Delegation Based User Authentication Framework over Cognitive Radio Networks
Abstract
:1. Introduction
2. Overview of ECMA-392: Cognitive Radio Standard
2.1. Cognitive Radio Technology
- -
- Spectrum sensing: Ability to scan the spectral band, identify vacant channels available for opportunistic transmission and determine a list of spectrum bands that are available. Since SUs do not get any direct feedback from PUs regarding their transmission, SUs have to depend on their own individual or cooperative sensing ability to detect PU transmissions.
- -
- Spectrum analysis and decision: It decides on the most appropriate band from the list of available bands according to their quality of service requirements. It is important to characterize the spectrum band in terms of both radio environment and the statistical behaviors of the PUs.
- -
- Spectrum sharing: It provides the capability to share the spectrum resource opportunistically with multiple SUs which allocates resources to avoid interference caused to the PUs. This function necessitates a CR medium access control (MAC) protocol, which facilitates the sensing control to distribute the sensing task among the coordinating SUs as well as spectrum access to determine the timing for transmission.
- -
- Spectrum mobility: It refers to the agility of CRNs to dynamically switch between spectrum accesses. As SUs are not guaranteed continuous spectrum access in any of the licensed bands and the availability of vacant spectrum bands frequently changes over time, spectrum mobility becomes an important factor when designing cognitive protocols.From this definition, two main characteristics of the CR can be defined as follows [25]
- -
- Unlicensed usage of spectrum: In spectrum sharing, the FCC allocates spectrum for unlicensed or shared services.
- -
- Higher priority of PUs: When an PU is detected in a given band, all SUs avoid accessing that band. However, when a SU is detected, other SUs may choose to share that same band. In other words, PUs have higher priority than SUs in accessing spectrum resources.
2.2. ECMA-392
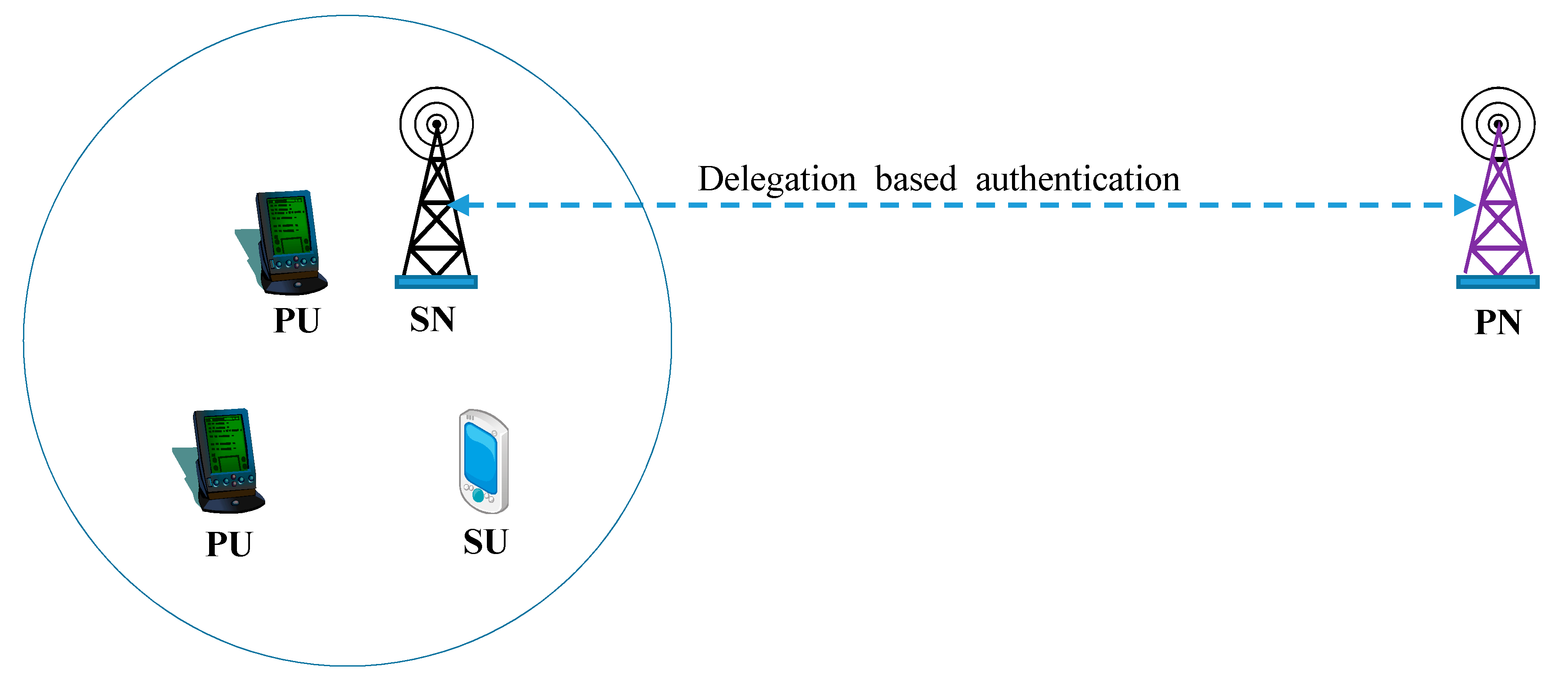
2.3. Assumed System Model
3. CRN Threats and Required Features
3.1. Threats on CRN
- -
- Selfish nodes: They seek to maximize their own gains at the expense of others.
- -
- Malicious nodes: They act to degrade the system or individual node performance with no explicit intention to maximize their own gains and act as a PU and transmit false information to the SU.
3.2. Required Security and Privacy Features
- -
