Formal Proof of the Dependable Bypassing Routing Algorithm Suitable for Adaptive Networks on Chip QnoC Architecture
Abstract
:1. Introduction and Related Work
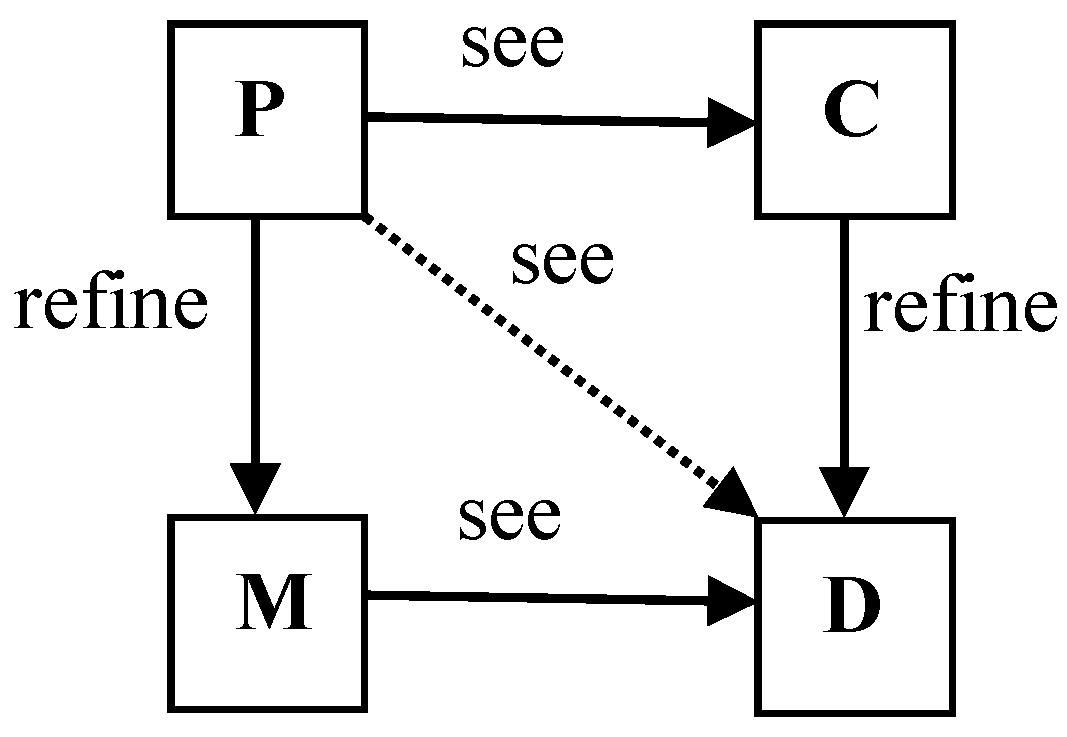
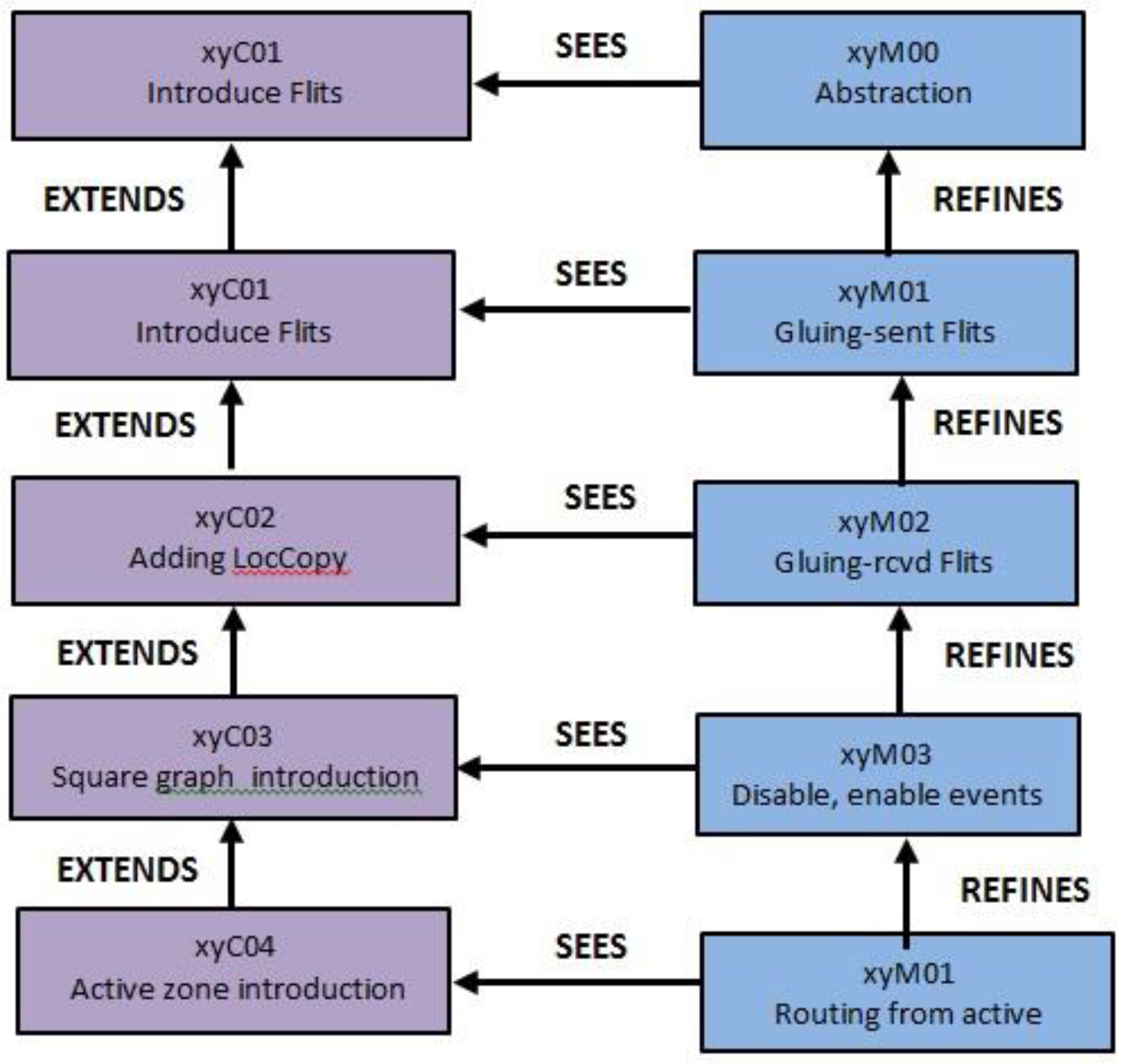
2. Stepwise Specification of the System Using Event-B
2.1. Definition of Event-Band and Proof Obligations
- -
- Contexts, which express the static information about the model.
- -
- Machines, which express dynamic information about the model, invariants, safety properties, and events.
