An Algorithm for Data Hiding in Radiographic Images and ePHI/R Application
Abstract
:1. Introduction
2. Related Work
3. Proposed Method
3.1. Challenges to Designing a New Method
- ➢
- Maximizes the probability of occurrence of Type II error;
- ➢
- Includes no transformation;
- ➢
- Processes the data byte by byte to reduce computational complexity.
- ➢
- Requires no classification of cover radiographic images into ROI and RONI;
- ➢
- Can be used for all types of radiographic images including MR images, CT scan images, X-ray images, ultrasounds, etc.;
- ➢
- Shows ε(θ) = ε(φ) even for the average and worst cases;
- ➢
- Should be ε-secure stego system.
3.2. Methodology
| Algorithms 1: The whole process of embedding data is divided into two algorithms. First algorithm is used at the sending end for embedding data and the second algorithm is for extraction process. |
| Key Generation Algorithm Inputs: Cover radiographic image (CRI), Patient Health information/Record (PHI/R) Output: Stego-radiographic image (Sri)
Formal presentation of the proposed algorithm for embeding phase with polynomial p is Inputs: Stego radiographic image Image Sri, lDePHI/R, p Output: Patient Health information/Record PHI/R
|
3.3. Evaluation Metrics
4. Experimental Results and Discussion
4.1. The Material
4.2. Histogram Computation
4.3. Unique Color Computation
4.4. Results and Discussion
Discussion
5. Conclusions
Acknowledgement
Author Contributions
Conflicts of Interest
Abbreviations
| Acronym | Expended Form |
| CT | Computed Tomography |
| DFT | Discrete Fourier Transform |
| DKL | Divergence Kullback Leibler |
| DWT | Discrete Wavelet Transform |
| ePHI/R | Electronic Patient Health Information/Record |
| ICT | Information and Communication Technology |
| IQM | Image Quality Measure |
| MRI | Magnetic Resonance imaging |
| NPCR | Number of Pixel Change Rate |
| ROI | Region of Interest |
| RONI | Region of Non-Interest |
| UACI | Unified Average Change intensity |
References
- Singh, A.K.; Dave, M.; Anand, M. Hybrid technique for robust and imperceptible multiple watermarking using medical images. Multimedia Tools Appl. 2016, 75, 8381–8401. [Google Scholar] [CrossRef]
- Rashid, A.; Rahim, M.K. Critical Analysis of Steganography “An Art of Hidden Writing”. Int. J. Secur. Its Appl. 2016, 10, 259–281. [Google Scholar] [CrossRef]
- Subhedar, M.S.; Mankar, V.H. Current status and key issues in image steganography: A survey. Comput. Sci. Rev. 2014, 13, 95–113. [Google Scholar] [CrossRef]
- Silman, J. Steganography and steganalysis: An overview. Sans Inst. 2001, 3, 61–76. [Google Scholar]
- Lee, Y.K.; Chen, L.H. High capacity image steganographic model. IEE Proc. Vis. Image Signal Process. 2000, 147, 288–294. [Google Scholar] [CrossRef]
