A Novel Effective Multipath Routing Technique Providing High Availability in Wireless Networks
Abstract
:1. Introduction
2. Related Works
2.1. AOMDV
2.2. AODVM
2.3. MP-AODV
- NDMR discovers and establishes two node-joint paths instead of many paths between a source and a destination in a wireless network to provide redundancy communications, resulting in reducing the number of network traffic frames sent between the source and the destination in the network compared with the existing multipath routing techniques.
- NDMR reduces duplicates of the control messages used for discovering and establishing paths between the source and destination nodes in wireless networks compared with the existing multipath routing techniques.
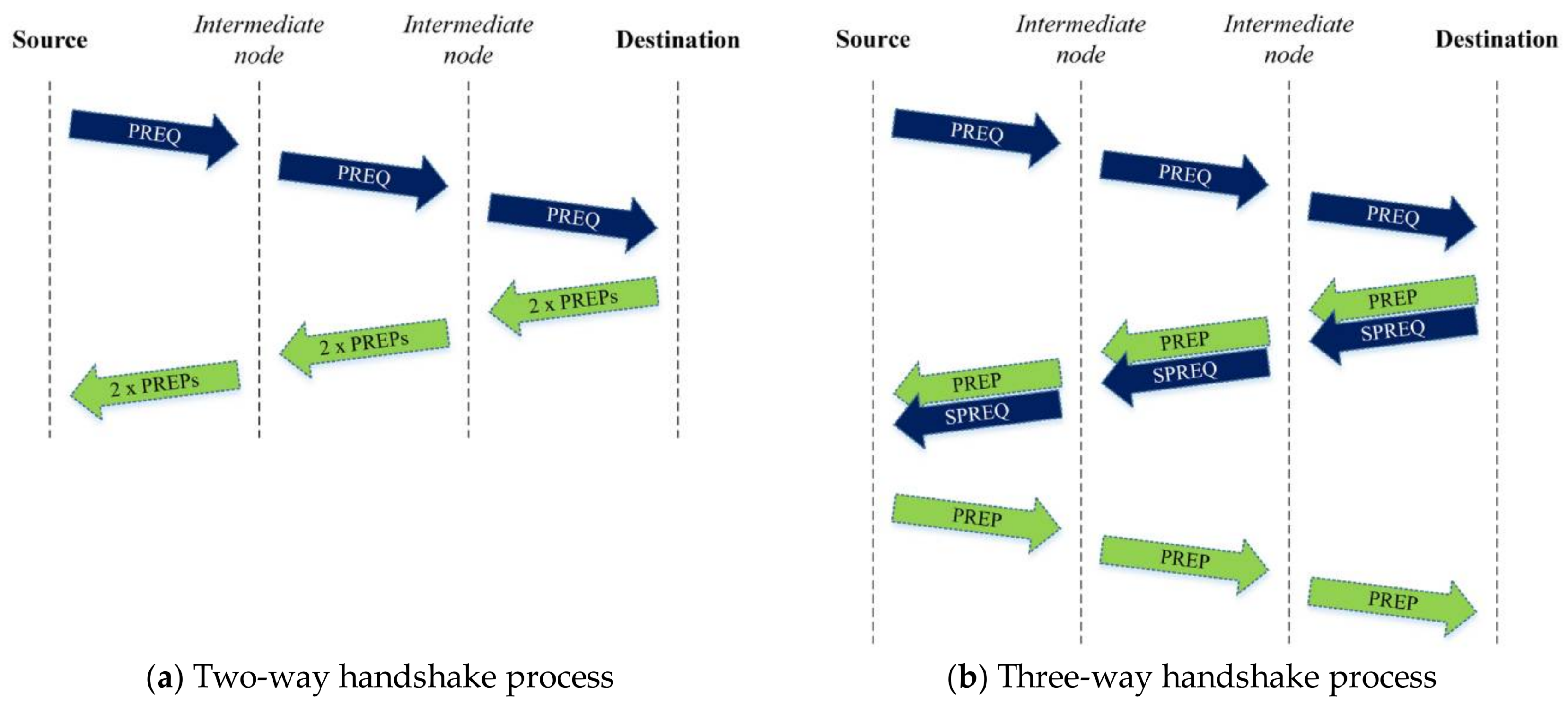
- NDMR uses a two-way or three-way handshake route discovery process instead of four-way process, resulting in decreasing the route discovery period compared with the existing multipath routing techniques.
