Cryptography in Wireless Multimedia Sensor Networks: A Survey and Research Directions
Abstract
:1. Introduction
2. Security Issues in Multimedia Sensor Networks
- Authenticity: Sensor nodes and transmitted packets should be authenticated. Malicious sensor nodes could enter the network to steal information or inject packets. The verification of the packets’ origins is desired in many cases.
- Availability: Some applications may require that a minimum level of availability is assured during the network operation, but attacks may reduce the attainable availability in different ways (compromising communication, processing or sensing coverage).
- Confidentiality: Sensed data and control information may be confidential, since their content must not be accessible by intruders or external elements.
- Freshness: Attackers should not be able to exploit old messages, which require the adoption of efficient mechanisms to control time scopes.
- Integrity: While confidentiality avoids that attackers can steal data, integrity will be concerned with data changing and manipulation.
- Localization: Secure localization is required to assure only accurate information is considered.
2.1. Security Threats
2.2. Security Defenses
2.3. Cryptography Algorithms
3. Multimedia Data Encryption
3.1. Image Cryptography
3.2. Video Cryptography
3.3. Audio Cryptography
4. Cryptography Approaches for WMSNs
5. Research Directions
6. Conclusions
Author Contributions
Conflicts of Interest
References
- Al-Fuqaha, A.; Mohammadi, M.; Aledhari, M.; Ayyash, M. Internet of Things: A Survey on Enabling Technologies, Protocols, and Applications. IEEE Commun. Surv. Tutor. 2015, 17, 2347–2376. [Google Scholar] [CrossRef]
- Atzori, L.; Iera, A.; Morabito, G. The Internet of Things: A Survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Granjal, J.; Monteiro, E.; Silva, J.S. Security in the Integration of Low-Power Wireless Sensor Networks with the Internet: A Survey. Ad Hoc Netw. 2015, 24, 264–287. [Google Scholar] [CrossRef]
- Almalkawi, I.; Zapata, M.; Al-Karaki, J.; Morillo-Pozo, J. Wireless multimedia sensor networks: Current trends and future directions. Sensors 2010, 10, 6662–6717. [Google Scholar] [CrossRef] [PubMed]
- Guerrero-Zapata, M.; Zilan, R.; Barcelo-Ordinas, J.M.; Bicakci, K.; Tavli, B. The future of security in wireless multimedia sensor networks. Telecommun. Syst. 2010, 45, 77–91. [Google Scholar] [CrossRef]
- Harjito, B.; Han, S. Wireless Multimedia Sensor Networks Applications and Security Challenges. In Proceedings of the International Conference on Broadband, Wireless Computing, Communication and Applications, Fukuoka, Japan, 4–6 November 2010; pp. 842–846.
- Winkler, T.; Rinner, B. Security and Privacy Protection in Visual Sensor Networks: A Survey. ACM Comput. Surv. 2014, 47, 97–116. [Google Scholar] [CrossRef]
- De Oliveira Gonçalves, D.; Costa, D.G. A Survey of Image Security in Wireless Sensor Networks. J. Imaging 2015, 1, 4–30. [Google Scholar] [CrossRef]
- Hayouni, H.; Hamdi, M.; Kim, T.H. A Survey on Encryption Schemes in Wireless Sensor Networks. In Proceedings of the International Conference on Advanced Software Engineering and Its Applications, Hainan, China, 20–23 December 2014; pp. 39–43.
- Shim, K.A. A Survey of Public-Key Cryptographic Primitives in Wireless Sensor Networks. IEEE Commun. Surv. Tutor. 2015, 18, 577–601. [Google Scholar] [CrossRef]
- Costa, D.G.; Guedes, L.A.; Vasques, F.; Portugal, P. Research Trends in Wireless Visual Sensor Networks When Exploiting Prioritization. Sensors 2015, 1, 1760–1784. [Google Scholar] [CrossRef] [PubMed]
- Costa, D.G.; Guedes, L.A. A Survey on Multimedia-Based Cross-Layer Optimization in Visual Sensor Networks. Sensors 2011, 11, 1084–1087. [Google Scholar] [CrossRef] [PubMed]
- Costa, D.G.; Guedes, L.A. The coverage problem in video-based wireless sensor networks: A survey. Sensors 2010, 10, 8215–8247. [Google Scholar] [CrossRef] [PubMed]
- Ghadi, M.; Laouamer, L.; Moulahi, T. Securing data exchange in wireless multimedia sensor networks: Perspectives and challenges. Multimed. Tools Appl. 2016, 75, 3425–3451. [Google Scholar] [CrossRef]
- Wang, Y.; Attebury, G.; Ramamurthy, B. Security issues in wireless sensor networks: A survey. Int. J. Future Gener. Commun. Netw. 2013, 6, 97–116. [Google Scholar] [CrossRef]
- Chen, X.; Makki, K.; Yen, K.; Pissinou, N. Sensor network security: A survey. IEEE Commun. Surv. Tutor. 2009, 11, 52–73. [Google Scholar] [CrossRef]
- Pathan, A.S.K.; Lee, H.W.; Hong, C.S. Wireless sensor networks: Security issues and challenges. Int. J. Comput. Inf. Technol. 2011, 2, 62–67. [Google Scholar]
- Costa, D.G.; Guedes, L.A. Exploiting the sensing relevancies of source nodes for optimizations in visual sensor networks. Multimed. Tools Appl. 2013, 64, 549–579. [Google Scholar] [CrossRef]
- Raymond, D.R.; Midkiff, S.F. Denial-of-Service in Wireless Sensor Networks: Attacks and Defenses. IEEE Pervasive Comput. 2008, 7, 74–81. [Google Scholar] [CrossRef]
- Ouyang, X.; Tian, B.; Li, Q.; Zhang, J.; Hu, Z.M.; Xin, Y. A Novel Framework of Defense System Against DoS Attacks in Wireless Sensor Networks. In Proceedings of the 7th International Conference on Wireless Communications, Networking and Mobile Computing (WiCOM), Wuhan, China, 23–25 September 2011; pp. 1–5.
