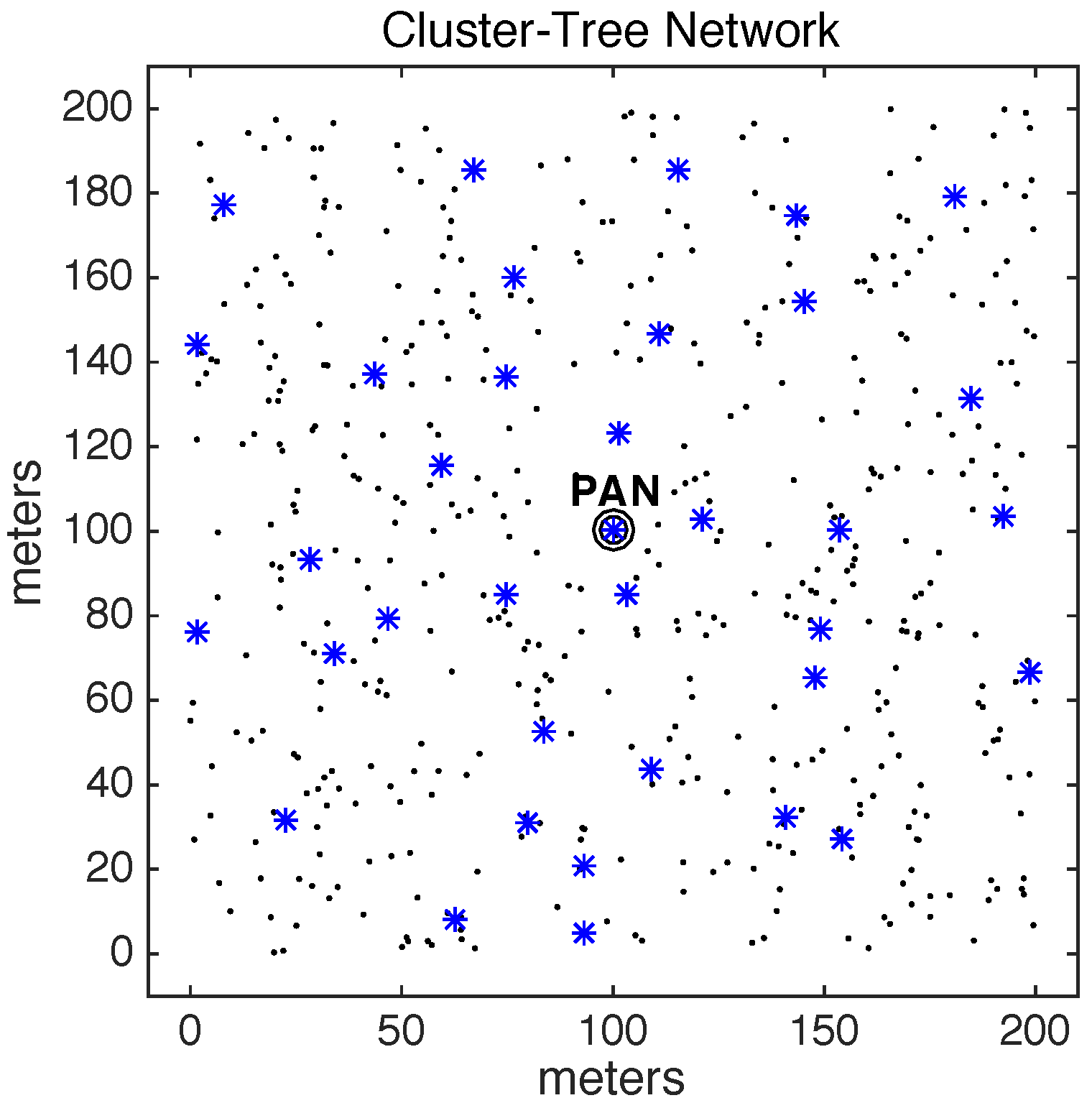
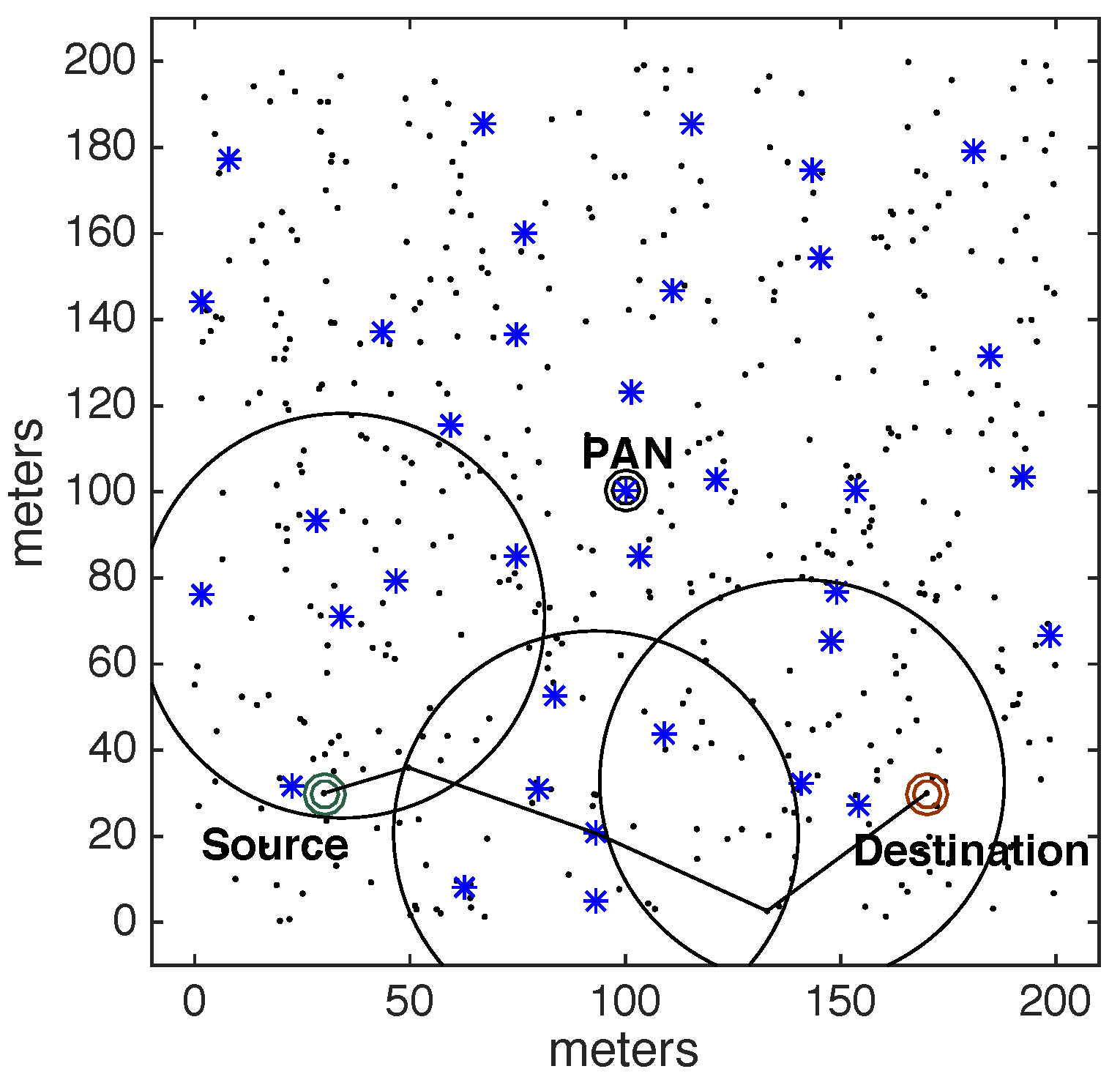
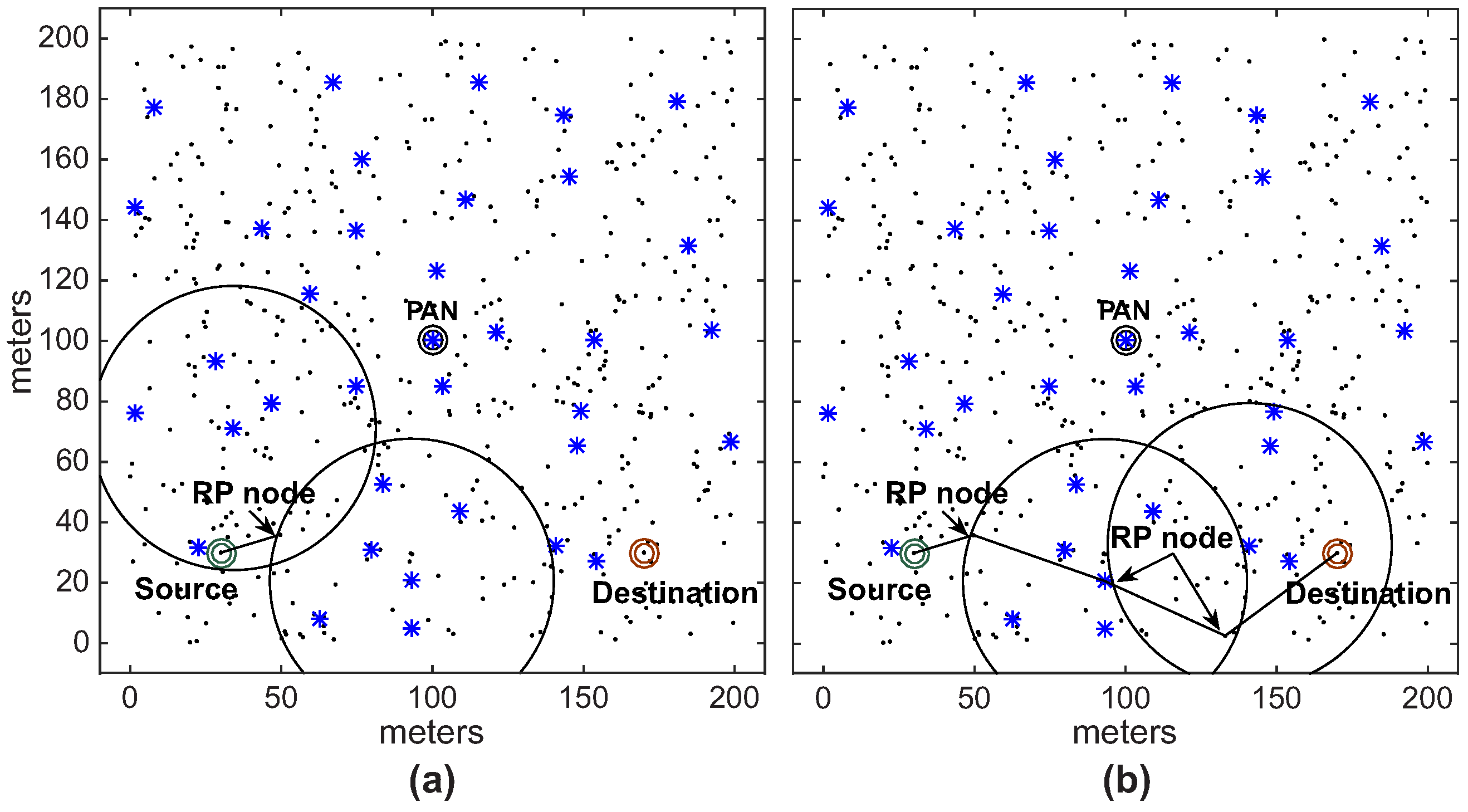
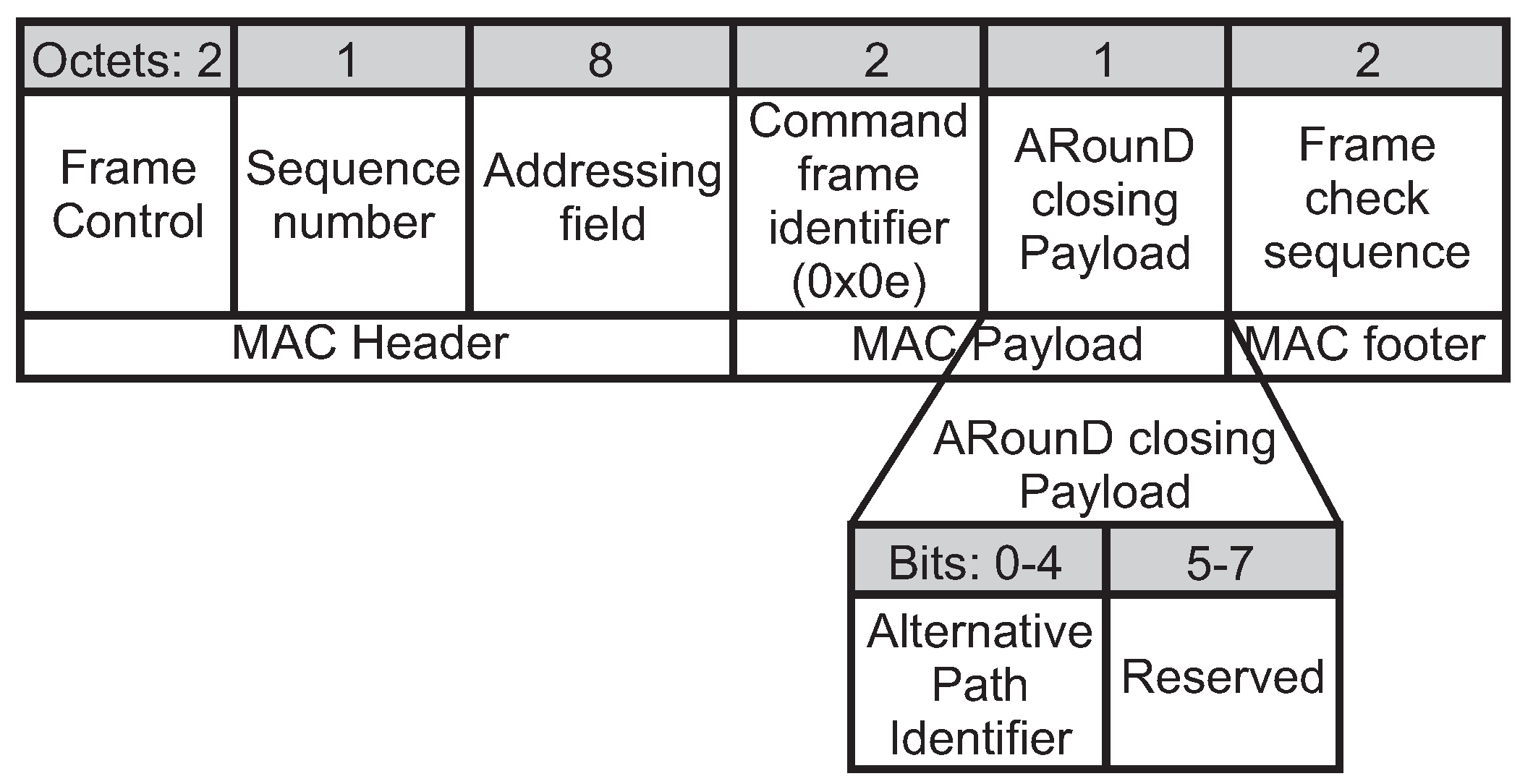
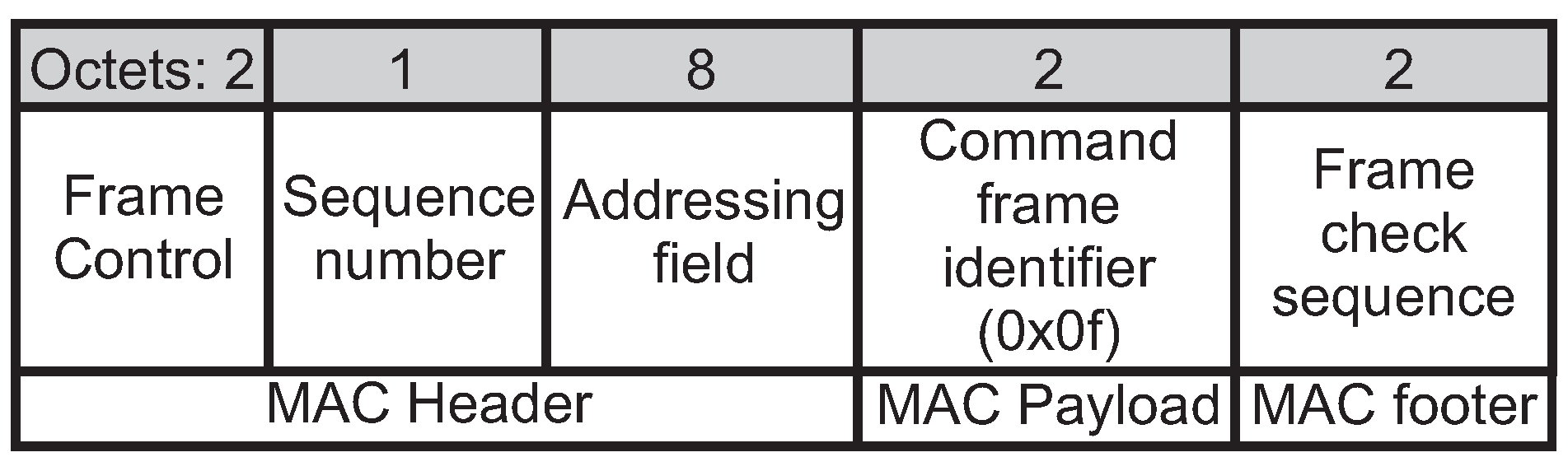
