Efficient Secure Mechanisms for In-Vehicle Ethernet in Autonomous Vehicles
Abstract
:1. Introduction
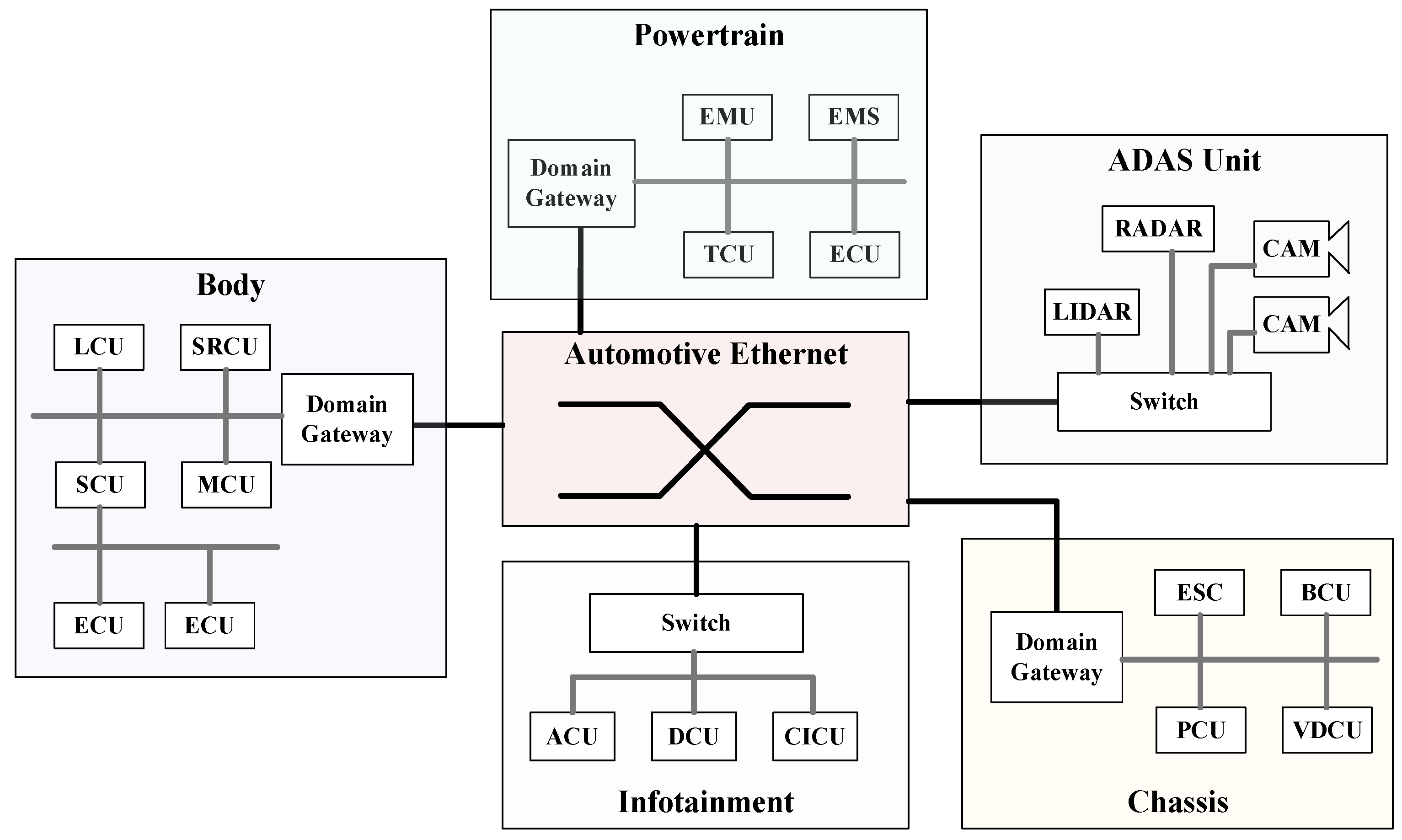
- Advanced Driver Assistance System (ADAS) Unit: This unit is equipped with an array of sensors, including a radar, a LiDAR, and cameras, along with advanced algorithms. It provides essential autonomous driving features such as collision avoidance, lane assistance, and adaptive cruise control.
- Body Control Unit (BCU): Manages vehicle body electronics, such as window controls and door locks, enhancing comfort and convenience. It includes various ECUs such as the Local Control Unit (LCU), System Control Unit (SCU), Sensor Region Control Unit (SRCU), and Microcontroller Unit (MCU).
- Powertrain Control Unit (PCU): Oversees the vehicle’s power output and transmission efficiency, which is crucial for performance and fuel economy. This unit integrates components like the Domain Gateway, Engine Management System (EMS), and Transmission Control Unit (TCU).
- Chassis Control Unit: This unit manages vehicle stability and control, including the Electronic Stability Control (ESC) Unit and Power Control Unit (PCU), which are vital for maintaining vehicle dynamics and energy management.
- Infotainment System: This system provides entertainment and connectivity features within the vehicle. It includes components like multimedia interfaces, navigation systems, and communication modules that enhance the in-car experience for passengers and drivers.
- AES-ECC Hybrid Algorithm: We develop a novel AES-ECC hybrid algorithm for critical vehicle control signals in Ethernet networks, balancing AES efficiency with ECC security.
- Improved AES-128 (IAES-128): We propose IAES-128, optimizing AES-128 for multimedia entertainment data with a 15% faster encryption time.
- Improved MD5 Authentication (IMD): We improve MD5 authentication (IMD) by 50% in computation time, ensuring efficient data integrity verification.
- Comprehensive Security Mechanism: These algorithms are integrated into a robust security framework, rigorously tested via CANoe attack simulations to protect both critical and non-critical vehicle systems.
- Validation Through Simulations: Validated through realistic cyberattack simulations, ensuring reliability in safeguarding autonomous vehicles from potential threats.
2. Background and Related Work
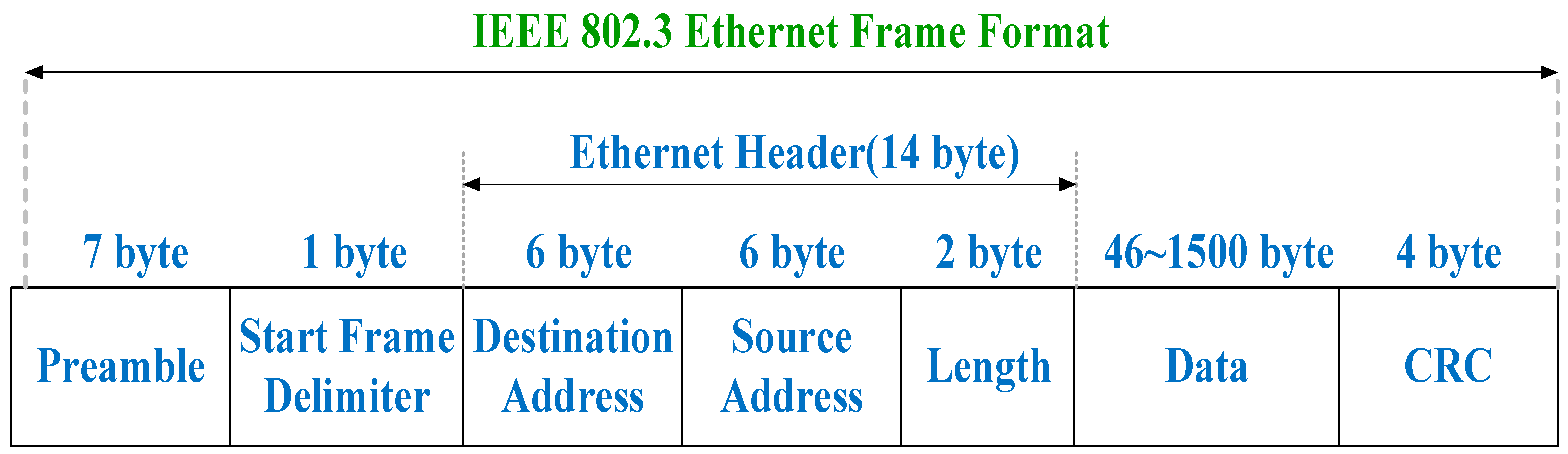
2.1. Introduction to Automotive Ethernet
2.2. Cybersecurity Hazards of In-Vehicle Ethernet
2.2.1. Intrusion Detection Solutions
- Woo et al. conducted an experiment to remotely and wirelessly attack a vehicle using a malicious smartphone and devised a security protocol for this purpose. The protocol adheres to the CAN bus specification and has been experimentally validated for feasibility, demonstrating improvements in communication load and authentication delay compared to existing protocols [15].