- Manju, V.C.; Sasi, K.M. Detection of jamming style DoS attack in Wireless Sensor Network. In Proceedings of the 2nd IEEE International Conference on Parallel Distributed and Grid Computing (PDGC), Solan, India, 6–8 December 2012; pp. 563–567.
- Butun, I.; Morgera, S.; Sankar, R. A Survey of Intrusion Detection Systems in Wireless Sensor Networks. IEEE Commun. Surv. Tutor. 2014, 16, 266–282. [Google Scholar] [CrossRef]
- Karlof, C.; Wagner, D. Secure routing in wireless sensor networks: Attacks and countermeasures. In Proceedings of the IEEE International Workshop on Sensor Network Protocols and Applications, Anchorage, AK, USA, 11 May 2003; pp. 113–127.
- Buttyan, L.; Grilo, A.M. A Secure Distributed Transport Protocol for Wireless Sensor Networks. In Proceedings of the IEEE International Conference on Communications (ICC), Kyoto, Japan, 5–9 June 2011; pp. 1–6.
- Xu, M.; Liu, G.; Guan, J. Towards a Secure Medium Access Control Protocol for Cluster-Based Underwater Wireless Sensor Networks. Int. J. Distrib. Sens. Netw. 2015, 2015. [Google Scholar] [CrossRef]
- Dener, M. Security Analysis in Wireless Sensor Networks. Int. J. Distrib. Sens. Netw. 2014, 2014. [Google Scholar] [CrossRef] [PubMed]
- Sen, J. A Survey on Wireless Sensor Network Security. Int. J. Commun. Netw. Inf. Secur. 2009, 1, 55–78. [Google Scholar]
- Modares, H.; Salleh, R.; Moravejosharieh, A. Overview of security issues in wireless sensor networks. In Proceedings of the International Conference on Computational Intelligence, Modelling & Simulation, Langkawi, Malaysia, 20–22 September 2011; pp. 308–311.
- Macedonio, D.; Merro, M. A semantic analysis of key management protocols for wireless sensor networks. Sci. Comput. Programm. 2014, 81, 53–78. [Google Scholar] [CrossRef]
- Gaubatz, G.; Kaps, J.P.; Ozturk, E.; Sunar, B. State of the art in ultra-low power public key cryptography for wireless sensor networks. In Proceedings of the IEEE International Conference on Pervasive Computing and Communications Workshops, Kauai Island, HI, USA, 8–12 March 2005; pp. 146–150.
- Wang, Q.X.; Xu, T.; Zhou Wu, P. Application research of the AES encryption algorithm on the engine anti-theft system. In Proceedings of the IEEE International Conference on Vehicular Electronics and Safety (ICVES), Beijing, China, 10–12 July 2011; pp. 25–29.
- Panda, M. Data security in wireless sensor networks via AES algorithm. In Proceedings of the 2015 IEEE 9th International Conference on Intelligent Systems and Control (ISCO), Coimbatore, India, 9–10 January 2015; pp. 1–5.
- Jindal, P.; Singh, B. Performance analysis of modified RC4 encryption algorithm. In Proceedings of the International Conference on Recent Advances and Innovations in Engineering (ICRAIE-2014), Jaipur, India, 9–10 May 2014; pp. 1–5.
- Kukkurainen, J.; Soini, M.; Sydänheimo, L. RC5-based Security in Wireless Sensor Networks: Utilization and Performance. WSEAS Trans. Comput. 2010, 9, 1191–1200. [Google Scholar]
- Al-Hamami, A.H.; Aldariseh, I.A. Enhanced Method for RSA Cryptosystem Algorithm. In Proceedings of the International Conference on Advanced Computer Science Applications and Technologies, Kuala Lumpur, Malaysia, 26–28 November 2012; pp. 402–408.
