AgPi: Agents on Raspberry Pi
Abstract
:1. Introduction
- Privacy: Most of the cloud servers are owned by multinational corporations such as Amazon (Seattle, WA, USA), Google (Mountain View, CA, USA), Microsoft (Redmond, WA, USA), Cisco (San Jose, CA, USA), etc. which continuously receive data from the user side. Leakage of personal information and data ownership becomes a critical issue when all of the user’s data is collected for analytics purpose in the cloud [6]. A safer solution would be to have a local infrastructure on which the user has more control than the cloud server. This would allow local data filtering and computation before sending it over to the cloud. An agent-based system could be a better solution for ensuring privacy.
- Cost: Cloud services follow a "Pay-as-you-go" model which adds to the cost as the storage and network communication increases [8]. In a local computational infrastructure model, these costs can be reduced if the data collected is filtered locally and only pertinent information is sent to the cloud.
- Network Latency: A cloud has inherent latency issues and thus may not be a viable solution for applications such as live video streaming in connected vehicles, real-time data analytics in smart grids [8], etc., all of which require a rapid response. An Intranet of Things that uses agents, on the contrary, can provide fast local computations, thereby decreasing latency.
- Energy: As already mentioned, agents in an Intranet of Things can filter the acquired data prior to sending it over to the cloud. Since this reduces communication overheads, it also reduces the energy consumed and consequently increases the battery life of the devices constituting the network [9].
2. Multi-Agent Systems (MAS)
2.1. Mobile Agents
- Bandwidth and latency reduction: A mobile agent has the innate ability to carry the computation in the form of code to a remote site. Instead of fetching the whole raw or unprocessed data from a remote site, the mobility allows for the computing program or logic to migrate to this site and process the data therein. This results in reducing network traffic and latency.
- Discontinuous operation: In a dynamic network where the devices are mobile, it is rare that a continuous connection is maintained between two nodes for a long time. In a conventional client-server system, a sudden disconnection may cause the server to resend the whole data, making it an expensive affair. On the contrary, in a mobile agent-based scenario, migration occurs only when a connection is established. The mobile agent then resides in the new node till the connection to the next node is available. Unlike the large amount of data to be processed, a mobile agent is comparatively lightweight. Thus, a failure in migration does not compound into large losses in bandwidth and time.
