1. Introduction
The problem of finding the shortest path from a specified source node to a destination node is a fundamental and well known combinatorial optimization problem in graph theory. Many real world problems, e.g., transportation, communication, scheduling, economical system analysis, supply chain management, computer network, etc., can be modeled as an SPP. A common algorithm to solve the classical SPP is the Dijkstra’s algorithm [
1,
2].
In many applications such as urban traffic planning, routing of telecommunication messages, telemarketing operator scheduling, optimal pipelining of VLSI chip, texture mapping, etc., graphs emerge as a mathematical model of the observed real world system. Many problems can be reformulated as a quest for a path between two nodes in a graph which is optimal in the sense of a number of preset criteria. These optimality criteria are evaluated in terms of weights, i.e., vectors of real numbers, associated with the links of the graph. In a real-world model, an edge is associated with a direction and with a measure of impedance, determining the parameters, like time, cost, capacity, demand, traffic frequency, etc., along the network. In real life applications, like vehicle green routing and scheduling, transportation, etc., which are related to environmental issues, the arc lengths could be uncertain due to the fluctuation with traffic conditions or weather conditions, even if the geometric distance is fixed. Therefore finding the optimal path in such networks could be challenging. Fuzziness can be introduced into a network/graph to deal with this type of uncertain situations.
There are many efforts in FSPP [
3,
4,
5,
6,
7,
8,
9,
10,
11,
12,
13,
14,
15,
16,
17] using T1FS. An algorithm for FSPP was proposed first by Dubois and Prade [
3] based on the extension of the classical Floyd and Ford-Moore-Bellman (FMB) algorithms. They introduced the idea of criticality of a path. Given a fuzzy number,
, which is equivalent to the length of the shortest path between the nodes
i and
j, the value of criticality for each path
p is defined as the possibility that the fuzzy length
of the path
p can be the shortest path. It can be considered as a membership value of path
p in the fuzzy set of the shortest paths between the nodes
i and
j.
has been treated as a possibility distribution of the shortest distance between the nodes
i and
j. However, the problem of the algorithm is that the path corresponding to the shortest distance may not exist. Chanas and Kamburowski [
6] defined a fuzzy strict preference relation to select a path and used it in their proposed algorithm for the shortest path problem. They have not used the membership function for the shortest path as described in [
3]. In klein’s algorithm [
4], each arc is represented by an integer value in between 1 and a fixed upper integer bound. The proposed algorithm used dynamic programming recursion to find a path or paths corresponding to a threshold value of membership degree decided by the decision maker. Yager proposed an algorithm [
11] for FSPP based on the idea of possibility production system. He assigned a possibility to traversing between two states and computed the overall possibility of a path between initial and goal states using T-norm. The proposed algorithm finds the path which has the maximum possibility. The author described a heuristic search technique to avoid the combinatorial explosion to reduce the time for finding optimal solution. In [
12], Lin and Chern defined an arc as a most vital arc in the network if its removal from the network increases the shortest distance maximum. The availability of a single most vital arc plays an important role in FSPP. The arc length of their network is represented by a triangular fuzzy number. They have derived a membership function of the shortest distance by applying a fuzzy linear programming approach. Based on this result, the authors have introduced an algorithm for computing the single most vital arc in a network. In [
13], Okada and Soper assigned a fuzzy number to each arc length. They introduced an order relation among the fuzzy numbers based on “fuzzy max” and “fuzzy min” for the purpose of generating nondominated paths. The proposed algorithm generates all nondominated paths from source node to other nodes. It is based on the multiple labeling [
18] method for a multicriteria shortest path. A drawback of the proposed algorithm is that the number of paths cannot be decided by the decision maker. For a large network, the number of paths is too large. In that case, the authors suggest
h-nondominated paths, where the higher the possibility level
h is, the lower the number of
h-nondominated paths is. In [
8], Okada has also used a fuzzy number for arc length of a directed network. The length of a path is defined as the fuzzy sum of all arc lengths present in the path. Every pair of paths from source node to another node is considered to be interactive, i.e., not independent because both the paths may share common arcs. Each arc has a degree of possibility to be in the shortest path. Multiple lebeling method and
α-level sets of fuzzy number were considered in the proposed algorithm. Takahashi et al. [
9] described the SPP with fuzzy parameters and modified the algorithm proposed by Okada [
8]. They also proposed a genetic algorithm to find an approximate solution for large-scale problems. Nayeem and Pal [
14] represented the arc lengths of a network by imprecise numbers, which are the interval number and triangular fuzzy number. The algorithm, proposed by them, finds a fuzzy shortest path and can handle both types of imprecise numbers. The authors have introduced the idea of acceptability index to define a ranking order among the fuzzy numbers. Acceptability index is used to find the grade of satisfaction of the decision maker. However, the disadvantage of their algorithm is that it can give more than one solution for a particular value of acceptability index [
