Computer-Aided Identification and Validation of Intervenability Requirements
Abstract
:1. Introduction
2. Deriving and Structuring Requirements on Intervenability
- Personal data
- “means any information relating to an identified or identifiable natural person (’data subject’)” This term is called personally identifiable information (PII) in ISO/IEC 29100:2011.
- Data subject
- “An identifiable natural person is one who can be identified directly or indirectly, in particular by reference to an identifier such as a name, an identification number, location data, on online identifier or to one or more factors specific to the physical, physiological, genetic, mental, economic, cultural or social identity of that natural person.” This term is called PII principal in ISO/IEC 29100:2011.
- Processing
- “means any operation or set of operations which is performed on personal data or sets of personal data, whether or not by automated means, such as collection, recording, organization, structuring, storage, adaptation or alteration, retrieval, consultation, use, disclosure by transmission, dissemination or otherwise making available, alignment or combination, erasure or destruction.”
- Controller
- “means the natural or legal person, public authority, agency or other body which, alone or jointly with others, determines the purposes and means of the processing of personal data; [...].” This term is called PII controller in ISO/IEC 29100:2011.
- Supervisory authority
- “means a public authority which is established by a Member State pursuant to Article 51.” Article 51 states that supervisory authorities are “responsible for monitoring the application of this Regulation, in order to protect the fundamental rights and freedoms of natural persons in relation to processing and to facilitate the free flow of personal data within the Union.”
2.1. Requirements Identification from Privacy Principles and Legislation
2.1.1. ISO/IEC 29100 Privacy Principles
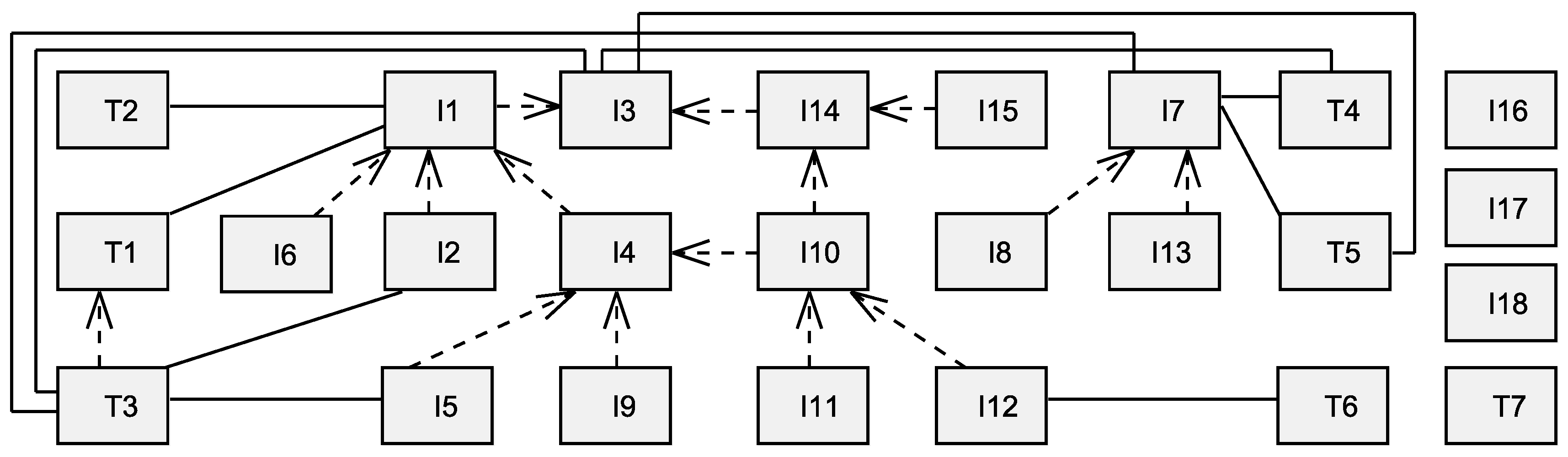
- I1
- Present the data subjects with the choice of whether or not to allow the processing of their personal data.
- I2
- Obtain the opt-in consent of the data subject for collecting or otherwise processing sensitive personal data. !
- T1
- Inform data subjects before obtaining consent about their rights to access their personal data and to influence the processing of these.
- I3
- Provide data subjects with the opportunity to choose how their personal data is handled.
- I4
- Allow data subjects to withdraw consent easily and free of charge.
- T2
- Where the personal data processing is not based on consent but instead on another legal basis, the data subject should be notified wherever possible.
- I5
- Where the data subject has the ability to withdraw consent and has chosen to do so, these personal data should be exempted from processing for any purpose not legally mandated.
- I6
- Provide data subjects with clear, prominent, easily understandable, accessible and affordable mechanisms to exercise choice and to give consent in relation to the processing of their personal data at the time of collection, first use or as soon as practicable thereafter.
- T3
- Disclose the choices and means offered by the controller to data subjects for the purposes of limiting the processing of, and for accessing, correcting and removing their information.
- I7
- Give data subjects the ability to access and review their personal data, provided their identity is first authenticated with an appropriate level of assurance and such access is not prohibited by applicable law.
- I8
- Allow data subjects to challenge the accuracy and completeness of their personal data and have it amended, corrected or removed as appropriate and possible in the specific context.
2.1.2. EU General Data Protection Regulation
- I9
- The data subject shall have the right to withdraw his or her consent at any time.
- T4
- The controller shall inform the data subject without delay and, at the latest within one month of receipt of the request, whether or not any action has been taken if a data subject requested information and shall provide the requested information.
- T5
- If the controller refuses to take action on the request of the data subject, the controller shall inform the data subject of the reasons for the refusal and on the possibilities of lodging a complaint to the supervisory authority and seeking a judicial remedy.
- I10
- The data subject shall have the right to obtain from the controller the erasure of personal data relating to them and the abstention from further dissemination of such data if the data subject withdraws consent or objects to the processing of personal data.
- I11
- The controller shall carry out the erasure without delay, except to the extent that the retention of the personal data is necessary.
- I12
- Where erasure is not possible, the controller shall instead restrict processing of personal data.
- T6
- The controller shall inform the data subject before lifting the restriction on processing.
- I13
- The data subject shall have the right, where personal data are processed by electronic means and in a structured and commonly used format, to obtain from the controller a copy of data undergoing processing in an electronic and structured format which is commonly used and allows for further use by the data subject.