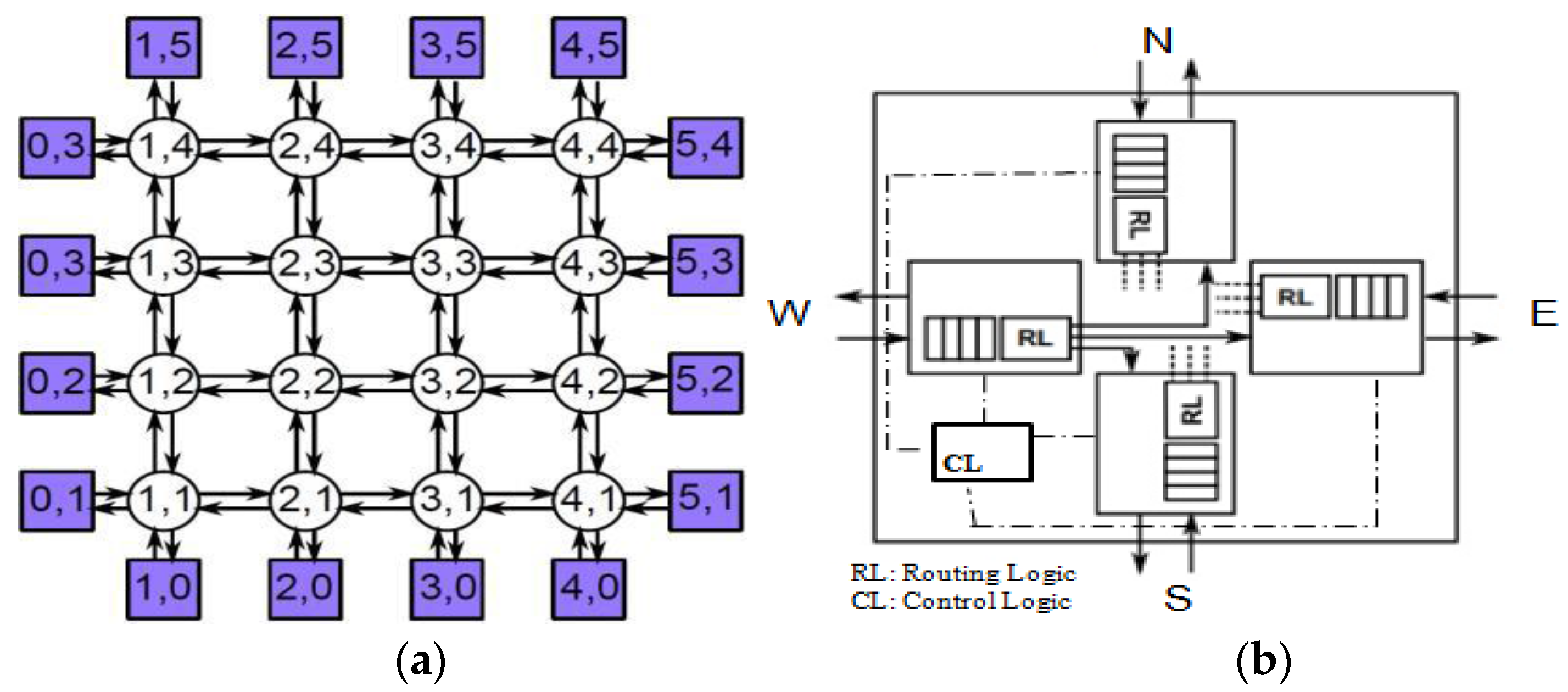
2.2. NoC Architecture Description and Modeling
2.3. NoC Formal Development and Discharge Obligations
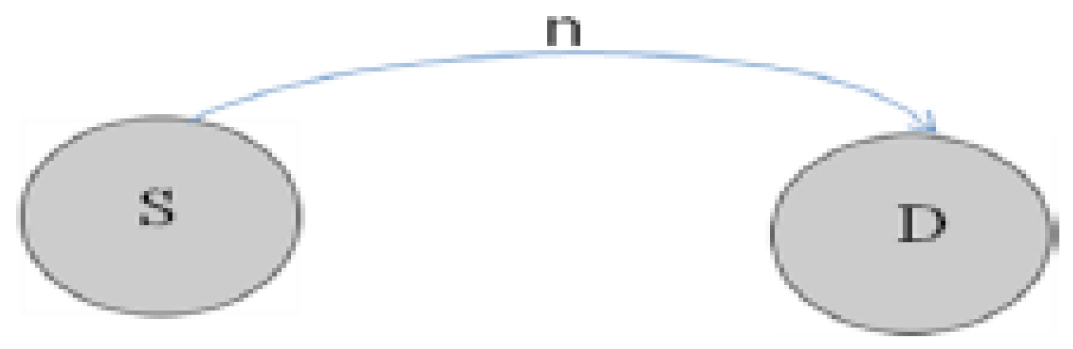
- An event SEND presents the sending of a packet (m), by its source (s), to a switch destination (d).
- An event RECEIVE depicts the receiving of a sent packet (m) by its destination (d).
- Event SEND: When a source sends a packet, it is put in the network.
- Event RECEIVE: A packet is received by its destination, if it has reached the destination.
- Event DISABLE: A node is disabled. The node is not allowed to communicate with its neighbours (failure, etc.). During the disabling of some nodes, we ensure that the packets transiting in the network will eventually reach their destinations (either after a reconfiguration of the network or by always keeping a path to destinations available).
- Event RELINK: This event models the reconfiguration of the network. Disabled nodes are re-enabled: the links between them and their neighbours are restored, therefore allowing communications and packets transfers. The reconfiguration of the network helps in demonstrating the safety of data transmission between a source switch and a destination switch.
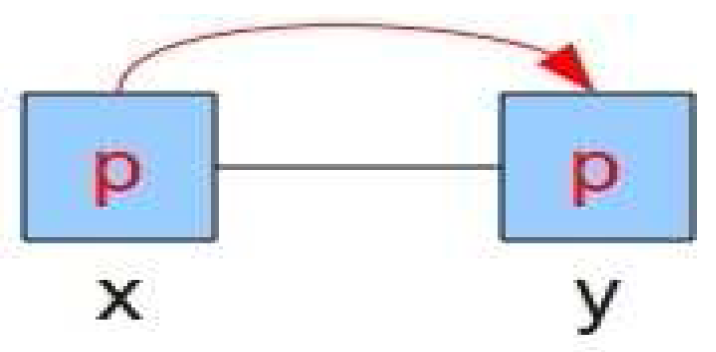
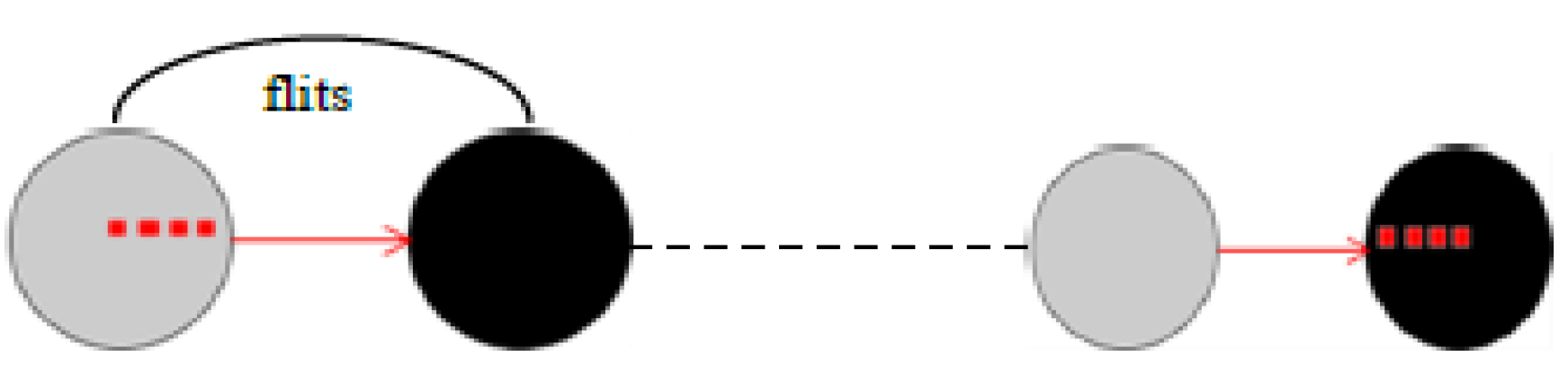
- A refinement of the event FORWARD depicts the passing of a packet (p) from a switch (x) to a channel (ch), leading to a neighbour (y) (see Figure 8).
- An event FROM_CHANNEL_TO_NODE models the transfer of a packet (p) from a channel (ch) to a connected switch (n) (see Figure 8). The machine xyM12 also defines some properties:ran(c) ∩ran(switch) = ∅
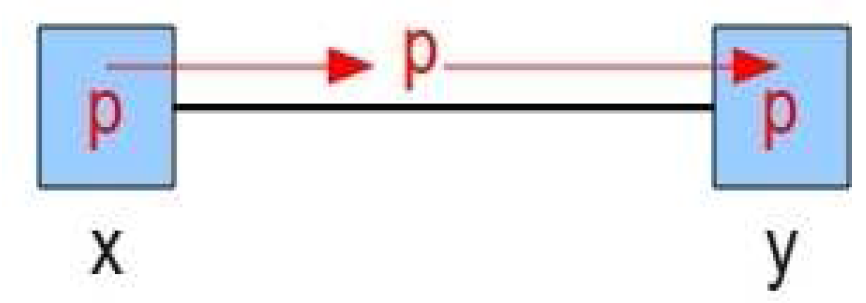
- The refinement of event FORWARD adds the fact that a packet (p), which is leaving a switch (x) and heading for a neighbour (y), first enters the output logic (op) of the switch (x) leading to (y).