19]. Moazeni [
15] assigned a positive fuzzy quantity with finite support for each arc length and defined a lexicographic order relation among the arcs. Based on extension principle, the author proposed an algorithm for finding the set of non dominated paths from a specified node to every other nodes on a network. The concept of Hansen’s multiple labeling method [
18] and Dijkstra’s shortest path algorithm [
1] were used in the proposed algorithm. In [
16], Hernandes et al. proposed a generic algorithm for FSPP, where triangular fuzzy numbers are used to represent the arc lengths. In their algorithm, a generic ranking index is used for comparing the fuzzy arcs. This algorithm is based on the Ford-Moore-Bellman algorithm. The proposed algorithm has some advantages. Firstly, It can detect the negative circuits and so can be applied in graphs having negative parameters. Secondly, various order relations or ranking indices can be used in the algorithm so that depending on the ranking index selected by the decision maker, the algorithm will provide a set of solution paths, which are shortest. Mahdavi et al. [
10] proposed a fuzzy dynamic programming approach to solve the fuzzy shortest path chain problem using a suitable fuzzy ranking method. This ranking method helps to avoid generating the set of Pareto optimal paths since the number of Pareto optimal paths from a large network can be a large number. In that case it could be very hard for a decision maker to select a preferable path. Deng et al. [
17] have introduced a generalized Dijkstra’s algorithm to handle the SPP in an fuzzy environment. They have described the SPP with trapezoidal fuzzy numbers. The graded mean integration representation of trapezoidal fuzzy numbers is used in their proposed algorithm to find the addition of fuzzy edges and to compare the fuzzy distance between two different paths. Hassanzadeh et al. [
5] proposed an algorithm for the computation of the shortest path in a network with mixed fuzzy arc lengths. They described an addition operation using
α cut to compute the path. In their addition, a least square model is constructed to find an approximation of the corresponding membership function for the addition. They presented a genetic algorithm for the FSPP to handle the complexity of the addition operation of mixed fuzzy numbers for a large fuzzy network.
In this study, we represent each arc length as an IT2FS. The membership degree of a T1FS is crisp, which is evaluated by human perception. There is also uncertainty in the membership degree and it is difficult to determine the exact membership function of the fuzzy set. If the edge weights of a network vary under certain condition such as time or edge weights are generated from multiple sources [
20,
21,
22,
23] which fluctuate regularly, then the weights can not be expressed by T1FS. For example, mathematical description of the time-variability of traffic frequency is unknown to us or knowledge (parameter values) gathered from a group of experts using questionnaires involve uncertain words [
24,
25,
26,
27]. T1FSs are not able to directly model such uncertainties as their membership functions are totally crisp. The solution for this problem can be type-2 fuzziness, where fuzzy sets have grades of membership those are themselves fuzzy [
28,
29]. Type-2 fuzzy set (T2FS) increases the number of degrees of freedom to describe uncertainty and has more capacity to handle inexact (fuzzy) information in a logically correct manner. Since the generalized type-2 fuzzy logic systems (T2FLS) are computationally very demanding, many researchers have used interval type-2 fuzzy logic system (IT2FLS) in practical fields [
30,
31,
32,
33]. Computations in IT2FLS are more manageable compared to generalized T2FLS [
34,
35]. Both the generalized and interval type-2 fuzzy membership functions are three-dimensional, only the difference is that the secondary membership value of the interval type-2 membership function, in general, is equal to 1. IT2FS is a special form of T2FS and can improve certain type of inference more efficiently than T1FS with an increasing imprecision and uncertainty. It opens up an efficient way of developing improved systems for modeling human decision making [
26,
36,
37,
38,
39,
40].
As a suitable application of IT2FS from the Indian context, we can consider the recently witnessed severe flood and landslide in Uttarakhand on 16 June 2013. Destruction of bridges and roads disconnected most of the cities and tourist spots and left about 100,000 pilgrims and tourists trapped in the valleys. This type of disasters need search for shortest/fastest evacuation routes and rescue routes. From the information of the beginning and terminal points of the remaining (after disaster) roads and bridges, the smallest route and distance can be computed for fastest rescue [
41,
42]. However, this information is not precise. The information is collected from different individuals, e.g., tourists, pilgrims, trekker, military personnel, civil engineers, etc. Different types of uncertainties associated with this information are as follows:
- (i)
The meaning of the words that are used in the description can be uncertain [
43,
44]. Words mean different things to different people [
45,
46,
47,
48,
49,
50,
51]. This is due to linguistic uncertainties.
- (ii)
Measurements that activate a type-1 fuzzy logic system may be noisy and therefore uncertain.
- (iii)
Information, i.e., data varies with time due to the new construction and repair of damaged roads and bridges.
All of these uncertainties translate into uncertainties about fuzzy set membership functions. T1FSs are not able to directly model such uncertainties because their membership functions are totally crisp. It can be tackled by T2FS or by its simpler version IT2FS.