- Adaptivity and flexibility: In a traditional centralized system, any upgrade would require the system to be brought down, changes made and then restarted. In a mobile agent-based system, upgrades could be packaged within the mobile agent and released into the network. This On-The-Fly Programming (OTFP) [10] support facilitates a higher amount of flexibility. Agents have the ability to sense and perceive their environment and change their behaviours accordingly. A mobile agent can add new behaviours in the form of a payload and can also adapt to different situations.
2.2. Multi-Agent Frameworks
3. Location-Aware and Tracking Service (LATS)
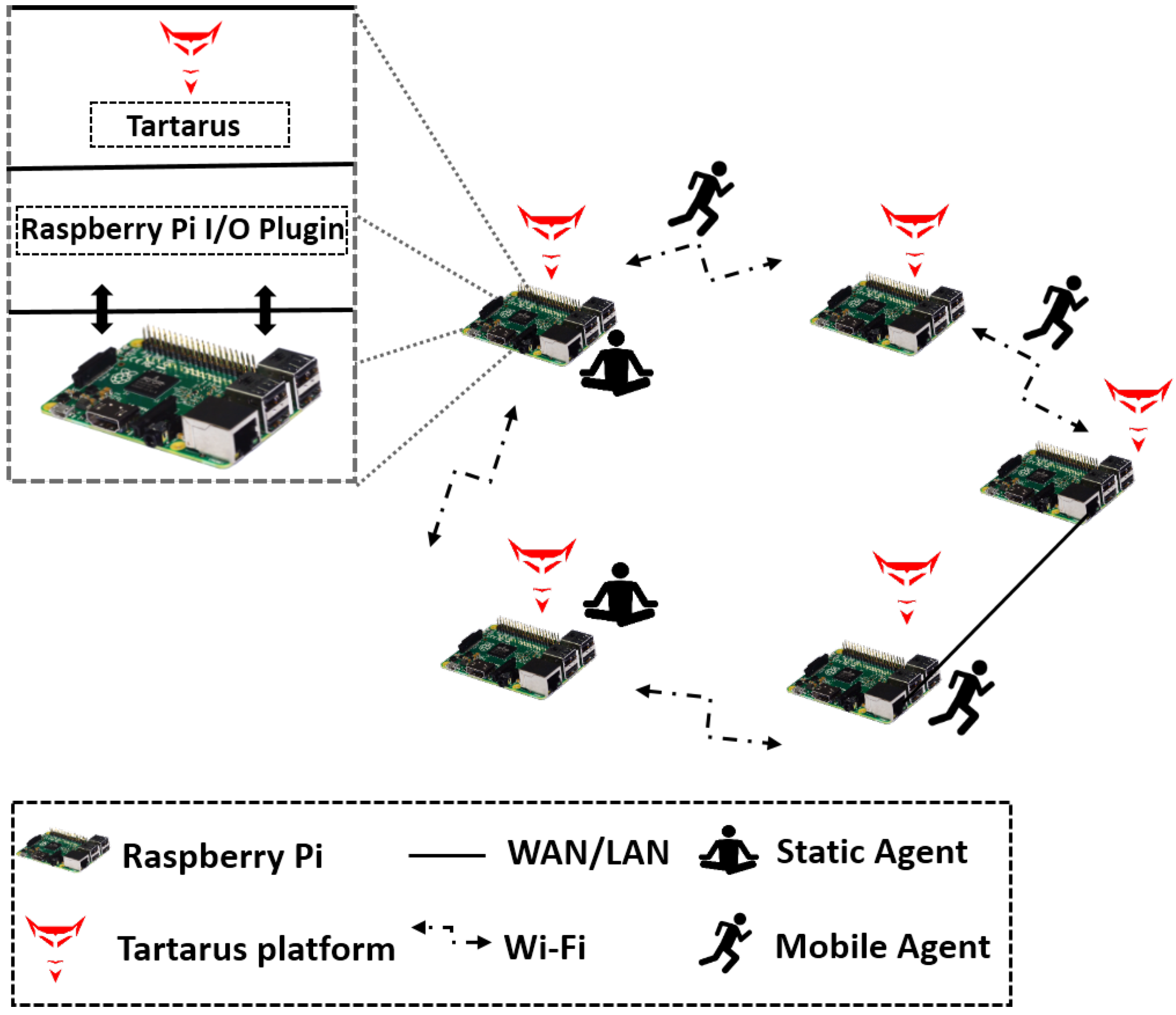
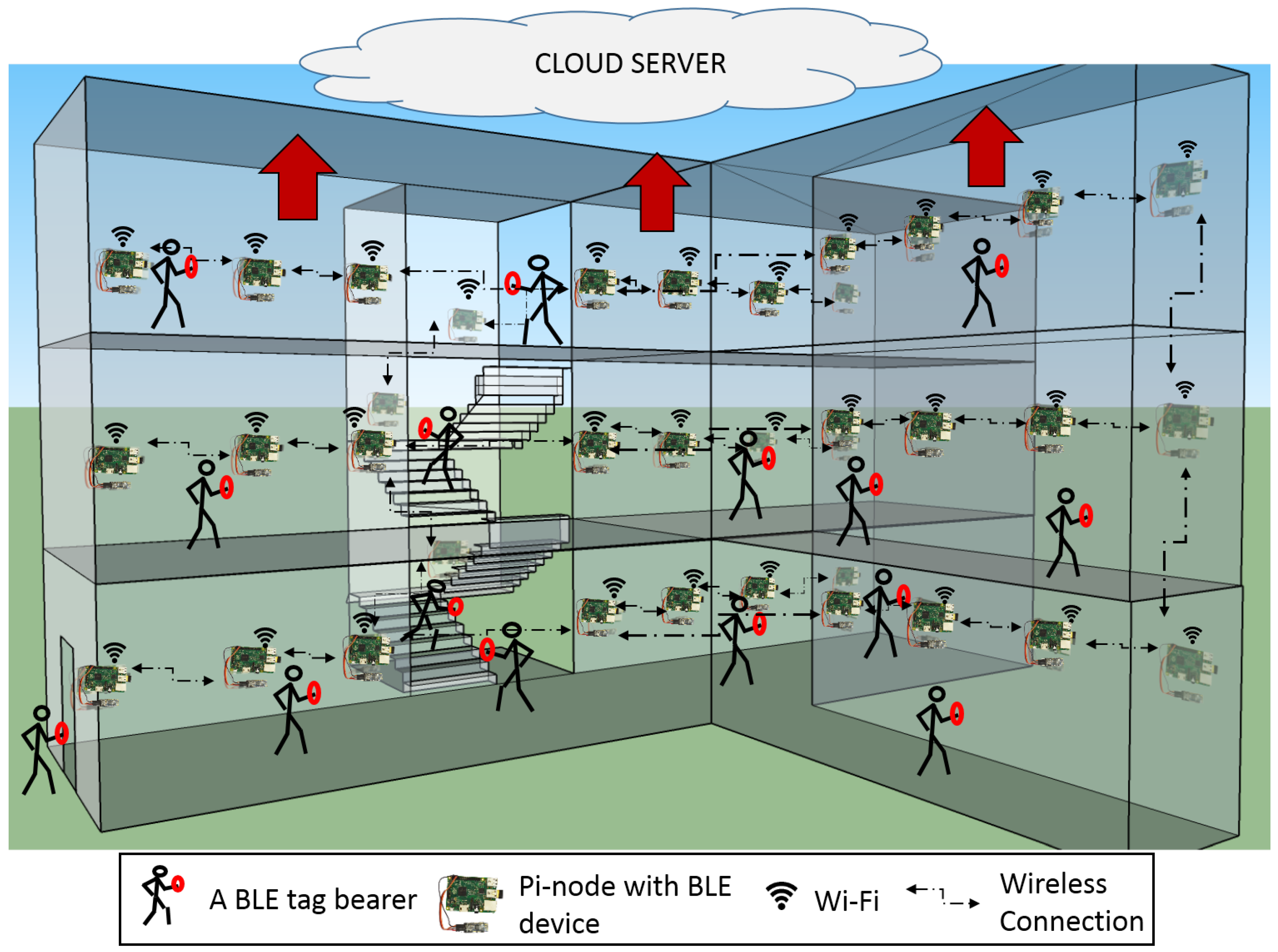
4. AgPi: The Cyber and Physical Confluence
5. AgPi in the Real World
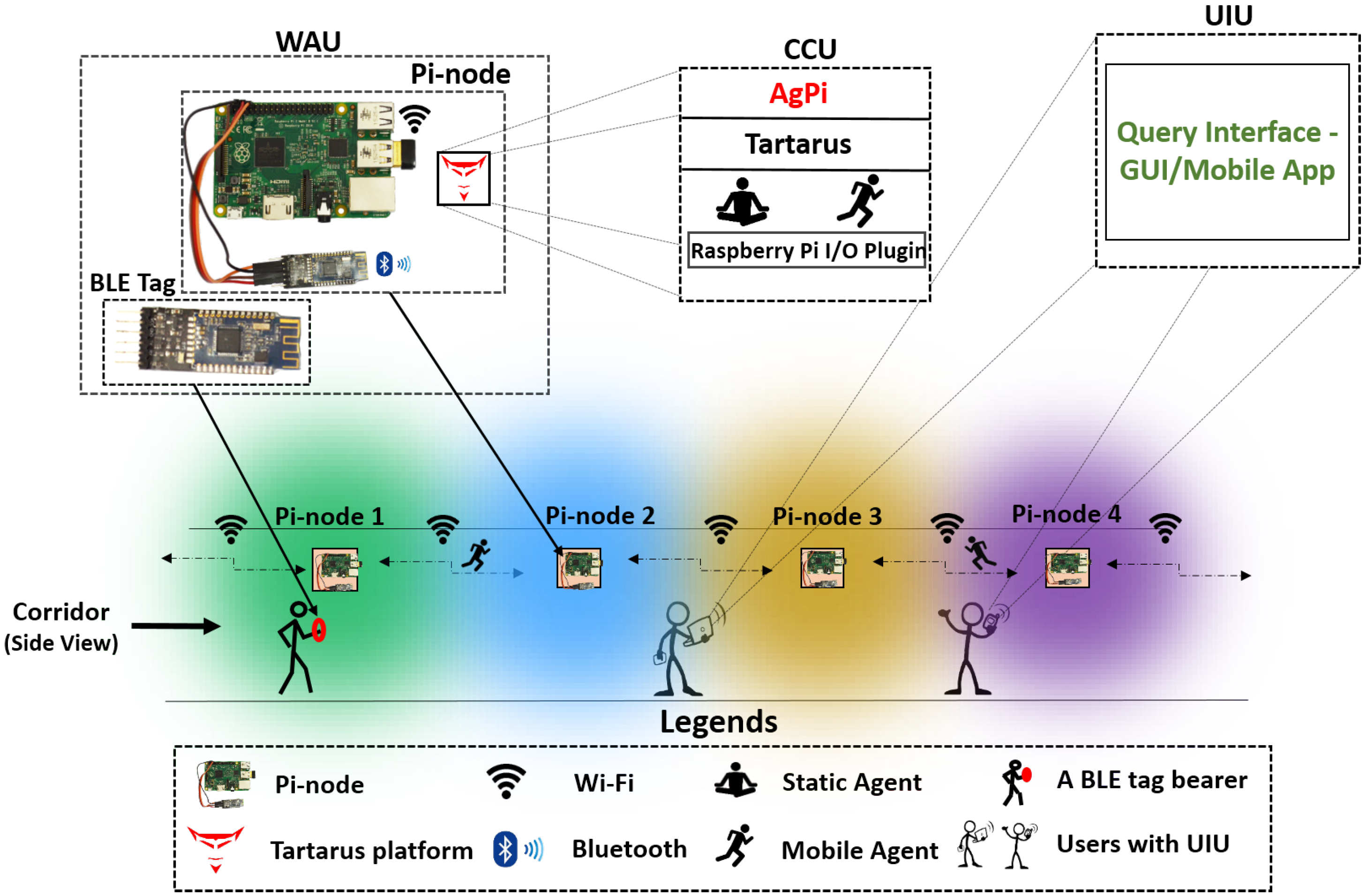
5.1. AgPi based LATS application
5.1.1. Detection Mechanism
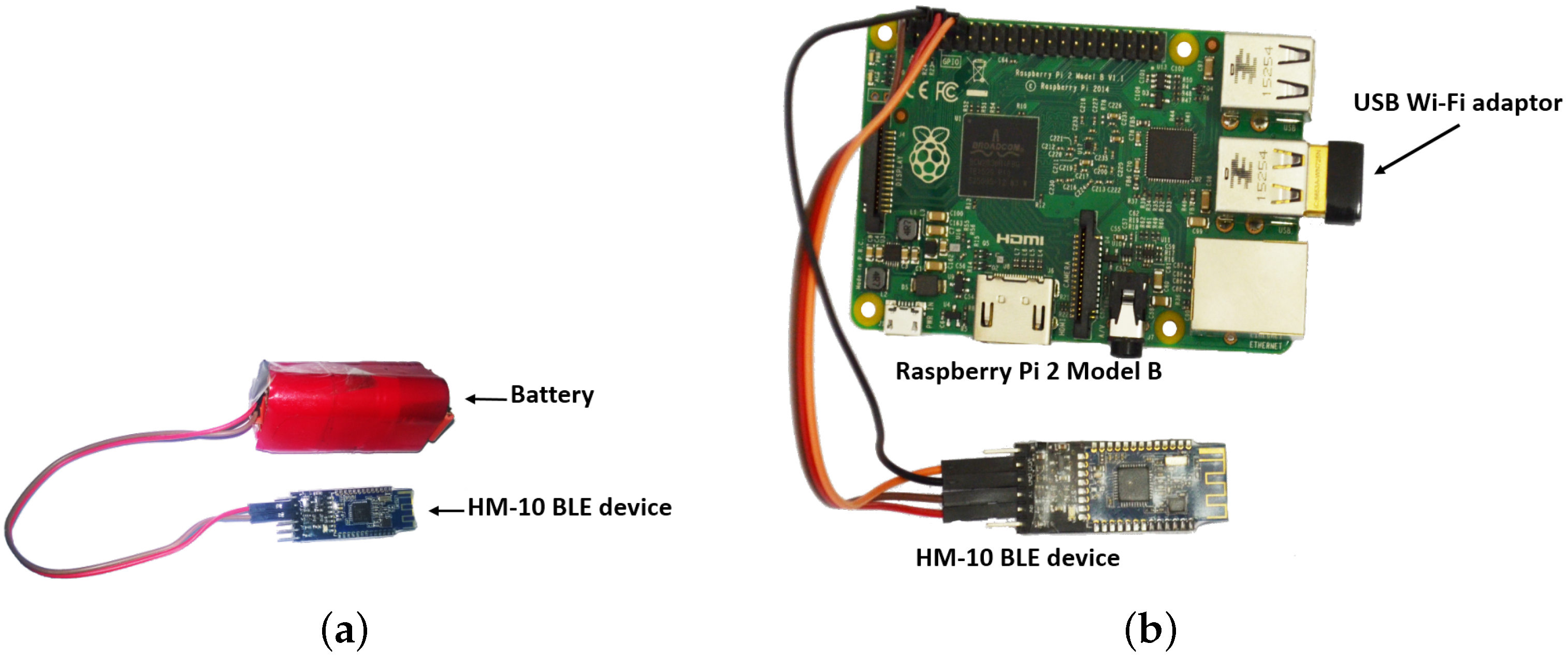
5.1.2. Wearable and Acquisition Unit (WAU)
- Preamble: This read-only field is 9 bytes wide and contains the manufacturer’s data.
- Universally Unique Identifier (UUID): This field, which is 16 bytes wide, can be preset to contain the identity of the BLE device.
- Major: This is a user writable field which helps in identifying a subset of such devices within a large group.
- Minor: It is also a writable field which is used for specifying a subset of the Major field.
