Performance Analysis of Secure and Private Billing Protocols for Smart Metering
Abstract
:1. Introduction
1.1. Motivation
1.2. Related Work
1.3. Pedersen Commitments Background
- q is a 256-bit random prime;
- p is a large (2048–4094 bit) prime of the form such that generates a subgroup of p;
- g and h are random members of the subgroup of of order ;
- x is the data to be committed to (an integer modulo ); and
- r is the random salt (an integer modulo p). Note: r is usually picked from the set of integers modulo q so that computation can remain within this subgroup; however, during the protocol, values for r become too large for this and so the more expensive computations across the whole of the group generated by p are allowed.
2. Smart Meter Billing
2.1. Security Specification
2.1.1. Adversaries
- Malicious customer
- Attempts to modify the smart meter to produce incorrect readings.
- Attempts to modify outputted bills before they are transmitted to the utility provider.
- Attempts to prevent transmission of bills to the utility provider.
- Attempts to change the prices input to the smart meter.
- Malicious utility provider
- Attempts to de-aggregate fine-grained utility readings.
- Malicious third-party
- Attempts to snoop the bill total off the wire (using passive or active attacks).
- Attempts to change the pricing information used by the customer.
- Attempts to de-aggregate fine-grained utility readings.
- A malicious utility provider disclosing the bill total to the malicious third party.
- Hardware and firmware malware embedded in the smart meter either during manufacture or firmware updates: causing the smart meter to act maliciously.
- Attempts by the utility provider to over-charge customers (this is only unmet in the simple protocol. In the three-party protocol, the user gets a signed copy of the smart meter readings and so these could be used as evidence against the utility provider so long as the smart meter does not collude alongside the utility provider).
2.1.2. Required Security Properties
- R1: Do not allow the utility provider (or any third party) to learn utility consumption measurements with any more temporal granularity than they learn in the traditional utility billing system (threats 2a and 3c).
- R2: Do not leak the bill amount to any third party (threat 3a).
- R3: Utility providers must be able to verify that they receive the correct bill amount (threats 1a–c).
- R4: Only the utility provider can change prices (threats 1d and 2b).
2.1.3. Assumptions
- A1: The smart meter is tamper resistant and is trusted by all parties.
- A2: The utility provider trusts its own servers to operate correctly.
- A3: Unless otherwise specified, all communications in these protocols are to be performed over a reliable, confidential, and authenticated channel.
- A4: (Specific to the three-party protocol). The customer trusts the “customer” device.
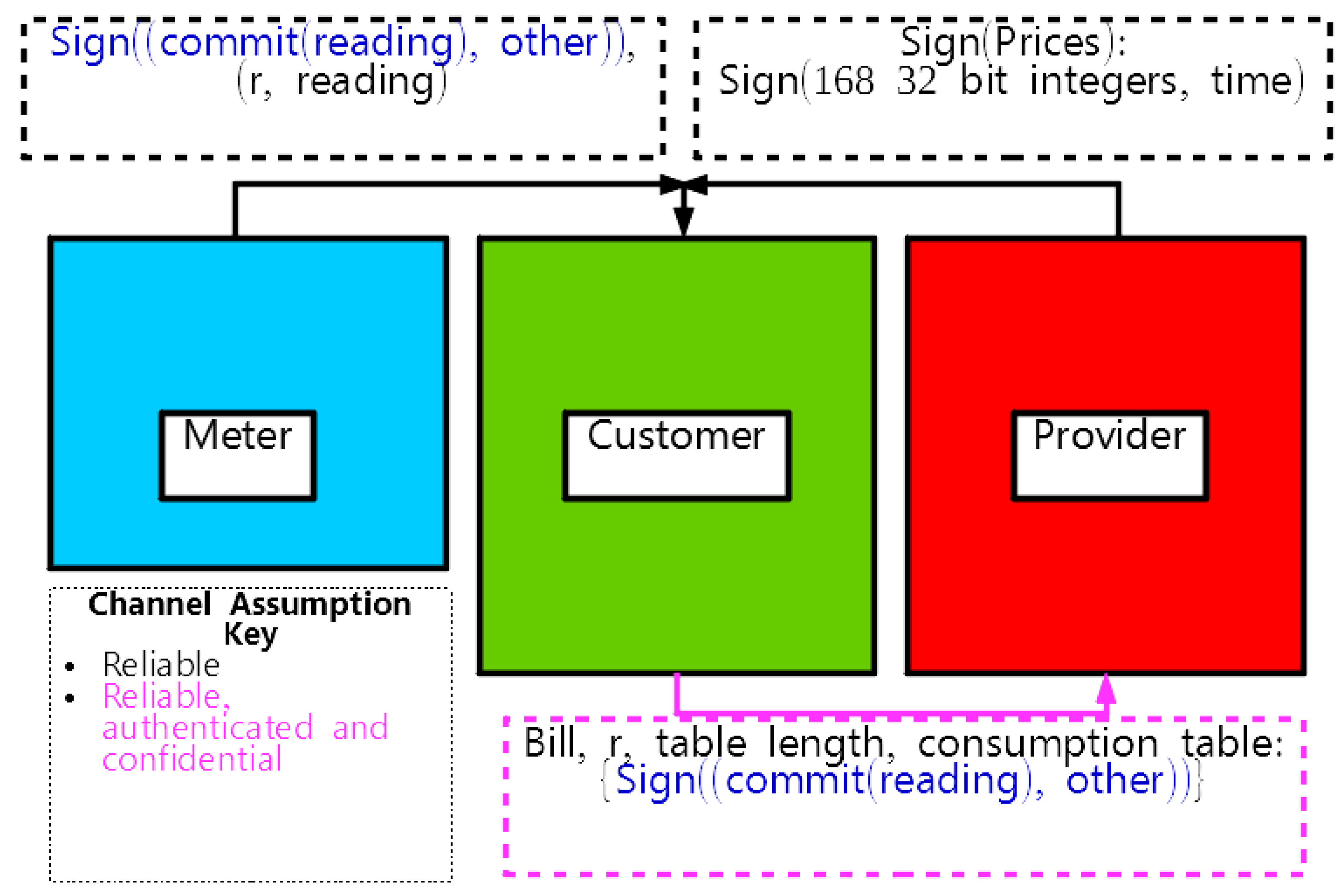
2.2. Simple Protocol
2.3. Three-Party Protocol
3. Security Analysis
- The output of A is trusted by B and so collusion between A and M is beyond the scope of this game. Therefore, signatures made by A are trusted by B.
- M cannot replay old legitimate messages because the unique timestamp would no longer match what was expected by B.