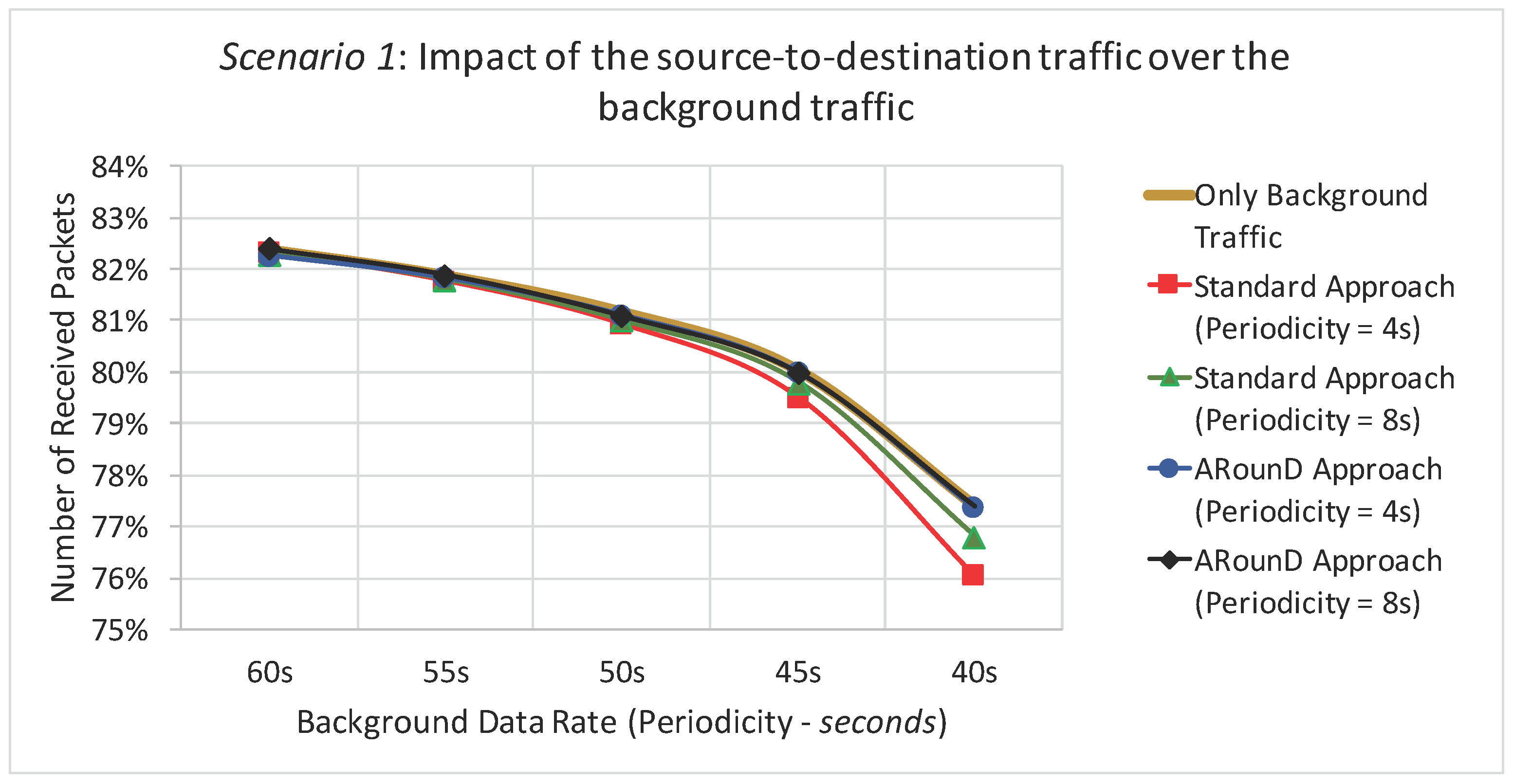
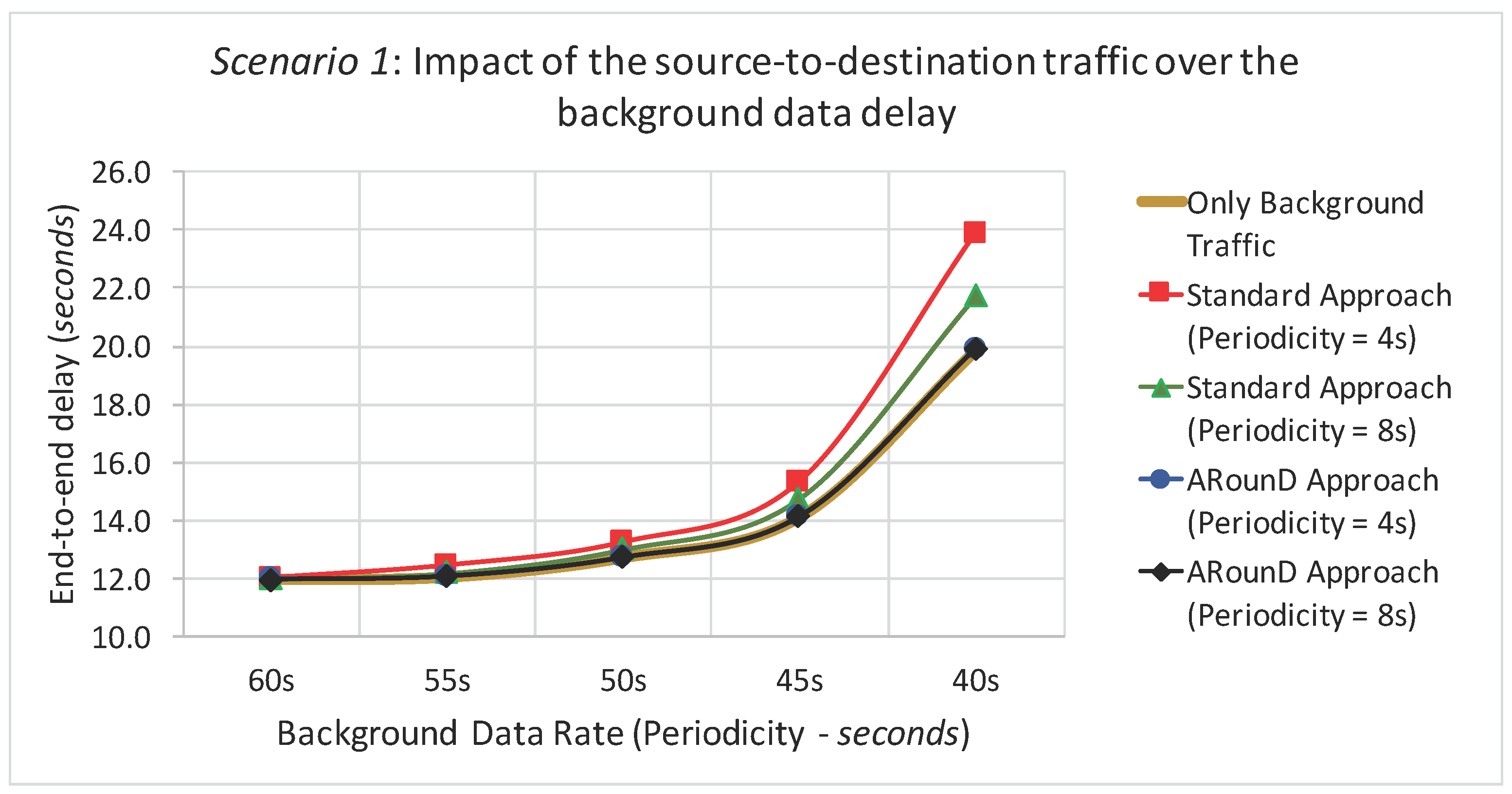
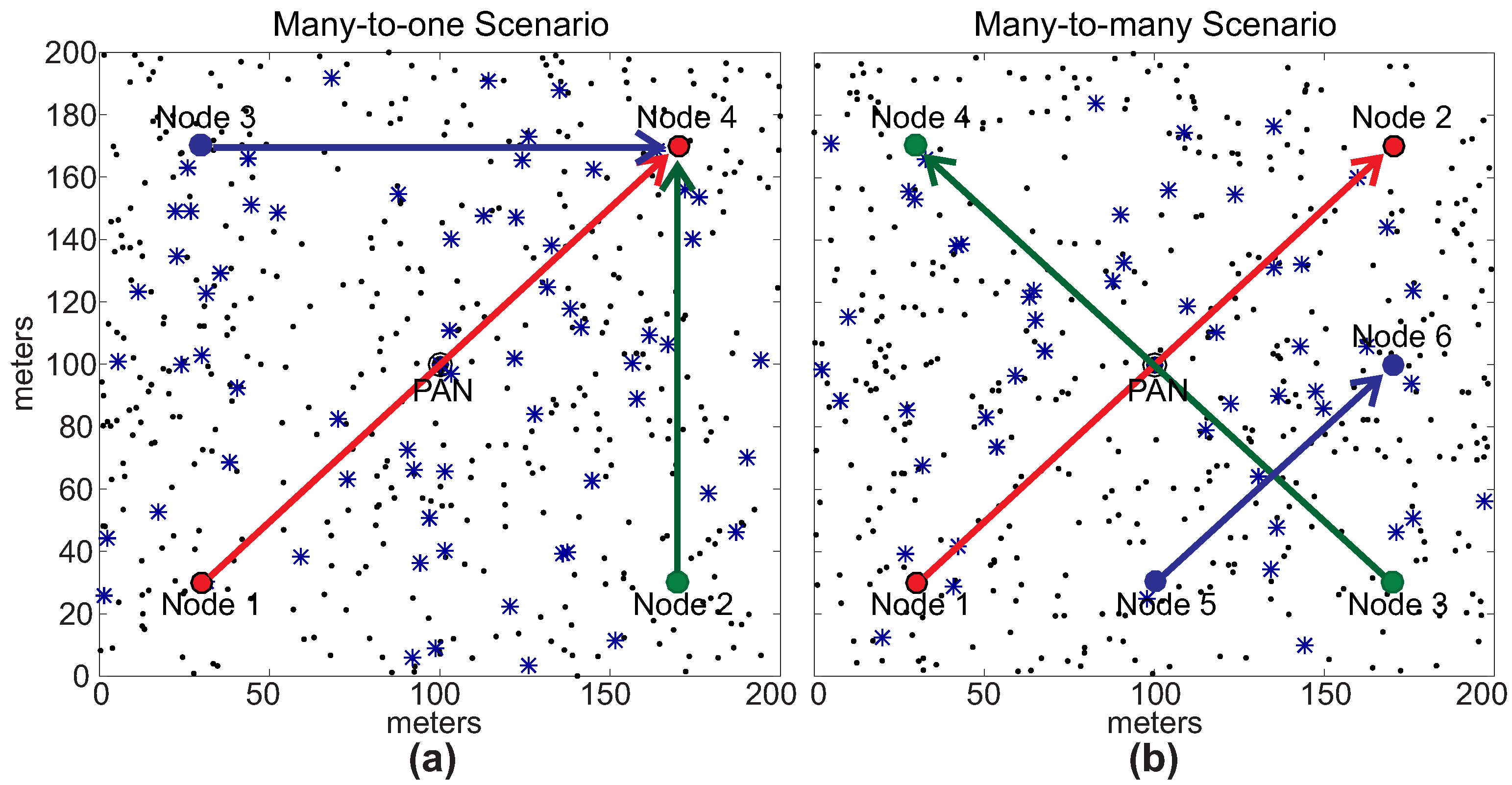
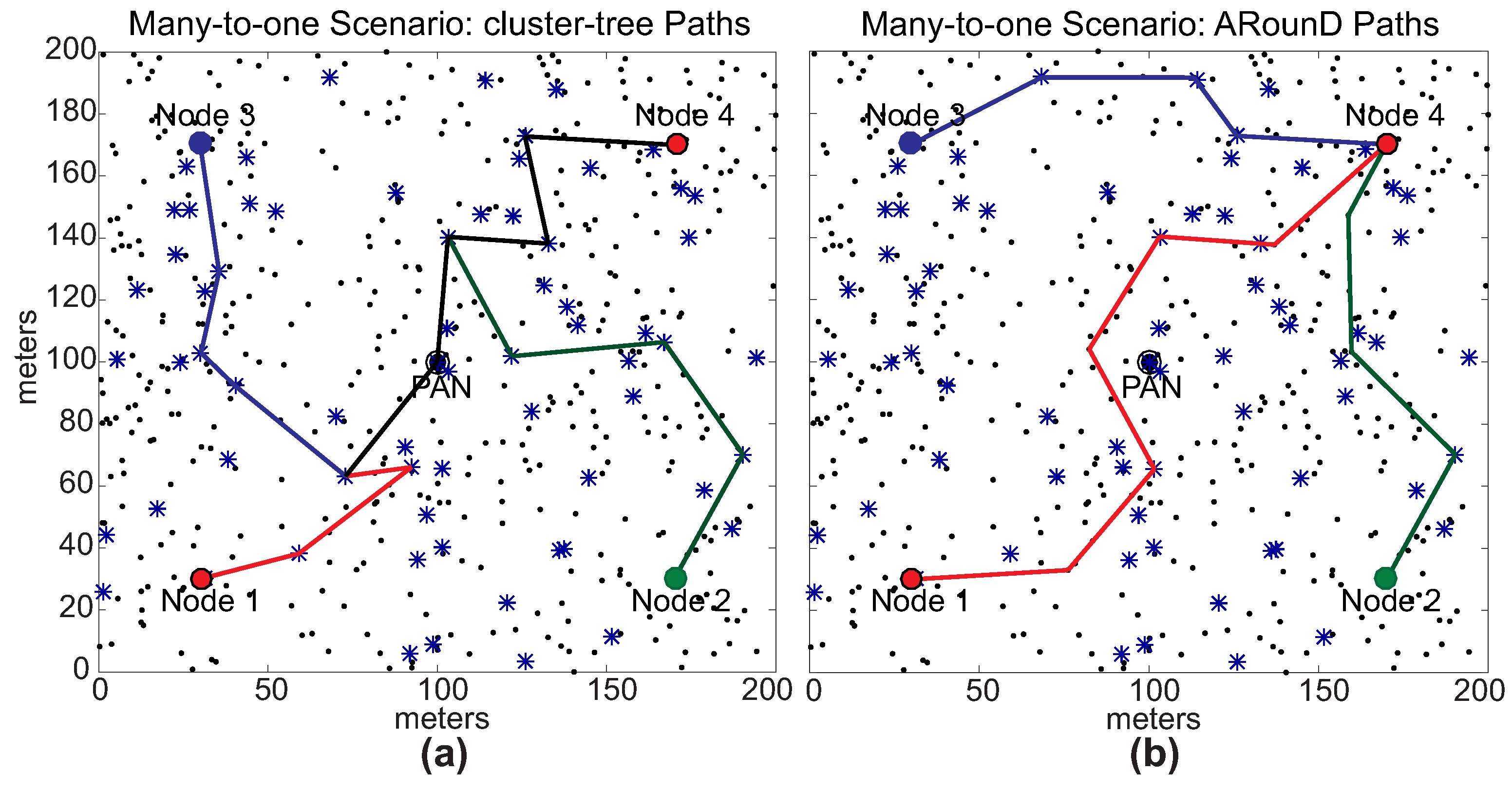