- I14
- The data subject shall have the right to object, on grounds relating to their particular situation, at any time to the processing of personal data, unless the controller demonstrates compelling legitimate grounds for the processing.
- I15
- If the objection is valid, the controller shall no longer use or otherwise process the personal data concerned.
- T7
- Supervisory authorities may order the controller to provide any information relevant to the performance of their duties to them.
- I16
- Supervisory authorities may order the rectification or erasure of all data when they have been processed in breach of the provisions of a regulation.
- I17
- Supervisory authorities may impose a temporary or definitive ban on processing.
- I18
- Supervisory authorities may order to suspend data flows to a recipient in a third country or to an international organization.
2.2. Setting Up an Intervenability Requirements Taxonomy
3. Comparison of the Taxonomy with Related Literature
4. Problem-Based Privacy Analysis
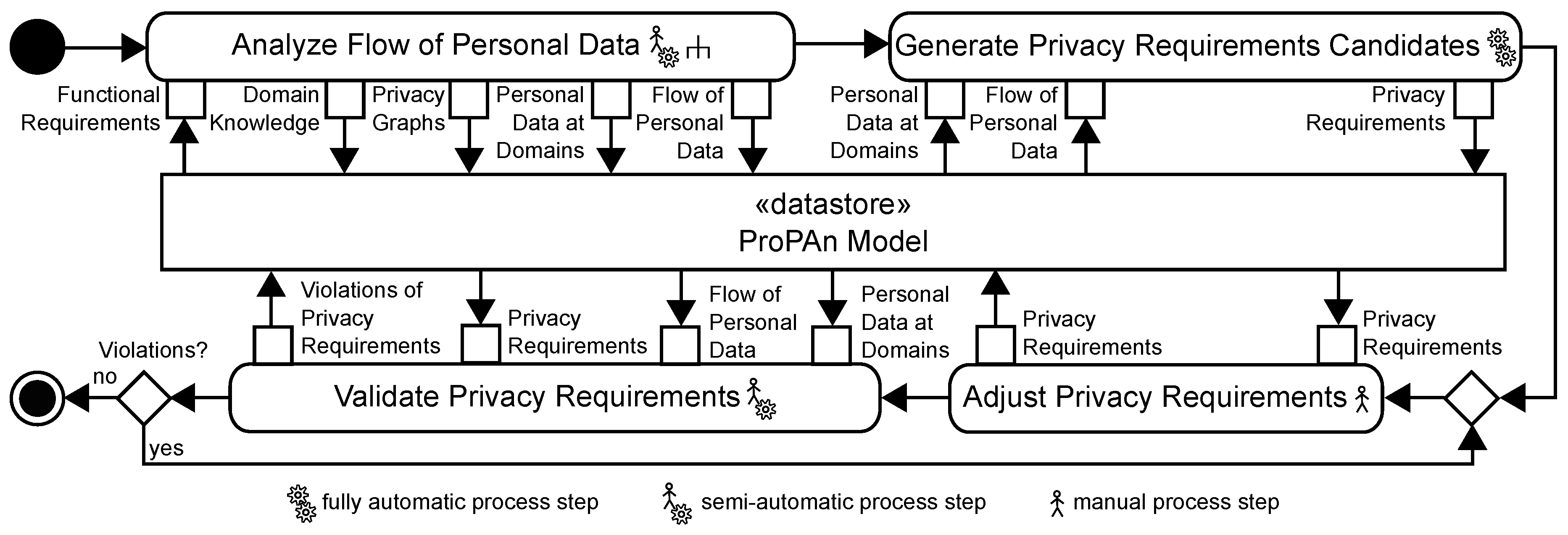
5. Computer-Aided Generation of Intervenability Requirements
5.1. eHealth Application Example
5.2. Generate Intervenability Requirements Candidates
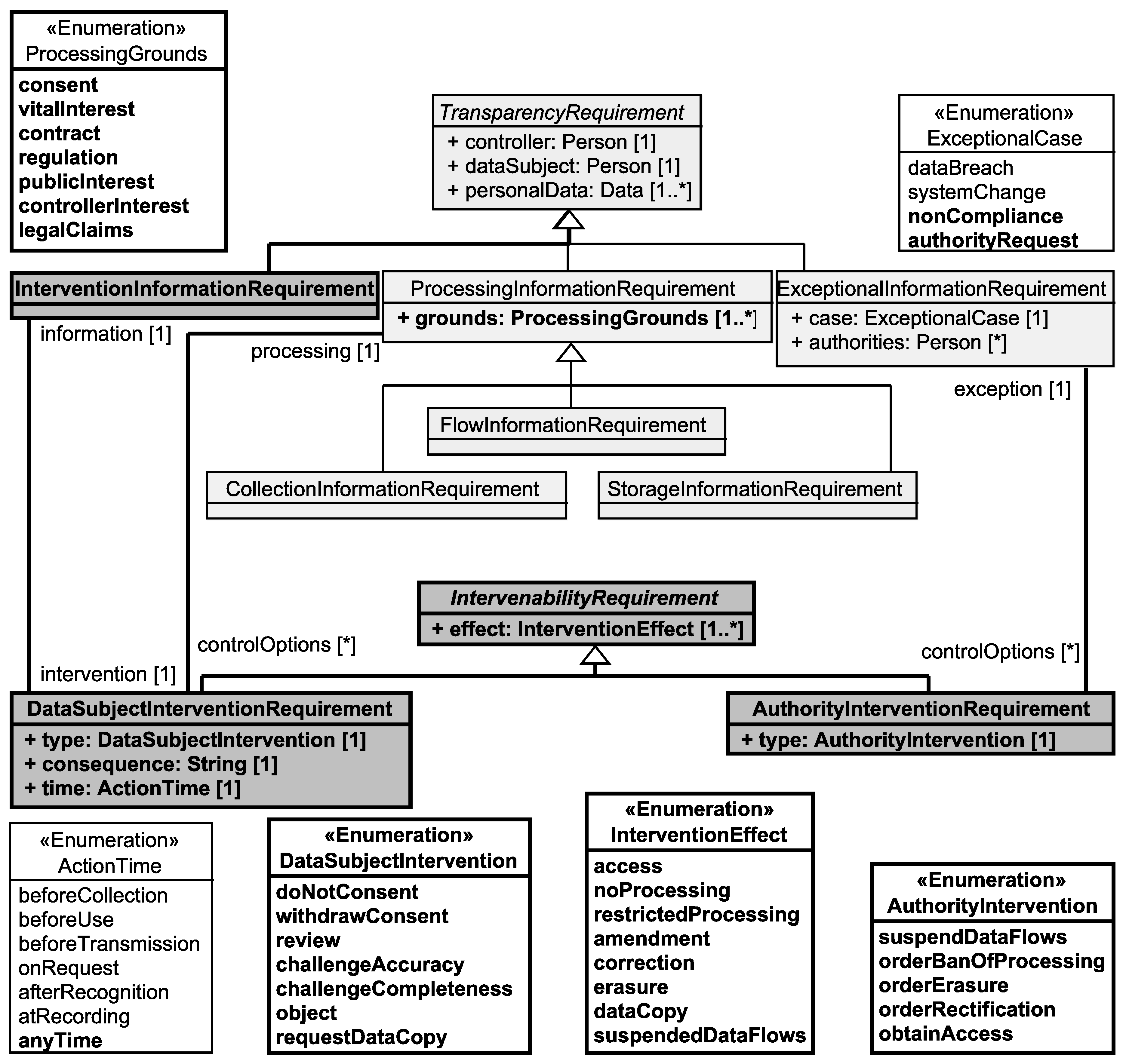
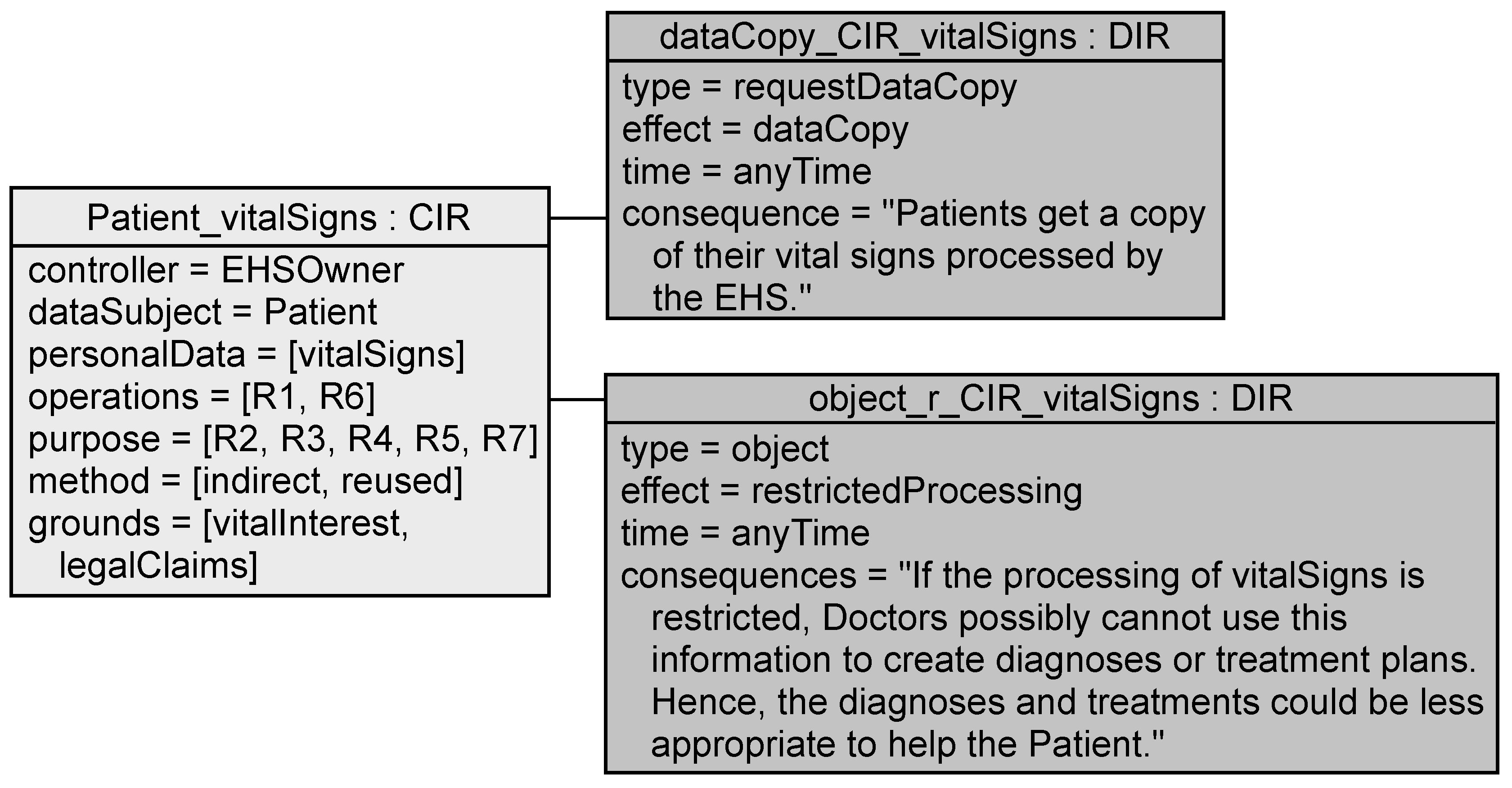
5.2.1. Data Subject Intervention Requirement
- <time> the <processing.dataSubject> shall be able to type to the processing described in <processing>. The intervention shall result in <effect> and can have the consequences <consequence> for <processing.dataSubject>s.
- <time> the <processing.dataSubject> shall be able to type (of) his/her personal data <processing.personalData>. This action shall result in <effect> to/of his/her personal data <processing.personalData> and can have the consequences <consequence> for <processing.dataSubject>s.