- Al-Haija, Q.A.; Tarayrah, M.A.; Al-Qadeeb, H.; Al-Lwaimi, A. A Tiny RSA Cryptosystem Based On Arduino Microcontroller Useful For Small Scale Networks. Procedia Comput. Sci. 2014, 34, 639–646. [Google Scholar] [CrossRef]
- Liu, A.; Ning, P. TinyECC: A Configurable Library for Elliptic Curve Cryptography in Wireless Sensor Networks. In Proceedings of the International Conference on Information Processing in Sensor Networks (IPSN ’08), St. Louis, MO, USA, 22–24 April 2008; pp. 245–256.
- Ahmed, M.H.; Alam, S.W.; Qureshi, N.; Baig, I. Security for WSN based on elliptic curve cryptography. In Proceedings of the International Conference on Computer Networks and Information Technology (ICCNIT), Abbottabad, Pakistan, 11–13 July 2011; pp. 75–79.
- Othman, S.B.; Trad, A.; Youssef, H. Performance evaluation of encryption algorithm for wireless sensor networks. In Proceedings of the International Conference on Information Technology and e-Services (ICITeS), Sousse, Tunisia, 24–26 March 2012; pp. 1–8.
- Trad, A.; Bahattab, A.A.; Othman, S.B. Performance trade-offs of encryption algorithms for Wireless Sensor Networks. In Proceedings of the World Congress on Computer Applications and Information Systems (WCCAIS), Prague, Czech Republic, 24–26 March 2014; pp. 1–6.
- Costa, D.G.; Silva, I.; Guedes, L.A.; Vasques, F.; Portugal, P. Availability Issues in Wireless Visual Sensor Networks. Sensors 2014, 14, 2795–2821. [Google Scholar] [CrossRef] [PubMed]
- ZainEldin, H.; Elhosseini, M.A.; Ali, H.A. Image compression algorithms in wireless multimedia sensor networks: A survey. Ain Shams Eng. J. 2015, 6, 481–490. [Google Scholar] [CrossRef]
- Al-Zoubi, H.R. Video Coding and Routing in Wireless Video Sensor Networks. AASRI Procedia 2013, 5, 48–53. [Google Scholar] [CrossRef]
- Imran, N.; Seet, B.C.; Fong, A.C.M. A comparative analysis of video codecs for multihop wireless video sensor networks. Multimed. Syst. 2012, 18, 373–389. [Google Scholar] [CrossRef]
- Li, L.; Xin, G.; Sun, L.; Liu, Y. QVS: Quality-Aware Voice Streaming for Wireless Sensor Networks. In Proceedings of the 29th IEEE International Conference on Distributed Computing Systems (ICDCS ’09), Montreal, QC, Canada, 22–26 June 2009; pp. 450–457.
- Fu, Y.; Guo, Q.; Chen, C. A-LNT: A Wireless Sensor Network Platform for Low-Power Real-Time Voice Communications. J. Electr. Comput. Eng. 2014, 2014. [Google Scholar] [CrossRef]
- Massoudi, A.; Lefebvre, F.; Vleeschouwer, C.D.; Macq, B.; Quisquater, J.J. Overview on Selective Encryption of Image and Video: Challenges and Perspectives. EURASIP J. Inf. Secur. 2008, 2008. [Google Scholar] [CrossRef]
- Xiang, T.; Yu, C.; Chen, F. Fast Encryption of JPEG 2000 Images in Wireless Multimedia Sensor Networks. In Wireless Algorithms, Systems, and Applications, Proceedings of the 8th International Conference, WASA 2013, Zhangjiajie, China, 7–10 August 2013; Ren, K., Liu, X., Liang, W., Xu, M., Jia, X., Xing, K., Eds.; Springer: Berlin/Heidelberg, Germany, 2013; pp. 196–205. [Google Scholar]
- Nikolakopoulos, G.; Kandris, D.; Tzes, A. Adaptive Compression of Slowly Varying Images Transmitted over Wireless Sensor Networks. Sensors 2010, 10, 7170–7191. [Google Scholar] [CrossRef] [PubMed]
- Liu, J.; Wang, G. A refined quadtree-based automatic classification method for remote sensing image. In Proceedings of the International Conference on Computer Science and Network Technology, Harbin, China, 24–26 December 2011; pp. 1703–1706.
- Wang, Y.; Rane, S.; Boufounos, P.; Vetro, A. Distributed compression of zerotrees of wavelet coefficients. In Proceedings of the 18th IEEE International Conference on Image Processing, Brussels, Belgium, 11–14 September 2011; pp. 1821–1824.
- Costa, D.G.; Guedes, L.A. A discrete wavelet transform (DWT)-based energy-efficient selective retransmission mechanism for wireless image sensor networks. J. Sens Actuator Netw. 2012, 1, 3–35. [Google Scholar] [CrossRef]
- Elsabi, E.; Ozdemir, S. Secure data aggregation in wireless multimedia sensor networks via watermarking. In Proceedings of the International Conference on Application of Information and Communication Technologies, Georgia, Tbilisi, 17–19 October 2012; pp. 1–6.