- Roque, J.J.; Minguet, J.M. SLSB: Improving the Steganographic Algorithm LSB. In Proceedings of the 7th International Workshop on Security in Information Systems (WOSIS 2009), In Conjunction with ICEIS 2009, Milan, Italy, 6–7 May 2009. [Google Scholar]
- Wu, D.C.; Tsai, W.H. A steganographic method for images by pixel-value differencing. Pattern Recognit. Lett. 2003, 24, 1613–1626. [Google Scholar] [CrossRef]
- Al-Momen, S.M.A.; George, L.E. Image hiding using magnitude modulation on the DCT coefficients. J. Appl. Comput. Sci. Math. 2010, 4, 9–14. [Google Scholar]
- Boney, L.; Tewfik, A.H.; Hamdy, K.N. Digital watermarks for audio signals. In Proceedings of the Third IEEE International Conference on Multimedia Computing and Systems, Hiroshima, Japan, 17–23 June 1996. [Google Scholar]
- Reddy, H.M.; Raja, K.B. High capacity and security steganography using discrete wavelet transform. Int. J. Comput. Sci. Secur. IJCSS 2009, 3, 462. [Google Scholar]
- Bender, W.; Gruhl, D.; Morimoto, N.; Lu, A. Techniques for data hiding. IBM Syst. J. 1996, 35, 313–336. [Google Scholar] [CrossRef]
- Johnson, N.; Jajodia, S. Steganalysis of Images Created Using Current Steganography Software. In Information Hiding; Springer: Berlin/Heidelberg, Germany, 1998. [Google Scholar]
- Marvel, L.M.; Boncelet, C.G.; Retter, C.T. Spread spectrum image steganography. IEEE Trans. Image Process. 1999, 8, 1075–1083. [Google Scholar] [CrossRef] [PubMed]
- Cachin, C. An information-theoretic model for steganography. In Information Hiding; Springer: Berlin/Heidelberg, Germany, 1998. [Google Scholar]
- Li, B.; He, J.; Huang, J.; Shi, Y.Q. A survey on image steganography and steganalysis. J. Inf. Hiding Multimedia Signal Process. 2011, 2, 142–172. [Google Scholar]
- Westfeld, A.; Pfitzmann, A. Attacks on steganographic systems. In International Workshop on Information Hiding; Springer: Berlin/Heidelberg, Germany, 1999. [Google Scholar]
- Fridrich, J.; Long, M. Steganalysis of LSB encoding in color images. In Proceedings of the 2000 IEEE International Conference on Multimedia and Expo, New York, NY, USA, 30 July–2 August 2000; Volume 3. [Google Scholar]
- Fridrich, J.; Goljan, M.; Du, R. Detecting LSB steganography in color, and gray-scale images. IEEE Multimedia 2001, 8, 22–28. [Google Scholar] [CrossRef]
- Dumitrescu, S.; Wu, X.; Wang, Z. Detection of LSB steganography via sample pair analysis. IEEE Trans. Signal Process. 2003, 51, 1995–2007. [Google Scholar] [CrossRef]
- Zhang, T.; Ping, X. Reliable detection of LSB steganography based on the difference image histogram. In Proceedings of the 2003 IEEE International Conference on Acoustics, Speech, and Signal Processing, Hong Kong, China, 6–10 April 2003. [Google Scholar]
- Lu, P.; Luo, X.; Tang, Q.; Li, S. An Improved Sample Pairs Method for Detection of LSB Embedding. In Information Hiding; Volume 3200, Springer: Berlin/Heidelberg, Germany, 2004. [Google Scholar]