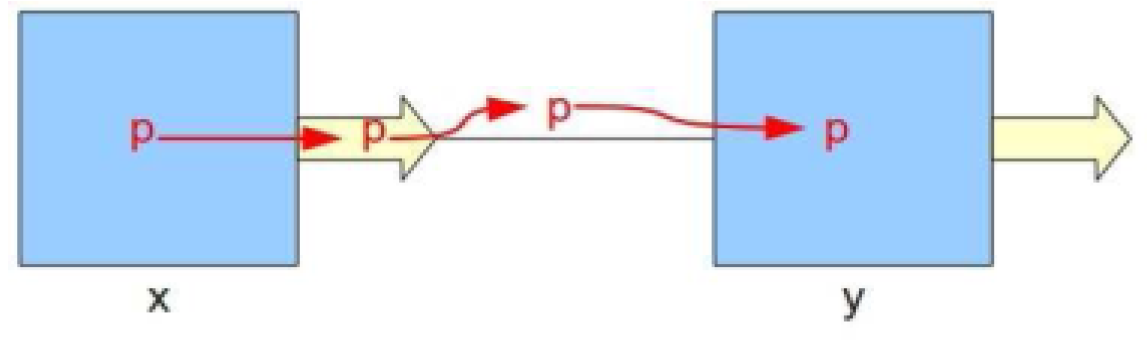
- A new event OUTPUT_BUFFER_TO_CHANNEL models the transition of a packet (p) from an output port (op) to a channel (ch) leading to a target switch (n).
- The event SWITCH_CONTROL, a refinement of FORWARD, models the passing of a packet (p), from an input port (ip) of a switch (x), to an output port (op) leading to a switch (y).
- The event OUTPUT_BUFFER_TO_CHANNEL presents the transition of a packet (p), from an output port (op), to a channel (ch) leading to a target switch (n).
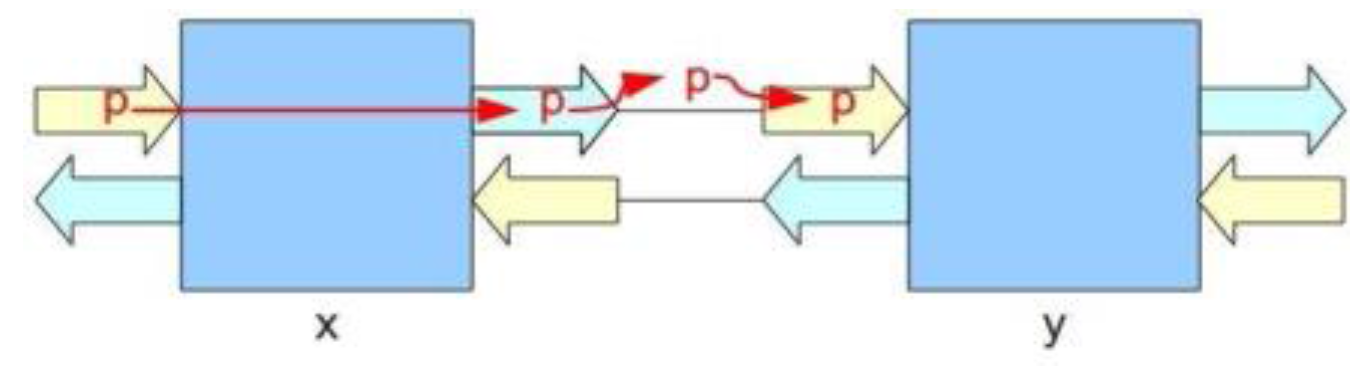
- The event FROM_CHANNEL_TO_INPUT_BUFFER demonstrates the transition of a packet (p) from a channel (ch) to an input port (ip) of a target switch (n).
- -
- The fifth refinement introduces the storage of packets in a switch: each output port of a switch can store a number of packets up to a limit (outputplaces) of three messages. Packets can be blocked in a switch, because of the “wait” or “occupation” signals from the neighbours. The event SWITCH_CONTROL is refined, and adds the fact that, following the transition of a packet from an input port of a switch (x) to an output port, if the switch (x) is not busy anymore, it sends a release signal to the previous switch linked to the input port. A new event RECEIVE_BUFFER_CREDIT models the receiving of a release signal by a switch (n).
- -
- The last model xyM16 describes the architecture of the network (graph): the graph has a mesh topology (see Figure 11). A numerical limit (nsize) is introduced to bound the number of routers in the dimensions x and y of the network topology; the network will be a regular 2D-Mesh, with a size of (nsize × nsize); each switch is coupled with unique coordinates (x; y), with x 2 [0..nsize − 1] and y 2 [0..nsize − 1].
- –
- Boundary switches at the corners only have two output ports and two input ports (N-E, N-W, S-E, and S-W).
- –
- Other boundary switches have three output ports and three input ports (N-S-E, and N-S-W).
- SWITCH_CONTROL_LEFT models Case 1: A packet (p) is transmitted from an input port of a switch (x) to an output port, resulting in a neighbour (y) located at W. This event is triggered if the x-coordinate of the destination (d) (of the packet (p)) is inferior to the x-coordinate of the current node (x).
- SWITCH_CONTROL_RIGHT models Case 2: A packet (p) is transmitted, from an input port of a switch (x), to an output port, leading to a neighbour (y), located at E. This event is triggered if the x-coordinate of the destination (d) (of the packet (p)) is superior to the x-coordinate of the current node (x).
- SWITCH_CONTROL_UP models Case 3: A packet (p) is transmitted, from an input port of a switch (x), to an output port, leading to a neighbour (y), located at N. This event is triggered if the y-coordinate of the destination (d) (of the packet (p)) is superior to the y-coordinate of the current node (x), and either, if the x-coordinate of the destination (d) is equal to the x-coordinate of the current node (x), or if the packet (p) cannot transit along the x-axis.
- SWITCH_CONTROL_DOWN models Case 4: A packet (p) is transmitted, from an input port of a switch (x), to an output port, leading to a neighbour (y), located at S. This event is triggered if the y-coordinate of the destination (d) (of the packet (p)) is inferior to the y-coordinate of the current node (x), and either, if the x-coordinate of the destination (d) is equal to the x-coordinate of the current node (x), or if the packet (p) cannot transit along the x-axis.
2.4. Formal Devlopement of the Proposed Fault Tolerant Routing Algorithm and Discharge Obligations
- Rule 1. All packets in the active region can be routed only along the X-axis.
- Rule 2. An activated node cannot route a packet from North to East side and vice versa.
- Rule 3. An activated node cannot route a packet from South to West side and vice versa.
- Rule 4. All activated nodes cannot route a packet from North to South and vice versa.
2.4.1. Vertex Colouring Algorithms
- -
- -
- Distributed algorithms [42,43,44,45]: These new algorithms involve all vertices of the graph that is coloured and the tops have their own “intelligence”. Usually, they choose their own colours using random probabilities when they have chosen the same colour as their neighbours, and, when they have a good colour, in this case, they withdrew from the uncoloured curve [42,43,44,45]. In this work, we focus on the development of algorithms using distributed techniques. In fact, there is little or no verification of the accuracy of previous algorithms [42,43,44,45] considering some random numbers to define the process of secure coloration.
- -
- Planning graph colouring [46] can be used to control a set of nodes. Two nodes are considered adjacent when they may occur simultaneously. The aim is to prevent adjacent nodes occurring at the same time. However, in our case, there may be two nodes that have the same job but two test nodes cannot fix the failed node at the same time.
