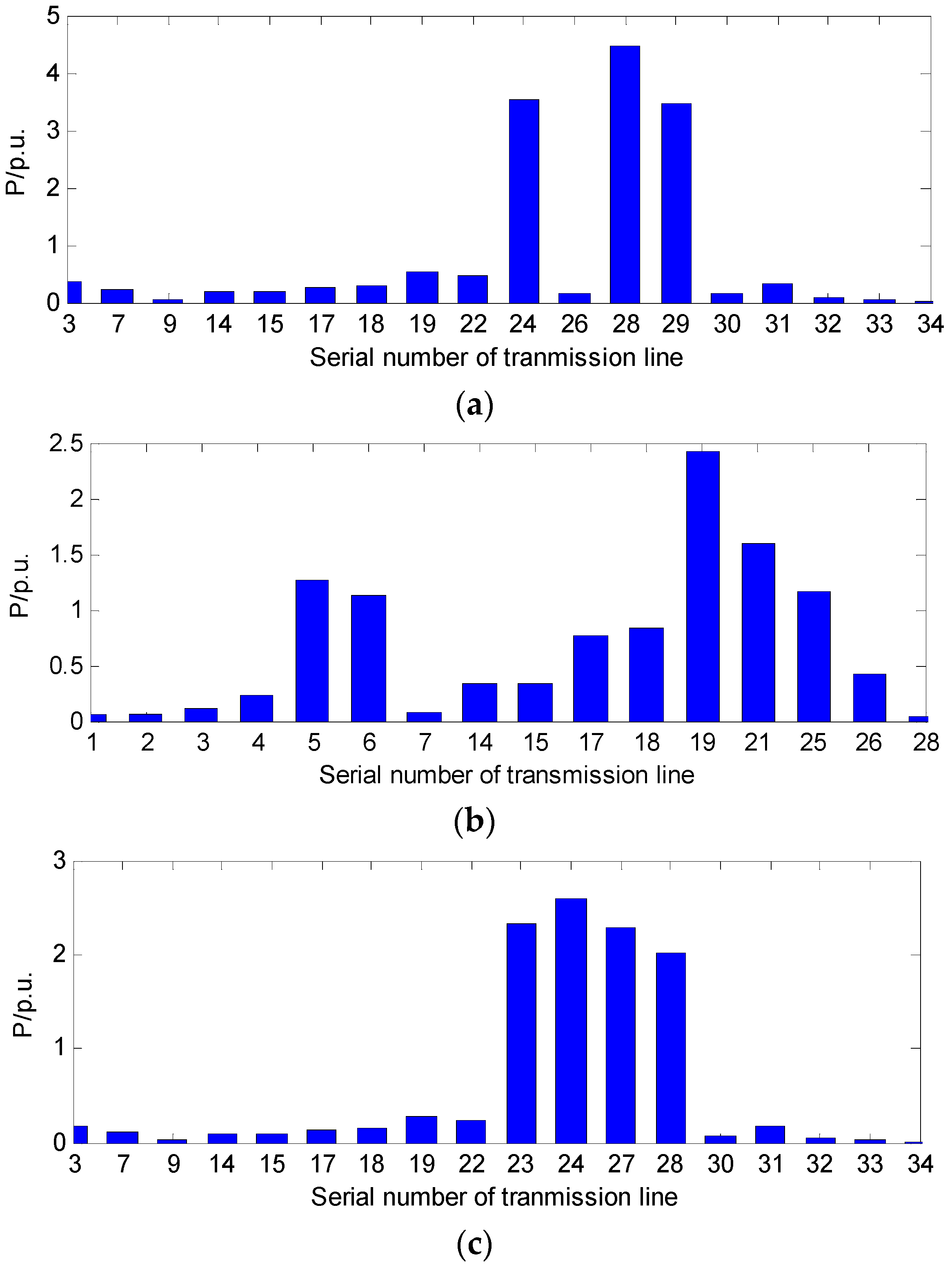
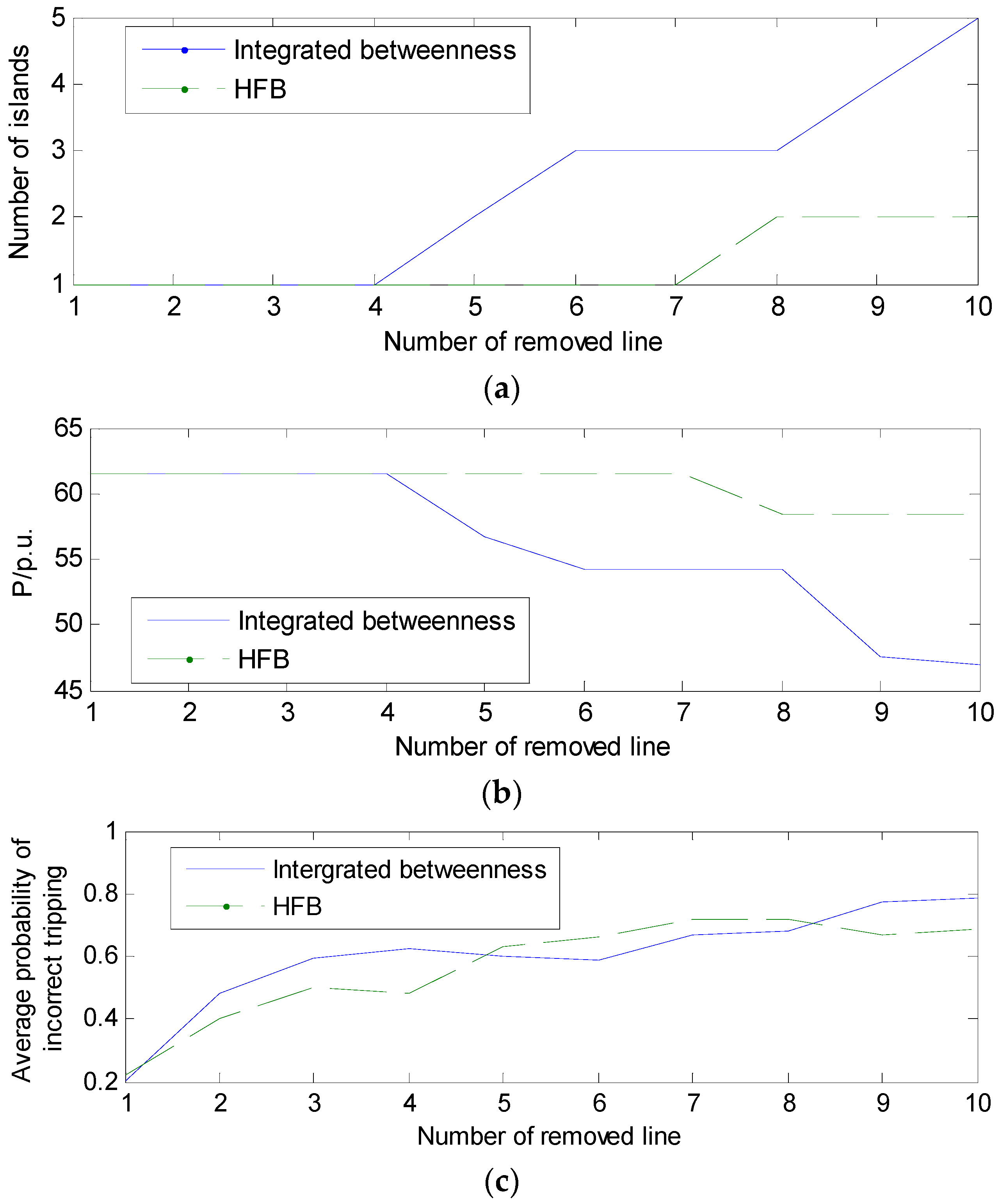
The integrated betweenness of each line is affected by the changes in the grid’s structure or the operating mode. The calculation time is large when the approach is applied to the data of the whole power network. In fact, Di, Hi, and Ci are all related to the changes of power flow before and after line i is removed, where the changes mainly occur on particularly sensitive lines. Therefore, a cyclic addition algorithm (CAA) is proposed to locate the sensitive regions which consist of the transmission lines with large variations of power. The impact on the sensitive regions is analyzed rather than the impact on the whole power network. Thus, the calculation time of the betweenness can be significantly reduced and the proposed identification method is more suited to the real-time analysis.