- Song H.M. et al. introduced a lightweight intrusion detection algorithm based on CAN message interval analysis, capable of detecting all attack messages without triggering false alarms [16].
- Boosun Jeon et al. analyzed traffic characteristics of vehicular Ethernet networks and developed a lightweight anomaly detection system, employing machine learning techniques to identify anomalous traffic in vehicular environments, ensuring real-time performance and bolstering vehicle security [17].
- Yousik Lee et al. scrutinized 13 instances of automotive hacking based on cyber kill chains, introducing an analysis methodology grounded in cyber kill chain attacks. They devised a vulnerability analysis system and recommended corresponding defensive measures [18].
- Ali Altalbe developed FFS-IDS, an advanced IDS for in-vehicle networks. It combined feature fusion with stacking ensemble learning to improve detection accuracy. FFS-IDS outperformed existing methods in identifying various attacks, achieving up to 99% accuracy for certain threats [19].
- Yinbin Miao developed an IDS for autonomous vehicles using K-nearest neighbors and ensemble learning. The system achieved up to 99% accuracy and improved F1-scores on real-world datasets, enhancing vehicle safety and cybersecurity [20].
2.2.2. Cryptographic Solutions
- Herrewege et al.’s Broadcast Authentication Protocol: Herrewege et al. proposed a backward-compatible broadcast authentication protocol for the CAN bus. This protocol is designed to be fully applicable without modifications to existing nodes [21].
- Mundhenk et al.’s LASAN Protocol: Mundhenk et al. introduced the Lightweight Authentication Protocol LASAN, which is suitable for in-vehicle networks. LASAN provides notable security and real-time advantages without requiring additional hardware support [22].
- Zhao et al.’s Keychain Authentication Mechanism: Zhao et al. proposed a unidirectional keychain delayed-exposure-based authentication mechanism for TTEthernet. This mechanism enhances message authenticity and reduces authentication delay while addressing system scheduling challenges through mixed-integer linear programming [23].
- Marco Iorio et al.’s Security Framework: Marco Iorio et al. developed a novel mechanism for securing applications in vehicles. This framework is integrated with Ethernet communication and the Service-Oriented Middleware-over-IP (SOME/IP) to bolster communication security [24].
- Wang et al.’s Hardware Security Module (SECU): Wang et al. proposed the SECU Hardware Security Module for key distribution and secure authentication. It also protects the ECU against attack messages before they are received [25].
- Shiyi Jin et al.’s Signal-Packing Method: Shiyi Jin et al. proposed a signal-packing method using the Next Decrease of Fit (NFD) algorithm, which facilitates swift message scheduling and minimizes Frame ID (FID) usage to control message load size and enhance transmission efficiency for FlexRay static segmented messages [26].
- Yinbin Miao et al. introduced PSRQ, a cryptographic scheme that combines Geohash with Coalesce Bloom Filter (CSC-BF) and Symmetric-key Hidden Vector Encryption (SHVE), to enhance privacy and query efficiency. PSRQ+ further improves security and range support, achieving 100× better efficiency compared to prior methods [27].
- Insufficient encryption mechanisms that do not provide adequate protection against sophisticated cyberattacks.
- A lack of robust authentication protocols that can verify the integrity and authenticity of messages in real-time [28].
- Inadequate consideration for the unique challenges posed by the automotive environment, such as the need for low latency and high reliability in safety-critical systems [29].
3. Automotive Ethernet Security Protocol
3.1. The Overall Network Security Scheme for In-Vehicle Ethernet
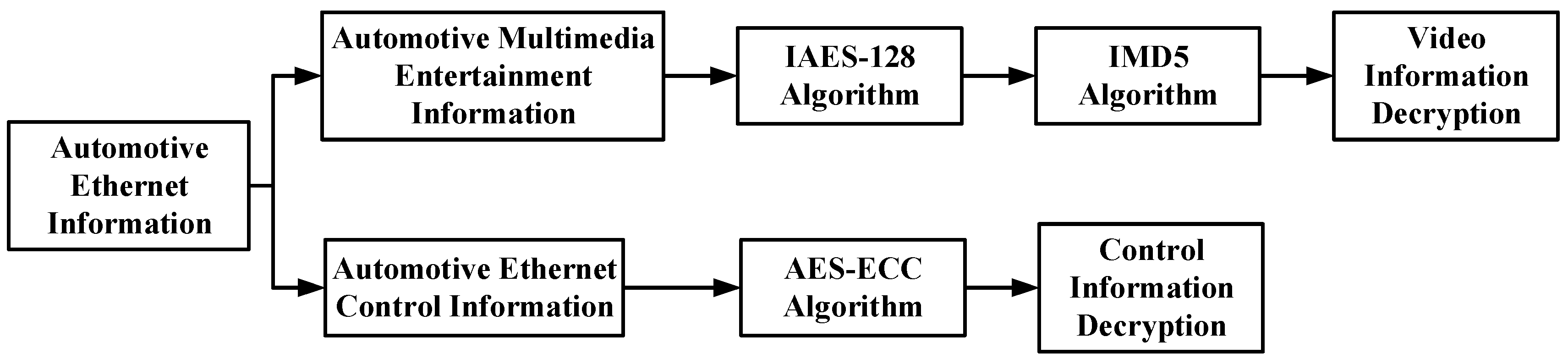
- In-vehicle multimedia signals:
- Functionality: In-vehicle infotainment signals, comprising audio, video, navigation, and diagnostics, are often perceived as non-safety-critical. However, their stable transmission is crucial for passenger comfort and indirectly reflects the reliability of the vehicle, thus influencing the passengers’ safety perception.
- Security Challenges: As evidenced by the 2015 Jeep hack, a breach in the multimedia system can serve as a gateway to manipulate critical vehicle controls. Therefore, safeguarding both multimedia and vehicle control networks is paramount.
- Attack Types: These include data theft (e.g., hackers attempting to illegally copy entertainment system data or analyze user behavior) and denial-of-service attacks (blocking multimedia signal transmission through sending numerous invalid requests) [33].