- -
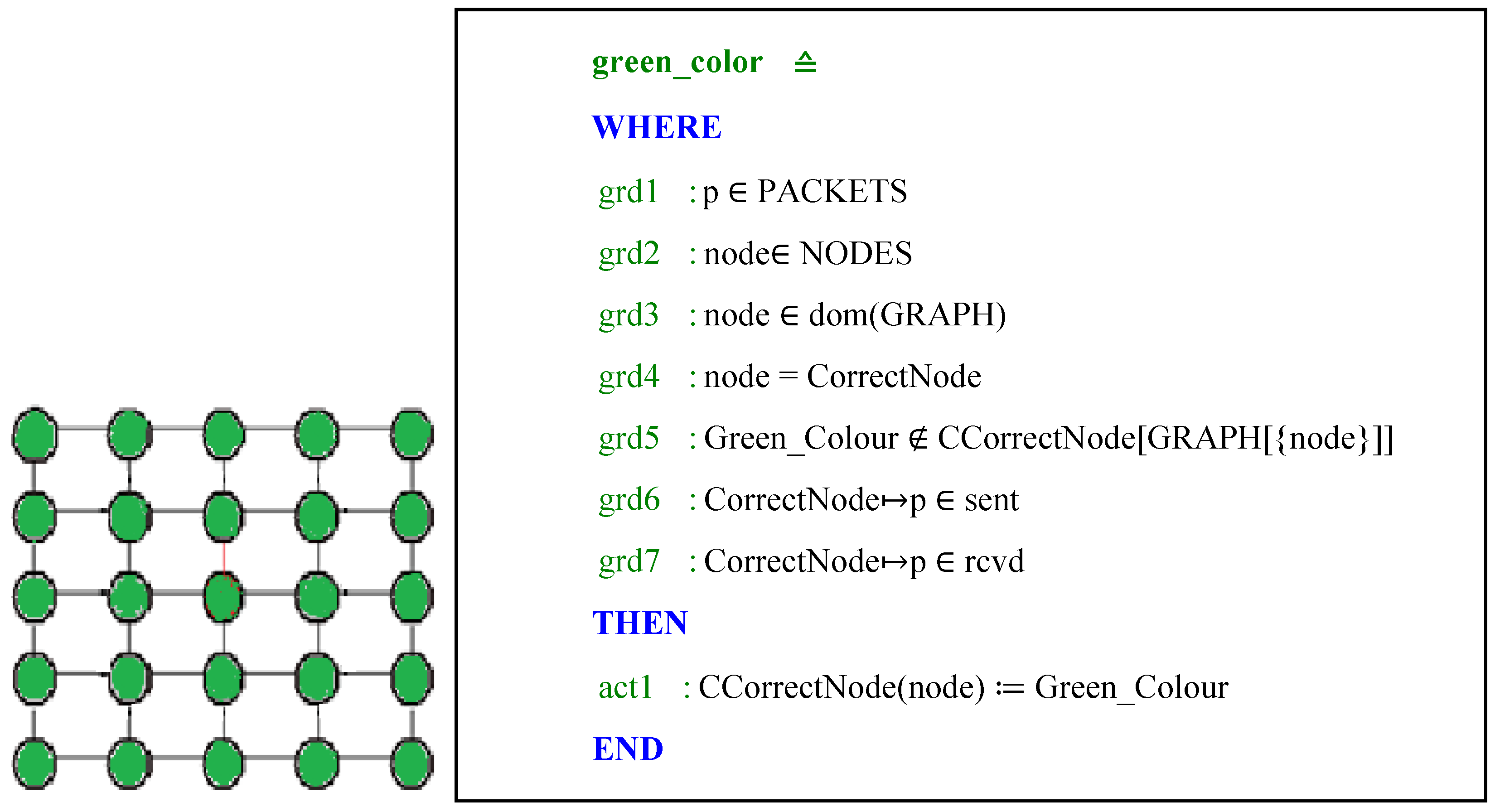
- Each correct node must be coloured in green; a correct node is a node that can send and receive packets.
- -
- Each failed node must be coloured in red; a failed node is a node that cannot send or receive packets or one of the two.
- -
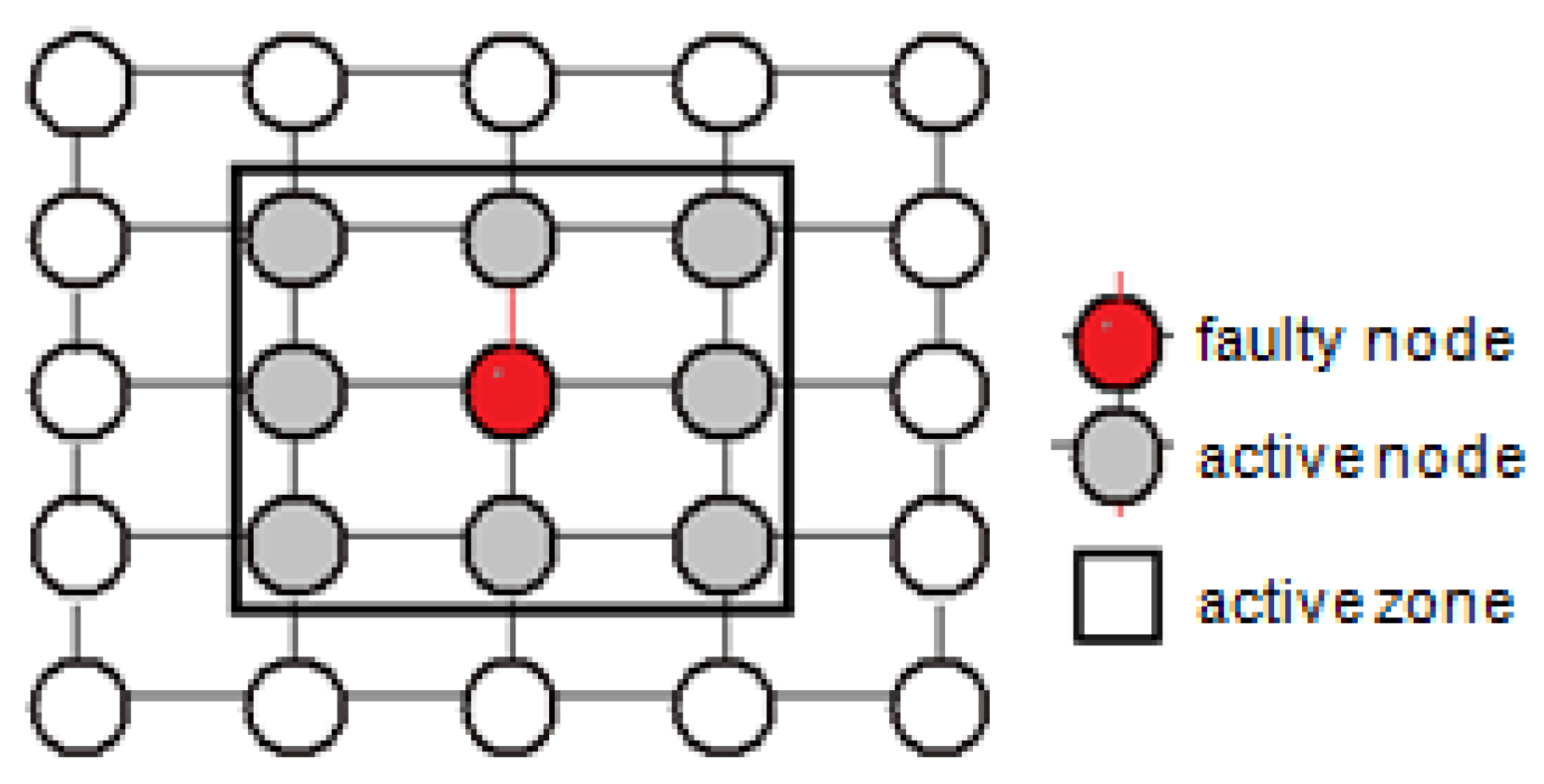
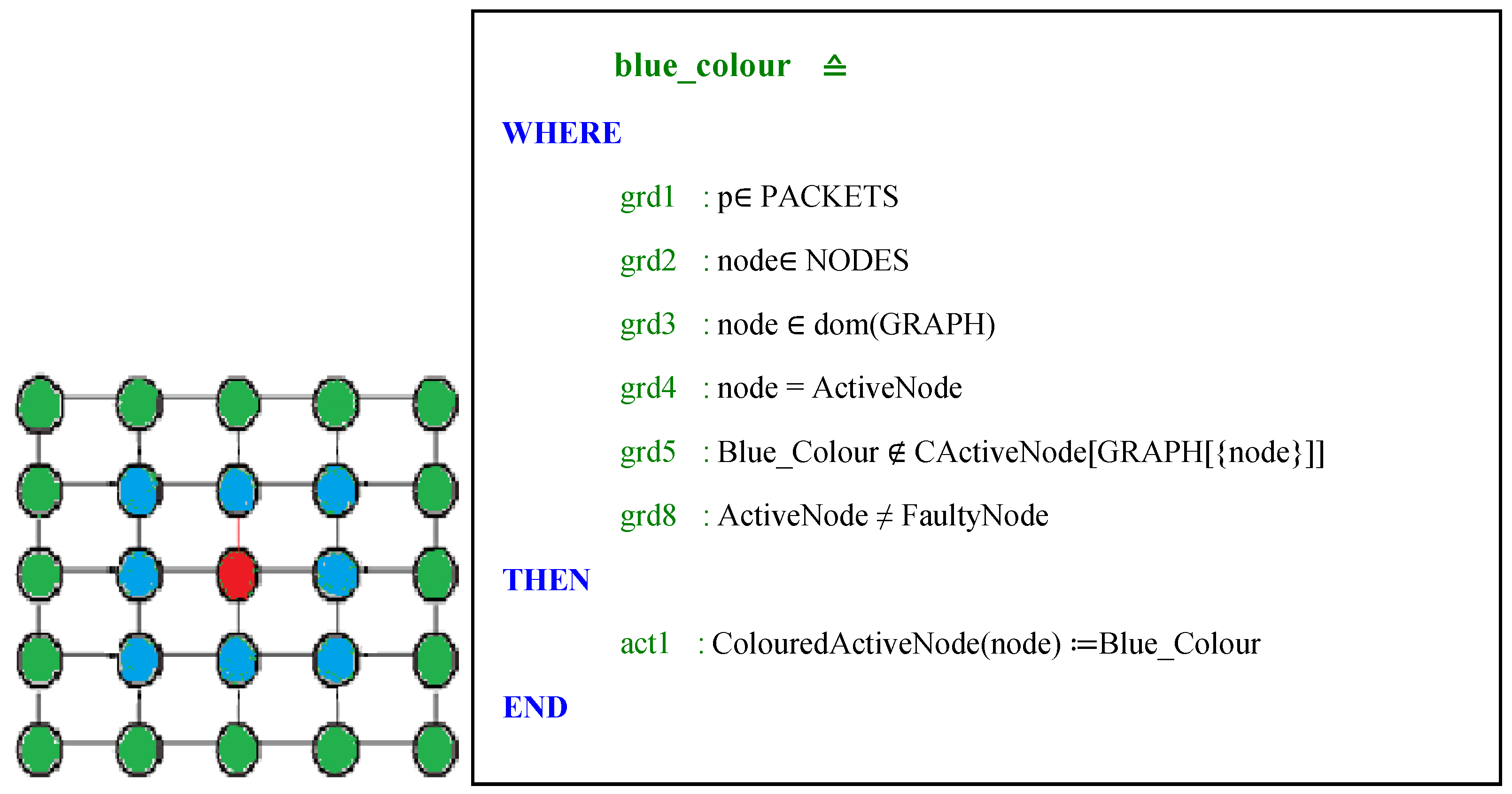
- Each active node must be coloured in blue; an active node is a neighbouring node to a failed node.
