IoT Privacy and Security Challenges for Smart Home Environments
Abstract
:1. Introduction
2. Key Issues in Cyber Security and Privacy
3. IoT Application Domains
IoT and the Smart Home
4. Security Threats in the Smart Home
4.1. Threats
4.2. Vulnerabilities
4.3. Vulnerability Example
5. Some Existing Security Support for IoT
5.1. 6LoWPAN and Security
5.2. RPL and Security
5.3. CoAP and Security
5.4. Future IoT Security Directions
6. A Suitable Smart Home Architecture for Security
6.1. Middleware Architectures and Security
6.2. Cloud Architectures and Security
6.3. Gateway Architectures
7. Future Smart Home Security Challenges
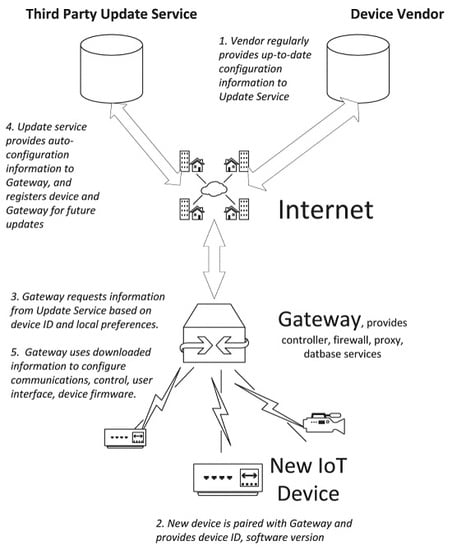
7.1. Auto-Configuration Support
7.2. IoT Software and Firmware Updates
8. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
Abbreviations
| 6LoWPAN | IP version 6 Low power Wireless Personal Area Network protocol |
| AES | Advanced Encryption Standard |
| AH | Authentication Headers |
| AIOTI | The Alliance for Internet of Things Innovation |
| API | Application Programming Interface |
| CoAP | Constrained Application Protocol |
| CoT | Cloud of Things |
| CPU | Central Processing Unit |
| DHCP | Dynamic Host Configuration Protocol |
| DNS | Domain Name Service |
| DODAG | Destination Oriented Directed Acyclic Graph |
| DTLS | Datagram Transport Layer Security |
| EAKES6Lo | Enhanced authentication and key establishment scheme for 6LoWPAN networks |
| ECC | Elliptic Curve Cryptography |
| ESP | Encapsulating Security Payloads |
| FTP | File Transfer Protocol |
| GITAR | Generic extension for Internet-of-Things ARchitectures |
| GPS | Global Positioning System |
| HAL | Hardware Abstraction Layer |
| HAN | Home Area Network |
| HI | Host Identity |
| HIL | Hardware Interface Layer |
| HIP | Host Identity Protocol |
| HIPDEX | Host Identity Protocol Diet Exchange |
| HIT | Host Identity Tag |
| HMS | Home Management System |
| HRA | Home Registration Authority |
| HTTP | HyperText Transport Protocol |
| HTTPS | HyperText Transport Protocol Secure |
| IAGW | Integrated Access Gateway |
| IEEE | Institute of Electrical and Electronics Engineers |
| IETF | Internet Engineering Task Force |
| IoT | Internet of Things |
| IP | Internet Protocol |
| IPSec | Internet Protocol Security |
| IPv6 | Internet protocol version 6 |
| IT | Information Technology |
| MAC | Media Access Control/Message Authentication Code |
| MTU | Minimum Transmission Unit |
| NIST | National Institute of Standards and Technology |
| QoS | Quality of Service |
| RA | Registration Authority |
| REST | Representational State Transfer |
| RFC | Request For Comment |
| RFID | Radio Frequency Identification |
| RPL | Routing Protocol for Low-Power and Lossy Networks |
| RSA | Rivest Shamir Adleman |
| RTSP | Real Time Streaming Protocol |
| SASL | Simple Authentication and Security Layer |
| SBIOTA | Server-Based Internet-Of-Things Architecture |
| SHA | Secure Hash Algorithm |
| SIP | Session Initiation Protocol |
| SMACK | Short Message Authentication ChecK |
| SMEPP | Secure Middleware for Embedded Peer-to-Peer systems |
| SSH | Secure Shell |
| TACIoT | Trust-aware access control system for IoT |
| TCP | Transmission Control Protocol |
| TLS | Transport Layer Security |
| TRAIL | Trust Anchor Interconnection Loop |
| UDP | User Datagram Protocol |
| UK | United Kingdom |
| US | United States |
| WPAN | Wireless Personal Area Networks |
| XMPP | eXtensible Messaging and Presence Protocol |
References
- Atzori, L.; Iera, A.; Morabito, G. The internet of things: A survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Evans, D. The internet of things: How the next evolution of the internet is changing everything. 2011. Available online: http://www.cisco.com/c/dam/en_us/about/ac79/docs/innov/IoT_IBSG_0411FINAL.pdf (accessed on 8 July 2016).
