based on prediction-error histogram shifting and EMD mechanism. AEU-Int. J. Electron. Commun. 2014, 68, 933–943. [Google Scholar] [CrossRef]
- Li, X.L.; Li, J.; Li, B.; Yang, B. High-fidelity reversible data hiding scheme based on pixel–value-ordering and prediction–error expansion. Signal Process. 2013, 93, 198–205. [Google Scholar] [CrossRef]
- Peng, F.; Li, X.L.; Yang, B. Improved PVO-based reversible data hiding. Digit. Signal Process. 2014, 25, 255–265. [Google Scholar] [CrossRef]
- Ou, B.; Li, X.L.; Zhao, Y.; Ni, R.R. Reversible data hiding using invariant pixel-value-ordering and prediction-error expansion. Signal Process. Image Commun. 2014, 29, 760–772. [Google Scholar] [CrossRef]
- Qu, X.; Kim, H.J. Pixel-based pixel value ordering predictor for high-fidelity reversible data hiding. Signal Process. 2015, 111, 249–260. [Google Scholar] [CrossRef]
- Zhang, X.P. Reversible data hiding in encrypted images. IEEE Signal Process. Lett. 2011, 18, 255–258. [Google Scholar] [CrossRef]
- Lai, I.J.; Tsai, W.H. Secret-fragment-visible mosaic image—A new computer art and its application to information hiding. IEEE Trans. Inf. Forensics Secur. 2011, 6, 936–945. [Google Scholar]
- Hong, W.; Chen, T.; Wu, H. An Improved Reversible Data Hiding in Encrypted Images Using Side Match. IEEE Signal Process. Lett. 2012, 19, 199–202. [Google Scholar] [CrossRef]
- Li, M.; Xiao, D.; Peng, Z.; Nan, H. A modified reversible data hiding in encrypted images using random diffusion and accurate prediction. ETRI J. 2014, 36, 325–328. [Google Scholar] [CrossRef]
- Wu, X.; Sun, W. High-capacity reversible data hiding in encrypted images by prediction error. Signal Process. 2014, 104, 387–400. [Google Scholar] [CrossRef]
- Li, M.; Xiao, D.; Zhang, Y.; Nan, H. Reversible data hiding in encrypted images using cross division and additive homomorphism. Signal Process. Image Commun. 2015, 39, 234–248. [Google Scholar] [CrossRef]
- Liao, X.; Shu, C. Reversible data hiding in encrypted images based on absolute mean difference of multipleneighboring pixels. J. Vis. Commun. Image Represent. 2015, 28, 21–27. [Google Scholar] [CrossRef]
- Pan, Z.; Wang, L.; Hu, S.; Ma, X. Reversible data hiding in encrypted image using new embedding pattern and multiple judgements. Multimed. Tools Appl. 2016, 75, 8595–8607. [Google Scholar] [CrossRef]
- Cao, X.; Du, L.; Wei, X.; Meng, D.; Guo, X. High capacity reversible data hiding in encrypted images by patch-level sparse representation. IEEE Trans. Cybern. 2016, 46, 1132–1143. [Google Scholar] [CrossRef] [PubMed]
- Qian, Z.; Zhang, X. Reversible data hiding in encrypted images with distributed source encoding. IEEE Trans. Circuits Syst. Video Technol. 2016, 26, 636–646. [Google Scholar] [CrossRef]
- Khanam, F.; Kim, S. Enhanced Joint and Separable Reversible Data Hiding in Encrypted Images with High Payload. Symmetry 2017, 9, 50. [Google Scholar] [CrossRef]
- Yi, S.; Zhou, Y. Binary-block embedding for reversible data hiding in encrypted images. Signal Process. 2017, 133, 40–51. [Google Scholar] [CrossRef]
- Xiao, D.; Xiang, Y.; Zheng, H.; Wang, Y. Separable reversible data hiding in encrypted image based on pixel value ordering and additive homomorphism. J. Vis. Commun. Image Represent. 2017, 45, 1–10. [Google Scholar] [CrossRef]
- Fluhrer, S.R.; McGrew, D.A. Statistical analysis of the alleged RC4 keystream generator. In Fast Software Encryption; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2001; pp. 19–30. [Google Scholar]
- Mantin, I.; Shamir, A. A practical attack on broadcast RC4. In Fast Software Encryption; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2001; pp. 152–164. [Google Scholar]
- Roos, A. A Class of Weak Keys in the RC4 Stream Cipher. Available online: http://www.impic.org/papers/WeakKeys-report.pdf (accessed on 24 October 2017).