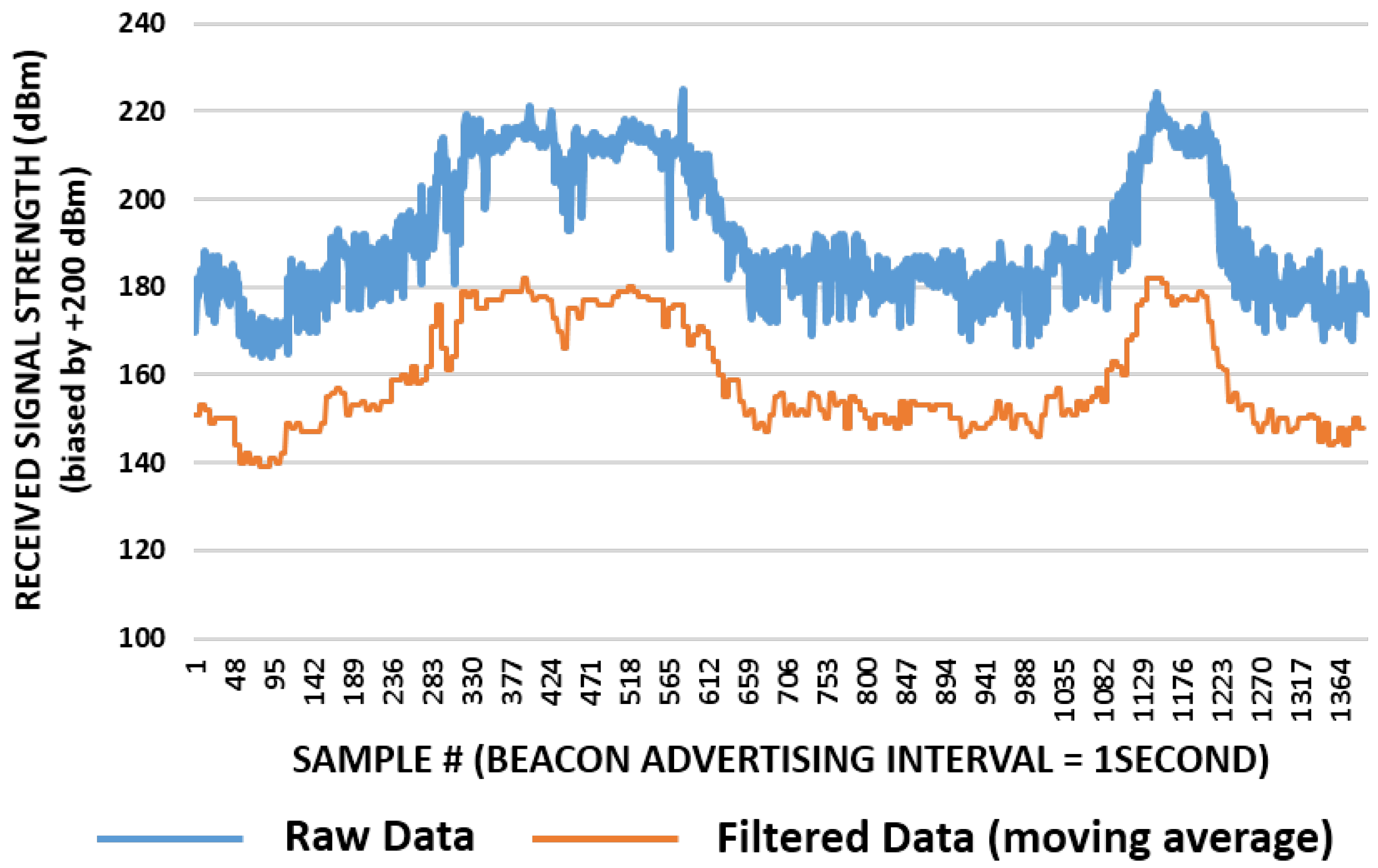
- Tx Power: This field is a calibrated 2’s complement value denoting the signal strength at 1 m from the device. This field is compared with the measured signal strength at the receiving end in order to ascertain the distance between the transmitter and receiver.
5.1.3. Cyber Computing Unit (CCU)
- (i)
- Beyond: When the RSS value is zero, it means that the person is not detected and is beyond the concerned zone.
- (ii)
- Far: This is a case when the person being tracked is far from the Pi-node. This is detected by a weak RSS value at the Pi-node of the concerned zone and would mean that the person wearing the BLE tag is in between 2 m to 5 m of the radial distance from the associated Pi-node.
- (iii)
- Near: A strong RSS value indicates the person to be well within the range i.e., less than 2 m in the present case.
5.1.4. User Interaction Unit (UIU)
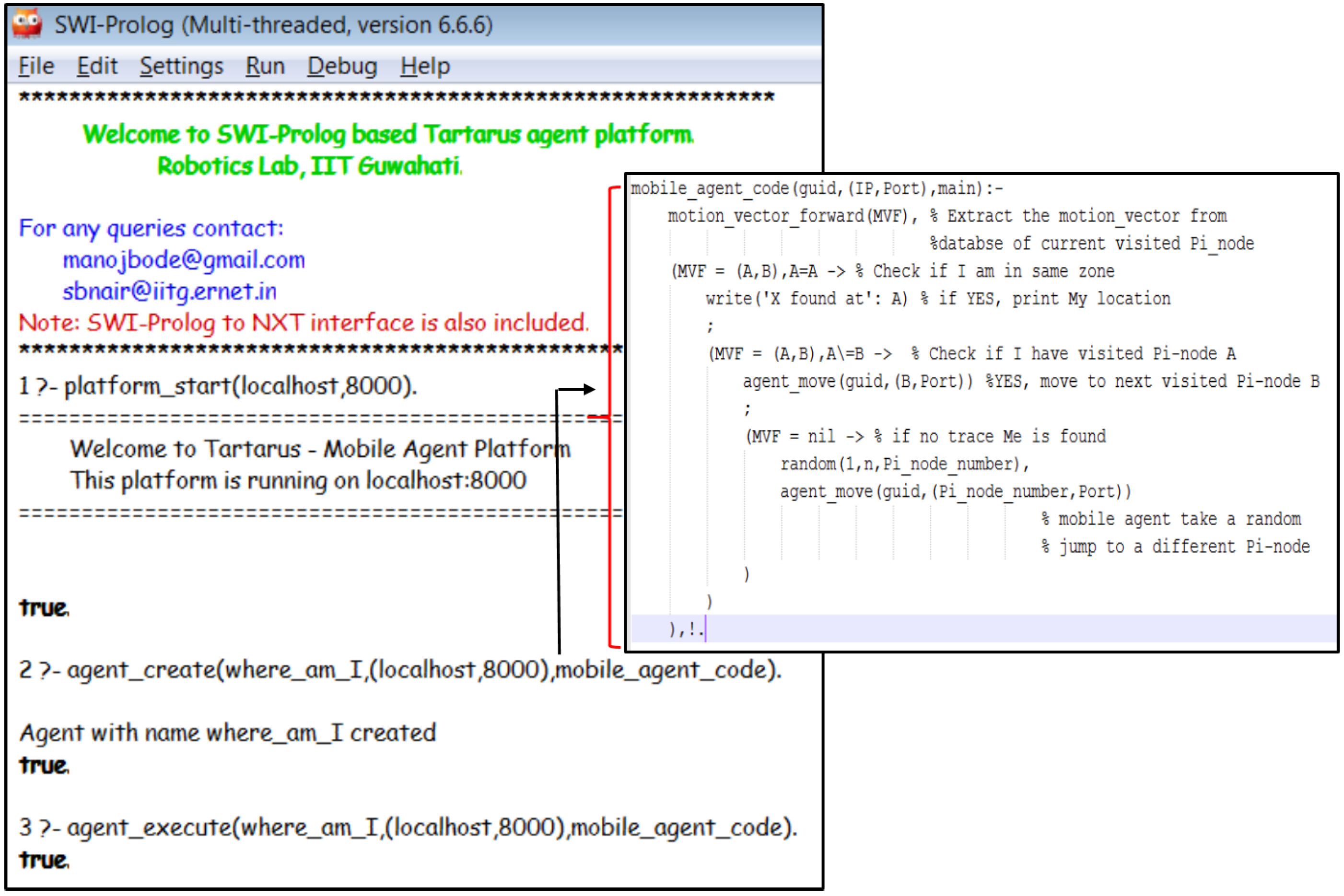
- Where am I?: Such a query invariably emanates from a person who is lost within the building or does not know how to move around or needs to convey his/her bearings to someone else. Under such conditions, the user can fire an SQL query packaged in a mobile agent to the nearest one-hop neighbouring Pi-node. Once the mobile agent enters this Pi-node, it executes its code and eventually lands up in the Pi-node of the zone in which the person is currently present. The agent then retrieves the location information stored a priori within this Pi-node and provides it to the user. A segment of the relevant mobile agent code is presented in Figure 6.
