Dominant Channel Occupancy for Wi-Fi Backscatter Uplink in Industrial Internet of Things
Abstract
:1. Introduction
- We propose a new MAC layer solution for the Wi-Fi backscatter uplink, which is essential in most IIoT applications. As mentioned above, the existing Wi-Fi backscatter approach mainly focuses on downlink communication, but most IIoT monitoring applications make little use of their downlink and only require a very small bandwidth (e.g., a few kilobits per second) for command transmissions if utilized.
- The DCO can be applied to all Wi-Fi standards including IEEE 802.11b/g/n that use CSMA/CA operations. In contrast, the existing Wi-Fi backscatter approach utilizes CTS-to-self packets to deal with interference, which is only supported by the Wi-Fi standards released after IEEE 802.11g. Thus, many devices that only conform to IEEE 802.11b may cause interference under the existing approach.
- The DCO guarantees reliable burst transmission for Wi-Fi backscatter devices without exchanging additional control packets such as CTS-to-self, regardless of the amount of tag information and number of channel measurements. This is clearly distinguished from the CTS-to-self manner of having a time limit of up to 32 ms.
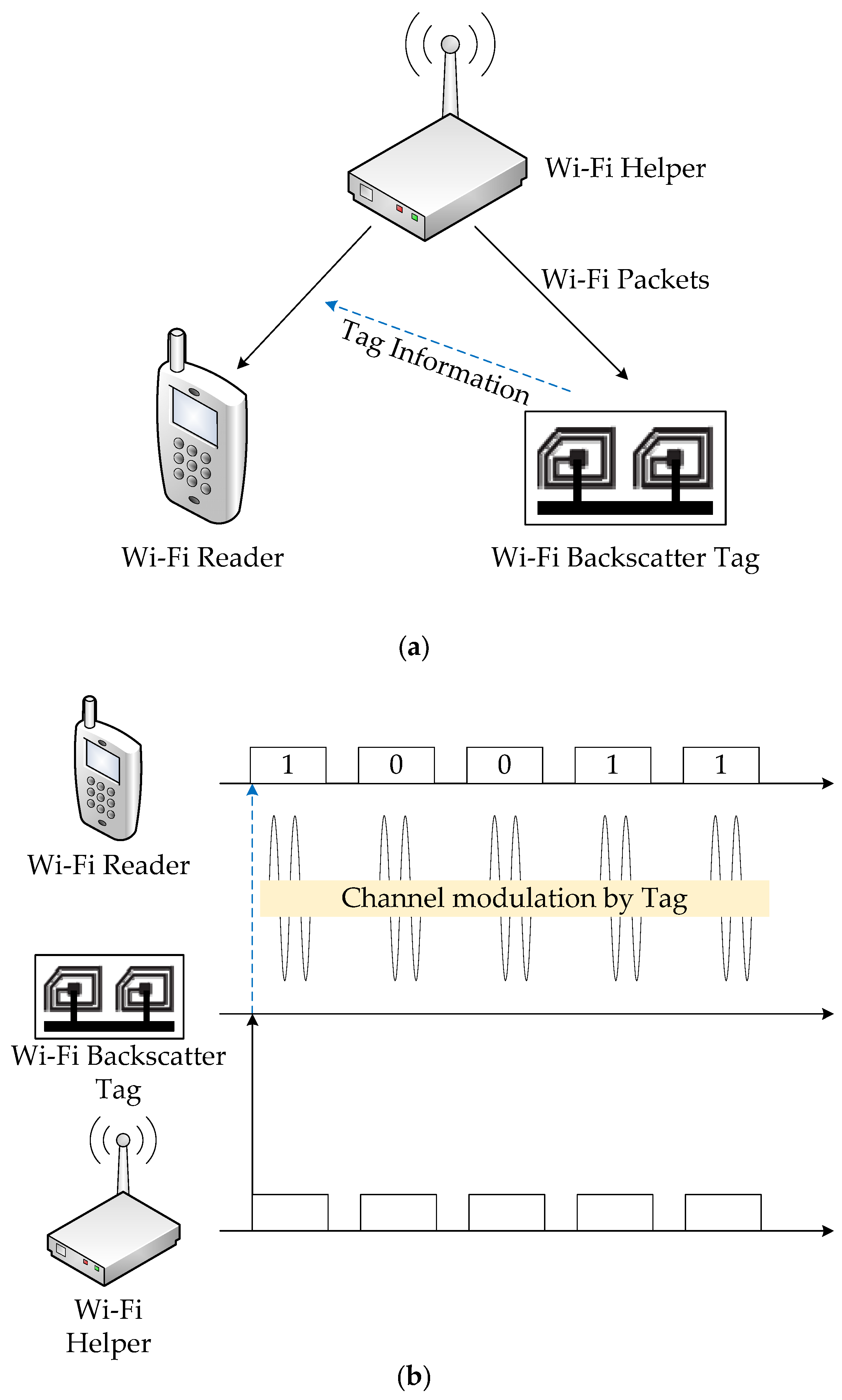
2. Wi-Fi Backscatter Uplink Communication
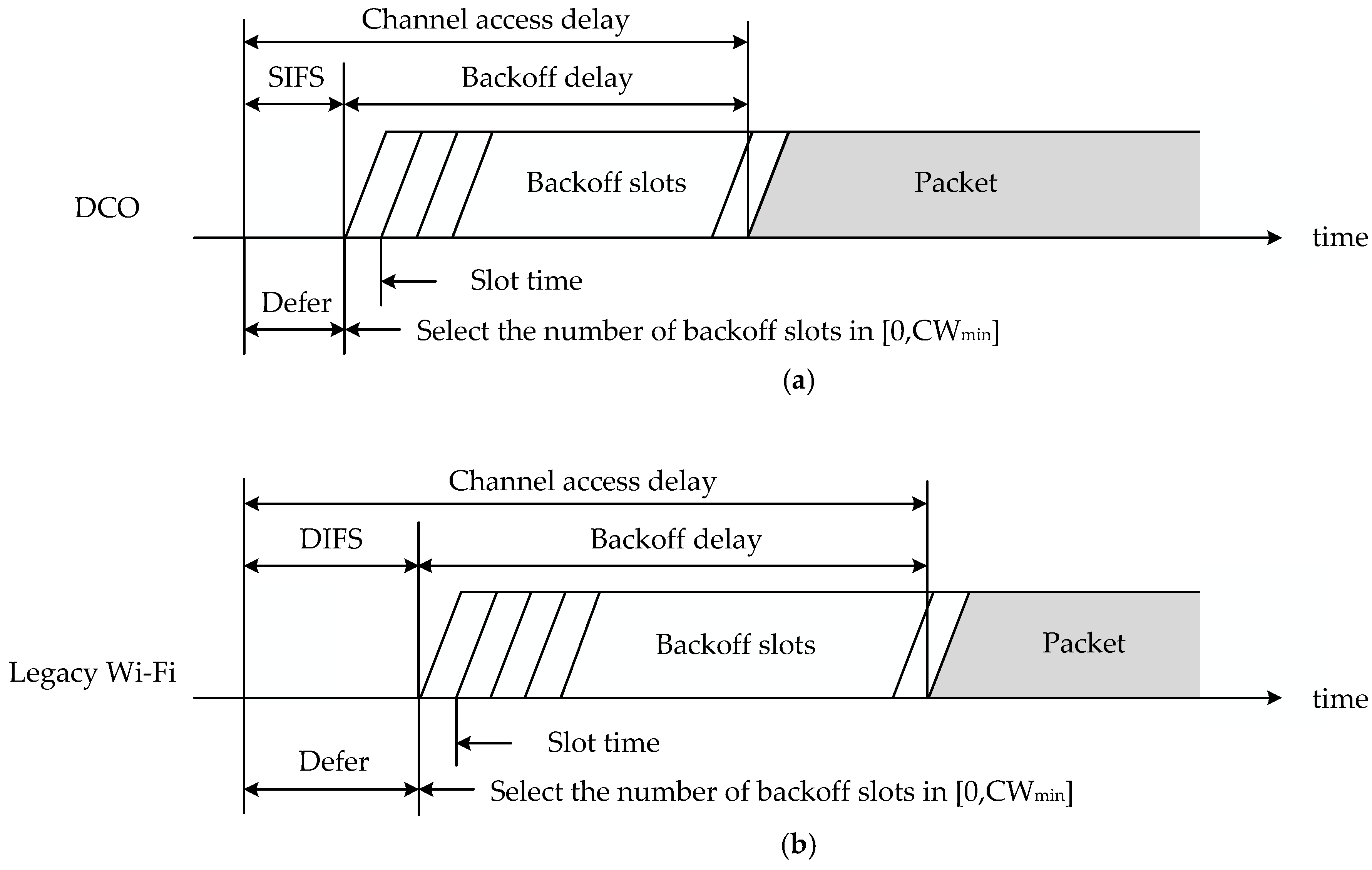
3. Design of the DCO
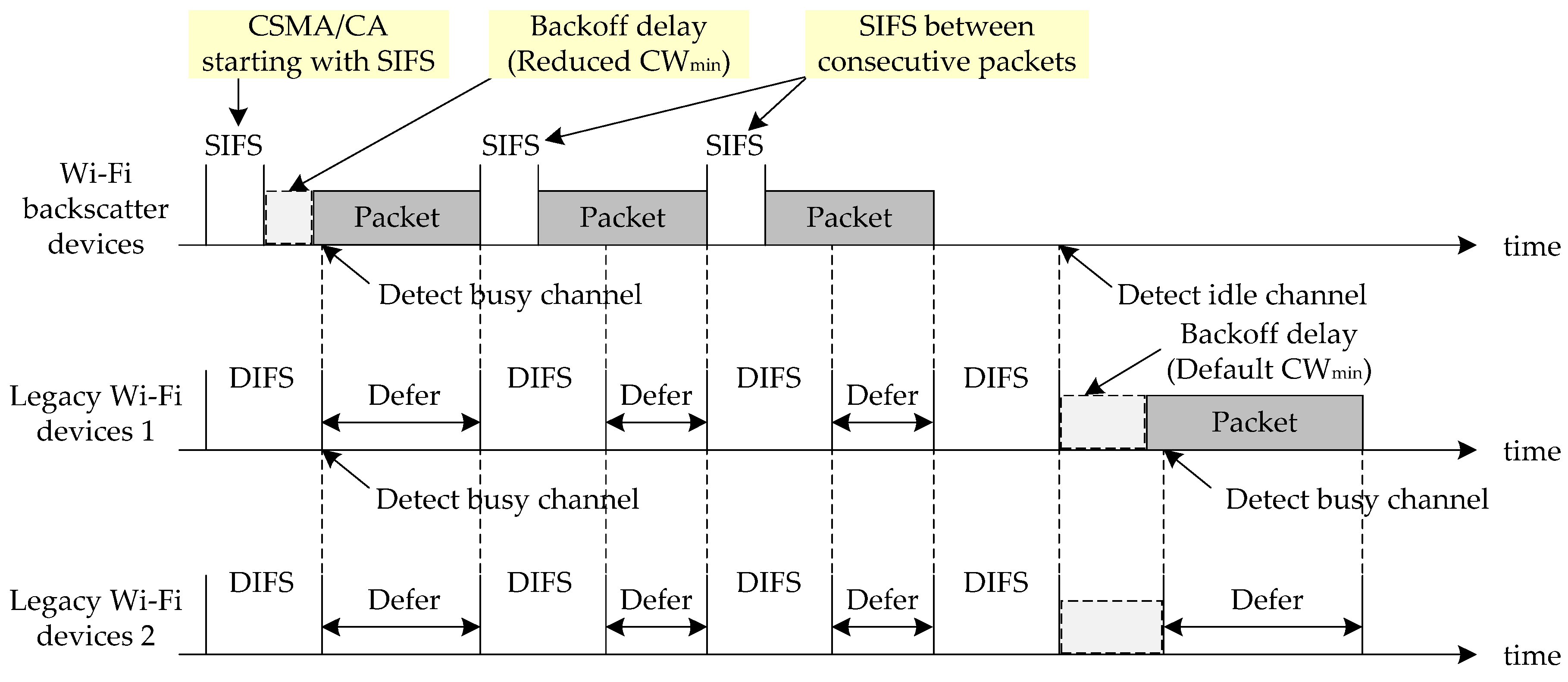
3.1. High-Priority Channel Access
3.2. Reliable Burst Transmission