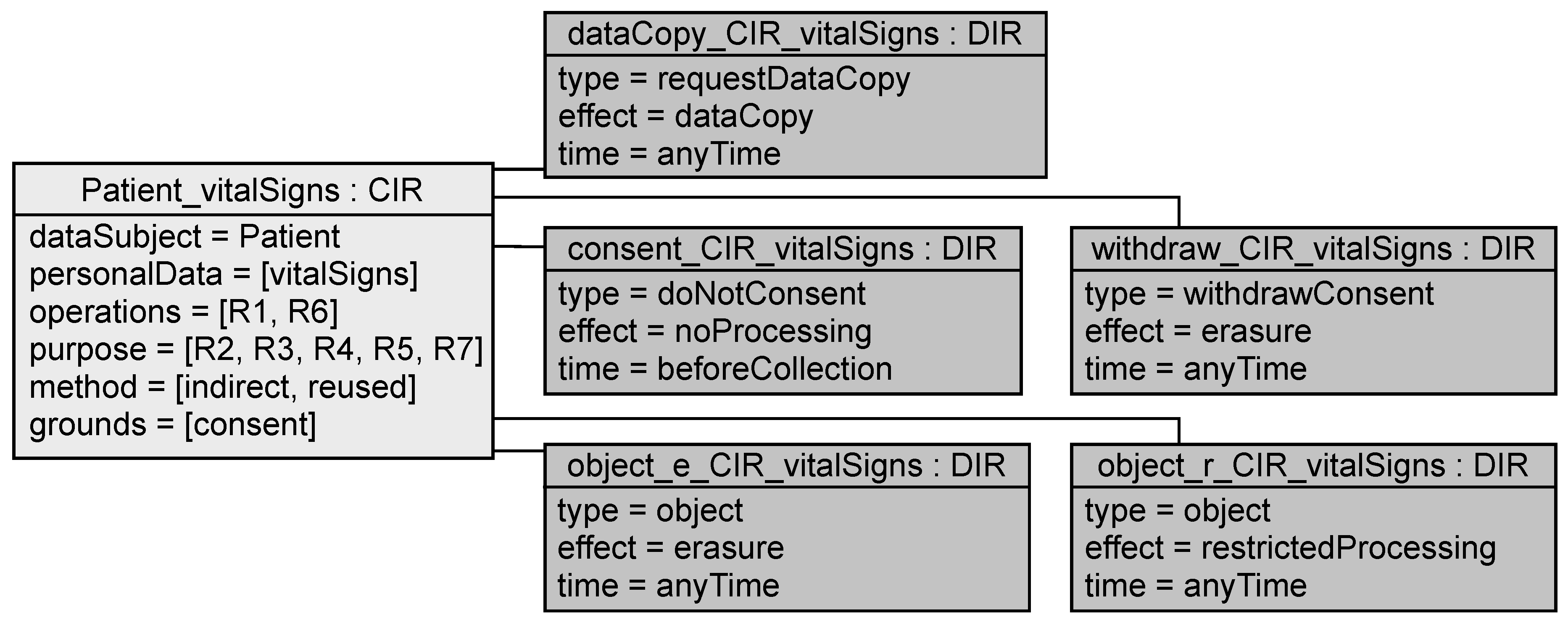
Application to EHS Example
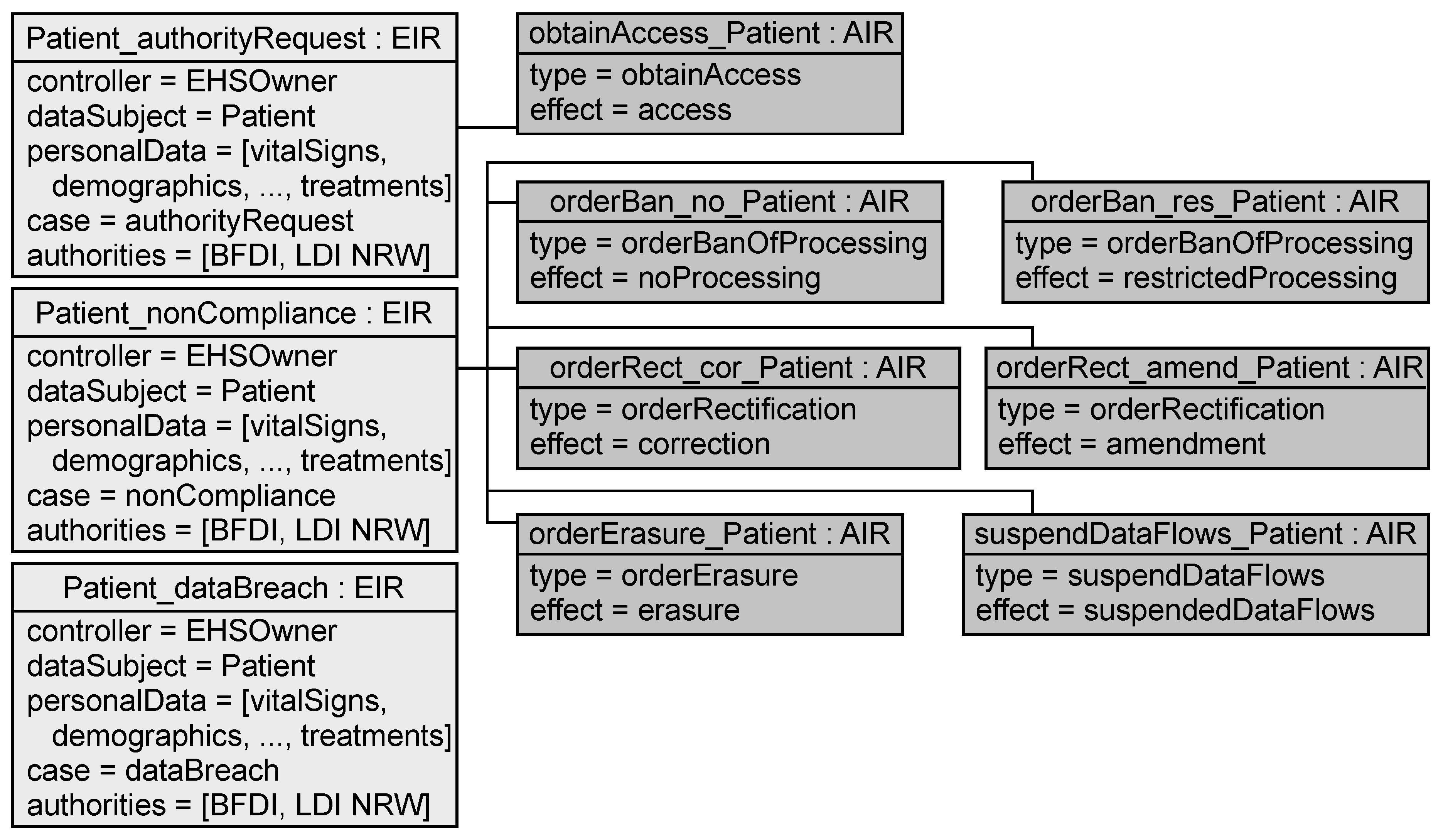
5.2.2. Exceptional Information Requirement and Authority Intervention Requirement
- In the case of a <case> concerning the personal data <personalData> the <dataSubject> and <authorities> have to be informed about the occurrence of this event. <authorities> have then the power to exercise <controlOptions>.