- George, F.H. The internet of things: A reality check. IEEE Comput. Soc. 2012, 14, 56–59. [Google Scholar]
- Gartner Inc. Hype cycle research methodology. Available online: http://www.gartner.com/technology/research/methodologies/hype-cycle.jsp (accessed on 8 February 2016).
- European Commission. The alliance for internet of things innovation (AIOTI). Available online: https://ec.europa.eu/digital-single-market/alliance-internet-things-innovation-aioti (accessed on 11 January 2016).
- National Intelligence Council (NIC). Disruptive Civil Technologies Six Technologies with Potential Impacts on Us Interests out to 2025; Conference Report CR; National Intelligence Council (NIC): Washington, DC, USA, 2008. [Google Scholar]
- PricewaterhouseCoopers (PwC). Information Security Breaches Survey 2015; HM Government: London, UK, 2015.
- Xu, L.D.; He, W.; Li, S. Internet of things in industries: A survey. IEEE Trans. Ind. Inform. 2014, 10, 2233–2243. [Google Scholar] [CrossRef]
- Yu, L.; Lu, Y.; Zhu, X. Smart hospital based on internet of things. J. Netw. 2012, 7, 1654–1661. [Google Scholar] [CrossRef]
- Mars, M. Telemedicine and advances in urban and rural healthcare delivery in africa. Prog. Cardiovasc. Dis. 2013, 56, 326–335. [Google Scholar] [CrossRef] [PubMed]
- Wade, V.; Soar, J.; Gray, L. Uptake of telehealth services funded by medicare in australia. Aust. Health Rev. 2014, 38, 528–532. [Google Scholar] [CrossRef] [PubMed]
- Fleming, B. Advances in automotive electronics (automotive electronics). IEEE Veh. Technol. Mag. 2014, 9, 4–19. [Google Scholar] [CrossRef]
- Karagiannis, G.; Altintas, O.; Ekici, E.; Heijenk, G.; Jarupan, B.; Lin, K.; Weil, T. Vehicular networking: A survey and tutorial on requirements, architectures, challenges, standards and solutions. IEEE Commun. Surv. Tutor. 2011, 13, 584–616. [Google Scholar] [CrossRef]
- Attaran, M. Critical success factors and challenges of implementing RFID in supply chain management. J. Supply Chain Operat. Manag. 2012, 10, 144–167. [Google Scholar]
- Zou, Z.; Chen, Q.; Uysal, I.; Zheng, L. Radio frequency identification enabled wireless sensing for intelligent food logistics. Philos. Trans. R. Soc. Lond. A Math. Phys. Eng. Sci. 2014, 372. [Google Scholar] [CrossRef]
- Ricquebourg, V.; Menga, D.; Durand, D.; Marhic, B.; Delahoche, L.; Loge, C. The Smart Home Concept: Our Immediate Future. In Proceedings of the 2006 1st IEEE International Conference on E-Learning in Industrial Electronics, Hammamet, Tunisia, 18–20 December 2006; pp. 23–28.
- Alam, M.R.; Reaz, M.B.I.; Ali, M.A.M. A Review of Smart Homes—Past, present, and future. IEEE Trans. Syst. Man Cybern. Part C (Appl. Rev.) 2012, 42, 1190–1203. [Google Scholar] [CrossRef]
- Patton, M.; Gross, E.; Chinn, R.; Forbis, S.; Walker, L.; Hsinchun, C. Uninvited connections: A study of vulnerable devices on the Internet of Things (IoT). In Proceedings of the 2014 IEEE Joint Intelligence and Security Informatics Conference (JISIC), The Hague, The Netherlands, 24–26 September 2014; pp. 232–235.
- Durumeric, Z.; Adrian, D.; Mirian, A.; Bailey, M.; Halderman, J.A. A search engine backed by internet-wide scanning. In Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, Denver, CO, USA, 12–16 October 2015; pp. 542–553.
