Protecting Touch: Authenticated App-To-Server Channels for Mobile Devices Using NFC Tags
Abstract
:1. Introduction
2. Related Work
3. Functionality of NFC Tags
4. Protecting Touch
- The first architecture (PT1) uses freely-readable NFC tags as storage for key material that is bound to a specific installation of the authenticating mobile app and can be used for authentication towards the backend system. This architecture is designed to work with any NFC tag, given that the tag has sufficient memory space for the key material. PT1 relies solely on the NDEF abstraction layer to provide a maximum level of interoperability.
- The second architecture (PT2) uses the mutual three-pass authentication protocol of MIFARE DESFire tags and specific side-effects of the DESFire communication protocol to generate deterministic random symmetric session keys between the mobile app and its backend. This architecture specifically targets MIFARE DESFire and, thus, the upper end (in terms of capabilities and cost) of available NFC tags. While PT2 requires more expensive tags, the price is still far below smart card solutions such as the YubiKey NEO (more than a factor of 10; see Section 4.5).
4.1. Requirements and Threats
- Anyone with access to the app may be able to use the session token to access some functionality of the app and some data about the bank account without knowing the password. Even if the user interface of the app is protected by a lock pattern or PIN that is verified locally in the app, an attacker may be able to bypass or discover that code by analyzing the app and its memory (e.g., using malware running on the mobile device).
- Going one step further, it is questionable whether session tokens are sufficiently secured within the app. Typically, it should not be possible to duplicate the app (including its session token) onto another device (e.g., through a backup and restore) without voiding the authenticated session.
- Users who often perform operations that require re-typing the password may tend to use passwords that can be easily typed using the limited input capabilities of the mobile device (cf. Greene et al. [2]). Additionally, these users are more frequently exposed to the possibility of eavesdropping on the password through shoulder surfing, etc.
- The app requires users to present their NFC tag whenever they use the app. Authenticating the NFC tag from the backend side prevents attacks possible with locally-verified lock mechanisms.
- Secured key vaults accessible only by the app, for instance the Android Keystore, are a means to facilitate storage for key material used by the app. Key vaults are dedicated hardware (or software) components that encapsulate the key material in a way that it never leaves the vault. In order to use the keys, apps delegate their cryptographic operations to the key vault.Binding key material stored on the tag to key material stored within the app (or a key vault) reduces the attack surface against extraction of that key material from the key vault since the bound key material is useless unless the attacker also has access to the NFC tag (or potentially a copy of it). Moreover, it binds the tag to one specific app installation.
- Requiring users to carry an NFC tag besides the smartphone is potentially less cumbersome than memorizing and frequently typing a complex password. Since the NFC tag is required for authentication, this may also reduce the risk of the password getting known to any third party since they would also need to get hold of the NFC tag. Nevertheless, new risks may be introduced through the use of NFC tags as well. For instance, the NFC interface may be easily eavesdropped on. Further, an NFC tag is a physical object that needs to be carried around by its user and may be subject to loss or theft.
- The NFC tag can be used besides a normal password as a secondary authentication factor. Moreover, it acts as an additional factor besides session tokens stored within the app. However, we acknowledge that in the latter case, both factors, the NFC tag and the smartphone app installation instance, follow the same principle, i.e., they are both something that the user has.