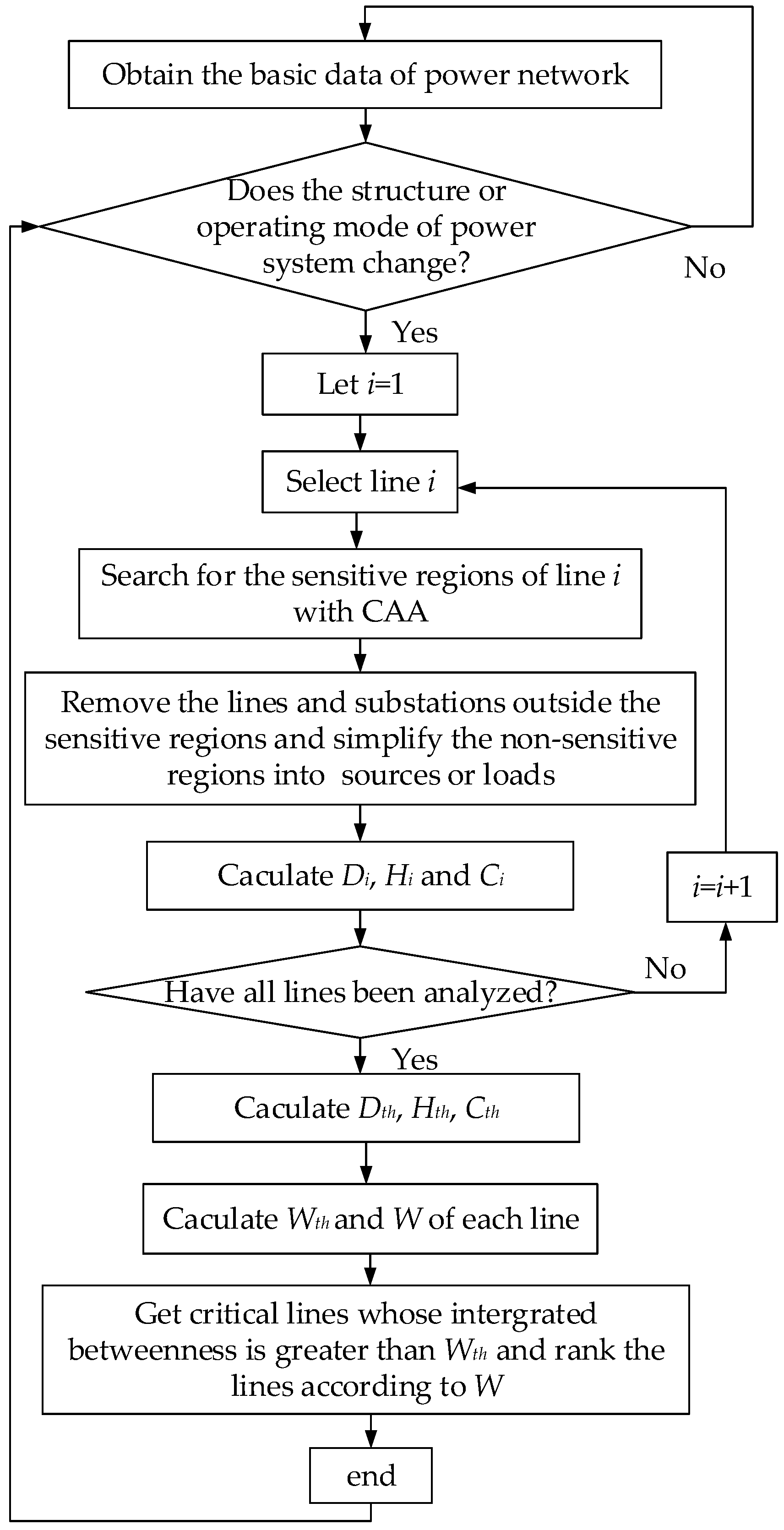
The process to identify the critical transmission lines is shown in
Figure 1. First, the basic data of the grid, such as the structural parameters and the information of power flow, are obtained. The data can be collected by phasor measurement units (PMUs). When the network structure or operating mode changes, the identification process of critical lines in this state will start. Possible changes of the network structure or operating mode include the disconnection/failure of primary equipment (generators, transformers, or lines), the connection/reconnection of primary equipment, and significant redistribution of power flow within the grid. Such changes can be caused by (1) faults, e.g., line trip, generator trip, and line failure; (2) planned adjustments, e.g., the operation of new generators/lines and planned load shedding. Then
Wth and the integrated betweenness of each line are calculated: sensitive regions can be located by CAA, and the remaining regions are regarded as non-sensitive regions in this study. Since the influence of the non-sensitive regions on the calculation results is quite small, those regions can be simplified as sources and loads. The number of lines and substations in the system is greatly reduced after the simplification, so that the integrated betweenness
W can be calculated more quickly. With the calculation method introduced in
Section 2,
W of each line can be obtained. Finally, the critical lines can be identified.
