Auction-Based Cloud Service Pricing and Penalty with Availability on Demand
Abstract
:1. Introduction
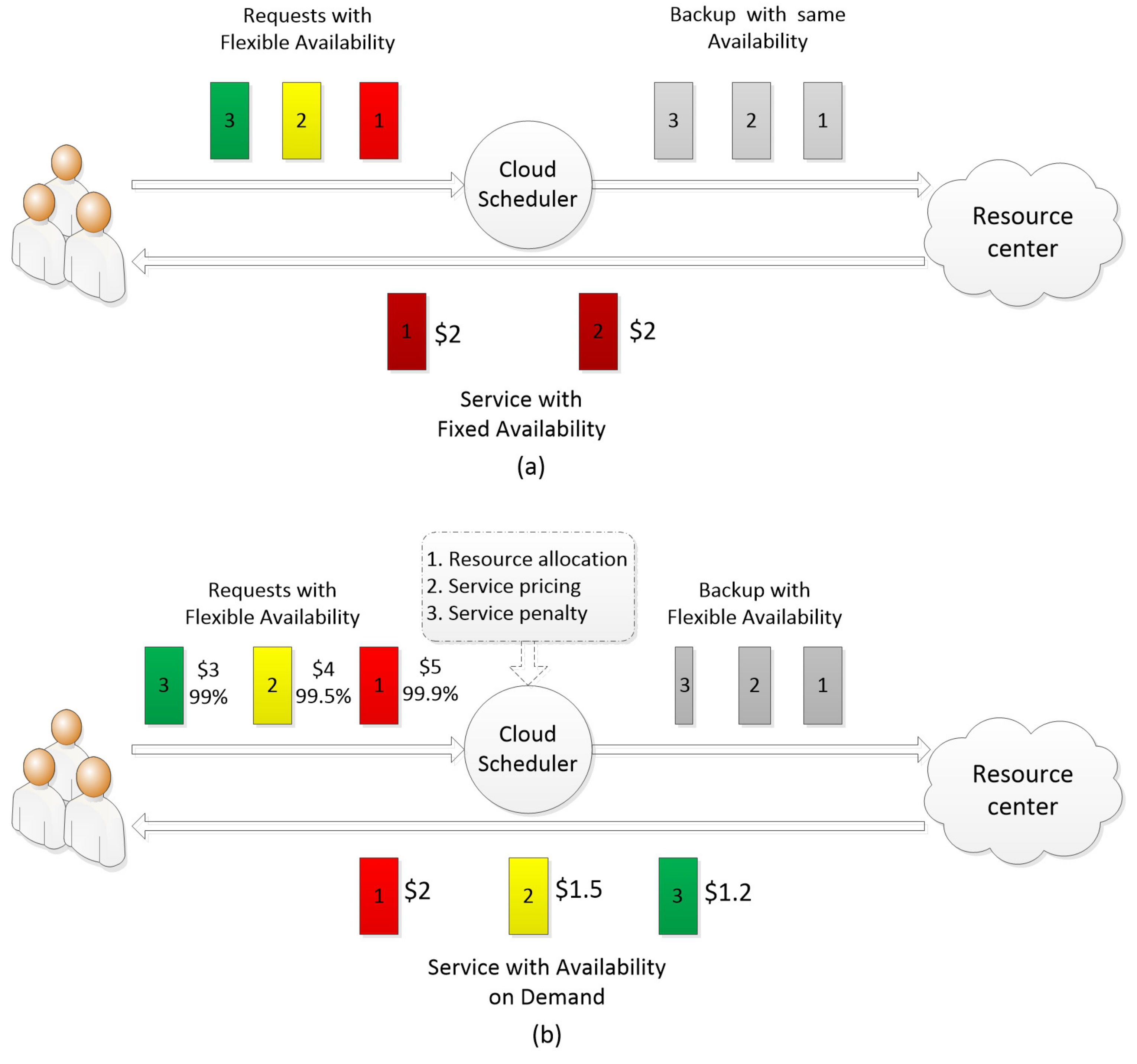
2. System Model
2.1. Availability on Demand and Service Credit
2.2. Description of the Problem
3. Truthful Auction Mechanism with Availability on Demand
3.1. Public Availability
| Algorithm 1: Auction for multi-unit request: HalfGreedy. |
 |
- (i)
- Monotonicity: A bidder who wins with bid keeps winning for any and for any (for any fixed settings of the other bids).