4.2. Protecting Touch 1
4.2.1. Tag Memory Layout
4.2.2. Protocol Operation
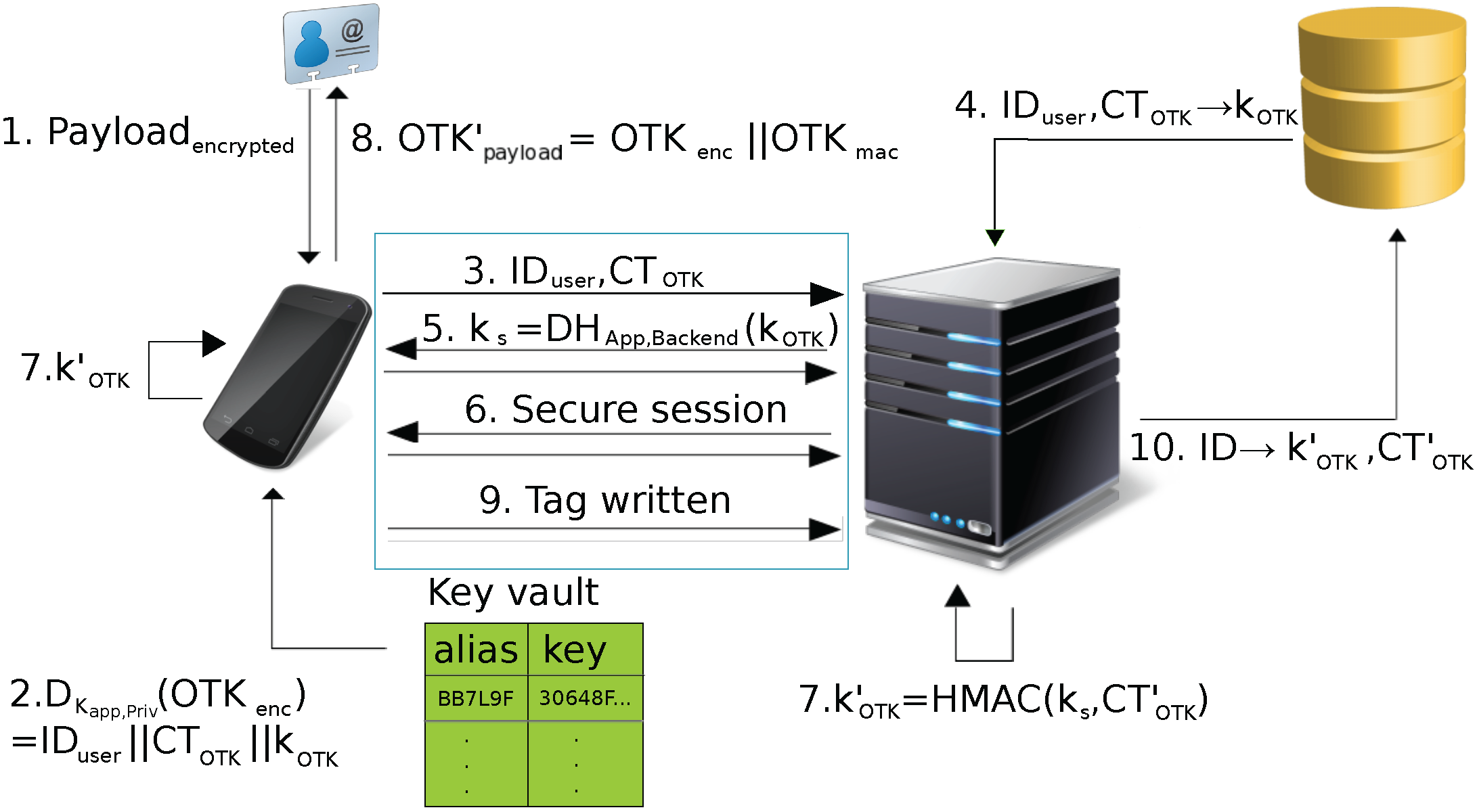
- The app reads the NDEF message from the NFC tag and extracts the OTK record.
- The app splits the payload into and , verifies the message authentication code, decrypts the OTK record payload, and extracts the data elements (, , ) using keys and stored in the key vault.If the key vault does not support symmetric keys directly, an asymmetric key pair stored within the key vault may be used instead. In that case, the symmetric keys and are stored in “insecure” device memory in encrypted form . The keys are only decrypted using the private key of the key pair inside the key vault when needed.
- The app initializes the interaction with the backend server by sending and in order to give the server a hint about the authenticating user and the used tag.
- The backend loads from its key database (based on and key index counter ) and starts the authentication phase. If no matching one-time key is in the database, communication with the app is ended.
- After agreeing on a session key , the app and backend continue their communication over a secure channel (authenticated and encrypted based on the agreed session key). The implementation of the secure channel protocol is beyond the scope of this paper.
- The app and the backend increment the key index counter and derive a new from . The key derivation is based on the HMAC-based One-Time Password (HOTP) algorithm [23].
- The app constructs the new OTK record (from , the incremented key index counter and the new one-time key), encrypts it and adds a message authentication code using the symmetric keys inside the key vault.If the key vault does not support symmetric keys directly, fresh symmetric keys and are generated and used for the above operations. They are then encrypted to using the asymmetric key pair in the key vault and stored in regular device memory.Then, the OTK record is stored onto the tag.
- Upon successfully writing the data to the tag, the app sends a confirmation to the backend. The user is instructed to reattach the tag in case of write errors.