3. The NDMR Approach
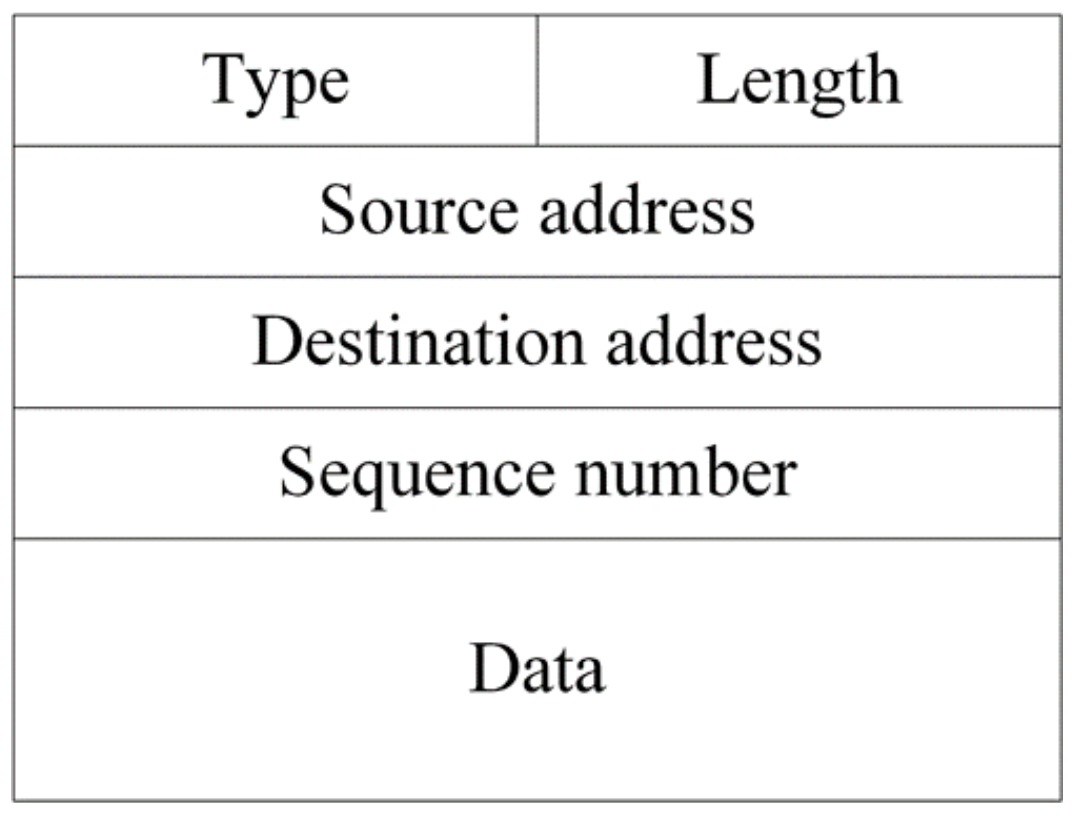
3.1. Control Messages
- Path request message: A PREQ message is broadcast by the source node when it initiates a new path discovery process. The PREQ contains the following data field:
- +
- Node_list: the list of nodes through which the PREQ has been passed.
- Path reply message: A PREP message is used to report a path discovered. The PREP contains the following data field:
- +
- Discovered_path: the path discovered between the source and destination.
- Secondary path request message: A secondary path request (SPREQ) message is used to discover the second path. The SPREQ contains the following data fields:
- +
- Node_list: the list of nodes through which the SPREQ has been passed.
