Wireless Industrial Monitoring and Control Networks: The Journey So Far and the Road Ahead
Abstract
:1. Introduction
2. Overview of Existing Wireless Standards and Protocols
| Item | Protocols | Standards | |||||
|---|---|---|---|---|---|---|---|
| TSMP | 802.15.4e | WISA | ZigBee Pro | WirelessHART | WIA-PA | ISA100.11a | |
| Application Layer | ------ | ------ | Released by ABB for strong real-time requirement such as Factory Automation | ZigBee Application layer | HART command | Multi wired fieldbus protocol interoperability; Virtual device |
|
| Transport Layer | ----- | ------ | ------ | ------ | Connection-orient and connectionless communication, TL acknowledgements, Message-based priority | ------ | TL acknowledgements, Message-based priority and Contract-based priority |
| Network Layer | ------ | ------ | ------ | Distributed Routing Algorithm: AODV, Route Aggregation, Tree routing (in ZigBee) | Extended HART address | Addressing, Fragmentation and reassembly | IPv6 addressing (6LoWPAN) |
| Data Link Layer | Network-wide time synchronization, channel hopping, Channel Blacklisting, Graph and source routing, dedicated slotted unicast communication bandwidth, link-layer ACKs, concurrent link activation, and omitting the poor method for synch such as sending Beacon | Time Slotted Channel Hopping (TSCH) or TSMP, MAC amendment to the existing standard 802.15.4-2006 | TDMA, Channel Hopping | CSMA/CA, Beacon Sync., GTS, Frequency Agility | TSMP features, Superframe Optimization, no frequency reuse for dedicated links | CSMA/CA, TDMA, and FDMA. Channel Hopping (AFH, AFS, and TH) | TSMP features, CSMA/CA (In SH period), Channel Hopping (SH, FH, Hybrid), AFH and BlackListing, Superframe Optimization |
| Physical Layer | Compatible with multi-channel standard such as the IEEE 802.15.4 2006 standard | IEEE 802.15.4, 2.4 GHz, DSSS (Direct-Sequence Spread Spectrum), Data rate 250 Kb/s | IEEE 802.15.1, 2.4 GHz, Data rate 1 Mb/s | IEEE 802.15.4, 2.4 GHz, 868 MHz, 915 MHz, DSSS (Direct-Sequence Spread Spectrum), Data rate 250 Kb/s | IEEE 802.15.4, 2.4 GHz, DSSS (Direct-Sequence Spread Spectrum), Data rate 250 Kb/s | IEEE 802.15.4, 2.4 GHz, DSSS (Direct-Sequence Spread Spectrum), Data rate 250 Kb/s | IEEE 802.15.4, 2.4 GHz, DSSS (Direct-Sequence Spread Spectrum), Data rate 250 Kb/s |