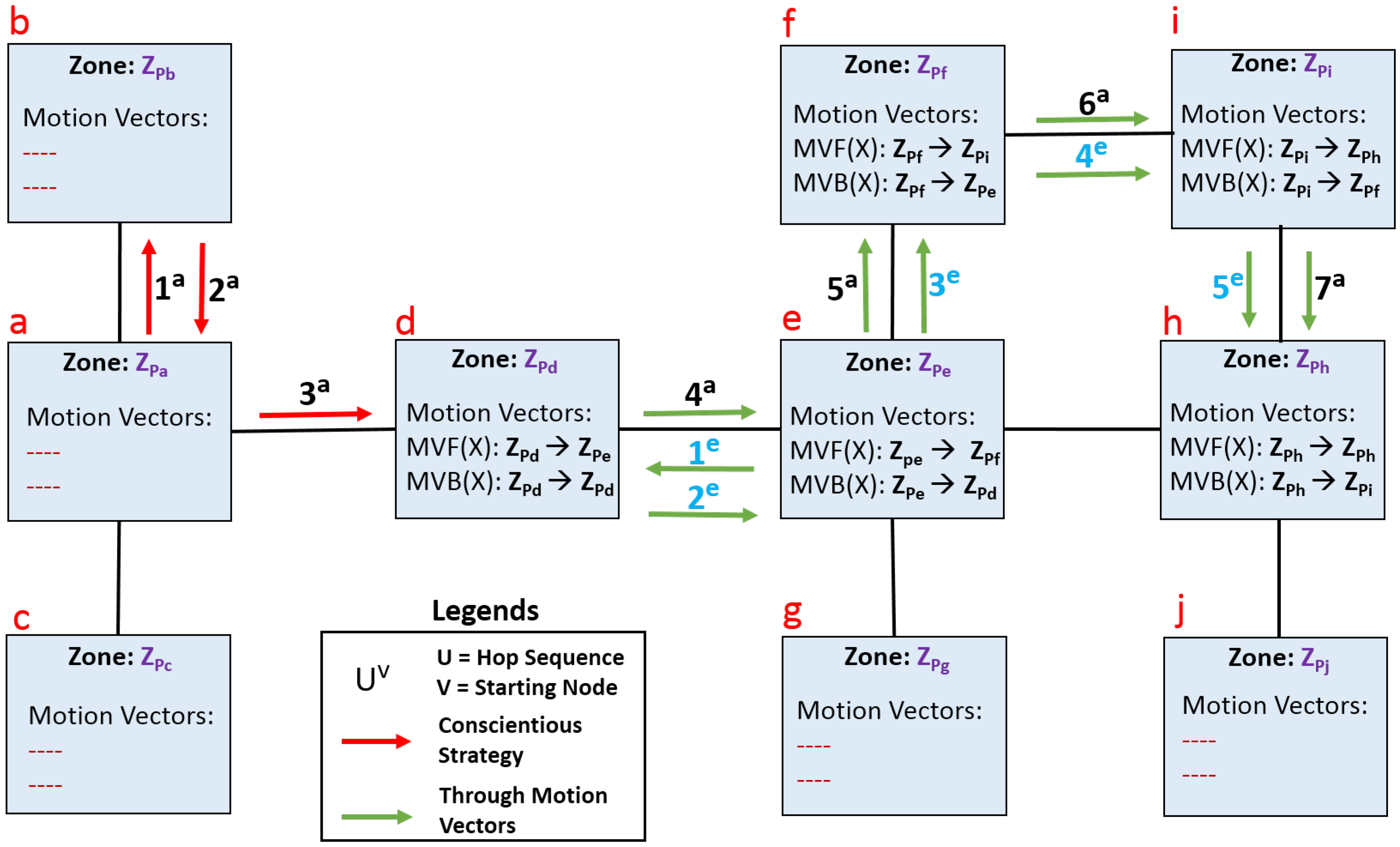
- Where is X?: A query of this kind is required for a person to know whether X is within the building under consideration and, if so, where. This agent-based LATS allows for a non-intrusive mechanism to find the location of X. The user packs this query into a mobile agent and transmits it onto the Tartarus platform of the closest Pi, the one within the zone s/he is in currently. On reaching this Pi, the mobile agent scans the database within it to find whether X is/was in this zone. (i) If it discovers that X is within a particular zone currently, it retrieves the location information from the Pi-node and backtracks its path to the user’s system and provides the information on X; (ii) if the agent finds a Motion Vector Forward for X in that zone, then it uses the vector to find the next zone visited by X and migrates to the concerned Pi-node of this zone. It continues to do so until it eventually lands in a Pi-node of a zone where X is currently present. On reaching this, it retrieves the relevant information and retraces its path back to the user’s system to provide the information on X. In case X has left the place, the Motion Vector Forward within the Pi-node in the zone where X was last present will point to INFINITY. The agent would then assume that X is no more in the area and report accordingly to the user; (iii) if no trace of X is found in the database, the mobile agent continues its migration along the Pi-nodes in a conscientious manner [60] (Appendix A) until it eventually finds that X has been within the zone of some Pi or left the place. It may be noted that a user who wishes to know the bearings of another can alter his query to extract a range of information on the person being tracked.
- Trace(X): This query will provide a list of locations associated with all those zones which X visited in order. The query can again be packed into a mobile agent and sent to the network of Pi-nodes to search the individual databases and retrieve the list. A mobile agent algorithm to trace the path of a BLE tag bearer is shown in Algorithm 1 and an example of mobile agent routing for the same is described in Appendix B.