- Thubert, P. Compression Format for Ipv6 Datagrams over IEEE 802.15.4-Based Networks; RFC 6282; Hui, J., Ed.; Internet Engineering Task Force: Fremont, CA, USA, 2011. [Google Scholar]
- Brandt, A.; Hui, J.; Kelsey, R.; Levis, P.; Pister, K.; Struik, R.; Vasseur, J.P.; Alexander, R. RPL: IPv6 Routing Protocol for Low-Power and Lossy Networks; RFC 6550; Winter, T., Thubert, P., Eds.; Internet Engineering Task Force: Fremont, CA, USA, 2012. [Google Scholar]
- Shelby, Z.; Hartke, K.; Bormann, C. The Constrained Application Protocol (Coap); RFC 7252; Internet Engineering Task Force: Fremont, CA, USA, 2014. [Google Scholar]
- Shelby, Z.; Bormann, C. 6lowpan: The Wireless Embedded Internet; John Wiley & Sons: New York, NY, USA, 2011; Volume 43. [Google Scholar]
- Raza, S.; Duquennoy, S.; Chung, T.; Yazar, D.; Voigt, T.; Roedig, U. Securing Communication in 6lowpan with Compressed Ipsec. In Proceedings of the 2011 International Conference on Distributed Computing in Sensor Systems and Workshops (DCOSS), Barcelona, Spain, 27–29 June 2011; pp. 1–8.
- Yue, Q.; Maode, M. An authentication and key establishment scheme to enhance security for m2m in 6lowpans. In Proceedings of the 2015 IEEE International Conference on Communication Workshop (ICCW), London, UK, 8–12 June 2015; pp. 2671–2676.
- Perrey, H.; Landsmann, M.; Ugus, O.; Schmidt, T.C.; Wahlisch, M. Trail: Topology Authentication in RPL. 2013; arXiv:1312.0984v2. [Google Scholar]
- Kenji, I.; Matsunaga, T.; Toyoda, K.; Sasase, I. Secure parent node selection scheme in route construction to exclude attacking nodes from rpl network. IEICE Commun. Exp. 2015, 4, 340–345. [Google Scholar] [CrossRef]
- Dierks, T.; Rescorla, E. The Transport Layer Security (Tls) Protocol Version 1.2; RFC 5246; Internet Engineering Task Force: Fremont, CA, USA, 2008. [Google Scholar]
- Rescorla, E.; Modadugu, N. Datagram Transport Layer Security Version 1.2; RFC 6347; Internet Engineering Task Force: Fremont, CA, USA, 2012. [Google Scholar]
- Conzon, D.; Bolognesi, T.; Brizzi, P.; Lotito, A.; Tomasi, R.; Spirito, M.A. The virtus middleware: An xmpp based architecture for secure iot communications. In Proceedings of the 2012 21st International Conference on Computer Communications and Networks (ICCCN), Munich, Germany, 30 July–2 August 2012; pp. 1–6.
- Caro-Benito, R.J.; Garrido-Márquez, D.; Plaza-Tron, P.; Sanz-Martín, N.; Serrano-Martín, J.L.; Castro, R.R. Smepp: A secure middleware for embedded p2p. In Proceedings of ICT-MobileSummit; ScienceOpen: Frankfurk, Germany, 2009; Volume 9. [Google Scholar]
- Kovatsch, M.; Lanter, M.; Shelby, Z. Californium: Scalable cloud services for the internet of things with coap. In Proceedings of the 2014 International Conference on the Internet of Things (IoT), Cambridge, MA, USA, 6–8 October 2014.
- Alohali, B.; Merabti, M.; Kifayat, K. A secure scheme for a smart house based on cloud of things (cot). In Proceedings of the 2014 6th Computer Science and Electronic Engineering Conference (CEEC), Colchester, UK, 25–26 September 2014; pp. 115–120.
- Ding, F.; Song, A.; Tong, E.; Li, J. A smart gateway architecture for improving efficiency of home network applications. J. Sens. 2016, 2016. [Google Scholar] [CrossRef]
- Bergmann, N.W.; Robinson, P.J. Server-based internet of things architecture. In Proceedings of the 2012 IEEE Consumer Communications and Networking Conference (CCNC), Las Vegas, NV, USA, 14–17 January 2012; IEEE: New York, NY, USA; pp. 360–361.
- Ruckebusch, P.; de Poorter, E.; Fortuna, C.; Moerman, I. Gitar: Generic extension for internet-of-things architectures enabling dynamic updates of network and application modules. Ad Hoc Netw. 2016, 36, 127–151. [Google Scholar] [CrossRef]



© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lin, H.; Bergmann, N.W. IoT Privacy and Security Challenges for Smart Home Environments. Information 2016, 7, 44. https://doi.org/10.3390/info7030044
Lin H, Bergmann NW. IoT Privacy and Security Challenges for Smart Home Environments. Information. 2016; 7(3):44. https://doi.org/10.3390/info7030044
Chicago/Turabian StyleLin, Huichen, and Neil W. Bergmann. 2016. "IoT Privacy and Security Challenges for Smart Home Environments" Information 7, no. 3: 44. https://doi.org/10.3390/info7030044