- Authentication: It assures that the communicating entity is the one that it claims to be. There is an inherent requirement to distinguish between PUs and SUs. Therefore, authentication can be considered as one of the basic requirements for the security and privacy of CRNs. The primary objective of an authentication is to prevent unauthorized users from gaining access to the protected systems. It is a necessary procedure for verifying both an entity’s identity and authority. Several aspects of authentication issues should be considered when securing collaborative works in CRNs.
- -
- Unlinkability: Different communication sessions associated with the same user should not be linkable. An adversary cannot link the communication activities of a particular user together and thus establish the user’s profile, which contains much private information.
- -
- Context privacy: An adversary should not be able to learn the exact access context information (duration, type of service request, etc.) of a SU without the SU’s prior approval or knowledge.
- -
- Anonymity: The identity of the origin and the destination of a conversation is hidden from adversaries unless it is intentionally disclosed by the user. Anonymity mechanisms should allow SUs to use the network services while protecting the identity or other identification information from possible abuse. For keeping SU anonymous, there should not be possibility to link any parameters of the SU identity with any context-based information.
- -
- PU protection: SUs can borrow idle spectrum from those who hold licensees, PUs, without causing harmful interference. Unlike traditional radios, CRs constantly monitor the spectrum and intelligently share the spectrum in an opportunistic manner, both in licensed and unlicensed bands. The most important regulatory aspect of these networks is that SUs must relinquish their operating channels and move to another available channel as soon as they learn or sense the presence of a PU on that channel.
- -
- No registration: A fundamental characteristic of a CR is its ability for spectrum sensing, as it shall use the spectrum in an opportunistic manner. This means that the SU has to vacate a currently used spectrum band if a PU signal is detected. Thereby, it is necessary for SUs not to be registered to SN.
- -
- Conditional traceability: Under SU misbehavior, the SU acts maliciously by providing false information about sensing and resource requirements. By doing so, they can either access more resources or prevent other SUs from gaining fair access. Thereby, both of SN and PN need to take rights to trace the misbehaving users.
4. Delegation Based User Authentication Framework
4.1. Setup and Registration
4.2. Online Authentication
- Step1
- SU sends a login request to SN.
- Step2
- SN generates a new random number n1, selects the permitted number of sessions, n and makes a response {IDSN, n1, n} to SU, where IDSN is the identity of SN.