6. Experiments and Results
6.1. Data Acquisition
6.2. Query Processing
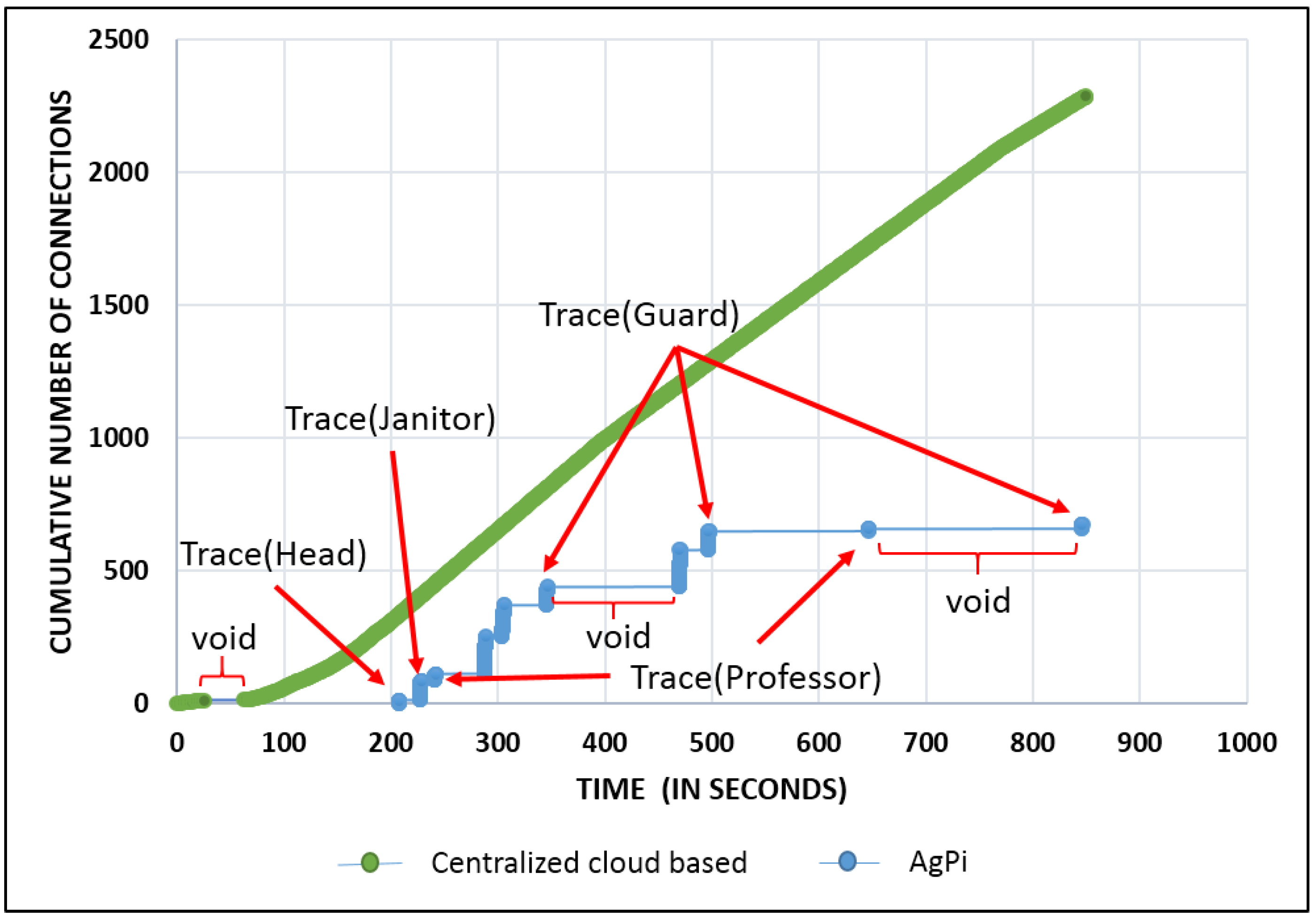
Scenario 1: Conventional Cloud Approach
Scenario 2: AgPi Scenario
Comparison of Scenario 1 with Scenario 2
7. AgPi: Applications Envisaged
8. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
Abbreviations
| Pi | Raspberry Pi |
| AgPi | Agents on Pi |
| BLE | Bluetooth Low Energy |
| IoT | Internet of Things |
| CPS | Cyber-Physical System |
| MAS | Multi-Agent Systems |
| GPS | Global Position System |
| LATS | Location-Aware and Tracking Services |
| SQL | Structured Query Language |
| RSS | Received Signal Strength |
| PC | Personal Computer (Desktop) |
| UHF | Ultra High Frequency |
| RFID | Radio Frequency Identification |
| I2C | Inter-Integrated Circuit |
| UART | Universal Asynchronous Receiver Transmitter |
| SPI | Serial Peripheral Interface |
| WSN | Wireless Sensor Network |
Appendix A. Conscientious Migration Strategy
Appendix B. Query Processing
Handling Failures
References
- Atzori, L.; Iera, A.; Morabito, G. The internet of things: A survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Gartner. Gartner Says By 2020, More Than Half of Major New Business Processes and Systems Will Incorporate Some Element of the Internet of Things. 2016. Available online: http://www.gartner.com/newsroom/id/3185623 (accessed on 3 June 2016).
- Schreyer, P. The contribution of information and communication technology to output growth. OECD Sci. Technol. Ind. Working Pap. 2000. [Google Scholar] [CrossRef]
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A vision, architectural elements, and future directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef]
- Khan, R.; Khan, S.U.; Zaheer, R.; Khan, S. Future Internet: The Internet of Things Architecture, Possible Applications and Key Challenges. In Proceedings of the 10th International Conference on Frontiers of Information Technology (FIT), Islamabad, Pakistan, 17–19 December 2012; pp. 257–260.
- Vaquero, L.M.; Rodero-Merino, L. Finding Your Way in the Fog: Towards a Comprehensive Definition of Fog Computing. SIGCOMM Comput. Commun. Rev. 2014, 44, 27–32. [Google Scholar] [CrossRef]
- Wooldridge, M. An Introduction to MultiAgent Systems; John Wiley & Sons: Hoboken, NJ, USA, 2009. [Google Scholar]
- Bonomi, F.; Milito, R.; Zhu, J.; Addepalli, S. Fog Computing and Its Role in the Internet of Things. In Proceedings of the First Edition of the MCC Workshop on Mobile Cloud Computing, MCC’ 12, Helsinki, Finland, 17 August 2012; ACM: New York, NY, USA, 2012; pp. 13–16. [Google Scholar]
- Calle, M.; Kabara, J. Measuring Energy Consumption in Wireless Sensor Networks Using GSP. In Proceedings of the 2006 IEEE 17th International Symposium on Personal, Indoor and Mobile Radio Communications, Helsinki, Finland, 11–14 September 2006; pp. 1–5.