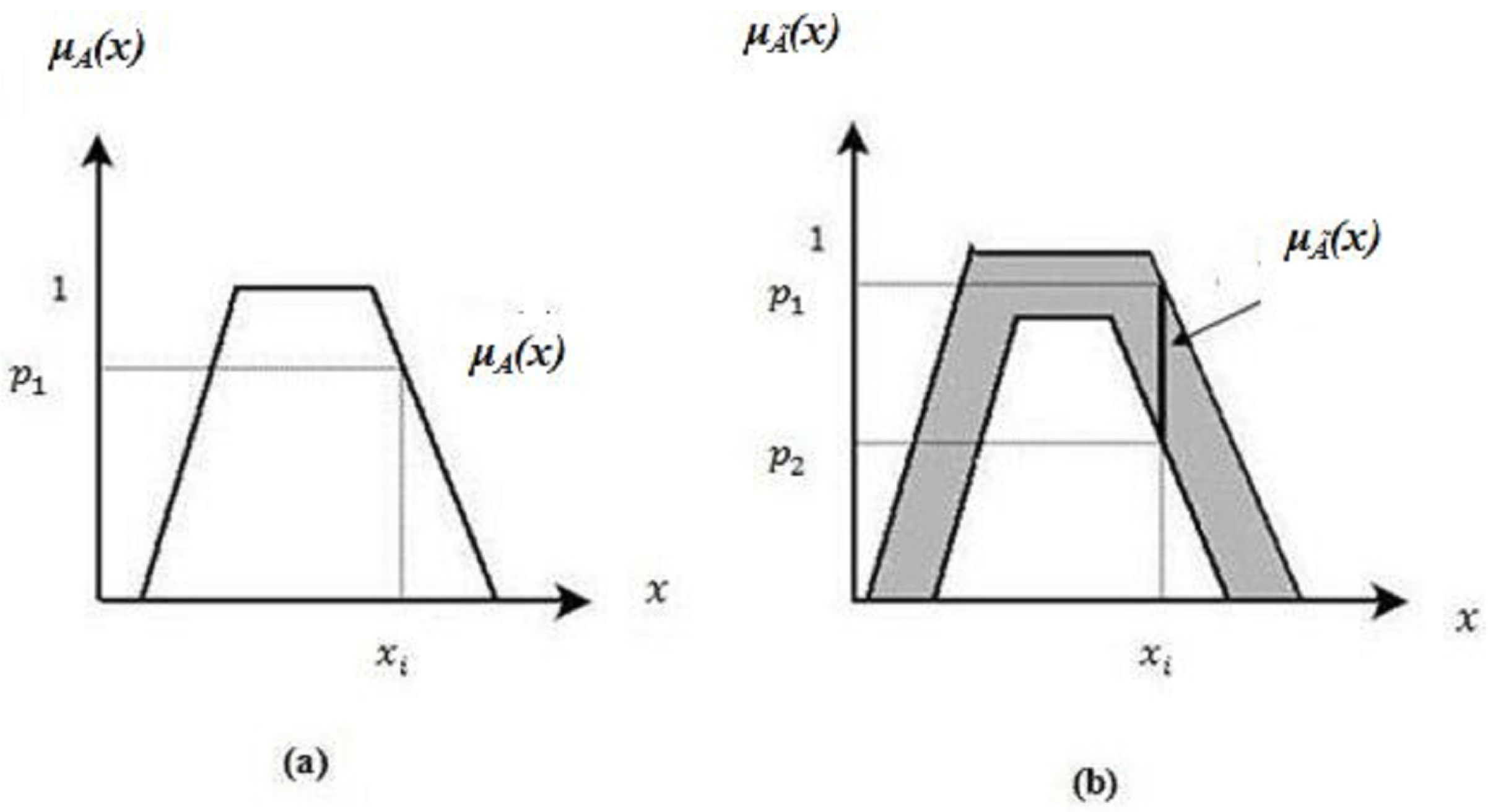
Let us define
A as a T1FS and
as an IT2FS respectively as shown in
Figure 1a,b. For a specific value of
x, say
, we get a single membership value
in
A. However, for the same value of
, there is a set of interval membership values between
and
in
.
Two key matters are generally addressed in SPP with IT2FSs or T2FS. One is how to find the addition of two arcs to determine the path length and the other is how to compare between the path lengths of two different paths. A variety of methods for addition operation between IT2FSs have been proposed in the literature [
52,
53,
54]. In [
52], the authors have used trapezoidal fuzzy set for upper membership function (UMF) and non normal triangular set (the height is less than or equal to 1) for lower membership function (LMF). The canonical forms for such kind of trapezoidal IT2FSs are used in their work [
52]. Let
=
=
, where
and
are respectively as given below.
Similarly = = .
An addition operation on such type of IT2FSs
and
is defined in [
52] as follows.