2.4.2. Formal Specification of the System


- -
- First refinement: We assume that the graph is given a set of nodes. Next, we define a set of colours (Red_Colour, Green_Colour, and Blue_Colour), whose components are the colours selected by the nodes during the execution of the algorithms of graph colouring. We specify some properties of these constants GRAPH, Green_Colour, Red_Colour and Blue_Colour as follows:
- -
- Axm5 axiom defines that all vertices belong to the GRAPH; they are not isolated.
- -
- Axm6 axiom defines that the graph is irreflexive.
- -
- Axm7 axiom expresses that the graph is symmetric.
- -
- Axm8 axiom expresses that the graph is connected.
- -
- Second refinement: The question turns now about the red colour and we need to find an inductive property which simulates the calculation of this function. Two variables will be added at this level; FaultyNode and CFaultyNode which are defined with the following properties where the FaultyNode is a failed node and coloured in red (see Figure 17):
- -
- Third refinement: In this level, the calculation of the selection function of the active node (see Figure 18) is specified in a simple way to break the complexity of the role of this node:
2.4.3. Formal Development of the Bypassing Routing
- Extension of the definition of the initial graph by adding the concept of square graph. g is the initial graph in which all nodes are connected together since their coordinates (prj1(c), prj2(c)) are neighbours. This is a graph that is part of the eligible graphs.(∀ n1, n2, c1, c2 ·n1 ↦ c1 ∈posnd∧ n2 ↦ c2 ∈ posnd∧ n1 ≠ n2 ∧((prj1(c1) = prj1(c2)−1 ∧ prj2(c1) = prj2(c2)) ∨(prj2(c1) = prj2(c2)−1 ∧ prj1(c1) = prj1(c2)) ∨(prj1(c1) = prj1(c2)+1 ∧ prj2(c1) = prj2(c2)) ∨(prj2(c1) = prj2(c2)+1 ∧ prj1(c1) = prj1(c2)))⇒ n1 ↦ n2 ∈ g)
- Let x be a node x with coordinates cx (posnd(x)). If there is another node with coordinates cd as the axis of the coordinate but which smaller then it can be moved on the x-axis to the left from x.∀ x, cx · x ∈ NODES ∧ cx = posnd(x) ∧(∃ d, cd · d ∈ NODES ∧ cd = posnd(d) ∧ prj1(cx) > prj1(cd))⇒(prj1(cx)−1 ↦ prj2(cx)) ∈ ran(posnd)
- Let x be a node with coordinates cx. If there is a node with coordinates cd as the axis of the coordinate but which are larger than that of the x-axis, then it can be moved to the right from x.∀ x, cx · x ∈ NODES ∧ cx = posnd(x) ∧(∃ d, cd · d ∈ NODES ∧ cd = posnd(d) ∧ prj1(cx) < prj1(cd))⇒(prj1(cx)+1 ↦ prj2(cx)) ∈ ran(posnd)
- g is an initial graph in which all nodes are interconnected in pairs of adjacent coordinates of x and y. This is a graph that is part of the eligible graphs.(∀ n1, n2, c1, c2 ·n1 ↦ c1 ∈posnd∧ n2 ↦ c2 ∈posnd∧ n1 ≠ n2 ∧ n1 ↦ n2 ∈ g⇒ ((prj1(c1) = prj1(c2)−1 ∧ prj2(c1) = prj2(c2)) ∨(prj2(c1) = prj2(c2)−1 ∧ prj1(c1) = prj1(c2)) ∨(prj1(c1) = prj1(c2)+1 ∧ prj2(c1) = prj2(c2)) ∨(prj2(c1) = prj2(c2)+1 ∧ prj1(c1) = prj1(c2))))
- We give the “neighbours” (ind_nbg) diagonal “distance 1” node:ind_nbg ∈ NODES → ℙ(NODES)
- If a node n is part of the faulty area and a node fails new_f_nodef_node, the set_of_f_nodes set is a direct neighbour or diagonal n. Thus, it is part of failing zone around new_f_node.∀ n, r, nod, nd · n ↦ r ∈dom(zn) ∧ nod ∈ r ∧ nd∈ zn(n ↦ r) ∧ (nod ↦nd ∈ g ∨nd ∈ ind_nbg(nod)) ⇒ nod ∈ zn(n ↦ r)
- Theorem: If a node fails f_nodeset_of_f_nodes, all nodes are direct neighbours or diagonal new_f_node. Then, it is part of the defective area new_f_node.∀ n, r, nod · n ↦ r ∈ dom(zn) ∧ nod ∈ r ∧ (n ↦ nod ∈ g ∨ nod ∈ ind_nbg(n)) ⇒ nod ∈ zn(n ↦ r)
- -