- The backend, in turn, stores the new one-time key and the incremented key index counter in its key database and removes the old one-time key. If the app does not confirm a successful write operation, the server discards the new one-time key and terminates the session. After too many failed attempts, it may block the current one-time key and require a fresh tag enrollment.
4.2.3. Initial Tag Enrollment
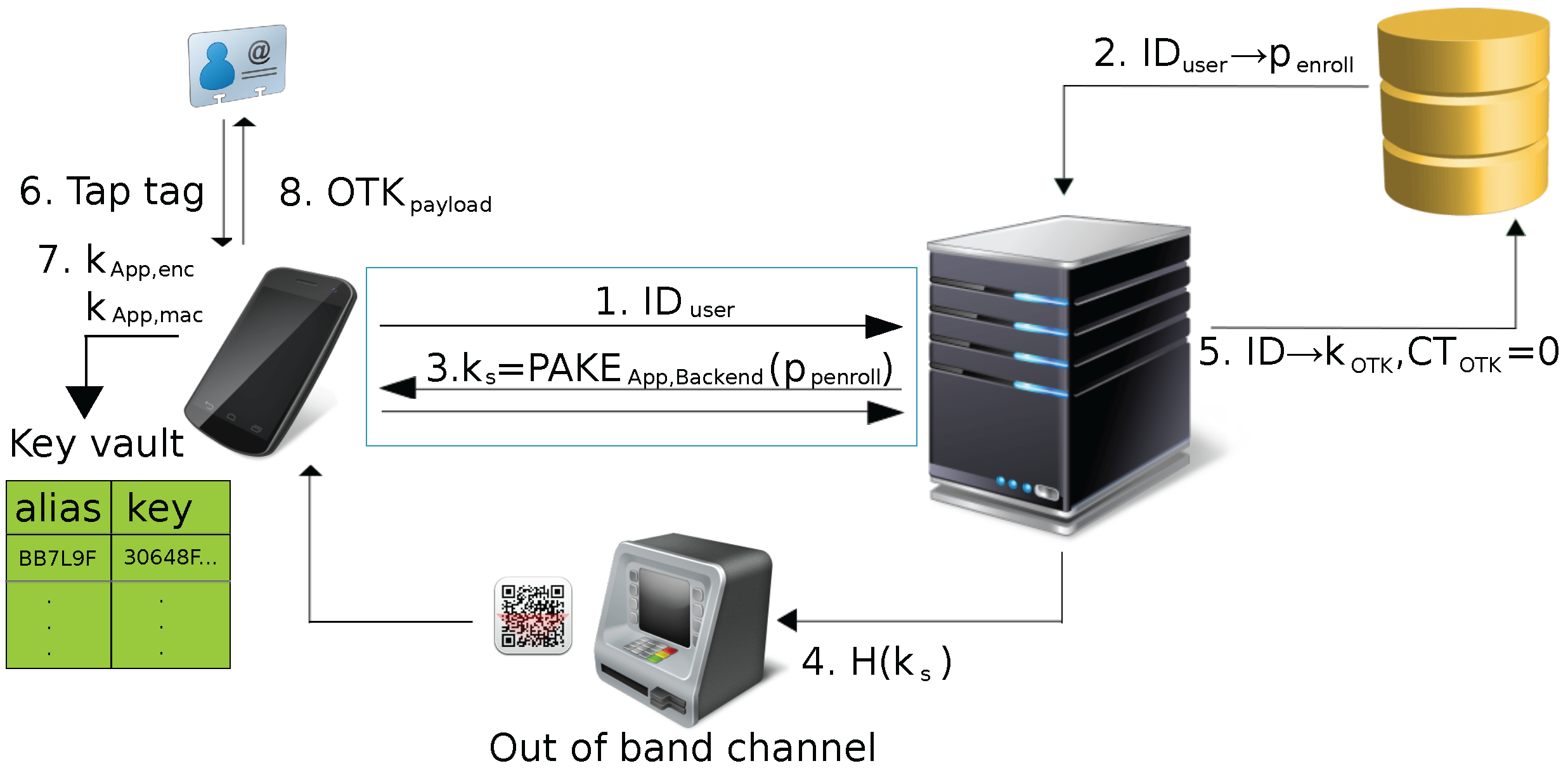
- The app initializes the interaction with the backend server by sending and indicating enrollment of a new tag.
- The backend loads the enrollment password from its user database (based on ) and starts the authentication phase. If no matching is found, the communication with the app is terminated.