- Ker, A.D. Improved detection of LSB steganography in grayscale images. In Proceedings of the International Workshop on Information Hiding, Toronto, ON, Canada, 23–25 May 2004; Springer: Berlin/Heidelberg, Germany, 2004. [Google Scholar]
- Ker, A.D. Derivation of error distribution in least squares steganalysis. IEEE Trans. Inf. Forensics Secur. 2007, 2, 140–148. [Google Scholar] [CrossRef]
- Rey, C.; Dugelay, J.L. A survey of watermarking algorithms for image authentication. EURASIP J. Adv. Signal Process. 2002, 6, 218932. [Google Scholar] [CrossRef]
- Singh, A.K.; Dave, M.; Mohan, A. Wavelet based image watermarking: Futuristic concepts in information security. Proc. Natl. Acad. Sci. USA 2014, 84, 345–359. [Google Scholar] [CrossRef]
- Zhang, L.; Zhou, P.P. Localized affine transform resistant watermarking in region-of-interest. Telecommun. Syst. 2010, 44, 205–220. [Google Scholar] [CrossRef]
- Memon, N.A.; Gilani, S.A.M. NROI watermarking of medical images for content authentication. In Proceedings of the 2008 IEEE International Multitopic Conference, Karachi, Pakistan, 23–24 December 2008. [Google Scholar]
- Zain, J.; Clarke, M. Security in telemedicine: Issues in watermarking medical images. In Proceedings of the 3rd International Conference: Sciences of Electronic, Technologies of Information and Telecommunications, Sousse, Tunisia, 27–31 March 2005. [Google Scholar]
- Yang, C.Y.; Hu, W.C. Reversible data hiding in the spatial and frequency domains. Int. J. Image Process. 2010, 3, 373–382. [Google Scholar]
- Rathi, S.C.; Inamdar, V.S. Analysis of watermarking techniques for medical Images preserving ROI. Comput. Sci. Inf. Technol. 2012, 287–308. [Google Scholar] [CrossRef]
- Pandey, R.; Singh, A.K.; Kumar, B.; Mohan, A. Iris based secure NROI multiple eye image watermarking for teleophthalmology. Multimedia Tools Appl. 2016, 75, 14381–14397. [Google Scholar] [CrossRef]
- Jasmine Selvakumari Jeya, I.; Suganthi, J. RONI based secured and authenticated indexing of lung CT images. In Computational and Mathematical Methods in Medicine; Hindawi Publishers: New York, NY, USA, 2015. [Google Scholar]
- Aherrahrou, N.; Tairi, H. PDE based scheme for multi-modal medical image watermarking. Biomed. Eng. Online 2015, 14, 108. [Google Scholar] [CrossRef] [PubMed]
- Al-Haj, A. Secured telemedicine using region-based watermarking with tamper localization. J. Digit. Imaging 2014, 27, 737–750. [Google Scholar] [CrossRef] [PubMed]
- Rayachoti, E.; Edara, S.R. Block Based Medical Image Watermarking Technique for Tamper Detection and Recovery. arXiv, 2014; arXiv:1412.6143. [Google Scholar]
- Nyeem, H.; Boles, W.; Boyd, C. Utilizing least significant bit-planes of RONI pixels for medical image watermarking. In Proceedings of the 2013 International Conference on Digital Image Computing: Techniques and Applications (DICTA), Hobart, Australia, 26–28 November 2013. [Google Scholar]