- The <exception.authorities> shall be able to type in the cases described in <exception>. The intervention shall result in <effect>.
Application to EHS Example
5.2.3. Intervention Information Requirement
- The <data subject> shall be informed about the progress of his/her interventions based on <intervention>.
Application to EHS Example
5.3. Adjust Intervenability Requirements
5.3.1. Data Subject Intervention Requirement
Application to EHS Example
5.3.2. Exceptional Information Requirement
Application to EHS Example
5.3.3. Authority Intervention Requirement
Application to EHS Example
5.3.4. Intervention Information Requirement
Application to EHS Example
5.4. Validate Intervenability Requirements
5.4.1. Transparency Requirements
- VT8
- Raise an error for every processing information requirement whose grounds include neither contract, regulation, vitalInterest, publicInterest, controllerInterest, nor legalClaims if its grounds do not include consent.
- VT9
- Raise an error for each processing information requirement whose grounds include consent if no data subject intervention requirements with type doNotConsent and withdrawConsent are controlOptions of the processing information requirement.
- VT10
- Raise an error for each processing information requirement that has as controlOptions data subject intervention requirements with type doNotConsent and withdrawConsent if its grounds do not include consent.
- VT11
- Raise an error for each storage and flow information requirement about personalData that the controller can uniquely link to the dataSubject if it does not have a data subject intervention requirement with type access as controlOption.
- VT12
- Raise an error for each storage and flow information requirement about personalData that the controller can uniquely link to the dataSubject if it does not have a data subject intervention requirement with type challengeAccuracy and challengeCompleteness as controlOption.
- VT13
- Raise an error for each processing information requirement about personalData that the controller can uniquely link to the dataSubject and whose grounds include neither regulation, publicInterest, nor legalClaims if it does not have a data subject intervention requirement with type object and effect erasure as controlOption.
- VT14
- Raise an error for each processing information requirement about personalData that the controller can uniquely link to the dataSubject if it does not have a data subject intervention requirement with type object and effect noProcessing or restrictedProcessing as controlOption.
- VT15
- Raise an error for each collection information requirement about personalData that the controller can uniquely link to the dataSubject and whose grounds do not include publicInterest if it does not have a data subject intervention requirement with type requestDataCopy as controlOption.
- VT16
- Raise an error for each personal data of a data subject if no exceptional information requirement with case dataBreach exists for this data subject and includes the personal data.
- VT17
- Raise an error for each personal data of a data subject if no exceptional information requirement with case authorityRequest exists for this data subject and includes the personal data.
- VT18
- Raise an error for each exceptional information requirement with case authorityRequest if its controlOptions do not include an authority intervention requirement with type obtainAccess.
- VT19
- Raise an error for each personal data of a data subject if no exceptional information requirement with case nonCompliance exists for this data subject and includes the personal data.
- VT20
- Raise an error for each exceptional information requirement with case nonCompliance if its controlOptions do not include authority intervention requirements with type suspendDataFlows, orderBanOfProcessing, orderErasure, and orderRectification.
- VT21
- Raise an error for each exceptional information requirement if the attribute authorities is empty.
Application to the EHS Example
5.4.2. Intervenability Requirements
- VI1
- Raise an error for each data subject intervention requirement where an attribute is not set.
- VI2
- VI3
- Raise an error for each data subject intervention requirement that is a controlOption of a collection information requirement, if its time is not beforeProcessing.
- VI4
- Raise an error for each data subject intervention requirement that is a controlOption of a flow information requirement, if its time is not beforeTransmission.
- VI5
- Raise an error for each data subject intervention requirement that is a controlOption of a storage information requirement, if its time is not atRecording.
- VI6
- Raise an error for each data subject intervention requirement with type access if it is not a controlOption of a storage or flow information requirement.
- VI7
- Raise an error for each data subject intervention requirement with type access if its time is not anyTime.
- VI8
- Raise an error for each data subject intervention requirement with type challengeAccuracy or challengeCompleteness if it is not a controlOption of a storage or flow information requirement.
- VI9
- Raise an error for each data subject intervention requirement with type challengeAccuracy or challengeCompleteness if its time is not anyTime.
- VI10
- Raise an error for each data subject intervention requirement with type withdrawConsent, object, or requestDataCopy if its time is not anyTime.
- VI11
- Raise an error for each data subject intervention requirement with type withdrawConsent that is a controlOption of a processing information requirement whose grounds include neither contract, regulation, vitalInterest, publicInterest, controllerInterest, nor legalClaims if this data subject intervention requirement does not have the effect erasure.
Application to the EHS Example
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
Abbreviations
| AIR | AuthorityInterventionRequirement |
| DIR | DataSubjectInterventionRequirement |
| EHR | Electronic Health Record |
| EHS | Electronic Health System |
| EIR | ExceptionalInformationRequirement |
| IIR | InterventionInformationRequirement |
| IR | IntervenabilityRequirement |
| OECD | Organisation for Economic Co-operation and Development |
| PET | Privacy Enhancing Technology |
| PIR | ProcessingInformationRequirement |
| ProPAn | Problem-based Privacy Analysis |
| RIT | Relation between intervenability and transparency requirements |
| SDFG | Stakeholder Data Flow Graph |
| UML | Unified Modeling Language |
References
- GSMA. MOBILE PRIVACY: Consumer Research Insights and Considerations For Policymakers. Available online: http://www.gsma.com/publicpolicy/wp-content/uploads/2014/02/MOBILE_PRIVACY_Consumer_research_insights_and_considerations_for_policymakers-Final.pdf (accessed on 20 June 2016).
- Symantec. State of Privacy Report 2015. Available online: https://www.symantec.com/content/en/us/about/presskits/b-state-of-privacy-report-2015.pdf (accessed on 20 June 2016).