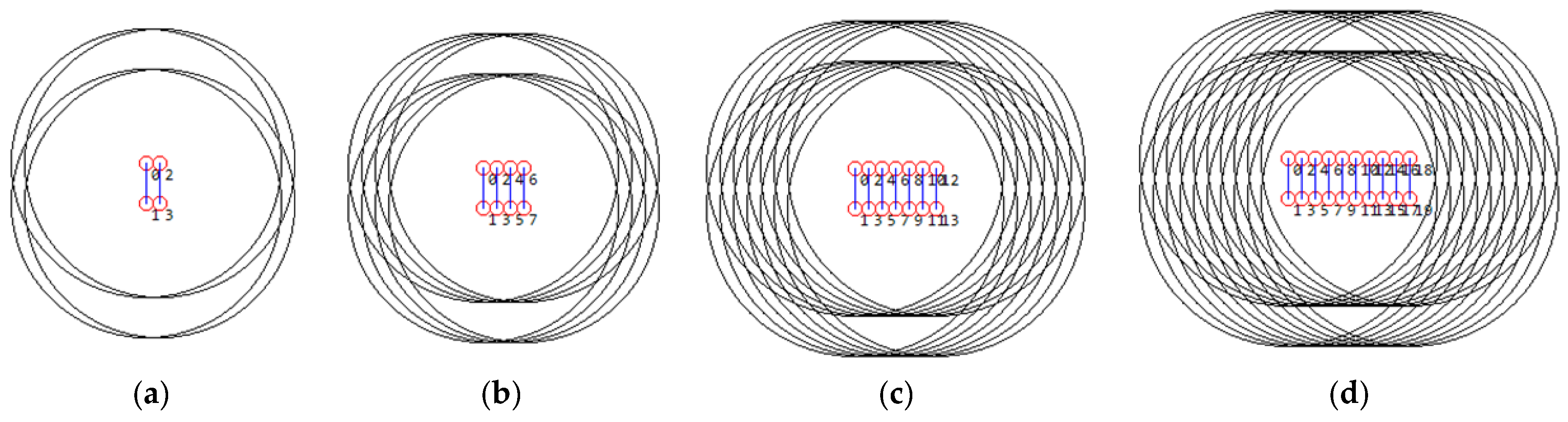
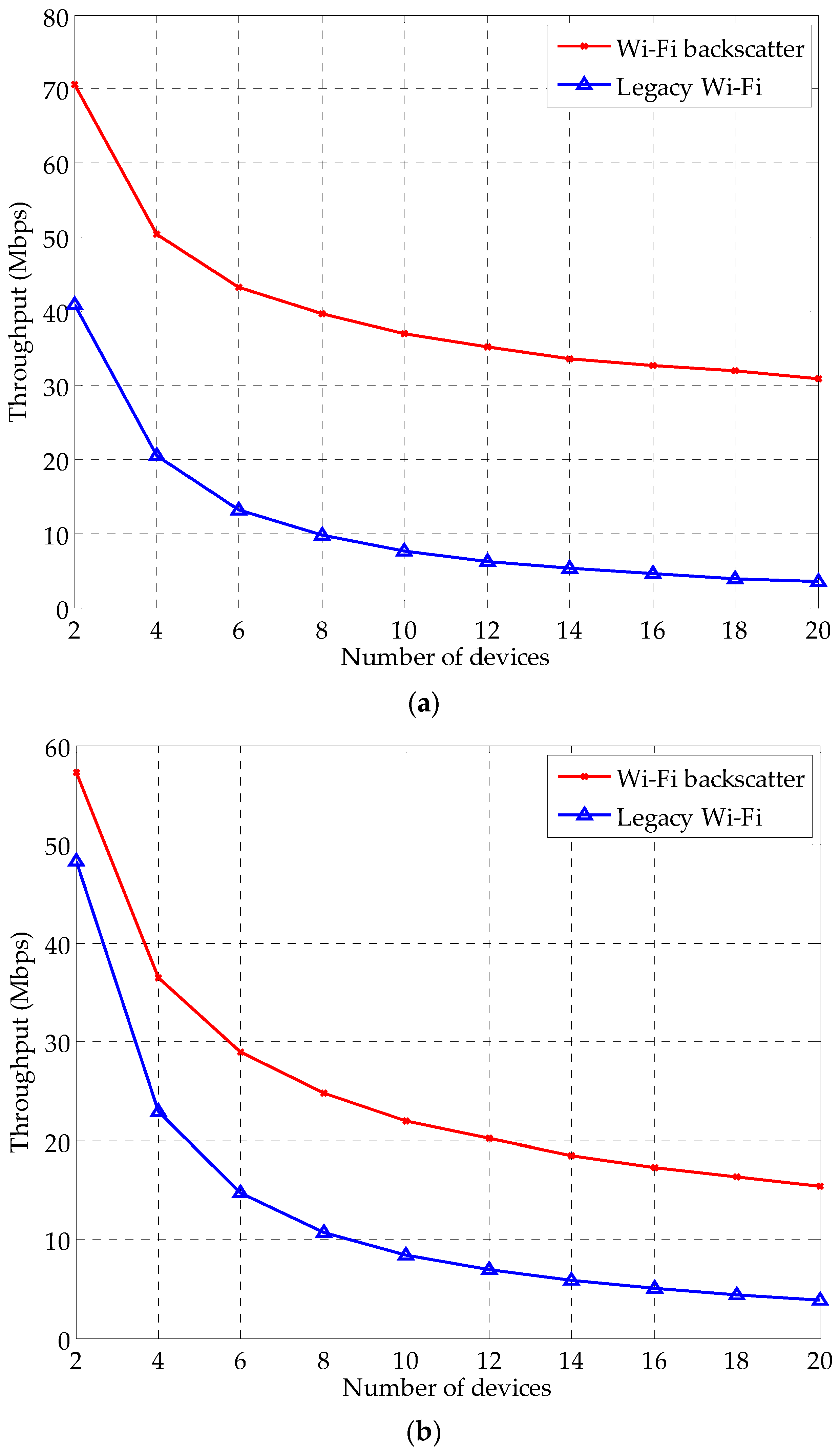
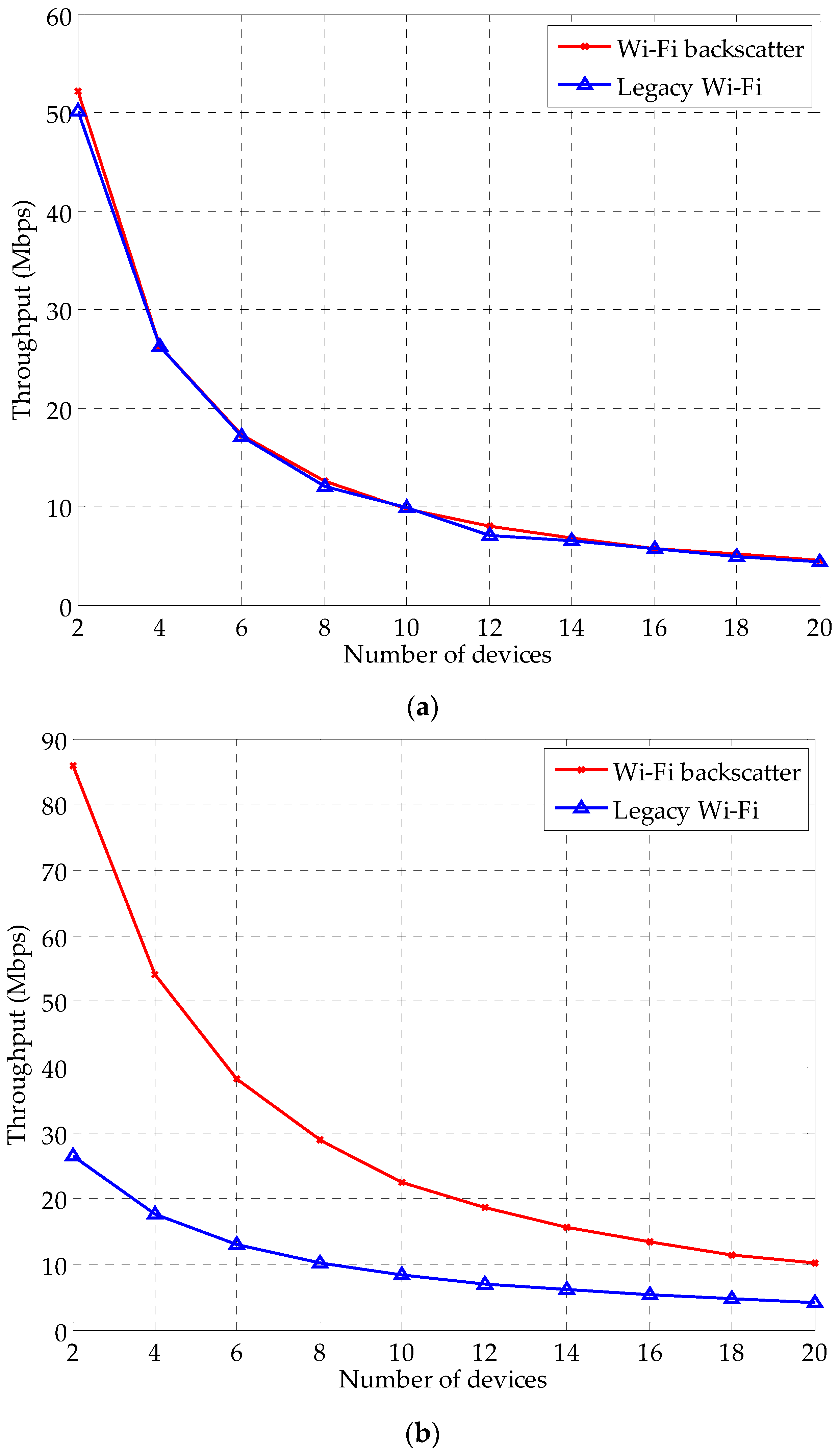
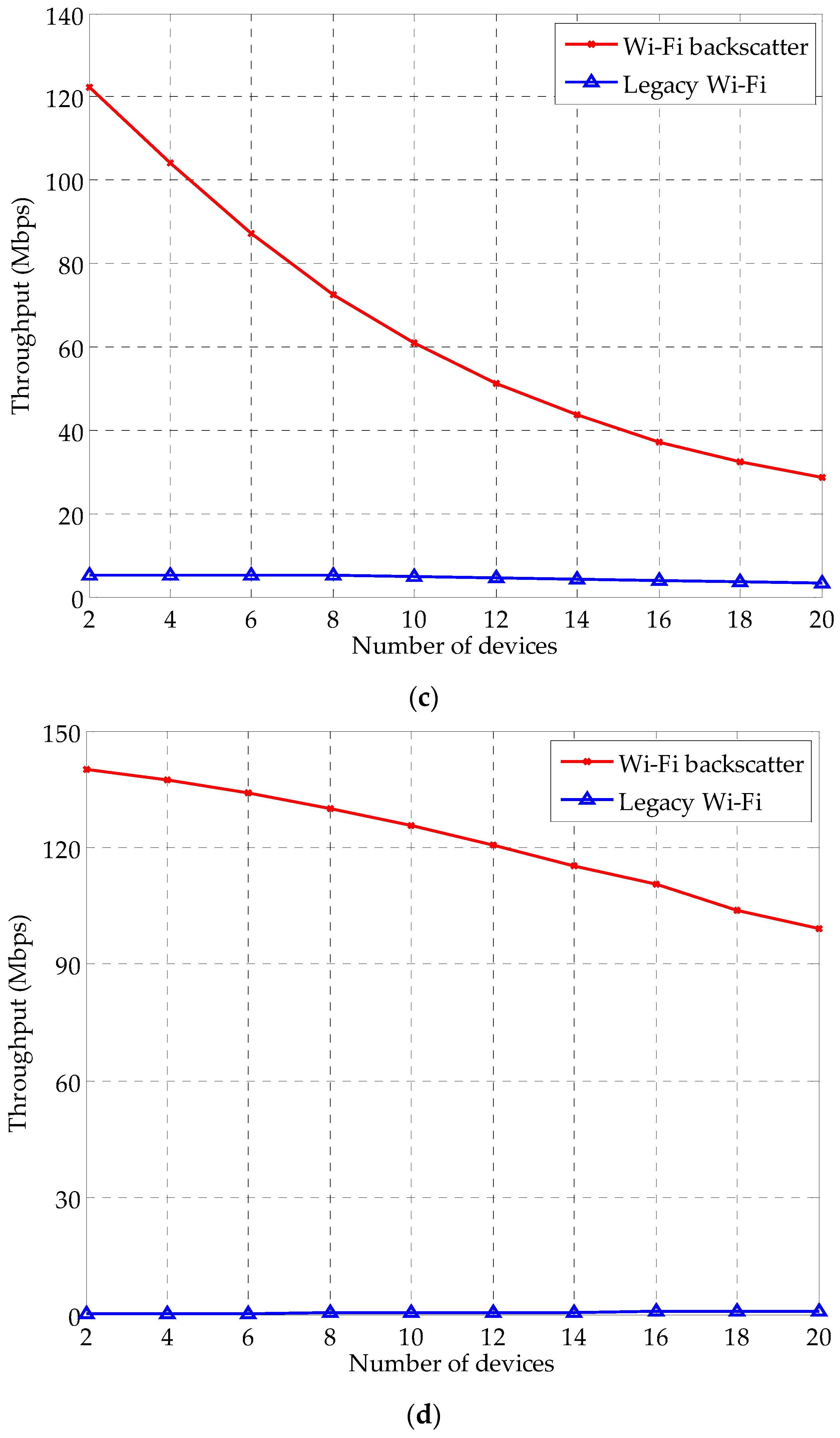
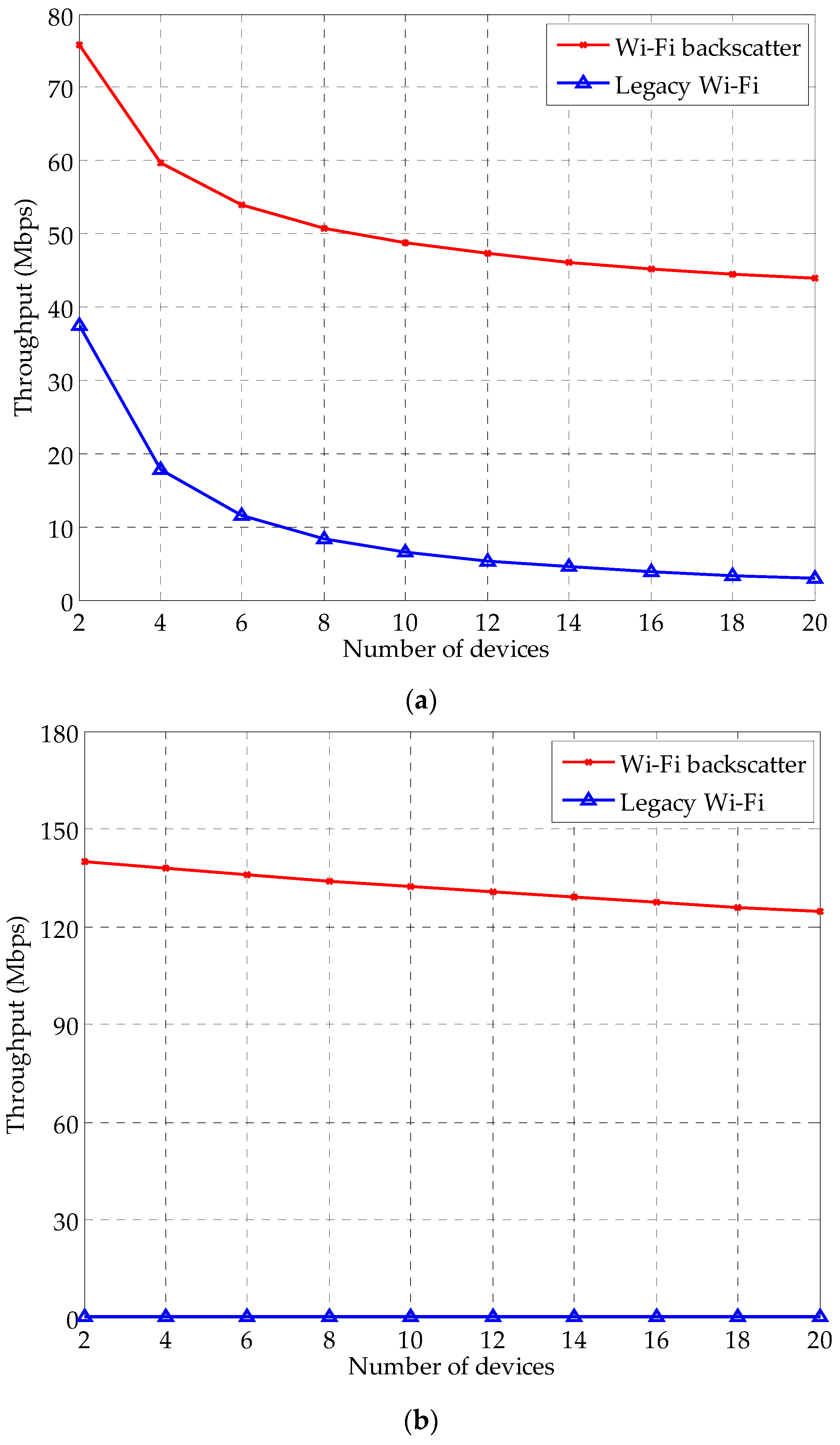
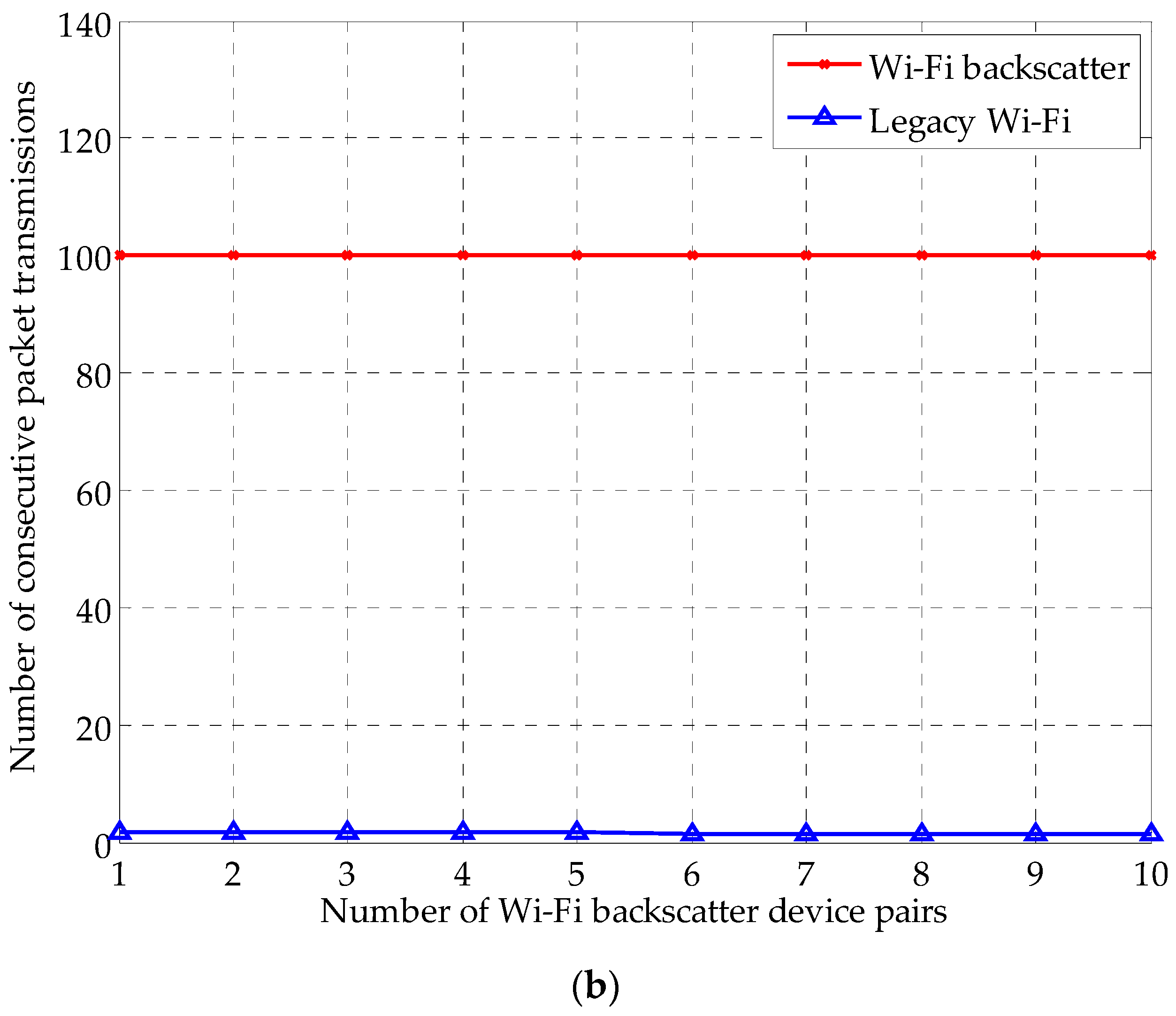
4. Performance Evaluation
4.1. Simulation Setup
4.2. Simulation Results
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Gilchrist, A. Designing Industrial Internet Systems. In Industry 4.0, 1st ed.; Apress: New York, NY, USA, 2016; pp. 87–118. [Google Scholar]
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A vision, architectural elements, and future directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef]