- Gunjal, B.L.; Mali, S.N. ROI based embedded watermarking of medical images for secured communication in telemedicine. Int. J. Comput. Commun. Eng. 2012, 6, 293–298. [Google Scholar]
- El-Samie, F.E.A.; Ahmed, H.E.H.; Elashry, I.F.; Shahieen, M.H.; Faragallah, O.S.; El-Rabaie, E.S.M.; Alshebeili, S.A. Image Encryption: A Communication Perspective; CRC Press: Boca Raton, FL, USA, 2013. [Google Scholar]
- El-Latif, A.A.A.; Li, L.; Zhang, T.; Wang, N.; Song, X.; Niu, X. Digital image encryption scheme based on multiple chaotic systems. Sens. Imaging Int. J. 2012, 13, 67–88. [Google Scholar] [CrossRef]
- Etemadi Borujeni, S.; Eshghi, M. Chaotic image encryption design using Tompkins-Paige algorithm. In Mathematical Problems in Engineering; Hindawi Publishers: New York, NY, USA, 2009. [Google Scholar]
- Stoer, J.; Bulirsch, R. Introduction to Numerical Analysis; Springer Science & Business Media: Berlin, Germany, 2013; Volume 12. [Google Scholar]
- Powell, M.J.D. Approximation Theory and Methods; Cambridge University Press: Cambridge, UK, 1981. [Google Scholar]
- Minoux, M. Mathematical Programming: Theory and Algorithms; John Wiley & Sons: Hoboken, NJ, USA, 1986. [Google Scholar]
- Rashid, A.; Rahim, M.K. Classification, Analysis and Comparison of Non-Blind Image Quality Measure. Int. J. Signal Process. Image Process. Pattern Recognit. 2016, 9, 347–360. [Google Scholar] [CrossRef]
- Eskicioglu, A.M.; Fisher, P.S. Image quality measures and their performance. IEEE Trans. Commun. 1995, 43, 2959–2965. [Google Scholar] [CrossRef]
- Sayood, K. Statistical evaluation of image quality measures. J. Electron. Imaging 2002, 11, 206–223. [Google Scholar]
- Wang, Z.; Bovik, A.C.; Sheikh, H.R.; Simoncelli, E.P. Image quality assessment: From error visibility to structural similarity. IEEE Trans. Image Process. 2004, 13, 600–612. [Google Scholar] [CrossRef] [PubMed]
- Snyder, H.L. Image Quality: Measures and Visual Performance. Flat-Panel Displays and CRTs; Springer: Houten, The Netherlands, 1985; pp. 70–90. [Google Scholar]
- Rashid, A. Experimental analysis and comparison of LSB substitution and LSB matching method of information security. Int. J. Comput. Sci. Issues IJCSI 2015, 12, 91. [Google Scholar]



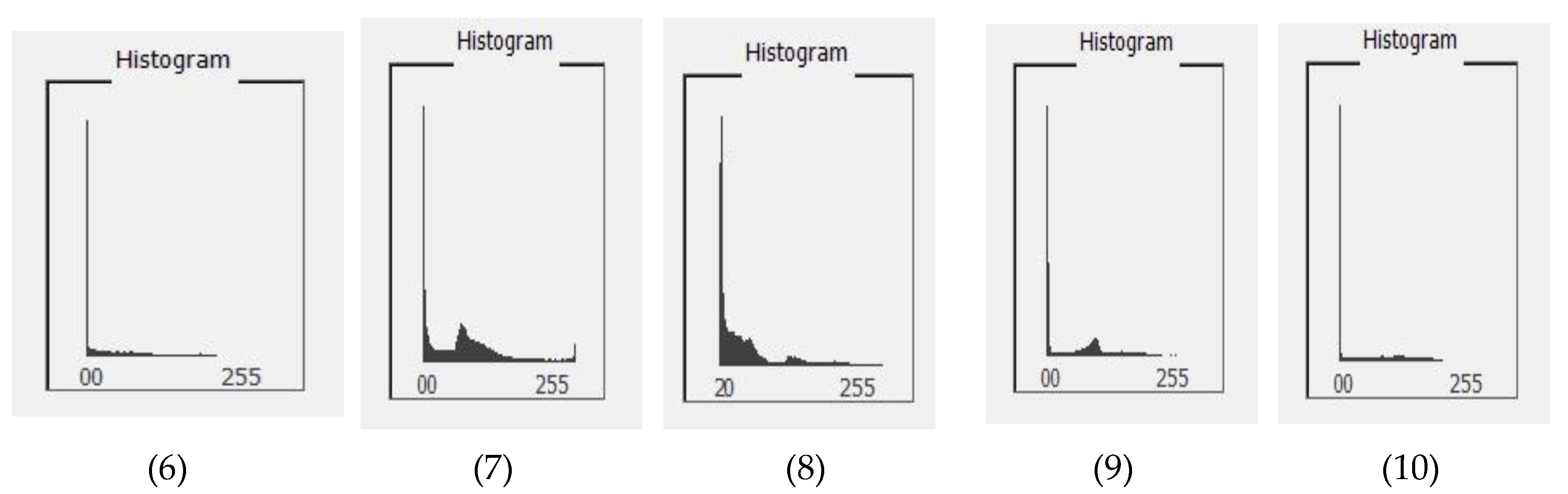
| Image | Unique Colors | Maximum Capacity (Bits) |
|---|---|---|
| Image 1 | 256 | 16,384 |
| Image 2 | 256 | 16,384 |
| Image 3 | 236 | 15,104 |
| Image 4 | 244 | 15,616 |
| Image 5 | 251 | 16,064 |
| Image 6 | 187 | 11,968 |
| Image 7 | 256 | 16,384 |
| Image 8 | 256 | 16,384 |
| Image 9 | 256 | 16,384 |
| Image 10 | 193 | 12,352 |