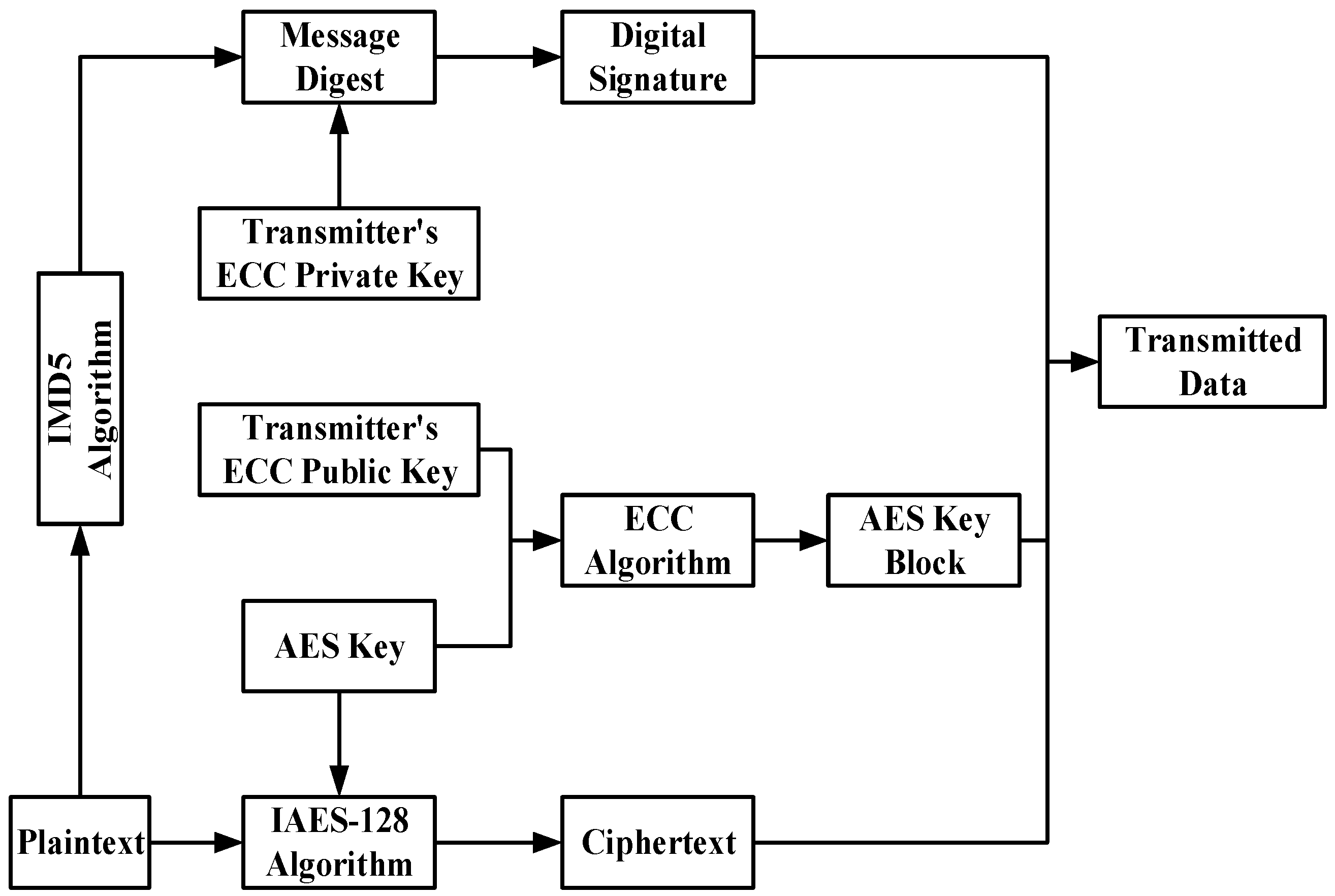
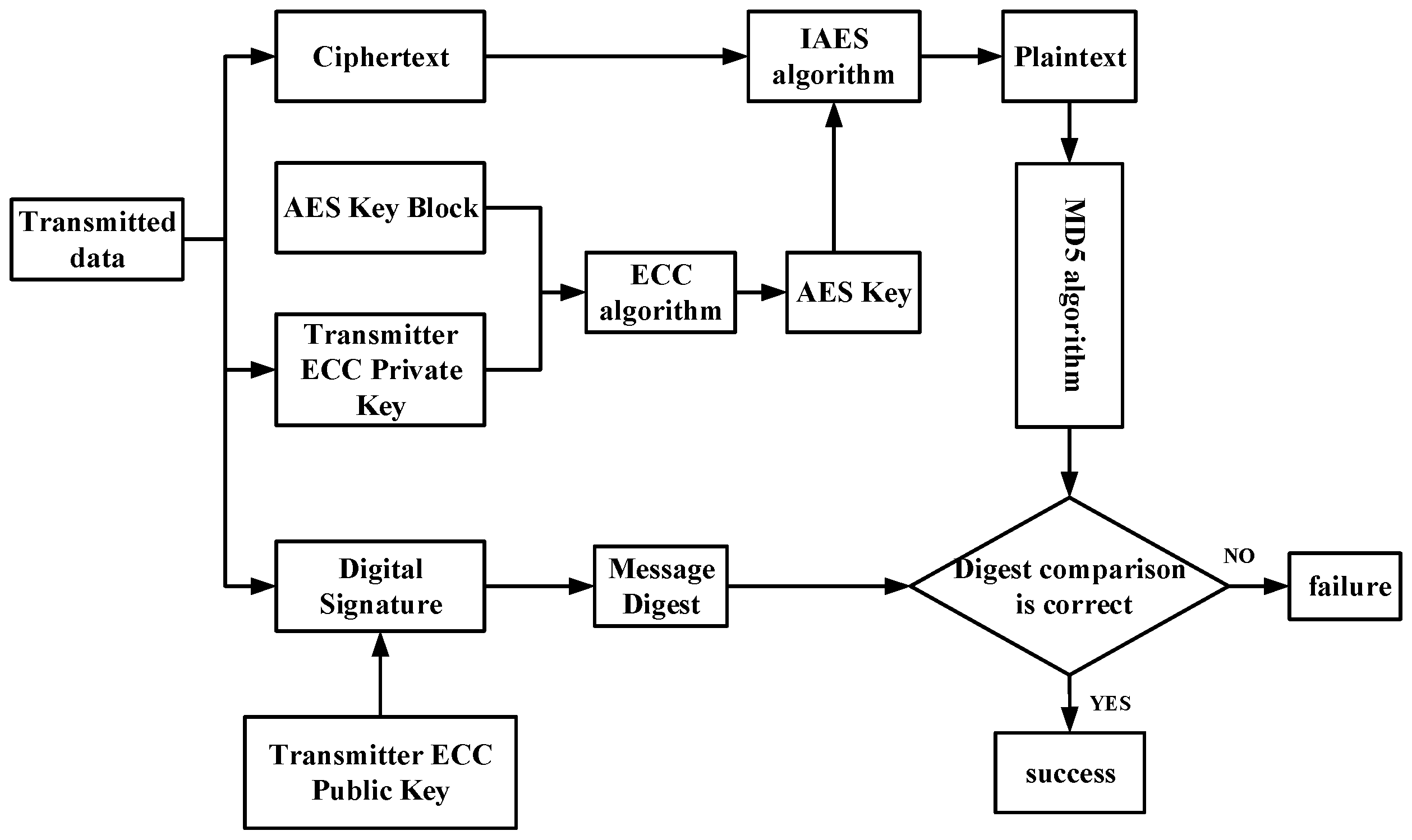
- Security Measures: To address these threats, this paper employs a combination of an improved IAES-128 algorithm and an IMD5 algorithm for encryption and authentication of in-vehicle multimedia signals. IAES-128 optimizes encryption speed for multimedia data, while IMD5 improves data integrity verification efficiency.
- In-vehicle control signals:
- Functionality: Encompassing steering, braking, power, and lighting signals, these control signals are pivotal in determining the fundamental functionality and safety of the vehicle.