- M cannot forge messages with either the data or timestamp modified because these are both covered by the signature, and forging a signature under an ideal public key signature algorithm is computationally infeasible.
- If M prevents the transmission of the data, this absence will be noticed by B because it knows to expect the message.
3.1. R1: Reading Privacy
3.1.1. Simple Billing Protocol
3.1.2. Three-Party Billing Protocol
- Applying Lemma 2, the aggregate bill is not an issue.
- The salt for the aggregate bill is the sum of all the salts on the individual commitments weighted by the prices. Therefore, by Lemma 2, this aggregate salt reveals no more information about the salts for individual commitments than the bill reveals about the individual readings.
- Pedersen commitments are information theoretically concealing [19], and so the series of commitments do not reveal information about the readings they commit to.□
3.2. R2: Security from Eavesdroppers
3.3. R3: Bill Correctness
3.3.1. Simple Billing Protocol
3.3.2. Three-Party Billing Protocol
- The signed commitment and timestamp pairs from the smart meter are trusted by the utility provider (Lemma 3 applied to the signed bill and timestamp pair transmitted from the smart meter (party A) to the utility provider (party B), with M as a malicious user and using the utility provider’s expectation that it will receive a bill for a billing period to detect a failed message transmission. This assignment is valid because the utility provider trusts the smart meter (A1) and its own computation (A2)).
- These commitments can be combined using the homomorphic operations as follows to obtain a commitment to the bill:
- If a commitment on the aggregate bill sent by the user is computed using the salt sent by the user, and it matches the signature generated from the trusted commitments, then the aggregate bill sent by the user must have been calculated honestly because Pedersen commitments are computationally binding [19].□
3.4. R4: Price Changes
3.4.1. Simple Billing Protocol
- After sending pricing information, the utility provider will expect a price acknowledgement response. Therefore, the utility provider can detect if the prices never made it to the smart meter.
- The price updates are signed by the utility provider. Apply Lemma 3 with A as the utility provider, B as the smart meter, a failed transmission detected as in the previous step, and a trust relationship between A and B supplied by A1. Using this lemma, the pricing information cannot be forged by a third party.□
3.4.2. Three-Party Billing Protocol
- If the user chooses to calculate the bill from its own fabricated prices, then either the bill will be different or the fabrication will be irrelevant and pointless.
- If the calculated bill is not computed correctly according to the prices on the utility provider’s server, then this can be detected when the bill is verified (Theorem 1).
- The price updates are signed by the utility provider. Apply Lemma 3 with A as the utility provider, B as the user device, a failed transmission detected as in the previous step, and a trust relationship between A and B supplied by A1. Using this lemma, the pricing information cannot be forged by a third party.□
4. Implementation and Evaluation
4.1. Existing Implementation
- Implementations of the smart meter billing protocols may be found at https://github.com/tblah/project-billing.