- Semwal, T.; Bode, M.; Singh, V.; Jha, S.S.; Nair, S.B. Tartarus: A Multi-Agent platform for integrating Cyber-Physical Systems and Robots. In Proceedings of the 2015 Conference on Advances in Robotics, Goa, India, 2–4 July 2015.
- Wolfson, O.; Sistla, P.; Xu, B.; Zhou, J.; Chamberlain, S.; Yesha, Y.; Rishe, N. Tracking moving objects using database technology in DOMINO. In Next Generation Information Technologies and Systems; Springer: Berlin, Germany, 1999; pp. 112–119. [Google Scholar]
- Franklin, S.; Graesser, A. Is it an Agent, or just a Program? A Taxonomy for Autonomous Agents. In Intelligent Agents III Agent Theories, Architectures, and Languages; Springer: Berlin, Germany, 1996; pp. 21–35. [Google Scholar]
- Maes, P. Artificial Life Meets Entertainment: Lifelike Autonomous Agents. Commun. ACM 1995, 38, 108–114. [Google Scholar] [CrossRef]
- Ferber, J. Multi-Agent System: An Introduction to Distributed Artificial Intelligence; Addison-Wesley Longman Publishing Co., Inc.: Boston, MA, USA, 1999. [Google Scholar]
- White, J.D.; Davies, M.; Mcgeachie, J.; Grounds, A.D. Mobile Agents. In Software Agents; AAAI/MIT Press: Palo Alto, CA, USA, 1997; pp. 437–472. [Google Scholar]
- Harrison, C.G.; Chess, D.M.; Kershenbaum, A. Mobile Agents: Are They a Good Idea? IBM TJ Watson Research Center Yorktown Heights: New York, NY, USA, 1995. [Google Scholar]
- Chen, M.; Gonzalez, S.; Leung, V. Applications and design issues for mobile agents in wireless sensor networks. IEEE Wirel. Commun. 2007, 14, 20–26. [Google Scholar] [CrossRef]
- Kambayashi, Y.; Takimoto, M. Higher-order mobile agents for controlling intelligent robots. Int. J. Intell. Inf. Technol. (IJIIT) 2005, 1, 28–42. [Google Scholar] [CrossRef]
- Takimoto, M.; Mizuno, M.; Kurio, M.; Kambayashi, Y. Saving energy consumption of multi-robots using higher-order mobile agents. In Agent and Multi-Agent Systems: Technologies and Applications; Springer: Wroclaw, Poland, 2007; pp. 549–558. [Google Scholar]
- Maes, P.; Guttman, R.H.; Moukas, A.G. Agents That Buy and Sell. Commun. ACM 1999, 42, 81–91. [Google Scholar] [CrossRef]
- Boukerche, A.; Machado, R.B.; Jucá, K.R.; Sobral, J.B.M.; Notare, M.S. An agent-based and biological inspired real-time intrusion detection and security model for computer network operations. Comput. Commun. 2007, 30, 2649–2660. [Google Scholar] [CrossRef]
- Machado, R.B.; Boukerche, A.; Sobral, J.; Juca, K.; Notare, M. A hybrid artificial immune and mobile agent intrusion detection based model for computer network operations. In Proceedings of the 19th IEEE International Proceedings on Parallel and Distributed Processing Symposium, 4 April 2005; pp. 1–8.
- Kawamura, T.; Sugahara, K. A Mobile Agent-Based P2P e-Learning System. IPSJ J. 2005, 46, 222–225. [Google Scholar]
- Godfrey, W.W.; Nair, S.B. An Immune System Based Multi-robot Mobile Agent Network. In Artificial Immune Systems; Springer: Berlin, Germany, 2008; pp. 424–433. [Google Scholar]
- Godfrey, W.W.; Nair, S.B. Mobile Agent Cloning for Servicing Networked Robots. In Principles and Practice of Multi-Agent Systems; Springer: Berlin, Germany, 2010; pp. 336–339. [Google Scholar]
- Godfrey, W.W.; Jha, S.S.; Nair, S.B. On a mobile agent framework for an internet of things. In Proceedings of the International Conference on Communication Systems and Network Technologies (CSNT), Gwalior, India, 6–8 April 2013; pp. 345–350.
- Satoh, I. MobileSpaces: A framework for building adaptive distributed applications using a hierarchical mobile agent system. In Proceedings of 20th International Conference on Distributed Computing Systems, Taipei, Taiwan, 10–13 April 2000; pp. 161–168.
- Bellifemine, F.; Poggi, A.; Rimassa, G. JADE: a FIPA2000 compliant agent development environment. In Proceedings of the Fifth International Conference on Autonomous Agents, Madrid, Spain, 10–11 September 2001; pp. 216–217.
- Bellifemine, F.L.; Caire, G.; Greenwood, D. Developing Multi-Agent Systems with JADE; Volume 7, John Wiley & Sons: Hoboken, NJ, USA, 2007. [Google Scholar]
- Johansen, D.; Renesse, R.; Schneider, F.B. An Introduction to the TACOMA Distributed System; Technical Report; University of Tromsø and Cornell University: Ithaca, NY, USA, 1995. [Google Scholar]
- Kotz, D.; Gray, R.; Nog, S.; Rus, D.; Chawla, S.; Cybenko, G. Agent Tcl: Targeting the needs of mobile computers. IEEE Internet Computing 1997, 1, 58–67. [Google Scholar] [CrossRef]
- Silva, A.; Da Silva, M.M.; Delgado, J. An overview of AgentSpace: Next-generation mobile agent system. In Mobile Agents; Springer: Berlin, Germany, 1998; pp. 148–159. [Google Scholar]
- Lange, D.B.; Oshima, M.; Karjoth, G.; Kosaka, K. Aglets: Programming mobile agents in Java. In Worldwide Computing and Its Applications; Springer: Berlin, Germany, 1997; pp. 253–266. [Google Scholar]
- Moreno, A.; Valls, A.; Viejo, A. Using JADE-LEAP to implement agents in mobile devices; Universitat Rovira i Virgili: Tarragona, Spain, 2003. [Google Scholar]
- Chen, B.; Cheng, H.H.; Palen, J. Integrating mobile agent technology with multi-agent systems for distributed traffic detection and management systems. Transp. Res. Part C Emerg. Technol. 2009, 17, 1–10. [Google Scholar] [CrossRef]
- Clocksin, W.; Mellish, C.S. Programming in PROLOG; Springer Science & Business Media: Berlin, Germany, 2003. [Google Scholar]
- Bratko, I. Prolog Programming for Artificial Intelligence; Pearson Education: Upper Saddle River, NJ, USA, 2001. [Google Scholar]
- Gal, A.; Lapalme, G.; Saint-Dizier, P.; Somers, H. Prolog for Natural Language Processing; Wiley: Chichester, England, 1991. [Google Scholar]
- Ceri, S.; Gottlob, G.; Wiederhold, G. Efficient database access from PROLOG. IEEE Trans. Softw. Eng. 1989, 15, 153–164. [Google Scholar] [CrossRef]
- van der Wilt, K. Knowledge systems and Prolog: A logical approach to expert systems and natural language processing. Mach. Transl. 1990, 4, 329–331. [Google Scholar] [CrossRef]
- Tarau, P. Jinni: Intelligent mobile agent programming at the intersection of Java and Prolog. In Proceedings of Practical Application of Intelligent Agents and Multi-Agent Technology (PAAM), London, UK, 19–21 Apirl 1999; Volume 99, pp. 109–123.