V. Anusuya and R. Sathya [
55] have proposed an algorithm for SPP from a source node to a destination node on a network in which a type-2 fuzzy number is assigned to each arc as its arc length. All the possible paths between source node and destination node and their corresponding path lengths are computed in their proposed algorithm. For this purpose, the authors have added type-2 fuzzy numbers corresponding to the arcs present in the path. Then, they have converted the type-2 fuzzy number representing a path length to its complement form and computed its rank. The path corresponding to the lowest rank has been assigned as the shortest path. Though the authors have claimed that this method is flexible and intelligent, they did not provide any justification for using the complement of type-2 fuzzy number. In [
56], the authors assigned a discrete type 2 fuzzy number to each arc of the network and computed the path lengths of all possible paths between source node and destination node using the same method as in [
55]. For comparison purpose they have used a function to find the minimum of two discrete type 2 fuzzy numbers representing two paths based on which a metric called similarity measure is computed. The shortest path corresponds to the highest similarity degree.
The motivation behind the work in this article is to find an algorithm for SPP which will be simple enough and effective in real world scenarios. We propose an algorithm to find a shortest path based on Dijkstra’s algorithm in a fuzzy graph, where the arc lengths are trapezoidal IT2FSs. Triangular IT2FS is a special case of trapezoidal IT2FS. Based on the concept described in [
53], we derive an operation for adding
2 number of IT2FSs corresponding to the arcs (arc lengths) present in the path. The operator for comparing two IT2FSs can be defined in a wide variety of ways [
45,
57]. We use centroid based ranking [
57] to choose the shortest path associated with the lowest value of centroid.
The paper is organized as follows.
Section 2 briefly reviews some basic concepts and definitions on fuzzy graph, type-2 fuzzy set (T2FS), IT2FS, centroid based ranking on IT2FS and path algebra. In
Section 3, we describe the proposed algorithm for IT2FSPP where uncertainty associated with IT2FS has been incorporated in Dijkstra’s algorithm. The corresponding path algebra and its generalized algorithm are also presented in this section. We present numerical examples in
Section 4 to illustrate the effectiveness of the algorithm. Finally, we conclude in
Section 5.