Location of Sensitive Regions with CAA
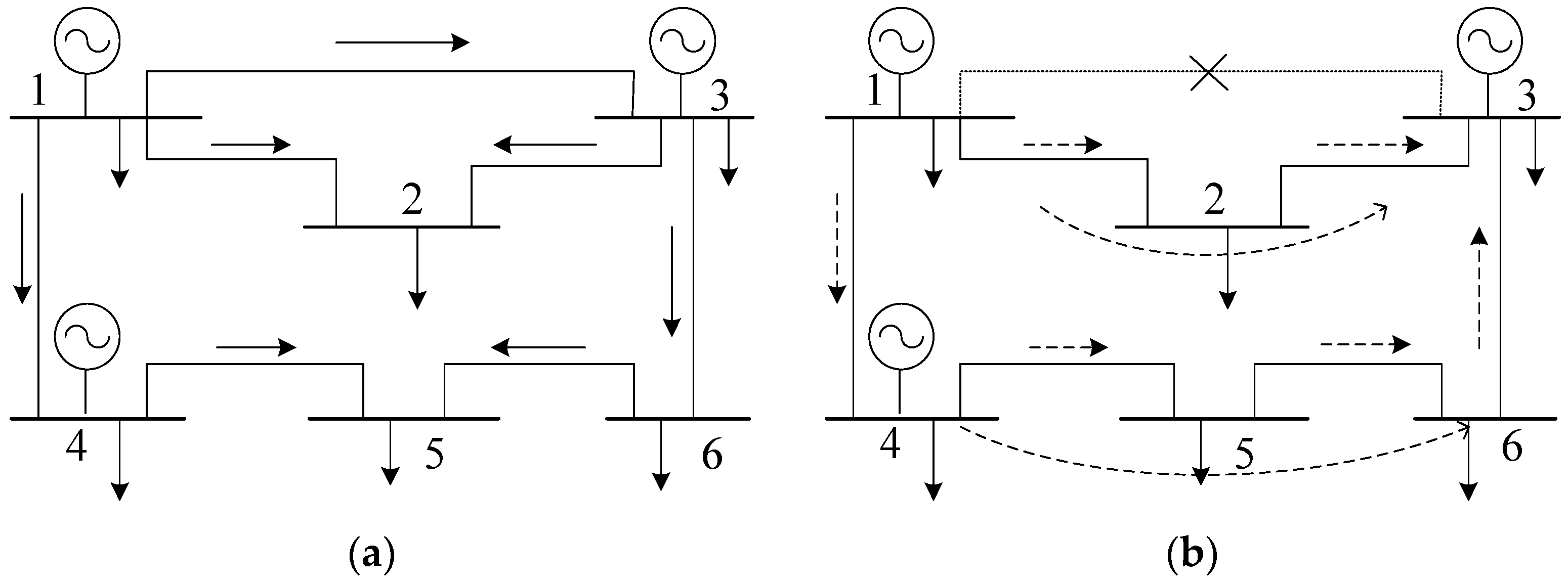
The power flow is transferred on all feasible paths, but the transferred power on each path is quite different. As can be seen from previous studies [
26,
27,
28,
29,
30,
31], when a transmission line is disconnected or removed from the power network, the power is usually transferred to other paths connected with the two-end nodes of the removed line, and mainly along the paths with short electrical distances, as is shown in
Figure 2.
The topological analysis-based method can provide a quick and effective way to identify the network structure and find propagation paths of power flow transfer [
34]. Some new approaches, such as the compressive sensing-based approach [
35] and graphical learning-based approach [
36,
37] were proposed in recent years. Based on Dijkstra’s algorithm [
38], CAA is proposed in this study. The sensitive regions can be obtained through the cyclic addition of different lines. The following is a detailed description of the process.