- The app and backend perform a password-authenticated key-agreement (e.g., SRP [24]) using as the password.
- We acknowledge that the enrollment password may not be considered sufficiently strong for all application scenarios. For these cases, the authentication phase may be enhanced through an out-of-band channel. Both sides generate a hash over the shared secret . The backend then transmits this hash to the app over the out-of-band channel. The app compares the hashes in order to verify it was communicating directly with the backend server.Such an out-of-band channel could, for instance, be an Automatic Teller Machine (ATM) that displays the hash in the form of a QR code scannable by the app and requests the user to provide the verification result after the user logged in using their bank card and PIN.
- The app and the backend set the key index counter to zero and derive from the session key. The backend stores the one-time key and the initial key index counter in its key database.
- The user taps an NFC tag (after being instructed to do so by the app).
- The app generates new symmetric keys and in its key vault. If the key vault does not support symmetric keys directly, a new asymmetric key pair is generated instead. In that case, random temporary keys and are generated, encrypted using the public key of the key pair in the key vault, and the encrypted version is stored in regular device memory.
- The app constructs the new OTK record (from , the initial key index counter and the one-time key), encrypts it and adds a message authentication code using the symmetric keys from the key vault or the temporary symmetric keys (see (1)–(4) in Section 4.2.1).
4.3. Protecting Touch 2
4.3.1. Tag Memory Layout
- The app reads and (anti-collision identifier) from the tag.
- The app and the backend mutually authenticate using a previously-established session token (which could rely on an application-accessible key vault). While the exact mechanism used for the session token is not relevant for our protocol, we implemented the token as an asymmetric key pair stored in the Android Key Store. The app uses the private key to authenticate sessions, and the backend stores the public key of this key pair during enrollment for verifying the session authentication.
- The app initializes the authentication phase with the backend server by sending and in order to give the server a hint about which user and tag are used to authenticate. Note that needs to also match the session.
- The backend loads and from its key database (based on and ) and starts the tag authentication phase. If no matching key is in the database, communication with the app is ended.
- The backend starts the three-pass mutual AES authentication with the tag by sending appropriate DESFire commands to the app. The app operates as a transparent proxy between the backend and the tag in order to exchange the commands needed for the mutual three-pass authentication.First, the tag generates a random , encrypts it using the shared and returns the cryptogram to the backend. The backend decrypts the received value, generates a random , concatenates that value with a rotated version of the received and sends that concatenated value encrypted with the shared . The tag, in turn, decrypts the received value and verifies to authenticate the backend. Upon successful verification, the tag returns a rotated and encrypted version of . Finally, the backend decrypts the received value and verifies to authenticate the tag.
4.3.2. Protocol Operation
- 6.
- The app reads the file containing the long-term shared secret () and gets its encrypted form (encrypted with the session key shared between the tag and the backend).
- 7.
- The backend also calculates from and . At this point, the app and the backend both know the shared session key .
- 8.
- The app and backend perform an authenticated key-agreement using as the shared key in order to prevent passive attackers spying on the NFC link from using an eavesdropped to decrypt any of the further communication.
- 9.
- After agreeing on a session key , the app and backend continue their communication over a secure channel (authenticated and encrypted based on that agreed session key). The implementation of the secure channel protocol is beyond the scope of this paper.