- Xmin(b) contains the minimum X coordinate found in b:∀ a, b · b ⊆ NODES ∧ b ≠ ∅∧ a ∈ b ⇒ (∃ c · c ∈ b ∧ prj1(posnd(c)) ≤ prj1(posnd(a)) ∧Xmin(b) = prj1(posnd(c)))
- -
- XMax(b) contains the maximum X coordinate found in b:∀ a, b · b ⊆ NODES ∧ b ≠ ∅∧ a ∈ b ⇒ (∃ c · c ∈ b ∧ prj1(posnd(c)) ≥ prj1(posnd(a)) ∧Xmax(b) = prj1(posnd(c)))
- -
- Ymin(b) contains the minimum Y coordinate found in b:∀ a, b · b ⊆ NODES ∧ b ≠ ∅∧ a ∈ b ⇒ (∃ c · c ∈ b ∧ prj2(posnd(c)) ≤ prj2(posnd(a)) ∧Ymin(b) = prj2(posnd(c)))
- -
- YMax(b) contains the maximum Y coordinate found in b:∀ a, b · b ⊆ NODES ∧ b ≠ ∅∧ a ∈ b ⇒ (∃ c · c ∈ b ∧ prj2(posnd(c)) ≥ prj2(posnd(a)) ∧Ymax(b) = prj2(posnd(c)))
- -
- Lim Xmin(a) contains less than the X coordinate of the bounding rectangle and has Xmin(a) -1 within the graph g:∀ a · a ⊆ NODES ∧ a ≠ ∅∧Xmin(a)−1 > 0 ⇒LimXmin(a) = Xmin(a)−1
- -
- Lim max (a) contains the coordinate of the upper X bounding rectangle and has Xmax (a) if one within the graph g:∀ a · a⊆ NODES ∧ a ≠ ∅∧Xmax(a)+1 < nsize−1 ⇒LimXmax(a) = Xmax(a)+1
- -
- Lim Ymin (a) contains the Y coordinate of the bounding rectangle and has lower Xmin (a) -1 within the graph g:∀ a · a ⊆ NODES ∧ a ≠ ∅ ∧ Ymin(a)−1 > 0 ⇒LimYmin(a) = Ymin(a)−1
- -
- Lim Ymax (a) contains the coordinate of upper rectangle encompassing a Y. Ymax (a) if one within the graph g:∀ a · a ⊆ NODES ∧ a ≠ ∅ ∧ Ymax(a)+1 < nsize−1 ⇒LimYmax(a) = Ymax(a)+1
- -
- The rectangle given by za(a) and including a contains n nodes whose coordinates (x, y) are defined as:LimXmin(a) ≤ x ≤ LimXmax(a) and LimYmin(a) ≤ y ≤ LimYmax(a)axm24 : ∀ a · a ⊆ NODES ∧ a ≠ ∅⇒za(a) = {nd∣ (prj1(posnd(nd)) ≥ LimXmin(a) ∧ prj1(posnd(nd)) ≤ LimXmax(a) ∧ prj2(posnd(nd)) ≥ LimYmin(a) ∧ prj2(posnd(nd)) ≤ LimYmax(a))}
- The routing flits in different directions depending on the destination. If after a node (s) is transmitted flit (f) to the node (y), (x) still has flits of (f), the local copy (LocCopy) does not change and x no longer has flits of (f). The local copy (LocCopy) of packet (p) changes from x to y. This is expressed in the following warning:flits(p) ⊈ (str[{y}] ∪ {f}) ⇒ newLocCopy = locCopyflits(p) ⊆ (str[{y}] ∪ {f}) ⇒ newLocCopy = (locCopy∖ {x ↦ p}) ∪ {y ↦ p}The cases of the XY routing algorithm are matched with refinements of event FORWARD:
- -
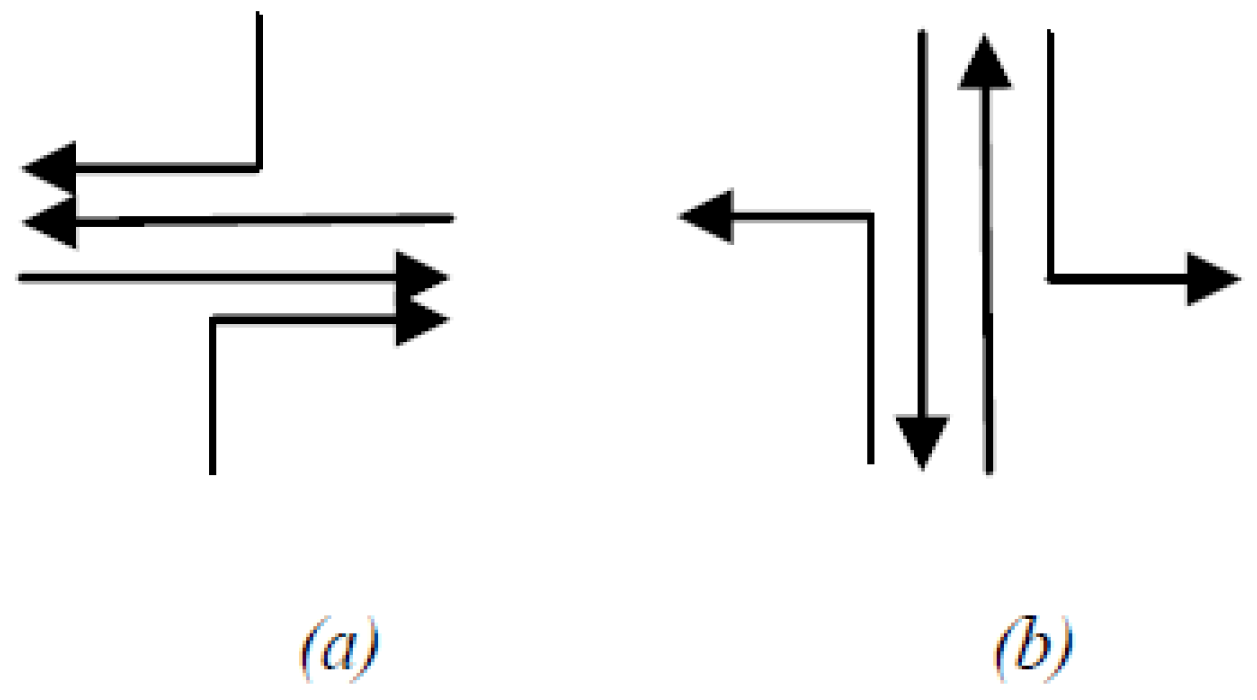
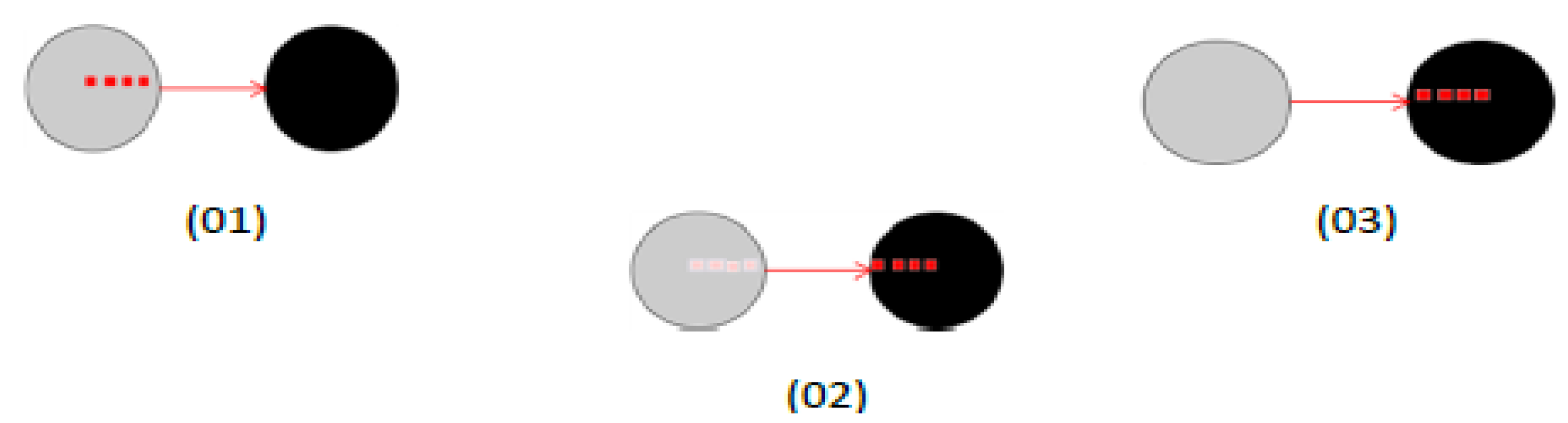
- Case 01: (FORWAD-W) It forwards a flit (f) of a pack (P) to a neighbouring node (y) located W. This event is raised if x-coordinated destination (d) (the flit (f)) is inferior to x-coordinated the current node (s).
- -
- Case 02: (FORWARD-E) It forwards a flit (f) of a pack (P) to a neighbouring node (y) located E. This event is raised if x-coordinated destination (d) (the flit (f)) is superior to x-ordinated the current node (s).
- -
- Case 03: (FORWARD-N) It forwards a flit (f) of a pack (P) to a neighbouring node (y) located in N. This event is triggered if y-coordinated destinations (d) (the flit (f)) is superior to y-coordinated current (x) and x-coordinated the destination node (d) is equal to x-ordinated the current node (s), or if conflicts cannot pass along the x-axis.
- -
- Case 04: (FORWARD-S) It forwards a flit (f) of a pack (P) to a neighbouring node (y) situated S. This event is triggered if y-coordinated destination (d) (the flit (f)) is less than y-coordinated to the current (x) and x-ordinated the destination node (d) is equal to x-ordinated the current node (s), or if conflicts cannot pass along the x-axis.
- The delivery of a flit (f) of the packet (p) from the node (s) in an active zone.
