A New Secure RFID Anti-Counterfeiting and Anti-Theft Scheme for Merchandise
Abstract
:1. Introduction
2. Literature Review
2.1. RFID Counterfeiting Definition
2.2. Our Previous Work
2.3. Other Anti-Counterfeiting Proposed Schemes
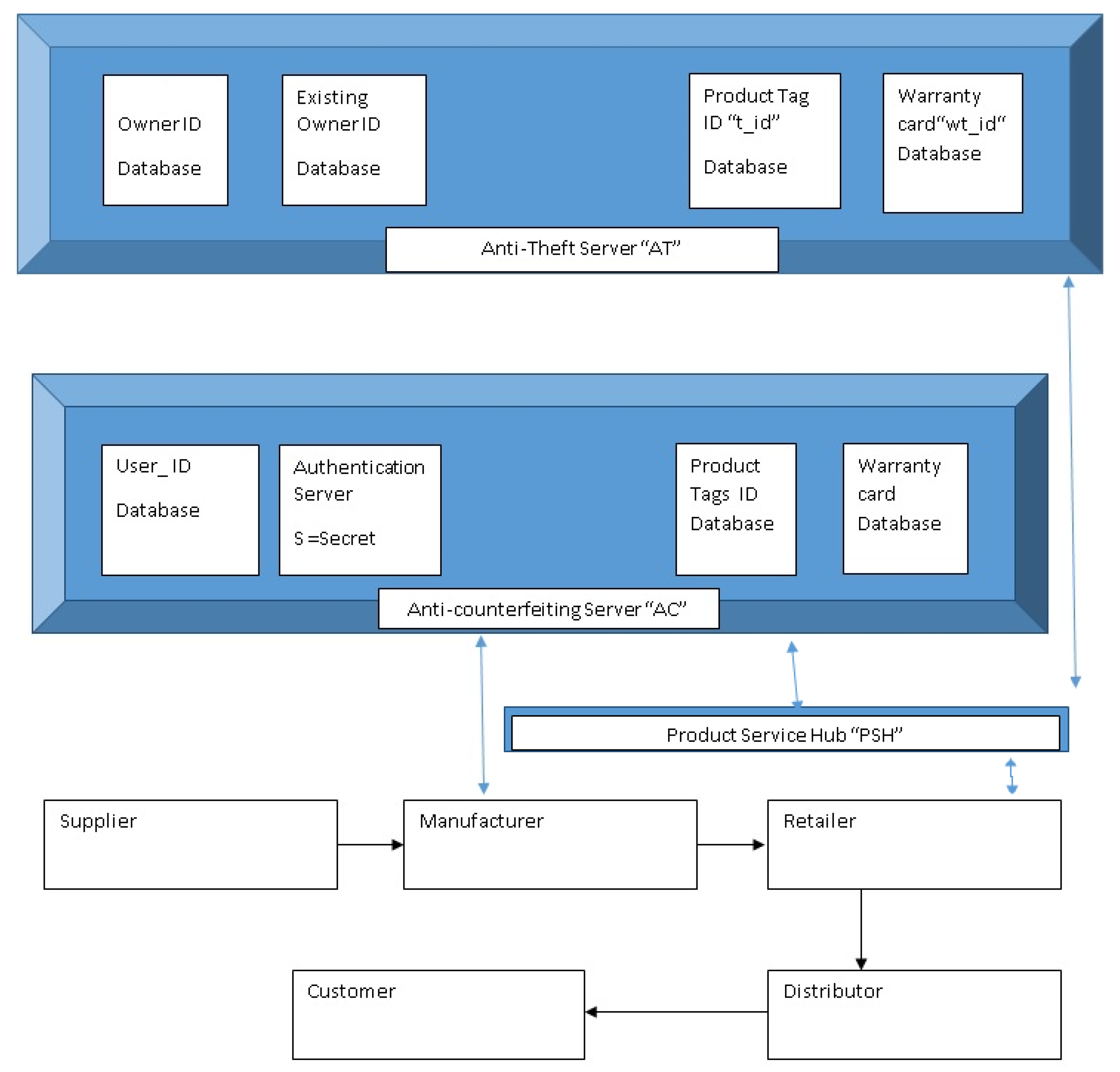
3. The Proposed Scheme
3.1. System Set-Up
- The product always has two tags: one attached to the product itself, and the other attached with the warranty card;
- The tag issuer is the product manufacturer who feeds the system with ;
- The product manufacturer also feeds the anti-counterfeiting server (AC) with the warranty card ID ;
- The product service hub (PSH), see Table 2, which is an intermediate server connected to both the AC and the anti-theft (AT) servers, is accessible by any reader with a correct to prevent the use of unauthorised or malicious applications. The reader is a device used by the customer or any Supply Chain (SC) entity and can be a smartphone with the authentication protocol downloaded from the PSH; only readers with this application can check and verify whether the product is genuine;
- Every time the buyer, customer, seller, distributor or any SC entity downloads the application from the PSH, the AT server issues an application ID to the downloader;
- If the application ID is not correct, the PSH responds ‘not correct application’ and terminates;
- The AC responds with to the PSH once the product is verified using the authentication method which we discuss later;
- The reader must read both tags simultaneously, otherwise, the read is incorrect or missing. In case of missing read, the PSH checks with the AT server whether the reader has an existing owner ID and application ID database, and if the tag ID is correct, it responds with to the PSH;
- If the AC did not respond or responds incorrectly to the PSH, the PSH responds with ‘not genuine product’ (), indicating that the product is not genuine;
- If both the AC and the AT server respond with OK to the PSH, the PSH responds with and the AT server issues a new owner record;
- If there is no warranty card tag ID and no existing owner number, the PSH provides the response ‘invalid’ and report the application ID for checking;
- Every two tags for the same product have the same secret stored in the tags (S).
3.2. System Flow
4. The System Process
4.1. Anti-Counterfeiting (AC) Server Process