- +
- First path: the first path discovered and established between the source and destination.
3.2. NDMR Operations
- Path discovery
- Frame forwarding
- Path maintenance
3.2.1. Path Discovery
- Reverse route is determined based on the potential reverse route stored in its buffer.
- Forward route is built based on the received PREP.
3.2.2. Frame Forwarding
3.2.3. Path Maintenance
- 1.
- Case 1: During the active communication between the source and destination nodes, the movement of intermediate nodes that do not lie along an active path does not affect the communication.
- 2.
- Case 2: If the source node moves during the active communication, it will decide whether to initiate a new path discovery process or not to establish one or two node-disjoint paths to the destination.
- (a)
- If the source can communicate with both its neighbors, which belong to the first and second paths, respectively, the movement of the source does not affect the active communication.
- (b)
- If the source becomes unreachable with a neighbor lying along an active path, the source will remove the path from its route table and set the remaining path to the first path. An SPREQ is then broadcast by the source to establish the second path to the destination.
- (c)
- If the source cannot communicate with its neighbors that belong to the first and second paths, the source will re-initiate a new path discovery to establish two new node-disjoint paths to the destination.
- 3.
- Case 3: If any node along an active path fails or becomes unreachable, the node upstream of the break will send a PFLR message to the source. Upon the message, the source removes the corresponding path from its route table and then initiates the secondary path discovery by broadcasting an SPREQ to establish the new alternate path.
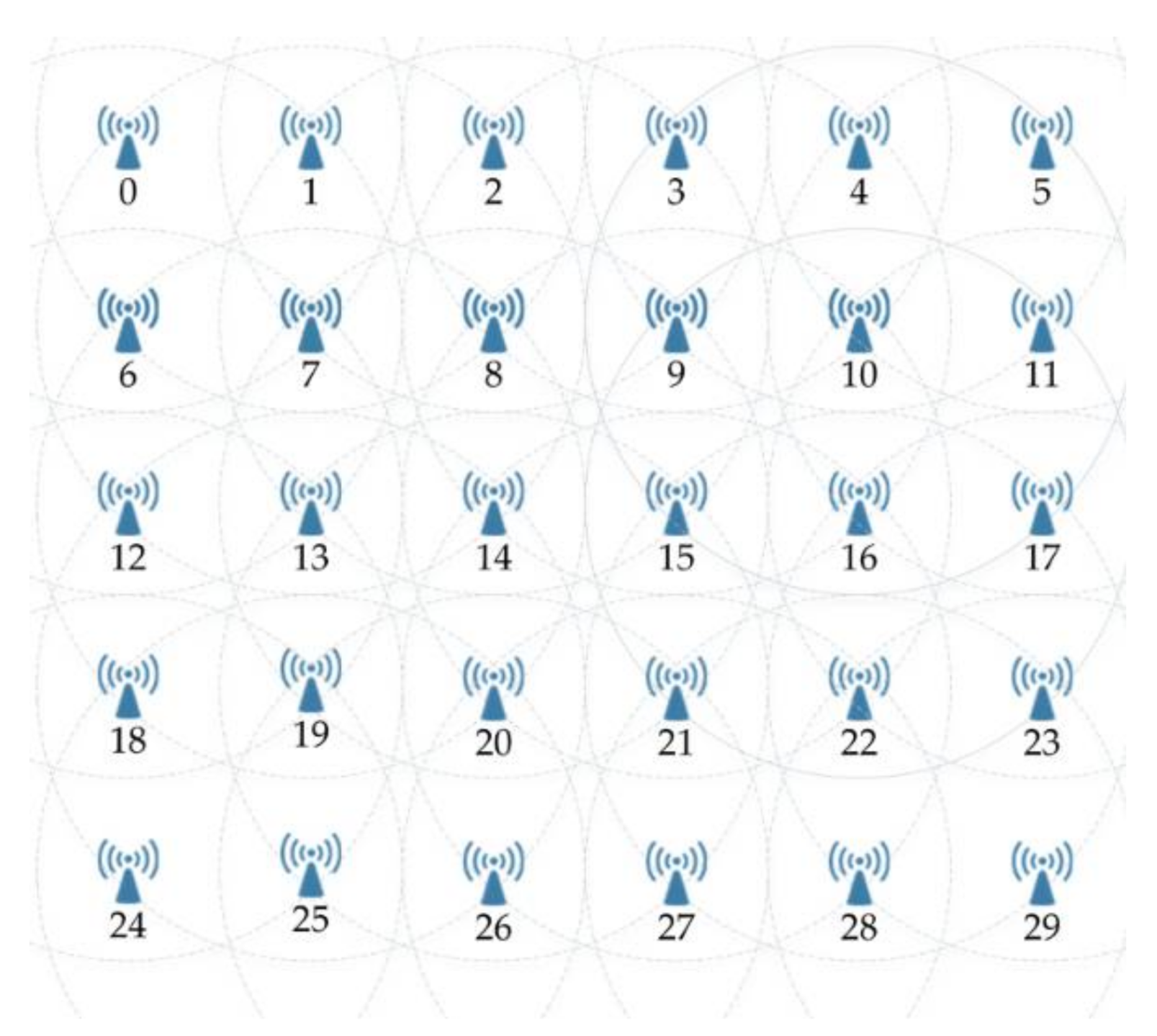
4. Performance Analysis
- Case 1: Source node 0 communicates with destination node 22.
- Case 2: Source node 0 communicates with destination node 24.
4.1. Hop Counts
4.1.1. Under MP-AODV
- Case 1:
- Case 2:
4.1.2. Under NDMR
- Case 1:
- Case 2:
4.2. Control Overhead
4.2.1. Under MP-AODV
- Case 1: Source node 0 communicates with destination node 22:
- Case 2: Source node 0 communicates with destination node 24:
4.2.2. Under NDMR
Two-Way Handshake Process
Three-Way Handshake Process
- Case 1: The route discovery in this case is the two-way handshake process:
- Case 2: The route discovery in this case is the three-way handshake process:
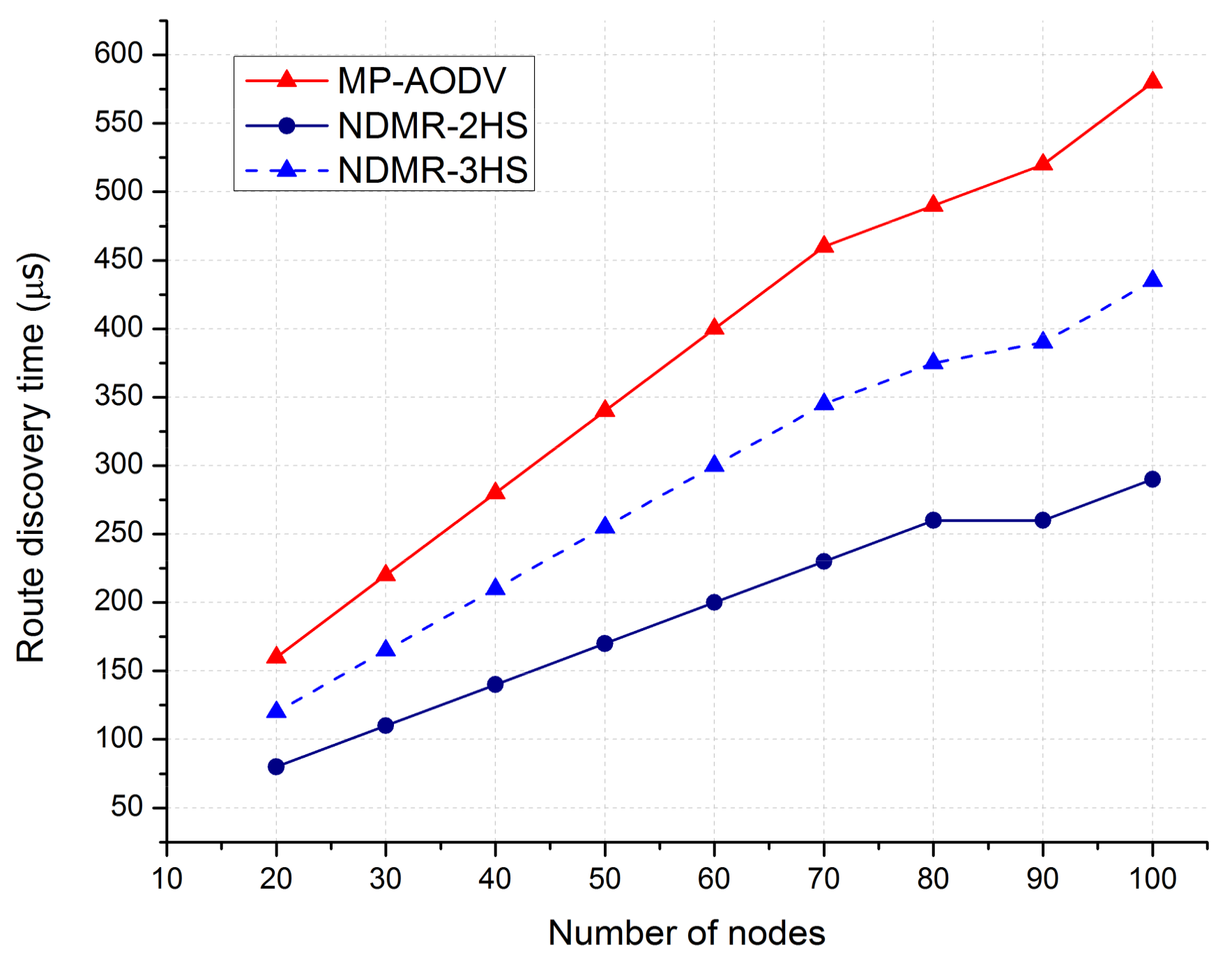
4.3. Route Discovery Time
4.3.1. Under MP-AODV
4.3.2. Under NDMR
Two-Way Handshake Process
Three-Way Handshake Process
5. Simulations and Discussion
5.1. Simulations
5.1.1. Simulation Description
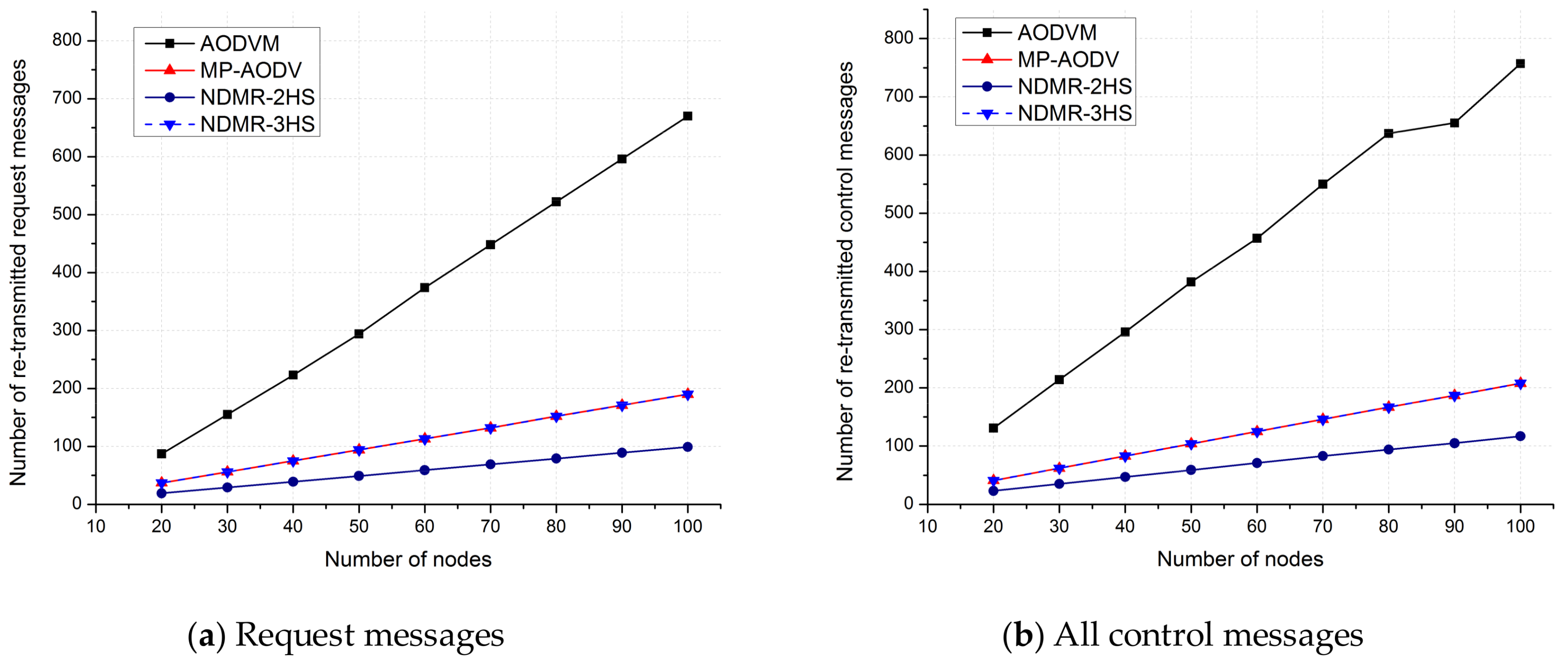
5.1.2. Simulation Results
5.2. Discussion
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Carlo, M.C.; Dharma, P.A. Ad Hoc and Sensor Networks—Theory and Applications, 2nd ed.; World Scientific Publishing Co. Pte. Ltd.: Singapore, 2011. [Google Scholar]
- Callaway, E.H. Wireless Sensor Networks—Architectures and Protocols; Auerbach Publications: Boca Raton, FL, USA, 2004. [Google Scholar]