2. Preliminaries
In this section, we introduce fuzzy graph, T2FS, IT2FS, footprint of uncertainty, addition of IT2FSs, centroid based ranking on IT2FS and path algebra to facilitate future discussion.
Definition 1. Let V be a finite and non empty set. A fuzzy graph is a pair of functions G = , where σ is a fuzzy subset of V and μ is a symmetric fuzzy relation on σ, i.e., σ: and μ: V such that Definition 2. [34] A type-2 fuzzy set, denoted as , is characterized by a type-2 membership function , where x ∈
X and u ∈
⊆
, i.e.,in which 0 ≤ ≤ 1. Here, x, , u and are respectively primary variable, primary membership function of x, secondary variable and secondary membership function at x. can also be expressed asHere, and denotes union over all admissible x and u. For discrete universes of discourse ∫ is replaced by ∑.
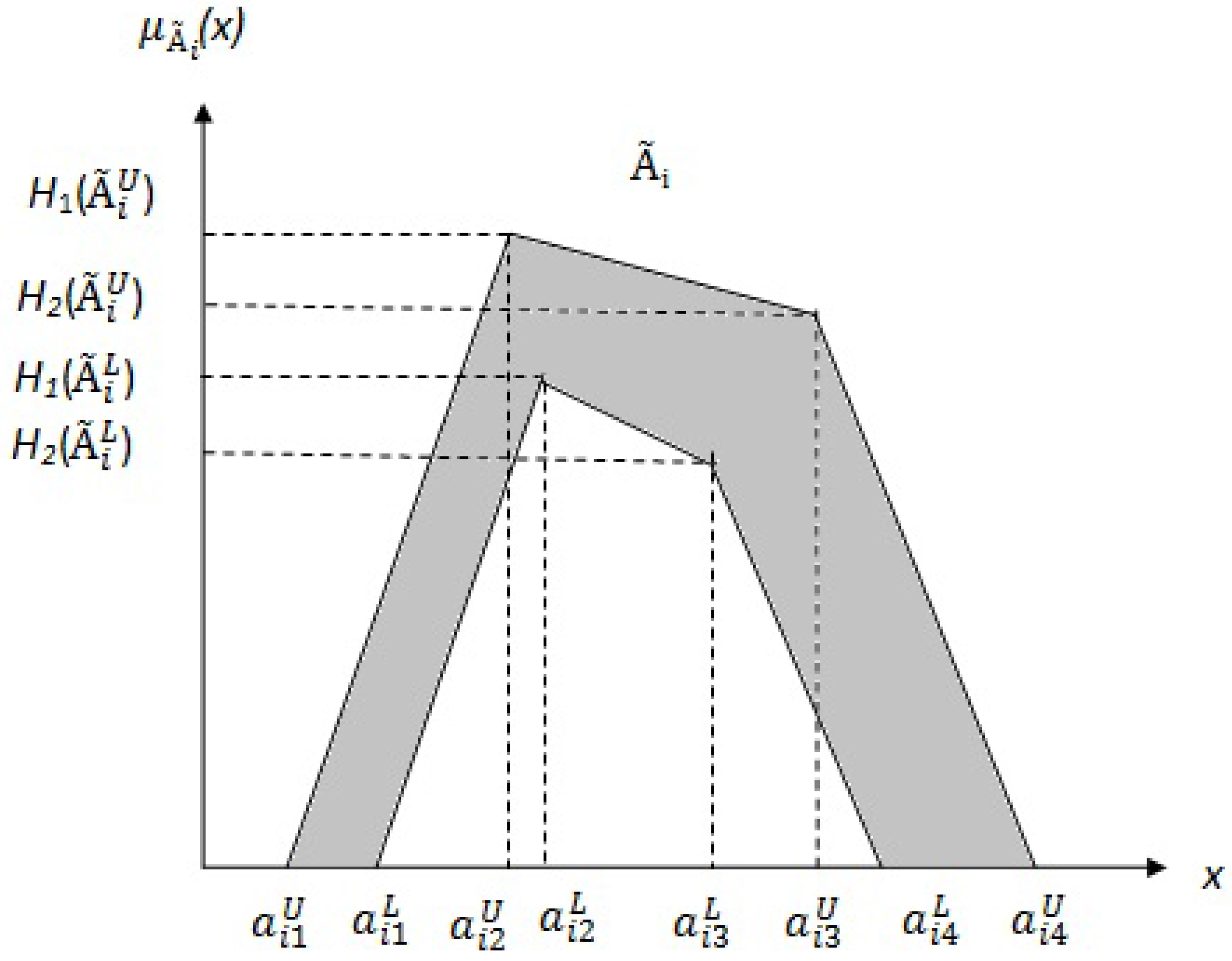
Definition 3. Let V be a finite and non empty set. A fuzzy graph is a pair of functions G = , where σ is a fuzzy subset of V and μ is a symmetric fuzzy relation on σ, i.e., σ: and μ: V such that Definition 4. [34] IT2FS is a special case of T2FS which has uniform shading over the entire FOU. A T2FS with uniform secondary membership function is called an IT2FS. Let be an IT2FS, then it is described asHere, x is the primary variable, , an interval in [0,1], is the primary membership of x, u is the secondary variable and is the secondary membership function at x. A trapezoidal IT2FS
is shown in
Figure 2. The reference points and their corresponding heights of the upper and the lower membership functions of IT2FS characterize an IT2FS. The shaded region is the FOU. It is bounded by an upper membership function (UMF), denoted by
or
, and a lower membership function (LMF), denoted by
or
. The UMF and LMF both are type-1 fuzzy Sets (T1FSs).
Let us consider two trapezoidal IT2FSs
and
, where
The addition [
53] operation (⊕) between the two trapezoidal IT2FSs
and
is defined in (6) as follows:
It shows that the result of addition operation is also a trapezoidal IT2FS. So, it can also be added to another IT2FS
, the result of which is again an IT2FS, say
. In this way, we can add
n number of IT2FSs as defined below in (7).
Here, (7) represents an IT2FS. So, we can conclude that the path between two nodes can be represented by an IT2FS, obtained by adding all the IT2FSs corresponding to the arcs, present in the path.
Definition 5. The path between any two nodes in a fuzzy graph can be represented by an IT2FS, obtained by adding all the IT2FSs corresponding to the arcs present in the path.