- Transmission Requirements: During vehicle operation, it is imperative for control signals to be transmitted swiftly and accurately to ensure the stability and safety of the vehicle.
- Security Measures: To mitigate these threats, this paper adopts a hybrid AES-ECC encryption mechanism with a higher security level to encrypt the control signals. This hybrid algorithm combines the efficiency of AES with the security of ECC, providing a high level of protection for critical vehicle control signals.
3.2. Design of Data Encryption and Authentication Algorithms for In-Vehicle Multimedia Signals
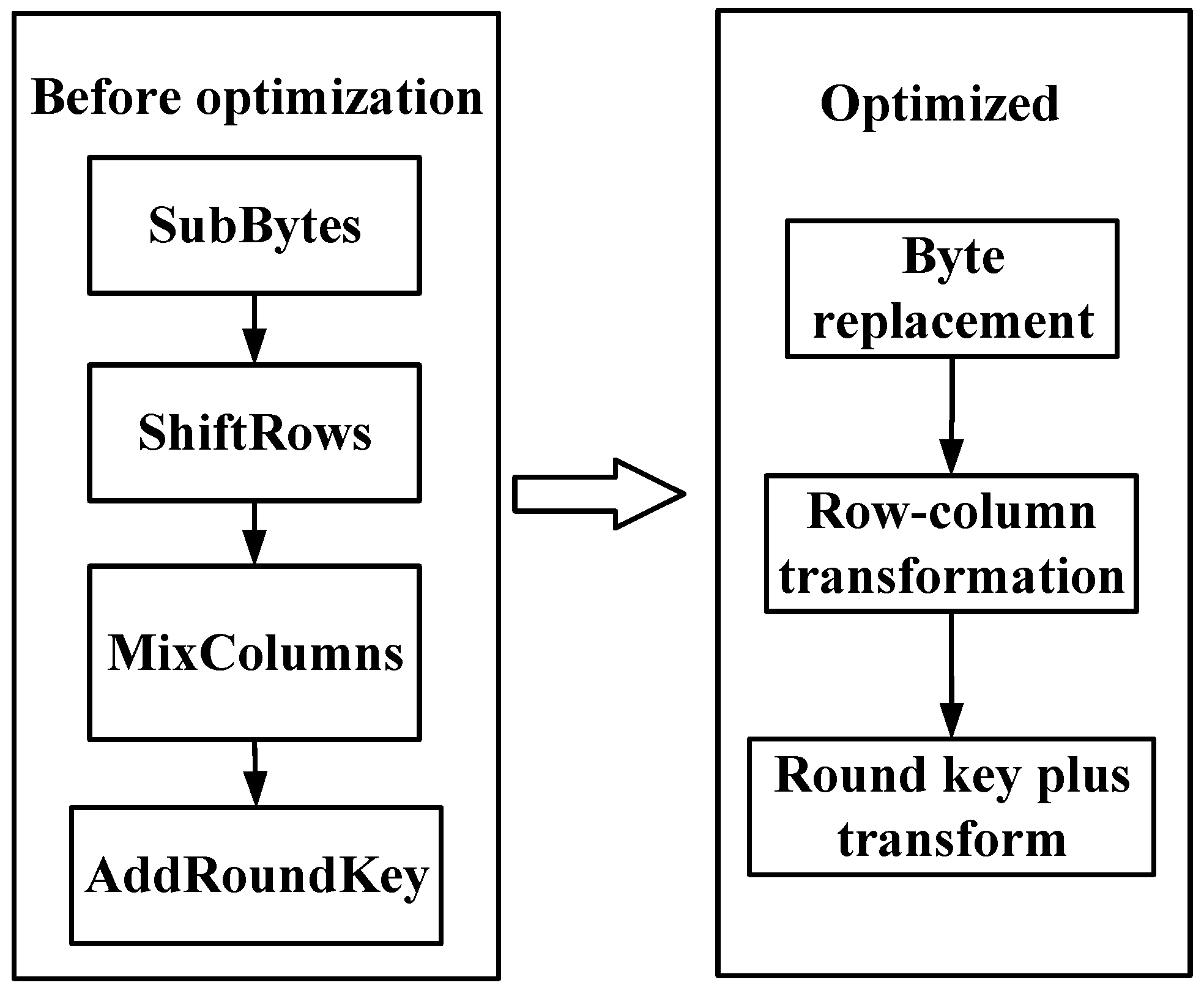
3.2.1. Improved AES-128 Encryption Algorithm Design (IAES-128)
3.2.2. Improved MD5 Data Authentication Algorithm Design (IMD5)
3.2.3. Design of Efficient Data Encryption Algorithm for In-Vehicle Control Signals
4. Simulation Experiment and Result Analysis
4.1. Simulation of Network Traffic and Attacks
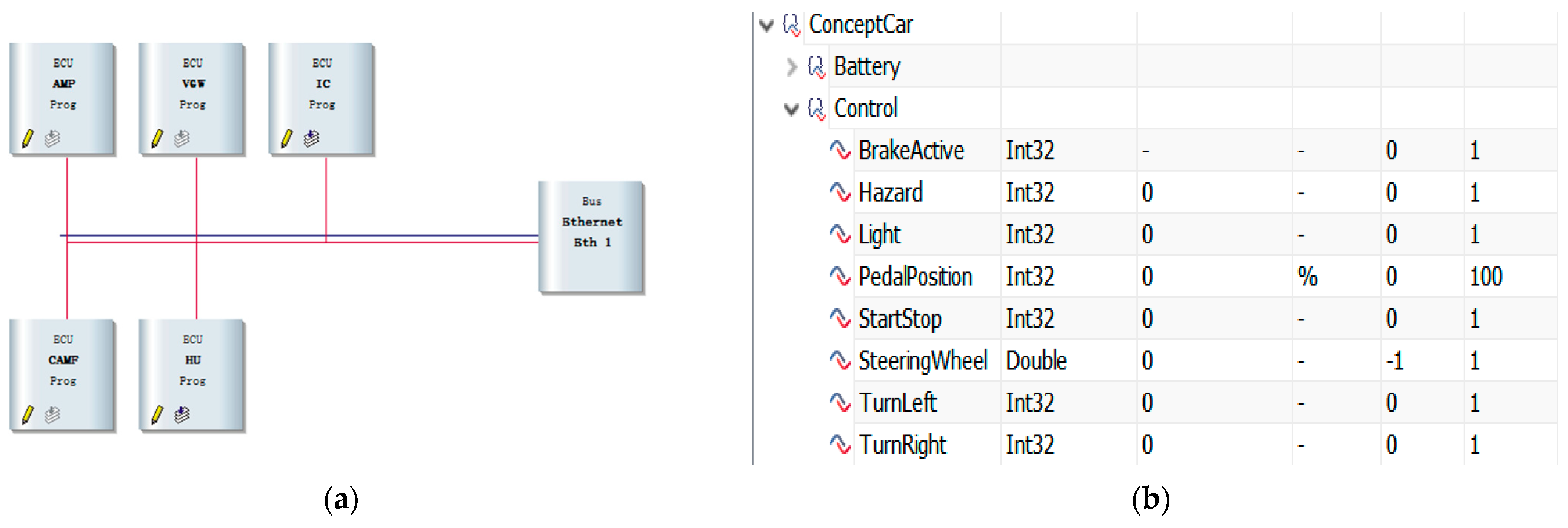
4.1.1. Generation of Normal Network Traffic
- (A)
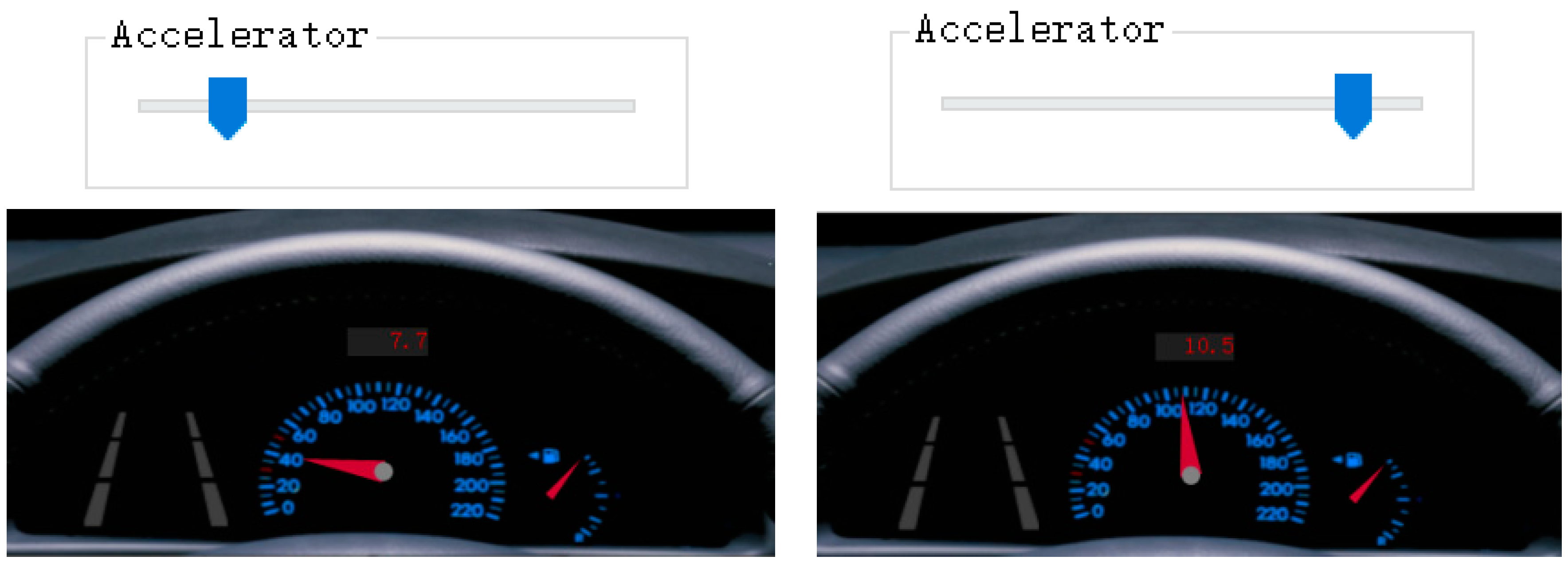
- Acceleration control: Figure 8 shows the analog acceleration control simulation results, where the vehicle’s speed is regulated by the gas pedal and an acceleration control lever. The simulation illustrates that increased pressure on the gas pedal proportionally boosts acceleration, as indicated by a real-time speed dial on the dashboard. Additionally, moving the acceleration control lever to the left decreases speed, while moving it to the right increases speed. This setup provides precise control over the vehicle’s acceleration, emulating real-world driving conditions and offering a comprehensive understanding of the vehicle’s response to inputs.
- (B)