| System Management | Centralized (Coordinates the communication schedule for the network and finding the routes) | Centralized & Distributed | ------ | Distributed | Centralized | Centralized & Distributed (The routing devices, serving as cluster heads, implement the task of an agent of the network manager) | Centralized & Distributed |
| Network Topology | Star, Mesh (Flat topology since all nodes are required to have routing capability) | ------ | Tree, Star (Allows two types of nodes, end devices and cell coordinators) | Tree, Star, Mesh (Allows two classes of nodes RFD and FFD) | Star, Mesh (Flat topology since all nodes are required to have routing capability) | Star, Mesh (The routing and gateway devices deploy the mesh topology. In star topology, which is called a cluster, the routing and field devices are deployed) | Star, Mesh (Nodes with and without routing capability) |
| Network Scalability | ------ | ------ | Three Cells, 120 end device in each cell | 16-bit node address and 16-bit group address or 64-bit extended network address (Replace tree adressing with stochanstic addressing and allows thousands of nodes) | 16-bit network address and 16-bit nickname and 64-bit address (Does not allow such large numbers) | 64-bit physical address (EUI-64) and a 16-bit network address (short address) | 64-bit network address and 64-bit device address (Allows multiple subnets each with 30,000 of nodes) |
| System management: Time measurement | Network-wide time synchronization | Network-wide time synchronization | ------ | Beacon Enabled and non-beacon Enabled mode (no syncronization) | Time measured in absolute slot counts that is translated to UTC | All nodes align to UTC/TAI time | Time is measured using International Atomic Time (TAI) |
| System management: Timeslot Duration | Flexible | Fixed timeslot duration, 64 and 128 μs | Flexible | All slots are 10 ms | All slots are 10 ms | Configurable timeslot duration: Timeslot duration is set by the system manager to a specific value. Timeslot duration of 10–12 ms is a typical value | |