- Harjito, B.; Han, S.; Potdar, V.; Chang, E.; Xie, M. Secure communication in wireless multimedia sensor networks using watermarking. In Proceedings of the IEEE International Conference on Digital Ecosystems and Technologies, Dubai, UAE, 13–16 April 2010; pp. 640–645.
- Wang, H. Communication-resource-aware adaptive watermarking for multimedia authentication in wireless multimedia sensor networks. J. Supercomput. 2013, 64, 883–897. [Google Scholar] [CrossRef]
- Varalakshmi, L.M.; Sudha, G.F.; Jaikishan, G. A selective encryption and energy efficient clustering scheme for video streaming in wireless sensor networks. Telecommun. Syst. 2014, 56, 357–365. [Google Scholar] [CrossRef]
- Imran, N.; Seet, B.C.; Fong, A.C.M. Distributed video coding for wireless video sensor networks: A review of the state-of-the-art architectures. SpringerPlus 2015, 4. [Google Scholar] [CrossRef] [PubMed]
- Razzaque, M.A.; Dobson, S. Energy-Efficient Sensing in Wireless Sensor Networks Using Compressed Sensing. Sensors 2014, 14, 2822–2859. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Tong, Y.; Zhao, M.; Wei, Z.; Liu, L. Compressive sensing image-fusion algorithm in wireless sensor networks based on blended basis functions. EURASIP J. Wirel. Commun. Netw. 2014, 2014. [Google Scholar] [CrossRef]
- Politis, I.; Tsagkaropoulos, M.; Dagiuklas, T.; Kotsopoulos, S. Power Efficient Video Multipath Transmission over Wireless Multimedia Sensor Networks. Mob. Netw. Appl. 2008, 13, 274–284. [Google Scholar] [CrossRef]
- Zaidi, S.M.A.; Jung, J.; Song, B.; Lee, H.; Youn, H.Y. Multi-Channel Multi-Path video transmission over wireless sensor networks. In Proceedings of the IEEE 10th Consumer Communications and Networking Conference (CCNC), Las Vegas, NV, USA, 11–14 January 2013; pp. 277–282.
- Wang, Y.; Attebury, G.; Ramamurthy, B. Index-based selective audio encryption for wireless multimedia sensor networks. IEEE Trans. Multimed. 2010, 12, 215–223. [Google Scholar] [CrossRef]
- James, S.P.; George, S.N.; Deepthi, P.P. Secure selective encryption of compressed audio. In Proceedings of the 2013 Annual International Conference on Emerging Research Areas and 2013 International Conference on Microelectronics, Communications and Renewable Energy, Kanjirapally, India, 4–6 June 2013; pp. 1–6.
- Ravelli, E.; Richard, G.; Daudet, L. Audio Signal Representations for Indexing in the Transform Domain. IEEE Trans. Audio Speech Lang. Process. 2010, 18, 434–446. [Google Scholar] [CrossRef]
- Zeng, G.; Qiu, Z. Audio watermarking in DCT: Embedding strategy and algorithm. In Proceedings of the 9th International Conference on Signal Processing, Beijing, China, 26–29 October 2008; pp. 2193–2196.
- Wang, H.; Wang, W.; Chen, M.; Yao, X. Quality-driven secure audio transmissions in wireless multimedia sensor networks. Multimed. Tools Appl. 2013, 67, 119–135. [Google Scholar] [CrossRef]
- Wu, Y.; Shimamoto, S. A Study on DWT-Based Digital Audio Watermarking for Mobile Ad Hoc Network. In Proceedings of the IEEE International Conference on Sensor Networks, Ubiquitous, and Trustworthy Computing (SUTC ’06), Taichung, Taiwan, 5–7 June 2006; Volume 2, pp. 247–251.
- Shete, R.; Agrawal, S. IoT based urban climate monitoring using Raspberry Pi. In Proceedings of the International Conference on Communication and Signal Processing (ICCSP), Madras, India, 6–8 April 2016; pp. 2008–2012.
- Wang, H.; Peng, D.; Wang, W.; Sharif, H.; Chen, H.H. Image transmissions with security enhancement based on region and path diversity in wireless sensor networks. IEEE Trans. Wirel. Commun. 2009, 8, 757–765. [Google Scholar] [CrossRef]
- Wang, W.; Hempel, M.; Peng, D.; Wang, H.; Sharif, H.; Chen, H.H. On Energy Efficient Encryption for Video Streaming in Wireless Sensor Networks. IEEE Trans. Multimed. 2010, 12, 417–426. [Google Scholar] [CrossRef]
- Tsitsipis, D.; Nikolakopoulos, G.; Tzes, A.; Koubias, S. A dual scheme for secured Multimedia Wireless Sensor Network. In Proceedings of the 19th Mediterranean Conference on Control Automation (MED), Corfu, Greece, 20–23 June 2011; pp. 1160–1165.