- Quah, A.M.Y.; Röhm, U. User Awareness and Policy Compliance of Data Privacy in Cloud Computing. In Proceedings of the First Australasian Web Conference–Volume 144, Adelaide, Australia, 29 January–3 February 2013; pp. 3–12.
- Ackerman, M.S.; Cranor, L.F.; Reagle, J. Privacy in e-Commerce: Examining User Scenarios and Privacy Preferences. In Proceedings of the 1st ACM Conference on Electronic Commerce (EC ’99), Denver, CO, USA, 3–5 November 1999; pp. 1–8.
- Hansen, M. Top 10 Mistakes in System Design from a Privacy Perspective and Privacy Protection Goals. In Privacy and Identity Management for Life; Camenisch, J., Crispo, B., Fischer-Hübner, S., Leenes, R., Russello, G., Eds.; Springer: Berlin/Heidelberg, Germany, 2012; pp. 14–31. [Google Scholar]
- Meis, R.; Heisel, M. Understanding the Privacy Goal Intervenability. In Trust, Privacy, and Security in Digital Business; Springer: Berlin/Heidelberg, Germany, 2016; pp. 79–94. [Google Scholar]
- Meis, R.; Heisel, M.; Wirtz, R. A Taxonomy of Requirements for the Privacy Goal Transparency. In Trust, Privacy, and Security in Digital Business; Springer: Berlin/Heidelberg, Germany, 2015; pp. 195–209. [Google Scholar]
- Meis, R.; Heisel, M. Computer-Aided Identification and Validation of Privacy Requirements. Information 2016, 7, 28. [Google Scholar] [CrossRef]
- International Organization for Standardization and International Electrotechnical Commission (ISO/IEC). ISO/IEC 29100:2011 Information Technology–Security Techniques–Privacy Framework. Available online: https://www.iso.org/standard/45123.html (accessed on 3 March 2017).
- European Commission. Regulation (EU) 2016/679 of the European Parliament and of the Council of 27 April 2016 on the Protection of Natural Persons with Regard to the Processing of Personal Data and on the Free Movement of such Data, and Repealing Directive 95/46/EC (General Data Protection Regulation). Available online: http://eur-lex.europa.eu/legal-content/EN/TXT/?uri=CELEX:32016R0679 (accessed on 14 December 2016).
- Organisation for Economic Co-operation and Development (OECD). OECD Guidelines on the Protection of Privacy and Transborder Flows of Personal Data. Available online: https://www.oecd.org/sti/ieconomy/oecdguidelinesontheprotectionofprivacyandtransborderflowsofpersonaldata.htm (accessed on 5 March 2017).
- US Federal Trade Commission. Privacy Online: Fair Information Practices in the Electronic Marketplace: A Federal Trade Commission Report to Congress. Available online: https://www.ftc.gov/reports/privacy-online-fair-information-practices-electronic-marketplace-federal-trade-commission (accessed on 5 March 2017).
- Jalali, S.; Wohlin, C. Systematic Literature Studies: Database Searches vs. Backward Snowballing. In Proceedings of the ACM-IEEE International Symposium on Empirical Software Engineering and Measurement, Lund, Sweden, 19–20 September 2012; pp. 29–38.
- CORE2014. Available online: http://www.core.edu.au/conference-portal (accessed on 20 June 2016).
- Bier, C. How Usage Control and Provenance Tracking Get Together—A Data Protection Perspective. In Presented at 2013 IEEE Security and Privacy Workshops (SPW), San Diego, CA, USA, 23–24 May 2013; 2013; pp. 13–17. [Google Scholar]
- Hoepman, J.H. In Privacy Design Strategies—(Extended Abstract). In ICT Systems Security and Privacy Protection; Springer: Berlin/Heidelberg, Germany, 2014; pp. 446–459. [Google Scholar]
- Mouratidis, H.; Islam, S.; Kalloniatis, C.; Gritzalis, S. A framework to support selection of cloud providers based on security and privacy requirements. J. Syst. Softw. 2013, 86, 2276–2293. [Google Scholar] [CrossRef]
- Miyazaki, S.; Mead, N.; Zhan, J. Computer-Aided Privacy Requirements Elicitation Technique. In Presented at IEEE 2008 Asia-Pacific Services Computing Conference (APSCC ’08), Yilan, Taiwan, 9–12 December 2008; pp. 367–372.
- Kalloniatis, C.; Mouratidis, H.; Vassilis, M.; Islam, S.; Gritzalis, S.; Kavakli, E. Towards the design of secure and privacy-oriented information systems in the cloud: Identifying the major concepts. Comput. Stand. Interfaces 2014, 36, 759–775. [Google Scholar] [CrossRef]
- Kalloniatis, C. Designing Privacy-Aware Systems in the Cloud. In Trust, Privacy and Security in Digital Business; Lecture Notes in Computer Science (LNCS); Springer: Berlin/Heidelberg, Germany, 2015; Volume 9264, pp. 113–123. [Google Scholar]
- Spiekermann, S.; Cranor, L. Engineering Privacy. IEEE Trans. Softw. Eng. 2009, 35, 67–82. [Google Scholar] [CrossRef]
- Makri, E.; Lambrinoudakis, C. Privacy Principles: Towards a Common Privacy Audit Methodology. In Trust, Privacy and Security in Digital Business; Springer: Berlin/Heidelberg, Germany, 2015; Volume 9264, pp. 219–234. [Google Scholar]
- Acquisti, A.; Adjerid, I.; Brandimarte, L. Gone in 15 Seconds: The Limits of Privacy Transparency and Control. IEEE Secur. Priv. 2013, 11, 72–74. [Google Scholar] [CrossRef]
- Masiello, B. Deconstructing the Privacy Experience. IEEE Secur. Priv. 2009, 7, 68–70. [Google Scholar] [CrossRef]
- Krol, K.; Preibusch, S. Effortless Privacy Negotiations. IEEE Secur. Priv. 2015, 13, 88–91. [Google Scholar] [CrossRef]
- Deng, M.; Wuyts, K.; Scandariato, R.; Preneel, B.; Joosen, W. A privacy threat analysis framework: Supporting the elicitation and fulfillment of privacy requirements. Requir. Eng. 2011, 1, 3–32. [Google Scholar] [CrossRef]
- Komanduri, S.; Shay, R.G.; Norcie, B.U.; Cranor, L.F. AdChoices? Compliance with Online Behavioral Advertising Notice and Choice Requirements. Available online: http://moritzlaw.osu.edu/students/groups/is/files/2012/02/Komanduir.Final_.pdf (accessed on 20 June 2016).