| Important Strength | Solves the time synchronization problem in a more energy-efficient manner by relying on ACKs to exchange timing offset information, Multipath routing | Low Power Consumption, Reliability, Robustness, Enhance and add functionality to the 802.15.4-2006 MAC to better support the industrial markets | High data rate, Minimum delay, Robustness | Scalability | Low Power Consumption, Reliability, Robustness, Multipath routing, Coexistence with other | Reliability, Using AFH for intra-cluster communications, Two-level packet aggregation | Scalability, Reliability, Robustness, Coexistence with other, Integration with internet, Low Power Consumption and Energy savings (adjustable transmission power of individual nodes), Multipath routing, Interoperability, Using field device aggregation. |
| Important Drawback | Dependent to the Centralized System Management, In the case of Distributed Management, a mechanism is missing which allows each pair of neighbor nodes to agree on cells to communicate on | TSMP Drawback | Interoperability, Multipath routing | Reliability, Multipath routing, Realtime, Robustness, Beacon transmision not permitted in mesh networks and introduces a larger overhead in terms of higher energy consumption as the radio needs to remain in listen mode for long periods | Scalability, Using blind channel hopping and not using ACH, Lack of centralized network management algorithm | Proving synchronization by beacon transmission, Supporting hybrid topology, Multipath routing, Lack of centralized/Distributed network management algorithm | Using blind channel hopping and not using ACH, Lack of centralized/Distributed network management algorithm as well as node’s transmission power adjustment algorithm |
3. Critical Metrics for Industrial Monitoring and Control
3.1. Real Time Capability
| Category | Class | Application | Description |  |
| Safety | 0 | Emergency action | Always critical e.g., Instrumented protective systems/Safeguarding systems | |
| Control | 1 | Closed-loop regulatory control | Often critical e.g., Regular control loops | |
| 2 | Closed-loop supervisory control | Usually noncritical e.g., Set point manipulation for control system optimization | ||