- The Secure Channel protocol may be found at https://github.com/tblah/project-net.
- Some cryptographic primitives used in these protocols are implemented at https://github.com/tblah/project-crypto, but most used the widely reviewed implementations in Libsodium through the SodiumOxide language bindings [21]. The integer exponentiation implementation in the GNU Multiple Precision Arithmetic Library GMP was used to implement the commitment scheme.
4.2. Performance Analysis
4.3. Barriers to Integration in A Real Product
5. Conclusions and Future Work
5.1. Conclusions
5.2. Future Work
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Cisco. The Internet of Things: It’s Not about Things, It’s about Service. Available online: https: //www.jasper.com/infographics/internet-things-its-not-about-things-its-about-service (accessed on 28 April 2017).
- Jawurek, M.; Kerschbaum, F.; Danezis, G. Privacy Technologies for Smart Grids—A Survey of Options. November 2012. Available online: https://www.microsoft.com/en-us/research/publication/privacy-technologies-for-smart-grids-a-survey-of-options/ (accessed on 28 April 2017).
- Jawurek, M.; Johns, M.; Kerschbaum, F. Plug-in privacy for smart metering billing. In Proceedings of the 11th International Symposium on Privacy Enhancing Technologies (PETS 2011), Waterloo, ON, Canada, 27–29 July 2011; Fischer-Hübner, S., Hopper, N., Eds.; Springer: Berlin/Heidelberg, Germany, 2011; pp. 192–210. [Google Scholar]
- Enev, M.; Gupta, S.; Kohno, T.; Patel, S.N. Televisions, video privacy, and powerline electromagnetic interference. In Proceedings of the 18th ACM Conference on Computer and Communications Security (CCS’11), Chicago, IL, USA, 17–21 October 2011; ACM: New York, NY, USA, 2011; pp. 537–550. [Google Scholar]
- Privacy Assessments. 2017. Available online: https://www.smartenergycodecompany.co.uk/sec/privacy-assessments (accessed on 28 April 2017).
- Rial, A.; Danezis, G.; Kohlweiss, M. Differentially Private Billing with Rebates. February 2011. Available online: https://www.microsoft.com/en-us/research/publication/differentially-private-billing-with-rebates/ (accessed on 28 April 2017).
- Backes, M.; Meiser, S. Differentially private smart metering with battery recharging. In Data Privacy Management and Autonomous Spontaneous Security; Springer Science + Business Media: New York, NY, USA, 2014; pp. 194–212. Available online: https://eprint.iacr.org/2012/183.pdf (accessed on 28 April 2017).
- Kalogridis, G.; Efthymous, C.; Denic, S.; Lewis, T.; Cepeda, R. Privacy for smart meters: Towards undetectable appliance load signatures. In Proceedings of the Smart Grid Communications, Gaithersburg, MD, USA, 4–6 October 2010; pp. 232–237. [Google Scholar]
- McLaughlin, S.; McDaniel, P.; Aiello, W. Protecting consumer privacy from electric load monitoring. In Proceedings of the 18th ACM Conference on Computer and Communications Security, Chicago, IL, USA, 17–21 October 2011. [Google Scholar]
- Yang, W.; Li, N.; Qi, Y.; Qardaji, W.; McLaughlin, S.; McDaniel, P. Minimizing private data disclosures in the smart grid. In Proceedings of the 2012 ACM Conference on Computer and Communications Security, Raleigh, NC, USA, 16–18 October 2012; ACM: New York, NY, USA, 2012. [Google Scholar]
- Rial, A.; Danezis, G. Privacy-Preserving Smart Metering. November 2010. Available online: https://www.microsoft.com/en-us/research/publication/privacy-preserving-smart-metering/ (accessed on 28 April 2017).