4.3.3. Initial Tag Enrollment
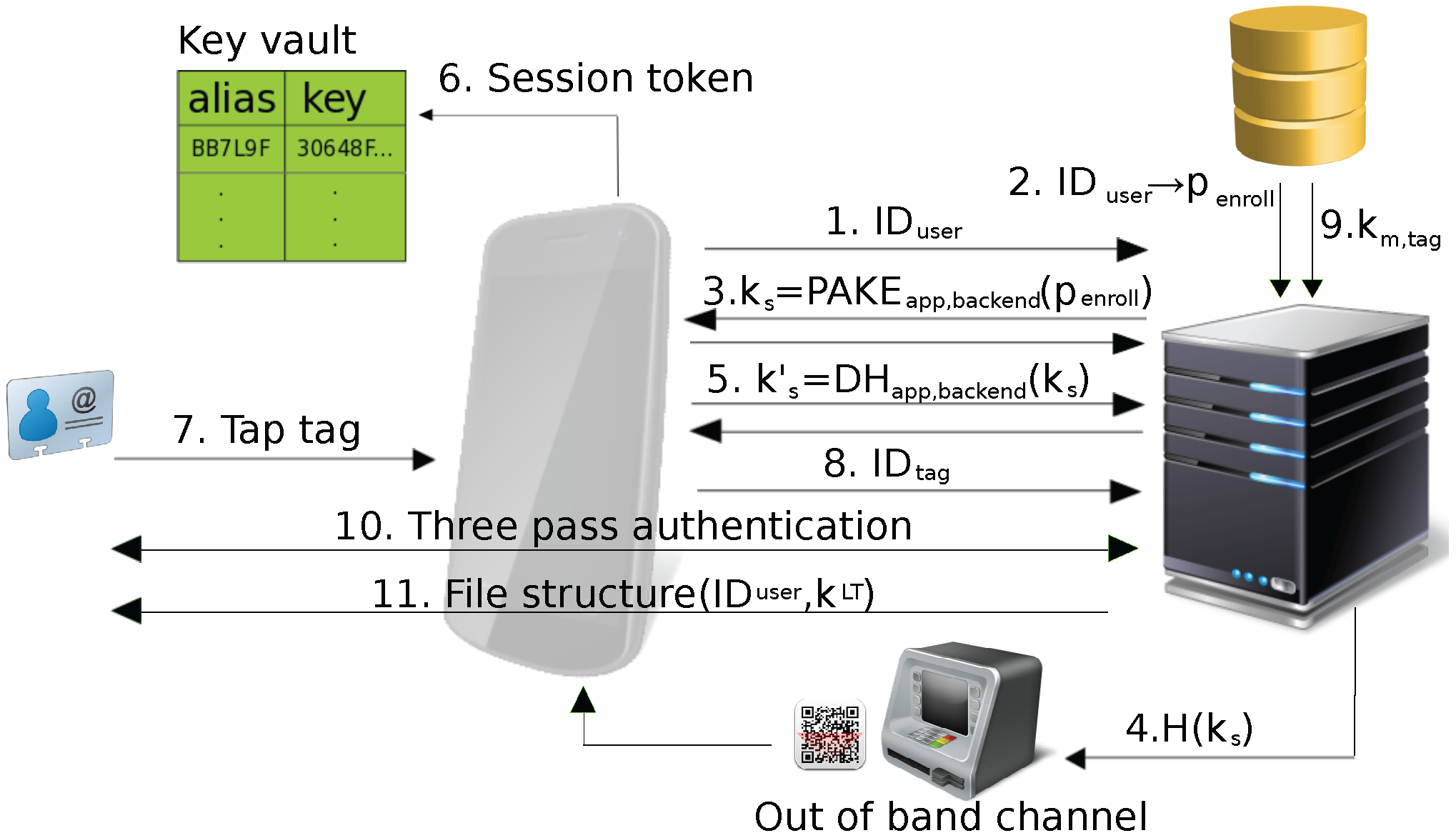
- The app initializes the interaction with the backend server by sending and indicating enrollment of a new tag.
- The backend loads the enrollment password from its user database (based on ) and starts the authentication phase. If no matching is found, communication with the app is terminated.
- The app and backend perform a password-authenticated key-agreement using as the password.
- The same mechanism as in PT1 may be used to perform additional verification over an out-of-band channel (see Section 4.2.3, Step 4).
- If no out-of-band verification is to be performed, the app and backend continue their communication on a secure channel using the session key (proceeding with Step 6). Otherwise, after out-of-band verification, they restart their communication by resending and performing an authenticated key-agreement using as the shared key. The newly established session key is then used for the secure channel. This additional step reduces the risks resulting from key leakage during the (potentially long) period of time it takes to complete out-of-band verification.
- The backend and the app agree on a session token used to authenticate the app installation instance in future communication sessions. While the exact mechanism used for the session token is not relevant for our protocol, we implemented the token as an asymmetric key pair stored in the Android Key Store with the public key stored by the backend (see Step 2 in Section 4.3.2).
- The user taps the DESFire tag (after being instructed to do so by the app).
- The app passes to the backend in order to allow the backend to lookup the pre-shared tag master key in its key database.
- The app then operates as a transparent proxy between the backend and the tag in order to exchange all DESFire commands necessary to configure the tag and its memory contents. This includes initial mutual three-pass authentication using the pre-shared tag master key and the configuration of the DESFire applications including the application-specific key , the file structure, the file data for the file containing , the file data for the file containing and all file access permissions.