| 3 | Open-loop control | Human in loop e.g., Manual human actions on alerts | ||
| Monitoring | 4 | Alerting | Short-term operational consequence e.g., Short term operational consequence, event-based maintenance | |
| 5 | Logging and downloading/uploading | No immediate operational consequence e.g. history collection, sequence-of-events, preventive maintenance |
3.2. Scalability
3.3. Power Consumption
3.4. Reliability
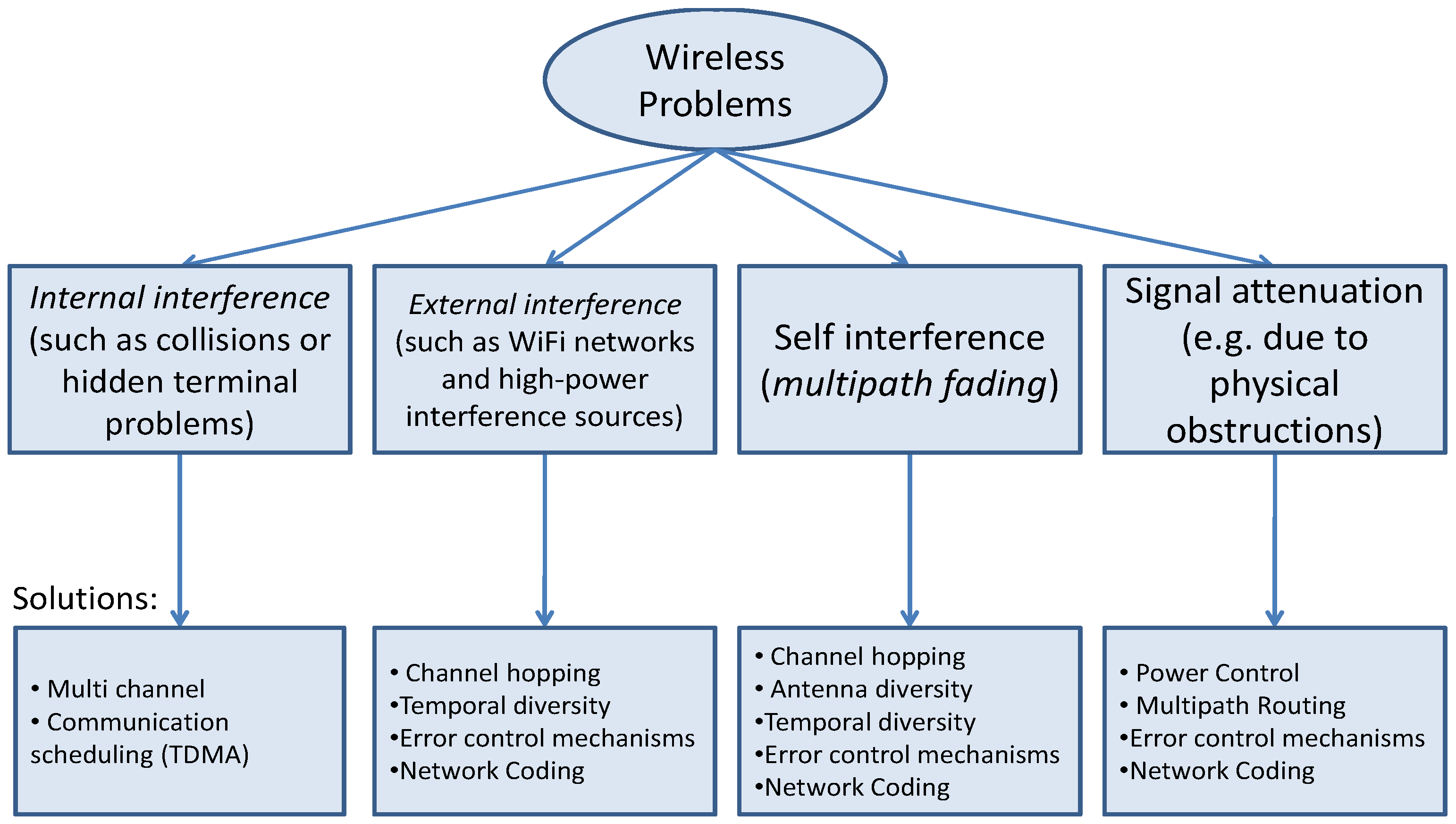
4. Techniques Used in Academia to Improve Performance Metrics
4.1. Mechanisms to Improve Reliability
4.1.1. Diversity
Spatial Diversity and Cooperative Diversity
Temporal Diversity
Frequency Diversity
4.1.2. Error Control Mechanisms
4.1.3. Multipath Routing
4.1.4. Network Coding
4.2. Mechanisms to Improve Latency and Real-Time Capability
4.2.1. MAC Protocols to Improve Latency
Contention-Free (Scheduled Communication)
Contention-Based
4.2.2. Routing Protocols to Improve Latency
5. Mechanisms Used by Industrial Technologies to Improve Performance Metrics
5.1. MAC Layer Contention Mechanism and Communication Scheduling

5.2. Priority Management Schemes
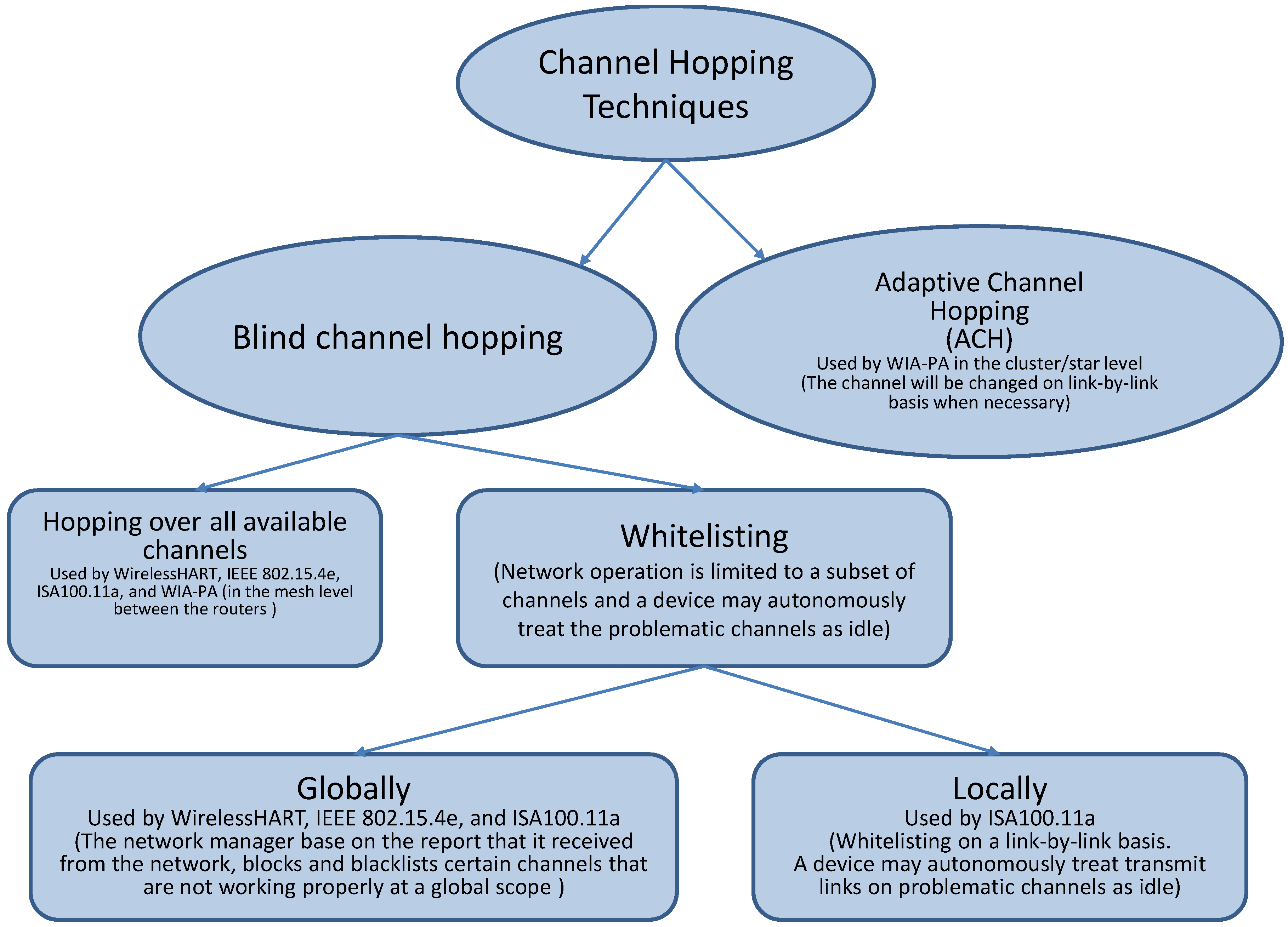
5.3. Channel Hopping Techniques
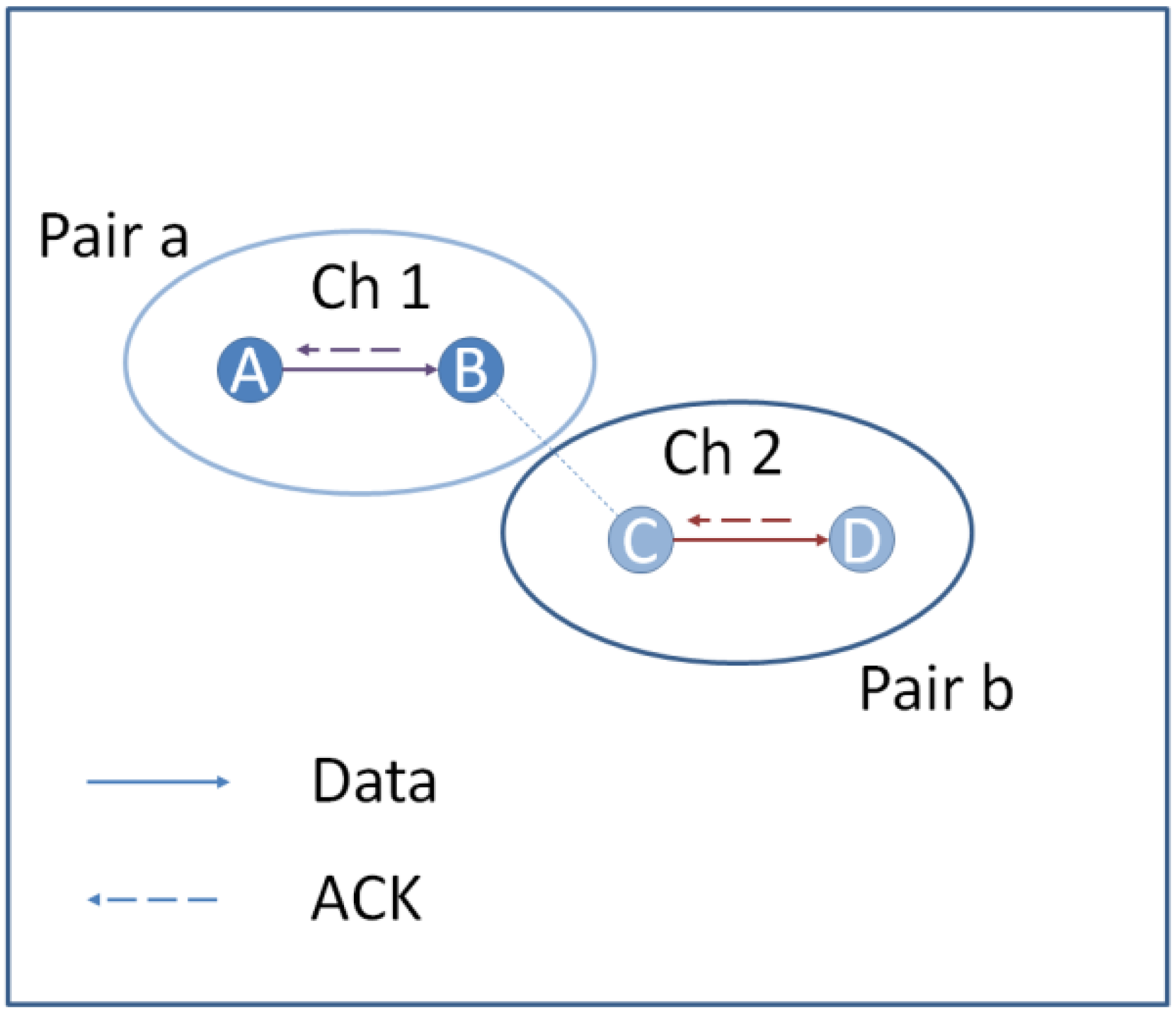
5.4. Multipath Routing
6. Physical Layer Aspects


 [dB] is a Gauss distributed random variable with a certain mean and
[dB] is a Gauss distributed random variable with a certain mean and  variance generated due to the shadowing effect. In the case of a home environment,
variance generated due to the shadowing effect. In the case of a home environment,  is generally considered as a zero mean random variable. However, in the industrial environment, we expect large shadowing due to the presence of heavy machinery, which typically causes a positive biased shadowing effect. The mean of the shadow fading can vary according to different industrial setups.
is generally considered as a zero mean random variable. However, in the industrial environment, we expect large shadowing due to the presence of heavy machinery, which typically causes a positive biased shadowing effect. The mean of the shadow fading can vary according to different industrial setups.