2.1. IEEE 802.15.4/ZigBee Cluster-Tree Topologies
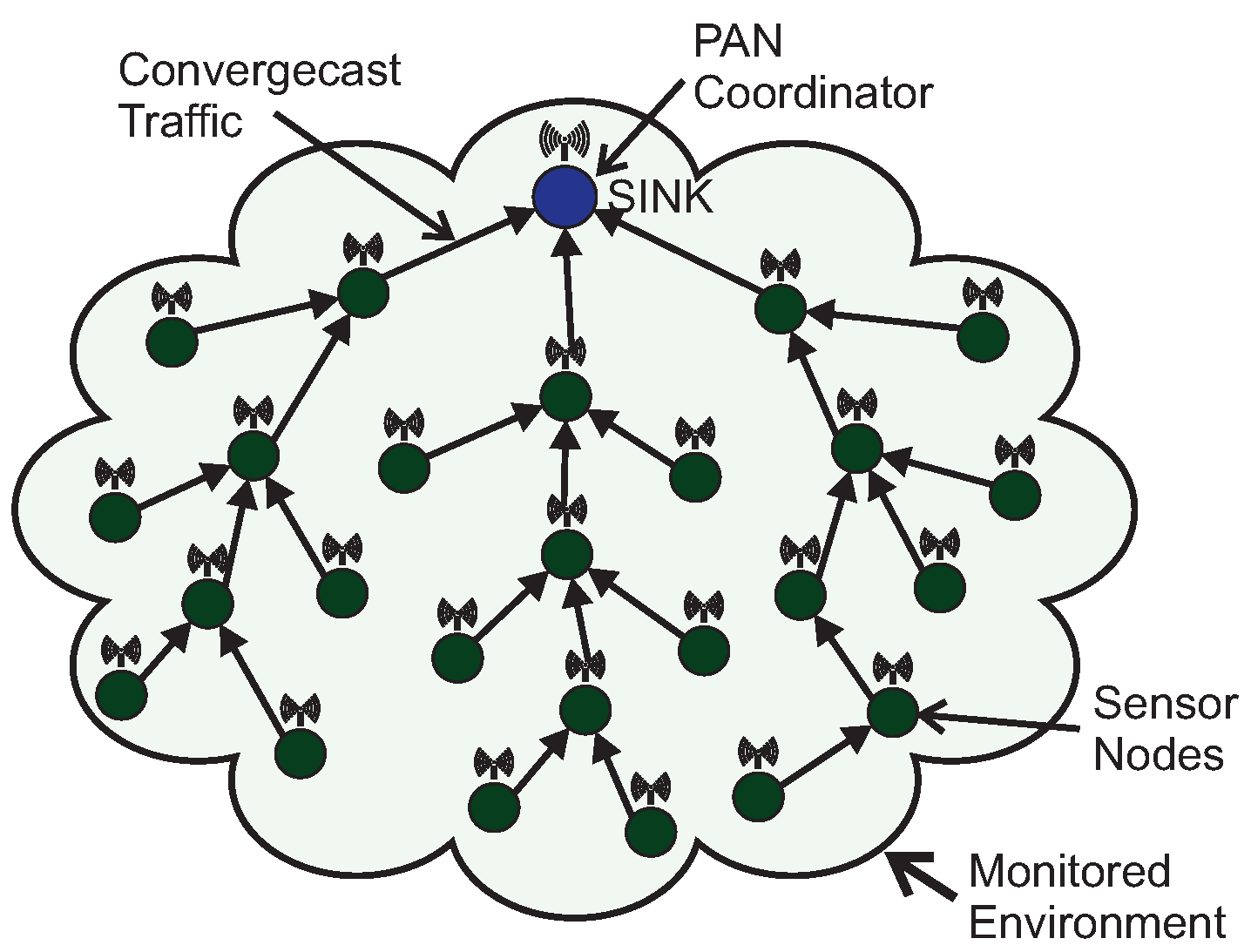
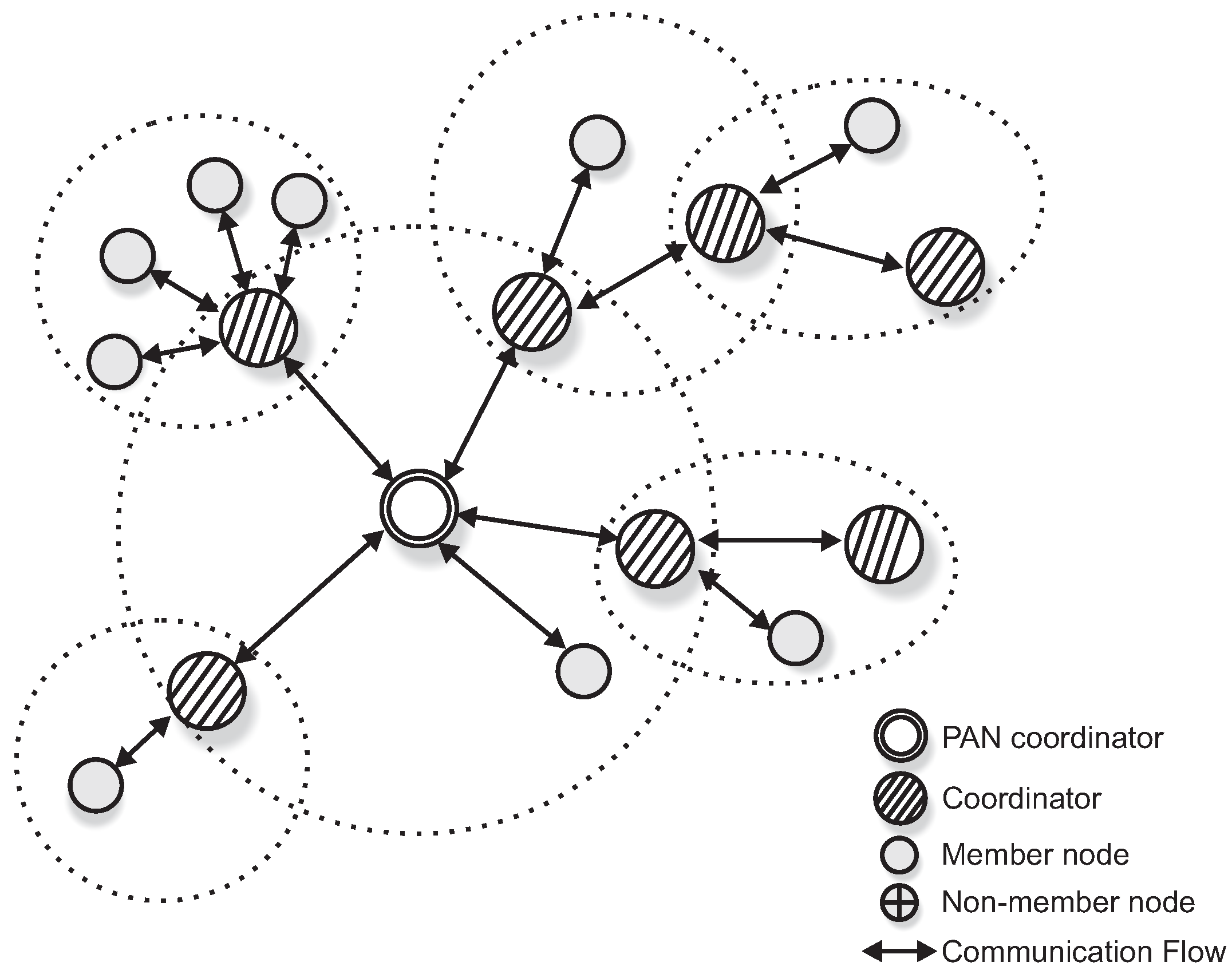
A cluster-tree topology is a special case of a peer-to-peer network. In a cluster-tree topology, nodes/devices are grouped in clusters, coordinated by a FFD node called Cluster-Head (CH). The CH provides synchronisation mechanisms for its associated nodes and centralises all intra-cluster communication. The cluster-tree network formation is initiated by the PAN coordinator, which acts as coordinator for the network, being responsible for all network management activities.