4.3.4. Alternative Enrollment Strategies
4.4. Security Analysis
4.4.1. Attacks on the NFC Tag
4.4.2. Attacks on the Client-Side Targeting the User
4.4.3. Attacks on the Client-Side Targeting the Device
4.4.4. Attacks on the App-to-Backend Channel
4.5. Comparison of PT1 and PT2
5. Conclusions and Future Work
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Yan, J.; Blackwell, A.; Anderson, R.; Grant, A. Password Memorability and Security: Empirical Results. IEEE Secur. Priv. 2004, 2, 25–31. [Google Scholar] [CrossRef]
- Greene, K.K.; Gallagher, M.A.; Stanton, B.C.; Lee, P.Y. I Can’t Type That! P@$$w0rd Entry on Mobile Devices. In Human Aspects of Information Security, Privacy, and Trust (HAS 2014); LNCS; Springer: Cham, Switzerland, 2014; Volume 8533. [Google Scholar]
- Schartner, P.; Bürger, S. Attacking mTAN-Applications Like e-Banking and Mobile Signatures; Technical Report, TR-syssec-11-01; University of Klagenfurt: Klagenfurt, Austria, 2011; Available online: https://syssec.at/Publikationen/TR1101.pdf (accessed on 3 July 2017).
- Konoth, R.K.; van der Veen, V.; Bos, H. How Anywhere Computing Just Killed Your Phone-Based Two-Factor Authentication. In Financial Cryptography and Data Security (FC 2016); LNCS; Springer: Berlin, Germany, 2016; Volume, 9603. [Google Scholar]
- FIDO Alliance. FIDO NFC Protocol Specification v1.0, 2015. Implementation Draft. Available online: https://fidoalliance.org/specs/fido-u2f-nfc-protocol-id-20150514.pdf (accessed on 3 July 2017).
- FIDO Alliance. Universal 2nd Factor (U2F) Overview. 2015. Proposed Standard. Available online: https://fidoalliance.org/specs/fido-u2f-overview-ps-20150514.pdf (accessed on 3 July 2017).
- Yubico. YubiKey NEO – Premium Strong Two-Factor Authentication for Secure Logins. Available online: https://www.yubico.com/products/yubikey-hardware/yubikey-neo/ (accessed on 3 July 2017).
- León-Coca, J.M.; Reina, D.G.; Toral, S.L.; Barrero, F.; Bessis, N. Authentication Systems Using ID Cards over NFC Links: The Spanish Experience Using DNIe. Procedia Comput. Sci. 2013, 31, 91–98. [Google Scholar] [CrossRef]
- Horsch, M.; Braun, J.; Wiesmaier, A. Mobile eID Application for the German Identity Card; Technical Report TUD-CS-2011-2918; TU Darmstadt: Darmstadt, Germany, 2011; Available online: http://www.cdc.informatik.tudarmstadt.de/reports/TR/Mobile_eID_app_for_the_German_ID_card.pdf (accessed on 3 July 2017).
- WISeKey. VaultIC150/150D/152. Available online: https://www.wisekey.com/vaultic/secure-solutions/vaultic150-150d-152/ (accessed on 3 July 2017).
- Urien, P. Introducing TLS-PSK authentication for EMV devices. In Proceedings of the International Symposium on Collaborative Technologies and Systems (CTS 2010), Chicago, IL, USA, 17–21 May 2010; pp. 371–377. [Google Scholar]
- Elenkov, N. Dissecting Lollipop’s Smart Lock. Android Explorations Blog. 2014. Available online: http://nelenkov.blogspot.com/2014/12/dissecting-lollipops-smart-lock.html (accessed on 3 July 2017).
- Duc, D.N.; Lee, H.; Konidala, D.M.; Kim, K. Open issues in RFID security. In Proceedings of the International Conference for Internet Technology and Secured Transactions (ICITST 2009), London, UK, 9–12 November 2009; pp. 1–5. [Google Scholar]
- NFC Forum. Type 1 Tag Operation, ver. 1.2. 2014. Technical Specification. Available online: http://nfc-forum.org/our-work/specifications-and-application-documents/specifications/tag-type-technical-specifications/ (accessed on 3 July 2017).
- NFC Forum. Type 2 Tag Operation, ver. 1.2. 2014. Technical Specification. Available online: http://nfc-forum.org/our-work/specifications-and-application-documents/specifications/tag-type-technical-specifications/ (accessed on 3 July 2017).