 falls below the minimum required SNR, γ0 for the pre-defined acceptable communication performance [63]. Mathematically,
falls below the minimum required SNR, γ0 for the pre-defined acceptable communication performance [63]. Mathematically, 


 is the SNR per bit; fb is the channel data rate (net bitrate) and B is the channel bandwidth [64]. As CdB = Pr and for the QPSK modulation,
is the SNR per bit; fb is the channel data rate (net bitrate) and B is the channel bandwidth [64]. As CdB = Pr and for the QPSK modulation,  , Equation (6) can be rewritten as:
, Equation (6) can be rewritten as:
7. Open Research Areas
7.1. A Distributed Approach to Achieving Real-Time Operation
7.2. Distributed Network Management
7.3. Adaptive Channel Hopping (ACH) Algorithms
7.4. Distributed or Centralized Radio Transmission Power Control
7.5. Network Management Algorithms for Different Traffic Patterns
7.6. In-Network Data Aggregation for Control Operations
7.7. Applying MIMO and OFDM in Physical Layer
8. Conclusions
Acknowledgements
References and Notes
- Berge, J. Fieldbuses for Process Control: Engineering, Operation, and Maintenance; ISA: Research Triangle Park, NC, USA, 2001. [Google Scholar]
- Gungor, V.C.; Hancke, G.P. Industrial wireless sensor networks: Challenges, design principles, and technical approaches. IEEE Trans. Ind. Electron. 2009, 56, 4258–4265. [Google Scholar]
- Willig, A.; Matheus, K.; Wolisz, A. Wireless technology in industrial networks. Proc. IEEE 2005, 93, 1130–1151. [Google Scholar] [CrossRef]
- IEEE Standard for Local and Metropolitan Area Networks—Part 15.4: Low-Rate Wireless Personal Area Networks (LR-WPANs); IEEE Stdandard 802.15.4-2011 (Revision of IEEE Std 802.15.4-2006), 2011.
- Scheible, G.; Dacfey, D.; Endresen, J.; Frey, J.E. Unplugged but connected [Design and implementation of a truly wireless real-time sensor/actuator interface]. IEEE Ind. Electron. Mag. 2007, 1, 25–34. [Google Scholar]
- ZigBee PRO Specification; ZigBee Alliance Standard, October 2007.
- British Standards Institute, Industrial Communication Networks-Fieldbus Specifications, WirelessHART Communication Network and Communication Profile, 1.0, 2009; IEC/PAS 62591.
- Liang, W.; Zhang, X.; Xiao, Y.; Wang, F.; Zeng, P.; Yu, H. Survey and experiments of WIA-PA specification of industrial wireless network. Wirel. Commun. Mob. Comput. 2011, 11, 1197–1212. [Google Scholar] [CrossRef]
- The International Society of Automation, Wireless Systems for Industrial Automation: Process Control and Related Applications; ISA Standard ISA-100.11a-2011, 2009.
- IEEE Standard for Local and Metropolitan Area Networks--Part 15.4: Low-Rate Wireless Personal Area Networks (LR-WPANs) Amendment 1: MAC Sublayer; IEEE Stdandard 802.15.4e-2012 (Amendment to IEEE Std 802.15.4-2011), 2012.
- Pister, K.; Doherty, L. TSMP: Time Synchronized Mesh Protocol. In Proceedings of IASTED Distributed Sensor Networks, Orlando, FL, USA, 16–18 November 2008; pp. 391–398.
- Zurawski, R. Networked Embedded Systems; CRC Press: Boca Raton, FL, USA, 2009. [Google Scholar]
- Christin, D.; Mogre, P.S.; Hollick, M. Survey on wireless sensor network technologies for industrial automation: The security and quality of service perspectives. Future Internet 2010, 2, 96–125. [Google Scholar] [CrossRef]
- Tse, D.; Viswanath, P. Fundamentals of Wireless Communication; Cambridge University Press: Cambridge, UK, 2005. [Google Scholar]
- Ketcham, R.; Frolik, J. A Low-Complexity, Compact Antenna for Mitigating Frequency-Selective Fading. In Proceedings of the 6th International Symposium on Information Processing in Sensor Networks (IPSN 2007), Cambridge, MA, USA, 25–27 April 2007; pp. 573–574.
- Liang, J.; Liang, Q. Channel Selection Algorithms in Virtual MIMO Sensor Networks. In Proceedings of the 1st ACM International Workshop on Heterogeneous Sensor and Actor Networks, Hong Kong, China, 30 May 2008; pp. 73–80.
- Nethi, S.; Jantti, R.; Nassi, V. Time and Antenna Diversity in Wireless Sensor and Actuator Networks. In Proceedings of 2009 IEEE the 9th Malaysia International Conference on Communications (MICC), Kuala Lumpur, Malaysia, 15–17 December 2009; pp. 932–937.
- Giorgetti, G.; Cidronali, A.; Gupta, S.K.S.; Manes, G. Exploiting Low-Cost Directional Antennas in 2.4 GHz IEEE 802.15.4 Wireless Sensor Networks. In Proceedings of 2007 European Conference on Wireless Technologies, Kuala Lumpur, Malaysia, 8–10 October 2007; pp. 217–220.
- Santivanez, C.; Redi, J. On the use of Directional Antennas for Sensor Networks. In Proceedings of 2003 IEEE Military Communications Conference (MILCOM ’03), Boston, MA, USA, 13–16 October 2003; 971, pp. 670–675.