- Step3
- SU inserts his (or her) smart card into the card reader and inputs IDSU and PWSU. Smart card generates two random numbers t and n2, computes a hash chain N1 = h (N2), N2 = h (N3), … , Nn-1 = h (Nn) and Nn = h (n1||n2), stores the hash chain in its memory and sets N1 as its current secret of the session. Note that N1 could be computed after applying n times of hash operations from both of n1 and n2. After that, smart card computes d = D ⊕ h (IDSU||PWSU), AIDSU = h (IDSU||d), APWSU = h (PWSU||d), (K,σ) = W ⊕ h (AIDSU||APWSU), r1 = t·P, r2 = h(t·Yv)⊕(K, N1) and v1 = σ·h (IDSN||IDPN||N1||n1||r1||r2)+t mod p, and makes a response {IDSN, IDPN, r1, r2, v1} to SN.
- Step4
- SN first uses xv to retrieve K and N1 by computing r2⊕h(xv·r1). After that, SN computes v1·P and h(IDSN||IDPN||N1||n1||r1||r2)(V·f(K))+r1 mod p, and verifies whether the two computed values are the same. If the verification is successful, SN computes CT1 = [N1||n1||K]KPS and v2 = h(IDSN||IDPN||N1||CT1), which []KPS is an encryption based on the symmetric key cryptosystem like AES by using the encryption key KPS, and sends {IDSN, IDPN, CT1, v2} to PN. Otherwise, SN denies the login request.
- Step5
- PN obtains N1, n1 and K by decrypting CT1 with the secret key KPS. After that, PN computes its corresponding σ = x·f(K) mod q and v2′ = h(IDSN||IDPN||N1||CT1), and validates v2 by checking whether it is the same with v2′. Only if the verification is successful, PN generates a random number n3, computes SKPU = h(N1||n1||σ), CT2 = [N1||n3||IDSN]SKPU and CT3 = [CT2||n3||n1]KPS and makes a response {IDSN, IDPN, CT3} to SN.
- Step6
- SN obtains CT2, n3 and n1 by decrypting CT3 with the secret key KPS and then verifies n3 and n1. If the verifications hold, SN computes SKSS = h(N1||n1||n3||K) and v3 = h(IDSN||IDPN||SKSS||CT2), and makes a response {IDSN, CT2, v3} to SU.
- Step7
- After computing SKPU′=h(N1||n2||σ), SU obtains N1, n3 and IDSN by decrypting CT2 with SKPU′ and checks the existence of N1 and IDSN in CT2. After that SU computes SKSS′ = h(N1||n1||n3||K) and v3′ = h(IDSN||IDPN||SKSS||CT2), and verifies v3 by comparing it with v3′. Only if the condition holds, SU authenticates SN and uses the session key with N1 for the further communications.
4.3. i-th Offline Authentication
5. Security and Privacy Analysis
- An adversary A can be either a SU or a SN. That means that SU as well as SN can act as an adversary.
- A can eavesdrop on every communication across public channels. He (or she) can capture any message that is exchanged among SU, SN and PN.
- A has the ability to alter, delete or reroute the captured message.
- Information can be extracted from the smart card by examining the power consumption of the card.
5.1. Proof Using BAN Logic
- Q |≡ X: Principal Q believes the statement X.
- #(X): Formula X is fresh.
- Q |⇒X: Principal Q has jurisdiction over the statement X.
- |Q: Principal Q has a public key K.
- Q X: Principal Q sees the statement X.
- Q |~ X: Principal Q once said the statement X.
- (X, Y): Formula X or Y is one part of the formula (X, Y).
- : Formula P combined with the formula Q.
- : Principal Q and R may use the shared session key, SK to communicate among each other. The session key SK is good, in that it will never be discovered by any principal except Q and R.
- Rule 1.
- Message-meaning rule: concerns the interpretation of messages.
- Rule 2.
- Nonce-verification rule: shows how to check that a message is fresh and that the sender believes so as well.
- Rule 3.
- Jurisdiction rule: states that a principal R sill trust the beliefs that S has jurisdiction over.
- Rule 4.
- Freshness-concatenation rule: shows freshness of the entire formula if any given part of a formula is fresh and the formula cannot be altered.