- NFC Forum. Type 3 Tag Operation, ver. 1.2. 2014. Technical Specification. Available online: http://nfc-forum.org/our-work/specifications-and-application-documents/specifications/tag-type-technical-specifications/ (accessed on 3 July 2017).
- NFC Forum. Type 4 Tag Operation, ver. 2.0. 2011. Technical Specification. Available online: http://nfc-forum.org/our-work/specifications-and-application-documents/specifications/tag-type-technical-specifications/ (accessed on 3 July 2017).
- NFC Forum. Type 5 Tag Operation, ver. 1.0. 2015. Technical Specification. Available online: http://nfc-forum.org/our-work/specifications-and-application-documents/specifications/nfc-forum-technical-specifications/ (accessed on 3 July 2017).
- NFC Forum. NFC Data Exchange Format (NDEF), ver. 1.0. 2006. Technical Specification. Available online: http://nfc-forum.org/our-work/specifications-and-application-documents/specifications/data-exchange-format-technical-specification/ (accessed on 3 July 2017).
- Murdoch, S.J.; Drimer, S.; Anderson, R.; Bond, M. Chip and PIN is Broken. In Proceedings of the IEEE Symposium on Security and Privacy, Berkeley/Oakland, CA, USA, 16–19 May 2010; pp. 433–446. [Google Scholar]
- Shin, S.; Kobara, K.; Imai, H. Leakage-Resilient Authenticated Key Establishment Protocols. In Proceedings of the Advances in Cryptology (ASIACRYPT 2003), 9th International Conference on the Theory and Application of Cryptology and Information Security, Taipei, Taiwan, 30 November–4 December 2003; Springer: Berlin, Germany, 2003; Volume 2894, pp. 155–172. [Google Scholar]
- Sahaa, M.; Roy Chowdhurya, D. Provably secure key establishment protocol using one-way functions. J. Discret. Math. Sci. Cryptogr. 2009, 12, 139–158. [Google Scholar] [CrossRef]
- M’Raihi, D.; Bellare, M.; Hoornaert, F.; Naccache, D.; Ranen, O. HOTP: An HMAC-Based One-Time Password Algorithm. RFC 4226. December 2005. Available online: https://tools.ietf.org/html/rfc4226 (accessed on 3 July 2017).
- Wu, T. The Secure Remote Password Protocol. In Proceedings of the Network and Distributed System Security Symposium (NDSS 1998), San Diego, CA, USA, March 1998; Available online: http://www.isoc.org/isoc/conferences/ndss/98/wu.pdf (accessed on 3 July 2017).
- Oswald, D.; Paar, C. Breaking Mifare DESFire MF3ICD40: Power Analysis and Templates in the Real World. In Proceedings of the Cryptographic Hardware and Embedded Systems (CHES 2011), Nara, Japan, 28 September–1 October 2011; LNCS. Springer: Berlin, Germany, 2011; Volume 6917. [Google Scholar]

| Symbol | Definition |
|---|---|
| Encryption of m using key k | |
| Decryption of c using key k | |
| Message authentication code over m using key k | |
| Authenticated key-agreement between A and B using shared key k based on the principles of Diffie-Hellman key exchange | |
| Password-authenticated key-agreement between A and B using password p | |
| Rotation of x to the left by n bits | |
| x scrambled following a defined scheme | |
| Concatenation of a and b | |
| Random value | |
| Shared key | |
| Public key of asymmetric key pair | |
| Private key of asymmetric key pair |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Carvalho Ota, F.K.; Roland, M.; Hölzl, M.; Mayrhofer, R.; Manacero, A. Protecting Touch: Authenticated App-To-Server Channels for Mobile Devices Using NFC Tags. Information 2017, 8, 81. https://doi.org/10.3390/info8030081
Carvalho Ota FK, Roland M, Hölzl M, Mayrhofer R, Manacero A. Protecting Touch: Authenticated App-To-Server Channels for Mobile Devices Using NFC Tags. Information. 2017; 8(3):81. https://doi.org/10.3390/info8030081
Chicago/Turabian StyleCarvalho Ota, Fernando Kaway, Michael Roland, Michael Hölzl, René Mayrhofer, and Aleardo Manacero. 2017. "Protecting Touch: Authenticated App-To-Server Channels for Mobile Devices Using NFC Tags" Information 8, no. 3: 81. https://doi.org/10.3390/info8030081