- Laneman, J.N.; Wornell, G.W. Distributed space-time-coded protocols for exploiting cooperative diversity in wireless networks. IEEE Trans. Inf. Theory 2003, 49, 2415–2425. [Google Scholar] [CrossRef]
- Sendonaris, A.; Erkip, E.; Aazhang, B. User cooperation diversity. Part I. System description. IEEE Trans. Commun. 2003, 51, 1927–1938. [Google Scholar] [CrossRef]
- Nosratinia, A.; Hunter, T.E.; Hedayat, A. Cooperative communication in wireless networks. IEEE Commun. Mag. 2004, 42, 74–80. [Google Scholar] [CrossRef]
- Hong, Y.W.; Huang, W.J.; Chiu, F.H.; Kuo, C.C.J. Cooperative communications in resource-constrained wireless networks. IEEE Signal Proc. Mag. 2007, 24, 47–57. [Google Scholar]
- Ochiai, H.; Mitran, P.; Tarokh, V. Design and Analysis of Collaborative Diversity Protocols for Wireless Sensor Networks. In Proceedings of 2004 IEEE 60th Vehicular Technology Conference (VTC2004-Fall), Los Angeles, CA, USA, 26–29 September 2004; 4647, pp. 4645–4649.
- Xuedong, L.; Min, C.; Yang, X.; Balasingham, I.; Leung, V.C.M. A Novel Cooperative Communication Protocol for QoS Provisioning in Wireless Sensor Networks. In Proceedings of the 5th International Conference onTestbeds and Research Infrastructures for the Development of Networks & Communities and Workshops (TridentCom 2009), Washington, DC, USA, 6–8 April 2009; pp. 1–6.
- Watteyne, T.; Lanzisera, S.; Mehta, A.; Pister, K.S.J. Mitigating Multipath Fading through Channel Hopping in Wireless Sensor Networks. In Proceedings of 2010 IEEE International Conference on Communications (ICC), Cape Town, South Africa, 23–27 May 2010; pp. 1–5.
- Watteyne, T.; Mehta, A.; Pister, K. Reliability through Frequency Diversity: Why Channel Hopping Makes Sense. In Proceedings of the 6th ACM Symposium on Performance Evaluation of Wireless ad hocSensorand Ubiquitous Networks, Tenerife, Spain, 28–29 October 2009; pp. 116–123.
- Liu, R.; Yan, W.; Wassell, I.J.; Soga, K. Can Frequency Diversity Provide Performance Gains for WSNs at 2.4GHz for the Fire Hydrant to above Ground Channel. In Proceedings of Antennas & Propagation Conference (LAPC 2009), Leicestershire, UK, 16–17 November 2009; pp. 545–548.
- Kusy, B.; Richter, C.; Wen, H.; Afanasyev, M.; Jurdak, R.; Brunig, M.; Abbott, D.; Cong, H.; Ostry, D. Radio Diversity for Reliable Communication in WSNs. In Proceedings of 2011 10th International Conference on Information Processing in Sensor Networks (IPSN), Chicago, IL, USA, 12–14 April 2011; pp. 270–281.
- Ortiz, J.; Culler, D. Multichannel Reliability Assessment in Real World WSNs. In Proceedings of the 9th ACM/IEEE International Conference on Information Processing in Sensor Networks, Stockholm, Sweden, 12–16 April 2010; pp. 162–173.
- Gonga, A.; Landsiedel, O.; Soldati, P.; Johansson, M. Multi-Channel Communication vs. Adaptive Routing for Reliable Communication in WSNs. In Proceedings of the 11th International Conference on Information Processing in Sensor Networks, Beijing, China, April 2012; pp. 125–126.
- Vuran, M.C.; Akyildiz, I.F. Cross-Layer Analysis of Error Control in Wireless Sensor Networks. In Proceedings of the 3rd Annual IEEE Communications Society on Sensor and Ad Hoc Communications and Networks (SECON ’06), Reston, VA, USA, 28–28 September 2006; pp. 585–594.
- Vuran, M.C.; Akyildiz, I.F. Error control in wireless sensor networks: A cross layer analysis. IEEE/ACM Trans. Netw. 2009, 17, 1186–1199. [Google Scholar] [CrossRef]
- Biswas, R.; Jain, V.; Ghosh, C.; Agrawal, D.P. On-Demand Reliable Medium Access in Sensor Networks. In Proceedings of the 2006 International Symposium on on World of WirelessMobile and Multimedia Networks, Buffalo, NY, USA, 26–29 June 2006; pp. 251–257.
- Shigang, C.; Nahrstedt, K. An overview of quality of service routing for next-generation high-speed networks: Problems and solutions. IEEE Netw. 1998, 12, 64–79. [Google Scholar] [CrossRef]
- Ganesan, D.; Govindan, R.; Shenker, S.; Estrin, D. Highly-resilient, energy-efficient multipath routing in wireless sensor networks. SIGMOBILE Mob. Comput. Commun. Rev. 2001, 5, 11–25. [Google Scholar]
- Dulman, S.; Nieberg, T.; Wu, J.; Havinga, P. Trade-off between Traffic Overhead and Reliability in Multipath Routing for Wireless Sensor Networks. In Proceeding of 2003 IEEE Wireless Communications and Networking (WCNC 2003), New Orleans, LA, USA, 20–20 March 2003; 1913, pp. 1918–1922.
- Deb, B.; Bhatnagar, S.; Nath, B. ReInForM: Reliable Information Forwarding Using Multiple Paths in Sensor Networks. In Proceedings of the 28th Annual IEEE International Conference on Local Computer Networks (LCN ’03), Bonn/Königswinter, Germany, 20–24 October 2003; pp. 406–415.