- Kong, J.H.; Seng, K.P.; Yeong, L.S.; Ang, L.M. Image compression with short-term visual encryption using the burrow wheeler transform and keyed transpose. In Proceedings of the IET International Conference on Wireless Communications and Applications (ICWCA), Kuala Lumpur, Malaysia, 8–10 October 2012; pp. 1–6.
- Rachedi, A.; Kaddar, L.; Mehaoua, A. EDES- Efficient dynamic selective encryption framework to secure multimedia traffic in wireless sensor networks. In Proceedings of the IEEE Communication and Information Systems Security Symposium, Ottawa, ON, Canada, 10–15 June 2012; pp. 1026–1030.
- Mahmoud, N.E.; Taha, M.H.; Mahdy, H.N.E.; Saroit, I.A. A Secure Energy Efficient Schema for Wireless Multimedia Sensor Networks. CiiT Int. J. Wirel. Commun. 2013, 5, 235–246. [Google Scholar]
- Mostefaoui, A.; Noura, H.; Fawaz, Z. Efficient and Secure Visual Data Transmission Approach for Wireless Multimedia Sensor Networks. In Proceedings of the IEEE 22nd International Symposium on Modelling, Analysis Simulation of Computer and Telecommunication Systems, Paris, France, 9–11 September 2014; pp. 463–472.
- Qi, J.; Hu, X.; Ma, Y.; Sun, Y. A Hybrid Security and Compressive Sensing-Based Sensor Data Gathering Scheme. IEEE Access 2015, 3, 718–724. [Google Scholar] [CrossRef]
- Fawaz, Z.; Mostefaoui, A.; Noura, H. Secure and Error Resilient Approach for Multimedia Data Transmission in Constrained Networks. In Proceedings of the 11th ACM Symposium on QoS and Security for Wireless and Mobile Networks (Q2SWinet ’15), Cancun, Mexico, 2–6 November 2015; pp. 149–156.
- Kim, J.M.; Lee, H.S.; Yi, J.; Park, M. Power Adaptive Data Encryption for Energy-Efficient and Secure Communication in Solar-Powered Wireless Sensor Networks. J. Sens. 2016, 2016. [Google Scholar] [CrossRef]
- Escamilla-Ambrosio, P.J.; Salinas-Rosales, M.; Aguirre-Anaya, E.; Acosta-Bermejo, R. Image compressive sensing cryptographic analysis. In Proceedings of the International Conference on Electronics, Communications and Computers (CONIELECOMP), Cholula, Mexico, 24–26 February 2016; pp. 81–86.
- De Oliveira Gonçalves, D.; Costa, D.G. Energy-efficient Adaptive Encryption for Wireless Visual Sensor Networks. In Proceedings of the Brazilian Symposium on Computer Networks and Distributed Systems, Salvador, Brazil, 30 May–3 June 2016; pp. 1–14.
- Ong, J.J.; Ang, L.M.; Seng, K.P. Selective secure error correction on SPIHT coefficients for pervasive wireless visual network. Int. J. Ad Hoc Ubiquitous Comput. 2013, 13, 73–82. [Google Scholar] [CrossRef]
- Naveenkumar, S.K.; Panduranga, H.T.; Kiran. Partial image encryption for smart camera. In Proceedings of the International Conference on Recent Trends in Information Technology, Chennai, India, 25–27 July 2013; pp. 126–132.
- Kanso, A.; Ghebleh, M. A novel image encryption algorithm based on a 3D chaotic map. Commun. Nonlinear Sci. Numer. Simul. 2012, 17, 2943–2959. [Google Scholar] [CrossRef]
- Mohammad Seyedzadeh, S.; Mirzakuchaki, S. A Fast Color Image Encryption Algorithm Based on Coupled Two-dimensional Piecewise Chaotic Map. Signal Process. 2012, 92, 1202–1215. [Google Scholar] [CrossRef]
- Zhang, X.; Zhao, Z. Chaos-based image encryption with total shuffling and bidirectional diffusion. Nonlinear Dyn. 2014, 75, 319–330. [Google Scholar] [CrossRef]
- Shin, J.; Ruland, C. A survey of image hashing technique for data authentication in WMSNs. In Proceedings of the IEEE 9th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Lyon, France, 7–9 October 2013; pp. 253–258.