- Perkins, C.; Belding-Royer, E.; Das, S. Ad hoc On-Demand Distance Vector (AODV) Routing. In Proceedings of the Second IEEE Workshop on Mobile Computing Systems and Applications, New Orleans, LA, USA, 25–26 February 1999. [Google Scholar]
- Tsai, J.; Moors, T. A Review of Multipath Routing Protocols: From Wireless Ad Hoc to Mesh Networks. In Proceedings of the ACoRN Early Career Researcher Workshop on Wireless Multihop Networking, Sydney, Australia, 17–18 July 2006. [Google Scholar]
- Tarique, M.; Tepe, K.E.; Adibi, S.; Erfani, S. Survey of multipath routing protocols for mobile ad hoc networks. J. Netw. Comput. Appl. 2009, 32, 1125–1143. [Google Scholar] [CrossRef]
- Sha, K.; Gehlot, J.; Greve, R. Multipath Routing Techniques in Wireless Sensor Networks: A Survey. Wirel. Pers. Commun. 2013, 70, 807–829. [Google Scholar] [CrossRef]
- Radi, M.; Dezfouli, B.; Bakar, K.A.; Lee, M. Multipath Routing in Wireless Sensor Networks: Survey and Research Challenges. Sensors 2012, 12, 650–658. [Google Scholar] [CrossRef] [PubMed]
- Marina, M.K.; Das, S.R. On-demand Multipath Distance Vector Routing in Ad Hoc Networks. In Proceedings of the International Conference for Network Protocol, Los Angeles, CA, USA, 11–14 November 2001. [Google Scholar] [CrossRef]
- Ye, Z.; Krishnamurthy, S.V.; Tripathi, S.K. A Framework for Reliable Routing in Mobile Ad Hoc Networks. In Proceedings of the Twenty-Second Annual Joint Conference of the IEEE Computer and Communications (INFORCOM 2003), Los Angeles, CA, USA, 30 March–3 April 2003. [Google Scholar] [CrossRef]