- Huang, X.; Fang, Y. Multiconstrained QoS multipath routing in wireless sensor networks. Wirel. Netw. 2008, 14, 465–478. [Google Scholar] [CrossRef]
- Matsuda, T.; Noguchi, T.; Takine, T. Survey of network coding and its applications. IEICE Trans. Commun. 2011, 94, 698–717. [Google Scholar]
- Al-Kofahi, O.M.; Kamal, A. Network coding-based protection of many-to-one wireless flows. IEEE J. Sel. Areas Commun. 2009, 27, 797–813. [Google Scholar] [CrossRef]
- Widmer, J.; Boudec, J.-Y.L. Network Coding for Efficient Communication in Extreme Networks. In Proceedings of the 2005 ACM SIGCOMM Workshop on Delay-Tolerant Networking, Philadelphia, PA, USA, August 2005; pp. 284–291.
- Yunfeng, L.; Liang, B.; Baochun, L. Passive Loss Inference in Wireless Sensor Networks Based on Network Coding. In Proceedings of IEEE INFOCOM 2009, Rio De Janeiro, Brazil, 19–25 April 2009; pp. 1809–1817.
- Shah-Mansouri, V.; Wong, V.W.S. Link Loss Inference in Wireless Sensor Networks with Randomized Network Coding. In Proceedings of 2010 IEEE Global Telecommunications Conference (GLOBECOM 2010), Miami, FL, USA, 6–10 December 2010; pp. 1–6.
- Ergen, S.C.; Varaiya, P. PEDAMACS: Power efficient and delay aware medium access protocol for sensor networks. IEEE Trans. Mob. Comput. 2006, 5, 920–930. [Google Scholar] [CrossRef]
- Chintalapudi, K.K.; Venkatraman, L. On the Design of MAC Protocols for Low-Latency Hard Real-Time Discrete Control Applications over 802.15.4 Hardware. In Proceedings of International Conference on Information Processing in Sensor Networks (IPSN ’08), Louis, MO, USA, 22–24 April 2008; pp. 356–367.
- Salajegheh, M.; Soroush, H.; Kalis, A. HYMAC: Hybrid TDMA/FDMA Medium Access Control Protocol for Wireless Sensor Networks. In Proceedings of IEEE the 18th International Symposium on PersonalIndoor and Mobile Radio Communications (PIMRC 2007), Athens, Greece, 3–7 September 2007; pp. 1–5.
- Ye, W.; Heidemann, J.; Estrin, D. Medium access control with coordinated adaptive sleeping for wireless sensor networks. IEEE/ACM Trans. Netw. 2004, 12, 493–506. [Google Scholar] [CrossRef]
- Wei, Y.; Heidemann, J.; Estrin, D. An Energy-Efficient MAC Protocol for Wireless Sensor Networks. In Proceedings of IEEE INFOCOM 2002. Twenty-First Annual Joint Conference of the IEEE Computer and Communications Societies, New York, NY, USA, 23–27 June 2002; 1563, pp. 1567–1576.
- van Dam, T.; Langendoen, K. An Adaptive Energy-Efficient MAC Protocol for Wireless Sensor Networks; ACM: New York, NY, USA, 2003; pp. 171–180. [Google Scholar]
- Lin, P.; Qiao, C.; Wang, X. Medium Access Control with a Dynamic Duty Cycle for Sensor Networks. In Proceedings of 2004 IEEE Wireless Communications and Networking Conference (WCNC), Atlanta, GA, USA, 21–25 March 2004; 1533, pp. 1534–1539.
- Namboodiri, V.; Keshavarzian, A. Alert: An Adaptive Low-Latency Event-Driven MAC Protocol for Wireless Sensor Networks. In Proceedings of the 7th International Conference on Information Processing in Sensor Networks, St. Louis, MO, USA, 22–24 April 2008; pp. 159–170.
- Lu, G.; Krishnamachari, B.; Raghavendra, C.S. An Adaptive Energy-Efficient and Low-Latency MAC for Data Gathering in Wireless Sensor Networks. In Proceedings of the 18th InternationalParallel and Distributed Processing Symposium, Santa Fe, NM, USA, 26–30 April 2004; p. 224.
- Vasanthi, N.A.; Annadurai, S. Energy Efficient Sleep Schedule for Achieving Minimum Latency in Query based Sensor Networks. In Proceedings of IEEE International Conference on Sensor NetworksUbiquitousand Trustworthy Computing, Taichung, Taiwan, 5–7 June 2006; pp. 214–219.
- Xue, Y.; Vaidya, N.H. A Wakeup Scheme for Sensor Networks: Achieving Balance between Energy Saving and End-to-End Delay. In Proceedings of the 10th IEEE Real-Time and Embedded Technology and Applications Symposium (RTAS 2004), Toronto, ON, Canada, 25–28 May 2004; pp. 19–26.
- Ruzzelli, A.G.; O’Hare, G.M.P.; O’Grady, M.J.; Tynan, R. MERLIN: A Synergetic Integration of MAC and Routing Protocol for Distributed Sensor Networks. In Proceedings of the 3rd Annual IEEE Communications Society on Sensor and Ad Hoc Communications and Networks (SECON ’06), Reston, VA, USA, 28–28 September 2006; pp. 266–275.