- Zhou, L.; Chao, H.C. Multimedia traffic security architecture for the internet of things. IEEE Net. 2011, 25, 35–40. [Google Scholar] [CrossRef]
- Abazeed, M.; Saleem, K.; Derhab, A.; Orgun, M.A.; Fisal, N.; Al-Muhtadi, J.; Zubair, S. A Review of Secure Routing Approaches for Current and Next-Generation Wireless Multimedia Sensor Networks. Int. J. Distrib. Sens. Netw. 2015, 2015. [Google Scholar] [CrossRef]
- Gao, R.; Wen, Y.; Zhao, H.; Meng, Y. Secure Data Aggregation in Wireless Multimedia Sensor Networks Based on Similarity Matching. Int. J. Distrib. Sens. Netw. 2014, 2014. [Google Scholar] [CrossRef]
- Ozdemir, S.; Xiao, Y. Secure data aggregation in wireless sensor networks: A comprehensive overview. Comput. Netw. 2009, 53, 2022–2037. [Google Scholar] [CrossRef]
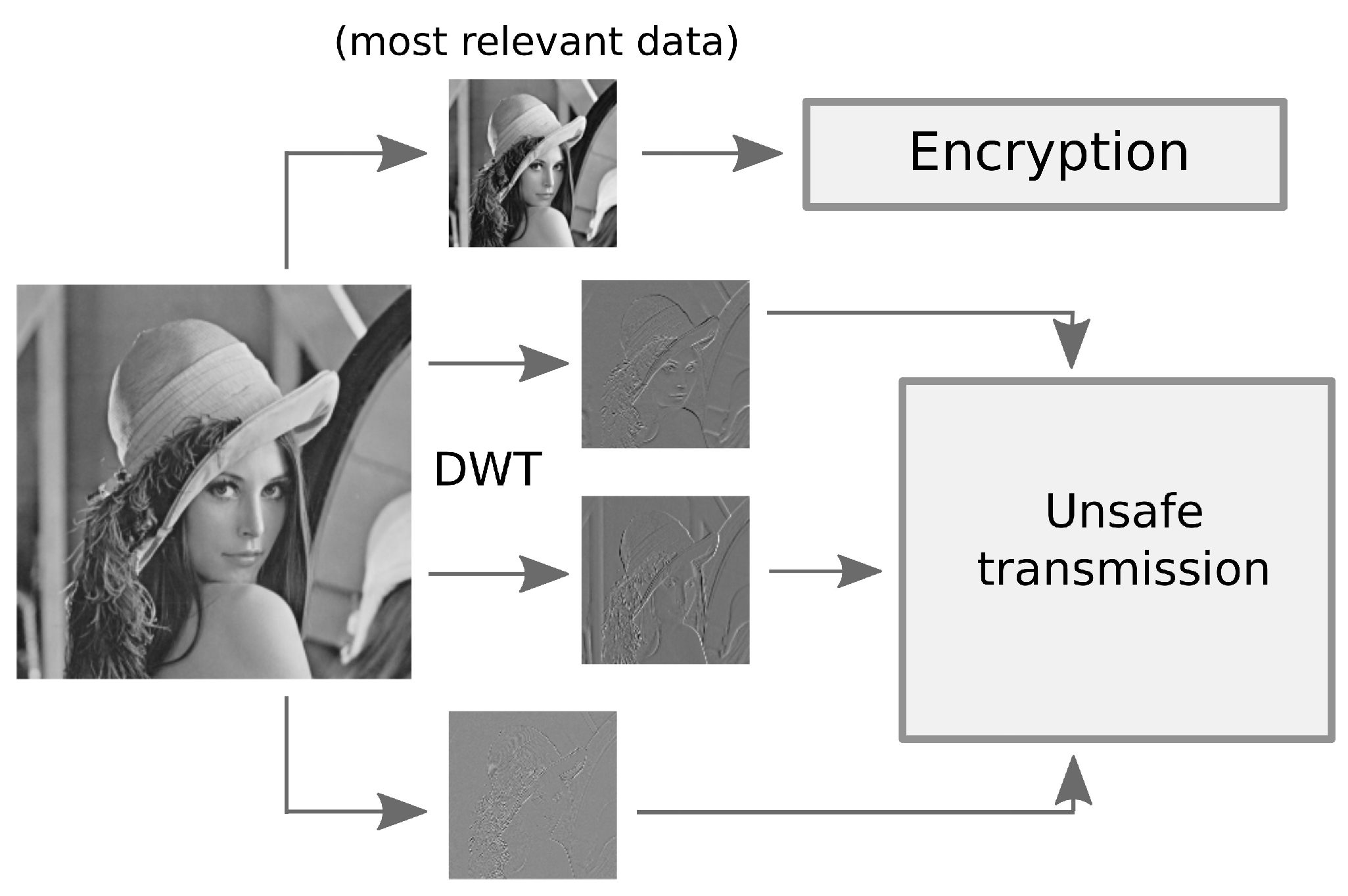
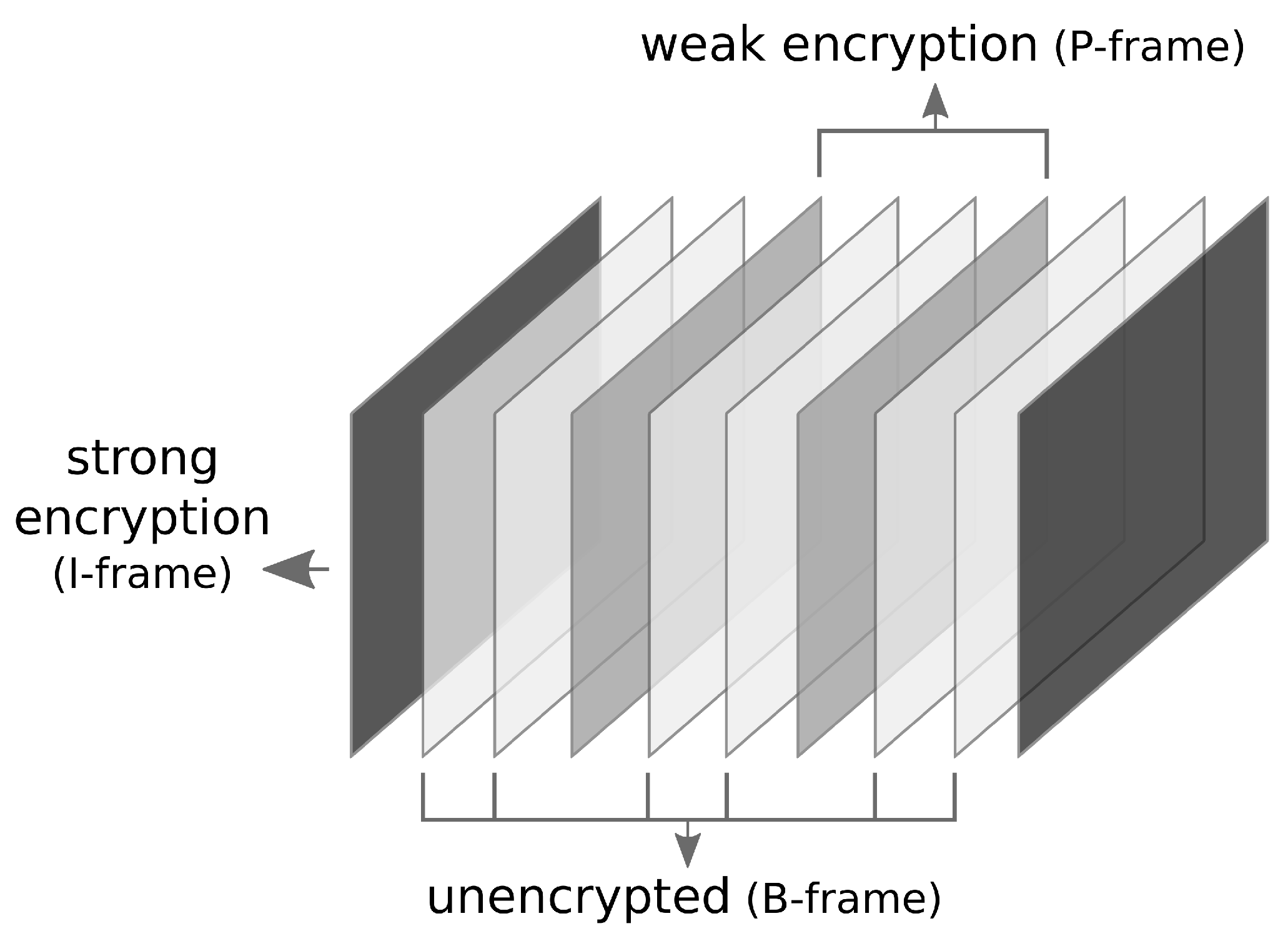
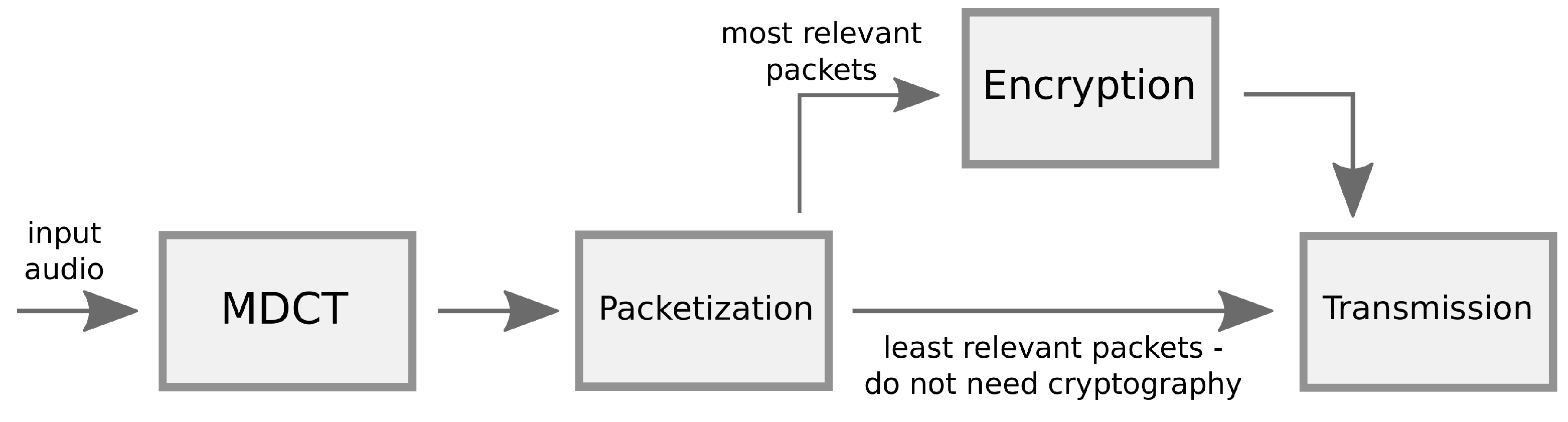
| Algorithm | Type | Description |
|---|---|---|
| AES (Advanced Encryption Standard) [31,32] | Symmetric | It is a block cipher, taking blocks of a fixed size. |
| RC4 (Rivest Cipher 4) [33] | Symmetric | It is a popular stream cipher algorithm. |
| RC5 (Rivest Cipher 5) [34] | Symmetric | It is also a block cipher algorithm, but with blocks with variable sizes. |
| RSA (Ron Shamir and Adleman) [35,36] | Asymmetric | It exploits factoring of large prime numbers. RSA may be computationally intensive. |