- Wang, J.; Hassanieh, H.; Katabi, D.; Indyk, P. Efficient and reliable low-power backscatter networks. In Proceedings of the ACM SIGCOMM 2012 Conference on Applications, Technologies, Architectures, and Protocols for Computer Communication, Helsinki, Finland, 13–17 August 2012; ACM: New York, NY, USA, 2012. [Google Scholar]
- Da Xu, L.; He, W.; Li, S. Internet of things in industries: A survey. Trans. Ind. Informat. 2014, 10, 2233–2243. [Google Scholar] [CrossRef]
- Zhu, R.; Zhang, X.; Liu, X.; Shu, W.; Mao, T.; Jalaian, B. ERDT: Energy-efficient reliable decision transmission for intelligent cooperative spectrum sensing in industrial IoT. IEEE Access 2015, 3, 2366–2378. [Google Scholar] [CrossRef]
- Kellogg, B.; Parks, A.; Gollakota, S.; Smith, J.R.; Wetherall, D. Wi-fi backscatter: Internet connectivity for RF-powered devices. In Proceedings of the 2014 ACM Conference on SIGCOMM, Chicago, IL, USA, 17–22 August 2014; ACM: New York, NY, USA, 2014. [Google Scholar]
- Kim, T.Y.; Kim, E.-J. Uplink scheduling of MU-MIMO gateway for massive data acquisition in Internet of things. J. Supercomput. 2016, 1–15. [Google Scholar] [CrossRef]
- Neto, J.B.B.; Silva, T.H.; Assunção, R.M.; Mini, R.A.; Loureiro, A.A. Sensing in the collaborative Internet of things. Sensors 2015, 15, 6607–6632. [Google Scholar] [CrossRef] [PubMed]
- IEEE Standard for Information Technology—Telecommunications and Information Exchange between Systems Local and Metropolitan Area Networks—Specific Requirements—Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications; IEEE: New York, NY, USA, 2003.