- (ii)
- Critical Payment: A bidder who wins pays the minimum value needed for winning: the minimum of all values such that still wins.
3.2. Private Availability
- With the probability , we run Auction A: Agent with highest value of gets the allocation and needs to pay , where is the user with second highest value of . Obviously, is not higher than the valuation . The service credit for is if the delivered availability is lower than the desired availability .
- With the probability , we run Auction B: according to the value density , we allocate the VMs to the users based on a greedy approach with respect to the value density of users until there is no sufficient capacity, and the payment of each i is , where = is the highest value density with which the user loses the allocation in Auction B. The service credit for user i is if the delivered availability is lower than the desired availability .
| Algorithm 2: Auction for private availability: RandomGreedy. |
 |
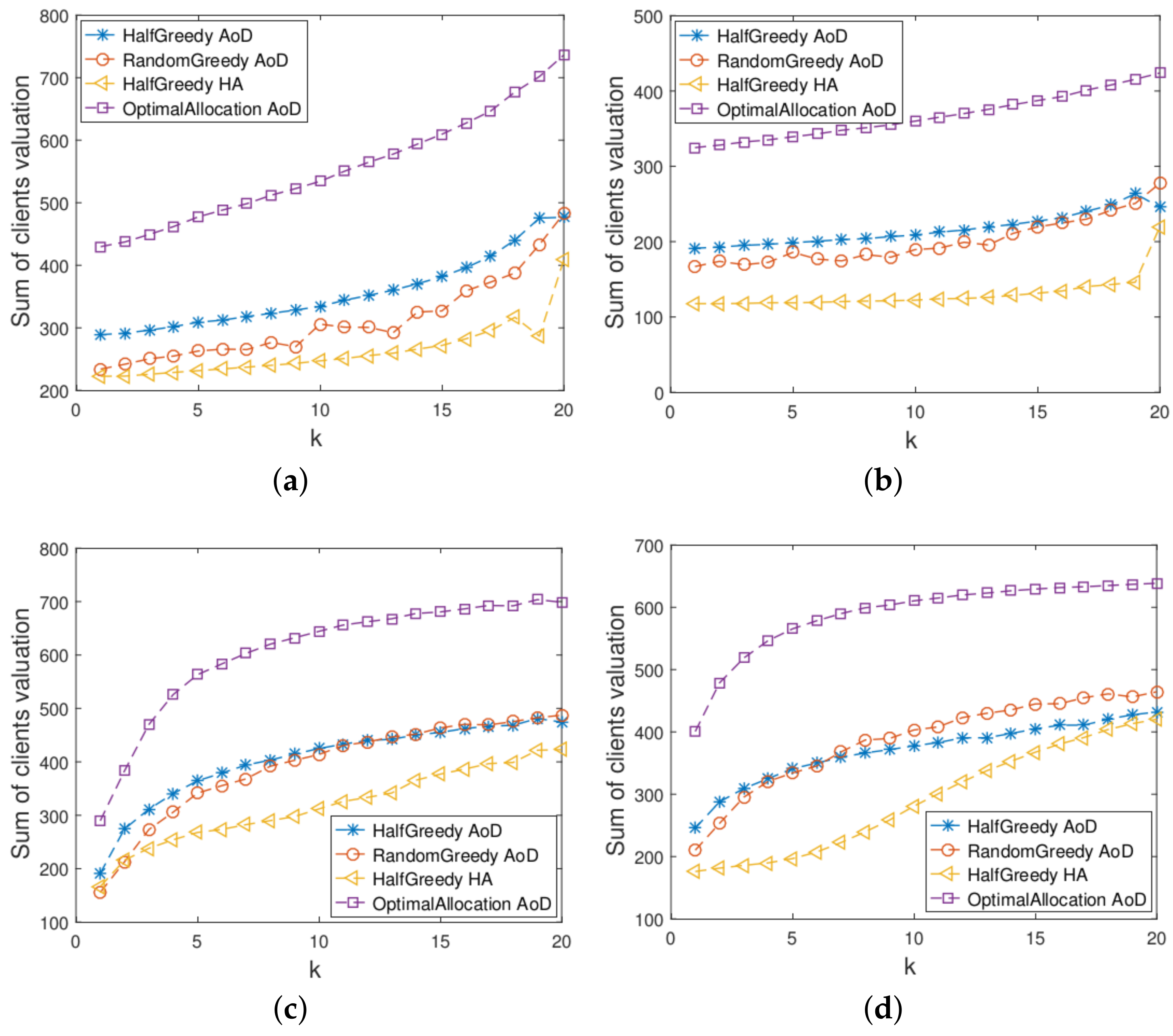
4. Experiment Results
- Half Greedy Auction with availability on demand (HalfGreedy AoD) is our proposed deterministic mechanism, which is a truthful mechanism if the availability is public information or all users are healthy.
- Random Greedy Auction with availability on demand (RandomGreedy AoD) is our proposed nondeterministic mechanism, which is truthful mechanism even if users might be unhealthy.
- Similar to the mechanism proposed by [16], Half Greedy Auction with highest availability (HalfGreedy HA) is the benchmark allocation without considering user-selection availability. Different from HalfGreedy AoD, this allocation provisions the highest availability for all users.
- Optimal allocation with availability on demand (OptimalAllocation AoD) is the benchmark allocation mechanism without considering the strategies of users. Since the optimization problem is a well-known NP-hard problem in this scenario, we obtain a relaxed optimal solution by allowing fraction allocation and using a greedy algorithm.
- No Backup: This option does not use any high availability techniques.
- Random-k Backup: Under this option, the cloud provider will use the Active/Active (AA) technique to improve the availability of the jobs: for each task, it will have a k% (i.e., 30) probability to add an AA backup task that runs for the entire duration of the job (each task corresponds to a virtual machine).
- Active/Active Backup : Under this option, the cloud provider will use the Active/Active (AA) backup for the tasks.