- Step 1: the reader first downloads the software or application from the PSH site. The PSH in return issues a for the buyer, including his name, his address and maybe his apple store or android ID (to obtain more security) depending on the operating system he uses (particularly when using his mobile phone), which is stored later in the AT server. The buyer can use this application to make an enquiry about a certain product in the retail store, for example, by scanning a barcode or entering the product serial number Q and sending it to the PSH through the software downloaded earlier. The reader initiates the protocol by sending Q to the reader, see Figure 1;
- Step 2: in this step, once Q is received, the PSH generates a w or a reader secret. This happens each time the reader has a request. Then, the PSH stores the w in the AC server. The PSH also verifies w from Table 3 and calculate RE from Equation (1) by generating a random number R1 and XOR-ing Q, R1 and S, before sending the results to the reader;
- Step 3: the reader forwards RE to the tags attached to the product and the warranty card. Then, the tags solve RE, determine R1 and calculate A and B. Then, the tags respond to the reader with A and B from Equations (2) and (3), as shown in Figure 2;
- Step 4:once A and B have been received by the reader, the reader generates the random number then calculate , and create C and D from Equations (4)–(7). Then, the reader sends C,D to PSH;
- Step 5: in this step, the PSH determines the user-id and the secret S, if the user-id and S are correct, it continues. If not, it terminates, then it contacts the AC server via a secure channel to determine the database of the t-id as well as the wt-ID in the record with Q, see the Table 3;The PSH gets R2 from Equation (8) then checks if Q = or Q = and if it is true, then it extracts C and D then check if and if = , again if true, the PSH determines the N value from Table 4.If all the elements , and S match the record, then it responds with signifying that the product is genuine to the PSH; if the or the secret S is not correct, the server responds signifying that the product is not genuine. If the is missing or 0, the PSH replies or tag missing. Then, it calculates E and F from Equations (9) and (10) and generate a new w before updating w(−1) with w and sending E and F to the reader;
- Step 6: in this step, the reader checks if = , and if N = , then it updates the w.