- IEEE Standard for Information Technology–Local and Metropolitan Area Networks–Specific Requirements–Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications–Amendment 8: Medium Access Control (MAC) Quality of Service Enhancements; IEEE: New York, NY, USA, 2005.
- Kim, E.-J.; Kwon, J.-H.; Choi, K.; Shon, T. Unified medium access control architecture for resource-constrained machine-to-machine devices. ACM T. Embed. Comput. Syst. 2016, 15, 40:1–40:17. [Google Scholar] [CrossRef]
- Xie, S.; Low, K.S.; Gunawan, E. A Distributed transmission rate adjustment algorithm in heterogeneous CSMA/CA networks. Sensors 2015, 15, 7434–7453. [Google Scholar] [CrossRef] [PubMed]
- Davenport, C.J.; Rigelsford, J.M.; Zhang, J.; Altan, H. Periodic comb reflection frequency selective surface for interference reduction. In Proceedings of the Antennas and Propagation Conference (LAPC), Loughborough, UK, 11–12 November 2013; IEEE: New York, NY, USA, 2013. [Google Scholar]
- Li, Y.; Fu, L.; Ying, Y.; Sun, Y.; Chi, K.; Zhu, Y. Goodput optimization via dynamic frame length and charging time adaptation for backscatter communication. Peer-to-Peer Netw. Appl. 2016, in press. [Google Scholar] [CrossRef]
- Kim, E.-J.; Youm, S.; Kang, C.-H. Power-controlled topology optimization and channel assignment for hybrid MAC in wireless sensor networks. IEICE Trans. Commun. 2011, E94-B, 2461–2472. [Google Scholar] [CrossRef]
- Bhandari, S.; Moh, S. A priority-based adaptive MAC protocol for wireless body area networks. Sensors 2016, 16, 401:1–401:16. [Google Scholar] [CrossRef] [PubMed]
- Bharadia, D.; Joshi, K.R.; Koraru, M.; Katti, S. Backfi: High throughput WiFi backscatter. In Proceedings of the 2015 ACM conference on Special Interest Group on Data Communication, London, UK, 17–21 August 2015; ACM: New York, NY, USA, 2015. [Google Scholar]