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Shojafar, M.; Canali, C.; Lancellotti, R.; Abawajy, J. Adaptive Computing-plus-Communication Optimization Framework for Multimedia Processing in Cloud Systems. IEEE Trans. Cloud Comput. 2016. [Google Scholar] [CrossRef]
- D’Andreagiovanni, F.; Caire, G. An unconventional clustering problem: User Service Profile Optimization. In Proceedings of the IEEE International Symposium on Information Theory, Barcelona, Spain, 10–15 July 2016; pp. 855–859. [Google Scholar]
- Canali, C.; Chiaraviglio, L.; Lancellotti, R.; Shojafar, M. Joint Minimization of the Energy Costs from Computing, Data Transmission, and Migrations in Cloud Data Centers. IEEE Trans. Green Commun. Netw. 2018. [Google Scholar] [CrossRef]
- Pan, W.; Rowe, J.; Barlaoura, G. Records in the Cloud (RiC) User Survey Report; Rhode Island College: Providence, RI, USA, 2013. [Google Scholar]
- Chan, H.; Chieu, T. An approach to high availability for cloud servers with snapshot mechanism. In Proceedings of the Industrial Track of the Acm/Ifip/Usenix International Middleware Conference, Montreal, QC, Canada, 6–7 December 2012; pp. 1–6. [Google Scholar]
- Cully, B.; Lefebvre, G.; Meyer, D.; Feeley, M.; Hutchinson, N.; Warfield, A. Remus: High Availability via Asynchronous Virtual Machine Replication. In Proceedings of the 5th USENIX Symposium on Networked Systems Design and Implementation (NSDI), San Francisco, CA, USA, 16–18 April 2008; pp. 161–174. [Google Scholar]
- Singh, D.; Singh, J.; Chhabra, A. High Availability of Clouds: Failover Strategies for Cloud Computing Using Integrated Checkpointing Algorithms. In Proceedings of the International Conference on Communication Systems and Network Technologies, Rajkot, India, 11–13 May 2012; pp. 698–703. [Google Scholar]
- Yang, C.T.; Chou, W.L.; Hsu, C.H.; Cuzzocrea, A. On Improvement of Cloud Virtual Machine Availability with Virtualization Fault Tolerance Mechanism. In Proceedings of the IEEE Third International Conference on Cloud Computing Technology and Science, Athens, Greece, 29 November–1 December 2013; pp. 122–129. [Google Scholar]
- Amazon EC2 Service Level Agreement. Available online: https://aws.amazon.com/ec2/sla (accessed on 4 March 2018).
- Google Compute Engine Service Level Agreement. Available online: https://cloud.google.com/compute/sla (accessed on 4 March 2018).
- SLA for Cloud Services. Available online: https://azure.microsoft.com/en-us/support/legal/sla/virtual-machines/v1_6 (accessed on 4 March 2018).