- Grosul, A.L.; Wallach, D.S. A Related-Key Cryptanalysis of RC4; Rice University: Houston, TX, USA, 2000. [Google Scholar]
- Knudsen, L.R.; Meier, W.; Preneel, B.; Rijmen, V.; Verdoolaege, S. Analysis methods for (alleged) RC4. In Advances in Cryptology—ASIACRYPT’98; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 1998; pp. 327–341. [Google Scholar]
- Golić, J.D. Linear statistical weakness of alleged RC4 keystream generator. In Advances in Cryptology—EUROCRYPT ’97; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 1997; pp. 226–238. [Google Scholar]
- Mister, S.; Tavares, S.E. Cryptanalysis of RC4-like ciphers. In Selected Areas in Cryptography; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 1999; pp. 131–143. [Google Scholar]

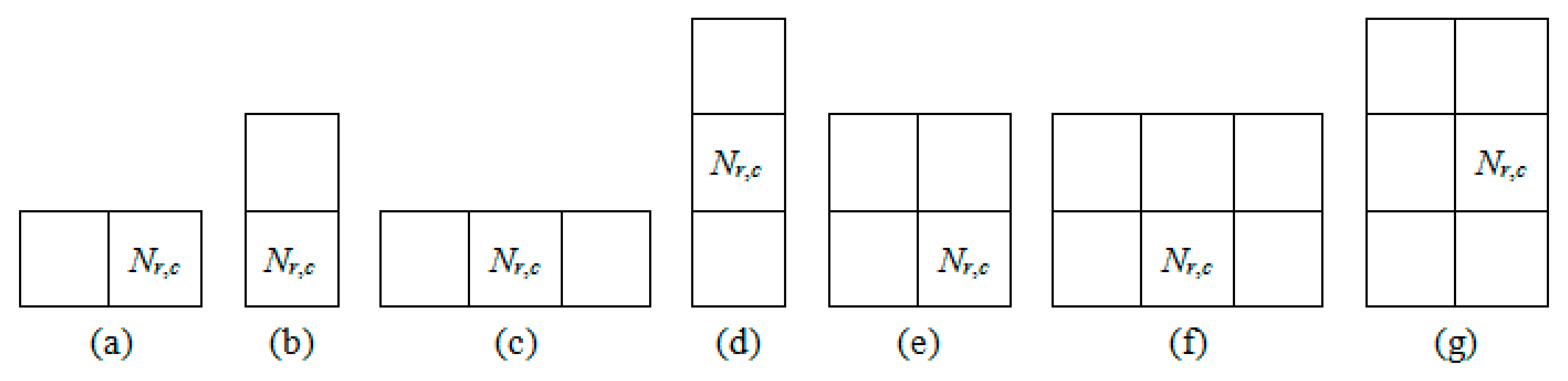
| Cover Image | Stego Image | |
|---|---|---|
| Lena |  |  |
| Baboon |  |  |
| Peppers |  |  |
| Jet |  |  |
| Scene |  |  |
| Tiffany |  |  |
| Proposed Method | Li et al. | |
|---|---|---|
| Lena | 39,241 | 38,155 |
| Baboon | 13,220 | 12,852 |
| Peppers | 32,432 | 28,266 |
| Jet | 58,565 | 57,058 |
| Scene | 27,722 | 24,166 |
| Tiffany | 47,200 | 45,043 |
| Proposed Method | Li et al. | |
|---|---|---|
| Lena | 9.223157 | 9.156620 |
| Baboon | 9.509704 | 9.491607 |
| Peppers | 8.920476 | 8.845069 |
| Jet | 7.987589 | 7.986285 |
| Scene | 8.239897 | 8.221679 |
| Tiffany | 6.873964 | 6.866277 |
| Proposed Method | Li et al. | |
|---|---|---|
| Lena | 7.999079 | 7.999010 |
| Baboon | 7.999247 | 7.999158 |
| Peppers | 7.999114 | 7.999192 |
| Jet | 7.998732 | 7.999125 |
| Scene | 7.999109 | 7.999164 |
| Tiffany | 7.998823 | 7.999067 |
| Proposed Method | Li et al. | |
|---|---|---|
| Lena | −0.000713 | 0.012889 |
| Baboon | −0.001393 | 0.003908 |
| Peppers | 0.011101 | −0.006034 |
| Jet | −0.000428 | 0.006841 |
| Scene | −0.001599 | −0.003999 |
| Tiffany | 0.005251 | 0.003879 |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, W.-L.; Leng, H.-S.; Huang, C.-K.; Chen, D.-C. A Block-Based Division Reversible Data Hiding Method in Encrypted Images. Symmetry 2017, 9, 308. https://doi.org/10.3390/sym9120308
Liu W-L, Leng H-S, Huang C-K, Chen D-C. A Block-Based Division Reversible Data Hiding Method in Encrypted Images. Symmetry. 2017; 9(12):308. https://doi.org/10.3390/sym9120308
Chicago/Turabian StyleLiu, Wei-Liang, Hui-Shih Leng, Chuan-Kuei Huang, and Dyi-Cheng Chen. 2017. "A Block-Based Division Reversible Data Hiding Method in Encrypted Images" Symmetry 9, no. 12: 308. https://doi.org/10.3390/sym9120308