- Talla, V.; Kellogg, B.; Ransford, B.; Naderiparizi, S.; Gollakota, S.; Smith, J.R. Powering the next billion devices with Wi-Fi. In Proceedings of the 11th International Conference on emerging Networking Experiments and Technologies, Heidelberg, Germany, 1–4 December 2015; ACM: New York, NY, USA, 2015. [Google Scholar]
- Scalia, L.; Tinnirello, I.; Tantra, J.W.; Foh, C.H. WLC24-1: Dynamic MAC parameters configuration for performance optimization in 802.11 e networks. In Proceedings of the IEEE Globecom 2006, San Francisco, CA, USA, 27 November–1 December 2006; IEEE: New York, NY, USA, 2006. [Google Scholar]
- IEEE Standard for Information Technology–Local and Metropolitan Area Networks–Specific Requirements–Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications–Amendment 5: Enhancements for Higher Throughput; IEEE: New York, NY, USA, 2009.
- Zhang, Z.; Tian, Z.; Zhou, M.; Li, Z.; Wu, Z.; Jin, Y. WIPP: Wi-Fi compass for indoor passive positioning with decimeter accuracy. Appl. Sci. 2016, 6, 108:1–108:18. [Google Scholar] [CrossRef]
- Maruta, K.; Iwakuni, T.; Ohta, A.; Arai, T.; Shirato, Y.; Kurosaki, S.; Iizuka, M. First eigenmode transmission by high efficient CSI estimation for multiuser massive MIMO using millimeter wave bands. Sensors 2016, 16, 1051:1–1051:16. [Google Scholar] [CrossRef] [PubMed]
- Kwon, J.-H.; Chang, H.S.; Shon, T.; Jung, J.-J.; Kim, E.-J. Neighbor stability-based VANET clustering for urban vehicular environments. J. Supercomput. 2016, 72, 161–176. [Google Scholar] [CrossRef]