- Goal 1: SU |≡ (SUSN)
- Goal 2: SU |≡ (SUPN)
- Goal 3: SN |≡ (SNSU)
- Goal 4: PN |≡ (PNSU)
- Goal 5: SN |≡ |≡ (SNSU)
- Goal 6: PN |≡ |≡ (PNSU)
- Message 1. SU → SN: Login Request
- Message 2. SN → SU: IDSN, n1, n
- Message 3. SU → SN: IDSN, IDPN, <r1>t, <r2>Yv, <v1>Yv
- Message 4. SN → PN: IDSN, IDPN, <CT1>KPS, <v2>K
- Message 5. PN → SN: IDSN, IDPN, <CT3>KPS
- Message 6. SN → SU: IDSN, <CT2>SKPU, <v3>SKSS
- A1: SU | ≡ # (t, n2)
- A2: SN | ≡ # (n1)
- A3: PN | ≡ #(n3)
- A4: SU | ≡ (SU PN)
- A5: PN | ≡ (PN SU)
- A6: SU | ≡ |SN
- A7: SN | ≡ ( SN PN)
- A8: PN | ≡ (PN SN)
- A9: SU | ≡ SN |SN
- A10: SN | ≡ SU |SU
- A11: SU | ≡ PN |PN
- A12: PN | ≡ PN |SU
5.2. Casual Analysis
5.2.1. Unlinkability and Context Privacy
5.2.2. Anonymity of SU
5.2.3. Nonrepudiation and Conditional Traceability
5.3. Performance Analysis
- Th: the time to execute a one-way hash operation
- Ts: the time to compute a symmetric key encryption or decryption
- Te: the time to compute an encryption or decryption operation in ECC-160 algorithm
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Mitola, J. Cognitive Radio: An Integrated Agent Architecture for Software Defined Radio. Ph.D. Thesis, KTH Royal Institute of Technology, Stockholm, Sweden, 2000. [Google Scholar]
- Liu, K.J.R.; Wang, B. Cognitive Radio Networking and Security; Cambridge University Press: Cambridge, UK, 2011; ISBN 0521762316 9780521762311. [Google Scholar]
- Facilitating the Provision of Spectrum-Based Services to Rural Areas and Promoting Opportunities for Rural Telephone Companies to Provide Spectrum-Based Services. Available online: https://www.fcc.gov/document/facilitating-provision-spectrum-based-services-rural-areas-and-promoting-opportunities-2 (accessed on 30 November 2017).
- Guimaraes, D.A.; Silva, C.R.N.; Souza, R.A.A. Cooperative spectrum sensing using eigenvalue fusion for OFDMA and other wideband signals. J. Sens. Actuator Netw. 2013, 2, 1–24. [Google Scholar] [CrossRef]
- Stevenson, C.R.; Chouinard, G.; Lei, Z.; Hu, W.; Shellhammer, S.J.; Caldwell, W. IEEE 802.22: The first cognitive radio wireless regional area network standard. IEEE Commun. Mag. 2009, 47, 130–138. [Google Scholar] [CrossRef]
- IEEE 802.22, IEEE P802.22/D1.0 Draft Standard for Wireless Regional Area Networks Part 22: Cognitive Wireless RAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications: Policies and Procedures for Operation in the TV Bands. Available online: https://mentor.ieee.org/802.22/dcn/13/22-13-0151-00-000b-802-22b-draft-1-0.pdf (accessed on 29 November 2017).
- IEEE 802.11, IEEE 802.11af/D1.01 Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications: TV White Spaces Operation. Available online: https://pdos.csail.mit.edu/archive/decouto/papers/802.11a.pdf (accessed on 29 November 2017).