According to the IEEE 802.15.4 standard, the simplest case of a cluster-tree network is a single cluster (coordinated by the PAN coordinator). New nodes may be allowed to create their own clusters, increasing the coverage of the network. Within this context, several neighbouring clusters can be used to build wide-scale cluster-tree networks, where the coordinators are connected by parent-child relationships, forming a multicluster hierarchical network structure.
Figure 3 shows an example of an IEEE 802.15.4 cluster-tree network.
Although considering cluster-tree networks, the IEEE 802.15.4 standard does not discuss the required network formation mechanisms. The ZigBee specification provides these mechanisms, defining a hierarchical addressing scheme and the associated tree routing algorithms, where network addresses are assigned based on address blocks. Thus, each cluster-head has its own block of sequential addresses, which are assigned to its child nodes. Based on this hierarchical addressing, ZigBee also provides a deterministic tree routing scheme. In this scheme, routing is based on the destination address. In case the destination address is a descendant node, the packet is forward to the corresponding child node; otherwise, the packet is forward to the parent node.
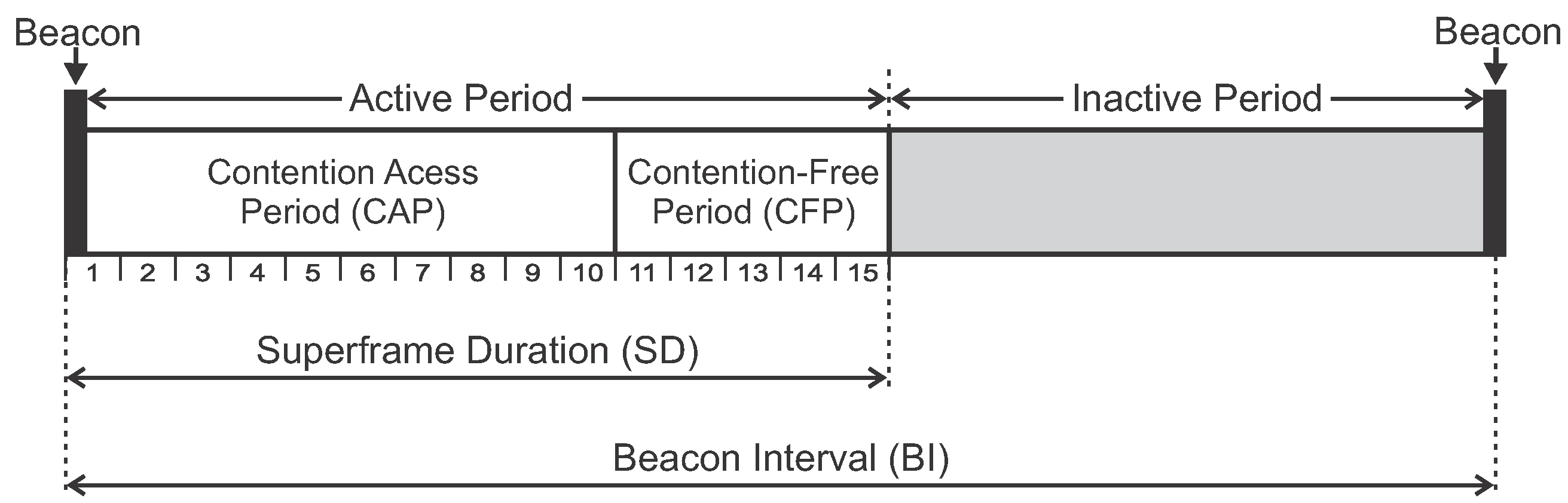
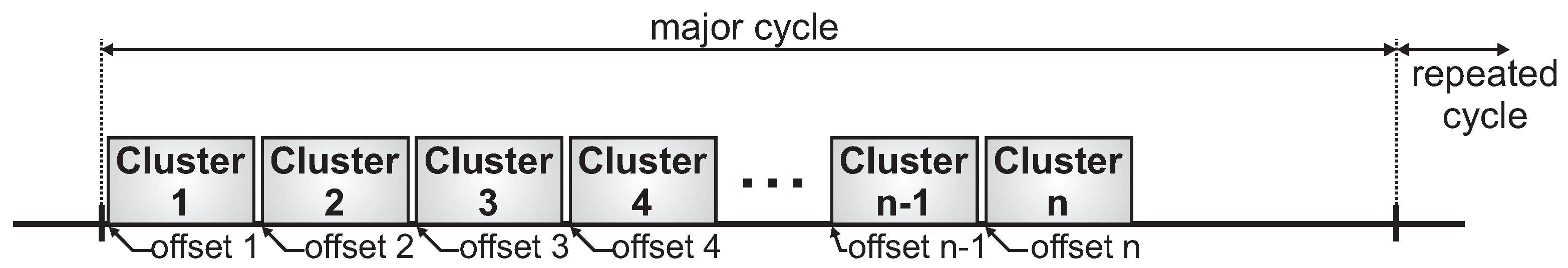
In cluster-tree topologies, the network operates in a beacon-enabled mode. In this mode, communication exchanges are organised according to a structure called Superframe. A superframe is bounded by beacon frames periodically transmitted by the coordinators (cluster-heads). These beacon frames synchronise the associated nodes, identify the PAN and describe the superframe structure.
Figure 4 illustrates the superframe structure.
The superframe is described by the
macBeaconOrder (BO) and
macSuperframeOrder (SO) parameters, where Beacon Interval (BI) and the Superframe Duration (SD) are defined as follows:
with .
BI defines the interval at which the coordinator periodically transmits beacon frames. In turn, the SD parameter defines the length of the active portion of the superframe. The aBaseSuperframeDuration parameter defines the minimum duration of the superframe when SO is 0. The IEEE 802.15.4 standard defines this parameter with 960 symbols duration, which corresponds to 15.36 ms (assuming a network with bit rate of 250 kbps, frequency band of 2.4 GHz, and one symbol as 4 bits).
Each superframe is divided in two parts: the active and inactive periods. During the inactive period, the coordinator and associated nodes can enter in low power mode to save energy (sleep mode). During the active period, nodes can communicate with the coordinator. The active part (communication period) comprises two periods: Contention Access Period (CAP) and Contention-Free Period (CFP).
In the CAP period, whenever a device wishes to communicate, it contends with other devices using a slotted Carrier Sense Multiple Access with Collision Avoidance (CSMA-CA) procedure to access the channel. The CFP is defined for applications that require low latency or specific bandwidth. In the CFP period, the coordinator allocates Guaranteed Time Slots (GTS) for specific nodes. In these slots, nodes can transmit data without contending for the channel access. The coordinator can allocate up to seven GTSs, and a GTS is allowed to occupy more than one slot period [
5].
In the cluster-tree topology, a coordinator node (excluded the PAN coordinator) must keep the synchronisation between its own active period (acting as coordinator node) and the parent’s active period (acting as child node). Also, for each cluster, low duty cycles can be activated to save energy, setting a value of SO smaller than BO.