- Devèze, B.; Chopinaud, C.; Taillibert, P. Alba: A generic library for programming mobile agents with prolog. In Programming Multi-Agent Systems; Springer: Berlin, Germany, 2006; pp. 129–148. [Google Scholar]
- Li, X. Imago: A Prolog-based system for intelligent mobile agents. In Mobile Agents for Telecommunication Applications; Springer: Berlin, Germany, 2001; pp. 21–30. [Google Scholar]
- Matani, J.; Nair, S.B. Typhon - A mobile agents framework for real world emulation in Prolog. In Multi-Disciplinary Trends in Artificial Intelligence; Springer: Berlin, Germany, 2011; pp. 261–273. [Google Scholar]
- Wielemaker, J.; Schrijvers, T.; Triska, M.; Lager, T. Swi-prolog. Theory and Practice of Logic Programming 2012, 12, 67–96. [Google Scholar] [CrossRef]
- Jha, S.S.; Godfrey, W.W.; Nair, S.B. Stigmergy-Based Synchronization of a Sequence of Tasks in a Network of Asynchronous Nodes. Cybern. Syst. 2014, 45, 373–406. [Google Scholar] [CrossRef]
- Jha, S.S.; Nair, S.B. On a Multi-agent Distributed Asynchronous Intelligence-Sharing and Learning Framework. In Transactions on Computational Collective Intelligence XVIII; Springer: Berlin, Germany, 2015; pp. 166–200. [Google Scholar]
- Bode, M.; Jha, S.S.; Nair, S.B. A Mobile Agent-based Autonomous Partial Green Corridor Discovery and Maintenance Mechanism for Emergency Services amidst Urban Traffic. In Proceedings of the First International Conference on IoT in Urban Space, Rome, Italy, 27–28 October 2014; pp. 13–18.
- Semwal, T.; Nikhil, S.; Jha, S.S.; Nair, S.B. TARTARUS: A Multi-Agent Platform for Bridging the Gap Between Cyber and Physical Systems (Demonstration). In Proceedings of the 2016 International Conference on Autonomous Agents and Multiagent Systems, Singapore, 9–13 May 2016; International Foundation for Autonomous Agents and Multiagent Systems: Richland, SC, USA, 2016; pp. 1493–1495. [Google Scholar]
- Kinnunen, J.; Krishnamurthy, G.; Huhtanen, K.; Jussila, P.; Ratschunas, K. Location Dependent Services. U.S. Patent 6,813,501, 2 November 2004. [Google Scholar]
- Catarinucci, L.; De Donno, D.; Mainetti, L.; Palano, L.; Patrono, L.; Stefanizzi, M.L.; Tarricone, L. An IoT-Aware Architecture for Smart Healthcare Systems. IEEE Internet Things J. 2015, 2, 515–526. [Google Scholar] [CrossRef]
- Dobkin, D.M. The RF in RFID: UHF RFID in Practice; Newnes: Burlington, VT, USA, 2012. [Google Scholar]
- Yick, J.; Mukherjee, B.; Ghosal, D. Wireless sensor network survey. Comput. Netw. 2008, 52, 2292–2330. [Google Scholar] [CrossRef]
- Gomez, C.; Oller, J.; Paradells, J. Overview and Evaluation of Bluetooth Low Energy: An Emerging Low-Power Wireless Technology. Sensors 2012, 12, 11734–11753. [Google Scholar] [CrossRef]
- Yoshimura, Y.; Krebs, A.; Ratti, C. An analysis of visitors’ length of stay through noninvasive Bluetooth monitoring in the Louvre Museum. 2016; arXiv: 1605.00108. [Google Scholar]
- Wolfson, O.; Chamberlain, S.; Kalpakis, K.; Yesha, Y. Modeling moving objects for location based services. In Developing an Infrastructure for Mobile and Wireless Systems; Springer: Berlin, Germany, 2001; pp. 46–58. [Google Scholar]
- Raspberry Pi — Wikipedia. Available online: https://en.wikipedia.org/wiki/Raspberry_Pi (accessed on 2 June 2016).
- Raspberry Pi Zero: The $5 Computer. Available online: https://www.raspberrypi.org/blog/raspberry-pi-zero/ (accessed on 3 June 2016).
- Michael, M.S. Universal Asynchronous Receiver/Transmitter. U.S. Patent 5,140,679, 18 August 1992. [Google Scholar]
- Minar, N.; Kramer, K.; Maes, P. Cooperating mobile agents for mapping networks. In Proceedings of the First Hungarian National Conference on Agent Based Computing, Budapest, Hungary, 29–31 May 1998.
- Faragher, R.; Harle, R. An analysis of the accuracy of bluetooth low energy for indoor positioning applications. In Proceedings of the 27th International Technical Meeting of the Satellite Division of the Institute of Navigation (ION GNSS+’14), Tampa, FL, USA, 8–12 September 2014.
- Lua, E.K.; Crowcroft, J.; Pias, M.; Sharma, R.; Lim, S. A survey and comparison of peer-to-peer overlay network schemes. IEEE Commun. Surv. Tutor. 2005, 7, 72–93. [Google Scholar]



| INFINITY → | Zone → | Zone |
|---|---|---|
| MVF | ||
| MVB | INFINITY |
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Semwal, T.; Nair, S.B. AgPi: Agents on Raspberry Pi. Electronics 2016, 5, 72. https://doi.org/10.3390/electronics5040072
Semwal T, Nair SB. AgPi: Agents on Raspberry Pi. Electronics. 2016; 5(4):72. https://doi.org/10.3390/electronics5040072
Chicago/Turabian StyleSemwal, Tushar, and Shivashankar Bhaskaran Nair. 2016. "AgPi: Agents on Raspberry Pi" Electronics 5, no. 4: 72. https://doi.org/10.3390/electronics5040072