Supposing there are a substations and b lines, all substations in the power grid can be simplified as nodes and form V according to graph theory, as is V = {v1, v2, ..., va}. All lines are represented by the edge set E, E = {e1, e2, e3, …, eb}. V and E constitute G(V, E), the topology graph of the power grid. All different paths connecting vi and vj in graph G form set D(G, vi, vj), and the length of path d is l(d). The line reactance is used as the weight of an edge, and l(d) is the sum of the weights of all edges in path d.
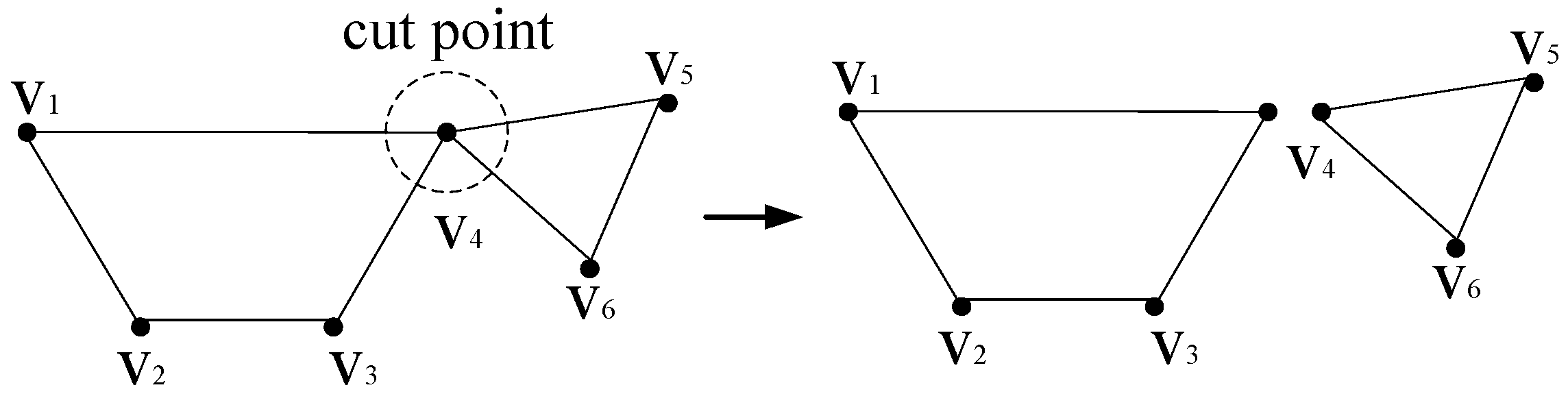
Theoretical principle 1: According to graph theory, if G cannot be fully connected when node v is removed, v is called the cut point in G, such as point v
4 in
Figure 3. Any edge and the paths connected with its two ends can only exist in the same part divided by cut points.
Theoretical principle 2: According to the conclusion in Reference [
39], any path between two nodes in graph G(V, E) must be the shortest path between the same nodes in G
g (V
g, E
g), where G
g is a sub-graph of G with a few (including
b) edges. It can be described as:
where
dshortest (G
g,
vp,
vq) is the shortest path between
vp and
vq in graph G
g. Therefore, the path between two nodes in G(V, E) can be transformed into the shortest path between the same nodes in a sub-graph.
In this study, line e0 is defined as the removed line, while vp and vq are its two-end nodes. Vector L is built to store the shortest distance between any two nodes which has been found currently. For the graph with a nodes, there are Ca2 elements in L and the elements can be described as L(1–2), L(1–3), L(1–4), …, L(1–a), L(2–3), L(2–4), …, L((a − 1)–a), where L(i–j) is the shortest distance between vi and vj, and i and j can be interchanged. Vector HJ is built to store the successor nodes along the shortest path. Similarly, there are Ca2 elements in HJ and the elements can be described as HJ(1–2), HJ(1–3), HJ(1–4), …, HJ(1–n), HJ(2–3), HJ(2–4), …, HJ((a − 1)–a). Each sub-graph has corresponding values for L and HJ.
Step 1: Find cut points and divide the graph into different parts. Find the parts G’ where e0 is located. Suppose that there are m lines and n nodes in G’. Delete e0 and get all the other edges in graph G’. Let k = 1.