- Cranor, L.F. Necessary But Not Sufficient: Standardized Mechanisms for Privacy Notice and Choice. J. Telecomm. High Tech. L. 2012, 10, 273–308. [Google Scholar]
- Wicker, S.; Schrader, D. Privacy-Aware Design Principles for Information Networks. Proc. IEEE 2011, 99, 330–350. [Google Scholar] [CrossRef]
- Strickland, L.S.; Hunt, L.E. Technology, Security, and Individual Privacy: New Tools, New Threats, and New Public Perceptions. J. Assoc. Inf. Sci. Technol. 2005, 56, 221–234. [Google Scholar] [CrossRef]
- Sheth, S.; Kaiser, G.; Maalej, W. Us and Them: A Study of Privacy Requirements Across North America, Asia, and Europe. In Proceedings of the 36th International Conference on Software Engineering (ICSE 2014), Hyderabad, India, 31 May–7 June 2014; pp. 859–870.
- Fhom, H.; Bayarou, K. Towards a Holistic Privacy Engineering Approach for Smart Grid Systems. In Presented at 2011 IEEE 10th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), Changsha, China, 16–18 November 2011; pp. 234–241.
- Antón, A.I.; Earp, J.B.; Reese, A. Analyzing Website Privacy Requirements Using a Privacy Goal Taxonomy. In Proceedings of the IEEE Joint International Conference on Requirements Engineering, Essen, Germany, 9–13 September 2002; pp. 23–31.
- Antón, A.I.; Earp, J.B. A requirements taxonomy for reducing Web site privacy vulnerabilities. Requir. Eng. 2004, 9, 169–185. [Google Scholar] [CrossRef]
- Van Der Sype, Y.S.; Seigneur, J.M. Case study: Legal requirements for the use of social login features for online reputation updates. In Proceedings of the 29th Annual ACM Symposium on Applied Computing (SAC ’14), Gyeongju, Korea, 24–28 March 2014; pp. 1698–1705.
- Basso, T.; Moraes, R.; Jino, M.; Vieira, M. Requirements, design and evaluation of a privacy reference architecture for web applications and services. In Proceedings of the 30th Annual ACM Symposium on Applied Computing (SAC ’15), Salamanca, Spain, 13–17 April 2015; pp. 1425–1432.
- Lobato, L.; Fernandez, E.; Zorzo, S. Patterns to Support the Development of Privacy Policies. In Presented at International Conference on Availability, Reliability and Security, 2009 (ARES ’09), Fukuoka, Japan, 16–19 March 2009; pp. 744–749.
- Caron, X.; Bosua, R.; Maynard, S.B.; Ahmad, A. The Internet of Things (IoT) and its impact on individual privacy: An Australian perspective. Comput. Law Secur. Rev. 2016, 32, 4–15. [Google Scholar] [CrossRef]
- Borgesius, F.Z. Informed Consent: We Can Do Better to Defend Privacy. IEEE Secur. Priv. 2015, 13, 103–107. [Google Scholar] [CrossRef]
- Breaux, T. Privacy Requirements in an Age of Increased Sharing. IEEE Softw. 2014, 31, 24–27. [Google Scholar] [CrossRef]
- Langheinrich, M. Privacy by Design — Principles of Privacy-Aware Ubiquitous Systems. In Ubicomp 2001: Ubiquitous Computing; LNCS 2201; Springer: Berlin/Heidelberg, Germany, 2001; pp. 273–291. [Google Scholar]
- Feigenbaum, J.; Freedman, M.; Sander, T.; Shostack, A. Privacy Engineering for Digital Rights Management Systems. In Security and Privacy in Digital Rights Management; LNCS 2320; Springer: Berlin/Heidelberg, Germany, 2002; pp. 76–105. [Google Scholar]
- Wright, D.; Raab, C. Privacy principles, risks and harms. Int. Rev. Law Comput. Technol. 2014, 28, 277–298. [Google Scholar] [CrossRef]
- Guarda, P.; Zannone, N. Towards the Development of Privacy-aware Systems. Inf. Softw. Technol. 2009, 51, 337–350. [Google Scholar] [CrossRef]
- Hedbom, H. A Survey on Transparency Tools for Enhancing Privacy. In The Future of Identity in the Information Society; IFIP AICT 298; Springer: Berlin/Heidelberg, Germany, 2009; pp. 67–82. [Google Scholar]
- Smith, H.J.; Dinev, T.; Xu, H. Information Privacy Research: An Interdisciplinary Review. MIS Q. 2011, 35, 989–1016. [Google Scholar]
- ProPAn Tool. Available online: http://www.uml4pf.org/ext-propan/ (accessed on 7 March 2017).
- Jackson, M. Problem Frames: Analyzing and Structuring Software Development Problems; Addison-Wesley: Boston, MA, USA, 2001. [Google Scholar]
- Meis, R. Problem-Based Consideration of Privacy-Relevant Domain Knowledge. In Privacy and Identity Management for Emerging Services and Technologies; IFIP AICT 421; Springer: Berlin/Heidelberg, Germany, 2014; pp. 150–164. [Google Scholar]
- Beckers, K.; Faßbender, S.; Gritzalis, S.; Heisel, M.; Kalloniatis, C.; Meis, R. Privacy-Aware Cloud Deployment Scenario Selection. In Trust, Privacy, and Security in Digital Business; LNCS 8647; Springer: Berlin/Heidelberg, Germany, 2014; pp. 94–105. [Google Scholar]
- Beckers, K.; Faßbender, S.; Heisel, M.; Meis, R. A Problem-based Approach for Computer Aided Privacy Threat Identification. In Privacy Technologies and Policy; LNCS 8319; Springer: Berlin/Heidelberg, Germany, 2014; pp. 1–16. [Google Scholar]
- Meis, R.; Heisel, M. Supporting Privacy Impact Assessments using Problem-based Privacy Analysis. Softw. Technol. 2016, 586, 79–98. [Google Scholar]
- Network of Excellence on Engineering Secure Future Internet Software Services and Systems (NESSoS). Available online: http://www.nessos-project.eu/ (accessed on 7 March 2017).
- European Data Protection Authorities. Available online: http://ec.europa.eu/justice/data-protection/article-29/structure/data-protection-authorities/index_en.htm (accessed on 14 December 2016).