- Deceleration control: Figure 9 illustrates the results of the deceleration control simulation. As the car reaches a certain speed, pressing the brake pedal triggers a braking signal, resulting in a reduction in speed. The simulation showcases a direct correlation between the force applied to the brake pedal and the vehicle’s deceleration rate. On the virtual dashboard of the simulated car, the speed value on the odometer decreases accordingly, accurately reflecting the actual speed change in real-time. This setup offers a realistic portrayal of braking dynamics, providing users with immediate feedback on how the vehicle responds to braking inputs. Furthermore, the simulation captures the progressive decrease in speed as more pressure is applied to the brake pedal, mimicking real-world deceleration behavior and enhancing the user’s understanding of the vehicle’s braking performance.
- (C)
- Lamp control: Figure 10 depicts the results of the headlight control simulation, showcasing various functions such as running light signals, turn-signal signals, hazard light signals, and brake light signals, among others. These functionalities are implemented by integrating lights on the simulated car. When the corresponding control buttons are pressed, the respective lights illuminate, thereby achieving visual control of the lights. It ensures that when control buttons are engaged, the corresponding lights illuminate accurately, providing essential visual cues for driving scenarios.
- (D)
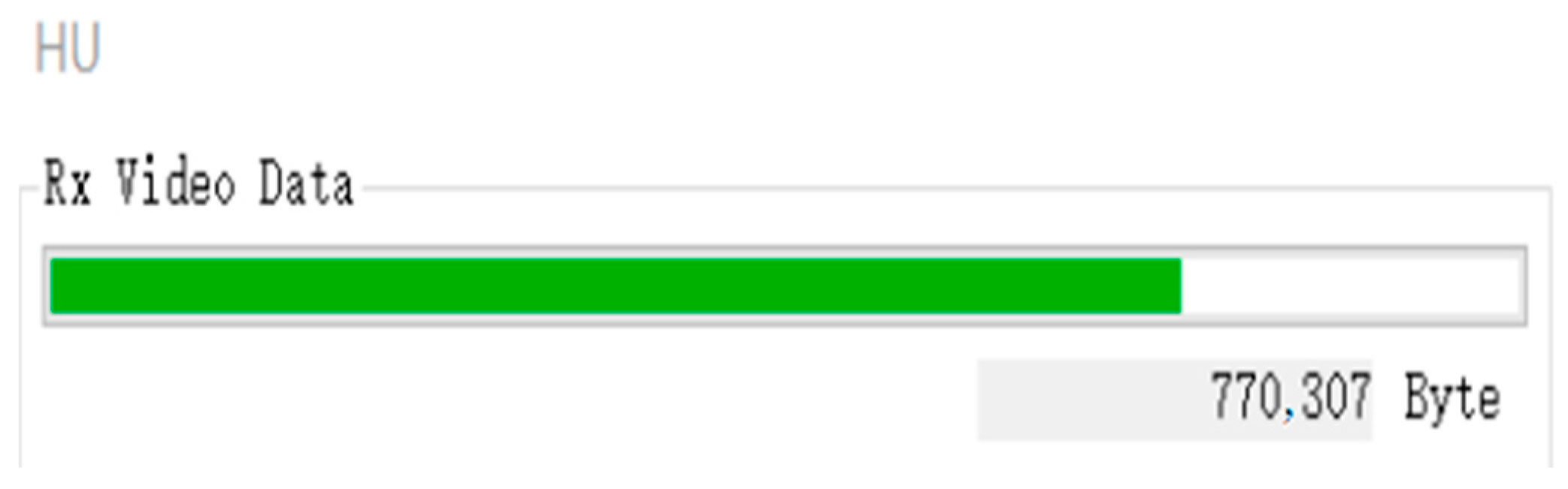
- Multimedia signals: The in-vehicle multimedia module successfully plays video on the designed HeadUnit analog video player. In this paper, we have tested this by intercepting a clip from the classic movie “Titanic” and verifying that it can be played normally and smoothly through the simulation player, as shown in Figure 11.