4.2. Anti-Theft Server AT Process
5. Security Analysis
5.1. ’s Point of View—The Nonce Test and Checking the Secrecy of
5.2. AA’s Point of View—The Encryption Test Checking the Secrecy of
5.3. CC’s Point of View—The Authentication Guarantee Test Checking the Secrecy of S
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Randhawa, P.; Calantone, R.J.; Voorhees, C.M. The pursuit of counterfeited luxury: An examination of the negative side effects of close consumer–brand connections. J. Bus. Res. 2015, 68, 2395–2403. [Google Scholar] [CrossRef]
- Meyer, T. Anti-Counterfeiting Trade Agreement: 2010–2012 European Parliament Discussions. In The Politics of Online Copyright Enforcement in the EU; Springer: Berlin/Heidelberg, Germany, 2017; pp. 247–280. [Google Scholar]
- Khalil, G.D.A. A Novel RFID Based Anti-Counterfeiting Scheme for Retailer Environments; Technical Report; Deakin University: Melbourne, Victoria, Australia, 2019. [Google Scholar]
- Hargreaves, S. Counterfeit Goods Becoming More Dangerous. Available online: https://money.cnn.com/2012/09/27/news/economy/counterfeit-goods/index.html (accessed on 20 December 2019).
- Bloch, P.H.; Bush, R.F.; Campbell, L. Consumer “accomplices” in product counterfeiting: A demand side investigation. J. Consum. Mark. 1993, 10, 27–36. [Google Scholar] [CrossRef]
- McKinney, G.F., Jr. Monitoring the Ligand-Nanopartcle Interaction for the Development of SERS Tag. Ph.D. Thesis, University of South Dakota, Vermillion, SD, USA, 2014. [Google Scholar]
- Estacio, L.S. Showdown in Chinatown: Criminalizing the Purchase of Counterfeit Goods. Seton Hall Legis. J. 2012, 37, 381. [Google Scholar]
- Khalil, G.; Doss, R.; Chowdhury, M. A Comparison Survey Study on RFID Based Anti-Counterfeiting Systems. J. Sens. Actuator Netw. 2019, 8, 37. [Google Scholar] [CrossRef] [Green Version]
- Preradovic, S.; Karmakar, N.C. Chipless RFID: Bar Code of the Future. IEEE Microw. Mag. 2010, 11, 87–97. [Google Scholar] [CrossRef]
- Yang, K.; Botero, U.; Shen, H.; Woodard, D.L.; Forte, D.; Tehranipoor, M.M. UCR: An Unclonable Environmentally Sensitive Chipless RFID Tag For Protecting Supply Chain. ACM Trans. Des. Autom. Electron. Syst. 2018, 23, 1–24. [Google Scholar] [CrossRef]
- Devadas, S.; Suh, E.; Paral, S.; Sowell, R.; Ziola, T.; Khandelwal, V. Design and implementation of PUF-based “unclonable” RFID ICs for anti-counterfeiting and security applications. In Proceedings of the 2008 IEEE International Conference on RFID, Las Vegas, NV, USA, 16–17 April 2008; pp. 58–64. [Google Scholar]
- Choi, S.; Yang, B.; Cheung, H.; Yang, Y. RFID tag data processing in manufacturing for track-and-trace anti-counterfeiting. Comput. Ind. 2015, 68, 148–161. [Google Scholar] [CrossRef]
- Bu, K.; Liu, X.; Xiao, B. Approaching the time lower bound on cloned-tag identification for large RFID systems. Ad Hoc Netw. 2014, 13, 271–281. [Google Scholar] [CrossRef]
- Lehtonen, M.; Ostojic, D.; Ilic, A.; Michahelles, F. Securing RFID systems by detecting tag cloning. In Proceedings of the International Conference on Pervasive Computing, Nara, Japan, 11–14 May 2009; Springer: Berlin/Heidelberg, Germany, 2009; pp. 291–308. [Google Scholar]
- Tran, D.T.; Hong, S.J. RFID anti-counterfeiting for retailing systems. J. Appl. Math. Phys. 2015, 3, 1. [Google Scholar] [CrossRef] [Green Version]