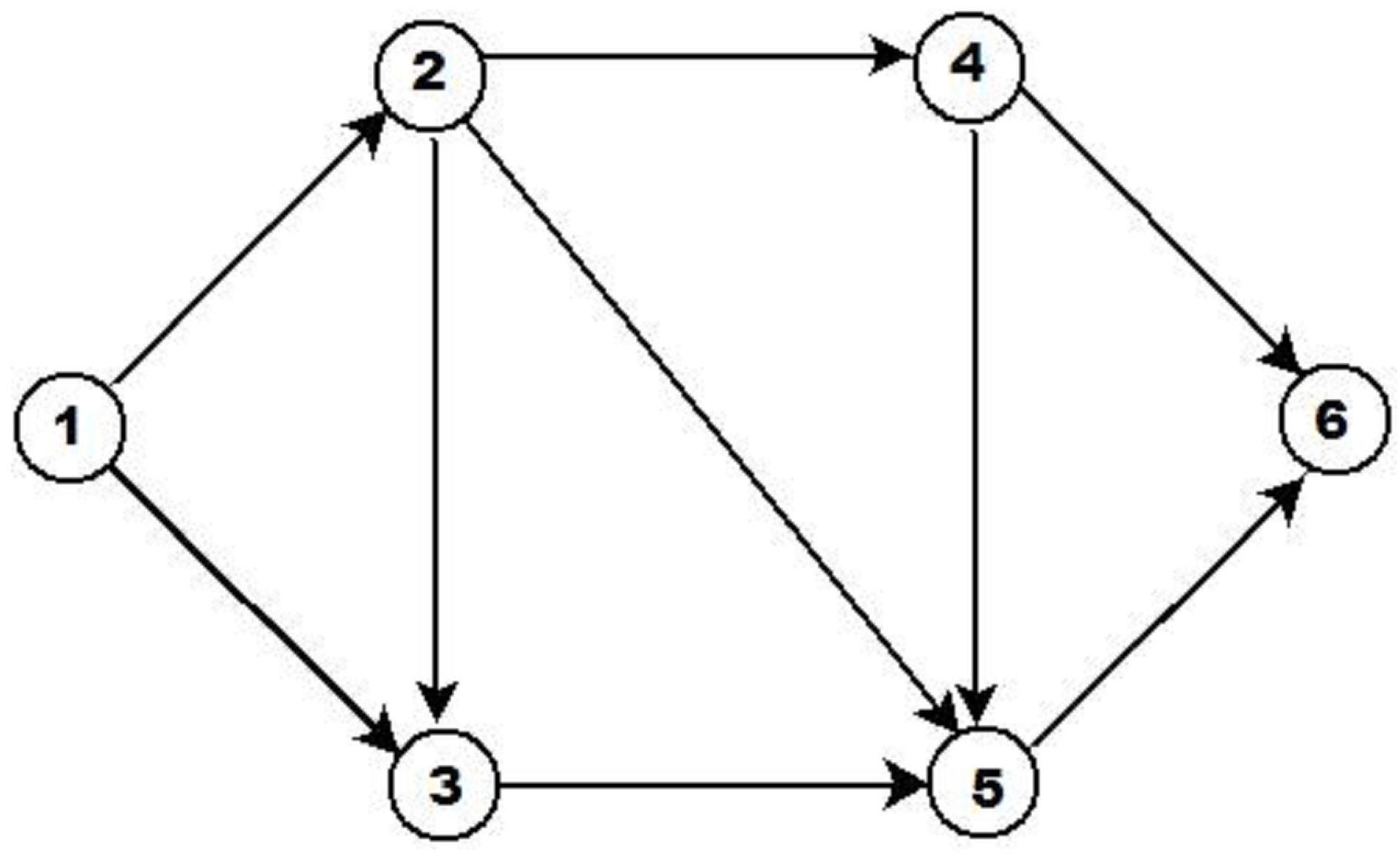
As an example, let us consider a fuzzy graph, shown in
Figure 3, having 6 nodes and 9 arcs. The arcs are represented by IT2FSs, which are shown in
Table 1. Let
is an IT2FS, where
i and
j denote two nodes associated with the arc (
) directly. Using the law of association on addition operation of IT2FSs, explained above, the path from the node 1 to the node 6, through the nodes 2, 3 and 5 can be expressed as follows:
Here,
and
are two IT2FSs representing two paths, first one from the node 1 to node 3 through the node 2 and the other one from the node 1 to the node 5 through the nodes 2 and 3. Note that there are two different paths represented by
and
, from node 1 to node 3.
represents the direct connection by the arc (1,3) and
is through the node 2.
Ranking of IT2FSs is important for IT2FSPP. Since IT2FSs do not form any natural linear order, like real numbers, a key issue is how to compare two IT2FSs. Defuzzification, in general, is a method to map an IT2FS into a real number. The real numbers are then compared. Many defuzzification [
57,
58,
59,
60,
61] methods are present in the literature. In this study, the centroid based ranking method [
61] is used to solve the IT2FSPP.
Definition 6. [61] The centroid of an IT2FS is the union of the centroids of all its embedded T1FSs , which is a closed interval as follows in (8). Here, and are respectively the minimum and maximum of all centroids of the embedded T1FSs in the FOU of as given below in (9) and (10). Equations (9) and (10) can be computed [
61,
62,
63] from the lower and upper membership functions of
as follows:
Here
is the switch point that marks the change from
to
and
is the switch point that marks the change from
to
.
N is the number of discrete points based on which the domain of
x for
has been discretized. Let
<
< ... <
, where
and
are respectively the smallest and highest discrete values of
x. The pseudocode for computing
L and
are given in Algorithm 1 [
61,
62,
63]. Here, we have considered the discrete version of the algorithm.
Similarly,
R and
can be computed. Then, the average of
and
of IT2FS
, i.e.,
is computed using (16), which is the centroid based ranking value of IT2FS
.