In cluster-tree networks, sending beacon frames without any special care on timing issues may result in collisions among beacons from neighbour clusters [
7]. Thus, it is necessary to implement inter-cluster synchronisation mechanisms to avoid this problem. Two types of beacon collisions are possible: direct or indirect. In a direct beacon collision, two or more coordinators (in the transmission range of each other) transmit their beacon frames at the same time. In the indirect beacon frame collision, two or more coordinators are hidden-nodes from each other and send messages to an overlapped node [
7].
This paper is focused on cluster-tree networks defined by the ZigBee specification [
6], due to some specific features, such as: suitability to deploy wide-scale networks, energy-efficiency and time-sensitive message guarantees.
2.2. Related Work
In recent years, due to the high demand of applications supported by wireless sensor networks, there have been a large number of works addressing cluster-tree WSNs. Multiple issues are being addressed, such as: network formation schemes, routing protocols, cross-layer approaches, real-time requirements, reliability and availability issues, energy-efficiency, scalability, congestion control and beacon frames scheduling. Each of these issues have their own challenges and special considerations. Additionally, with the increased demand for wide-scale applications that need to operate with time-sensitive data and must be energy-efficient, the design of wide-scale WSNs is becoming more challenging due to the large number of constraints that need to be simultaneously addressed.
The state-of-the-art indicates that the use of hierarchical clustering protocols has some advantages over flat protocols for wide-scale applications with respect to scalability [
36,
37,
38], energy-efficiency [
7,
14,
36,
38,
39] and time-sensitive data operation [
7,
14,
15,
38,
39,
40]. Therefore, several works have been published in the literature, encompassing clustering for WSNs, with different concerns. As an example, there are several surveys that summarise popular clustering protocols and analyse the strengths and weaknesses of available routing protocols based on different metrics [
41,
42,
43,
44,
45,
46]. For example, LEACH (Low Energy Adaptive Clustering Hierarchy) protocol [
47] is one of the most cited hierarchical protocols in the literature, which has motivated the design of several other protocols. In LEACH, sensor nodes are grouped in clusters for sending data to their cluster-heads, which aggregate data and send it to the base station. In order to balance the energy consumption of sensor nodes, this protocol randomly selects a set of different cluster-heads during each round. Also, Kumar et al. [
36] proposed an Energy Efficient Heterogeneous Clustered Scheme (EEHC) based on the LEACH protocol, considering the heterogeneity of network resources. However, as it uses single-hop routing, the cluster-heads send directly data to the base station, which leads to an increase of energy consumption. Thus, this type of communication may be impracticable for wide-scale environments.
Additionally, several cross-layer approaches have been proposed to deal with energy-efficient communication in Wireless Sensor Networks [
48,
49,
50,
51,
52]. Typically, cross-layer approaches blend common protocol layer functionalities into a cross-layer module, addressing simultaneously congestion control, routing and medium access control issues to enhance the efficiency of the traditional layered protocol architectures.
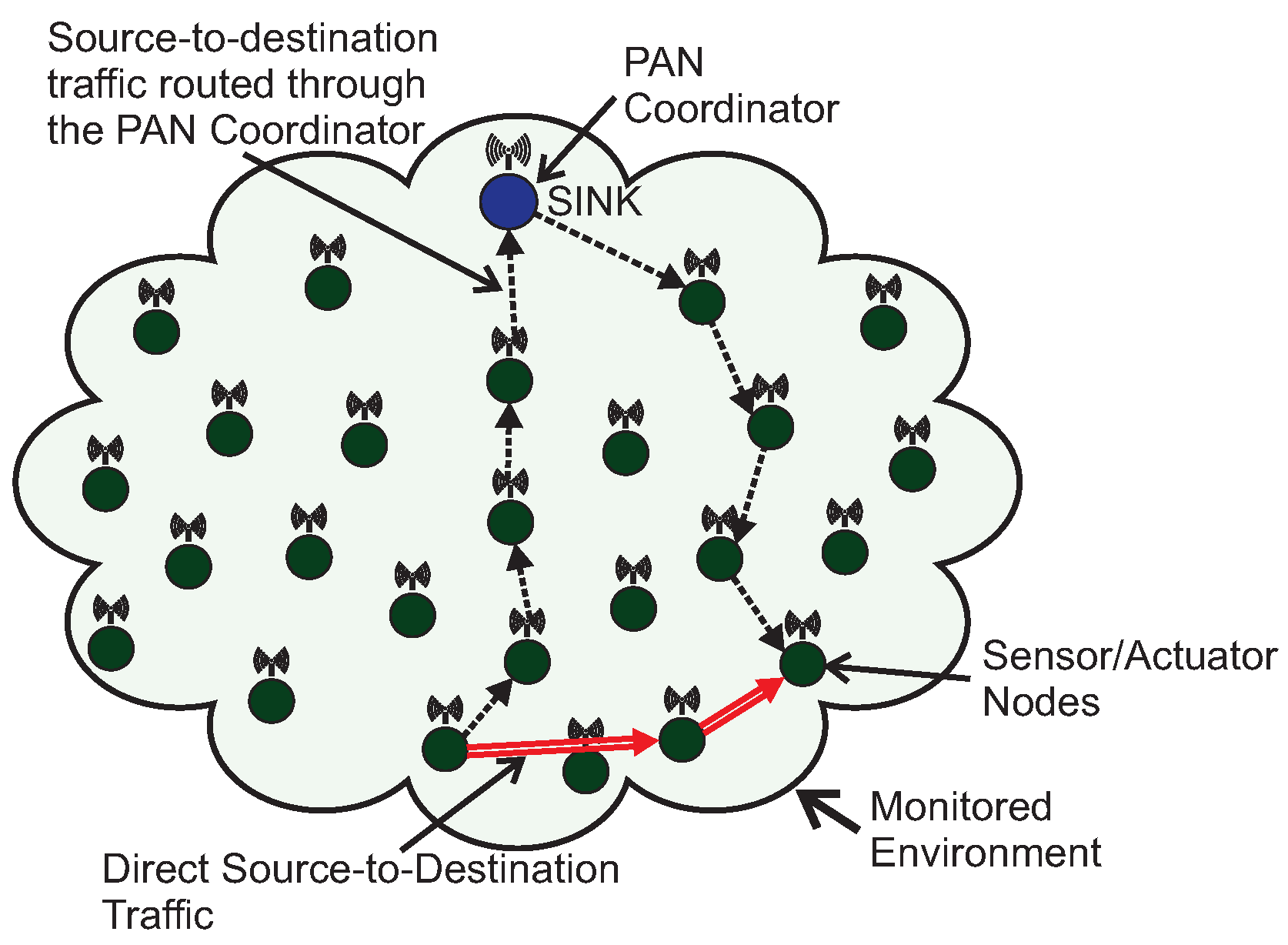
As the communication scheme proposed in this paper addresses setting-up new communication paths in wide-scale cluster-tree networks, this state-of-the-art study does not consider the use of cross-layer approaches, as the use of this type of architectures would not be compatible with the use of standard IEEE 802.15.4/ZigBee cluster-tree networks. Instead, it is focused on relevant approaches that can be implemented upon cluster-tree networks, regarding cluster-tree formation, its synchronisation, congestion control and data communication support in wide-scale cluster-tree networks.
Within this context, Zhu et al. [
53] proposed a Tree-Cluster-Based Data-Gathering Algorithm (TCBDGA) using a mobile sink to improve the non-uniform energy consumption of WSNs. The basic idea of this algorithm is to build a cluster-tree network considering specific characteristics of the nodes, such as their residual energy, distance to base station and number of neighbours. After this, the network is decomposed in several sub-trees and each sub-tree has its own set of collecting nodes. The mobile sink is responsible to collect data from nodes. This algorithm is a location-aware based algorithm, which implies more energy consumption and complexity. The communication approach proposed in this paper considers a static topology (no mobile nodes), where the information is gathered through message exchanges.