- The UC Berkeley/Stanford Recovery-Oriented Computing (Roc) Project. Available online: http://roc.cs.berkeley.edu/ (accessed on 4 March 2018).
- Shen, S.; Iosup, A.; Israel, A.; Cirne, W.; Raz, D.; Epema, D. An Availability-on-Demand Mechanism for Datacenters. In Proceedings of the IEEE/ACM International Symposium on Cluster, Cloud and Grid Computing, Shenzhen, China, 4–7 May 2015; pp. 495–504. [Google Scholar]
- Shahrad, M.; Wentzlaff, D. Availability Knob: Flexible User-Defined Availability in the Cloud. In Proceedings of the ACM Symposium on Cloud Computing, Shenzhen, China, 4–7 May 2016; pp. 42–56. [Google Scholar]
- Xiaoyong, Y.; Hongyan, T.; Ying, L.; Tong, J.; Tiancheng, L.; Zhonghai, W. A Competitive Penalty Model for Availability Based Cloud SLA. In Proceedings of the IEEE International Conference on Cloud Computing, New York, NY, USA, 27 June–2 July 2015; pp. 964–970. [Google Scholar]
- Mashayekhy, L.; Nejad, M.M.; Grosu, D. Physical Machine Resource Management in Clouds: A Mechanism Design Approach. IEEE Trans. Cloud Comput. 2015, 3, 247–260. [Google Scholar] [CrossRef]
- Wang, C.; Ma, W.; Qin, T.; Chen, X.; Hu, X.; Liu, T. Selling reserved instances in cloud computing. In Proceedings of the International Joint Conference on Artificial Intelligence, Buenos Aires, Argentina, 25–31 July 2015; pp. 224–230. [Google Scholar]
- Bonacquisto, P.; Modica, G.D.; Petralia, G.; Tomarchio, O. A Procurement Auction Market to Trade Residual Cloud Computing Capacity. IEEE Trans. Cloud Comput. 2015, 3, 345–357. [Google Scholar] [CrossRef]
- Toosi, A.N.; Vanmechelen, K.; Khodadadi, F.; Buyya, R. An Auction Mechanism for Cloud Spot Markets. ACM Trans. Auton. Adapt. Syst. 2016, 11, 1–33. [Google Scholar] [CrossRef]
- Zhang, H.; Li, B.; Jiang, H.; Liu, F. A framework for truthful online auctions in cloud computing with heterogeneous user demands. In Proceedings of the 2013 Proceedings IEEE INFOCOM, Turin, Italy, 14–19 April 2013; pp. 1510–1518. [Google Scholar]
- Zhang, X.; Huang, Z.; Wu, C.; Li, Z.; Lau, F.C.M. Online Auctions in IaaS Clouds: Welfare and Profit Maximization with Server Costs. In Proceedings of the ACM SIGMETRICS International Conference on Measurement and Modeling of Computer Systems, Portland, OR, USA, 15–19 June 2015; pp. 3–15. [Google Scholar]
- Toeroe, M.; Tam, F. Service Availability: Principles and Practice; John Wiley and Sons Ltd. Publication: New York, NY, USA, 2012; p. 59. [Google Scholar]
- Nabi, M.; Toeroe, M.; Khendek, F. Availability in the cloud: State of the art. J. Netw. Comput. Appl. 2016, 60, 54–67. [Google Scholar] [CrossRef]