| ECC (Elliptic Curve Cryptography) [37,38] | Asymmetric | It is based on the elliptic curve discrete logarithm problem. ECC employs small keys compared to other algorithms. |
| Media | Size | Coding | Some Relevant Issues |
|---|---|---|---|
| image | medium | DCT(JPEG); DWT(JPG2000); SPIHT; EZW [42] | Selective encryption; watermarking |
| video | high | H.264/AVC; DVC; compressive Sensing [43,44] | Multipath routing; real-time delivery |
| audio | low/medium | PCM/ADPCM; CVSD; MDCT [45,46] | Aggregation |
| scalar | low | Raw data or compressed data | Redundancy |
| Approach | Scalar | Image | Video | Audio | Cryptography | Encryption | Selective | Compression | Year |
|---|---|---|---|---|---|---|---|---|---|
| Wang et al. [69] | - | X | - | - | - | Image correlation from multiple sensors | - | Based on correlated images | 2009 |
| Wang et al. [70] | - | - | X | - | Symmetric | AES | X | H.264 | 2010 |
| Wang et al. [62] | - | - | - | X | Symmetric | AES | X | MDCT | 2010 |
| Tsitsipis et al. [71] | - | X | - | - | Symmetric | skipjack | - | Quadtree | 2011 |
| Kong et al. [72] | - | X | - | - | Symmetric | Transposition | - | Burrows-Wheeler Transform (BWT) | 2012 |
| Rachedi et al. [73] | - | - | X | - | Symmetric | AES; Message Authentication Code | X | H.264 ; H.263 | 2012 |
| Mahmoud et al. [74] | - | - | X | - | Symmetric | AES; Message Authentication Code | - | H.264 | 2013 |
| Xiang et al. [48] | - | X | - | - | Symmetric | RC4 | X | JPEG2000 (DWT) | 2013 |