4.1.2. Generation of Normal Attack Scenarios
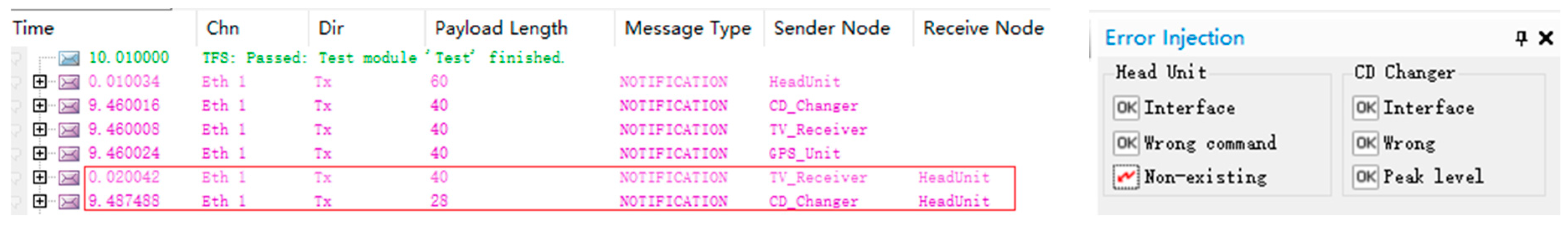
- (A)
- Non-existing Attacks: This type of attack simulates the presence of messages that should not exist in the network under normal operation. The simulation incorporates such attacks by generating and transmitting packets with identifiers that do not correspond to any known ECU. Following this approach, we conducted a non-existing attack on the entire Ethernet network through a malicious module targeting control and video signals. The results, as depicted in Figure 14, show that the attack was successful, with the CANoe software trace confirming the malicious module’s impact.
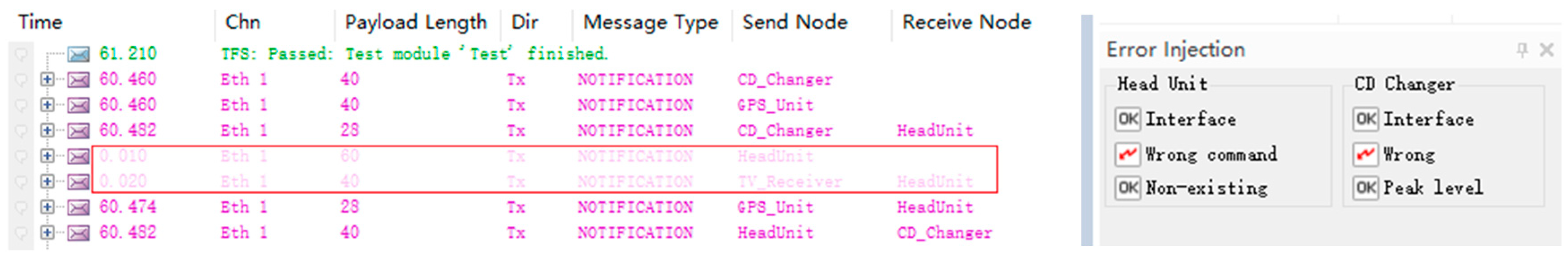
- (B)
- Wrong command Attacks: These attacks are characterized by the transmission of messages that are correct in format but incorrect in content. The simulation introduces wrong attacks by altering the payload of legitimate messages to contain incorrect data. As shown in Figure 15, the video device (TV_Receiver) and the GPS_Unit, acting as attack modules, conducted a wrong command attack on the Ethernet bus. This manipulation of data within the network demonstrates the potential for malicious actors to disrupt normal vehicle operations by sending misleading commands.
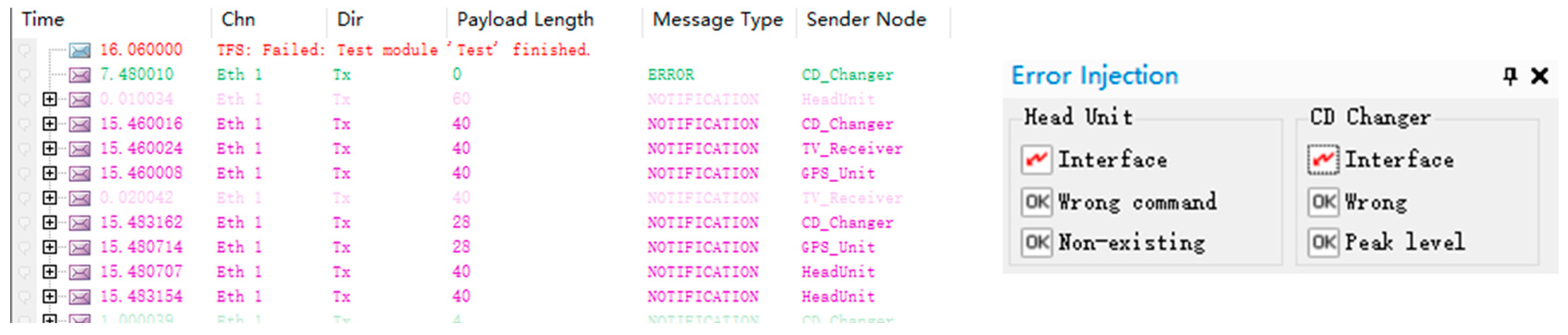
- (C)
- Tampering Attacks: Tampering attacks involve the modification of legitimate messages in transit. In the simulation, tampering attacks are recreated by intercepting and modifying legitimate traffic, changing data such as sensor readings or control commands. As illustrated in Figure 16, tampering attacks on control signals were conducted, demonstrating that effective control signal tampering can be achieved, particularly targeting the HeadUnit module. This manipulation of critical signals highlights the vulnerability of in-vehicle networks to unauthorized alterations that can lead to compromised vehicle control.