- Sabit, S. Consideration of Intervenability Requirements in Software Development. Master Thesis, University of Duisburg-Essen, Duisburg, Germany, 2015. [Google Scholar]

| Principle/Article | In/Tn | IR | DIR | AIR | PIR | EIR | IIR |
|---|---|---|---|---|---|---|---|
| Consent and choice | I1-I6, T1, T2 | X | X | X | |||
| Openness, transparency and notice | T3 | X | X | ||||
| Individual participation and access | I7, I8 | X | X | ||||
| Article 7 | I9 | X | |||||
| Article 12 | T4, T5 | X | |||||
| Article 15 | I7, T3 | X | X | X | |||
| Article 16 | I8 | X | X | ||||
| Article 17 | I10-I12, T6 | X | X | X | |||
| Article 20 | I13 | X | X | ||||
| Article 18 and 21 | I14, I15 | X | X | ||||
| Article 58 | I16-I18, T7 | X | X | X |
| Requirement | Attribute | In/Tn |
|---|---|---|
| IntervenabilityRequirement | effect | I1, I3, I5, I7, I8, I10-I13, I15-I18 |
| DataSubjectInterventionRequirement | type | I1-I5, I7, I8, I10-I15 |
| time | I6, I9, I14 | |
| consequences | T1, T3, I6 | |
| AuthorityInterventionRequirement | type | I16, I17, I18 |
| ProcessingInformationRequirement | controlOptions | T1, T3, I6 |
| grounds | T2 | |
| ExceptionalInformationRequirement | exceptionalCase | I16, I17, I18, T7 |
| InterventionInformationRequirement | T4, T5, T6 |
| Intervention Type | Possible Intervention Effects | Source |
|---|---|---|
| suspendDataFlows | suspendedDataFlows | I18 |
| orderBanOfProcessing | noProcessing, restrictedProcessing | I17 |
| orderErasure | erasure | I16 |
| orderRectification | correction, amendment | I16 |
| obtainAccess | access | T7 |
| Intervention Type | Possible Intervention Effects | Source |
|---|---|---|
| doNotConsent | noProcessing | I2 |
| withdrawConsent | noProcessing, restrictedProcessing, erasure | I4, I5, I10, I12 |
| review | access | I7 |
| challengeAccuracy | correction, amendment, erasure | I8 |
| challengeCompleteness | amendment, erasure | I8 |
| object | noProcessing, restrictedProcessing, erasure | I10, I12, I15 |
| requestDataCopy | dataCopy | I13 |
| Source | DIR | AIR | RIT |
|---|---|---|---|
| Bier [15], Hansen [5] | + | + | o |
| Hoepman [16] | + | o | o |
| Mouratidis et al. [17] | o | o | o |
| Miyazaki et al. [18] | + | + | - |
| Kalloniatis et al. [19,20], Spiekermann and Cranor [21] | o | o | - |
| Makri and Lambrinoudakis [22], Acquisti et al. [23], Masiello [24], Krol and Preibusch [25], Deng et al. [26], Komanduri et al. [27], Cranor [28], Wicker and Schrader [29] | o | - | o |
| Strickland and Hunt [30], Sheth et al. [31], Fhom and Bayarou [32], Antón et al. [33,34], Van der Sype and Seigneur [35], Basso et al. [36] | + | - | - |
| Lobato et al. [37], Caron et al. [38], Zuiderveen Borgesius [39], Breaux [40], Langheinrich [41], Feigenbaum et al. [42], Wright and Raab [43], Guarda and Zannone [44], Hedbom [45], Smith et al. [46] | o | - | - |
| Processing Information Requirement | Requirements with Intervention Type |
|---|---|
| Collection, Storage, and Flow | doNotConsent, withdrawConsent, and object |
| Storage and Flow | review, challengeAccuracy, challenge Completeness |
| Collection | requestDataCopy |
| Condition | Result | Reason |
|---|---|---|
| VT8 | not applicable | grounds include vitalInterest and legalClaims |
| VT9 | not applicable | grounds do not include consent |
| VT10 | not applicable | no controlOptions with type doNotConsent and withdrawConsent are assigned |
| VT11 | not applicable | requirement is neither a storage nor flow information requirement |
| VT12 | not applicable | requirement is neither a storage nor flow information requirement |
| VT13 | not applicable | grounds includes legalClaims |
| VT14 | satisfied | a controlOption with type object and effect restrictedProcessing exists |
| VT15 | satisfied | a controlOption with type requestDataCopy exists |
| VT16 | not applicable | requirement is not an exceptional information requirement |
| VT17 | not applicable | requirement is not an exceptional information requirement |
| VT18 | not applicable | requirement is not an exceptional information requirement |
| VT19 | not applicable | requirement is not an exceptional information requirement |
| VT20 | not applicable | requirement is not an exceptional information requirement |
| VT21 | not applicable | requirement is not an exceptional information requirement |
| Condition | Result | Reason |
|---|---|---|
| VI1 | satisfied | all attributes are set (the intervention information requirement is not shown) |
| VI2 | satisfied | the combination of object and restrictedProcessing exists in Table 4 |
| VI3 | satisfied | anyTime beforeProcessing |
| VI4 | not applicable | requirement is not related to a flow information requirement |
| VI5 | not applicable | requirement is not related to a storage information requirement |
| VI6 | not applicable | requirement does not have type access |
| VI7 | not applicable | requirement does not have type access |
| VI8 | not applicable | requirement does not have type challengeAccuracy or challengeCompleteness |
| VI9 | not applicable | requirement does not have type challengeAccuracy or challengeCompleteness |
| VI10 | satisfied | time is anyTime |
| VI11 | not applicable | requirement does not have type withdrawConsent |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license ( http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Meis, R.; Heisel, M. Computer-Aided Identification and Validation of Intervenability Requirements. Information 2017, 8, 30. https://doi.org/10.3390/info8010030
Meis R, Heisel M. Computer-Aided Identification and Validation of Intervenability Requirements. Information. 2017; 8(1):30. https://doi.org/10.3390/info8010030
Chicago/Turabian StyleMeis, Rene, and Maritta Heisel. 2017. "Computer-Aided Identification and Validation of Intervenability Requirements" Information 8, no. 1: 30. https://doi.org/10.3390/info8010030