- Nisan, N.; Roughgarden, T.; Tardos, E.; Vazirani, V.V. Algorithmic Game Theory; Cambridge University Press: Cambridge, UK, 2007. [Google Scholar]
- Chekuri, C.; Gamzu, I. Truthful Mechanisms via Greedy Iterative Packing; Springer: Berlin/Heidelberg, Germany, 2009; p. 56. [Google Scholar]
- Fu, S.; Xu, C.Z. Quantifying Temporal and Spatial Correlation of Failure Events for Proactive Management. In Proceedings of the IEEE International Symposium on Reliable Distributed Systems, Beijing, China, 10–12 October 2007; pp. 175–184. [Google Scholar]
- Oppenheimer, D.; Ganapathi, A.; Patterson, D.A. Why Do Internet Services Fail, and What Can Be Done About It? In Proceedings of the Usenix Symposium on Internet Technologies and Systems, Seattle, WA, USA, 26–28 March 2003; pp. 165–171. [Google Scholar]
- Schroeder, B.; Gibson, G.A. A large-scale study of failures in high-performance computing systems. In Proceedings of the International Conference on Dependable Systems and Networks, Philadelphia, PA, USA, 25–28 June 2006; pp. 249–258. [Google Scholar]

| Data Setting | Resource Demand | Availability on Demand | Unit Resource Valuation |
|---|---|---|---|
| DS1 | uniform distribution | uniform distribution | uniform distribution |
| in [1,C/k] | in | in [0,1] | |
| DS2 | uniform distribution | uniform distribution | Gaussian Distribution |
| in [1,C/k] | in | with | |
| DS3 | Exponential Distribution | uniform distribution | uniform distribution |
| in | in [0,1] | ||
| DS4 | Exponential Distribution | uniform distribution | Gaussian Distribution |
| in | with |
| Backup Ratio | Served or Not | Payment | Increased Payment | Service Credit |
|---|---|---|---|---|
| 0.1 | Yes | 82.6717 | 0 | 0 |
| 0.2 | Yes | 89.7892 | 7.1175 | 7.1175 |
| 0.3 | Yes | 99.3982 | 16.7265 | 14.6010 |
| 0.4 | Yes | 106.6987 | 24.0270 | 21.9014 |
| 0.5 | Yes | 117.2437 | 34.5720 | 30.0330 |
| 0.6 | No | 0 | 0 | 0 |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wu, X.; Han, J. Auction-Based Cloud Service Pricing and Penalty with Availability on Demand. Information 2018, 9, 87. https://doi.org/10.3390/info9040087
Wu X, Han J. Auction-Based Cloud Service Pricing and Penalty with Availability on Demand. Information. 2018; 9(4):87. https://doi.org/10.3390/info9040087
Chicago/Turabian StyleWu, Xiaohong, and Jingti Han. 2018. "Auction-Based Cloud Service Pricing and Penalty with Availability on Demand" Information 9, no. 4: 87. https://doi.org/10.3390/info9040087