- Al, G.; Doss, R.; Chowdhury, M.; Ray, B. Secure RFID Protocol to Manage and Prevent Tag Counterfeiting with Matryoshka Concept. In Proceedings of the International Conference on Future Network Systems and Security, Paris, France, 23–25 November 2016; Springer: Berlin/Heidelberg, Germany; pp. 126–141. [Google Scholar]
- Al, G.; Doss, R.; Chowdhury, M. Adjusting Matryoshka Protocol to Address the Scalability Issue in IoT Environment. In Proceedings of the International Conference on Future Network Systems and Security, Gainesville, FL, USA, 31 August–2 September 2017; Springer: Berlin/Heidelberg, Germany; pp. 84–94. [Google Scholar]
- Al, G. Chapter: A Survey on RFID tag ownership transfer protocols. In RFID Technology: Design Principles, Applications and Controversies; Nova Science Publishers, Inc.: Commack, NY, USA, 2017; pp. 83–92. ISBN 978-1-53613-251-9. [Google Scholar]
- Al, G.K.; Ray, B.R.; Chowdhury, M. RFID Tag Ownership Transfer Protocol for a Closed Loop System. In Proceedings of the 2014 IIAI 3rd International Conference on Advanced Applied Informatics (IIAIAAI), Kitakyushu, Japan, 31 August–4 September 2014; pp. 575–579. [Google Scholar]
- Al, G. RFID Technology: Design Principles, Applications and Controversies; Nova Science Publishers, Inc.: Commack, NY, USA, 2018. [Google Scholar]
- AL, G.; Ray, B.; Chowdhury, M. Multiple Scenarios for a Tag Ownership Transfer protocol for A Closed Loop System. IJNDC 2015, 3, 128–136. [Google Scholar] [CrossRef] [Green Version]
- Choi, E.Y.; Lee, D.H.; Lim, J.I. Anti-cloning protocol suitable to EPCglobal Class-1 Generation-2 RFID systems. Comput. Stand. Interfaces 2009, 31, 1124–1130. [Google Scholar] [CrossRef]
- Cheung, H.; Choi, S. Implementation issues in RFID-based anti-counterfeiting systems. Comput. Ind. 2011, 62, 708–718. [Google Scholar] [CrossRef]
- Chen, Y.C.; Wang, W.L.; Hwang, M.S. RFID authentication protocol for anti-counterfeiting and privacy protection. In Proceedings of the 9th International Conference on Advanced Communication Technology, Phoenix Park, Korea, 12–14 February 2007; Volume 1, pp. 255–259. [Google Scholar]
- Yuan, Y.; Cao, L. Liquor Product Anti-counterfeiting System Based on RFID and Two-dimensional Barcode Technology. J. Converg. Inf. Technol. 2013, 8, 88–96. [Google Scholar]
- Zhu, Y.; Gao, W.; Yu, L.; Li, P.; Wang, Q.; Yang, Y.; Du, J. Research on RFID-based anti-counterfeiting system for agricultural production. In Proceedings of the World Automation Congress (WAC), Kobe, Japan, 19–23 September 2010; pp. 351–353. [Google Scholar]
- Sabbaghi, A.; Vaidyanathan, G. Effectiveness and efficiency of RFID technology in supply chain management: Strategic values and challenges. J. Theor. Appl. Electron. Commer. Res. 2008, 3, 71–81. [Google Scholar] [CrossRef] [Green Version]
- Kriara, L.; Alsup, M.; Corbellini, G.; Trotter, M.; Griffin, J.D.; Mangold, S. RFID shakables: Pairing radio-frequency identification tags with the help of gesture recognition. In Proceedings of the Ninth ACM Conference on Emerging Networking Experiments and Technologies, Santa Barbara, CA, USA, 9–12 December 2013; ACM: New York, NY, USA, 2013; pp. 327–332. [Google Scholar]
- Repo, P.; Kerttula, M.; Salmela, M.; Huomo, H. Virtual product design case study: The Nokia RFID tag reader. IEEE Pervasive Comput. 2005, 4, 95–99. [Google Scholar] [CrossRef]
- Yuan, Y. Crowd monitoring using mobile phones. In Proceedings of the 2014 Sixth International Conference on Intelligent Human-Machine Systems and Cybernetics, Hangzhou, China, 26–27 August 2014; Volume 1, pp. 261–264. [Google Scholar]