- Khattab, A.; Bayoumi, M.A. An overview of IEEE standardization efforts for cognitive radio networks. In Proceedings of the 2015 IEEE International Symposium on Circuits and Systems, Lisbon, Portugal, 24–27 May 2015; pp. 982–985. [Google Scholar]
- Um, J.; Hwang, S.; Jeong, B.J. A Comparison of PHY Layer on the Ecma-392 and IEEE 802.11af Standards. In Proceedings of the Cognitive Radio Oriented Wireless Networks and Communications (CROWNCOM), Stockholm, Sweden, 18–20 June 2012; pp. 315–319. [Google Scholar]
- Mao, H.; Zhu, L. An investigation on security of cognitive radio networks. In Proceedings of the International Conference on Management and Service Science, Wuhan, China, 2–14 August 2011; pp. 1–4. [Google Scholar]
- Mansour, I.; Chalhoub, G.; Lafourcade, P. Key Management in Wireless Sensor Networks. J. Sens. Actuator Netw. 2015, 4, 251–273. [Google Scholar] [CrossRef]
- Akyildiz, I.F.; Lee, W.Y.; Chowdhury, K.R. CRAHNs: Cognitive radio ad hoc networks. Ad Hoc Netw. 2009, 7, 810–836. [Google Scholar] [CrossRef]
- Kim, H. Security on Cognitive Radio—Effort on IEEE 802.22. In Proceedings of the Conference on Convergence, Smart and Cloud, Daegu, Korea, 14–16 October 2012; pp. 73–80. [Google Scholar]
- Jang, D.; Kim, H. Security standardization status of ECMA-International for personal/portable devices supporting cognitive radio networking. J. Secur. Eng. 2011, 8, 553–565. [Google Scholar]
- Kim, H. Security aspects analysis for secondary user authentication over cognitive radio network. In Proceedings of the Conference on Convergence, Smart and Cloud, Daegu, Korea, 14–16 October 2013; pp. 56–59. [Google Scholar]
- Kim, H. Analysis on delegation-based authentication protocol for wireless roaming service. IEEE Commun. Lett. 2014, 16, 1100–1102. [Google Scholar]
- Zhang, T. Security Issues in Cognitive Radio Networks. Ph.D. Thesis, University of Calgary, Calgary, AB, Canada, 2014. [Google Scholar]
- Katiyar, H.; Rastogi, A.; Agarwal, R. Cooperative communication: A review. IETE Tech. Rev. 2011, 28, 409–417. [Google Scholar] [CrossRef]
- Kim, H. Privacy preserving security framework for cognitive radio networks. IETE Tech. Rev. 2013, 30, 142–148. [Google Scholar] [CrossRef]
- Wang, C.; Guo, J. Public-keys-based entity authentication protocol with digital signature for cognitive radio networks. Lect. Notes Electr. Eng. 2012, 140, 341–346. [Google Scholar] [CrossRef]
- Kim, H. Location-based authentication protocol for first cognitive radio networking standard. J. Netw. Comput. Appl. 2011, 34, 1160–1167. [Google Scholar] [CrossRef]
- Tsai, J.; Lo, N.; Wu, T. Secure Delegation-Based Authentication Protocol for Wireless Roaming Service. IEEE Commun. Lett. 2012, 16, 1100–1102. [Google Scholar] [CrossRef]
- Notice of Proposed Rule Making and Order. Available online: http://web.cs.ucdavis.edu/~liu/289I/Material/FCC-03-322A1.pdf (accessed on 30 November 2017).