The larger is the centroid value
, the greater is the arc length of the corresponding IT2FS
. As an example, let us consider the IT2FS
=
, used for the arc (1,2), as shown in
Table 1. To find the centroid based rank of
, we consider
N, specified in Algorithm 1, as 50. We compute an initial point
= 7.86 using (13). This value is assigned in
. Then the value of
k = 21 is computed following the loop defined in step 4. From (15), we get
= 7.28 using the value of
k as 21. As the values of
(=7.86) and
(=7.28) are not equal, we repeat the do — while loop (step 2 to step 13) of Algorithm 1 until the value of
and
converges, i.e., they have the same value, which is 7.24 for this example. So, we get the value of
= 7.24. Similarly, we compute the value of
= 8.56. The average of
and
of IT2FS
, i.e.,
= 7.90 is computed using (16).
| Algorithm 1 Pseudocode for computing left switch point L and . |
| 1: | Initialize |
| | |
| | where
|
| 2: | do |
| 3: | Set = |
| 4: | Find k (1 ≤k ≤ ) such that ≤ ≤ |
| 5: | for i=1 to N do |
| 6: | if then |
| 7: | = |
| 8: | else |
| 9: | = |
| 10: | end if |
| 11: | end for |
| 12: | Compute |
| | |
| 13: | while ( is not equal to ) |
| 14: | = (= ) and L=k |
| 15: | Print the value of and L and terminate |
Definition 7. Let and are two IT2FSs. Then ≻ if and only if > .
≺ if and only if < .
∼ if and only if = .
Here, ≻
implies that the length of the arc represented by is greater than the length of the arc represented by . Similarly, ≺
implies that the length of the arc represented by is less than the length of the arc represented by . ∼
implies that the length of the arc represented by is same the length of the arc represented by . Thus, ranking values of IT2FSs provide a natural order among those IT2FSs. As an example, let us consider a fuzzy graph, shown in
Figure 3. Here, node 1 is connected with node 2 and node 3. The arcs (1,2) and (1,3) are represented by IT2FSs, which are shown in
Table 1. By the centroid based ranking value, we get
= 7.90 and
= 8.12, i.e.,
≺
. Thus, the length of the arc represented by
is less than the length of the arc represented by
.
Path Algebra
Here, we consider the SPP in an algebraic framework, namely path algebra for the purpose of generalization of the proposed algorithm.
Definition 8. Let E be a set and ⊕
be an operator on E and ϵ ∈
E. Then is said to be a monod with zero element ϵ if- (i)
⊕ is associative: ∀ a, b, c ∈ E, a ⊕ (b ⊕ c) = (a ⊕ b) ⊕ c
- (ii)
∀ a ∈ E, a ⊕ ϵ = ϵ ⊕ a = a.
A monod is said to be commutative if ⊕ is commutative: ∀ a, b ∈ E, a ⊕ b = b ⊕ a.
Definition 9. [64] Let us consider an algebraic structure consisting of a set E, with two internal operator ⊕
(“addition”) and ⊗
(“multiplication”). is a semiring if the following properties hold:- (i)
is a commutative monod with zero element ϵ.
- (ii)
is a monod with unit element e.
- (iii)
⊗ is a right and left distributive with respect to ⊕.
- (iv)
ϵ is absorbing, i.e., ϵ ⊗ a = a ⊗ ϵ = ϵ ()
Definition 10. [64] being a monod, the binary relation ≤ on E is defined as: a ≤ b if ∃
c ∈
E such that b = a ⊕
c, is a preorder relation (transitive and reflexive) called the canonical preorder. A monod is known as canonically ordered if the canonical preorder is an order, or equivalently if ≤ is antisymmetric relation, i.e., (a ≤ b and b ≤ a ⇒
a = b). A semiring in which is canonically ordered is a diod. Definition 11. [65] A path algebra is an algebraic structure with the following two properties.- 1.
is a diod.
- 2.
The operator ⊕ is idempotent, i.e., ∀ a ∈ L, a ⊕ a = a.
The second property imposes a natural order in the path algebra.
3. Proposed Dijkstra’s Algorithm for IT2FSPP
Proposed algorithm is the extension of Dijkstra’s algorithm for SPP. We have incorporated the concept of uncertainty in Dijkstra’s algorithm using IT2FS as an arc length. The pseudocode of the proposed Dijkstra’s algorithm for IT2FSPP is shown in Algorithm 2. The proposed algorithm finds the shortest path from a source node to a destination node of a directed acyclic graph. The source and destination nodes are different and denoted respectively by s and d. Q is used to store all the nodes of the fuzzy graph G, which are currently unvisited. Let v be a node of fuzzy graph G, then is the current shortest distance of v from the source node and is the length of the arc connecting two adjacent nodes u and v. The and both are expressed by IT2FS and stores the node, previous to the current node v along the shortest path from the source node. We use a function that receives an IT2FS as input and returns the centroid based ranking value, i.e., rank of the IT2FS. Another variable is used to store the rank of the shortest path from the source node to v. u is used as a node in Q which has currently the lowest value of rank.