Step 2: Select k edges, and there are Cm−1k different selection results. Let c = 1.
Step 3: Deal with the selection result c, where k edges and their connected nodes constitute a sub-graph G’kc. If vp or vq is an isolated node without any connected lines, or vp and vq are located in different islands in G′kc, go to step 8, i.e., the sub-graph can be ignored directly; otherwise go to step 4.
Step 4: Take away and rank k edges. Let f = 1 and initialize Lkc and HJkc. When there is no edge in graph G’kc, the values of the elements in Lkc are equal to an infinite value, as is Lkc = [∞, ∞, ∞, …, ∞]. All elements in HJkc are Ø, showing there is no path currently.
Step 5: Put edge f back. The two-end nodes of f are vu and vv, vu and vv V′kc. Next apply the following judgment: If Lkc(u − v) < l(f), go directly to step 7. Otherwise, let Lkc(u − v) = l(f), HJkc(u − v) = v, and go to step 6.
Step 6: Deal with Lkc and HJkc:
For w (1 ≦ w ≦ n, w ≠ u, w ≠ v):
If Lkc(u − w) > Lkc(u − v) + Lkc(v − w), change the value of Lkc(u − w) into Lkc(u − v) + Lkc(v − w), and change HJkc(u − w) into v; If Lkc(v − w) > Lkc(u − v) + Lkc(u − w), change the value of Lkc(v − w) into Lkc(u − v) + Lkc(u − w), and change HJkc(v − w) into u;
If Lkc(u − w) = Lkc(u − v) + Lkc(v − w) ≠ ∞, insert v into HJkc(u − w); If Lkc(v − w) = Lkc(u − v) + Lkc(u − w) ≠ ∞, insert u into HJkc(v − w); then go to step 7.
Step 7: If f = k, go to step 8; otherwise f = f + 1, then go back to step 5.
Step 8: If c = Cm−1k, go to step 9; otherwise c = c + 1, then go back to step 3.
Step 9: if k = m−1, go to step 10; otherwise k = k + 1, then go back to step 2.
Step 10: All the paths between vp and vq and their lengths can be got. Remove duplicate paths.
Supposing that there are
y paths between v
p and v
q, the lengths of all paths (
l(1),
l(2), ...,
l(
y)) can be derived by the above process. According to the principle of electric circuits, the transferred power flow on path
d changes inversely with the length
l(
d). Thus, the power sharing coefficient of edge
i is:
where
μ is the set of paths which contain line
i. Judge whether the power sharing coefficient can satisfy:
where
ξth is the threshold value,
ξth ≥ 0. If (23) is satisfied, line
i will be regarded as a sensitive line, as is closely related to line e
0. The sensitive lines should be selected effectively and the sensitive regions which consist of sensitive lines should be fully connected. According to the definition of sensitive lines or transmission sections in Reference [
40], the threshold value usually varies between 0.2 and 0.3. Based on the above analysis, the threshold
ξth can be obtained by the following iterative process:
ξth is initialized with 0.3. If the sensitive regions are not fully connected,
ξth will be decreased with a fixed step size, until the requirement of full connection can be satisfied or the value of
ξth is 0.
To improve the accuracy of integrated betweenness and to avoid missing sensitive lines, ξth can be taken as 0 directly in an extreme situation.
Sensitive regions can be obtained by the above process. For G′ with
m lines and
n nodes, the calculation amount of the cyclic process in CAA in the worst condition is:
where
P = 1 means that one element in
L or
HJ is updated once. For G′ with
m lines and
n nodes. C
m−1k is the number of sub-graphs with
k lines. In the worst case, all sub-graphs can satisfy the requirement in step 3, and none will be ignored. 2(
n − 2) + 1 elements in
L and 2(
n − 2) + 1 elements in
HJ are updated when one transmission line is put back through steps 5 and 6. The process of CAA only contains some simple comparisons based on a pure topology model. Therefore, the calculation time of the identification method can be significantly reduced. At the same time, it should be noticed that CAA is effective for most lines in power systems. For the lines which do not have other paths connected with their two ends, the removal of the lines can result in the islanding phenomenon. In these cases, the injected power of sources and absorbed power of loads in each island should be balanced first. After that, the calculation of the integrated betweenness can be carried out using the analysis of the whole power network.