- Ding, G.; Wang, J.; Wu, Q.; Zhang, L.; Zou, Y.; Yao, Y.D.; Chen, Y. Robust spectrum sensing with crowd sensors. IEEE. Trans. Commun. 2014, 62, 3129–3143. [Google Scholar] [CrossRef]
- Raychaudhuri, D.; Jing, X.; Seskar, I.; Le, K.; Evans, J.B. Cognitive radio technology: From distributed spectrum coordination to adaptive network collaboration. Pervasive Mob. Comput. 2008, 4, 278–302. [Google Scholar] [CrossRef]
- Baykas, T.; Kasslin, M.; Cummings, M.; Kang, H.; Kwak, J.; Paine, R.; Reznik, A.; Saeed, R.; Shellhammer, S.J. Developing a Standard for TV White Space Coexistence: Technical Challenges and Solution Approaches. IEEE Wirel. Commun. 2012, 19, 10–22. [Google Scholar] [CrossRef]
- Liang, Y.C.; Chen, K.C.; Li, G.Y.; Mähönen, P. Cognitive radio networking and communications: An overview. IEEE Tran. Veh. Tech. 2011, 60, 3386–3407. [Google Scholar] [CrossRef]
- Chakravarthy, V.; Li, X.; Wu, Z.; Temple, M.A.; Garber, F.; Kannan, R.; Vasilakos, A. Novel overlay/underlay cognitive radio waveforms using SD-SMSE framework to enhance spectrum efficiency-Part I: Theoretical framework and snalysis in AWGN channel. IEEE Trans. Commun. 2009, 57, 3794–3804. [Google Scholar] [CrossRef]
- Parvin, S.; Han, S.; Tian, B.; Hussain, F.K. Trust-Based Authentication for Secure Communication in Cognitive Radio Networks. In Proceedings of the 2010 IEEE/IEIP International Conference on Embedded and Ubiquitous Computing, Hong Kong, China, 11–13 December 2010; pp. 589–596. [Google Scholar]
- Slimeni, F.; Scheers, B.; Chtourou, Z.; Nir, V.L. Jamming mitigation in cognitive radio networks using a modified Q-learning algorithm. In Proceedings of the 2015 International Conference on Military Communications and Information Systems, Cracow, Poland, 18–19 May 2015. [Google Scholar]
- Slimeni, F.; Scheers, B.; Chtourou, Z. Security threats in military cognitive radio networks. In Proceedings of the 2015 International Conference on Military Communications and Information Systems, Cracow, Poland, 18–19 May 2015. [Google Scholar]
- Al-Hraishawi, H.; Baduge, G.A.A.; Schaefer, R.F. Artificial noise-aided physical layer security in underlay cognitive massive MIMO systems with pilot contamination. Entropy 2017, 19, 349. [Google Scholar] [CrossRef]
- Li, J.; Feng, A.; Feng, Z.; Zhang, P. A survey of security issues in cognitive radio networks. China Commun. 2015, 13, 132–150. [Google Scholar] [CrossRef]
- Naveed, A.; Kanhere, S.S. NIS07-5: Security vulnerabilities in channel assignment of multi-radio multi-channel wireless mesh networks. In Proceedings of the IEEE Globecom, San Francisco, CA, USA, 11 November–1 December 2006; pp. 1–5. [Google Scholar]
- Zhang, J.; Cai, L.; Zhang, S. Malicious cognitive user identification algorithm in centralized spectrum sensing system. Futur. Int. 2017, 9, 79. [Google Scholar] [CrossRef]
- Ye, F.; Zhang, X.; Li, Y. Comprehensive reputation-based security mechanism against dynamic SSDF attack in cognitive radio networks. Symmetry 2016, 8, 147. [Google Scholar] [CrossRef]
- Ye, F.; Zhang, X.; Li, Y.; Tang, C. Faithworthy collaborative spectrum sensing based on credibility and evidence theory for cognitive radio networks. Symmetry 2017, 9, 36. [Google Scholar] [CrossRef]
- Guimarães, D.A.; Souza, R.A.A.; Barreto, A.N. Performance of cooperative eigenvalue spectrum sensing with a realistic receiver model under impulsive noise. J. Sens. Actuator Netw. 2013, 2, 46–69. [Google Scholar] [CrossRef]
- Zhang, L.; Ding, G.; Wu, Q.; Zou, Y.; Han, Z.; Wang, J. Byzantine Attack and Defense in Cognitive Radio Networks: A Survey. IEEE Commun. Surv. Tutor. 2015, 17, 1341–1363. [Google Scholar] [CrossRef]
- Wu, H.; Hui, N.; Zhou, X.; Bai, B. Puzzle-based selfish behavior punishment mechanism of MAC layer in cognitive radio networks. In Proceedings of the IET 3rd International Conference on Wireless, Mobile and Multimedia Networks, Beijing, China, 26–29 September 2010; pp. 213–216. [Google Scholar]
- Das, D.; Das, S. Intelligent resource allocation scheme for the cognitive radio network in the presence of primary user emulation attack. IET Commun. 2017, 15, 2370–2379. [Google Scholar] [CrossRef]
- El-Malek, A.H.A.; Salhab, A.M.; Zummo, S.A. New bandwidth efficient relaying schemes in cooperative cognitive two-way relay networks with physical layer security. IEEE Trans. Veh. Technol. 2017, 66, 5372–5386. [Google Scholar] [CrossRef]
- Burrow, M.; Abadi, M.; Needham, R. A Logic of Authentication. ACM Trans. Comput. Syst. 1990, 8, 18–36. [Google Scholar] [CrossRef]
- Dai, W. Crypto++ Library 5.6.1. Available online: http://www.cryptopp.com (accessed on 5 December 2016).