| Embedded Payload (Bits) | Entropy of Cover Image ε(θ) | Entropy of Stego Image ε(φ) | Change in Entropy ε(θ) − ε(φ) | Kullback Leibler Divergence | Distortion Function | NPCR | UACI | |
|---|---|---|---|---|---|---|---|---|
| Image 1 | 100% | 7.001516 × 102 | 7.001516 × 102 | 0 | 0 | 0 | 0 | 0 |
| 75% | 7.001516 × 102 | 7.001516 × 102 | 0 | 0 | 0 | 0 | 0 | |
| 50% | 7.001516 × 102 | 7.001516 × 102 | 0 | 0 | 0 | 0 | 0 | |
| Image 2 | 100% | 6.329050 × 102 | 6.329050 × 102 | 0 | 0 | 0 | 0 | 0 |
| 75% | 6.329050 × 102 | 6.329050 × 102 | 0 | 0 | 0 | 0 | 0 | |
| 50% | 6.329050 × 102 | 6.329050 × 102 | 0 | 0 | 0 | 0 | 0 | |
| Image 3 | 100% | 6.013431 × 102 | 6.013431 × 102 | 0 | 0 | 0 | 0 | 0 |
| 75% | 6.013431 × 102 | 6.013431 × 102 | 0 | 0 | 0 | 0 | 0 | |
| 50% | 6.013431 × 102 | 6.013431 × 102 | 0 | 0 | 0 | 0 | 0 | |
| Image 4 | 100% | 7.266514 × 102 | 7.266514 × 102 | 0 | 0 | 0 | 0 | 0 |
| 75% | 7.266514 × 102 | 7.266514 × 102 | 0 | 0 | 0 | 0 | 0 | |
| 50% | 7.266514 × 102 | 7.266514 × 102 | 0 | 0 | 0 | 0 | 0 | |
| Image 5 | 100% | 6.192335 × 102 | 6.192335 × 102 | 0 | 0 | 0 | 0 | 0 |
| 75% | 6.192335 × 102 | 6.192335 × 102 | 0 | 0 | 0 | 0 | 0 | |
| 50% | 6.192335 × 102 | 6.192335 × 102 | 0 | 0 | 0 | 0 | 0 | |
| Image 6 | 100% | 5.389515 × 102 | 5.389515 × 102 | 0 | 0 | 0 | 0 | 0 |
| 75% | 5.389515 × 102 | 5.389515 × 102 | 0 | 0 | 0 | 0 | 0 | |
| 50% | 5.389515 × 102 | 5.389515 × 102 | 0 | 0 | 0 | 0 | 0 | |
| Image 7 | 100% | 6.982189 × 102 | 6.982189 × 102 | 0 | 0 | 0 | 0 | 0 |
| 75% | 6.982189 × 102 | 6.982189 × 102 | 0 | 0 | 0 | 0 | 0 | |
| 50% | 6.982189 × 102 | 6.982189 × 102 | 0 | 0 | 0 | 0 | 0 | |
| Image 8 | 100% | 6.401003 × 102 | 6.401003 × 102 | 0 | 0 | 0 | 0 | 0 |
| 75% | 6.401003 × 102 | 6.401003 × 102 | 0 | 0 | 0 | 0 | 0 | |
| 50% | 6.401003 × 102 | 6.401003 × 102 | 0 | 0 | 0 | 0 | 0 | |
| Image 9 | 100% | 5.757388 × 102 | 7.001516 × 102 | 0 | 0 | 0 | 0 | 0 |
| 75% | 5.757388 × 102 | 7.001516 × 102 | 0 | 0 | 0 | 0 | 0 | |
| 50% | 5.757388 × 102 | 7.001516 × 102 | 0 | 0 | 0 | 0 | 0 | |
| Image 10 | 100% | 5.523392 × 102 | 5.523392 × 102 | 0 | 0 | 0 | 0 | 0 |
| 75% | 5.523392 × 102 | 5.523392 × 102 | 0 | 0 | 0 | 0 | 0 | |
| 50% | 5.523392 × 102 | 5.523392 × 102 | 0 | 0 | 0 | 0 | 0 |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Rashid, A.; Salamat, N.; Prasath, V.B.S. An Algorithm for Data Hiding in Radiographic Images and ePHI/R Application. Technologies 2018, 6, 7. https://doi.org/10.3390/technologies6010007
Rashid A, Salamat N, Prasath VBS. An Algorithm for Data Hiding in Radiographic Images and ePHI/R Application. Technologies. 2018; 6(1):7. https://doi.org/10.3390/technologies6010007
Chicago/Turabian StyleRashid, Aqsa, Nadeem Salamat, and V. B. Surya Prasath. 2018. "An Algorithm for Data Hiding in Radiographic Images and ePHI/R Application" Technologies 6, no. 1: 7. https://doi.org/10.3390/technologies6010007