4.2. Performance Analysis of Data Encryption and Authentication Algorithms
- (A)
- IAES-128 algorithm simulation result:
- (B)
- IMD5 algorithm simulation result:
- (C)
- AES-ECC algorithm simulation result:
4.3. Simulation Results of the Overall Security Mechanism
- (A)
- Control signal security defense:
- (B)
- Multimedia signal security defense:
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Karanki, S.S.; Khan, M.S. SMMV: Secure multimedia delivery in vehicles using rode side infrastructure. Veh. Commun. 2017, 7, 40–50. [Google Scholar]
- Shaw, R.; Jackman, B. An introduction to FlexRay as an industrial network. In Proceedings of the IEEE International Symposium on Industrial Electronics, Cambridge, UK, 30 June–2 July 2008. [Google Scholar]
- Jadhav, S.; Kshirsagar, D. A Survey on Security in Automotive Networks. In Proceedings of the Fourth International Conference on Computing Communication Control and Automation (ICCUBEA), Pune, India, 16–18 August 2018. [Google Scholar]
- Zhou, L.; Du, S.G.; Zhu, H.J. Location Privacy in Usage-based Automotive Insurance: Attacks and Countermeasure. IEEE Trans. Inf. Forensics Secur. 2019, 14, 196–211. [Google Scholar] [CrossRef]
- Mortazavi, S.; Schleicher, D.; Gerfers, F. Modeling and Verification of Automotive Multi-Gig Ethernet Communication up to 2.5 Gbps and the Corresponding EMC Analysis. In Proceedings of the IEEE Symposium on Electromagnetic Compatibility, Signal Integrity and Power Integrity (EMC, SI & PI), Long Beach, CA, USA, 30 July–3 August 2018. [Google Scholar]
- Liu, Z.Q.; Wan, L.; Guo, J.J.; Huang, F.R.; Feng, X.; Wang, L.B.; Ma, J.F. PPRU: A Privacy-Preserving Reputation Updating Scheme for Cloud-Assisted Vehicular Networks. IEEE Trans. Veh. Technol. 2023, 1, 1–16. [Google Scholar] [CrossRef]
- Baee, M.A.R.; Simpson, L.; Boyen, X.; Foo, E.; Pieprayk, J. Anonymous Lightweight Inter-Vehicle Broadcast Authentication with Encryption. IEEE Trans. Dependable Secur. Comput. 2023, 20, 1799–1817. [Google Scholar]
- Tangade, S.; Manvi, S.S.; Lorenz, P. Trust Management Scheme Based on Hybrid Cryptography for Secure Communications in VANETs. IEEE Trans. Veh. Technol. 2020, 69, 5232–5243. [Google Scholar] [CrossRef]
- Li, Y.J.; Bi, R.; Jiang, N.; Li, F.Q.; Wang, M.S.; Jing, X.P. Methods and Challenges of Cryptography-Based Privacy-Protection Algorithms for Vehicular Networks. Electronics 2024, 69, 2372. [Google Scholar] [CrossRef]
- An, B.; Kim, Y. Optimization of Vehicle Communication Networking Parameters in eAVB. In Proceedings of the IEEE International Conference on Consumer Electronics—Asia (ICCE-Asia), Seoul, Republic of Korea, 1–3 November 2020. [Google Scholar]
- Bello, L.L.; Patti, G.; Leonardi, L. A Perspective on Ethernet in Automotive Communications—Current Status and Future Trends. Appl. Sci. 2021, 13, 1278. [Google Scholar] [CrossRef]
- Lee, T.Y.; Lin, I.A.; Liao, R.H. Design of a FlexRay/Ethernet Gateway and Security Mechanism for In-Vehicle Networks. Sensors 2020, 20, 641. [Google Scholar] [CrossRef]
- Ju, H.; Jeon, B.; Kim, D.; Jung, B.; Jung, K. Security Considerations for In-Vehicle Secure Communication. In Proceedings of the International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Republic of Korea, 16–18 October 2019. [Google Scholar]
- Zhang, L.X.; Ma, D. A Binarized Neural Network Approach to Accelerate In-Vehicle Network Intrusion Detection. IEEE Access 2022, 10, 123505–123520. [Google Scholar] [CrossRef]
- Woo, S.; Jo, H.J.; Le, H.H. A practical wireless attack on the connected car and security protocol for in-vehicle CAN. IEEE Trans. Intell. Transp. Syst. 2015, 16, 993–1006. [Google Scholar] [CrossRef]
- Song, H.M.; Kim, H.R.; Kim, H.K. Intrusion detection system based on the analysis of time intervals of CAN messages for in-vehicle network. In Proceedings of the International Conference on Information Networking 2016, International Conference on Information Networking (ICOIN), Kota Kinabalu, Malaysia, 13–15 January 2016; pp. 63–68. [Google Scholar]
- Jeon, B.; Ju, H.; Jung, B.; Kim, K.; Lee, D. A Study on Traffic Characteristics for Anomaly Detection of Ethernet-based IVN. In Proceedings of the International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Republic of Korea, 16–18 October 2019. [Google Scholar]
- Lee, Y.; Woo, S.; Song, Y.; Lee, J.; Lee, D.H. Practical Vulnerability Information Sharing Architecture for Automotive Security-Risk Analysis. IEEE Access 2020, 8, 120009–120018. [Google Scholar] [CrossRef]
- Altalbe, A. Enhanced Intrusion Detection in In-Vehicle Networks Using Advanced Feature Fusion and Stacking-Enriched Learning. IEEE Access 2023, 12, 2045–2056. [Google Scholar] [CrossRef]
- Anthony, C.; Elgenaidi, W.; Rao, M. Intrusion Detection System for Autonomous Vehicles Using Non-Tree Based Machine Learning Algorithms. Electronics 2024, 13, 809. [Google Scholar] [CrossRef]
- Herrewege, A.V.; Singelée, D.; Verbauwhede, I. CANAuth—A simple, backward compatible broadcast authentication protocol for CAN bus. In Proceedings of the ECRYPT Workshop on Lightweight Cryptography 2011, Louvain-la-Neuve, Belgium, 28–29 November 2011. [Google Scholar]
- Mundhenk, P.; Paverd, A. Security in Automotive Networks: Lightweight Authentication and Authorization. ACM Trans. Des. Autom. Electron. Syst. 2017, 22, 1–27. [Google Scholar] [CrossRef]
- Zhao, R.; Qin, G.; Lyu, Y.; Yan, J. Security-Aware Scheduling for TTEthernet-Based Real-Time Automotive Systems. IEEE Access 2019, 7, 85971–85984. [Google Scholar] [CrossRef]
- Iorio, M.; Buttiglieri, A.; Reineri, M.; Risso, F.; Sisto, R.; Valenza, F. Protecting In-Vehicle Services: Security-Enabled SOME/IP Middleware. IEEE Veh. Technol. Mag. 2020, 15, 77–85. [Google Scholar] [CrossRef]