- Efthymiou, C.; Kalogridis, G. Smart grid privacy via anonymization of smart metering data. In Proceedings of the IEEE Smart Grid Communications, Gaithersburg, MD, USA, 4–6 October 2010; pp. 238–243. [Google Scholar]
- Jo, H.J.; Kim, I.S.; Lee, D.H. Efficient and privacy-preserving metering protocols for smart grid system. IEEE Trans. Smart Grid 2016, 7, 1732–1742. [Google Scholar] [CrossRef]
- Gong, Y.; Cai, Y.; Guo, Y.; Fang, Y. A privacy-preserving scheme for incentive-based demand response in the smart grid. IEEE Trans. Smart Grid 2016, 7, 1304–1313. [Google Scholar] [CrossRef]
- Kursawe, K.; Danezis, G.; Kohlweiss, M. Privacy-Friendly Aggregation for the Smart-Grid. In Proceedings of the 11th International Conference on Privacy Enhancing Technologies (PETS’11), Waterloo, ON, Canada, 27–29 July 2011. [Google Scholar]
- LeMay, M.; Gross, G.; Gunter, C.A.; Garg, S. Unified architecture for large-scale attested metering. In Proceedings of the 40th Hawaii International Conference on Systems Science (HICSS 2007), Waikoloa, HI, USA, 3–6 January 2007; pp. 115–124. [Google Scholar]
- Zhao, J.; Liu, J.; Qin, Z.; Ren, K. Privacy Protection Scheme Based on Remote Anonymous Attestation for Trusted Smart Meters. IEEE Trans. Smart Grid. 2016. [Google Scholar] [CrossRef]
- Hirt, M.; Sako, K. Efficient Receipt-Free Voting Based on Homomorphic Encryption. In Advances in Cryptology—EUROCRYPT 2000; Preneel, B., Ed.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2000; Volume 1807. [Google Scholar]
- Smart, N. Cryptography: An Introduction; McGraw-Hill: New York, NY, USA, 2003; pp. 363–367. ISBN 0077099877. [Google Scholar]
- Pedersen, T.P. Non-interactive and information-theoretic secure verifiable secret sharing. In Advances in Cryptology—CRYPTO ’91; Springer: Berlin/Heidelberg, Germany, 1991; pp. 129–140. [Google Scholar]
- Dnaq. Sodium Oxide: Fast Crypto-Graphic Library for Rust (Bindings to Libsodium). Available online: https://github.com/dnaq/sodiumoxide (accessed on 28 April 2017).
- Rust. The Rust Programming Language. Available online: https://www.rust-lang.org/en-us/ (accessed on 1 September 2017).
- Kerrisk, M. The Linux Programming Interface; No Starch Press: San Francisco, CA, USA, 2010; ISBN 78-1-59327-220-3. [Google Scholar]
- Molina-Markham, A.; Danezis, G.; Fu, K.; Shenoy, P.; Irwin, D. Designing Rivacy-Preserving Smart Meters with Ow-Cost Microcontrollers; Springer: Berlin, Germany, 2011. [Google Scholar]
| Operation | Platform | Average Time Taken (ms) |
|---|---|---|
| Commitment | Raspberry Pi B+ (700 MHz BCM2835) | 71,000 ± 1000 |
| Commitment | Novena (1.2 GHz Freescale iMX6) | 25,790 ± 30 |
| Commitment | Desktop Computer (Intel i5-3570k) | 1140 ± 70 |
| Ed25519 Signature | Raspberry Pi B+ (700 MHz BCM2835) | 2.2 ± 0.3 |
| Ed25519 Signature | Novena (1.2 GHz Freescale iMX6) | 0.67 ± 0.07 |
| Ed25519 Signature | Desktop Computer (Intel i5-3570k) | 0.05 ± 0.04 |
| Protocol | Operation | Type | Worst-Case Size in Implementation (Bytes) | Theoretical Minimum Size (Bytes) |
|---|---|---|---|---|
| Three-Party | Meter Reading | Local | 2490 | 1048 |
| Three-Party | Change Prices (168 32-bit prices) | Receive from remote | 808 | 688 |
| Three-Party | Send Bill (168 measurements) | Send to remote | 211,923 | 89,232 |
| Simple | Change Prices (168 32-bit prices) | Receive from remote | 808 | 688 |
| Simple | Send Bill | Send to remote | 16 | 16 |
| Protocol | Operation | Required Operations |
|---|---|---|
| Three-Party | All Meter Readings in a cycle. | Smart Meter:
|
| Customer: N Ed25519 signature verifications. | ||
| Three-Party | Change Prices | Utility Provider: 1 Ed25519 signature. |
| Customer: 1 Ed25519 signature verification. | ||
| Three-Party | Send Bill | Utility Provider:
|
| Simple | Change Prices | Utility Provider: 1 Ed25519 signature. |
| Smart Meter: 1 Ed25519 signature verification. | ||
| Simple | Send Bill | Smart Meter: 1 Ed25519 signature. |
| Utility Provider: 1 Ed25519 signature verification. |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Eccles, T.; Halak, B. Performance Analysis of Secure and Private Billing Protocols for Smart Metering. Cryptography 2017, 1, 20. https://doi.org/10.3390/cryptography1030020
Eccles T, Halak B. Performance Analysis of Secure and Private Billing Protocols for Smart Metering. Cryptography. 2017; 1(3):20. https://doi.org/10.3390/cryptography1030020
Chicago/Turabian StyleEccles, Tom, and Basel Halak. 2017. "Performance Analysis of Secure and Private Billing Protocols for Smart Metering" Cryptography 1, no. 3: 20. https://doi.org/10.3390/cryptography1030020