- Lee, Y.S.; Chung, S.H. MP-AODV: A New Multipath Routing Protocol Based on AODV in Mobile Ad Hoc Networks. J. Korea Soc. Comput. Inf. 2011, 16, 131–142. [Google Scholar] [CrossRef]
- Taha, A.; Alsaqour, R.; Uddin, M.; Abdelhaq, M.; Saba, T. Energy Efficient Multipath Routing Protocol for Mobile Ad-Hoc Network Using the Fitness Function. IEEE Access 2017, 5, 10369–10381. [Google Scholar] [CrossRef]
- Igartua, M.A.; Frías, V.C. Self-configured multipath routing using path lifetime for video-streaming services over Ad Hoc networks. Comput. Commun. 2010, 33, 1879–1891. [Google Scholar] [CrossRef] [Green Version]
- Kanellopoulos, D. QoS routing for multimedia communication over wireless mobile ad hoc networks: A survey. Int. J. Multimed. Data Eng. Manag. 2017, 8, 42–71. [Google Scholar] [CrossRef]
- Tien, N.X.; Kim, S.; Rhee, J.M.; Park, S.Y. A Novel Dual Separate Paths (DSP) Algorithm Providing Fault-Tolerant Communication for Wireless Sensor Networks. Sensors 2017, 17, 1699. [Google Scholar] [CrossRef] [PubMed]
- Agrawal, J.; Singhal, A.; Yadav, R.N. Multipath Routing in Mobile Ad-hoc Network using Meta-heuristic Approach. In Proceedings of the 2017 International Conference on Advances in Computing, Communications and Informatics (ICACCI), Udupi, India, 13–16 September 2017. [Google Scholar]
- Bennis, I.; Fouchal, H.; Piamrat, K.; Zytoune, O.; Aboutajdine, D. A Realistic Multipath Routing for Ad Hoc Networks. In Proceedings of the 2015 IEEE Global Communications Conference (GLOBECOM), San Diego, CA, USA, 25 February 2016. [Google Scholar]