- -
- FORWARD_AUTH1: Can forward a flit (f) a packet (p) to a neighbouring node (y) to the east of the current node (x) knowing that the source node (b) in the south compared to the current node (x) and headed to a destination (d) to the east. With RODIN, this case is expressed as follows:grd14 : b ∈ NODESgrd15 : d ∈ NODESgrd16 : x ≠ dgrd17 : x ∈ z_agrd18 : prj1(posnd(x))< prj1(posnd(d))grd19 : prj2(posnd(y)) = prj2(posnd(x))grd20 : prj1(posnd(y)) = prj1(posnd(x))+1grd21 : prj2(posnd(b))< prj2(posnd(x))grd22 : prj1(posnd(x)) = prj1(posnd(b))grd23 : b=src(p)
- -
- FORWARD_AUTH2: Can forward a flit (f) and a packet (p) to a neighbouring node (y) to the right of the current (x) node knowing the source node (b) to the West relative to the current node (x) and headed to a destination (d) to the east. With RODIN, this case is expressed as as follows:grd20 : prj1(posnd(y)) = prj1(posnd(x))+1grd21 : prj2(posnd(b))= prj2(posnd(x))grd22 : prj1(posnd(b)) = prj1(posnd(x)) -1
- -
- FORWARD_AUTH3: Can forward a flit (f) and a packet (p) to a neighbouring node (y) to the West of the current (x) node knowing the source node (b) is located in relation to node current (x) and headed to a destination (d) to the west. With RODIN, this case is expressed as follows:grd18 : prj1(posnd(x))> prj1(posnd(d))grd19 : prj2(posnd(y)) = prj2(posnd(x))grd20 : prj1(posnd(y)) = prj1(posnd(x))-1grd21 : prj2(posnd(b))= prj2(posnd(x))grd22 : prj1(posnd(b)) = prj1(posnd(x)) +1
- -
- FORWARD_AUTH4: Can forward a flit (f) and a packet (p) to a neighbouring node (y) to the West of the current (x) node knowing the source node (b) to the east from the node current (x) and headed to a destination (d) to the west. With RODIN, this case is expressed as follows:grd18 : prj1(posnd(x))> prj1(posnd(d))grd19 : prj2(posnd(y)) = prj2(posnd(x))grd20 : prj1(posnd(y)) = prj1(posnd(x))-1grd21 : prj2(posnd(b))> prj2(posnd(x))grd22 : prj1(posnd(b)) = prj1(posnd(x))
3. Discussion
4. Conclusions and Future Work
Author Contributions
Conflicts of Interest
References
- Killian, C.; Tanougast, C.; Monteiro, F.; Dandache, A. Smart Reliable Network-on-Chip. IEEE Trans. Very Large Scale Integr. Syst. 2014, 22, 242–255. [Google Scholar] [CrossRef]
- Leonidas, T.; Sere, K.; Plosila, J. Modeling Communication in Multi–Processor Systems–on–Chip Using Modular Connectors. Innovations in Embedded and Real-Time Systems Engineering for Communication. IGI Glob. 2012, 219–240. [Google Scholar] [CrossRef]
- Guang, L.; Plosila, J.; Isoaho, J.; Tenhunen, H. Hierarchical Agent Monitored Parallel On-Chip System: A Novel Design Paradigm and Its Formal Specification. In Innovations in Embedded and Real-Time Systems Engineering for Communication; IGI Publishing: Hershey, PA, USA, 2010; pp. 86–105. [Google Scholar]
- Ostroumov, S.; Tsiopoulos, L.; Plosila, J.; Sere, K. Formal approach to agent-based dynamic reconfiguration in Networks-On-Chip. J. Syst. Archit. 2013, 59, 709–728. [Google Scholar] [CrossRef]
- Verbeek, F.; Schmaltz, J. Easy Formal Specification and Validation of Unbounded Networks-on-Chips Architectures. ACM Trans. Design Autom. Electron. Syst. 2012, 17. [Google Scholar] [CrossRef]
- Borrione, D.; Helmy, A.; Pierre, L.; Schmaltz, J. A Formal Approach to the Verification of Networks on Chip. EURASIP J. Embed. Syst. 2009, 2009, 548324. [Google Scholar] [CrossRef]
- Aydi, Y.; Tligue, R.; Elleuch, M.; Abid, M.; Dekeyser, J. A Multi Level Functional Verification of Multistage Interconnection Network for MPSOC. In Proceedings of the 16th IEEE International Conference on Electronics, Circuits, and Systems, Yasmine Hammamet, Tunisia, 13–16 December 2009; pp. 439–442. [CrossRef]
- Van den Broek, T.; Schmaltz, J. Towards A Formally Verified Network-on-Chip. In Proceedings of the 2009 Formal Methods in Computer-Aided Design, (FMCAD 2009), Austin, TX, USA, 15–18 November 2009; pp. 184–187.
- Schmaltz, J.; Borrione, D. A functional formalization of on chip communications. Form. Asp. Comput. 2008, 20, 241–258. [Google Scholar] [CrossRef]
- Voros, J.; Snook, C.; Hallerstede, S.; Masselos, K. Embedded System Design Using Formal Model Refinement: An Approach Based on the Combined Use of UML and the B Language. Design Autom. Embed. Syst. 2004, 9, 67–99. [Google Scholar] [CrossRef]
- Laibinis, L.; Troubitsyna, E.; Leppänen, S. Service-Oriented Development of Fault Tolerant Communicating Systems: Refinement Approach. Int. J. Embed. Real-Time Commun. Syst. 2010, 1, 61–85. [Google Scholar] [CrossRef]
- Verbeek, F.; Schmaltz, J. Formal Specification of Networks-on-Chips:Deadlock and Evacuation. In Proceedings of the Design, Automation Test Europe Conference & Exhibition, Dresden, Germany, 8–12 March 2010; pp. 1701–1706.
- Helmy, A.; Pierre, L.; Jantsch, A. Theorem Proving Techniques for the Formal Verification of NoC Communications with Non-minimal Adaptive Routing. In Proceedings of the IEEE 13th International Symposium on Design and Diagnostics of Electronic Circuits and Systems, Vienna, Austria, 14–16 April 2010; pp. 221–224.
- Yang, S.-A.; Baras, J.S. Correctness Proof for a Dynamic Adaptive Routing Algorithm for Mobile Ad-hoc Networks. In IFAC Workshop—Modeling and Analysis of Logic Controlled Dynamic Systems; Elsevier: New York, NY, USA, 2003; pp. 1–10. [Google Scholar]
- Wu, J. A fault-tolerant and deadlock-free routing protocol in 2D meshes based on odd-even turn model. IEEE Trans. Comput. 2003, 52, 1154–1169. [Google Scholar]
- Park, D.; Nicopoulos, C.; Kim, J.; Vijaykrishnan, N.; Das, C. Exploring fault-tolerant network-on-chip architectures. In Proceedings of the International Conference on Dependable Systems and Networks (DSN 2006), Philadelphia, PA, USA, 25–28 June 2006; pp. 93–104.
- Cansell, D.; Tanougast, C.; Beviller, Y. Integration of the proof process in the design of microelectronic architecture for bitrate measurement instrumentation of transport stream program MPEG-2 DVB-T. In Proceedings of the IEEE International Workshop on Rapid System Prototyping, Geneva, Switzerland, 28–30 June 2004; pp. 157–163.
- Leavens, G.T.; Abrial, J.-R.; Batory, D.S.; Butler, M.J.; Coglio, A.; Fisler, K.; Hehner, E.C.R.; Jones, C.B.; Miller, D.; Jones, S.L.P.; et al. Roadmap for enhanced languages and methods to aid verification. In Proceedings of the 5th International Conference on Generative Programming and Component Engineering, Portland, OR, USA, 22–26 October 2006; Jarzabek, S., Schmidt, D.C., Veldhuizen, T.L., Eds.; ACM: New York, NY, USA, 2006; pp. 221–236. [Google Scholar]
- Abrial, J.-R.; Cansell, D.; Mery, D. A mechanically proved and incremental development of IEEE 1394 tree identify protocol. Form. Asp. Comput. 2003, 14, 215–227. [Google Scholar] [CrossRef]
- Clarke, E.M.; Grumberg, O.; Jha, S. Verifying parameterzed networks. ACM Trans. Program. Lang. Syst. 1997, 19, 726–750. [Google Scholar] [CrossRef]
- Bharadwaj, R.; Felty, A.; Stomp, F. Formalizing Inductive Proofs of Network Algorithms. In Proceedings of the 1995 Asian Computing Science Conference, Springer-Verlag, London, UK, 11–13 December 1995.
- Curzon, P. Experiences formally verifying a network component. In Proceedings of the IEEE Conference on Computer Assurance, Gaithersburg, MD, USA, 27 June–1 July 1994.
- Gordon, M.; Melham, T. Introduction to HOL: A Theorem Proving Environment for Higher Order Logic; Cambridge University Press: Cambridge, UK, 1993. [Google Scholar]
- Chenard, J.S.; Bourduas, S.; Azuelos, N.; Boul’e, M.; Zilic, Z. Hardware Assertion Checkers in On-line Detection of Network-on-Chip Faults. In Proceedings of the Desig Automation and Test in Europe, Worshop on Diagnostic Services in Networks-on-Chips, Nice, France, 16–20 April 2007.
- IEEE. IEEE Standard for Property Specification Language (PSL). IEEE STD 1850. Available online: http://ieeexplore.ieee.org/document/1524461/ (accessed on 20 February 2017).
- Boule, M.; Zilic, Z. Automata-based assertion-checker synthesis of PSL properties. ACM Trans. Des Autom. Electron. Syst. 2008, 13, 1–21. [Google Scholar] [CrossRef]
- Clarke, E.M., Jr.; Grumberg, O.; Peled, D.A. Model Cheking; The MIT Press: Cambridge, MA, USA; London, UK, 1999; p. 6. [Google Scholar]
- Ogras, U.; Hu, J.; Marculescu, R. Key Research Problems in NoC Design: A Holistic Perspective. In Proceedings of the International Conference on Hardware/Software Codesign and System Synthesis (CODES+ISSS′2005), New York, NY, USA, 18–21 September 2005; pp. 69–74.