Choi and Lee [
13] implemented a multihop GTS mechanism for IEEE 802.15.4 beacon-enabled networks. The aim of this work is to allocate GTS slots from the requesting nodes to the sink node along the cluster-to-cluster path. In turn, Felske et al. [
19] proposed the GLHOVE approach for cluster-tree networks to maximise the number of received messages in the base station, prioritizing specific clusters of the network. GLHOVE comprises a distributed algorithm that guarantees a balanced message delivery per cluster and, at the same time, avoiding congestion. However, none of these approaches consider any message prioritisation mechanism.
Khatiri et al. [
54] and Kim et al. [
55] proposed two different approaches to decrease the number of hops to reach the sink node using the neighbouring table defined in the ZigBee standard. The purpose is to reduce the routing costs, improving the energy consumption, network lifetime and end-to-end delays. In [
54], each node keeps a neighbouring table with relevant information about the neighbouring nodes, such as: depth, link quality and device type. Thus, the algorithm defines the shortest path using three criteria: minimum hop count, minimum congestion and maximum link quality. Each criterion has its weight and the next hop (neighbour node) is selected based on a minimum cost function. In [
55], the algorithm inspects the neighbouring table in order to find a node with a shortest tree path until the destination node and selects it as next hop. Although these algorithms define shortest paths until the sink node, they do not consider any information about network scheduling (top-down or bottom-up), nor about how data communication is performed.
Misic [
56] presented an approach using border nodes (slave-slave bridge) to interconnect neighbouring clusters. The slave-slave bridge nodes listen to the beacons generated by source and sink clusters. During the source cluster active period, the bridge node can receive data from the coordinator, and during the sink cluster active period, the bridge node delivers its data to the sink coordinator. Considering this approach, the cluster-tree path is not used. Although using bridge nodes to avoid the cluster-tree path, data is transmitted during the clusters’ active period, and therefore, end-to-end delays are still dependent of the cluster scheduling.
Also, Huang et al. [
57] proposed an adoptive-parent-based framework for ZigBee networks, to increase the bandwidth between the source and sink nodes. For this, a specific cluster-head can request bandwidth from neighbour cluster-heads (adoptive parents) during a given time period. However, even using additional paths to transmit messages between source and sink nodes, these additional paths are cluster-tree paths and therefore the problem of a higher energy consumption of the cluster-heads still remains. The communication scheme proposed in this paper defines new alternative paths for message streams, instead of cluster-tree paths, which can improve end-to-end communication delays and reduce network congestion.
Regarding beacon frame scheduling, some relevant works have also been presented in [
7,
14,
15,
16,
39,
58]. The key idea of these works is to schedule the clusters’ active period, considering the main constraints imposed by the message streams supported by the cluster-tree network.
Toscano and Lo Bello [
15] and Abdeddaim et al. [
58] follow a multichannel approach to avoid overlapping cluster collisions, while maintaining the cluster connectivity. In [
15], the proposed approach schedules adjacent clusters in alternate timeslices, using different channels to avoid cross-channel interferences. Thus, while a coordinator schedules its own superframe, its adjacent clusters can not schedule their owns. Therefore, collisions are avoided between neighbour clusters. Following this approach, a specific cluster is able to receive the parent’s superframe in a given timeslice and schedule its superframe in an adjacent timeslice. The clusters are scheduled within a major cycle, which is cyclically repeated. In order to avoid inter-cluster collisions, a set composed of the PAN coordinator and all the clusters that can be reached in an even number of hops are scheduled in a given timeslice; then, all other clusters are scheduled in alternate timeslices. Abdeddaim et al. [
58] proposed an IEEE 802.15.4-based cluster-tree formation protocol, named Multi-Channel Cluster Tree (MCCT), which uses multiplexed transmissions across different channels, in order to avoid beacon collisions. In addition, it uses a shared control channel for the cluster-tree construction and maintenance operations. Thus, a node just scans the control channel to request an association. The joining node defines its parent cluster-head based on the number of associated children. The cluster-head with lower number of children is selected. Thus, the association process occurs during the active period, using the channel of the specific cluster-head. These works use multi-channel approaches in order to avoid beacon collisions, which add overheads related to the channel’s maintenance and control.
Koubaa et al. [
7] proposed the Time Division Beacon Frame Scheduling (TDBS) approach, which defines a Superframe Duration Scheduling (SDS) algorithm for cluster-tree networks. In this approach, superframe duration and beacon frames of a given cluster are scheduled in the inactive periods of its neighbour clusters to avoid inter-cluster interferences. The schedulability condition of SDS is both necessary and sufficient, and is obtained considering the duty cycle information of nodes [
15]. The TDBS approach defines minor and major cycles to schedule a cluster set with different superframe durations and beacon intervals. All clusters are organised within the defined major cycle, based on the Least Common Multiple (LCM) of the beacon periodicities for all clusters. The major cycle is divided in minor cycles, which are used to sequentially fit all clusters. In this approach, clusters are organised in an increasing order of beacon periodicities. To break ties, these clusters are organised in a decreasing order of superframe durations. Clusters are sequentially organised within the minor cycles, until reaching the end of the major cycle. TDBS defines the start time for all clusters in a collision-free scheduling scheme. However, it does not consider any message stream prioritisation and therefore may not be adequate to support time-sensitive applications.
Hanzalek and Jurcík [
14] present a Time-Division Cluster Scheduling (TDCS) mechanism to avoid inter-cluster collisions and to meet all end-to-end deadlines of time-bounded message streams. This mechanism employs a pure time-division scheduling approach, avoiding the inter-cluster collision problem. Besides, it aims to define the maximum TDCS period (major cycle) in order to minimise the energy consumption of the nodes. This is a challenging task because it is necessary to consider the message stream requirements, meeting all their end-to-end deadlines. To solve this problem, the authors formulate the TCDS approach as a cyclic extension of the Resource Constrained Project Scheduling with Temporal Constraints (RCPS/TC), which defines a feasible schedule considering the temporal and resource constraints of a set of tasks. After modelling this problem, they use an integer linear programming algorithm to solve the scheduling problem.
The main weakness of TDBS and TDCS approaches is the use of an off-line scheduling approach, that assumes static network conditions. Thus, Severino et al. [
39] presented an interesting alternative to modify the scheduling at run-time, in order to provide QoS (Quality of Service) to message streams. Basically, they proposed the use of two different techniques: Dynamic Cluster Re-ordering (DCR) and Dynamic Bandwidth Re-allocation (DBR). The DCR technique is used to re-order at run-time the cluster scheduling. The clusters involved in the data streams are re-ordered, in order to minimise the traffic latency. This re-scheduling is performed based on the priority of the data streams, in order to decrease end-to-end communication delays. In turn, the DBR technique is used to change the superframe duration of the clusters, increasing the bandwidth of the clusters involved in the message stream. This technique uses the free space (not used to allocate clusters) and distributes it among the involved clusters. If there is no available free space, it tries to reduce the bandwidth of the non-involved clusters, in order to re-distribute it among the involved clusters. Unfortunately, this communication approach only considers the use of cluster-tree paths.
While TDBS and TDCS approaches just address upstream communication traffic (convergecast pattern), Yeh and Pan [
16] proposed an efficient beacon scheduling approach to support low-latency upstream and downstream traffic. The authors formulate the Low-latency Two-way Beacon Scheduling (LTBS) problem for ZigBee networks. In this problem, nodes try to get slots for upstream and downstream traffic, while avoiding interferences from other clusters. LTBS modifies the IEEE 802.15.4 original superframe structure, in order to allow each cluster-head to broadcast two beacons: one for upstream direction and another for downstream direction. The authors propose two algorithms (centralised and distributed) to assign interference-free upstream and downstream slots to reduce the network latency. Basically, the difference between centralised and distributed approaches is the sequencing order. The centralised algorithm assigns slots using a bottom-up approach. On the other hand, the distributed algorithm assigns slots using a top-down approach. This proposal minimises the network latency without considering any message stream prioritisation.
Although improving the performance of cluster-tree networks, the efficiency of the proposed communication schemes is upper-bounded by the cluster-tree routing scheme and its inherent problems, such as: network congestion near the PAN coordinator [
19], poor bandwidth allocation to the different clusters, and higher energy consumption of crucial nodes.