- Park, H.; Lee, C.; Lee, Y.S.; Kim, E.-J. Performance analysis for contention adaptation of M2M devices with directional antennas. J. Supercomput. 2015, 72, 3387–3408. [Google Scholar] [CrossRef]
- OpenWrt wireless freedom. Available online: https://openwrt.org (accessed on 13 November 2016).
- DD-WRT Wiki. Available online: https://www.dd-wrt.com/wiki/index.php/Main_Page (accessed on 13 November 2016).
- Tomato firmware. Available online: http://www.polarcloud.com/tomato (accessed on 13 November 2016).
- The MadWifi project. Available online: http://madwifi-project.org (accessed on 13 November 2016).
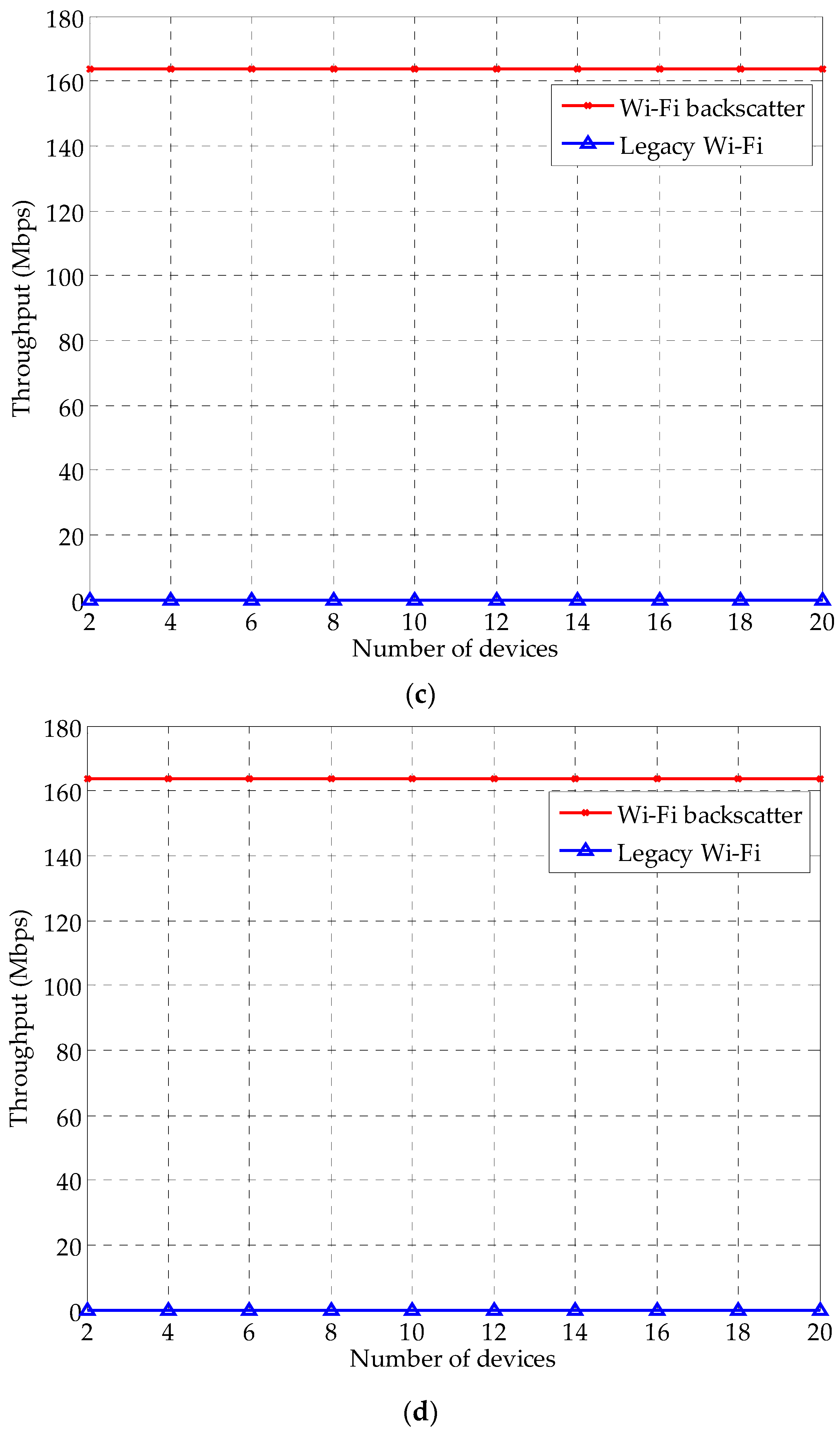
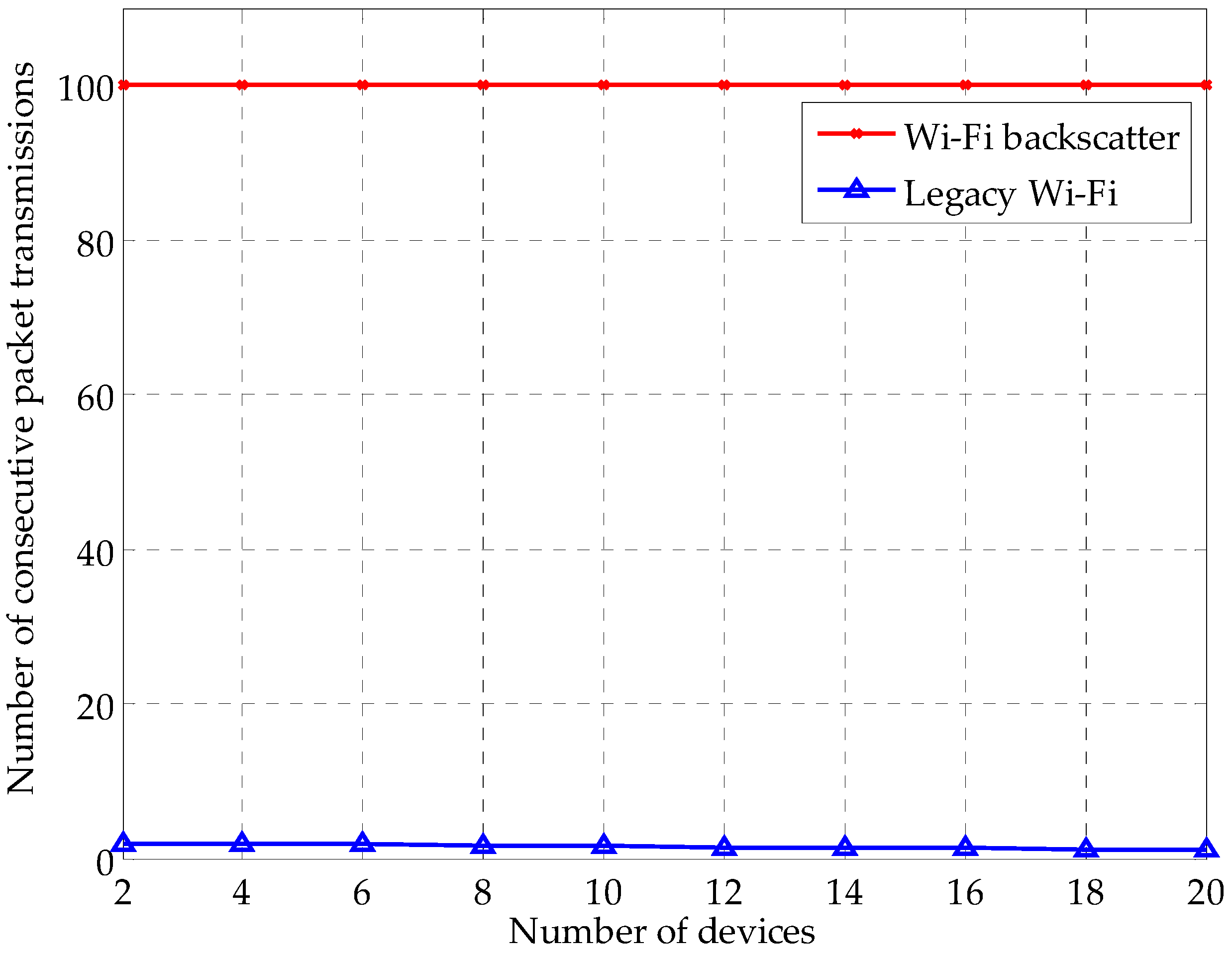

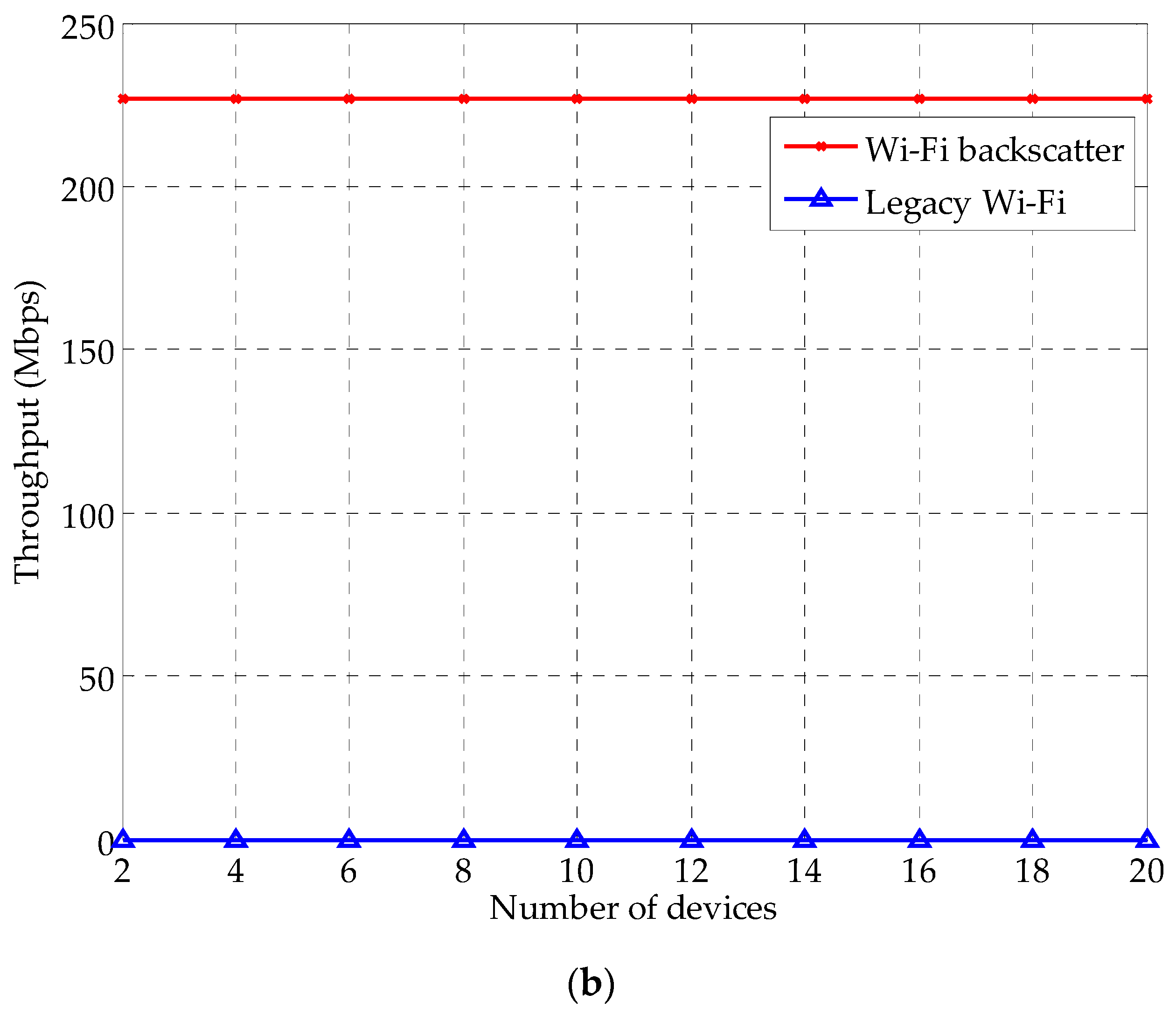
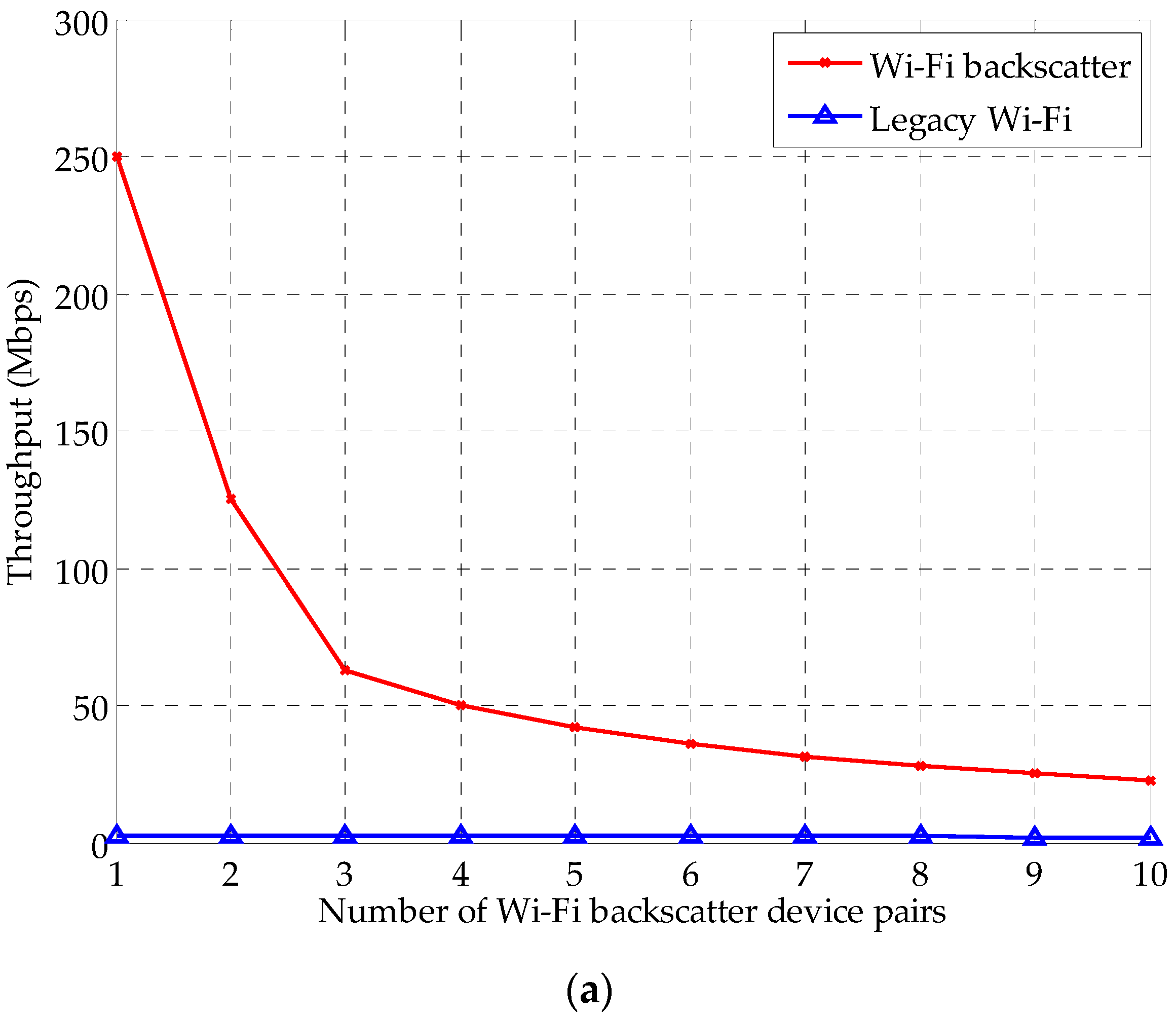
| Parameter | Value | Parameter | Value |
|---|---|---|---|
| PHY/MAC model | IEEE 802.11n | Traffic application | CBR |
| Simulation time | 1000 ms | Date rate | 300 Mbps |
| SIFS | 16 μs | Payload | 2304 bytes |
| DIFS | 34 μs | PHY header | 16 bytes |
| Slot time | 9 μs | MAC header | 30 bytes |
| Maximum retransmission | 6 | CWmin, CWmax | 15, 511 |
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kwon, J.-H.; Lee, H.-H.; Lim, Y.; Kim, E.-J. Dominant Channel Occupancy for Wi-Fi Backscatter Uplink in Industrial Internet of Things. Appl. Sci. 2016, 6, 427. https://doi.org/10.3390/app6120427
Kwon J-H, Lee H-H, Lim Y, Kim E-J. Dominant Channel Occupancy for Wi-Fi Backscatter Uplink in Industrial Internet of Things. Applied Sciences. 2016; 6(12):427. https://doi.org/10.3390/app6120427
Chicago/Turabian StyleKwon, Jung-Hyok, Hwi-Ho Lee, Yongseok Lim, and Eui-Jik Kim. 2016. "Dominant Channel Occupancy for Wi-Fi Backscatter Uplink in Industrial Internet of Things" Applied Sciences 6, no. 12: 427. https://doi.org/10.3390/app6120427