| Attacks | Properties |
|---|---|
| Intentional jamming attack [30,31,32] PU receiver jamming attack [30,31,32] Sensitivity amplifying attack [30,31,32] Overlapping SU attack [33] | SU jams PUs and the other SUs |
| Biased utility attack [33,34] Asynchronous sensing attack [35,36,37,38] Byzantine attack [39] False feedback attack [33] Selfish misbehaviour attack [39,40] | SU tweaks parameters of the utility function |
| Network Endo-parasite attack [33,34] Channel Ecto-parasite attack [33,34] Low cost ripple effect attack [33,34] | SU attempts to increase the interference |
| Key depletion attack [33,34] | High round trip times and frequent retransmissions increase key usage |
| Any attacks against confidentiality, integrity, authentication, non-repudiation, access control, and availability [19,33] | Any attacks on below layers from application layer impact adversely on the layer |
| Jellyfish attack [41] Routing information jamming attack [42] | Performed in a network layer but affected to the other layers |
| Network | General Network | CRN | |
|---|---|---|---|
| Feature | |||
| Consideration of PU protection | Not required | Required | |
| Relationship between SN and PN | Required | Need not or need partially for traceability | |
| Authentication when SU visits the other networks | Delegation | Delegation | |
| Notation | Definition |
|---|---|
| p, q | The prime numbers satisfying q|(p-1) |
| g | A generator in Zp |
| IDSU, IDSN, IDPN | The identities of SU, SN and PN |
| AIDSU | The amplified identity of SU |
| PWSU | The password of SU |
| [M]K | A symmetric encryption for message M with the key K |
| KPS | A symmetric key between SN and PN |
| G | A cyclic additive group |
| P | The generator of the cyclic additive group G |
| h() | One way hash function such that h():Zp→Zp |
| f() | One way hash function such that f():G→Zp |
| (K,σ) | A proxy key pair of SU |
| SK | A session key established between any two parties |
| ⊕ | The exclusive-or operation |
| || | The string concatenation operation |
| Protocol | Kim’s in [21] | Tsai et al.’s in [22] | Proposed Framework | |
|---|---|---|---|---|
| Feature | ||||
| Security Issue | PU protection | Provide | N/A | Provide |
| No registration | N/A | Provide | Provide | |
| Weakness | Weak against carousel Desynchronization attack | Weak against smartcard breach attack | No security weakness | |
| Privacy Issue | UL and CP | N/A | N/A | Provide |
| UA | Provide | N/A | Provide | |
| NR and CT | Provide | N/A | Provide |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kim, H.; Ryu, E.K. Delegation Based User Authentication Framework over Cognitive Radio Networks. J. Sens. Actuator Netw. 2017, 6, 29. https://doi.org/10.3390/jsan6040029
Kim H, Ryu EK. Delegation Based User Authentication Framework over Cognitive Radio Networks. Journal of Sensor and Actuator Networks. 2017; 6(4):29. https://doi.org/10.3390/jsan6040029
Chicago/Turabian StyleKim, Hyunsung, and Eun Kyung Ryu. 2017. "Delegation Based User Authentication Framework over Cognitive Radio Networks" Journal of Sensor and Actuator Networks 6, no. 4: 29. https://doi.org/10.3390/jsan6040029