In this study, we are interested only for the shortest path from node s to node d. So, we do not need to check whether Q is empty or not as done in original Dijkstra’s algorithm. Once we get the destination node d, we terminate the algorithm. Finally, gives the length of the shortest path from s to d, which is an IT2FS. We can also find the corresponding path starting from the destination node and moving backward to the source node using .
The classical Dijkstra’s algorithm has time complexity of
when adjacency matrix is used. Here,
represents the number of nodes in the graph. In our proposed algorithm, we have used the well known KM algorithm [
57,
61,
66], for computing the centroid based ranking value of an IT2FS, as described earlier in Definition 6. The time complexity to compute the rank of an IT2FS, which represents a path is
, where
N is the number of discretization points in the interval and
M is the number of iterations required for convergence. Hence, the computational complexity of the proposed algorithm is
.
| Algorithm 2 Pseudocode of the proposed algorithm. |
| 1: | rank[s] ← 0 | |
| 2: | dist[s] ← null | ▷ Corresponding IT2FS is empty |
| 3: | add s to Q | |
| 4: | for each vertex i (except the s) in the fuzzy graph do | |
| 5: | rank[i] ← INFINITY | |
| 6: | add i to Q | ▷ Initialize Q with all the nodes of the graph |
| 7: | end for | |
| 8: | | |
| 9: | while (u is not the the destination node d) do | ▷ Shortest path from s to d |
| 10: | remove the node u from Q | |
| 11: | for every node v adjacent to u do | |
| 12: | temp_dist ← dist ⊕ arc_length() | ▷ as described in (6) |
| 13: | temp_rank ← centroid_rank (temp_dist) | |
| 14: | if (temp_rank < rank[v]) then | |
| 15: | dist ← temp_dist | |
| 16: | rank[v] ← temp_rank[v] | |
| 17: | previous[v]←u | |
| 18: | end if | |
| 19: | end for | |
| 20: | vertex in Q with the smallest rank value | |
| 21: | end while | |
| 22: | The IT2FS is an IT2FS and it represents length of the shortest path. | |
In the path algebra L, defined in Definition 11, let p be the set of all IT2FSs and the binary operators ⊕ and ⊗ are replaced respectively by among two IT2FSs for which the rank is less and addition of two IT2FSs. This two operators are defined below.
,
a ⊕
b =
where
=
Here,
is the centroid based ranking value of
a and the
operator is same as the addition operation of two IT2FSs, respectively defined in (13) and (6). Then the algebraic structure
L =
follows the properties of path algebra which corresponds to the generalization of the proposed algorithm, i.e., Dijkstra’s algorithm using IT2FSs, where, zero element
and unit element
e = ((0, 0, 0, 0; 1, 1), (0, 0, 0, 0; 1, 1)). Here,
ϵ is the largest IT2FS, i.e.,
= ∞. The proof that the proposed algebraic framework
is a path algebra is provided in
Appendix A. The path algebra has been widely applied for the formulation of graph path finding problems [
64,
67].
The generalized algorithm for the proposed modification based on path algebra
L =
is presented in Algorithm 3. Here,
is the current shortest path length from the source node
s to a node
l of the fuzzy graph
G. The weights of the edges in
G, i.e., arc lengths are the IT2FSs and
G does not contain any cycle of negative length.
is the set of all nodes connected to
u by an arc. From Gondran’s theorem [
68,
69] we can claim that the generalized algorithm for the proposed modification of Dijkstra’s algorithm always converges.
From the generalized algorithm, we can also compute its time complexity. In the worst case, outer loop (while-do) is executed times and the inner loop is executed times because for a particular node the maximum possible numbers of its neighbors is . Hence, the time complexity of the algorithm is . It is worth mentioning that for computation of time complexity of Algorithm 3, step 10 has been considered as a single unit. The operations and , used in step 10, have not been considered separately for the execution of step 10.
| Algorithm 3 Pseudocode of the generalized algorithm for the proposed modification. |
| 1: | ← e | |
| 2: | add s to Q | |
| 3: | for each vertex i (except s) in G do | |
| 4: | ← ϵ | ▷ϵ is the highest IT2FS. |
| 5: | add i to Q | |
| 6: | end for | |
| 7: | s | |
| 8: | while (u is not the destination node d) do | |
| 9: | for all v ∈ { ∩ Q} do | ▷ is the set of all nodes connected to u through an arc. |
| 10: | ← (, (, arc_length)) | ▷ Choose a node v for which is minimum. |
| 11: | end for | |
| 12: | previous[v]←u | |
| 13: | Q ← Q \ {u} | |
| 14: | Find u, u ∈ Q such that is minimum among all s, i ∈ Q. | ▷ Using the natural order in the monod |
| 15: | end while | |
| 16: | gives the shortest path length from s to d. | |