- Wang, E.; Xu, W.; Sastry, S.; Liu, S.; Zeng, K. Hardware Module-Based Message Authentication in Intra-vehicle Networks 2017. In Proceedings of the ACM/IEEE 8th International Conference on Cyber-Physical Systems (ICCPS), Pittsburgh, PA, USA, 18–21 April 2017. [Google Scholar]
- Jin, S.Y.; Liu, M.Z.; Wu, Y.J.; Xu, Y.H.; Jiang, J.N.; Xu, Y.N. Research of Message Scheduling for In-vehicle FlexRay Network Static Segment Based on Next Fit Decreasing (NFD) Algorithm. Appl. Sci. 2018, 8, 2071. [Google Scholar] [CrossRef]
- Miao, Y.B.; Yang, Y.; Li, X.G.; Liu, Z.Q.; Li, H.W.; Choo, K.K.R.; Deng, R.H. Efficient Privacy-Preserving Spatial Range Query over Outsourced Encrypted Data. IEEE Trans. Inf. Forensics Secur. 2023, 18, 3921–3933. [Google Scholar] [CrossRef]
- Jeong, S.H.; Chung, B.H.; Kim, H.K. Convolutional neural network-based intrusion detection system for AVTP streams in automotive Ethernet-based networks. Veh. Commun. 2021, 29, 100338. [Google Scholar] [CrossRef]
- Liu, X.Y.; Nie, Z.B.; Li, D.; Yu, H.B. Design of An Improved Ethernet AVB Model for Real-time Communication in In-Vehicle Network. In Proceedings of the IEEE 3rd Information Technology, Networking, Electronic and Automation Control Conference (ITNEC), Chengdu, China, 15–17 March 2019. [Google Scholar]
- Priyanka, M.P. FPGA implementation of image encryption and decryption using AES 128-bit core. In Proceedings of the International Conference on Communication and Electronics Systems (ICCES), Coimbatore, India, 21–22 October 2016. [Google Scholar]
- Bella, G.P.; Costantino, G.; Mattueucci, I. Designing and implementing an AUTOSAR-based Basic Software Module for enhanced security. Comput. Netw. 2022, 218, 109377. [Google Scholar] [CrossRef]
- Ma, B.; Yang, S.; Zuo, Z.; Zou, B.; Cao, Y.; Yan, X.; Zhou, S.; Li, J. An Authentication and Secure Communication Scheme for In-Vehicle Networks Based on SOME/IP. Sensors 2022, 22, 647. [Google Scholar] [CrossRef] [PubMed]
- Alkhatib, N.; Mushtaq, M.; Ghauch, H.; Danger, J.L. Unsupervised Network Intrusion Detection System for AVTP in Automotive Ethernet Networks 2022. In Proceedings of the IEEE Intelligent Vehicles Symposium (IV), Aachen, Germany, 4–9 June 2022. [Google Scholar]
- Staat, P.; Jansen, K.; Zenger, C.; Boll, H.E.; Paar, C. Analog Physical-Layer Relay Attacks with Application to Bluetooth and Phase-Based Ranging. In Proceedings of the 15th ACM Conference on Security and Privacy in Wireless and Mobile Networks, New York, NY, USA, 16–19 May 2022. [Google Scholar]
- Ju, Z.; Zhang, H.; Li, X.; Chen, X. A Survey on Attack Detection and Resilience for Connected and Automated Vehicles: From Vehicle Dynamics and Control Perspective. IEEE Trans. Intell. Veh. 2022, 7, 815–837. [Google Scholar] [CrossRef]
- Cui, J.; Chen, Y.; Zhong, H.; He, D.B.; Bolodurina, I.; Liu, L. Lightweight Encryption and Authentication for Controller Area Network of Autonomous Vehicles. IEEE Trans. Veh. Technol. 2023, 72, 14756–14770. [Google Scholar] [CrossRef]
- Shirvani, S.; Baseri, Y.; Ghorbani, A. Evaluation Framework for Electric Vehicle Security Risk Assessment. IEEE Trans. Intell. Transp. Syst. 2023, 25, 33–56. [Google Scholar] [CrossRef]
- Wang, C.T.; Qin, G.H.; Zhao, R.; Song, S.M. An Information Security Protocol for Automotive Ethernet. J. Comput. 2021, 32, 39–52. [Google Scholar]
- Padmanaban, R.; Ranjani, J.J. Vehicle Intruder Alert System using Multi-Layered Authentication Technique. Indian J. Sci. Technol. 2016, 9, 1–7. [Google Scholar] [CrossRef]
- Douss, A.B.; Abassi, R. Sauveron.State-of-the-art survey of in-vehicle protocols and automotive Ethernet security and vulnerabilities. Math. Biosci. Eng. 2023, 20, 17057–17095. [Google Scholar] [CrossRef]
- Zhang, Q. An Overview and Analysis of Hybrid Encryption: The Combination of Symmetric Encryption and Asymmetric Encryption 2021. In Proceedings of the 2nd International Conference on Computing and Data Science (CDS), California, CA, USA, 28–29 January 2021. [Google Scholar]
- VenkataGiri, J.; Murty, A. Elliptical Curve Cryptography Design Principles 2021, International Conference on Recent Trends on Electronics. In Proceedings of the International Conference on Recent Trends on Electronics, Information, Communication & Technology (RTEICT), Bangalore, India, 27–28 August 2021. [Google Scholar]





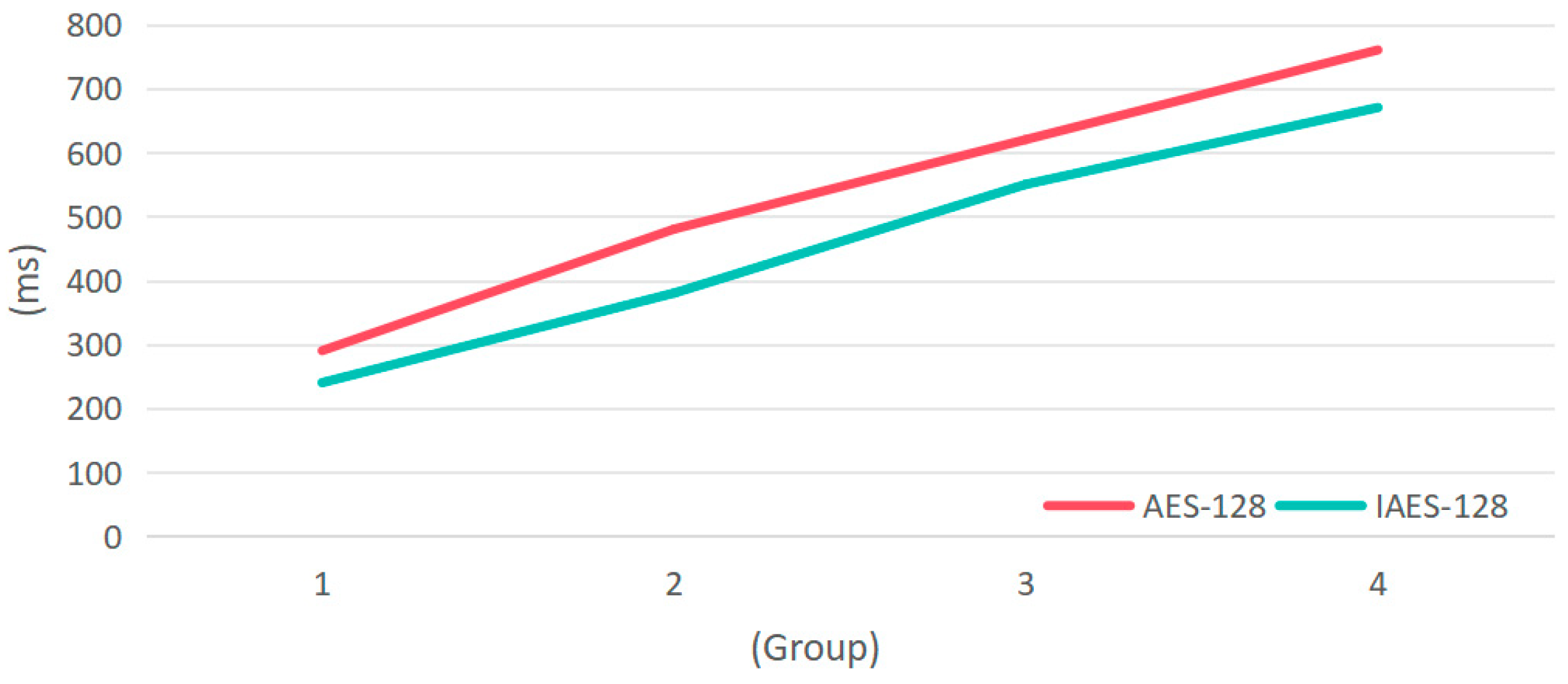




| Group | Data Size (Bytes) | AES-128 Encryption Time (ms) | IAES-128 Encryption Time (ms) | Efficiency Improvement |
|---|---|---|---|---|
| 1 | 100 | 293 | 240 | 18.12% |
| 2 | 500 | 473 | 376 | 20.53% |
| 3 | 1000 | 613 | 536 | 12.56% |
| 4 | 2000 | 759 | 664 | 11.88% |
| Group | Data Size (Bytes) | AES-128 Encryption Time (ms) | ECC Encryption Time (ms) | AES-ECC Encryption Time (ms) |
|---|---|---|---|---|
| 1 | 100 | 243 | 300 | 360 |
| 2 | 200 | 390 | 468 | 410 |
| 3 | 300 | 487 | 590 | 505 |
| 4 | 400 | 604 | 800 | 624 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wu, Y.; Xiong, L.; Wang, C.; Xu, Y. Efficient Secure Mechanisms for In-Vehicle Ethernet in Autonomous Vehicles. Electronics 2024, 13, 3625. https://doi.org/10.3390/electronics13183625
Wu Y, Xiong L, Wang C, Xu Y. Efficient Secure Mechanisms for In-Vehicle Ethernet in Autonomous Vehicles. Electronics. 2024; 13(18):3625. https://doi.org/10.3390/electronics13183625
Chicago/Turabian StyleWu, Yujing, Liping Xiong, Caiyuan Wang, and Yinan Xu. 2024. "Efficient Secure Mechanisms for In-Vehicle Ethernet in Autonomous Vehicles" Electronics 13, no. 18: 3625. https://doi.org/10.3390/electronics13183625