| Varalakshmi et al. [56] | - | - | X | - | Symmetric | RC5 | X | H.264 | 2014 |
| Mostefaoui et al. [75] | - | X | - | - | Symmetric | RC4 | - | Voronoi tessellation | 2014 |
| Qi et al. [76] | X | X | X | X | Symmetric | Feistel; Message Authentication Code | - | Compressive sensing | 2015 |
| Fawaz et al. [77] | - | X | - | - | Symmetric | RC4 | - | - | 2015 |
| Kim et al. [78] | X | - | - | - | Symmetric/Asymmetric | AES; Elliptic Curve Integrated Encryption Scheme (ECIES) | - | - | 2016 |
| E.-Ambrosio et al. [79] | - | X | - | - | Symmetric | CS-based | - | Compressive sensing | 2016 |
| Gonçalves and Costa [80] | - | X | - | - | Symmetric | AES | X | DWT | 2016 |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license ( http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Costa, D.G.; Figuerêdo, S.; Oliveira, G. Cryptography in Wireless Multimedia Sensor Networks: A Survey and Research Directions. Cryptography 2017, 1, 4. https://doi.org/10.3390/cryptography1010004
Costa DG, Figuerêdo S, Oliveira G. Cryptography in Wireless Multimedia Sensor Networks: A Survey and Research Directions. Cryptography. 2017; 1(1):4. https://doi.org/10.3390/cryptography1010004
Chicago/Turabian StyleCosta, Daniel G., Solenir Figuerêdo, and Gledson Oliveira. 2017. "Cryptography in Wireless Multimedia Sensor Networks: A Survey and Research Directions" Cryptography 1, no. 1: 4. https://doi.org/10.3390/cryptography1010004