- Goossens, K. Formal Methods for Networks on Chips. In Proceedings of the Fifth International Conference on Application of Concurrency to System Design (ACSD′05), Saint Malo, France, 7–9 June 2005; IEEE Computer Society: Washington, DC, USA, 2005; pp. 188–189. [Google Scholar]
- Pande, P.; De Micheli, G.; Grecu, C.; Ivanov, A.; Saleh, R. Design, Synthesis, and Test of Networks on Chips. IEEE Design Test Comput. 2005, 22, 404–413. [Google Scholar] [CrossRef]
- Bjerregaard, T.; Mahadevan, S. A survey of research and practices of Network-on-chip. ACM Comput. Surv. 2006, 38, 1–51. [Google Scholar] [CrossRef]
- Jantsch, A. Models of Computation for Networks on Chip. In Proceedings of the Sixth International Conference on Application of Concurrency to System Design (ACSD′06), Turku, Finland, 28–30 June 2006; IEEE Computer Society: Washington, DC, USA, 2006; pp. 165–178. [Google Scholar]
- Nielsen, S.F.; Sparso, J. Analysis of low-power SoC interconnection networks. In Proceedings of the IEEE 19th Norchip Conference, Kista, Sweden, 12–13 November 2001; pp. 77–86.
- Grecu, C.; Ivanov, A.; Saleh, R.; Sogomonyan, E.; Pande, P. On-line Fault Detection and Location for NoC Interconnects. In Proceedings of the International On-Line Testing Symposium (IOLTS′06), Lake of Como, Italy, 10–12 July 2006; pp. 1–8.
- Murali, S.; De Micheli, G.; Benini, L.; Theocharides, T.; Vijaykrishnan, N.; Irwin, M.J. Analysis of Error Recovery Schemes for Networks on Chips. IEEE Design Test Comput. 2005, 22, 434–442. [Google Scholar] [CrossRef]
- Schafer, M.; Hollstein, T.; Zimmer, H.; Glesner, M. Deadlock-free routing and Component placement for irregular mesh-based networks-on-chip. In Proceedings of the 2005 IEEE/ACM International Conference on Computer-Aided Design (ICCAD′05), San Jose, CA, USA, 6–10 November 2005; IEEE Computer Society: Washington, DC, USA, 2005; pp. 238–245. [Google Scholar]
- Gebremichael, B.; Vaandrager, F.W.; Zhang, M.; Goossens, K.; Rijpkema, E.; Radulescu, A. Deadlock Prevention in the Æthereal protocol. In Proceedings of the 13th IFIP WG 10.5 Advanced Research Working Conference on Correct Hardware Design and Verification Methods (CHARME′05), Saarbrücken, Germany, 3–6 October 2005.
- Bendisposto, J.; Leuschel, M.; Ligot, O.; Samia, M. La validation de modèles Event-B avec le plug-in ProB pour RODIN. TSI 2008, 27, 1065–1084. [Google Scholar] [CrossRef]
- Sayar, I.; Bhiri, M.-T. From an abstract specification in event-B toward an UML/OCL model. In Proceedings of the 2nd FME Workshop on Formal Methods in Software Engineering (FormaliSE 2014), Hyderabad, India, 3 June 2014; pp. 17–23.
- Jastram, M. (Ed.) RODIN User’s Handbook. Sponsored by the Deploy Project. 2012. Available online: https://www3.hhu.de/stups/handbook/rodin/current/pdf/rodin-doc.pdf (accessed on 20 February 2017).
- Andriamiarina, M.B.; Daoud, H.; Belarbi, M.; Méry, D.; Tanougast, C. Formal verification of fault tolerant NoC-based architecture. In Proceedings of the First International Workshop on Mathematics and Computer Science (IWMCS 2012), Tiaret, Algeria, 16–17 December 2012.
- Métivier, Y.; Robson, J.M.; Saheb-Djahromi, N.; Zemmari, A. Brief Annoucement: Analysis of an Optimal Bit Complexity Randomised Distributed Vertex Colouring Algorithm (Extended Abstract). In Proceedings of 13th International Conference on Principles of Distributed Systems (OPODIS 2009), Nîmes, France, 15–18 December 2009; pp. 359–364.
- Duffy, K.; O’Connell, N.; Sapozhnikov, A. Complexity analysis of a decentralised graph colouring algorithm. Inf. Process. Lett. 2008, 107, 60–63. [Google Scholar] [CrossRef]
- Nickerson, B.R. Graph colouring register allocation for processors with multi-register operands. In Proceedings of the ACM SIGPLAN 1990 Conference on Programming Language Design and Implementation (PLDI′90), White Plains, NY, USA, 20–22 June 1990; ACM: New York, NY, USA; pp. 40–52.
- Schneider, J.; Wattenhofer, R. Anew technique for distributed symmetry breaking. In Proceedings of the 29th ACM SIGACT-SIGOPS Symposium on Principles of Distributed Computing (PODC′10), Zurich, Switzerland, 25–28 July 2010; ACM: New York, NY, USA; pp. 257–266.
- Malkawi, M.; Hassan, M.A.-H.; Hassan, O.A.-H. Anew exam scheduling algorithm using graph coloring. Int. Arab J. Inf. Technol. 2008, 5, 80–86. [Google Scholar]






| Model | Total | Auto | Interactive | ||
|---|---|---|---|---|---|
| xyC0 | 3 | 3 | 100% | 0 | 0% |
| xyC1 | 6 | 6 | 100% | 0 | 0% |
| xyC12 | 0 | 0 | 100% | 0 | 0% |
| xyC13 | 0 | 0 | 100% | 0 | 0% |
| xyC14 | 1 | 1 | 100% | 0 | 0% |
| xyC15 | 5 | 0 | 0% | 5 | 100% |
| xyM0 | 26 | 25 | 96.15% | 1 | 3.85% |
| xyM1 | 38 | 28 | 73.68% | 10 | 26.32% |
| xyM12 | 72 | 45 | 62.5% | 27 | 37.5% |
| xyM13 | 74 | 37 | 50% | 37 | 50% |
| xyM14 | 67 | 23 | 34.33% | 44 | 65.67% |
| xyM15 | 24 | 14 | 58.33% | 10 | 41.67% |
| xyM16 | 26 | 18 | 69.23% | 8 | 30.77% |
| Total | 342 | 200 | 58.48% | 142 | 41.52% |
| Element Name | Total | Auto | Manuel | Reviewed | Undischarged |
|---|---|---|---|---|---|
| ColourActiveZone | 27 | 25 | 2 | 0 | 0 |
| Test C00 | 1 | 1 | 0 | 0 | 0 |
| Test C01 | 0 | 0 | 0 | 0 | 0 |
| Test M00 | 16 | 14 | 2 | 0 | 0 |
| Test M01 | 3 | 3 | 0 | 0 | 0 |
| Test M02 | 3 | 3 | 0 | 0 | 0 |
| Test M03 | 4 | 4 | 0 | 0 | 0 |
| Element Name | Total | Auto | Manuel | Reviewed | Undischarged |
|---|---|---|---|---|---|
| ActiveZone | 27 | 25 | 2 | 0 | 0 |
| xyC00 | 1 | 1 | 0 | 0 | 0 |
| xyC01 | 0 | 0 | 0 | 0 | 0 |
| xyC02 | 16 | 14 | 2 | 0 | 0 |
| xyC03 | 3 | 3 | 0 | 0 | 0 |
| xyC04 | 3 | 3 | 0 | 0 | 0 |
| xyM00 | 0 | 0 | 0 | 0 | 0 |
| xyM01 | 0 | 0 | 0 | 0 | 0 |
| xyM02 | 13 | 9 | 4 | 0 | 0 |
| xyM03 | 41 | 33 | 8 | 0 | 0 |
| xyM04 | 22 | 10 | 12 | 0 | 0 |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license ( http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Daoud, H.; Tanougast, C.; Belarbi, M.; Heil, M.; Diou, C. Formal Proof of the Dependable Bypassing Routing Algorithm Suitable for Adaptive Networks on Chip QnoC Architecture. Systems 2017, 5, 17. https://doi.org/10.3390/systems5010017
Daoud H, Tanougast C, Belarbi M, Heil M, Diou C. Formal Proof of the Dependable Bypassing Routing Algorithm Suitable for Adaptive Networks on Chip QnoC Architecture. Systems. 2017; 5(1):17. https://doi.org/10.3390/systems5010017
Chicago/Turabian StyleDaoud, Hayat, Camel Tanougast, Mostefa Belarbi, Mikael Heil, and Camille Diou. 2017. "Formal Proof of the Dependable Bypassing Routing Algorithm Suitable for Adaptive Networks on Chip QnoC Architecture" Systems 5, no. 1: 17. https://doi.org/10.3390/systems5010017