- Lee, J.D. Anti-Counterfeiting Mechanism Based on RFID Tag Ownership Transfer Protocol. J. Korea Multimed. Soc. 2015, 18, 710–722. [Google Scholar] [CrossRef]
- Kapoor, G.; Piramuthu, S. Single RFID tag ownership transfer protocols. IEEE Trans. Syst. Man Cybern. Part C (Appl. Rev.) 2012, 42, 164–173. [Google Scholar] [CrossRef]
- Guttman, J.D. Shapes: Surveying crypto protocol runs. In Formal Models and Techniques for Analyzing Security Protocols. Cryptology and Information Security Series; IOS Press: Amsterdam, The Netherlands, 2011. [Google Scholar]
- Guttman, J.D. Cryptographic protocol composition via the authentication tests. In Proceedings of the International Conference on Foundations of Software Science and Computational Structures, York, UK, 22–29 March 2009; Springer: Berlin/Heidelberg, Germany, 2009; pp. 303–317. [Google Scholar]
- Guttman, J.D. Fair exchange in strand spaces. arXiv 2009, arXiv:0910.4342. [Google Scholar] [CrossRef] [Green Version]
- Paulson, L.C. Proving properties of security protocols by induction. In Proceedings of the 10th Computer Security Foundations Workshop, Rockport, MA, USA, 10–12 June 1997; pp. 70–83. [Google Scholar]



| Properties | Physical | Track and Trace | Distance Bounding Protocols | Cryptography |
|---|---|---|---|---|
| Use of Resources | High | Medium | Medium | Low |
| Complexity | Medium | Medium | Low | High |
| Security | High | Medium | High | Medium |
| Limitations | High | Low | High | Low |
| Adaptability | Low | High | Low | High |
| Research | Medium | High | Low | Medium |
| Pros | Impossible to clone | More reliable in industry | Best for large scale RFID tags | Low cost |
| Cons | Expensive and not adaptable for every industry | Issues in synchronization between e-pedigree | Distance limitations | Weak security |
| Notations | |
|---|---|
| AC | Anti-counterfeiting server |
| AT | Anti-theft server |
| PSH | Product service Hub |
| Unique tag id attached to product | |
| S | Secret stored in the tags |
| NGP | Not genuine product |
| New owner ID | |
| Existing owner ID | |
| Genuine product | |
| Warranty tag missing | |
| Random number | |
| Q | Item number |
| Second random number | |
| A,B,C,D,E,F,, | Variables |
| w | Updated Reader secret |
| User id generated by PSH | |
| Unique tag id attached to warranty card or boxes | |
| AC Server Records | ||||
|---|---|---|---|---|
| Serial Number | Sticker or Bar Code Number | Product Tag ID | Warranty Tag ID | Secret |
| n | Q | S | ||
| N Value | |
|---|---|
| OK | 1 |
| MT | 2 |
| NGP | 3 |
| AT Server Records | ||||
|---|---|---|---|---|
| Record Number | Tag ID | Warranty Tag ID | New Owner ID | Existing Owner ID |
| n | ||||
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Khalil, G.; Doss, R.; Chowdhury, M. A New Secure RFID Anti-Counterfeiting and Anti-Theft Scheme for Merchandise. J. Sens. Actuator Netw. 2020, 9, 16. https://doi.org/10.3390/jsan9010016
Khalil G, Doss R, Chowdhury M. A New Secure RFID Anti-Counterfeiting and Anti-Theft Scheme for Merchandise. Journal of Sensor and Actuator Networks. 2020; 9(1):16. https://doi.org/10.3390/jsan9010016
Chicago/Turabian StyleKhalil, Ghaith, Robin Doss, and Morshed Chowdhury. 2020. "A New Secure RFID Anti-Counterfeiting and Anti-Theft Scheme for Merchandise" Journal of Sensor and Actuator Networks 9, no. 1: 16. https://doi.org/10.3390/jsan9010016