- Akkaya, K.; Younis, M. An Energy-Aware QoS Routing Protocol for Wireless Sensor Networks. In Proceedings of the 23rd International Conference on Distributed Computing Systems Workshops, Providence, RI, USA, 19–22 May 2003; pp. 710–715.
- Tian, H.; Stankovic, J.A.; Chenyang, L.; Abdelzaher, T. SPEED: A Stateless Protocol for Real-Time Communication in Sensor Networks. In Proceedings of the 23rd International Conference on Distributed Computing Systems, Providence, RI, USA, 19–22 May 2003; pp. 46–55.
- Willig, A. Recent and emerging topics in wireless industrial communications: A selection. IEEE Trans. Ind. Inf. 2008, 4, 102–124. [Google Scholar] [CrossRef]
- International Organization for Standardization (ISO), Road Vehicles–Controller Area Network; ISO 11898-1:2003, International Organization for Standardization: Geneva, Switzerland, 2003.
- Kerkez, B.; Watteyne, T.; Magliocco, M.; Glaser, S.; Pister, K. Feasibility Analysis of Controller Design for Adaptive Channel Hopping. In Proceedings of the Fourth International ICST Conference on Performance Evaluation Methodologies and Tools, Pisa, Italy, 20–22 October 2009; pp. 1–6.
- Goyal, M.; Prakash, S.; Xie, W.; Bashir, Y.; Hosseini, H.; Durresi, A. Evaluating the Impact of Signal to Noise Ratio on IEEE 802.15.4 PHY-Level Packet Loss Rate. In Proceedings of 2010 13th International Conference on Network-Based Information Systems (NBiS), Takayama, Japan, 14–16 September 2010; pp. 279–284.
- Goldsmith, A. Wireless Communications; Cambridge University Press: Cambridge, UK, 2005. [Google Scholar]
- Jee-Hye, L.; Myung-Sun, B.; Hyoung-Kyu, S. Efficient MIMO receiving technique in IEEE 802.11n system for enhanced services. IEEE Trans. Consum. Electron. 2007, 53, 344–349. [Google Scholar] [CrossRef]
- IEEE Standard for Information Technology—Telecommunications and Information Exchange Between Systems—Local and Metropolitan Area Networks—Specific Requirements Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications; IEEE Stdandard 802.11e-2005 (Amendment 8: Medium Access Control (MAC) Quality of Service Enhancements), 2005.
- Lin, S.; Zhang, J.; Zhou, G.; Gu, L.; Stankovic, J.A.; He, T. ATPC: Adaptive Transmission Power Control for Wireless Sensor Networks. In Proceedings of the 4th International Conference on Embedded Networked Sensor Systems, Boulder, CO, USA, 19–22 June 2006; pp. 223–236.
- Hackmann, G.; Chipara, O.; Lu, C. Robust Topology Control for Indoor Wireless Sensor Networks. In Proceedings of the 6th ACM Conference on EMBEDDED Network Sensor Systems, Raleigh, NC, USA, 5–7 November 2008; pp. 57–70.
- Haibo, Z.; Soldati, P.; Johansson, M. Optimal Link Scheduling and Channel Assignment for Convergecast in Linear WirelessHART Networks. In Proceedings of the 7th International Symposium on Modeling and Optimization in MobileAd Hocand Wireless Networks (WiOPT 2009), Seoul, Korea, 23–27 June 2009; pp. 1–8.
- Soldati, P.; Zhang, H.; Johansson, M. Deadline-Constrained Transmission Scheduling and Data Evacuation in Wirelesshart Networks. In Proceedings of 10th European Control Conference (ECC), Budapest, Hungary, 23–26 August 2009.
- Zhang, H.; Soldati, P.; Johansson, M. Efficient Link Scheduling and Channel Hopping for Convergecast in Wirelesshart Networks; Techchnical Report; School of Electrical Engineering, Royal Institute of Technology (KTH): Stockholm, Sweden, 2009. [Google Scholar]
- Ahmad, M.R.; Dutkiewicz, E.; Xiaojing, H. BER-Delay Characteristics Analysis of IEEE 802.15.4 Wireless Sensor Networks with Cooperative MIMO. In Proceedings of Asia-Pacific Conference on Applied Electromagnetics (APACE 2007), Melaka, Malaysia, 4–6 December 2007; pp. 1–5.
© 2012 by the authors; licensee MDPI, Basel, Switzerland. This article is an open-access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/3.0/).
Share and Cite
Zand, P.; Chatterjea, S.; Das, K.; Havinga, P. Wireless Industrial Monitoring and Control Networks: The Journey So Far and the Road Ahead. J. Sens. Actuator Netw. 2012, 1, 123-152. https://doi.org/10.3390/jsan1020123
Zand P, Chatterjea S, Das K, Havinga P. Wireless Industrial Monitoring and Control Networks: The Journey So Far and the Road Ahead. Journal of Sensor and Actuator Networks. 2012; 1(2):123-152. https://doi.org/10.3390/jsan1020123
Chicago/Turabian StyleZand, Pouria, Supriyo Chatterjea, Kallol Das, and Paul Havinga. 2012. "Wireless Industrial Monitoring and Control Networks: The Journey So Far and the Road Ahead" Journal of Sensor and Actuator Networks 1, no. 2: 123-152. https://doi.org/10.3390/jsan1020123