- Xiao, Y.; Zhao, X.; Wang, H.; Hsu, C.H. Energy-aware multipath routing for data aggregation in wireless sensor networks. In Proceedings of the 2014 20th IEEE International Conference on Parallel and Distributed Systems (ICPADS), Hsinchu, Taiwan, 16–19 December 2014. [Google Scholar]
- Jemili, I.; Tekaya, G.; Belghith, A. A Fast Multipath Routing Protocol for wireless sensor networks. In Proceedings of the 2014 IEEE/ACS 11th International Conference on Computer Systems and Applications (AICCSA), Doha, Qatar, 10–13 November 2014. [Google Scholar]
- Forouzan, B.A. Data Communications and Networking, 4th ed.; McGraw-Hill: Singapore, 2007. [Google Scholar]
- OMNeT++ Discrete Event Simulator Version 4.6. Available online: http://www.omnetpp.org/ (accessed on 15 April 2017).



© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tien, N.X.; Rhee, J.M.; Park, S.Y. A Novel Effective Multipath Routing Technique Providing High Availability in Wireless Networks. Electronics 2018, 7, 42. https://doi.org/10.3390/electronics7040042
Tien NX, Rhee JM, Park SY. A Novel Effective Multipath Routing Technique Providing High Availability in Wireless Networks. Electronics. 2018; 7(4):42. https://doi.org/10.3390/electronics7040042
Chicago/Turabian StyleTien, Nguyen Xuan, Jong Myung Rhee, and Sang Yoon Park. 2018. "A Novel Effective Multipath Routing Technique Providing High Availability in Wireless Networks" Electronics 7, no. 4: 42. https://doi.org/10.3390/electronics7040042




